Introduction
In the contemporary digital era, where businesses increasingly rely on cloud computing, the importance of robust cloud security cannot be overstated. As organizations transition their operations to the cloud, they face an escalating array of threats that jeopardize sensitive data and operational integrity. Recent statistics underscore a troubling trend: cloud security breaches have surged significantly, affecting a substantial portion of businesses worldwide.
The financial implications of these breaches can be staggering, with average losses reaching millions, not to mention the reputational damage that can linger for years. This article delves into the essential role of cloud security in safeguarding business interests, exploring the myriad benefits of implementing effective security measures, the various solutions available, and the best practices that can help organizations fortify their defenses against an evolving threat landscape. Understanding the risks associated with inadequate cloud security is paramount for any organization aiming to thrive in today's technology-driven marketplace.
The Essential Role of Cloud Security in Business Protection
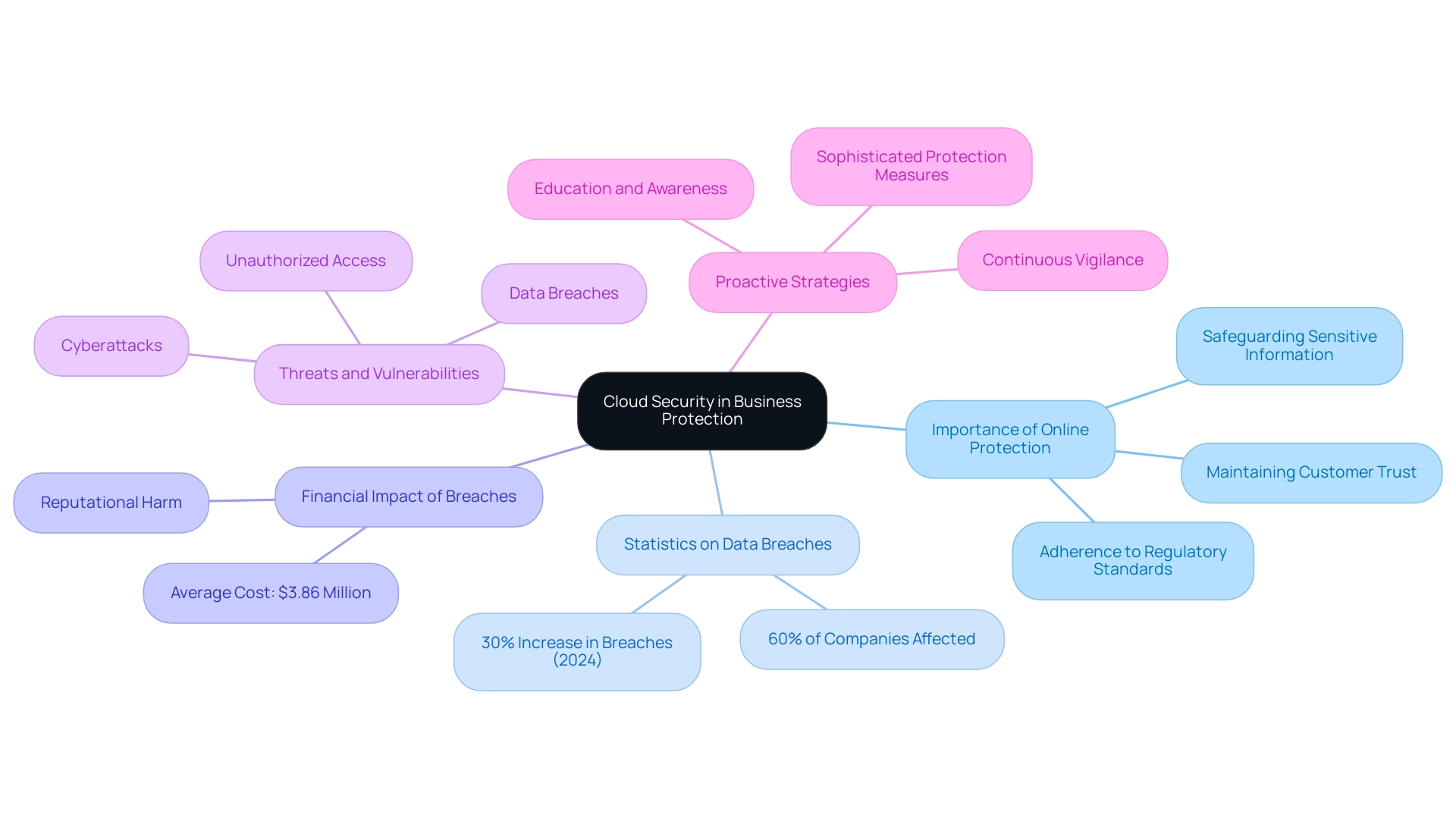
In the quickly changing digital environment, online protection has emerged as a fundamental pillar of business safeguarding. As organizations progressively shift their operations to online platforms, the protection of sensitive information becomes essential. Recent statistics show that in 2024, breaches in online data protection have increased by 30%, impacting more than 60% of companies worldwide.
Cloud protection measures are intended to safeguard against unauthorized access, data breaches, and cyberattacks—threats that can lead to significant financial losses, averaging $3.86 million per data breach, along with irreparable reputational harm. For example, a prominent financial organization established sophisticated online protection measures and effectively prevented a possible breach that might have endangered millions of customer records.
With the increase in online service reliance, the potential for vulnerabilities amplifies, requiring strong protection measures to maintain customer trust and ensure adherence to regulatory standards. As Eric Raymond aptly states,
Being able to break into systems doesn’t make you a hacker any more than being able to hotwire cars makes you an automotive engineer.
This perspective highlights the complexity and urgency of cybersecurity, reinforcing the need for continuous vigilance and proactive strategies. Thus, a thorough comprehension of online protection is vital for any entity striving to thrive in a technology-oriented market.
Key Benefits of Implementing Cloud Security Measures
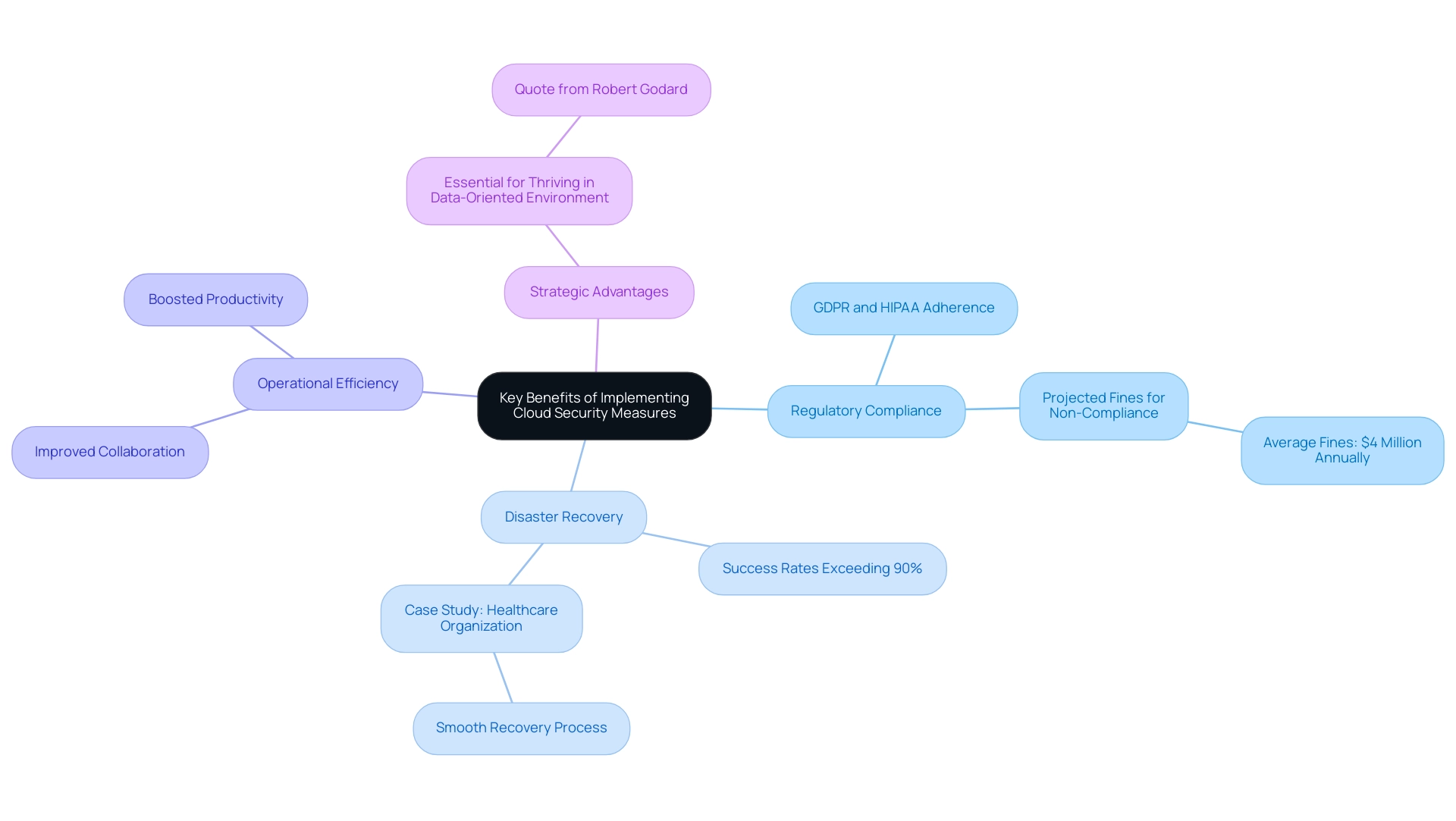
Implementing cloud protection measures offers a multitude of advantages that extend well beyond basic defense. For entities handling sensitive data, adherence to regulations such as GDPR and HIPAA is essential. Cloud protection solutions are often designed with features that facilitate adherence to these regulations, significantly mitigating the risk of incurring costly fines, which are projected to increase in 2024 due to stricter enforcement. Recent reports indicate that entities failing to comply could face fines averaging $4 million annually, underscoring the financial stakes involved.
Furthermore, the incorporation of strong online protection not only improves regulatory adherence but also bolsters disaster recovery abilities. Statistics indicate that entities employing online protection strategies for disaster recovery report success rates surpassing 90%, demonstrating their efficiency in rapidly reinstating operations after a breach or loss of information.
For example, a significant case study involving a healthcare organization illustrated how adopting online protection not only ensured adherence to HIPAA but also enabled a smooth recovery process following an information incident, allowing the organization to resume operations within hours. The recent success stories from various sectors highlight the significance of these digital solutions.
Moreover, investing in online protection can result in improved operational efficiency, facilitating smooth collaboration and data access among teams, ultimately boosting productivity. As Robert Godard, a Principal at I.S. Partners, LLC, emphasizes,
The strategic benefits of online protection are essential for entities aiming to thrive in today’s data-oriented environment.
In summary, the advantages of online protection are diverse, providing organizations with the essential resources for both safeguarding and development.
Exploring Different Types of Cloud Security Solutions
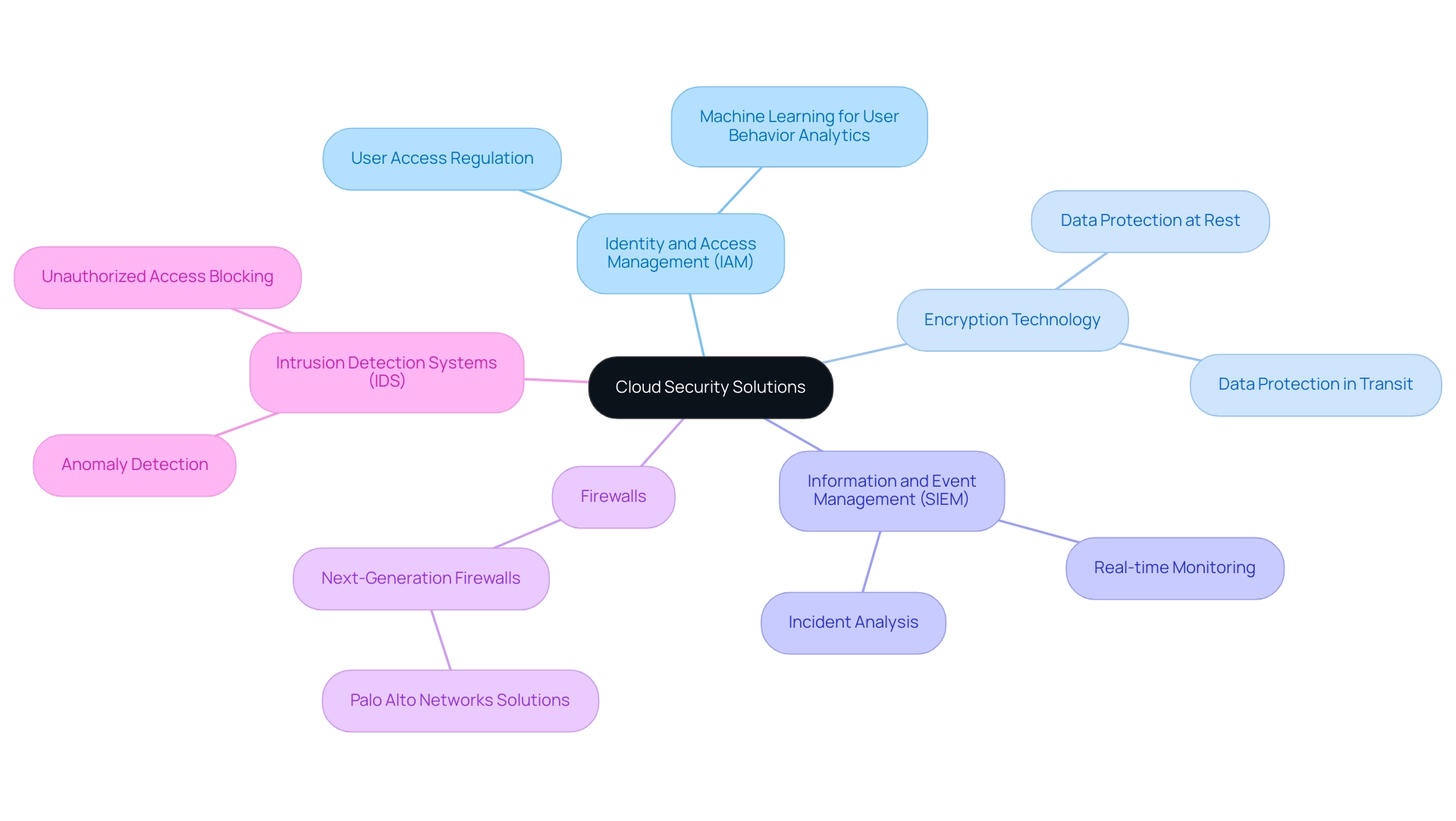
Security in the digital realm includes a wide range of solutions specifically created to protect information and applications within the online environment. Among the most critical components is identity and access management (IAM), which plays a pivotal role in regulating user access to online resources. Efficient IAM solutions guarantee that only permitted individuals can access sensitive information, thereby minimizing the risk of breaches. As noted by cybersecurity expert John Doe, 'The role of identity and access management in cloud safety cannot be overstated; it is a fundamental layer of protection against unauthorized access.'
Complementing IAM is encryption technology, which secures data both at rest and during transit, effectively protecting it from unauthorized interception. Moreover, information and event management (SIEM) systems provide real-time monitoring and thorough analysis of incidents, allowing entities to react quickly to possible threats.
In addition, advanced firewalls and intrusion detection systems (IDS) act as crucial safeguards, blocking unauthorized access and detecting anomalies within the network. As entities explore these different forms of online protection solutions, they can enhance their defensive stance against a changing threat environment. Significantly, worldwide expenditure on cybersecurity products and services is expected to attain an impressive $1.75 trillion cumulatively from 2021 to 2025, highlighting the essential requirement for efficient online protection measures.
In 2024, the newest online protection solutions comprise improved IAM features that employ machine learning for more precise user behavior analytics, enabling proactive threat detection. A prime example of innovation in this field is demonstrated by Palo Alto Networks, Inc., which offers next-generation firewalls and endpoint protection to counteract cyber threats. Their subscription services for threat detection and prevention have significantly enhanced protective measures against a variety of cyberattack methods, including phishing, SQL injection attacks, and DDoS attacks. By thoroughly exploring and implementing these varied online protection solutions, entities can customize their strategies to effectively tackle specific risks and compliance requirements, ensuring that IAM remains a robust and effective aspect of their protection framework.
Best Practices for Ensuring Robust Cloud Security
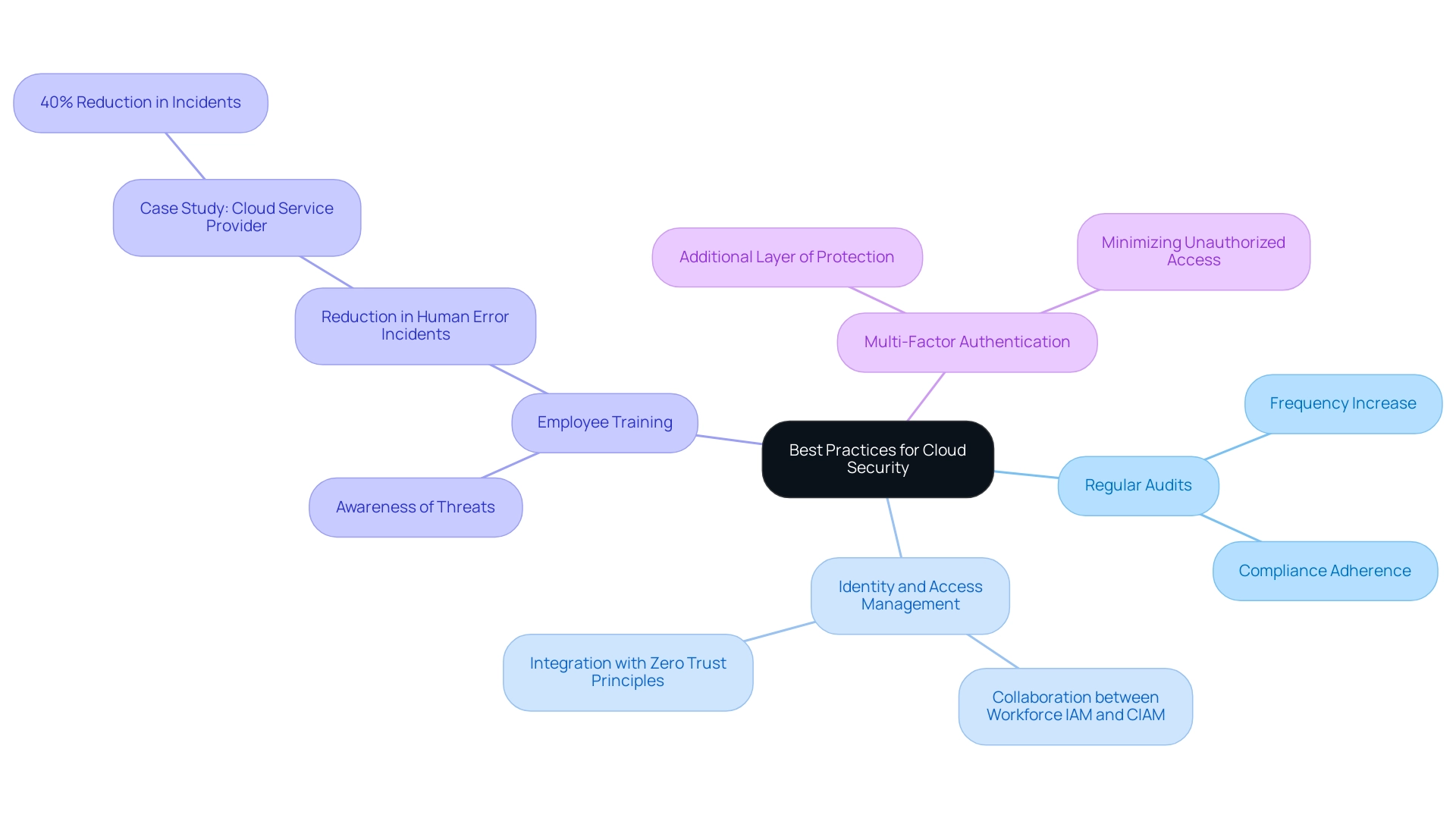
To create a strong framework for online protection, entities must adopt a series of best practices. Regular audits and assessments are essential for identifying vulnerabilities and ensuring adherence to compliance requirements. In fact, a recent survey indicates that the frequency of safety audits in companies is expected to rise by 30% in 2024, highlighting their increasing significance in the evolving environment of digital protection.
Furthermore, a strong identity and access management strategy is imperative; collaboration between Workforce IAM and CIAM is leading to significant advancements in controlling user access and minimizing insider threats. Recent trends show that organizations are increasingly adopting identity verification technologies and integrating them with zero trust architectural design principles, which enhances this approach and fosters innovation in digital identity management.
Additionally, prioritizing employee training on awareness of threats is critical, given that human error remains a prevalent factor in breaches. Organizations that invest in comprehensive training programs can significantly reduce their risk exposure. For instance, a case study involving a major cloud service provider demonstrated that after implementing a tailored training program, they saw a 40% reduction in incidents attributed to human error.
Implementing multi-factor authentication (MFA) is another crucial step, as it adds an additional layer of protection, making unauthorized access to sensitive information increasingly difficult. By adhering to these best practices, entities can cultivate a security-centric culture that permeates their operations and fortifies their defenses against potential threats.
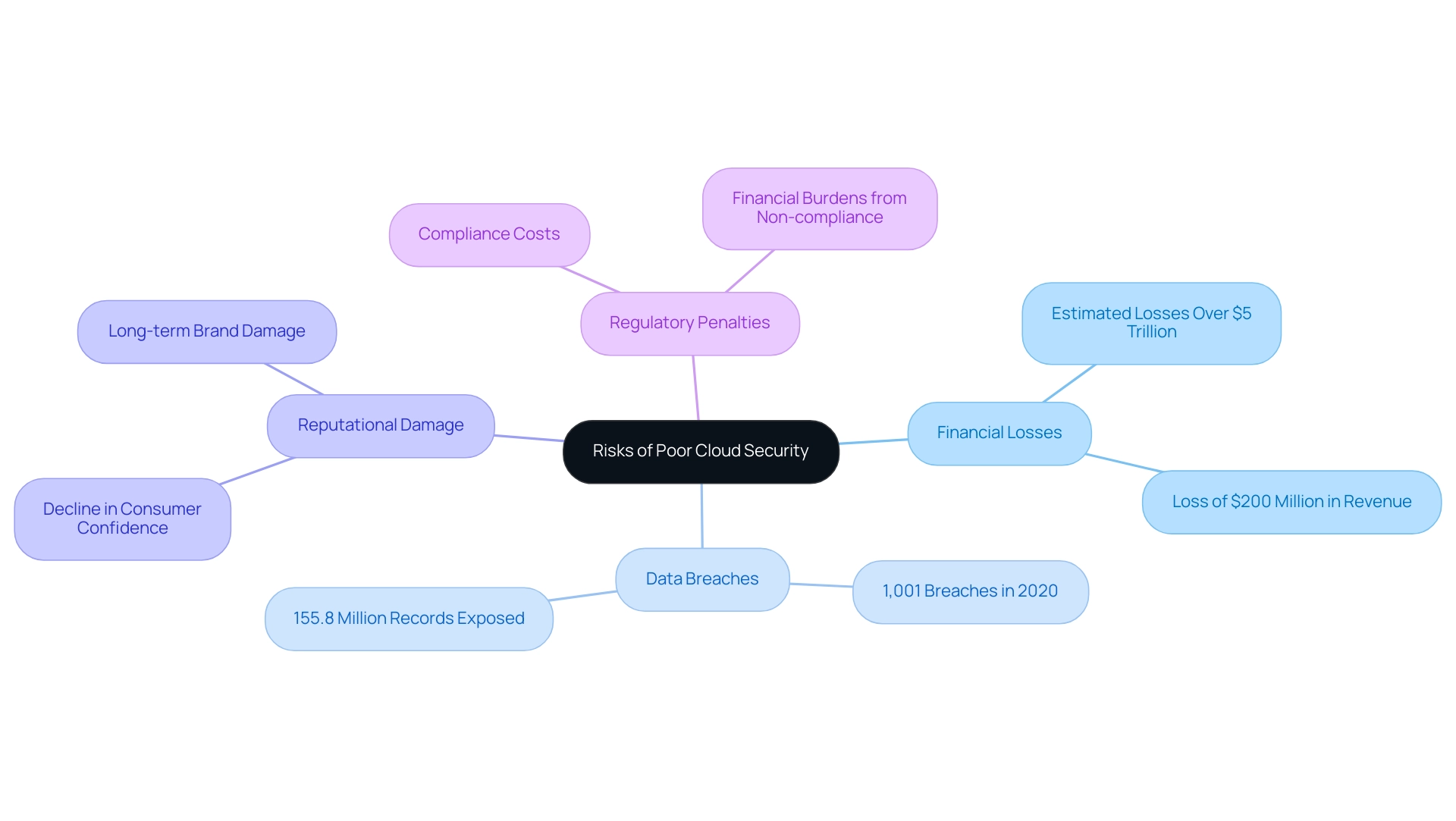
Understanding the Risks of Poor Cloud Security
Ignoring online protection presents considerable dangers for businesses, frequently resulting in information breaches that can reveal confidential details and cause substantial financial setbacks. In 2020 alone, 1,001 data breaches compromised 155.8 million records, highlighting the pervasive threat of unauthorized access. Fast forward to 2024, the financial consequences are anticipated to rise, with estimates indicating that companies could encounter losses surpassing $5 trillion due to inadequate cloud protection measures.
The repercussions of poor security practices extend far beyond immediate financial implications; they can inflict lasting damage on customer trust and brand reputation. For instance, organizations encountering breaches often experience a decline in consumer confidence, which can take years to rebuild. A recent event involving a major online service provider resulted in a breach that exposed client information, leading to a reported loss of $200 million in revenue and a significant decline in stock value.
Additionally, regulatory penalties for non-compliance with data protection laws can impose substantial financial burdens, further complicating recovery efforts. As noted by experts at ne Digital, a leading IT consultation firm specializing in asset value creation for private equity, implementing robust cybersecurity measures is not merely an operational necessity but a strategic imperative. Organizations that prioritize cloud security can protect their assets and maintain their competitive edge, making it crucial to understand and mitigate the risks associated with inadequate cloud security practices.
Conclusion
As organizations continue to embrace cloud computing, the significance of robust cloud security measures cannot be overstated. The alarming rise in cloud security breaches—up by 30% in 2024—underscores the urgent need for businesses to prioritize the protection of sensitive data and operational integrity. Implementing effective cloud security solutions not only mitigates the risk of financial losses, which can average $3.86 million per breach, but also enhances compliance with stringent regulations like GDPR and HIPAA.
The myriad benefits of these measures, including improved disaster recovery capabilities and operational efficiency, highlight their essential role in sustaining business growth in a data-driven environment.
Moreover, exploring a variety of cloud security solutions, such as identity and access management, encryption technologies, and advanced monitoring systems, equips organizations with the tools necessary to combat evolving cyber threats. Best practices, including regular security audits, employee training, and multi-factor authentication, further fortify defenses, fostering a culture of security awareness that permeates all levels of an organization.
In an era where the financial implications of poor cloud security can exceed $5 trillion, understanding the risks associated with inadequate measures is paramount. Organizations must recognize that robust cloud security is not merely an operational requirement but a strategic imperative that protects assets, maintains customer trust, and preserves brand reputation. By prioritizing cloud security, businesses can navigate the complexities of the digital landscape with confidence, ensuring their continued success and resilience in an increasingly interconnected world.




