Introduction
The delivery of malware via email remains one of the most pressing threats in the digital landscape, exploiting the inherent trust users place in their inboxes. Cybercriminals utilize a variety of tactics, from malicious attachments to deceptive links, to infiltrate systems and compromise sensitive data.
In an environment where phishing attacks account for a staggering percentage of cyber incidents, understanding the mechanics behind these threats is crucial for both individuals and organizations. As the sophistication of these attacks evolves, driven by advancements in technology such as artificial intelligence, the need for robust security measures becomes increasingly urgent.
This article delves into the mechanisms of email malware delivery, the risks associated with opening suspicious emails, the motivations behind cybercriminal activities, and essential best practices for protection. By equipping themselves with knowledge and proactive strategies, organizations can fortify their defenses and navigate the complexities of the ever-changing cybersecurity landscape.
How Malware is Delivered via Email: Understanding the Mechanisms
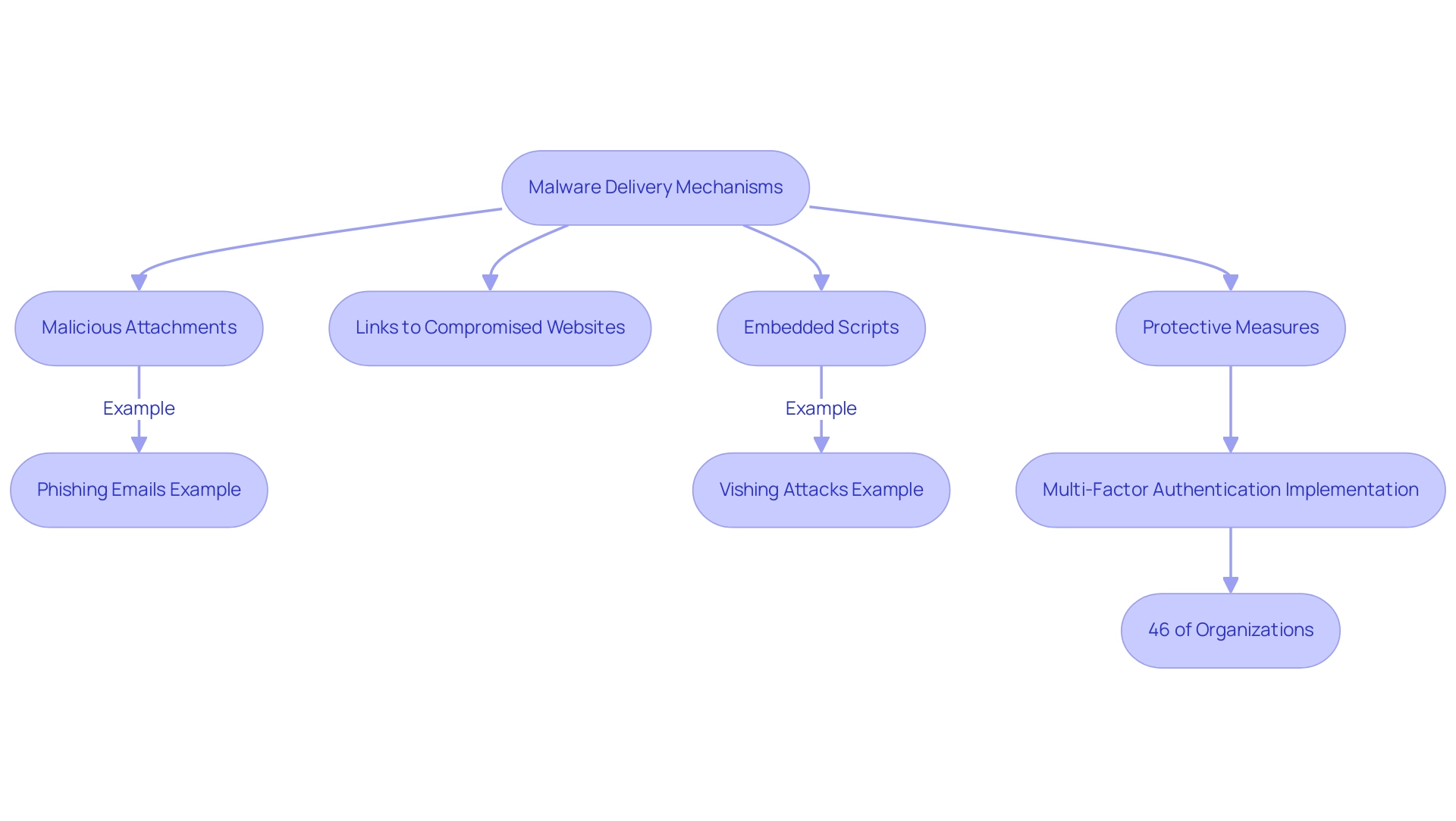
Malware distribution through messages is a prevalent threat, leading many to wonder, can malware be sent by email, and it is characterized by various tactics that leverage user trust. Cybercriminals frequently employ methods such as:
- Malicious attachments
- Links to compromised websites
- Embedded scripts
to infiltrate systems. For instance, a common approach involves crafting emails that mimic legitimate communications from trusted entities, such as banks, raising the question of how can malware be sent by email, encouraging recipients to open attachments laced with harmful code.
This exploitation of trust is not merely anecdotal; it is underpinned by data indicating that authority figures are often used to persuade victims, as seen in vishing attacks where authority was utilized in over 95% of cases. Furthermore, with 70% of cyber crimes targeting financial institutions involving lateral movement, it is crucial for entities to recognize these delivery mechanisms. As Jessica Valasek Estenssoro notes, 'Thanks to emerging technologies, particularly Artificial Intelligence (AI), cybercriminals can now create exponentially more sophisticated attacks, including audio and visual manipulation to produce convincing deep fakes.'
This emphasizes the changing characteristics of dangers entities encounter. Recent statistics indicate that a significant percentage of malware can malware be sent by email attachments, underscoring the urgent need for strong protective measures. In this context, 46% of organizations are implementing multi-factor authentication to secure remote access, illustrating a proactive strategy that is essential in combating these threats effectively.
Additionally, the rapid adoption of IoT devices, as seen in the case study where 93% of executives believe the benefits of IoT outweigh the risks, further emphasizes the need for comprehensive security frameworks to mitigate potential risks.
The Risks of Opening Suspicious Emails: What You Need to Know
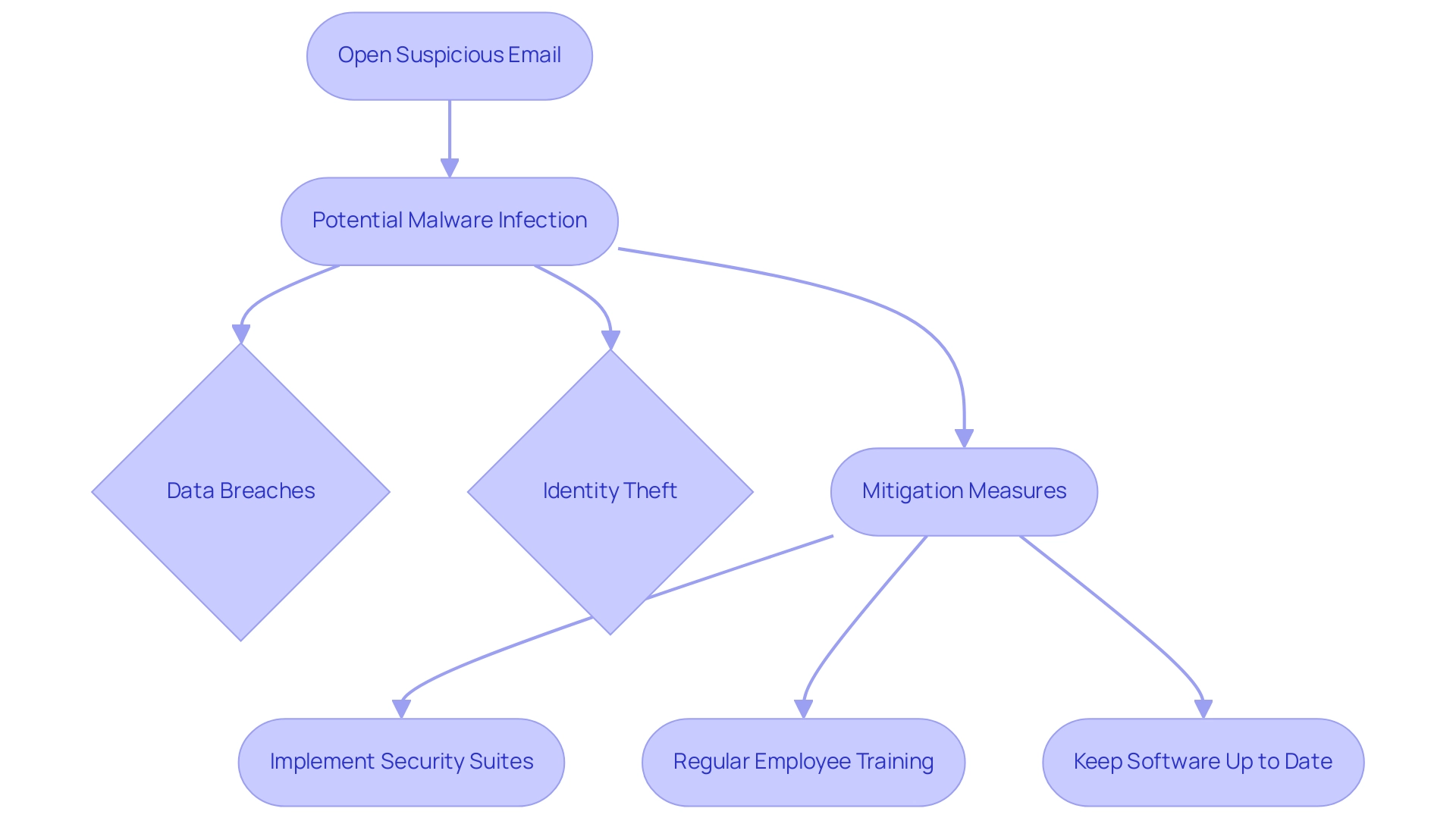
Opening dubious messages poses significant risks and raises the question of whether can malware be sent by email, which can lead to severe consequences, including data breaches and identity theft. Alarmingly, reports indicate that 35% of ransomware attacks raise concerns about whether can malware be sent by email communications, underscoring the vulnerability of this channel. Charles Griffiths, Director of Technology and Innovation, emphasizes that phishing was a primary delivery method for the notorious REvil ransomware, raising the question of how can malware be sent by email, which illustrates the ongoing risk encountered by entities today.
Once a user inadvertently opens an infected attachment or clicks on a malicious link, it raises the question of whether can malware be sent by email, allowing the malware to execute its payload and compromising not only the user's device but also potentially spreading throughout the network. This chain of events can lead to significant financial losses, reputational damage, and regulatory repercussions. In 2024, the environment of communication risks keeps changing, making it essential for both individuals and organizations to comprehend these dangers thoroughly.
Businesses should consider implementing comprehensive security suites, which can provide robust protection against these threats, as highlighted in the recent case study on security solutions. Additionally, adopting cybersecurity best practices—such as regular training for employees on recognizing phishing attempts and ensuring software is up to date—can significantly mitigate the risks associated with digital interactions. By doing so, organizations are better prepared to safeguard their sensitive data against the ever-growing tide of malware attacks.
Motivations Behind Email Malware: Why Cybercriminals Target Your Inbox
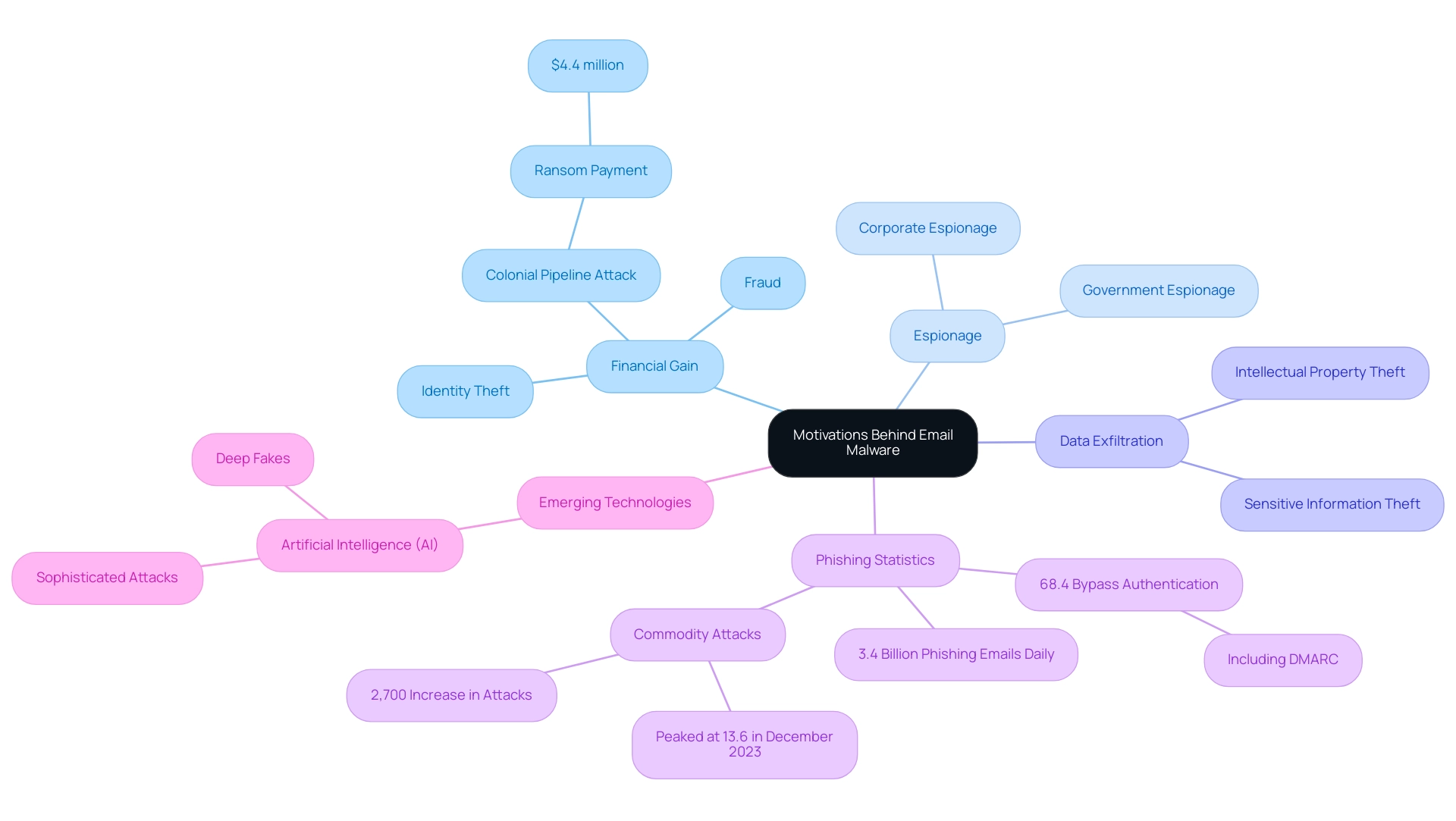
Cybercriminals increasingly exploit digital messaging as a primary vector for malware, leading to concerns about whether malware can be sent by email, as they capitalize on its ubiquity and the inherent trust users place in such communications. Their motivations are multifaceted, encompassing financial gain through identity theft, fraud, and more nefarious activities such as espionage and data exfiltration. With an estimated 3.4 billion phishing messages sent daily, the scale of this danger is staggering.
Notably, a concerning 68.4% of phishing attacks successfully bypass authentication checks, including DMARC protocols, underscoring the severity of the issue. Jessica Valasek Estenssoro notes,
Thanks to emerging technologies, particularly Artificial Intelligence (AI), cybercriminals can now create exponentially more sophisticated attacks, including audio and visual manipulation to produce convincing deep fakes.
This sophistication often manifests in phishing strategies that raise the question of how malware can be sent by email, designed to invoke urgency or fear, prompting users to act without critical scrutiny.
The rise of commodity attacks, which impersonate brands and peaked at 13.6% of all detected phishing messages in December 2023, exemplifies this trend and has resulted in a staggering 2,700% increase in attacks during such campaigns. This trend highlights the increasing sophistication and frequency of phishing attempts. A notable case is the 2021 Colonial Pipeline attack, where the perpetrators gained initial access through a compromised password likely acquired via phishing, leading to a ransom payment of approximately $4.4 million.
This incident not only reveals the financial motivations of cybercriminals but also highlights the essential need for companies to comprehend these dangers. By understanding these motivations and the changing environment of digital risks, entities can enhance their readiness and strengthen their protections against possible intrusions, particularly regarding whether malware can be sent by email.
Protecting Yourself from Email Malware: Best Practices and Tools
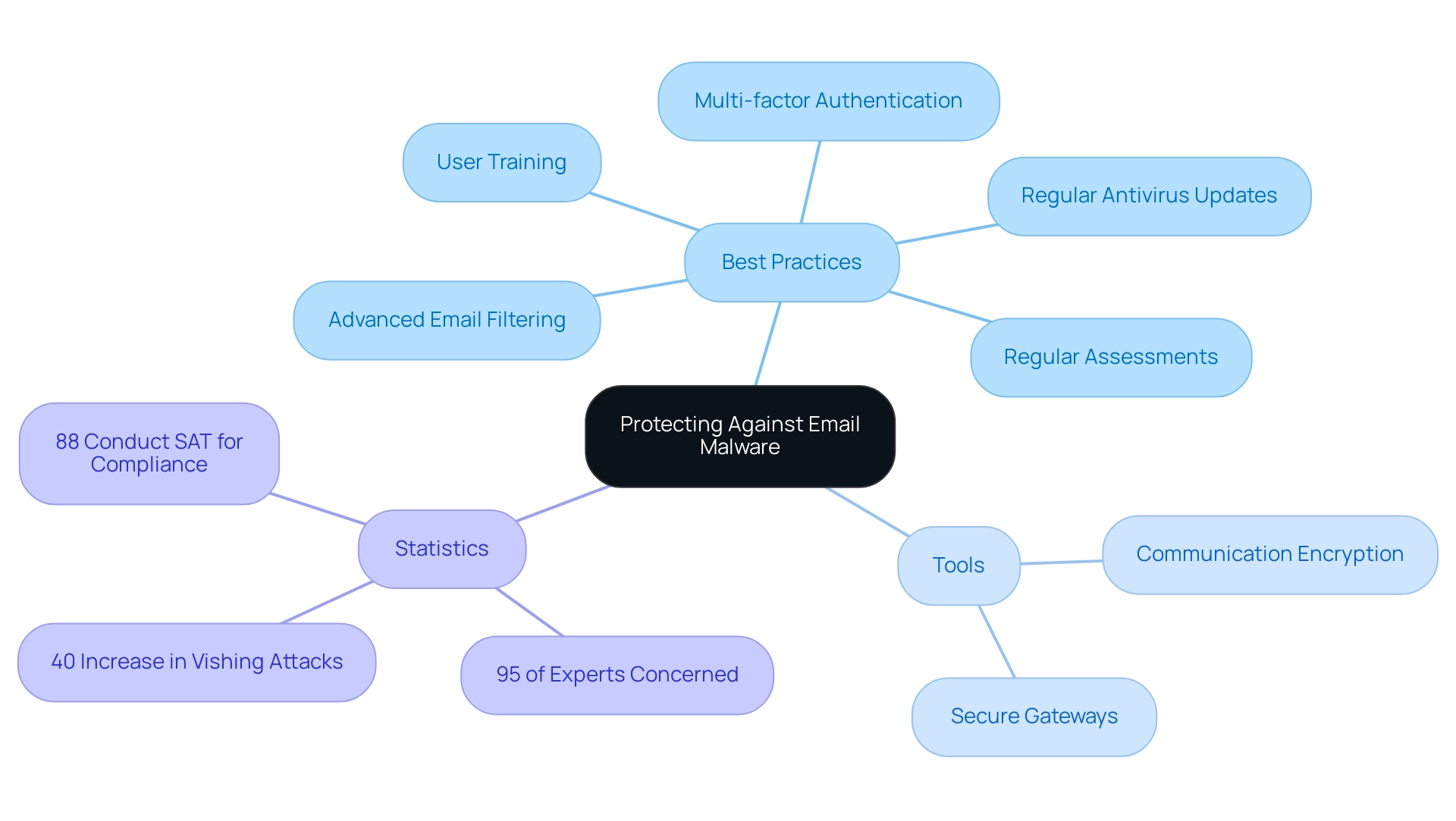
To effectively tackle the increasing danger of malicious software, individuals and organizations must adopt a variety of best practices, as it is important to understand if and how malware can be sent by email. Advanced email filtering solutions are crucial for detecting and blocking malicious content, especially when considering how malware can be sent by email before it reaches users' inboxes. Regular updates of antivirus software also play a vital role, ensuring that systems are equipped to handle the latest threats.
Multi-factor authentication further enhances protection by adding an additional layer of verification. Training users to identify phishing attempts and suspicious messages is essential, especially considering how malware can be sent by email. A proactive and comprehensive cybersecurity strategy should include:
- Regular assessments
- Robust employee training programs
These measures can dramatically lessen the risk of malware infections.
Tools such as communication encryption and secure gateways serve to enhance protection, safeguarding sensitive information from potential breaches. As emphasized in recent reports, with 95% of cybersecurity experts expressing concern regarding electronic communication protection, it is clear that organizations must remain informed and implement these strategies as we approach 2024 to effectively navigate the intricate cybersecurity environment. Furthermore, as Keepnet notes, 'Senior citizens were disproportionately targeted by vishing, with a 40% increase in attacks in the last two years, making them a key demographic for scammers.'
This emphasizes the necessity for focused communication protection measures. Furthermore, case studies such as the deployment of authorized devices for communication access illustrate that establishing clear policies and employing device management solutions can greatly diminish the threat of data breaches and unauthorized entry, ultimately improving protection and compliance. Significantly, 88% of organizations perform SAT mainly for adherence obligations, highlighting the importance of aligning communication protection practices with compliance standards.
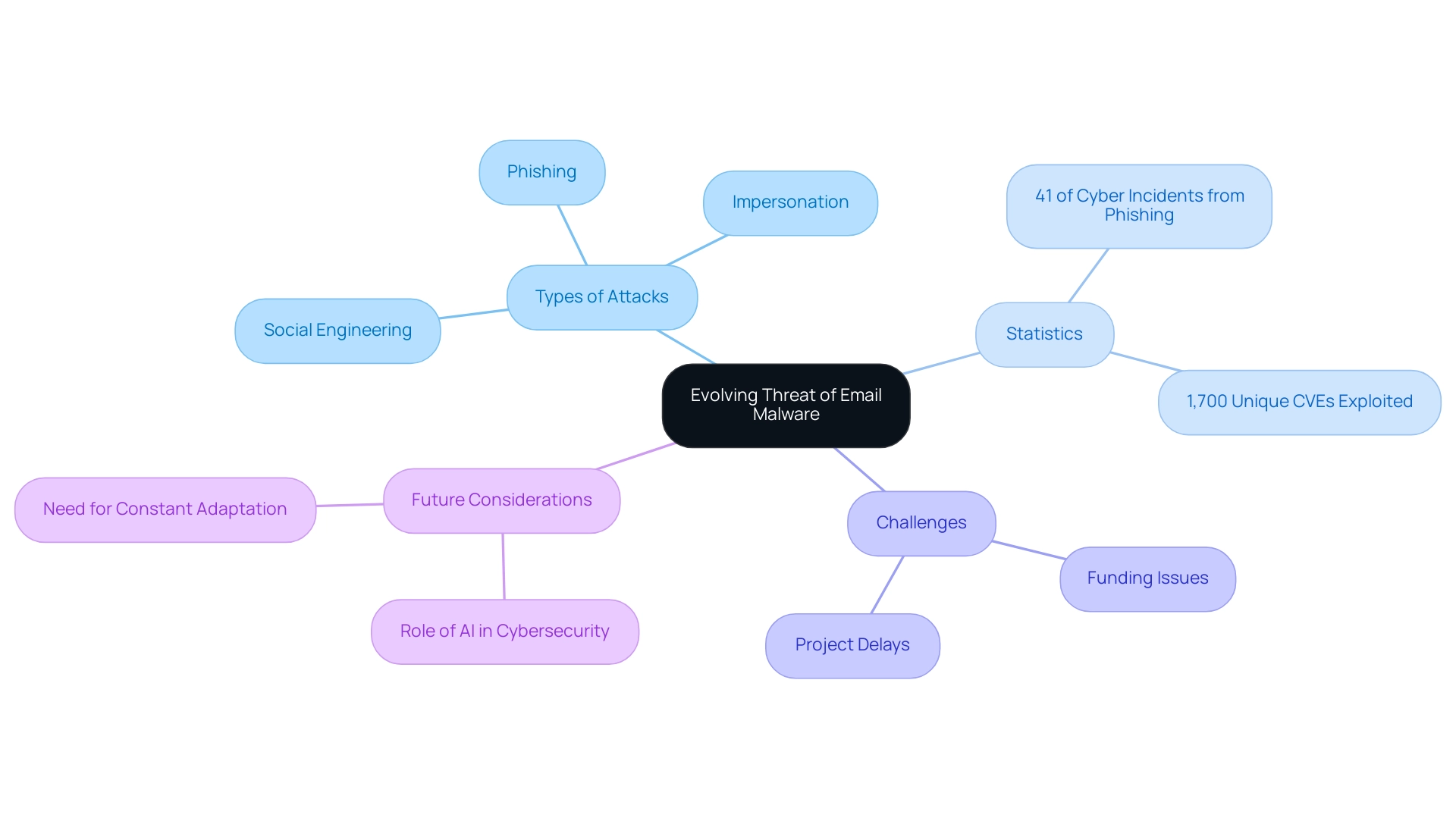
The Evolving Threat of Email Malware: Staying Ahead of Cybercriminals
The environment of email malware challenges is quickly changing, leading to concerns about whether malware can be sent by email as cybercriminals constantly enhance their strategies to bypass established protective measures. Recent data reveals that more than 1,700 unique Common Vulnerabilities and Exposures (CVEs) have been reported as exploited in the wild, showcasing the breadth of vulnerabilities attackers are targeting. One alarming trend is the increased use of sophisticated social engineering techniques, particularly impersonation attacks, where attackers masquerade as trusted entities to extract sensitive information from unsuspecting users.
This tactic is further complicated by the announcement from the FBI regarding a rise in fraud and phishing schemes linked to the US Student Loan Forgiveness procedure, emphasizing the need for vigilance.
In light of these developments, IBM's research highlights that phishing is responsible for 41% of all cyber incidents, making it one of the most prevalent and dangerous forms of attack. Additionally, Kaspersky data shows that device users in Vietnam are statistically the most likely to experience a phishing attack, highlighting the worldwide aspect of these dangers. Furthermore, a significant challenge entities encounter is emphasized by the fact that 31% of Chief Information Security Officers (CISOs) report project delays or cancellations due to insufficient funding, which can impede the execution of essential protective measures.
The integration of artificial intelligence and machine learning into both offensive and defensive strategies is reshaping the risk landscape, creating a dynamic environment that demands constant adaptation. While the consequences of AI in digital communication protection are substantial, specialist views indicate that entities must stay alert against advancing dangers. As we move into 2024, organizations must prioritize staying informed about these evolving threats and regularly updating their security measures.
This proactive approach is essential not only for combating traditional email malware but also for understanding how malware can be sent by email, along with addressing the increasingly sophisticated social engineering tactics employed by cybercriminals.
Conclusion
The threat of email malware delivery remains a critical concern in today's digital environment, as cybercriminals continue to exploit user trust to infiltrate systems. The article has elucidated various tactics employed by these criminals, such as malicious attachments and deceptive links, highlighting the necessity for individuals and organizations to remain vigilant. With alarming statistics indicating that a significant percentage of ransomware attacks originate from email communications, understanding the mechanics of these threats is paramount for safeguarding sensitive data and maintaining operational integrity.
Moreover, the motivations driving cybercriminal activities reveal a complex landscape where financial gain is often pursued through identity theft and fraud. The rise of sophisticated phishing tactics, underscored by the use of artificial intelligence, further complicates efforts to combat these threats. As the article outlines, it is imperative for organizations to adopt comprehensive security strategies that encompass:
- User training
- Advanced email filtering
- Regular updates to security protocols
In conclusion, as email malware continues to evolve, proactive measures and a robust understanding of the associated risks are essential for effective defense. Staying informed about emerging threats and adapting security practices accordingly will empower organizations to navigate the complexities of the cybersecurity landscape and mitigate potential damage from email-based attacks. By prioritizing these strategies, both individuals and organizations can fortify their defenses against the ever-present threat of email malware, ensuring a more secure digital environment.




