Introduction
In an increasingly digital world, where web applications are integral to business operations and customer interactions, the importance of robust security measures cannot be overstated. As cyber threats evolve and proliferate, organizations face the daunting task of safeguarding sensitive data against a backdrop of rising vulnerabilities.
Recent statistics reveal a staggering surge in cyber scams, alongside high-profile data breaches that have affected millions. In this landscape, web application security testing emerges as a critical strategy for identifying and mitigating these risks.
By employing established methodologies and leveraging advanced tools, organizations can not only enhance their security posture but also ensure compliance with regulatory standards while fostering customer trust.
This article delves into the essential components of web application security testing, exploring key methodologies, techniques, and tools that empower organizations to navigate the complexities of today’s cyber threats effectively.
Understanding Web Application Security Testing
Web platform vulnerability assessment acts as an essential method for detecting weaknesses within web interfaces, which could be taken advantage of by cybercriminals. As companies increasingly rely on these applications for essential operations and customer interactions, employing a web application security testing methodology has never been more crucial. The landscape of cyber threats has evolved dramatically, evidenced by a staggering 400 percent increase in cyber scams in March 2020.
This increase highlights the urgent requirement for prompt measures from entities to improve their protection protocols. Furthermore, the T-Mobile data breach of 2023, which affected around 37 million individuals, exemplifies the magnitude of data breaches and their potential to devastate companies. Efficient assessment not only shields sensitive information from unauthorized access but also preserves a firm's reputation and guarantees compliance with regulatory standards.
In a setting where remote work has resulted in breaches affecting 20 percent of companies, as highlighted by Malwarebytes, it is essential for firms to prioritize the web application security testing methodology. This is crucial for maintaining operational integrity and fostering customer trust. Moreover, entities that collaborate with managed service providers (MSSPs) encounter a 21% reduced breach lifecycle, emphasizing another approach to lessen risks linked to web vulnerabilities.
Key Methodologies in Web Application Security Testing
In the domain of web software testing, several key methodologies are prominent, especially the web application security testing methodology, which includes the OWASP Testing Guide. This guide provides a systematic structure for assessing web application safety through a web application security testing methodology, making it an essential resource for entities aiming to identify vulnerabilities comprehensively. Recent data indicates that 42% of organizations believe their cybersecurity budgets are adequately funded, the highest level in eight years, reflecting a growing recognition of the importance of robust security measures.
Complementing the OWASP Testing Guide are methodologies such as NIST SP 800-115 and those from the SANS Institute, each tailored to specific web application security testing methodology scenarios. These methodologies advocate for an in-depth analysis of the system’s architecture, code, and data flow, ensuring that potential vulnerabilities are thoroughly identified and addressed. As Or Katz observed, 'The OWASP Top 10 offers a fundamental comprehension of the most critical threats to web systems.'
Furthermore, the OWASP Mobile Top 10 Methodology exemplifies a data-driven approach, continually updating the list of critical mobile vulnerabilities based on unbiased sources. Key points to consider include:
- Software and data integrity failures, which often arise from weak update processes and unsigned code, making systems susceptible to supply chain attacks and malware injections.
By adhering to the web application security testing methodology, organizations can significantly enhance their protective stance, effectively mitigating risks and fortifying their defenses against evolving threats.
Types of Security Testing Techniques
In the field of web application security testing methodology, various methodologies play crucial roles in detecting and addressing vulnerabilities. Static Application Vulnerability Testing (SAST) emphasizes examining the source code of a system prior to its deployment, effectively revealing possible vulnerabilities early in the Software Development Life Cycle (SDLC). This proactive approach not only facilitates timely remediation but also reduces associated costs.
In contrast, Dynamic Application Security Testing (DAST) assesses the software in a live setting, pinpointing vulnerabilities that may occur during operation. This method is crucial for recognizing flaws that may not be evident in the source code. Interactive Application Security Testing (IAST) presents a hybrid method, utilizing both static and dynamic evaluation techniques to offer deeper insights into application protection.
Furthermore, penetration assessments simulate real-world attacks, exposing vulnerabilities that could be exploited by malicious actors. Based on recent data, only 33% of companies feel assured in handling external risks associated with APIs, highlighting the need for strong testing methods. Each of these techniques serves a distinct purpose, making them integral to the comprehensive web application security testing methodology.
Significantly, the combination of SAST and DAST methodologies improves a company's comprehension of its risk stance. A case study contrasting these methods shows that utilizing both in conjunction offers a more thorough comprehension of a program's safety, enabling companies to enhance the protection of their systems. This is additionally backed by Jacob Schmitt, Senior Technical Content Marketing Manager, who asserts,
Implementing both evaluation strategies in your CI/CD pipelines not only enhances your protective stance but also guarantees that safety is a continuous, essential aspect of your development process.
Together, these methodologies contribute to a robust strategy for web system protection, which includes a comprehensive web application security testing methodology, ensuring that entities are well-prepared to defend against evolving threats.
Essential Tools for Web Application Security Testing
A thorough web application security testing methodology for evaluating web software protection requires the use of industry-standard tools like Burp Suite, OWASP ZAP, and Fortify. These tools are instrumental in performing both Static Application Vulnerability Testing (SAST) and Dynamic Application Vulnerability Testing (DAST), allowing organizations to conduct thorough assessments. Burp Suite, for example, is famous for its strong capabilities in web penetration evaluation, offering features that allow the identification of vulnerabilities such as SQL injection and cross-site scripting.
Industry leaders have praised Burp Suite for its user-friendly interface and effective scanning features, establishing it as a favored option among professionals in the field.
Recent reports suggest that the market for web application assessment tools is anticipated to expand considerably, with over 30,000 high-growth opportunities recognized across various sectors. Additionally, organizations that utilize AI and automation can identify and contain breaches 28 days faster than those that do not, according to IBM. This highlights the critical role of technology in effective breach management.
Moreover, the case study suggests that the typical expense of a data breach is $4.35 million, highlighting the importance of efficient protective measures to reduce such risks. Tools such as OWASP ZAP have received favorable user satisfaction scores, with specialists highlighting its efficiency in automating vulnerability assessment procedures. The incorporation of tools like Nessus and Qualys in protection strategies can improve overall network evaluations, complementing focused web software analysis efforts.
Choosing the appropriate instruments is essential in guaranteeing efficient evaluation and attaining wanted results, as companies are progressively acknowledging that a proactive approach to web application security testing methodology is vital in today's threat environment.
The Web Application Security Testing Process
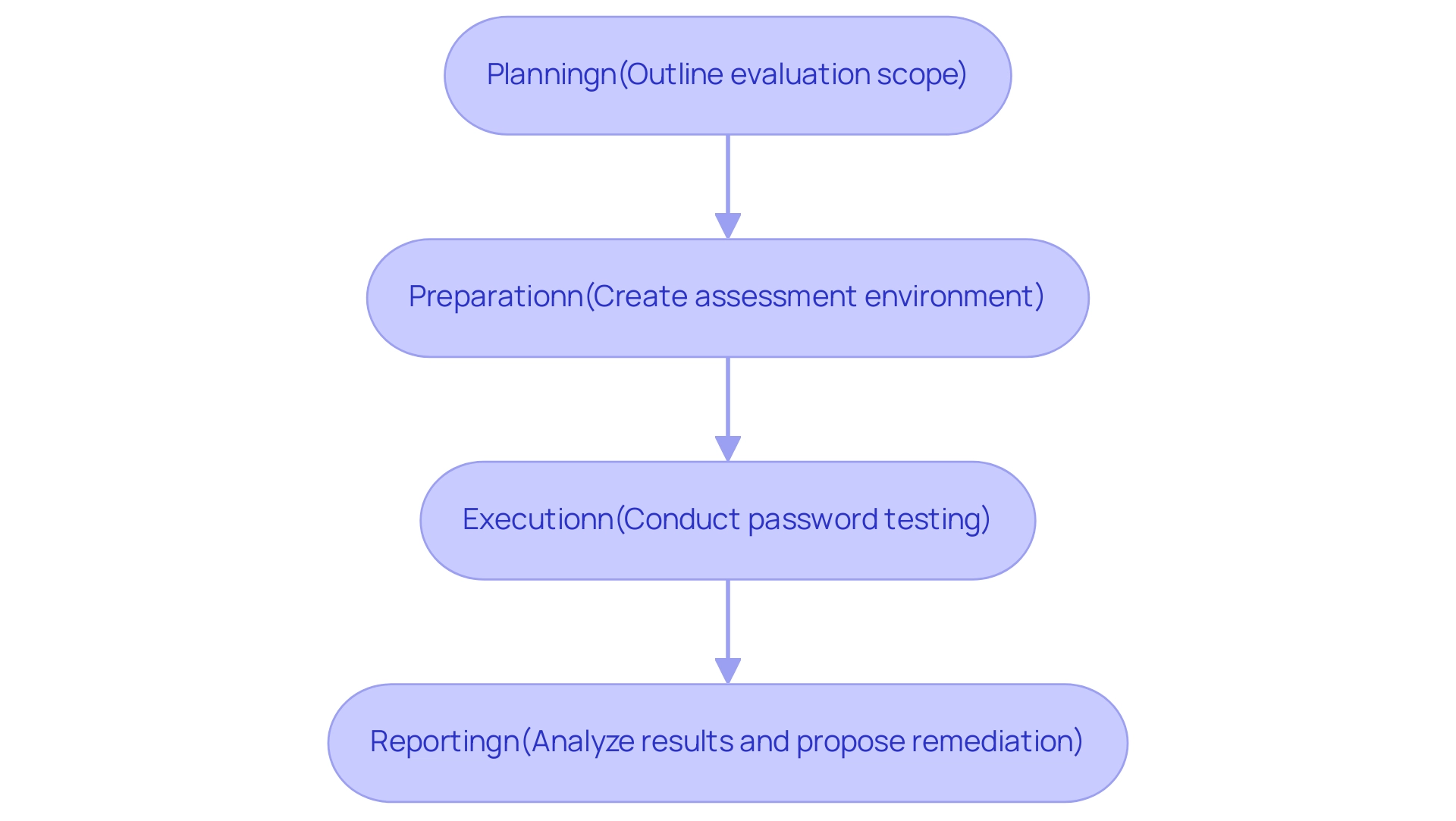
The web application assessment procedure is a thorough framework made up of several essential stages:
- Planning
- Preparation
- Execution
- Reporting
During the planning stage, entities carefully outline the extent of evaluation and recognize vital resources that need safeguarding. This is especially crucial considering that 44% of entities have started to incorporate testing and assessments into their coding processes, indicating an increasing awareness of proactive protective measures.
In fact, the Application Security market is projected to generate approximately $6.97 billion in 2024, with a forecasted annual growth rate of 14.14% from 2024 to 2028, highlighting the increasing financial implications of web application security evaluation.
Preparation includes creating a strong assessment environment and choosing the most appropriate tools and approaches customized to the entity’s particular context. The execution phase then entails rigorous testing using various techniques, including:
- Password spraying, which has been utilized by 49% of pentesters
- Password guessing, employed by 33%
Documenting findings during this phase is crucial for transparency and accountability. Finally, the reporting phase involves thorough analysis of results, where remediation strategies are proposed to address identified vulnerabilities.
Significantly, Positive Technologies highlights that 85% of entities encountered password policy flaws during their assessments, with 60% revealing high-risk vulnerabilities linked to outdated software versions.
This structured approach not only aids organizations in effectively evaluating their web application security using a web application security testing methodology but also facilitates the implementation of necessary improvements for enhanced protection against emerging threats.
Conclusion
In the current digital landscape, the significance of web application security testing cannot be underestimated. As organizations increasingly rely on web applications for critical functions, the necessity to identify and mitigate vulnerabilities has become paramount. The alarming rise in cyber scams and the occurrence of high-profile data breaches serve as a stark reminder of the potential risks that businesses face. By implementing rigorous security testing methodologies, organizations can safeguard sensitive data, protect their reputations, and ensure compliance with regulatory standards.
The article highlighted various key methodologies, including the OWASP Testing Guide and techniques such as:
- Static Application Security Testing (SAST)
- Dynamic Application Security Testing (DAST)
Each of these methodologies plays a vital role in uncovering security flaws at different stages of the software development life cycle. Additionally, the use of advanced tools like Burp Suite and OWASP ZAP is essential for conducting thorough security assessments, enabling organizations to effectively identify and address vulnerabilities.
Furthermore, the structured web application security testing process, encompassing planning, preparation, execution, and reporting, equips organizations with a comprehensive framework to enhance their security posture. By prioritizing web application security testing, organizations not only bolster their defenses against evolving cyber threats but also foster greater trust among customers and stakeholders.
In conclusion, as cyber threats continue to proliferate, organizations must adopt a proactive approach to web application security. Emphasizing the importance of robust security measures and continuous testing will ultimately lead to a more resilient and secure digital environment, safeguarding both organizational assets and customer trust in an ever-evolving threat landscape.




