Introduction
In an age where cyber threats loom larger than ever, organizations must prioritize the safeguarding of their digital assets. Vulnerability Assessment and Penetration Testing (VAPT) emerge as critical components of a robust security strategy, providing essential insights into potential weaknesses within web applications.
By systematically identifying vulnerabilities and simulating real-world attacks, these practices not only illuminate security gaps but also empower organizations to fortify their defenses against malicious actors. As the landscape of cybersecurity evolves, the integration of VAPT into organizational protocols has become not just advisable, but imperative.
With rising compliance requirements and the staggering financial repercussions of breaches, understanding the nuances of VAPT is essential for any entity looking to maintain a resilient security posture.
This article delves into the intricacies of vulnerability assessments and penetration testing, exploring their methodologies, tools, and the vital role they play in contemporary cybersecurity strategies.
Understanding Vulnerability Assessment and Penetration Testing
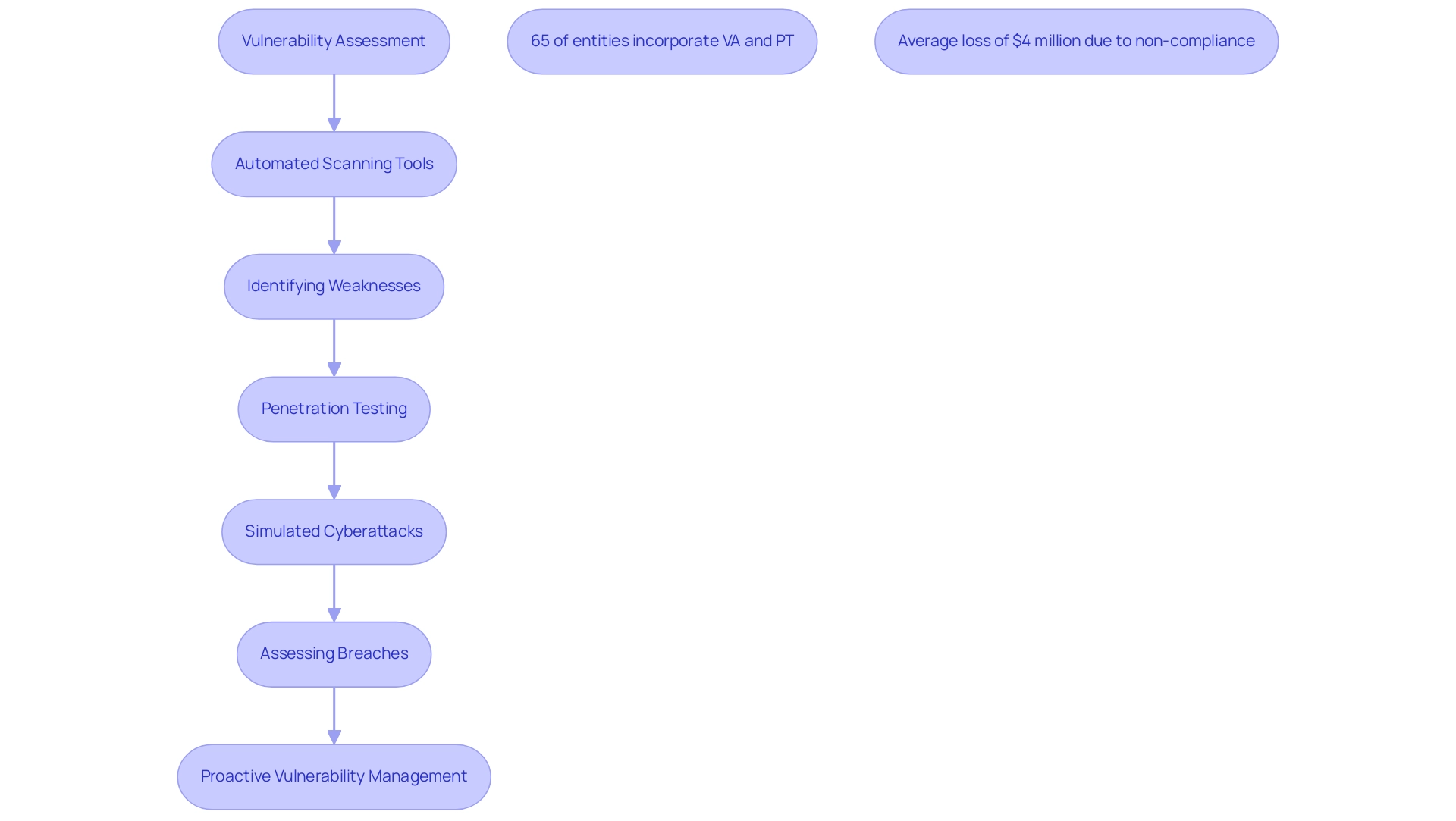
Vulnerability assessment and penetration testing of web application function as crucial foundations of an effective protection strategy. A risk evaluation methodically analyzes a system's weaknesses, identifying potential flaws that harmful individuals could exploit. This process frequently utilizes automated scanning tools created to detect known weaknesses in software and configurations.
Conversely, penetration testing entails performing simulated cyberattacks to evaluate the protection of a system. By taking advantage of recognized weaknesses, entities can assess how far an intruder might possibly breach their defenses, resulting in unauthorized access or system harm. The incorporation of vulnerability assessment and penetration testing of web application not only aids in uncovering critical flaws but also equips entities with a thorough understanding of their protective stance, which is essential for proactive vulnerability management.
Notably, industry data indicates that 65% of entities are now incorporating Vulnerability Assessment and Penetration Testing into their cybersecurity strategies, reflecting a growing recognition of its importance. Furthermore, the financial stakes are significant; entities can incur an average loss of $4 million due to a single non-compliance incident, underscoring the need for rigorous and regular security evaluations. As the cybersecurity environment changes, with over 25,000 weaknesses reported in 2022—a 20% rise from the prior year—the necessity for entities to conduct vulnerability assessment and penetration testing of web application becomes increasingly evident.
In the public sector, penetration assessments are expected to enhance future growth by 2028, emphasizing its crucial role in protecting sensitive information. The rising count of risks reported by the National Vulnerability Database (NVD) further emphasizes the need for organizations to implement proactive protective measures.
Key Differences Between Vulnerability Assessment and Penetration Testing
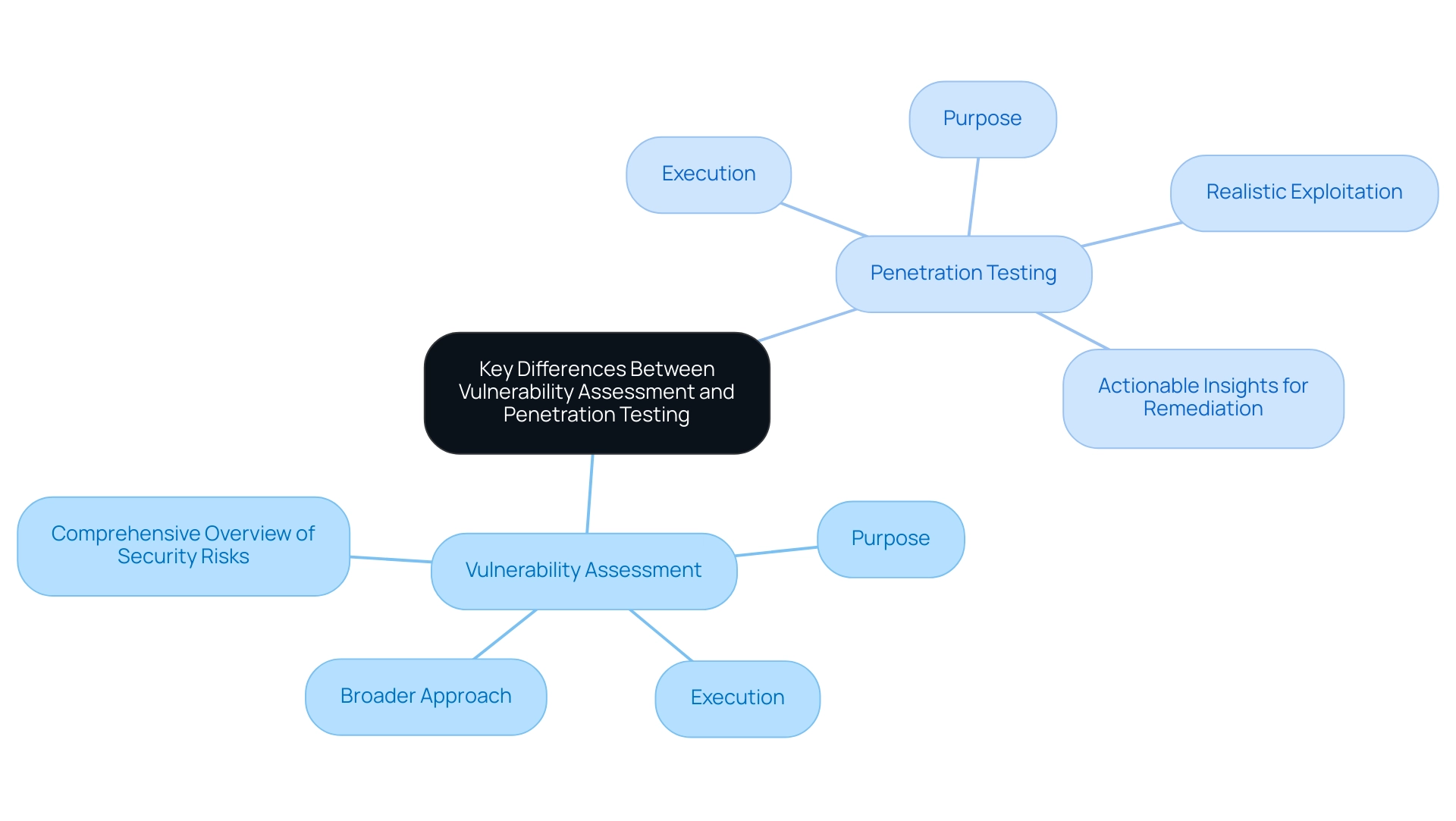
While both risk evaluations and vulnerability assessment and penetration testing of web applications serve the critical function of improving safety, their differences in purpose and execution are significant. An assessment of weaknesses takes a broader approach, aimed at identifying and categorizing issues without necessarily exploiting them. This process results in a comprehensive overview of security risks, allowing organizations to understand potential weaknesses.
In contrast, the vulnerability assessment and penetration testing of web applications is more tactical and concentrated, specifically designed to exploit identified weaknesses in order to assess the actual risk they present. This method provides a realistic vulnerability assessment and penetration testing of web applications by illustrating how weaknesses can be exploited in real-world scenarios, leading to actionable insights for remediation. According to the 2021 Data Breach Investigations Report, which noted that 85% of breaches involved a human element, the importance of vulnerability assessment and penetration testing of web applications in uncovering these exploitation scenarios cannot be overstated.
Furthermore, the longevity of weaknesses is illustrated by the discovery of CVE-1999-0517, which was identified in 2020, highlighting the need for ongoing assessments. Moreover, a case study named "Challenges in Security Risk Prioritization" shows that only 33% of entities prioritize adopting Zero Trust and multifactor authentication, highlighting a significant gap in risk management practices. Consequently, while a vulnerability assessment and penetration testing of web applications provide a comprehensive list of problems, penetration tests yield essential insights that guide strategic enhancements.
The Importance of Vulnerability Assessments and Penetration Testing
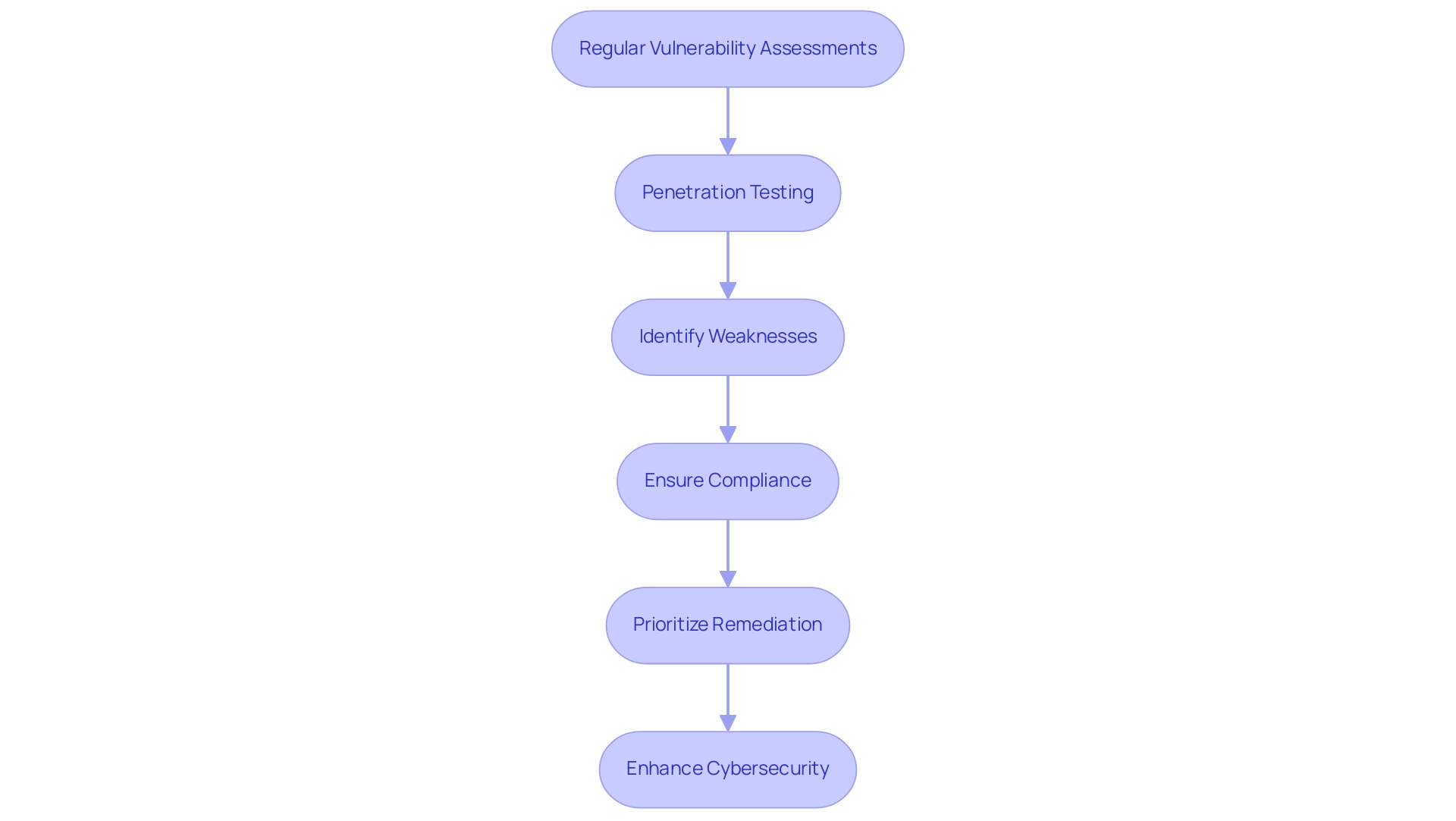
In today's changing cybersecurity environment, performing regular vulnerability assessment and penetration testing of web applications is essential for entities aiming to strengthen their defenses against cyber threats. These practices serve a dual purpose: they not only uncover security weaknesses before adversaries can exploit them but also ensure compliance with industry standards, such as PCI-DSS. This is especially vital as significant vulnerabilities in applications handling payment card data have risen to 8%, emphasizing an urgent need for companies to adhere to compliance requirements to safeguard sensitive information.
By maintaining a consistent assessment schedule, organizations can effectively prioritize their remediation efforts and allocate resources more efficiently. This proactive approach not only enhances overall resilience but also fosters a culture of awareness among employees. Furthermore, a recent study revealed that fifty-two percent of all 10.0 issues reported in the first half of 2022 are likely scored incorrectly.
This statistic highlights the consequences of misprioritization, as depending exclusively on conventional scoring systems may cause teams to miss crucial weaknesses. Furthermore, with the increase of surveillance activities assumed by employees in the U.S. in 2023, companies must stay alert in their cybersecurity practices. Ultimately, the vulnerability assessment and penetration testing of web application plays a crucial role in protecting sensitive data and maintaining customer trust, which reinforces the necessity of regular assessments in a robust cybersecurity strategy.
Methodologies for Conducting Vulnerability Assessments and Penetration Tests
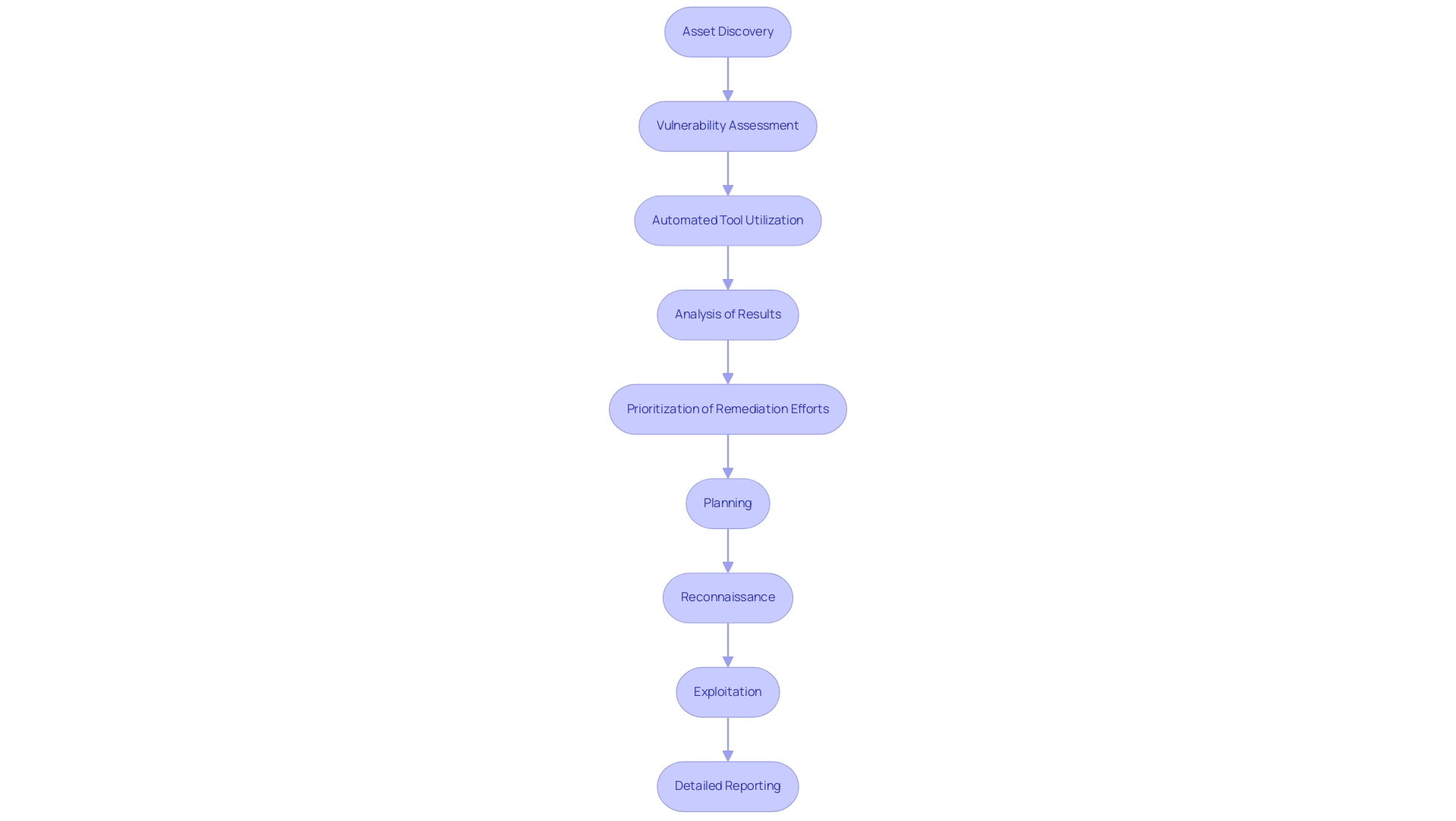
The methodologies for conducting vulnerability assessment and penetration testing of web application encompass several critical steps essential for robust security evaluations. Initiating with asset discovery, organizations identify all relevant systems and applications, which is essential for conducting a vulnerability assessment and penetration testing of web application. This is succeeded by vulnerability assessment and penetration testing of web application, where automated tools are employed to uncover known vulnerabilities, followed by a thorough analysis of the results.
A detailed report is generated that prioritizes remediation efforts based on the findings. In contrast, the process of vulnerability assessment and penetration testing of web application is more dynamic, comprising phases of planning, reconnaissance, exploitation, and detailed reporting. During the vulnerability assessment and penetration testing of web applications, testers simulate real-world attack scenarios, meticulously documenting their findings to provide actionable insights aimed at improving protective measures.
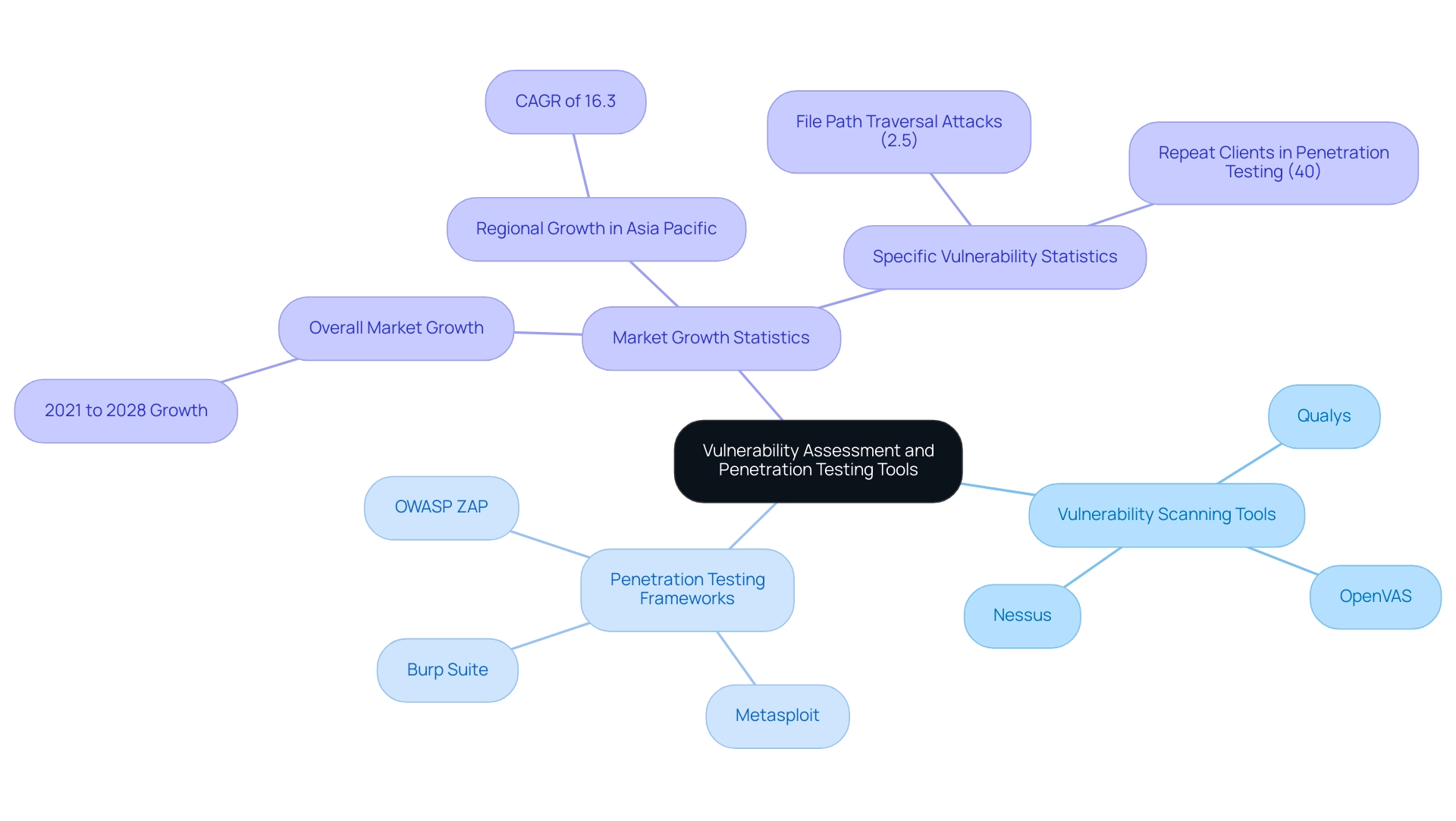
With the global network protection market projected to surge from $27.39 billion in 2021 to $60.38 billion by 2028—growing at a compound annual growth rate (CAGR) of 12.0%—the significance of adopting standardized methodologies becomes increasingly evident. As noted, "Penetration evaluations for the public sector are likely to boost future growth by 2028" (Digital Journal), emphasizing the critical role of these assessments in securing public resources. Furthermore, with file path traversal assaults representing 2.5% of all web application breaches, entities must stay alert and adopt revised vulnerability assessment and penetration testing of web application methods, especially in light of the swift uptake of cloud technologies and infrastructure as code.
The shift toward these methodologies not only guarantees thorough evaluations but also significantly enhances overall safety outcomes through vulnerability assessment and penetration testing of web application. Notably, grey box evaluation, which involves penetration assessments where the tester has partial knowledge of the target system, is a key approach that organizations should consider. Moreover, as emphasized in a case study on cloud and infrastructure as code, the swift embrace of cloud technologies requires new evaluation processes, such as vulnerability assessment and penetration testing of web application, to tackle the unique security characteristics and risks linked to these environments, underscoring the necessity for revised security assessment practices.
Tools and Technologies for Effective Vulnerability Assessment and Penetration Testing
A variety of tools and technologies are essential for performing effective vulnerability assessment and penetration testing of web applications. For security assessments, widely adopted tools such as Nessus and Qualys, alongside OpenVAS, facilitate automated scanning and detailed reporting. These solutions are instrumental in identifying known vulnerabilities across diverse systems, thereby enhancing an organization’s risk management strategies.
Notably, the global network protection market is anticipated to grow from $27.39 billion in 2021 to $60.38 billion by 2028, reflecting a robust compound annual growth rate (CAGR) of 12.0%. The Asia Pacific region is expected to achieve the highest CAGR of 16.3% during this period, highlighting significant investment opportunities in that area. This growth highlights the increasing focus on advanced protective solutions in response to escalating cyber threats.
Regarding penetration assessments, frameworks such as Metasploit, Burp Suite, and OWASP ZAP are preferred by professionals in the field because of their abilities to simulate attacks and identify vulnerabilities. For example, recent statistics suggest that 40% of penetration tests were performed for repeat clients, emphasizing the effectiveness of these tools in promoting continuous enhancements. Furthermore, protection specialists predict that penetration testing for the public sector is likely to catalyze significant growth by 2028, as noted in a recent quote emphasizing its importance.
By leveraging an optimal mix of these tools, organizations can enhance their vulnerability assessment and penetration testing of web application processes, allowing them to conduct thorough assessments that substantially improve their security posture against evolving threats. Additionally, it is important to note that file path traversal attacks accounted for 2.5% of web application attacks, underscoring specific vulnerabilities that these tools can effectively address.
Conclusion
The integration of Vulnerability Assessment and Penetration Testing (VAPT) into an organization’s cybersecurity strategy is no longer a luxury but an essential practice in the face of escalating cyber threats. By systematically identifying vulnerabilities and simulating real-world attacks, VAPT equips organizations with the insights needed to reinforce their defenses and address potential security gaps before they can be exploited by malicious actors.
Understanding the distinct roles of vulnerability assessments and penetration testing is crucial for effective security management. While vulnerability assessments provide a comprehensive overview of potential weaknesses, penetration testing offers a tactical approach that reveals the practical implications of these vulnerabilities in real-world scenarios. This dual strategy not only enhances security resilience but also fosters a proactive culture of risk management within organizations.
Moreover, leveraging advanced tools and methodologies ensures that VAPT processes are thorough and tailored to the evolving landscape of cyber threats. As organizations face increasing compliance requirements and the financial repercussions of breaches, the importance of regular and rigorous VAPT cannot be overstated.
In conclusion, prioritizing VAPT is imperative for safeguarding sensitive information and maintaining customer trust. By committing to ongoing assessments, organizations can stay ahead of emerging threats, ensuring a robust security posture that is adaptable to the complexities of today’s digital environment.




