Introduction
In the realm of cybersecurity, understanding the complexities of adversary behavior is paramount for organizations striving to safeguard their digital assets. The MITRE ATT&CK framework emerges as a critical tool in this endeavor, offering a structured approach to deciphering the tactics, techniques, and procedures employed by cyber threats.
As organizations confront an alarming rise in cyber incidents—from the surge of phishing attacks to the exploitation of social media platforms—leveraging this framework becomes essential for enhancing defenses and fostering a proactive security culture.
With its comprehensive insights into adversarial methodologies, the MITRE ATT&CK framework not only aids in anticipating potential threats but also equips security teams with the knowledge necessary to devise effective incident response strategies.
As the landscape of cyber threats continues to evolve, the importance of frameworks like MITRE ATT&CK cannot be overstated, serving as a beacon for organizations aiming to navigate the intricacies of modern cybersecurity challenges.
Understanding the MITRE ATT&CK Framework: Definition and Purpose
The mitre att&ck model serves as a vital knowledge repository that outlines the tactics, techniques, and procedures (TTPs) used by cyber adversaries. It is essential for organizations seeking to improve their cybersecurity stance through a systematic approach to intelligence and incident response. By classifying opponent actions, the system enables organizations to foresee possible risks and strengthen their protections against cyberattacks.
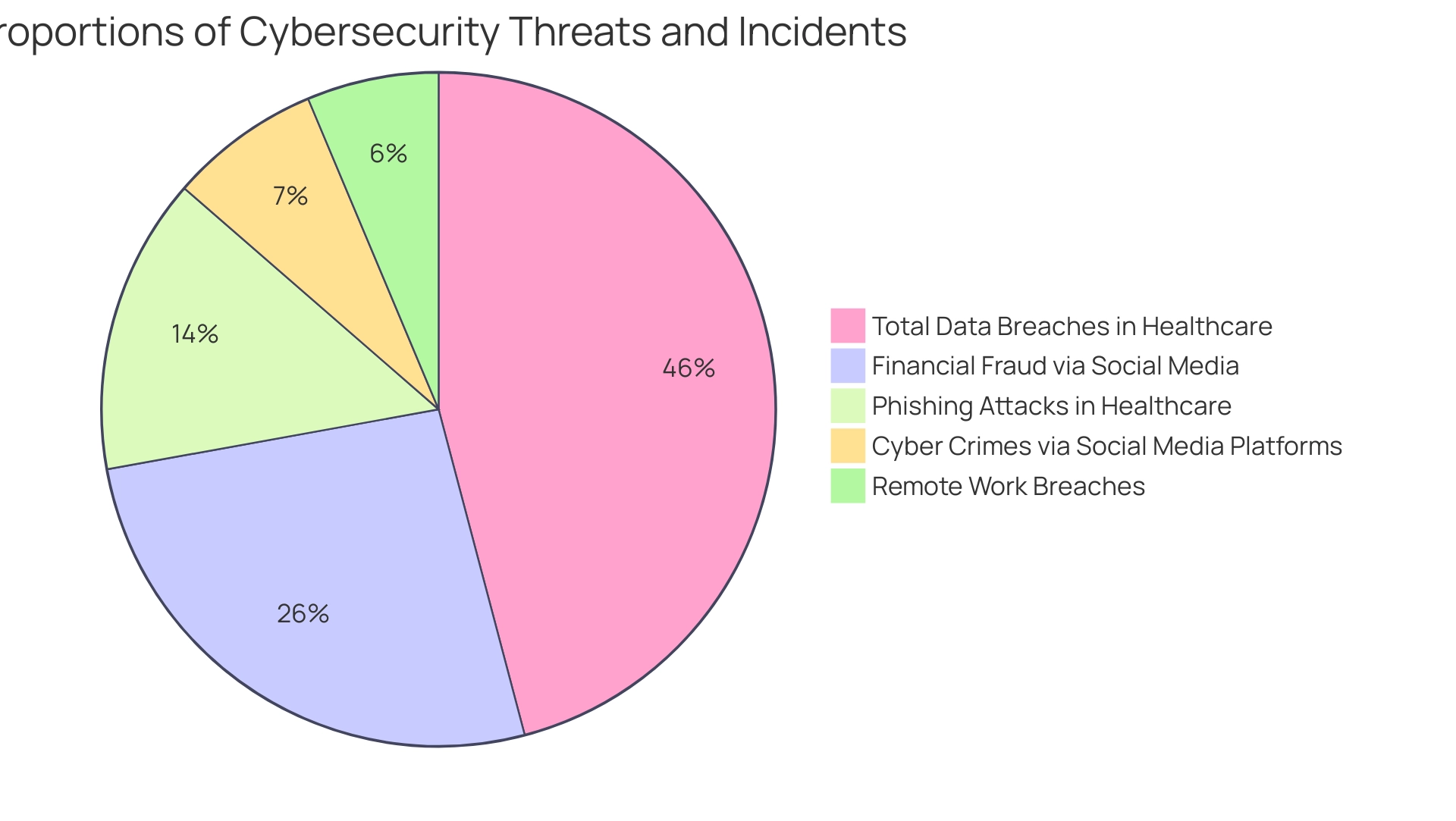
For instance, during the pandemic, remote workers were linked to security breaches in 20% of organizations, underscoring the necessity for such proactive measures. Furthermore, with a remarkable 83% rise in financial fraud through social media in Pakistan from 2018 to 2021, where 23% of cyber crimes utilized platforms like Facebook, the need for effective intelligence has never been more apparent. The exploitation of social media platforms emphasizes the need for organizations to utilize the mitre att&ck model to comprehend and address such threats effectively.
Additionally, the healthcare sector exemplifies the pressing need for strong digital security measures, as it reported 145 data breaches in Q1 2023, with 45% of these incidents involving phishing attacks. This case highlights the importance of the mitre att&ck model in addressing specific adversary methodologies. As investment in information security reached $176 billion in 2023, with expectations to exceed $200 billion in 2024, the significance of the MITRE ATT&CK model continues to grow for effective cybersecurity strategies.
Key Components of the MITRE ATT&CK Model: Tactics, Techniques, and Sub-Techniques
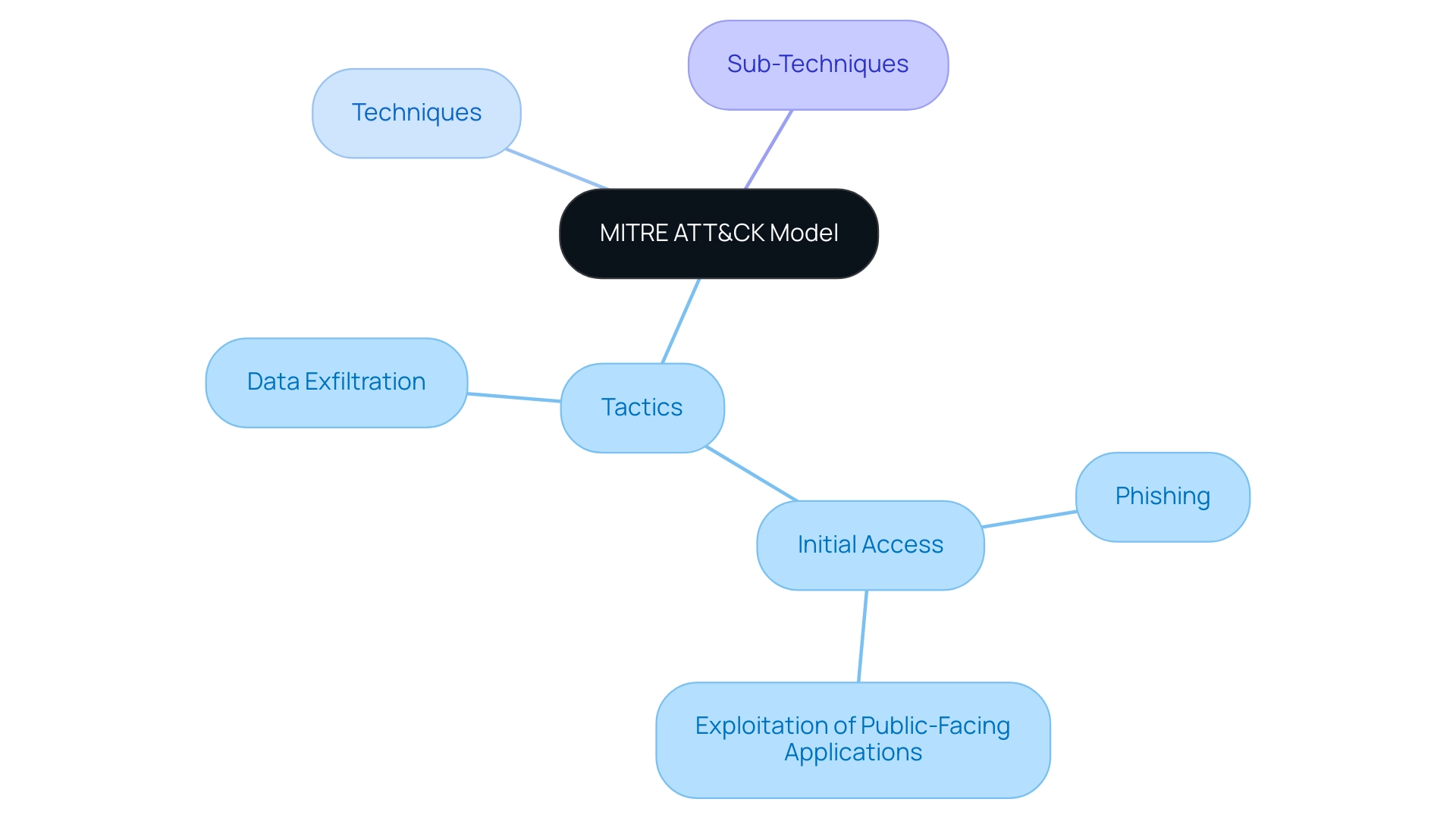
The MITER ATT&CK structure is meticulously organized into three fundamental components: tactics, techniques, and sub-techniques. Tactics denote the overarching goals adversaries seek to accomplish, including objectives such as initial access and data exfiltration. Within this framework, techniques serve as the specific methodologies employed to realize these high-level goals.
For example, under the 'Initial Access' tactic, techniques may comprise 'Phishing' and 'Exploitation of Public-Facing Applications.' Sub-techniques further refine these categories, presenting a nuanced perspective on the variations within each technique, which is vital for understanding the complexity of modern cyber risks. This hierarchical structure allows security teams to establish focused protections and develop incident response plans customized to the particular challenges they face.
As organizations face an alarming growth in cyber incidents—evidenced by enterprises experiencing an average of 130 security breaches per year and a 22.7% increase in cybersecurity costs—utilizing the MITRE ATT&CK model becomes essential for enhancing their security posture and effectively mitigating risks. Joe Devanny, a lecturer at King’s College London, emphasizes the urgent nature of these issues, stating, 'It’s not surprising that it happened, it’s not surprising it was being reported as a Russian group, and it’s not surprising it’s healthcare related.' Moreover, with 70% of cyber crimes aimed at surveyed financial institutions involving lateral movement, the MITRE ATT&CK model provides an essential resource for comprehending and addressing these particular dangers.
Practical Applications of the MITRE ATT&CK Framework in Cybersecurity
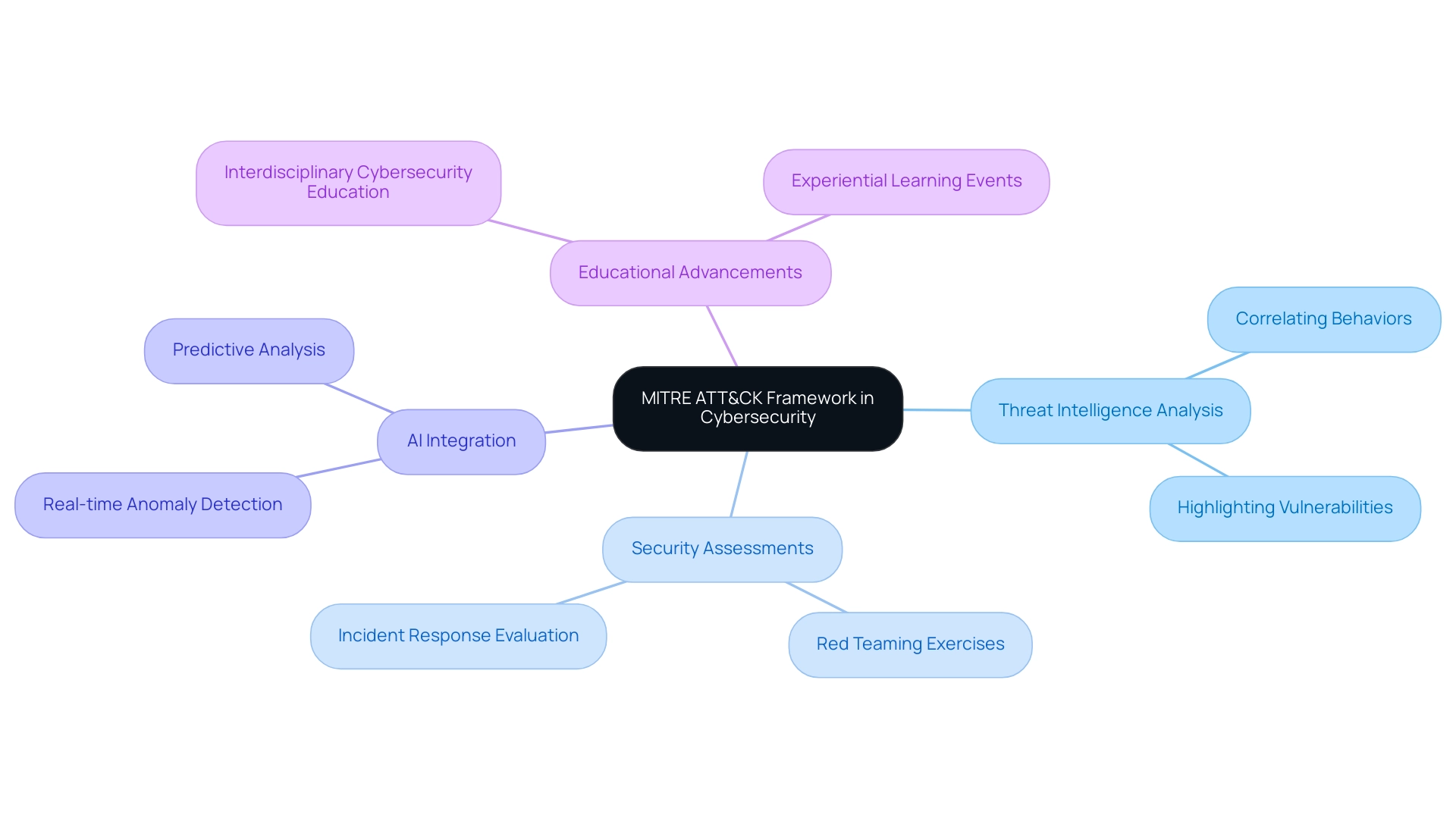
Organizations are increasingly utilizing the mitre att&ck model to enhance their cybersecurity strategies through various practical applications. Primarily, the mitre att&ck model serves as a foundational tool for threat intelligence analysis, allowing security teams to correlate observed adversary behaviors with established tactics and techniques. This correlation not only highlights vulnerabilities within existing defenses but also informs the creation of proactive security measures.
For instance, recent reports indicate that a surge in cyber attacks, including a coronavirus scam that cost victims over £800,000 in just one month, underscores the need for robust defenses. Furthermore, the mitre att&ck model is integral to security assessments and red teaming exercises, as it is employed to simulate real-world attack scenarios, thereby allowing organizations to rigorously evaluate their incident response capabilities. D.A., a specialist in validation and supervision, asserts,
Our ultimate goal is to assist both organizations and individuals in comprehending adversary thinking and behavioral patterns while cultivating a deeper and substantial cyber-security culture.
Additionally, the integration of AI and ML technologies is proposed as a transformative approach to enhance digital security, enabling real-time anomaly detection and predictive analysis. By integrating the mitre att&ck model into their security practices, organizations not only enhance their resilience against evolving cyber threats but also foster a culture of continuous improvement in security readiness. Furthermore, advancing interdisciplinary security education is crucial for preparing teams with the expertise to efficiently apply these systems.
The recent paper by Georgiadou et al. further highlights the significance of evaluating MITER ATT&CK risk within a security culture context, offering timely insights into its practical uses.
MITRE ATT&CK in Context: Comparing with Other Cybersecurity Frameworks
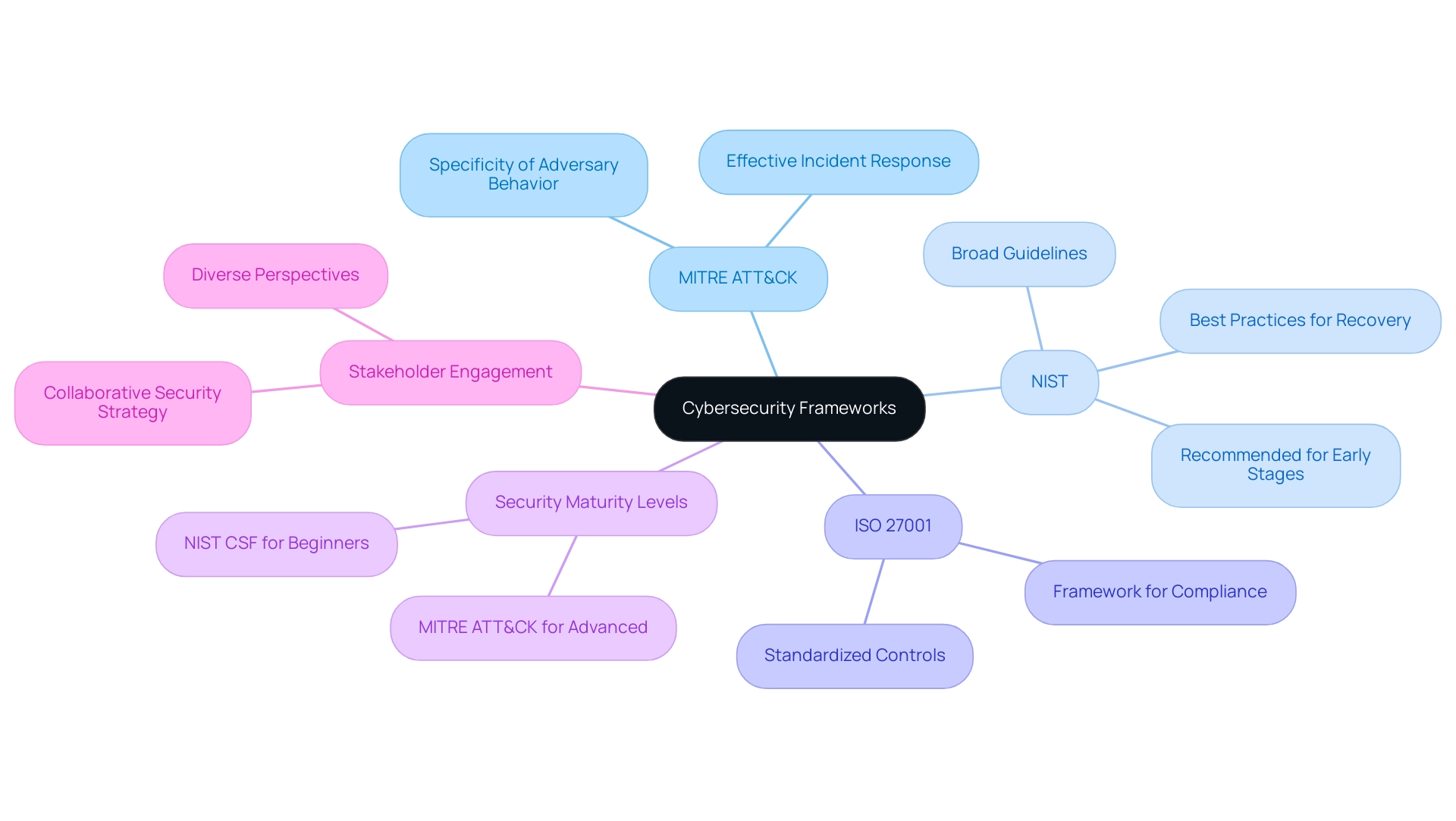
The mitre att&ck model sets itself apart from other security approaches, like the NIST model (currently at version 1.1) and ISO 27001, through its remarkable specificity in outlining adversary behavior. While both NIST and ISO structures offer broad guidelines for handling security risks, the MITRE ATT&CK model explores the complex tactics and techniques used by adversaries. This level of detail enables organizations to construct more accurate threat models and formulate effective incident response strategies.
Moreover, the mitre att&ck model serves as a beneficial addition to current systems, providing a practical viewpoint that improves the understanding and implementation of broader security principles. Recent discussions emphasize that the choice between adopting MITER ATT&CK or NIST first hinges on an organization’s security maturity level, with NIST CSF being more suited for those in the early stages of their security journey. In contrast, organizations with more mature capabilities often find greater utility in integrating the mitre att&ck model into their security operations.
Engaging stakeholders from various departments enriches the understanding of unique security challenges and fosters buy-in for a collaborative security strategy. As mentioned by Gurinder Pal Singh, 'HIPAA is such a powerful act that it is referred to as total silence all the time,' emphasizing the importance of adherence in the context of digital security.
The Evolution of the MITRE ATT&CK Framework: History and Development
Introduced in 2013, the mitre att&ck model was created to standardize the understanding of adversary behaviors within the cybersecurity landscape. This initiative arose from the urgent need for a universal language that organizations could adopt to effectively discuss and address cyber risks. Since its beginning, the structure has experienced significant development, adjusting to the growing complexity of cyber challenges by incorporating new tactics and techniques.
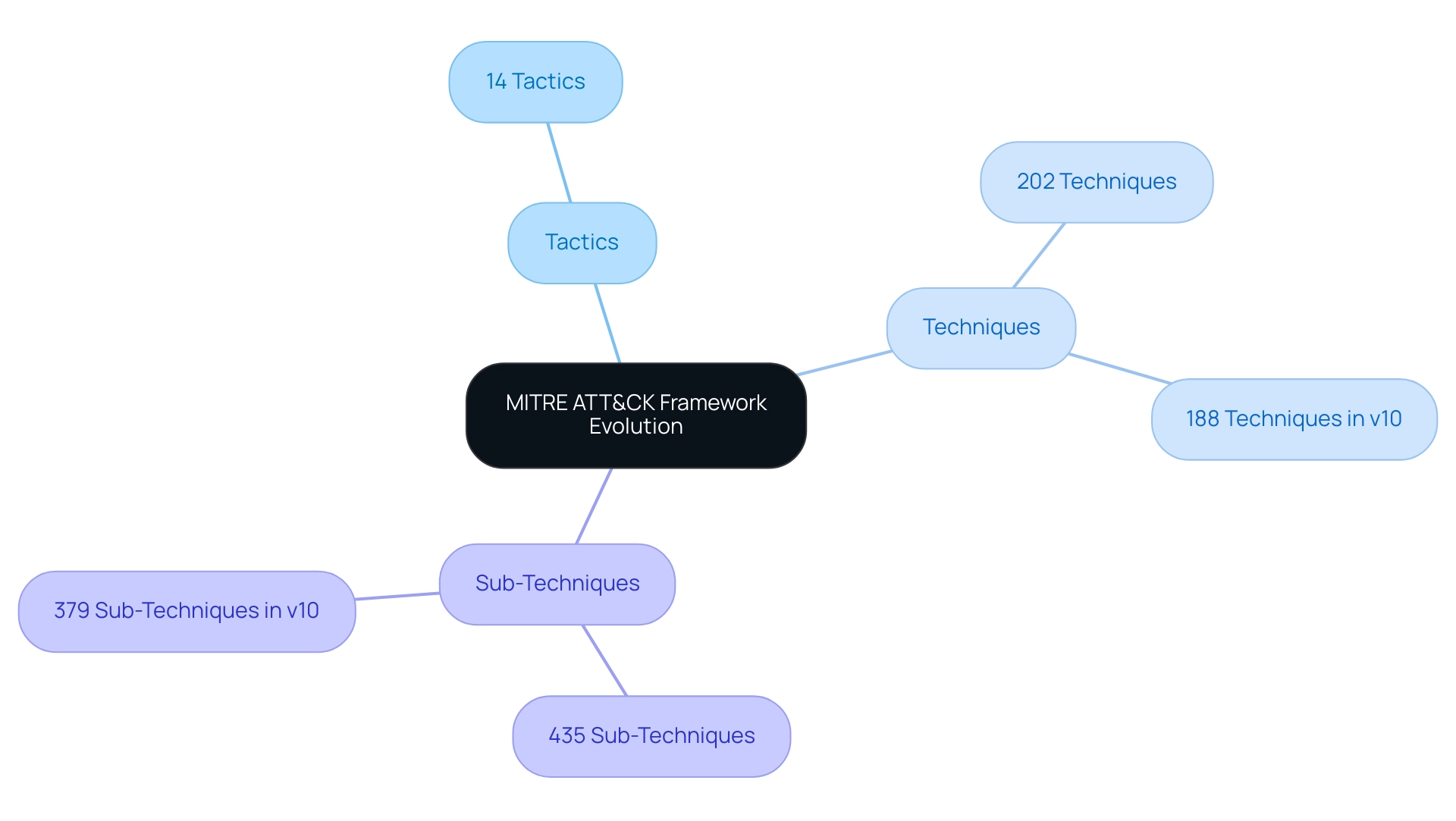
Significantly, the structure now includes:
- 202 techniques
- 435 sub-techniques
demonstrating its all-encompassing method to modeling risks. Regular updates—usually issued twice a year—are guided by real-world risk intelligence, ensuring that the ATT&CK structure stays relevant amidst the constantly changing danger environment. For instance, the launch of ATT&CK v10 in October 2021 introduced Data Sources and Data components, expanding the matrix to include:
- 14 tactics
- 188 techniques
- 379 sub-techniques
As MITER states, 'The three components of the MITRE ATT&CK model are tactics, techniques, and procedures (i.e., techniques in practice).' This ongoing development highlights the necessity for organizations to adopt adaptive cybersecurity strategies that are in sync with the latest threat vectors, ultimately reinforcing their security posture in an ever-evolving digital environment.
Conclusion
The MITRE ATT&CK framework is an invaluable resource for organizations striving to enhance their cybersecurity defenses against increasingly sophisticated cyber threats. By systematically categorizing adversary tactics, techniques, and procedures, it empowers organizations to anticipate potential risks and implement targeted incident response strategies. The framework's relevance is underscored by alarming statistics, such as the surge in financial fraud linked to social media and the significant number of data breaches reported in critical sectors like healthcare.
Through its structured approach, MITRE ATT&CK not only aids in threat intelligence analysis but also serves as a foundational tool for security assessments and red teaming exercises. Organizations utilizing this framework can better understand adversary behavior, which is essential for developing robust security measures. Moreover, as cybersecurity incidents continue to rise, the integration of MITRE ATT&CK with other frameworks, such as NIST and ISO, further enhances its practical applications, allowing for a comprehensive approach to risk management.
In light of the continuous evolution of cyber threats, embracing the MITRE ATT&CK framework is crucial for organizations aiming to maintain a proactive security posture. By staying informed about the latest developments and incorporating the framework into their cybersecurity strategies, organizations can foster a culture of resilience and adaptability. Ultimately, the MITRE ATT&CK framework serves as a guiding light, equipping organizations with the insights necessary to navigate the complexities of the modern cybersecurity landscape effectively.




