Introduction
In an age where digital threats loom larger than ever, the role of security consulting has emerged as a cornerstone of organizational resilience. This multifaceted discipline not only encompasses the assessment and enhancement of security measures but also adapts to the rapid technological advancements shaping our world. As businesses grapple with the complexities of safeguarding their assets, information, and personnel, the demand for expert guidance in this field has surged.
From conducting thorough risk assessments to implementing cutting-edge cybersecurity frameworks, security consultants are pivotal in fortifying defenses against an array of threats. This article delves into the essential components of security consulting, exploring the evolving landscape, the critical responsibilities of consultants, and the innovative strategies that are redefining how organizations approach security in an increasingly interconnected environment.
Defining Security Consulting: An Overview
Protection advisory represents an essential area within the wider field of information protection, focusing on the evaluation, creation, and execution of strong protective measures aimed at safeguarding a company's assets, information, and personnel. This field encompasses a diverse array of activities, including:
- Comprehensive risk assessments
- Thorough audits
- Compliance evaluations
- The formulation of tailored protection policies and procedures
A main goal of risk assessment is to effectively reduce threats while improving a company's overall safety stance.
By doing so, entities are better equipped to respond to potential threats, thereby safeguarding their most vital resources. As evidenced by the latest market reports, the demand for these services, or what is security consulting, is rising significantly, particularly in North America, which remains the largest market for Information Security Consulting Services. This trend reflects a growing recognition of the importance of proactive risk management in today’s increasingly complex digital landscape.
For example, the recent collaboration between Atos and Daiwabo Information System in Japan illustrates how consulting can enable entities to safeguard their data during digital transformation. Furthermore, based on the Bureau of Labor Statistics, this industry employs 18,200 guards, which is 4.42% of the industry's total employment, emphasizing the scale and significance of protection in the current market.
Roles and Responsibilities of Security Consultants
To understand what is security consulting, it's important to recognize the pivotal role security consultants play in protecting entities through a diverse array of responsibilities. The task primarily involves conducting comprehensive evaluations of an organization's safety requirements and developing tailored strategies that align with industry regulations, essentially answering what is security consulting. Essential to their role is the capability to navigate different operating systems and protective protocols, a skill set that improves their effectiveness in incident response planning and vulnerability assessments.
The typical employer expenses for engaging protective advisors can be substantial, averaging $26.39 per hour for wages and $8.88 for benefits, which highlights the financial consequences of investing in protective expertise. Moreover, vital abilities required for safety advisors encompass:
- Coding
- Programming
- Network setup
- Protection protocols
- Cloud infrastructure knowledge
These skills are critical for efficient risk management. Beyond these primary duties, professionals also handle additional responsibilities such as:
- Client meetings
- Training junior staff
- Ensuring adherence to industry standards
For instance, the case study titled 'Nonstandard Duties for Security Consultants' illustrates how these professionals may delegate tasks and meet with clients to ensure comprehensive protection solutions are in place. This complex position highlights the importance of effective communication, as advisors must inform staff on best practices for safety and foster a culture of awareness throughout the entity. As aptly stated by the American Statistical Association,
It is always easier to steer a ship than to raise it off the ocean floor,
highlighting the proactive nature required in risk management.
Ultimately, what is security consulting involves a combination of technical expertise and interpersonal skills that are crucial for consultants as they strive to maintain robust cybersecurity practices within organizations.
Comparing Approaches: Traditional vs. Modern Security Consulting
Conventional protection advisory services have historically focused on physical safety measures, including access control systems and surveillance, primarily aimed at safeguarding tangible assets. However, the landscape of consulting in risk management has undergone a significant transformation. Contemporary methods now combine advanced technologies such as cybersecurity structures, cloud protection, and comprehensive data safeguarding strategies.
The necessity for this evolution is underscored by alarming statistics; for instance, external attacks on cloud accounts surged by 630% in early 2020. Moreover, an astonishing 20% of entities still lack efficient measures to safeguard remote users accessing the internet, emphasizing a crucial weakness in protective practices. While traditional methods provide a foundational layer of protection, they are often insufficient in addressing the complexities of today's threat environment.
Modern methodologies capitalize on data analytics and threat intelligence, enabling entities to proactively anticipate and mitigate risks. A notable 46% of organizations now employ multi-factor authentication to secure remote access, illustrating the shift towards more advanced protective measures. Additionally, a case study titled 'Strategies for Reducing Cyber Attack Risks' emphasizes the importance of implementing strong passphrases, multi-factor authentication, and regular software updates to significantly enhance protection.
With phishing attacks estimated to be involved in 90% of breaches in 2019, it is clear that integrating both physical and digital protection concerns is not just beneficial but essential in today’s interconnected world.
The Role of Cybersecurity in Security Consulting
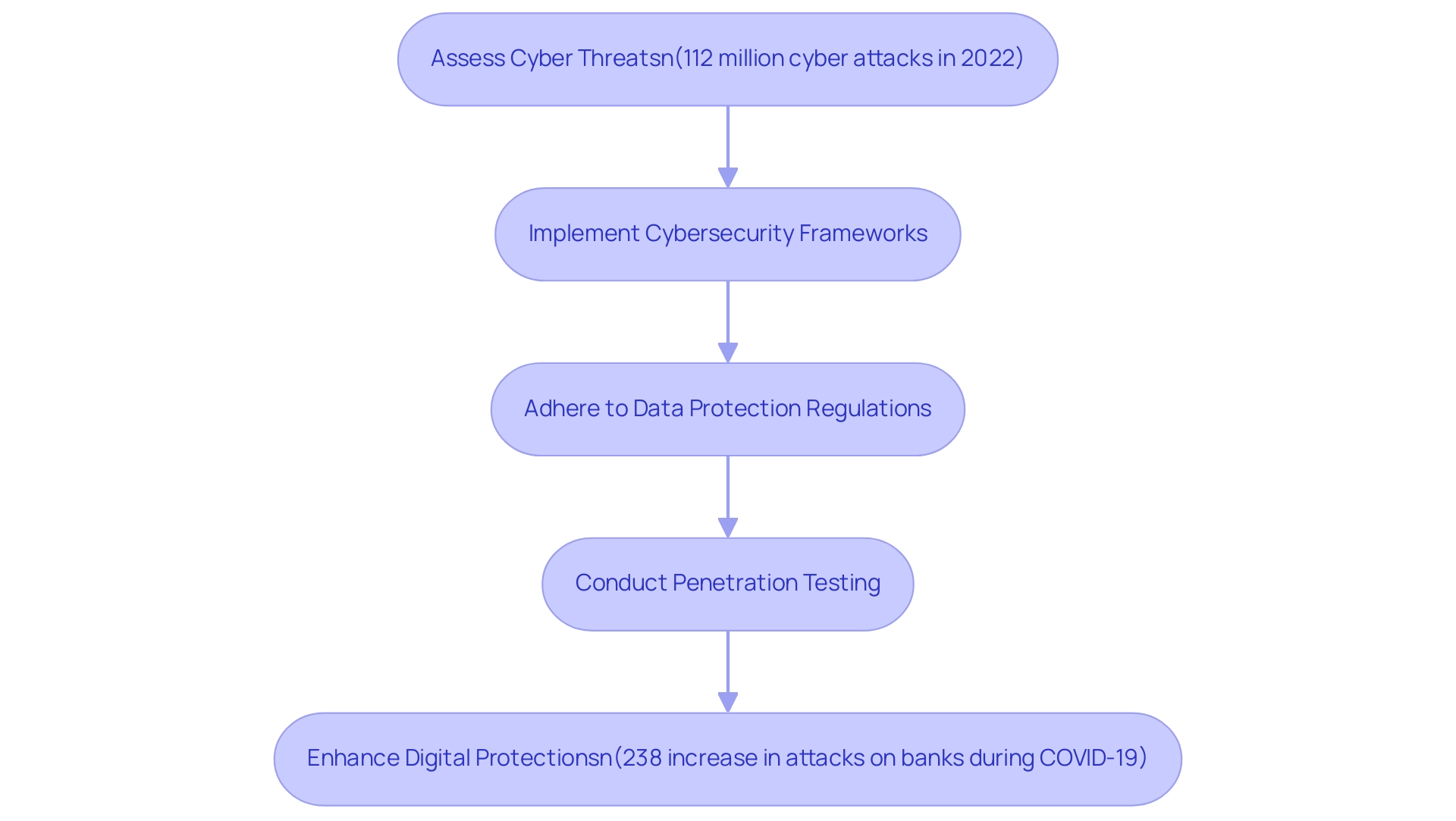
In the current digital landscape, cybersecurity has become a fundamental component of understanding what is security consulting. As companies increasingly rely on technology, they encounter heightened risks from cyber threats; for instance, in 2022 alone, there were over 112 million cyber attacks targeting Internet of Things (IoT) devices—an alarming increase from 32 million in 2018. Additionally, nearly 41% of entities rely on human memory to manage passwords, and 30% write down passwords on paper, highlighting common vulnerabilities that can be exploited by cybercriminals.
Security experts play a vital role in evaluating and enhancing what is security consulting for a company's digital protections, which are necessary for preserving data integrity and confidentiality. This process encompasses the implementation of robust cybersecurity frameworks and adherence to data protection regulations. A significant instance is the COVID-19 pandemic, which resulted in a 238% increase in cyberattacks on banks in 2020, with 27% of these attacks aimed at banks or healthcare institutions.
Confirmed data breaches in healthcare increased by 58% during this period, illustrating the urgency and impact of cybersecurity threats. Additionally, regular penetration testing is vital, serving as a proactive measure to identify vulnerabilities before they can be exploited. By prioritizing cybersecurity, consultants empower organizations to navigate the complexities of digital threats effectively, thereby safeguarding their most critical information assets.
Future Trends and Challenges in Security Consulting
As technology progresses, the field of consulting is set for both substantial opportunities and considerable challenges. Emerging technologies such as artificial intelligence and machine learning are poised to transform protective measures, particularly in automating threat detection and response. However, the rapid evolution of these technologies necessitates continuous skill development among professionals, as they must stay ahead of the curve in an environment where human error accounts for 68% of breaches, as highlighted in the 2024 Data Breach Investigations Report.
The decentralization of cybersecurity responsibilities is reshaping traditional operating models; cybersecurity leaders are evolving their strategies to empower resource owners with the knowledge and processes essential for local governance. This shift reflects a trend toward greater accountability in managing risks. Furthermore, phishing-related breaches can take up to 206 days to detect and contain, prolonging the damage and emphasizing the urgency for effective responses.
A recent incident in February 2024, where a finance worker was deceived into paying scammers $25 million after taking part in a deepfake video call that portrayed the company’s chief financial officer, illustrates the real-world challenges consultants encounter today. Consultants must also navigate the complexities of regulatory changes that demand adaptive strategies to ensure compliance. To successfully harness these advancements, organizations must remain agile and proactive in understanding what is security consulting, seizing opportunities for growth while simultaneously addressing the evolving nature of cyber threats.
Conclusion
The integral role of security consulting is increasingly evident as organizations navigate the complex landscape of digital threats. By defining security consulting as a critical domain focused on the assessment and enhancement of security measures, it becomes clear that this discipline is essential for protecting an organization’s most vital resources. Through comprehensive risk assessments, tailored security strategies, and adherence to regulatory standards, security consultants empower businesses to proactively mitigate risks and bolster their overall security posture.
As explored, the responsibilities of security consultants extend far beyond traditional physical security measures. The shift towards modern methodologies that incorporate advanced technologies, such as cybersecurity frameworks and data protection strategies, highlights the importance of an adaptive approach in today’s interconnected world. The alarming statistics surrounding cyber threats underscore the necessity for organizations to prioritize cybersecurity as a fundamental component of their security consulting efforts.
Looking forward, the landscape of security consulting presents both challenges and opportunities. Emerging technologies such as artificial intelligence and machine learning promise to enhance security measures, but they also demand continuous skill development among consultants. Organizations must remain agile, adapting to the evolving nature of cyber threats while fostering a culture of security awareness and accountability.
In conclusion, the expertise offered by security consultants is indispensable for organizations striving to safeguard their assets and information in an increasingly volatile digital environment. By embracing innovative strategies and technologies, organizations can cultivate resilience and ensure robust defenses against a myriad of threats, securing their future in a digitally-driven world.




