Introduction
In an increasingly interconnected digital landscape, the security of web applications has emerged as a paramount concern for organizations striving to protect sensitive data and uphold customer trust. Web application penetration testing serves as a critical line of defense, simulating cyberattacks to identify and remediate vulnerabilities before they can be exploited by malicious actors.
As the global investment in cybersecurity continues to soar, understanding the methodologies, tools, and benefits associated with this practice becomes essential for businesses aiming to fortify their security frameworks. This article delves into the intricacies of web application penetration testing, exploring its significance, various methodologies, essential tools, and the multifaceted advantages it offers in navigating the ever-evolving threat landscape.
Through a comprehensive examination, organizations can better appreciate the necessity of proactive security measures in safeguarding their digital assets.
Understanding Web Application Penetration Testing
Penetration testing web applications represents a strategic simulation of cyber attacks aimed at identifying vulnerabilities within web systems that could be exploited by malicious actors. This thorough evaluation involves assessing the program's defense stance through attempts to bypass various protective measures in place. The primary aim is to fortify the system’s defenses by uncovering weaknesses before they can be manipulated by cybercriminals.
As worldwide expenditure on cybersecurity products and services is expected to hit an astonishing $1.75 trillion from 2021 to 2025, organizations must prioritize comprehending the essential function of web application evaluation in protecting sensitive information and maintaining customer trust. Rob Sobers, a software engineer specializing in web security, highlights the urgency of these measures by stating,
In 2023, AT&T experienced a breach that exposed approximately 9 million customers' personal details.
This incident highlights the potential consequences of insufficient evaluation.
As companies increasingly rely on online tools for their operations, the need for thorough penetration testing web applications becomes essential. Failure to address known vulnerabilities not only jeopardizes sensitive information but also threatens the overall integrity of the organization. In a landscape where computer programmer job positions in the U.S. are expected to decline by 11 percent between 2022 and 2032, the demand for specialized cybersecurity roles is critical.
Moreover, the anticipated growth of 32% for information security analyst roles by 2032, along with a cybersecurity unemployment rate close to zero percent, emphasizes the critical demand for skilled professionals in the sector, underscoring the significance of strong web security measures.
Methodologies and Processes in Penetration Testing
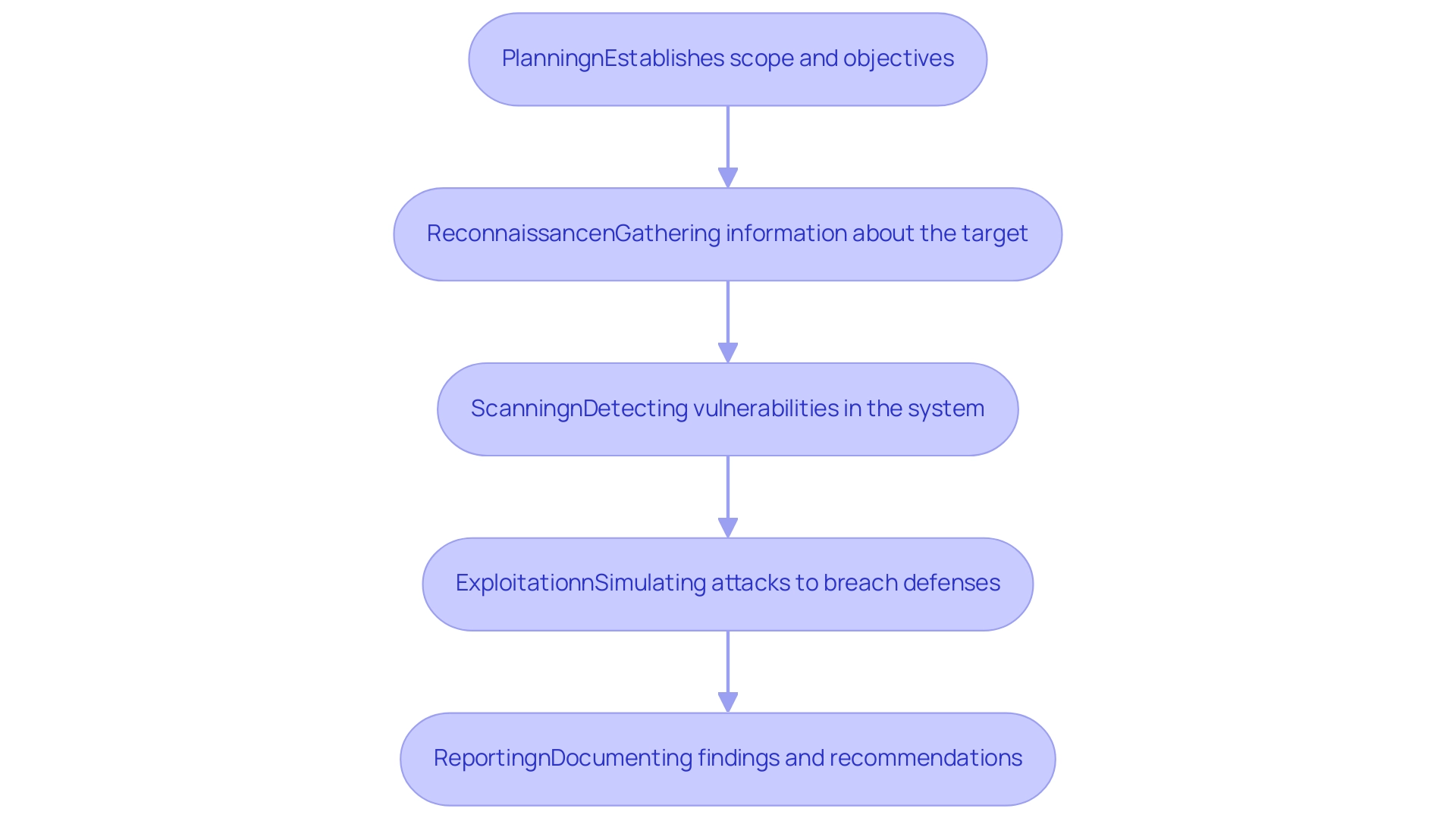
The structured framework that enhances both effectiveness and reliability is essential for penetration testing web applications methodologies. This framework typically encompasses several key phases:
- Planning
- Reconnaissance
- Scanning
- Exploitation
- Reporting
The initial planning phase is critical as it establishes the scope and objectives of the assessment, ensuring that all stakeholders have a clear understanding of the goals.
Following this, the reconnaissance phase involves gathering pertinent information about the target system, which is essential for identifying potential entry points. The scanning phase then takes a proactive approach to detect vulnerabilities within the system's architecture. Once vulnerabilities are identified, the phase of penetration testing web applications aims to breach the application’s defenses, simulating real-world attacks to evaluate the protective stance effectively.
Finally, the reporting phase is vital; it not only documents the findings but also provides actionable recommendations for remediation. By following these established methodologies, organizations can ensure that their security assessments are comprehensive and systematic, ultimately strengthening their defenses against the alarming statistic that indicates 70% of breaches stem from external sources, with 67% resulting from stolen credentials or human error. Moreover, it is troubling that 20% of organizations do not utilize any strategies to safeguard remote users accessing the internet, emphasizing a considerable deficiency in protection that highlights the significance of vulnerability assessments.
As cyber threats keep advancing, adopting organized assessment methodologies will be crucial for protecting sensitive information and preserving operational integrity. As Keepnet emphasizes, 'Watch the video below to see how Keepnet’s Phishing Simulator strengthens your defenses by training your team to quickly spot and respond to phishing threats.' This reinforces the necessity of training and preparedness in the face of emerging cyber threats.
Comprehending present trends and obstacles in vulnerability assessment can assist organizations in maneuvering through the changing environment and improving their protective stance.
Essential Tools for Web Application Penetration Testing
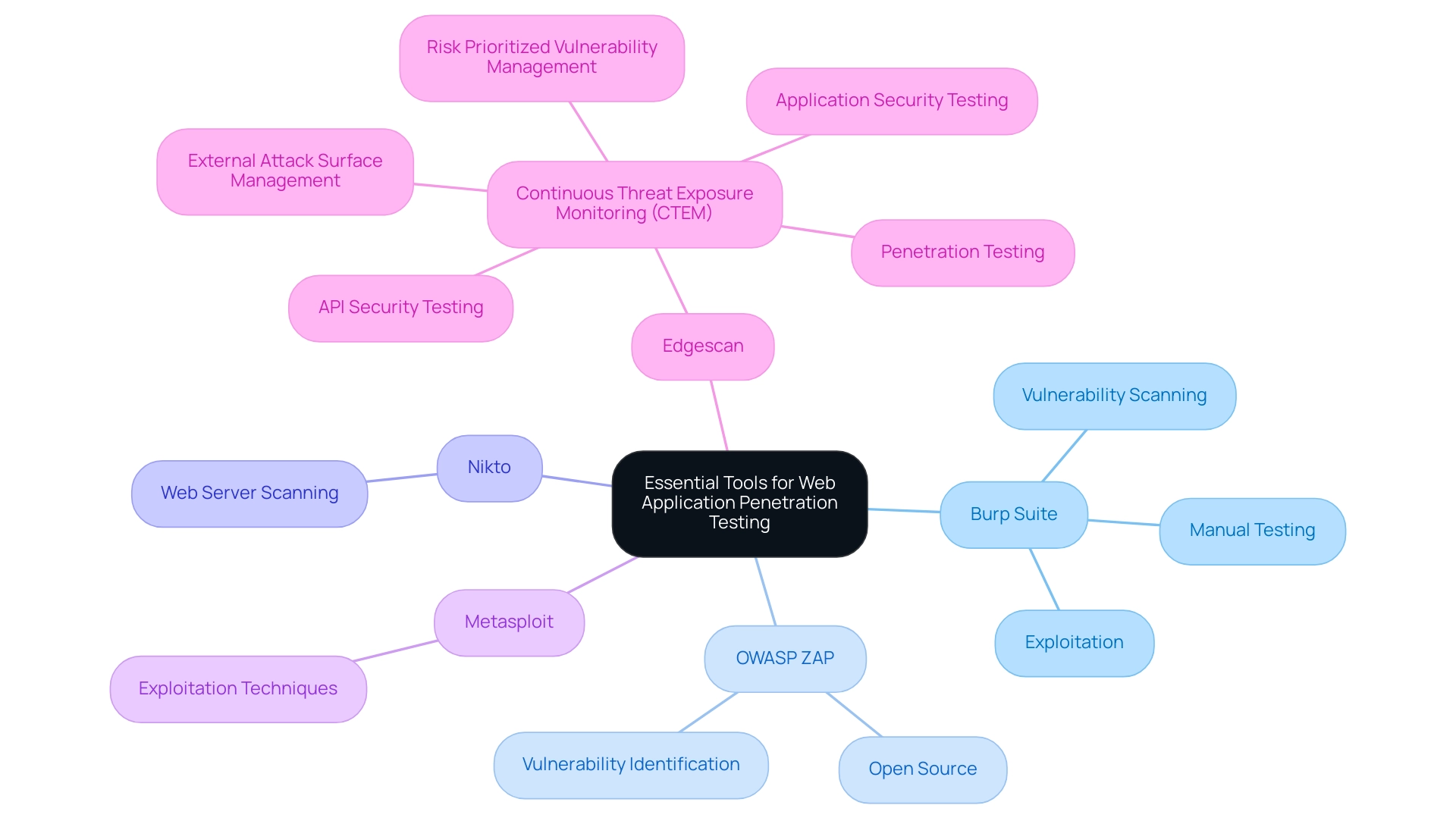
A range of tools serve a crucial function in penetration testing web applications, each created to tackle particular safety issues. Burp Suite distinguishes itself as a top option, providing a powerful collection for thorough web platform evaluation. Its capabilities include an array of features for vulnerability scanning, manual testing, and exploitation, making it an indispensable asset for security professionals.
Similarly, OWASP ZAP serves as a powerful open-source tool, adept at identifying vulnerabilities in web applications. Notably, tools like Nikto facilitate web server scanning, while Metasploit focuses on exploitation techniques, providing a well-rounded toolkit for security testers. Comprehending the unique features of these tools is essential for implementing successful security assessment strategies.
The significance of these tools is highlighted by the fact that the Open Web Project (OWASP) updates its list of top 10 vulnerabilities each year, reflecting the changing environment of web-related threats. According to Strahinja Stankovic, a Senior Information Security Analyst, if the software manages some credit card data, personal information, or even health records, it would be in a company’s best interest to conduct annual web-based penetration evaluations to fulfill the regulatory compliance that most of the data necessitates. This emphasizes the necessity of utilizing a comprehensive toolkit to ensure strong protective measures.
Moreover, Edgescan offers an extensive Continuous Threat Exposure Monitoring (CTEM) solution that encompasses various elements of software evaluation, further emphasizing the importance of these tools in a wider context. In practical uses, tools such as Burp Suite and OWASP ZAP have been crucial in detecting weaknesses, as demonstrated in the case study of w3af, an open-source web scanner that effectively identified flaws in major banks' online platforms, contributing to enhanced protection across various sectors.
The Benefits of Web Application Penetration Testing
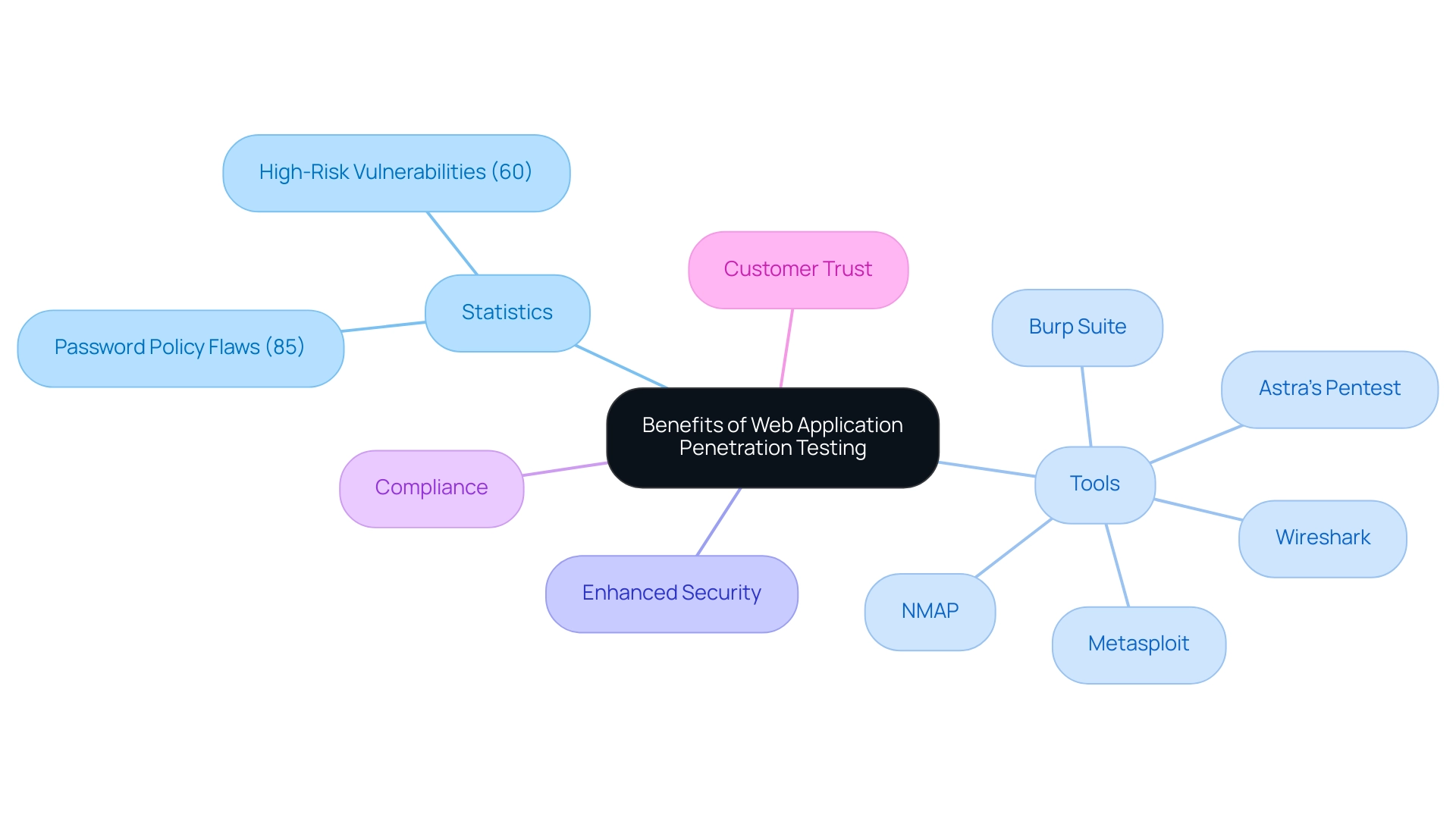
Implementing penetration testing web applications yields a multitude of benefits, most notably the early identification of vulnerabilities that could be exploited by malicious actors. By proactively addressing these vulnerabilities, organizations enhance their overall defense posture, ensuring compliance with evolving industry regulations. According to internal results from Positive Technologies:
- 85% of organizations noted instances of password policy flaws during security assessments.
- 60% uncovered high-risk vulnerabilities linked to outdated software versions.
Such statistics highlight the essential role of regular evaluations in sustaining a strong protection framework. Furthermore, employing particular tools like Astra’s Pentest, NMAP, Wireshark, Metasploit, and Burp Suite can greatly improve the assessment process. Each of these tools offers unique functionalities that aid in identifying and mitigating vulnerabilities effectively.
It is crucial to select the appropriate instruments to guarantee thorough coverage during evaluations, as the choice process can greatly affect the results of risk assessments.
Moreover, vulnerability assessment serves as a testament to an organization’s commitment to safeguarding, significantly enhancing customer trust. As companies encounter growing dangers from bot-driven assaults—one of the primary factors in successful breaches—those that engage in penetration testing web applications on a regular basis are better prepared to adjust to these new challenges. A well-organized method for evaluation not only assists in the creation of robust protective measures but also emphasizes the repercussions of minor errors, which can result in serious weaknesses if ignored.
The risk of financial loss linked to security breaches can be reduced through careful evaluation methods. In 2024, the necessity of these assessments will only continue to grow, as organizations strive to stay ahead of sophisticated cyber threats while fostering trust among their clientele.
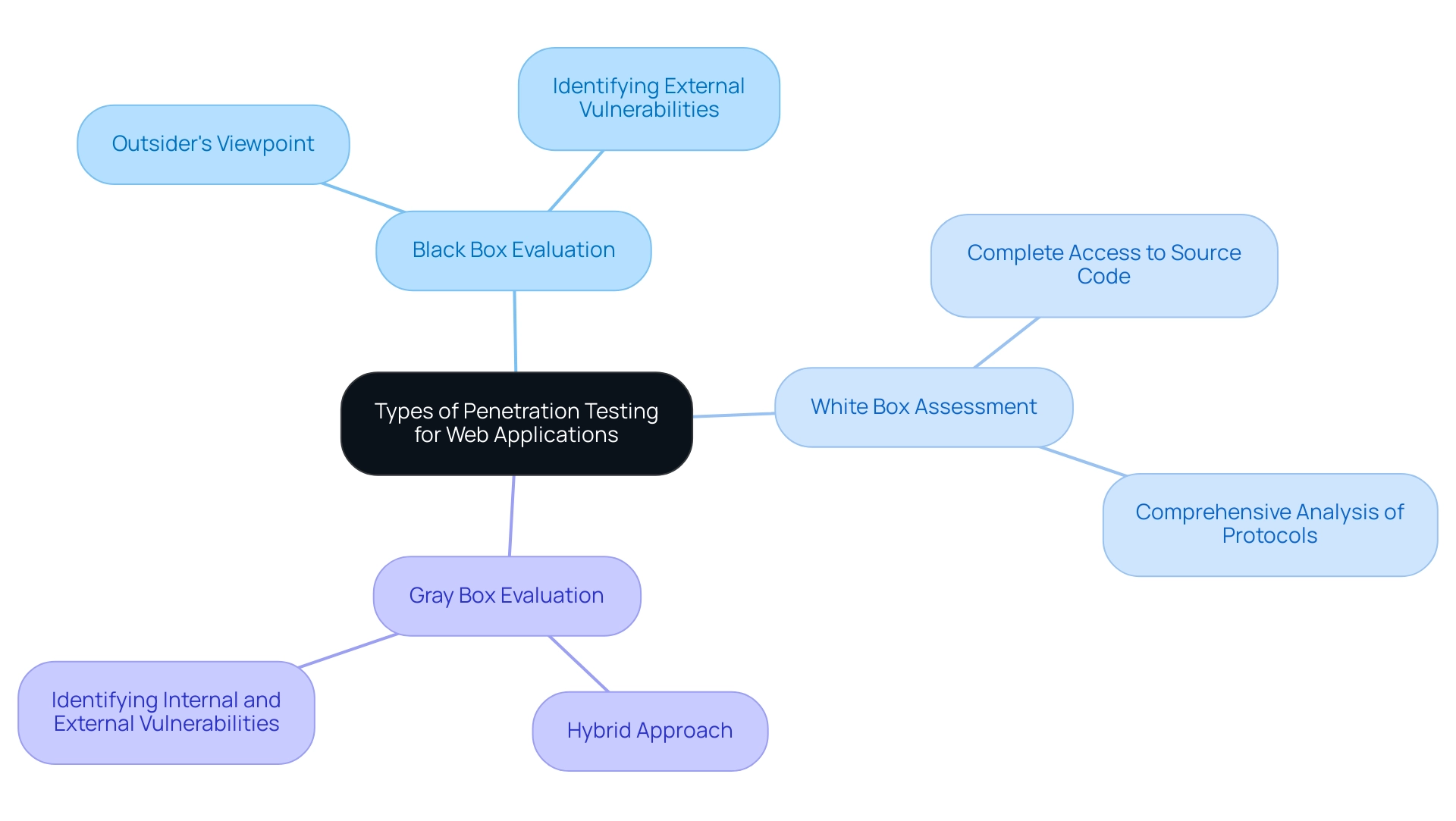
Types of Penetration Testing for Web Applications
The process of penetration testing web applications includes several methodologies, mainly classified as black box, white box, and gray box evaluations.
-
Black box evaluation mimics an outsider's viewpoint, offering a genuine assessment without previous awareness of the system’s internal functions. This approach can be particularly effective in identifying vulnerabilities that external threats might exploit.
-
White box assessment provides a thorough evaluation, granting testers complete access to the system's source code and architecture. This method enables a more comprehensive analysis of protocols and potential weaknesses within the system.
-
Gray box evaluation serves as a hybrid approach, where testers possess partial knowledge of the application, enabling them to identify vulnerabilities from both internal and external viewpoints.
Each of these evaluation types has unique benefits, rendering them appropriate for various situations according to an organization's particular protection needs and goals. As the vulnerability management market is expected to grow from USD 6.7 billion in 2020 to USD 15.86 billion by 2030, with a compound annual growth rate (CAGR) of 9%, organizations must strategically select the suitable assessment method to enhance their protective stance effectively. Additionally, the substantial rise in scams—up 400% since March 2020—highlights the urgent need for enhanced protective measures across all sectors, including penetration testing web applications.
Notably, 10% of vulnerabilities found during these assessments are information-related, highlighting a critical area for organizations to address. Additionally, penetration assessment for the public sector is likely to boost future growth by 2028, emphasizing the growing recognition of its importance. A case study on the manufacturing sector indicates that gray box testing is expected to have the second-highest CAGR of 15.8% from 2021 to 2028, reflecting a rising awareness and need for security testing in manufacturing processes.
Conclusion
The significance of web application penetration testing cannot be overstated in today's digital landscape. As organizations increasingly rely on web applications, the potential risks associated with vulnerabilities also escalate. By simulating cyberattacks, penetration testing serves as a proactive measure to identify and remediate weaknesses before they can be exploited by malicious actors. The structured methodologies and essential tools discussed, such as Burp Suite and OWASP ZAP, provide a robust framework for effectively assessing security postures and ensuring compliance with industry regulations.
Moreover, the myriad benefits of conducting regular penetration tests underscore the necessity of integrating this practice into an organization's security strategy. From enhancing customer trust to mitigating potential financial losses, the early identification of vulnerabilities leads to a more resilient security framework. As highlighted, the alarming statistics regarding breaches and vulnerabilities further reinforce the urgency for organizations to adopt comprehensive testing approaches.
In conclusion, as cyber threats continue to evolve, the need for robust web application security measures becomes increasingly critical. Organizations that prioritize penetration testing not only protect sensitive data but also demonstrate their commitment to maintaining a secure digital environment. Embracing these practices will not only fortify defenses but also foster trust and confidence among stakeholders in an era where security breaches can have far-reaching consequences.




