Introduction
In an era where cyber threats are becoming increasingly sophisticated, ensuring the security of endpoint devices such as laptops, desktops, and mobile devices is paramount. Managed Endpoint Protection emerges as a vital service in this landscape, offering a comprehensive approach to safeguarding these devices against a myriad of cyber threats. This article delves into the intricacies of Managed Endpoint Protection, exploring its core components, key benefits, and the strategic advantages it provides to organizations.
By leveraging advanced technologies and expert oversight, this service not only enhances security but also drives operational efficiency and compliance, making it an indispensable tool for modern enterprises.
What is Managed Endpoint Protection?
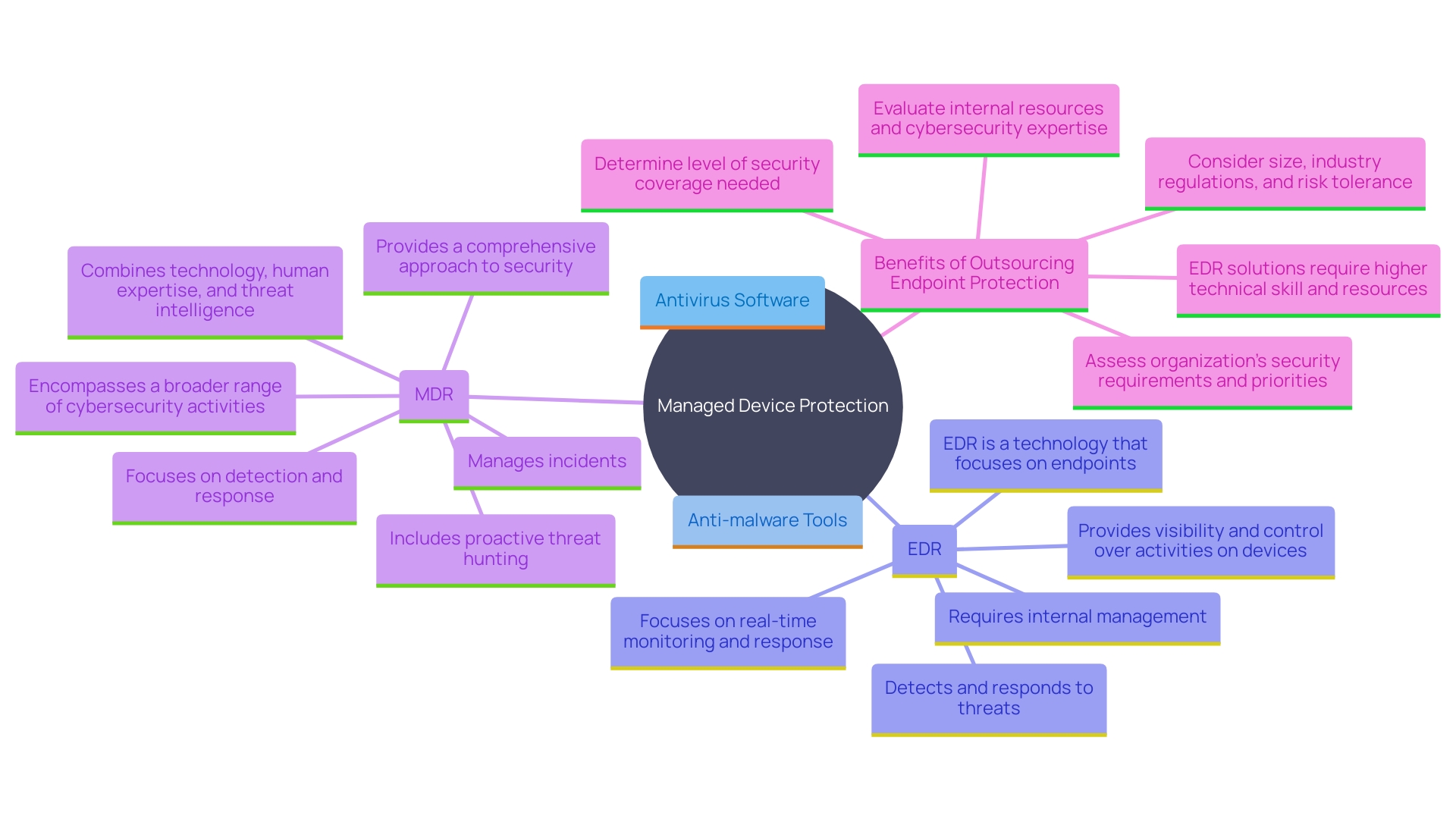
Managed Device Protection is a strong defense solution created to safeguard endpoint gadgets—including laptops, desktops, and mobile devices—from a variety of cyber risks. This service is usually provided by specialized external vendors who merge advanced technologies such as antivirus software, anti-malware tools, and intelligence to deliver real-time monitoring, detection, and response to security incidents.
Endpoint Detection and Response (EDR) plays a critical role in this ecosystem by providing visibility and control over activities on endpoint devices. EDR solutions concentrate on identifying and reacting to dangers through ongoing surveillance and data gathering from endpoints. Managed Detection and Response (MDR) further extends these capabilities by integrating human expertise and proactive danger hunting, making it a more comprehensive approach to cybersecurity.
The benefits of outsourced endpoint protection are clear. For instance, Trellix has demonstrated a 100% detection rate and zero false positives in recent independent tests, underscoring its reliability and operational efficiency. This high level of performance is crucial for organizations aiming to protect their devices against continually evolving threats without the complexity and resource burden of managing these systems in-house.
Gartner highlights the significance of adaptive data protection strategies, advising leaders in risk management to concentrate on risk-based techniques. By utilizing managed endpoint defense solutions, organizations can guarantee strong protective stances, enabling them to focus on their primary business functions while upholding a high level of trust and adherence in their protective operations.
Key Benefits of Managed Endpoint Protection
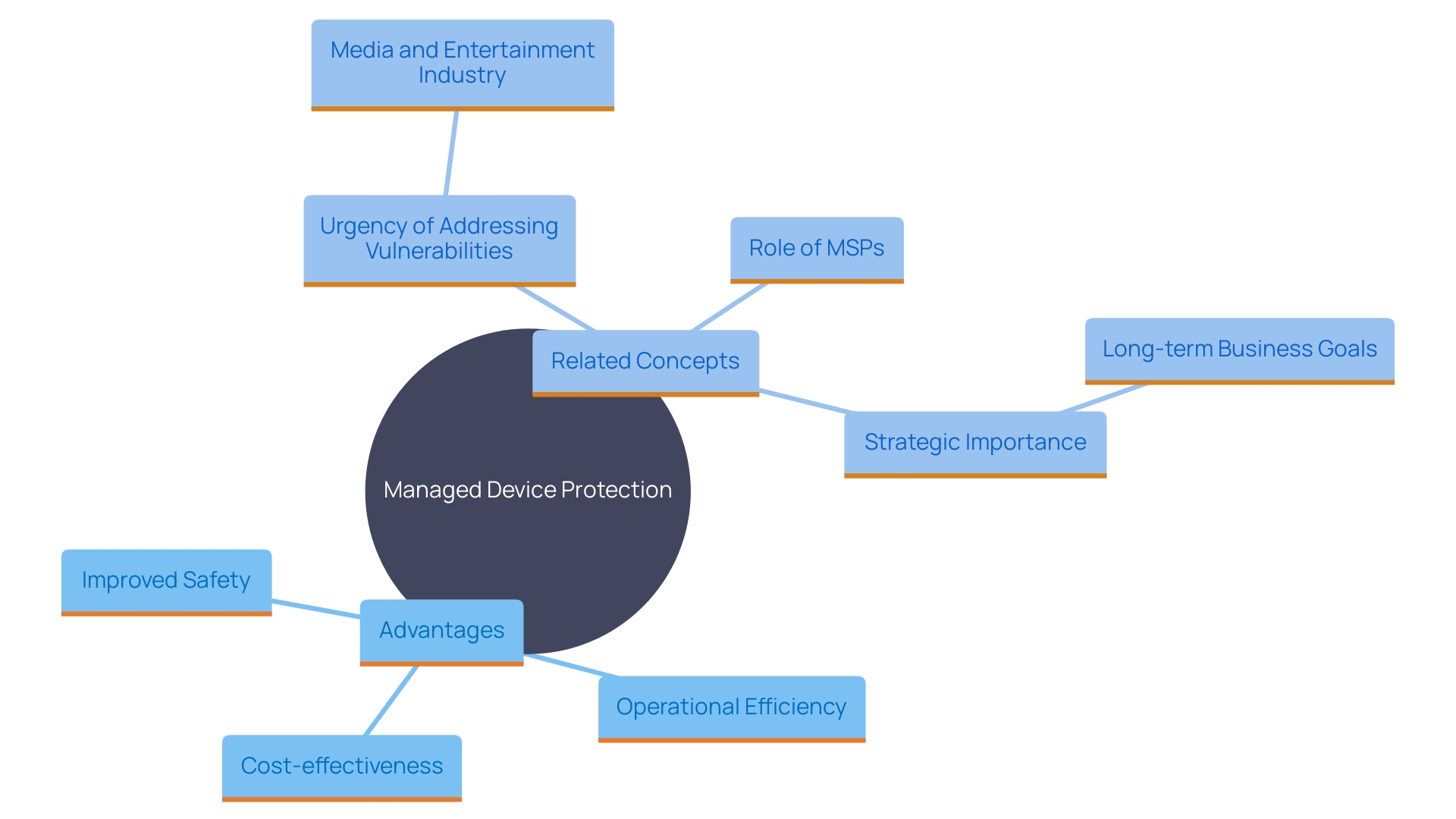
'Implementing Managed Device Protection offers critical advantages for organizations aiming to bolster their cybersecurity measures.'. This offering not only improves safety but also boosts operational efficiency and cost-effectiveness. A recent report by Palo Alto Networks underscores the urgency, revealing that the media and entertainment industry alone creates over 7,000 new vulnerabilities every month. Managed protection solutions can reduce these risks by offering ongoing surveillance and swift reaction to new threats.
A case study involving a multi-utility provider illustrates the broader benefits. By integrating Managed Endpoint Protection, the provider ensured the safety of significant volumes of customer data, including information from municipalities and military installations. This method strengthened their protective measures and enabled them to concentrate on providing vital functions without jeopardizing data integrity.
Furthermore, Managed Service Providers (MSPs) are increasingly seen as strategic partners in digital transformation. A survey of 700 MSP decision-makers indicated that nearly half of their revenue in 2024 is expected to come from managed services, with a strong focus on protection. This highlights the growing reliance on MSPs to navigate the complexities of modern cybersecurity landscape while maintaining operational efficiency.
In essence, Managed Device Protection is not just a defensive measure but a strategic investment that aligns with long-term business goals. It provides an all-encompassing answer to the difficulties presented by changing online dangers, guaranteeing both protection and operational continuity.
Enhanced Security and Threat Detection
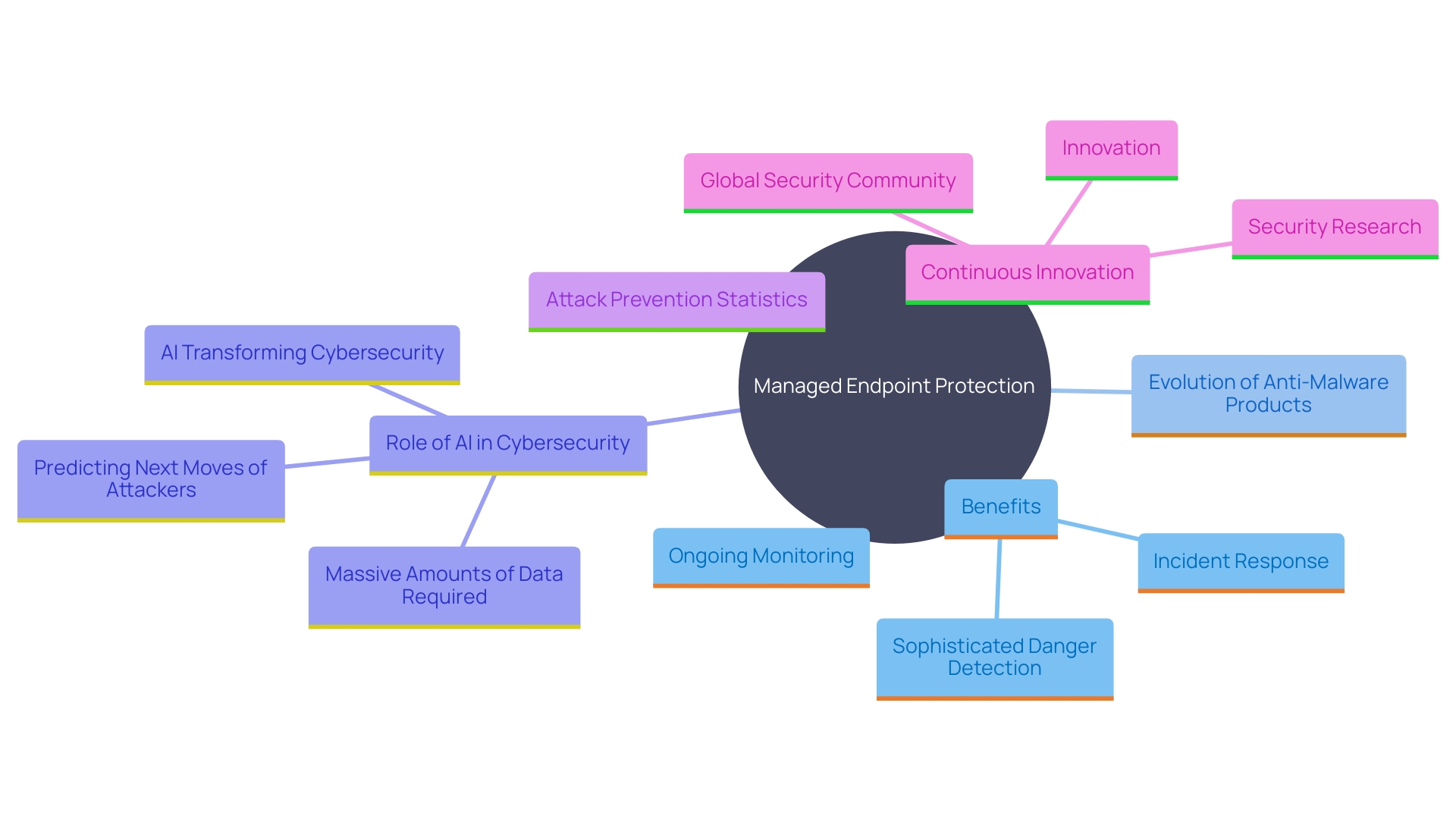
Managed Endpoint Protection provides notable benefits by improving safety through ongoing monitoring and sophisticated danger detection capabilities. By leveraging sophisticated algorithms and machine learning, these services can proactively identify potential dangers before they exploit vulnerabilities. This approach not only reduces the risk of data breaches but also ensures swift incident response.
For instance, Delivery Hero, a leading local delivery platform operating in over 70 countries, faced significant challenges with employees getting locked out of their accounts. With around 800 requests per month, each taking an average of 35 minutes to resolve, the IT team led by Dennis Zahrt implemented automated solutions to streamline access recovery. This improved efficiency and minimized downtime, illustrating the practical benefits of advanced endpoint protection.
In a broader context, the evolution of anti-malware products from the late 1980s has transformed endpoint security. Originally designed to combat known viruses, these tools have evolved into comprehensive solutions capable of detecting a wide range of malicious software, including spyware, ransomware, and trojans. This evolution highlights the significance of ongoing innovation in cybersecurity to remain proactive against advanced dangers.
Additionally, the Microsoft Digital Defense Report highlights the critical role of AI in transforming cybersecurity. By analyzing massive amounts of data, AI can predict and counteract the next moves of attackers, providing a strategic advantage in threat prevention and detection.
According to a comprehensive study of 14 million attack simulations, organizations typically prevent only 6 out of every 10 attacks. This statistic underscores the necessity of robust endpoint protection solutions that balance prevention and detection capabilities. It also illustrates the ongoing need for organizations to invest in advanced protective measures to safeguard their digital assets effectively.
Cost Savings and Reduced Infrastructure Needs
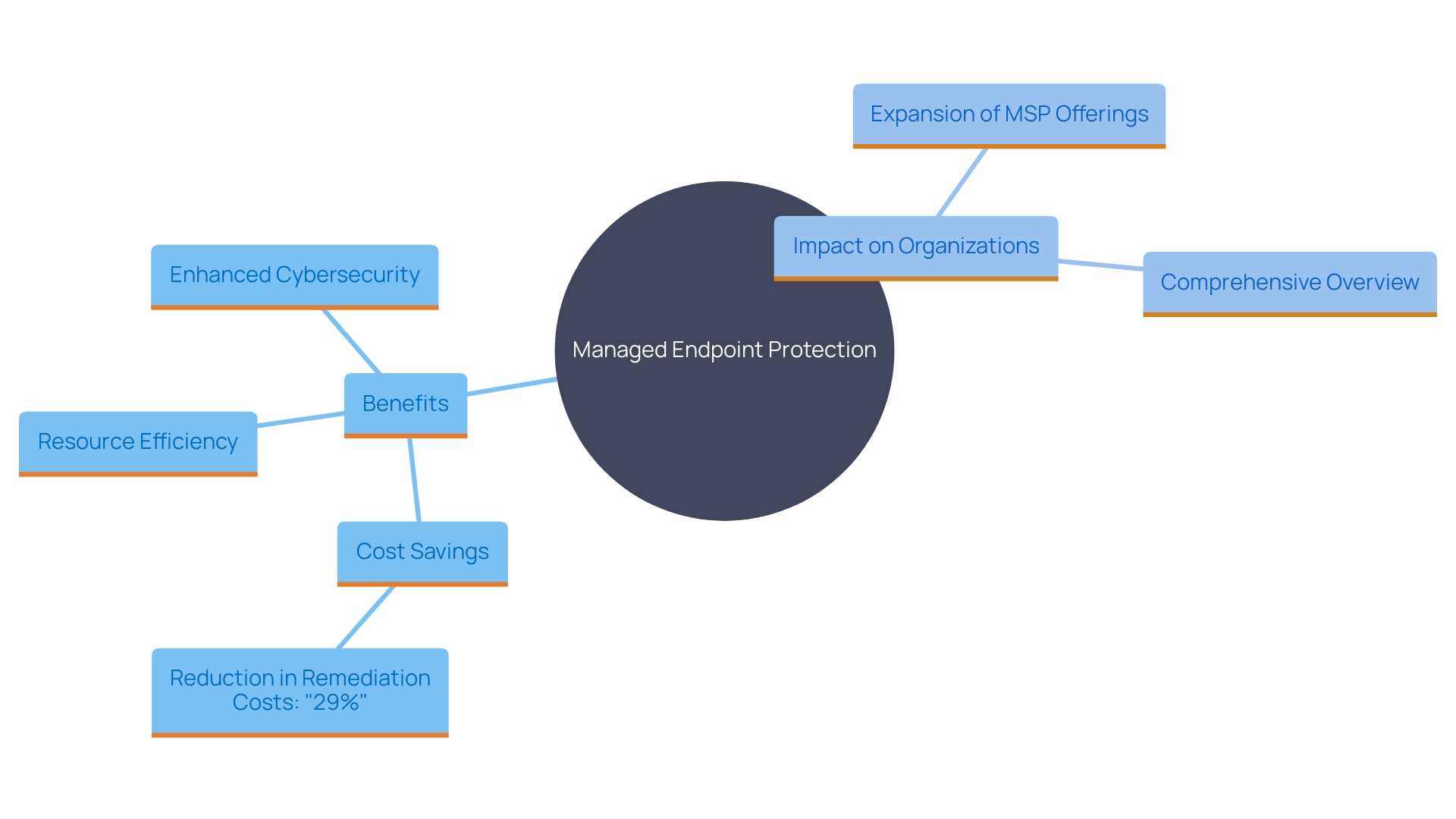
Organizations can achieve substantial cost savings by utilizing Managed Endpoint Protection solutions. This approach removes the requirement for extensive in-house infrastructure and personnel solely dedicated to endpoint protection. Data indicates that 97% of MSPs surveyed anticipate expanding their offerings, with a strong emphasis on protection, which highlights the significance and effectiveness of managed solutions in today's cybersecurity environment. By utilizing the knowledge of managed support providers, businesses can allocate resources more efficiently, reducing overall operational costs. For instance, Forrester's study on Microsoft 365 Education A5 revealed a 29% reduction in remediation costs for incidents, demonstrating the financial benefits of managed services. Moreover, embracing a comprehensive safeguarding strategy, as demonstrated by Ing's integration of protective tools, provides enhanced defense and streamlined administration, further promoting cost efficiencies and strengthening protective measures.
Scalability and Flexibility
Managed Endpoint Protection solutions provide unmatched scalability, enabling organizations to dynamically modify their protection protocols in response to changing business requirements. This flexibility is crucial, whether it involves scaling up to support a burgeoning workforce or integrating the latest technological advancements. By leveraging these adaptive services, companies can ensure continuous, robust protective measures without facing disruptions. As highlighted in the Microsoft Digital Defense Report, the evolving digital landscape requires innovative and collaborative approaches to cybersecurity. This adaptability is further backed by industry leaders and government organizations who stress the significance of remaining updated on the latest technological developments and safety regulations. Such collaborative efforts and investments in innovation for protection are vital for maintaining a resilient and safe business environment.
Improved Compliance and Data Protection
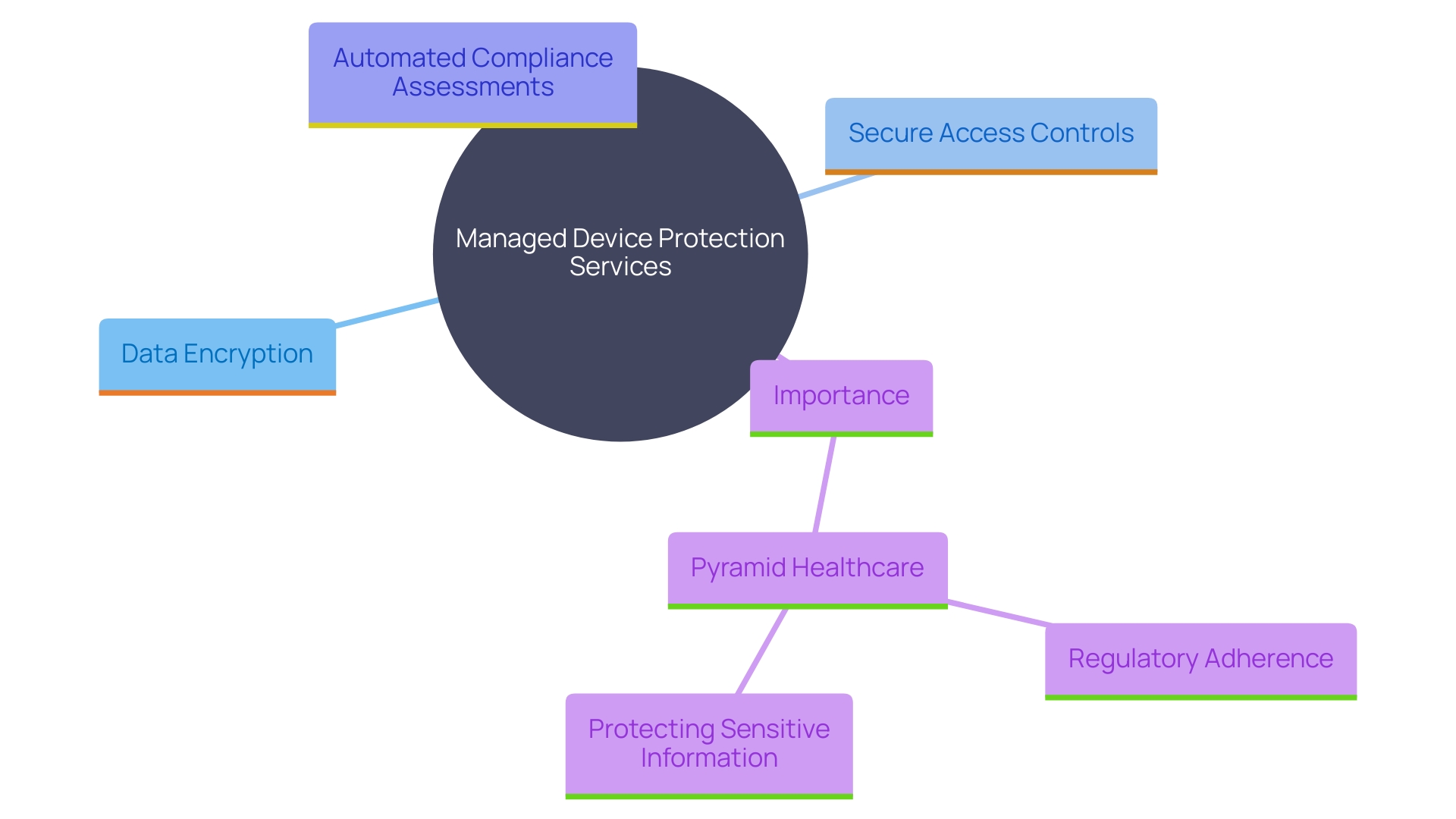
In an era of stringent regulatory requirements for data protection, Managed Device Protection Services play a critical role in assisting organizations with compliance. These solutions provide strong features such as data encryption, secure access controls, and regular evaluations of safety. For instance, Pyramid Healthcare, which operates over 100 facilities and employs more than 2,800 staff, relies on such technology to manage its complex IT infrastructure and ensure regulatory adherence. Furthermore, as organizations must adhere to numerous regulatory updates each day, the incorporation of automated compliance assessments in Managed Protection Services assists in reducing the risk of non-compliance. As regulatory compliance fundamentally signifies following governmental and industry-specific regulations, these services are essential for preserving the integrity and protection of sensitive information.
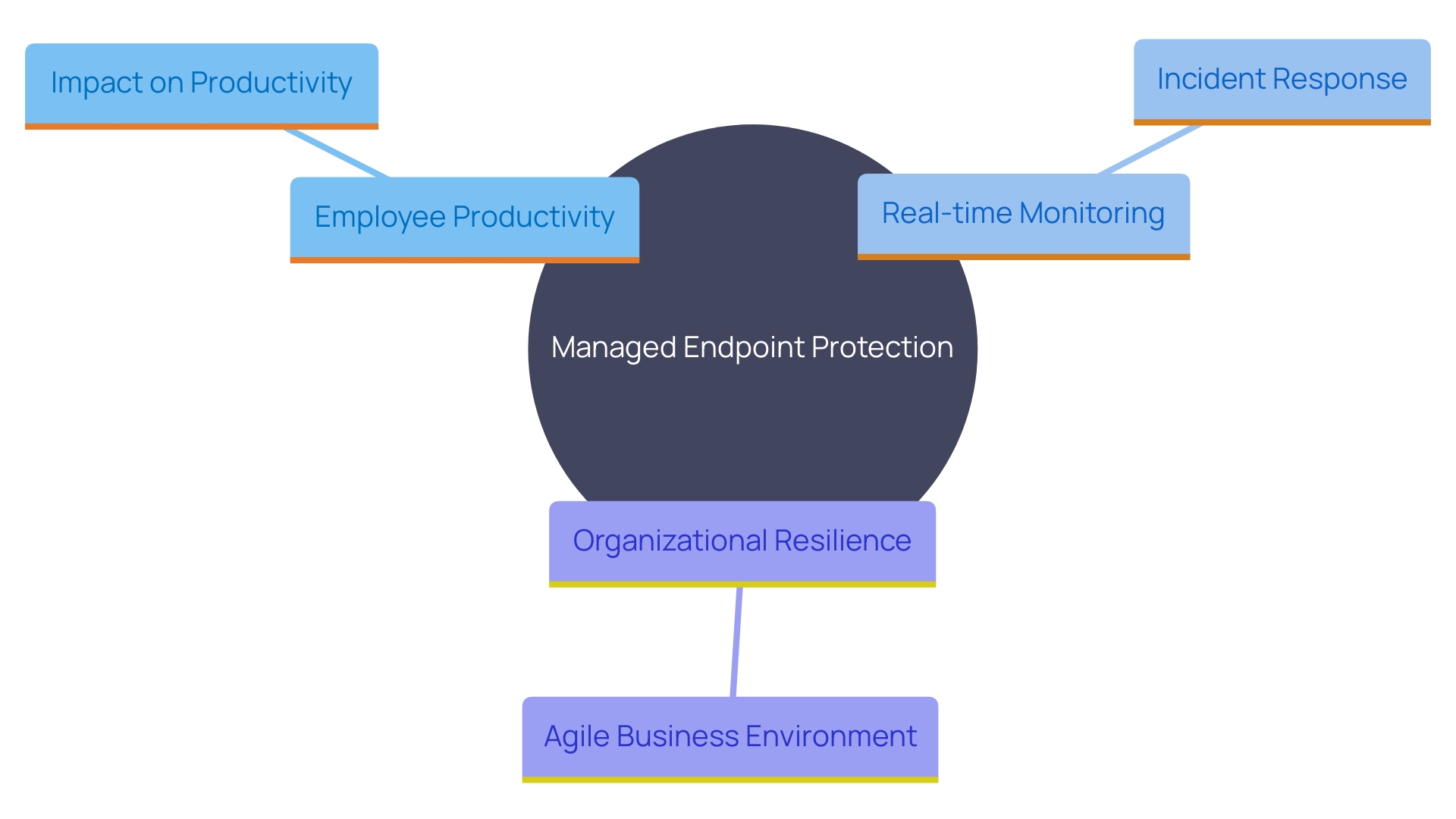
Enhanced Productivity and Reduced Downtime
By leveraging Managed Endpoint Protection, organizations can significantly minimize downtime related to security breaches or system failures. Delivery Hero, for instance, faced a high volume of account lockouts, leading to substantial employee downtime. Through improved endpoint protection strategies, such issues can be addressed more efficiently, ensuring employees remain productive. Real-time monitoring and rapid incident response are critical components, as highlighted by Microsoft Security's end-to-end approach, which spans over 50 categories within six product families. This proactive approach not only reduces risks but also simplifies the management and response processes. Ultimately, these advancements contribute to creating a more resilient and agile business environment, capable of adapting swiftly to evolving cyber challenges.
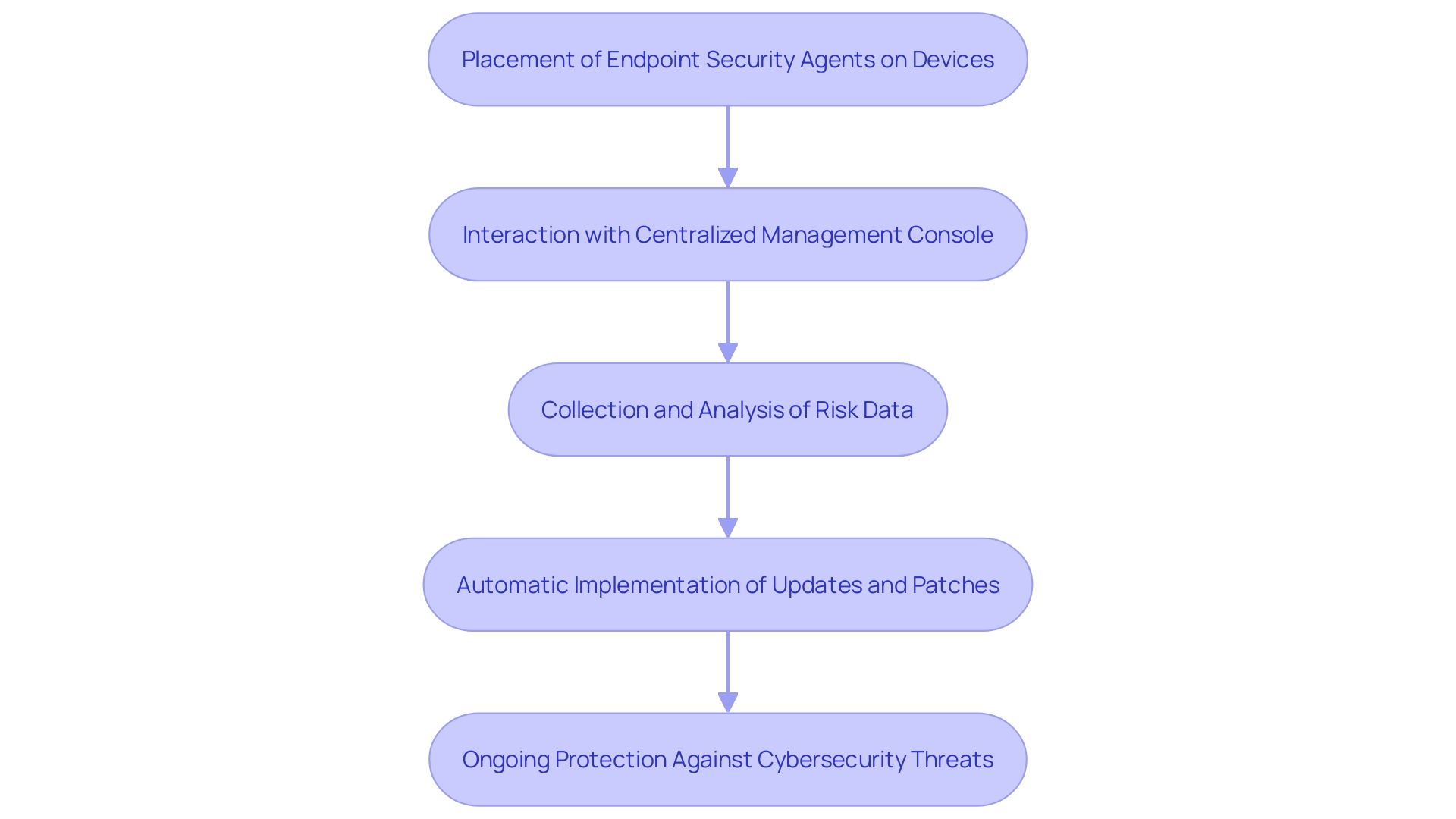
How Managed Endpoint Protection Works
Managed Device Protection integrates advanced software solutions with expert oversight to safeguard all devices within an organization. Endpoint security agents are strategically placed across devices, continuously observing for suspicious activities and possible dangers. These agents interact instantly with a centralized management console, allowing the collection of risk data for thorough analysis and prompt responses. The system guarantees ongoing protection by automatically implementing routine updates and patches, thereby strengthening devices against new vulnerabilities. This proactive approach leverages both signature-based detection and behavior analysis, effectively adapting to the evolving landscape of cybersecurity threats.
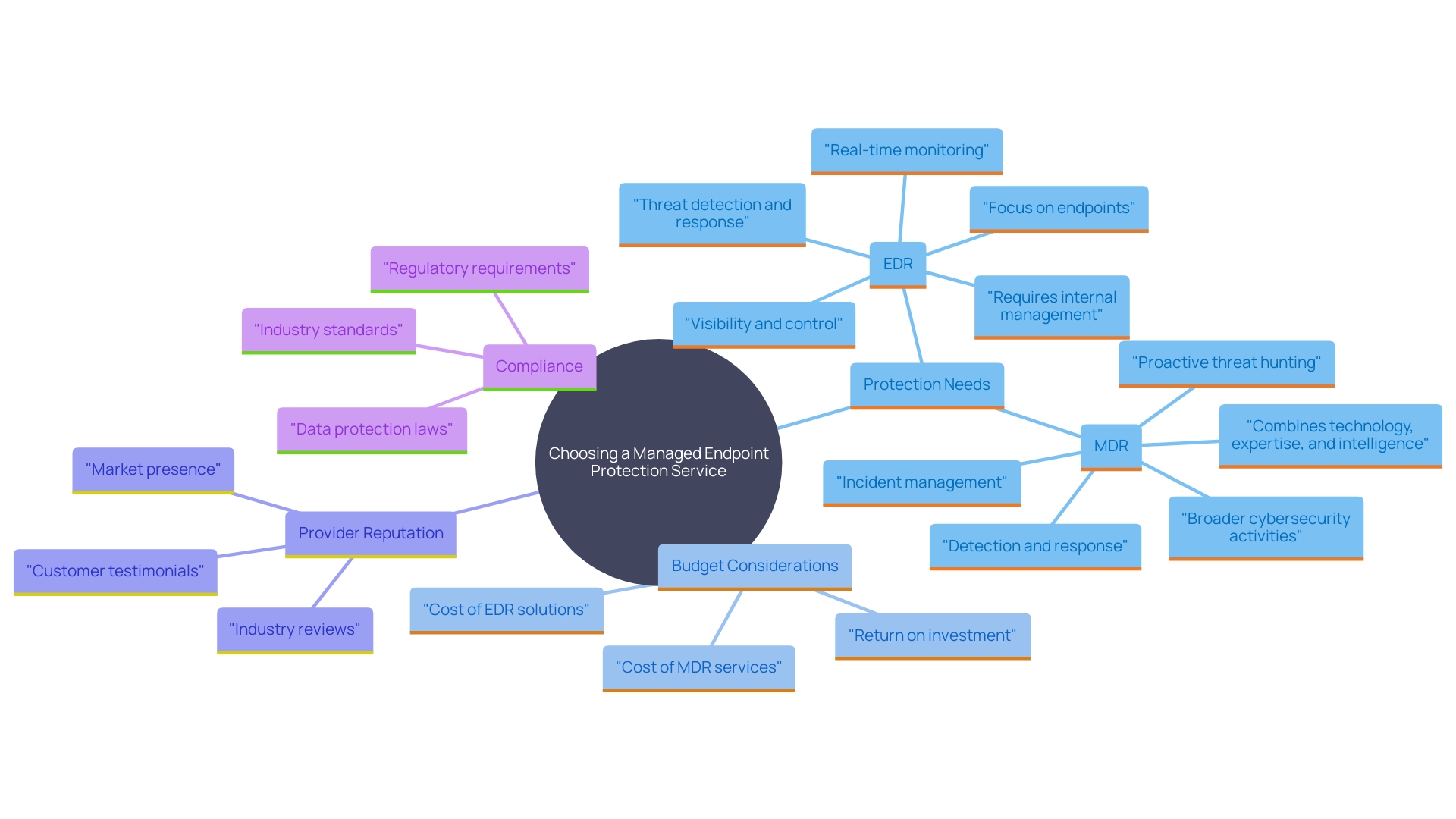
Choosing the Right Managed Endpoint Protection Service
Selecting an appropriate Managed Endpoint Protection service involves evaluating several critical factors. First, comprehending the particular protection requirements of your organization is paramount. This includes evaluating the provider's abilities in danger detection and incident response. According to Gartner, effective cybersecurity risk management is essential for confidently embracing emerging solutions without jeopardizing safety. Providers should demonstrate their ability to leverage advanced extended detection and response tools, which are crucial for faster and more accurate threat identification.
Budget constraints also play a significant role in the decision-making process. Engaging with Managed Service Providers who prioritize your business goals and align security measures with desired outcomes can offer cost efficiencies. A collaborative approach guarantees that there is no 'one-size-fits-all' solution, customizing offerings to suit distinct business environments.
Reputation and customer support of the service provider are equally important. As noted in the Microsoft Digital Defense Report, ongoing innovation and collaboration are key in the evolving digital domain. Providers that invest in protection research and maintain a strong global protection community can offer valuable insights and actionable steps to enhance your organization's cybersecurity posture.
Finally, compliance with industry standards and regulations cannot be overlooked. Leaders in protective measures and risk management should concentrate on adaptive data safeguarding methods to enhance organizational data protection, according to Gartner's advice. This holistic evaluation ensures that the chosen Managed Endpoint Protection service aligns with the strategic objectives of the organization, providing robust and reliable security solutions.
Conclusion
In the face of increasingly sophisticated cyber threats, the significance of Managed Endpoint Protection cannot be overstated. This comprehensive service equips organizations with the necessary tools to secure their endpoint devices against a wide array of vulnerabilities. By integrating advanced technologies and expert oversight, Managed Endpoint Protection not only enhances security but also fosters operational efficiency and compliance.
The ability to leverage solutions such as Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR) further underscores the importance of a proactive approach in today's complex cybersecurity landscape.
The benefits of adopting Managed Endpoint Protection are manifold. Organizations can achieve substantial cost savings by minimizing the need for extensive in-house infrastructure and personnel dedicated solely to security. This strategic investment allows businesses to focus on their core operations while ensuring robust protection against evolving threats.
Furthermore, the scalability and flexibility of these services enable organizations to adapt their security measures in response to changing business needs, thereby maintaining a resilient security posture.
Ultimately, Managed Endpoint Protection serves as an indispensable tool for organizations striving to safeguard their digital assets. By providing enhanced security, improved compliance, and reduced downtime, this service empowers businesses to navigate the challenges posed by the modern cybersecurity landscape confidently. As the threat environment continues to evolve, the integration of managed services into cybersecurity strategies will be essential for maintaining operational continuity and trust.




