Introduction
In an era where cyber threats are increasingly sophisticated and prevalent, the need for robust security measures has never been more critical. HashiCorp Vault emerges as a pivotal solution, serving as a secure repository for managing sensitive information such as passwords, API keys, and encryption keys. This article delves into the multifaceted features of Vault, highlighting its capabilities in centralized secrets management, dynamic credential generation, and stringent access control mechanisms.
As organizations grapple with regulatory pressures and the ever-evolving landscape of cybersecurity threats, understanding how Vault integrates into their security framework is essential. Through a comprehensive examination of its benefits and operational principles, this article aims to illuminate the significance of HashiCorp Vault in safeguarding sensitive data and enhancing overall security posture.
What is HashiCorp Vault?
'HashiCorp's secure storage functions as a highly protected digital repository for handling sensitive data, providing centralized secrets oversight that is essential in today’s intricate cybersecurity environment.'. As organizations increasingly face risks from supply chain attacks—highlighted by incidents like SolarWinds—effective credential oversight becomes paramount. This system addresses these challenges by offering a unified repository to store different kinds of secrets, such as passwords, API keys, certificates, and encryption keys, thereby greatly simplifying the management process.
One of the crucial characteristics of HashiCorp's solution is its strong control systems. With the proliferation of users and applications, determining who can utilize specific secrets is essential for maintaining security. The system enables organizations to implement regulations that control entry, ensuring that only permitted parties can obtain sensitive information. This ability is an essential element in reducing threats linked to privileged control systems (PAM) and identity control systems (IAM).
Additionally, the system improves protection by providing dynamic credential management. This is particularly important as many organizations have historically relied on less secure methods, such as hardcoding secrets into codebases or using .env files. By utilizing the centralized method of the system, developers can reliably obtain credentials in all environments, reducing the likelihood of breaches. For instance, integrating automated tools that scan for plaintext secrets before code commits can prevent vulnerabilities at an early stage in the software development lifecycle.
The increasing dependence on cloud technologies and the necessity for adherence to regulations, such as the Telecom Security Act, further highlight the significance of utilizing platforms like that. Organizations such as British Telecom (BT) are already moving towards a password-free experience to simplify safe entry while enhancing user satisfaction, emphasizing a wider industry trend towards improving protection without sacrificing usability.
In summary, HashiCorp's solution not only simplifies secrets management but also strengthens organizational protection by enabling centralized storage, stringent access control, and dynamic credential management, making it an indispensable tool for modern enterprises.
Key Features of HashiCorp Vault
HashiCorp Vault is a powerful tool that significantly enhances security and efficiency within organizations by offering a suite of essential features:
-
Secret Management: The system excels in securely storing, retrieving, and managing sensitive information, which can range from passwords and API keys to certificates and encryption keys. This centralized method simplifies the complexities related to dispersed secrets across different systems, enhancing management and protection.
-
Dynamic Secrets: One of the system's standout capabilities is its ability to generate secrets on-demand. This feature mitigates the risks associated with static secrets, which can be exposed or compromised over time. By providing temporary credentials, organizations can improve safety while reducing the potential attack surface.
-
Encryption as a Service: The platform provides robust encryption solutions for data both at rest and in transit. This guarantees that sensitive information is safeguarded from unauthorized entry, in accordance with contemporary protective measures that prioritize data integrity and confidentiality.
-
Audit Logging: Every access and operation within the system is meticulously logged, facilitating compliance and forensic analysis. This capability is vital for organizations that need to adhere to regulatory standards and conduct thorough investigations in the event of a breach.
-
Multi-Cloud Support: Vault is designed to operate seamlessly across various cloud platforms and environments. This flexibility is essential for enterprises that are navigating the complexities of multi-cloud architectures, ensuring that protection policies are consistently enforced regardless of the underlying infrastructure.
'Recent industry shifts, including the Telecom Security Act and heightened concerns over supply chain attacks exemplified by incidents like SolarWinds, underscore the importance of dynamic credential oversight.'. Companies like British Telecom (BT) are increasingly prioritizing solutions like HashiCorp's tool to enhance their security posture while improving user experience. 'The incorporation of the system within cloud operations not only simplifies user oversight but also corresponds with the increasing demand for strong identity and entry governance practices.'.
With the support of industry leaders, including HashiCorp being named the 2023 Global Technology Partner of the Year by Palo Alto Networks, the effectiveness of this tool in protecting sensitive information and managing dynamic credentials is being validated on a global scale.
Understanding Secrets Management in Vault
Secrets handling in HashiCorp Vault is centered on the secure storage of sensitive data while managing access effectively. This is particularly vital in the context of modern security challenges, where organizations face heightened risks from supply chain attacks and data breaches. Recent incidents, such as the SolarWinds breach, have underscored the critical need for robust credential and secrets management systems.
HashiCorp Vault categorizes secrets into two main types: static and dynamic. Static secrets are predefined and securely stored within the system, providing a stable but potentially vulnerable point if compromised. In contrast, dynamic secrets are created as needed, providing temporary permission that can be revoked at any moment. This dual approach significantly minimizes exposure risk by employing less predictable entry patterns, essential for organizations like British Telecom (BT), which are transitioning towards more secure, passwordless experiences.
Furthermore, organizations are encouraged to classify their secrets based on sensitivity and importance. Not all secrets carry the same weight; prioritizing which ones require immediate attention is crucial in formulating an effective response plan. For instance, understanding whether a secret has been exposed publicly or remains within internal systems enables organizations to assess potential impacts accurately.
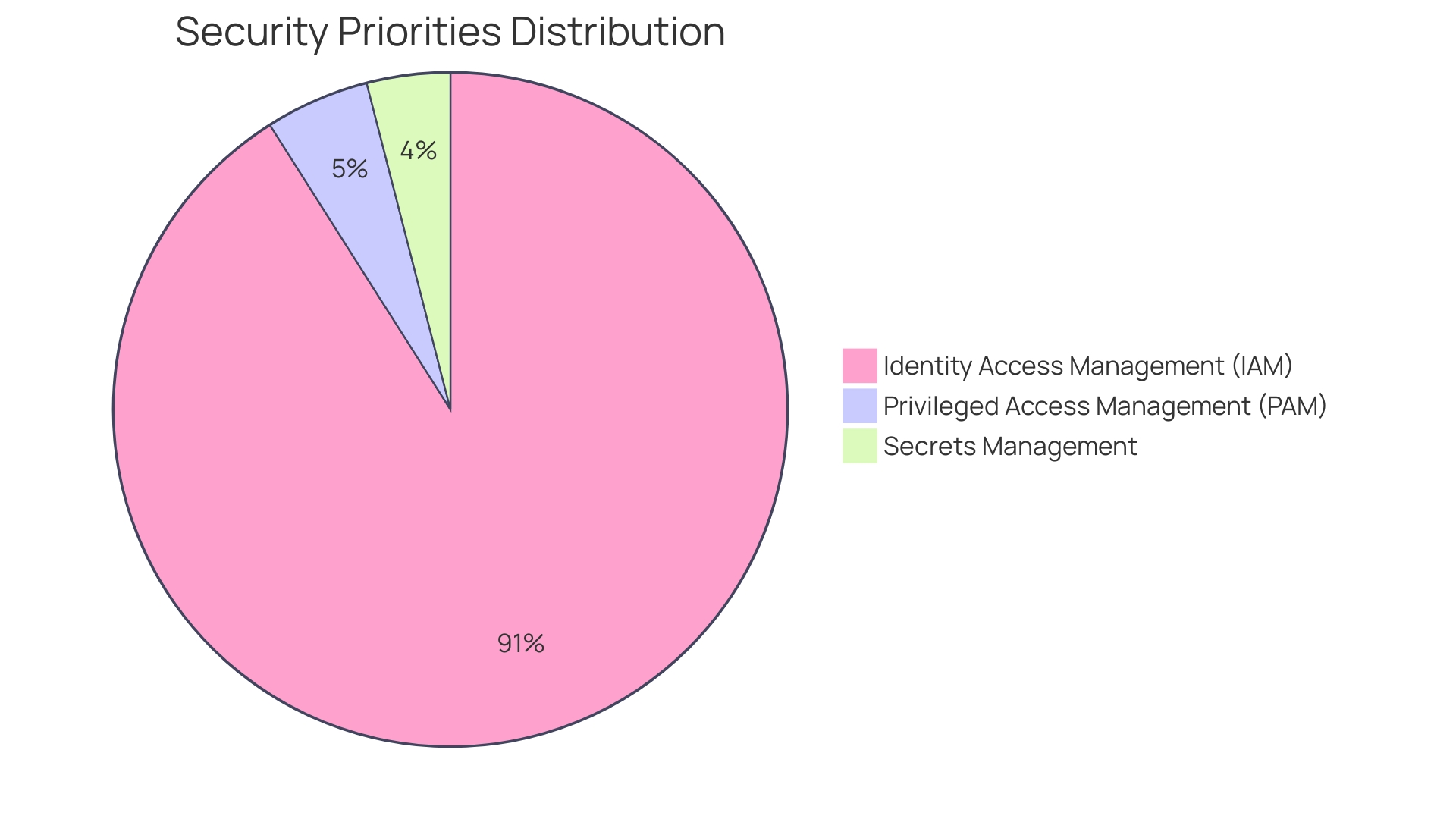
According to recent studies, 91% of organizations acknowledge the importance of Identity Access Management (IAM) as a core strategy for implementing Zero Trust frameworks. This expanding awareness emphasizes that safeguarding identities not only shields confidential data but also acts as a fundamental component for thwarting unauthorized entry. As organizations continue to face evolving threats, leveraging robust secrets management practices in tools like HashiCorp becomes essential for maintaining a strong security posture.
How Vault Works: Authentication, Validation, Authorization, and Access
HashiCorp's system implements a sophisticated authentication framework designed to ensure strict control over sensitive secrets. This framework supports multiple authentication methods, including tokens, LDAP, and various cloud identity providers, allowing both users and applications to authenticate seamlessly and securely.
Upon successful authentication, the system not only verifies the identity of the requester but also assesses permissions associated with that identity. This process culminates in the issuance of time-limited tokens that provide access to specific secrets, thus reinforcing the principle of least privilege. By ensuring that only authorized entities can interact with sensitive data, Vault reduces exposure to potential threats, such as those highlighted by the recent SolarWinds incident, which underscored the urgent need for strong credential oversight practices.
Organizations like British Telecom (BT) are increasingly acknowledging the importance of contemporary protection measures. BT's transition from conventional SSH dependence to more flexible credential handling solutions demonstrates a wider industry movement towards boosting protection while also enhancing user experience. This is essential as many protection experts struggle with the challenge of balancing improvements with user accessibility.
Moreover, as the telecom sector adjusts to new regulations such as the Telecom Security Act, the focus on privileged management (PAM), identity management (IAM), and efficient secrets management is crucial. This evolution in protective practices aligns with the necessity for organizations to safeguard credentials against risks, particularly as supply chain attacks become more prevalent.
In summary, HashiCorp's system stands out as a trustworthy option for organizations aiming to enhance their protective stance through effective authentication and access control measures.
Benefits of Using HashiCorp Vault
Introducing HashiCorp's solution within a company greatly improves safety through its centralized secrets handling features. This tool acts as a highly secure digital safe that consolidates sensitive information—ranging from passwords and API keys to certificates and encryption keys—into a single, manageable repository. 'With the increasing incidence of cyber threats and data breaches, such as the SolarWinds incident, organizations are acutely aware of the critical importance of strong credential oversight.'.
The dynamic secrets capability of the system reduces the risk of revealing sensitive information by creating new credentials as needed, guaranteeing that entry is tightly regulated and observed. This capability directly addresses the prevalent concerns in contemporary protection, namely privileged access management (PAM), identity access management (IAM), and effective secrets management. As highlighted in recent discussions, organizations are increasingly prioritizing strong IAM strategies, with 91% of respondents recognizing it as essential to their Zero Trust initiatives.
Moreover, the system's integration capabilities with various tools and platforms streamline workflows, allowing for a more efficient and secure operational environment. This is particularly crucial for organizations navigating cloud transformations while also preparing for regulatory changes, such as the Telecom Security Act, which demands rigorous trust boundaries and network segmentation. By enabling safer remote connections, this system not only boosts protection but also improves the user experience—an often difficult balance to maintain.
Furthermore, the system guarantees data encryption both during transfer and while stored, strengthening its role as a complete solution for safeguarding sensitive information. With its capabilities to simplify management and improve security, HashiCorp Vault stands as a vital asset for organizations aiming to fortify their data protection strategies.
Conclusion
The exploration of HashiCorp Vault reveals its critical role in modern cybersecurity, particularly in managing sensitive data amidst escalating threats. As organizations increasingly confront risks associated with supply chain attacks and compliance requirements, Vault emerges as a robust solution, centralizing secrets management and enhancing security measures.
Key features such as dynamic secrets generation and stringent access control mechanisms underscore Vault's effectiveness in minimizing exposure risks while facilitating secure access to sensitive information. The dual approach of managing both static and dynamic secrets allows organizations to better protect their assets, aligning with best practices in identity and access management (IAM) and privileged access management (PAM).
Furthermore, the integration of Vault within cloud environments not only streamlines operations but also supports compliance with emerging regulations like the Telecom Security Act. By prioritizing security without sacrificing user experience, Vault serves as an indispensable tool for organizations striving to bolster their cybersecurity frameworks. As the landscape of cyber threats continues to evolve, leveraging solutions like HashiCorp Vault is essential for maintaining a robust security posture and safeguarding critical information.




