Introduction
In an age where cyber threats are becoming increasingly sophisticated, organizations must prioritize the implementation of Advanced Threat Protection (ATP) to safeguard their digital assets. ATP encompasses a comprehensive suite of security solutions designed to combat complex attacks that traditional defenses often overlook.
By utilizing advanced technologies such as machine learning and real-time monitoring, ATP systems can detect, analyze, and respond to a myriad of threats, including:
- Malware
- Ransomware
- Targeted phishing schemes
The urgency for robust ATP measures is underscored by alarming statistics, such as the significant rise in spear-phishing groups and the staggering financial losses attributed to cyber incidents.
As organizations navigate this perilous landscape, understanding the multifaceted nature of ATP and its critical role in enhancing cybersecurity resilience becomes imperative for sustaining operational integrity and protecting sensitive information.
Understanding Advanced Threat Protection (ATP)
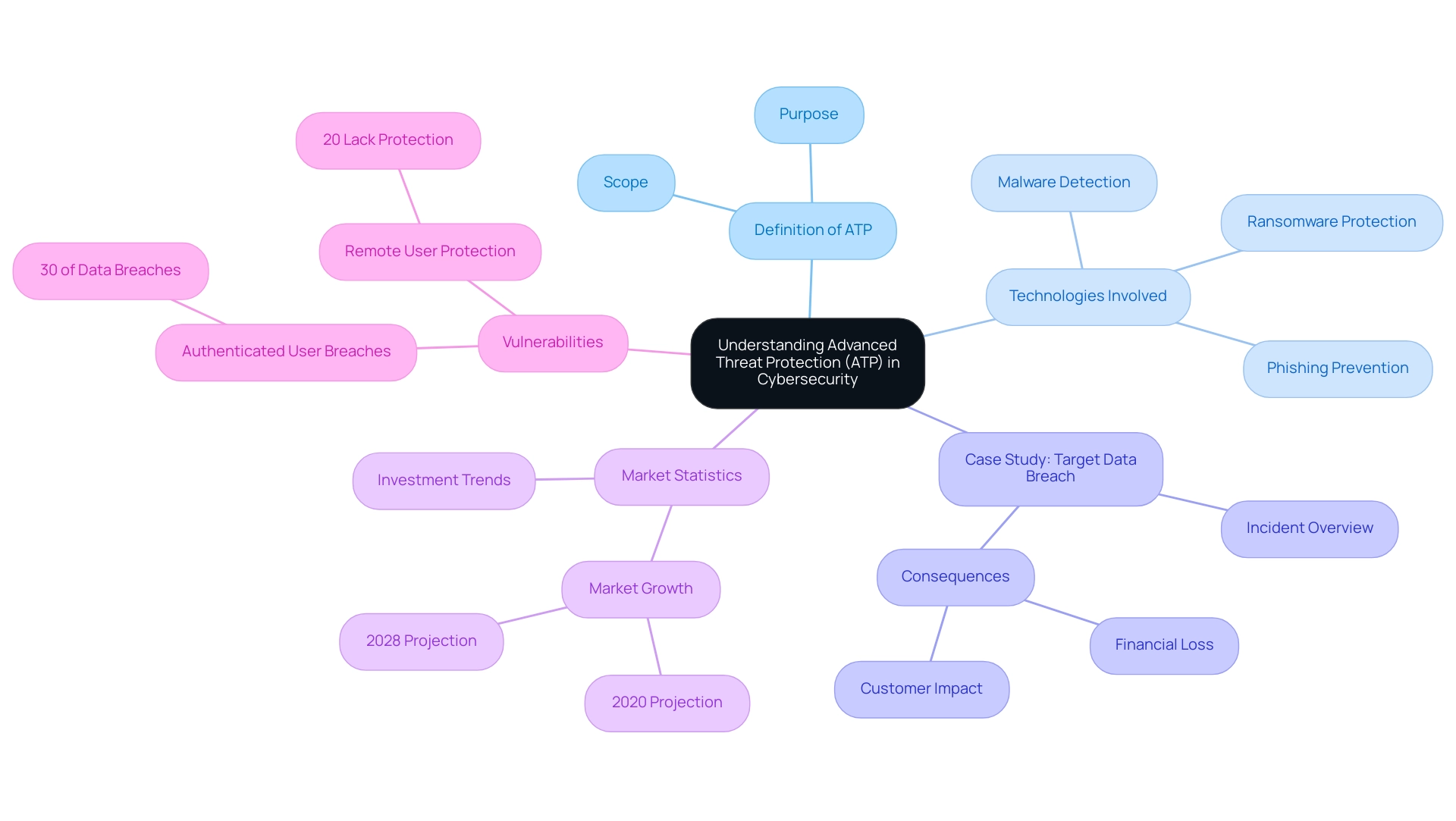
What is ATP in cyber security refers to Advanced Threat Protection, which encompasses a suite of security solutions specifically engineered to defend organizations against advanced cyber threats that conventional security measures often fail to mitigate. ATP systems deploy an array of technologies and methodologies to detect, analyze, and respond to intricate attacks, including malware, ransomware, and targeted phishing schemes. A relevant example is the Target Data Breach of 2013, where cyber attackers exploited vulnerabilities in the retail giant's security measures, compromising the information of approximately 110 million customers.
This incident underscores the dire consequences of inadequate online security measures and highlights the necessity of implementing ATP. Furthermore, with 30% of data breaches involving authenticated users, there is a significant vulnerability in traditional defenses that can be addressed effectively by understanding what is ATP in cyber security. The worldwide market for energy IT and security software and services, expected to exceed $19 billion in 2020 and attain over $32 billion by 2028, highlights the increasing significance and investment in ATP solutions.
Additionally, approximately 20% of entities lack protective measures for remote users browsing the internet, making the integration of ATP into their cybersecurity architecture imperative. By adopting what is ATP in cyber security, entities can significantly enhance their abilities to safeguard sensitive information and maintain operational integrity in an increasingly dangerous risk environment.
Types of Threats Addressed by ATP
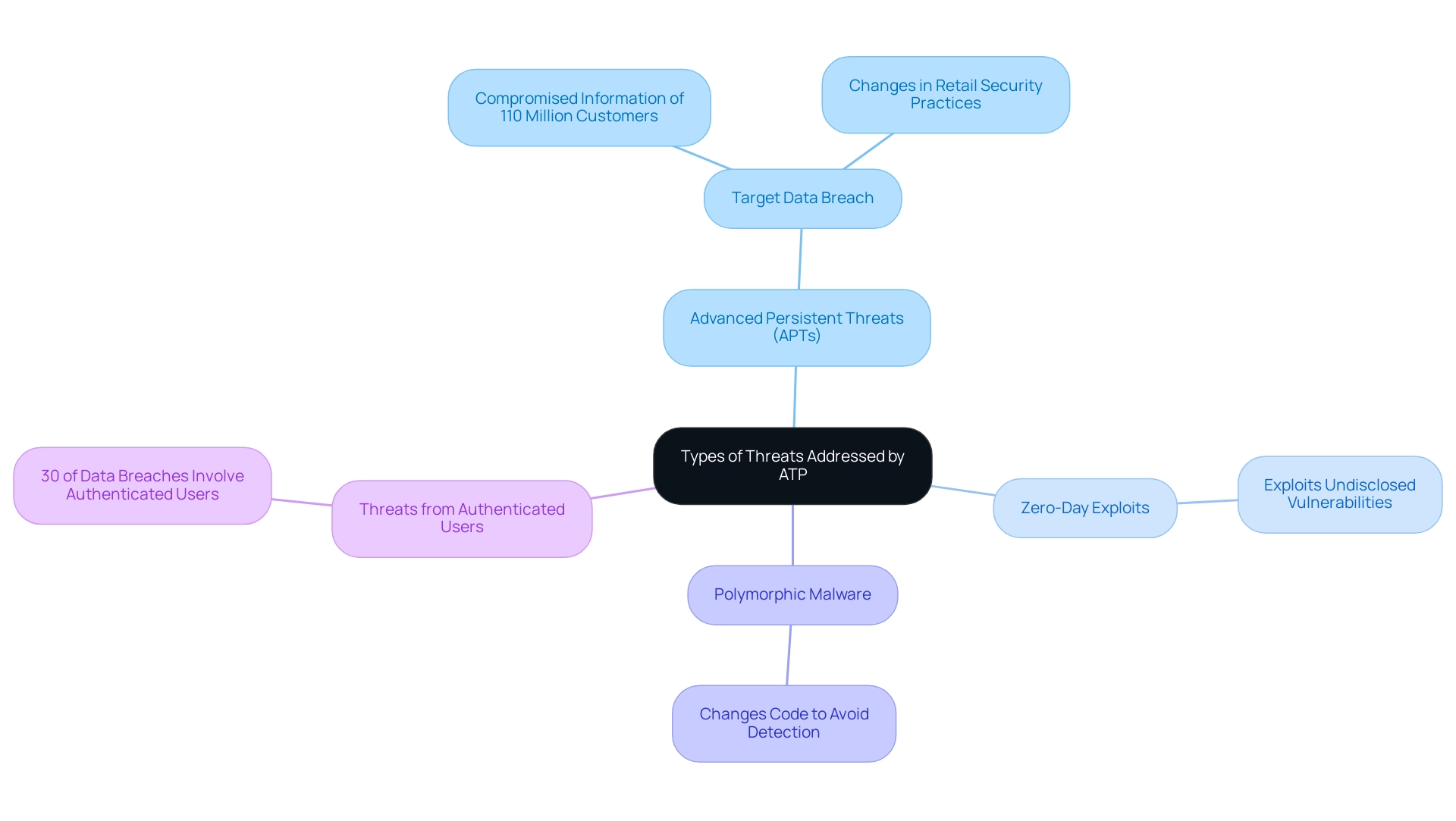
Understanding what is ATP in cyber security is crucial, as Advanced Threat Protection (ATP) solutions are essential in defending against a variety of sophisticated cyber threats, particularly Advanced Persistent Threats (APTs). These are prolonged and targeted cyber attacks specifically designed to infiltrate organizations with the intent to steal sensitive information or disrupt operations. The global market for energy IT and security software and services exceeded $19 billion in 2020, highlighting the increasing significance and investment in ATP solutions.
Additionally, ATP solutions play a vital role in mitigating zero-day exploits, which capitalize on undisclosed vulnerabilities in software before they can be patched. With 30% of data breaches involving authenticated users, the significance of ATP solutions in protecting against threats that exploit authenticated access cannot be overstated. Understanding what is ATP in cyber security is crucial, as it highlights the ability of ATP to fight polymorphic malware—malware that changes its code to avoid detection—further emphasizing its importance in modern digital security.
A notable example is the Target Data Breach, where cyber attackers used malware to steal data from Target's point of sale systems, compromising information of approximately 110 million customers. This incident resulted in significant alterations in retail security practices and highlights the need for strong ATP solutions to avert similar events. For entities, a thorough comprehension of these sophisticated dangers is not just advantageous; it is crucial for formulating effective cybersecurity plans that protect their assets and maintain their reputations.
As the landscape of cyber risks continues to evolve, knowing what is ATP in cyber security is imperative for the adoption of robust solutions to stay ahead of increasingly sophisticated attack vectors.
How Advanced Threat Protection Works
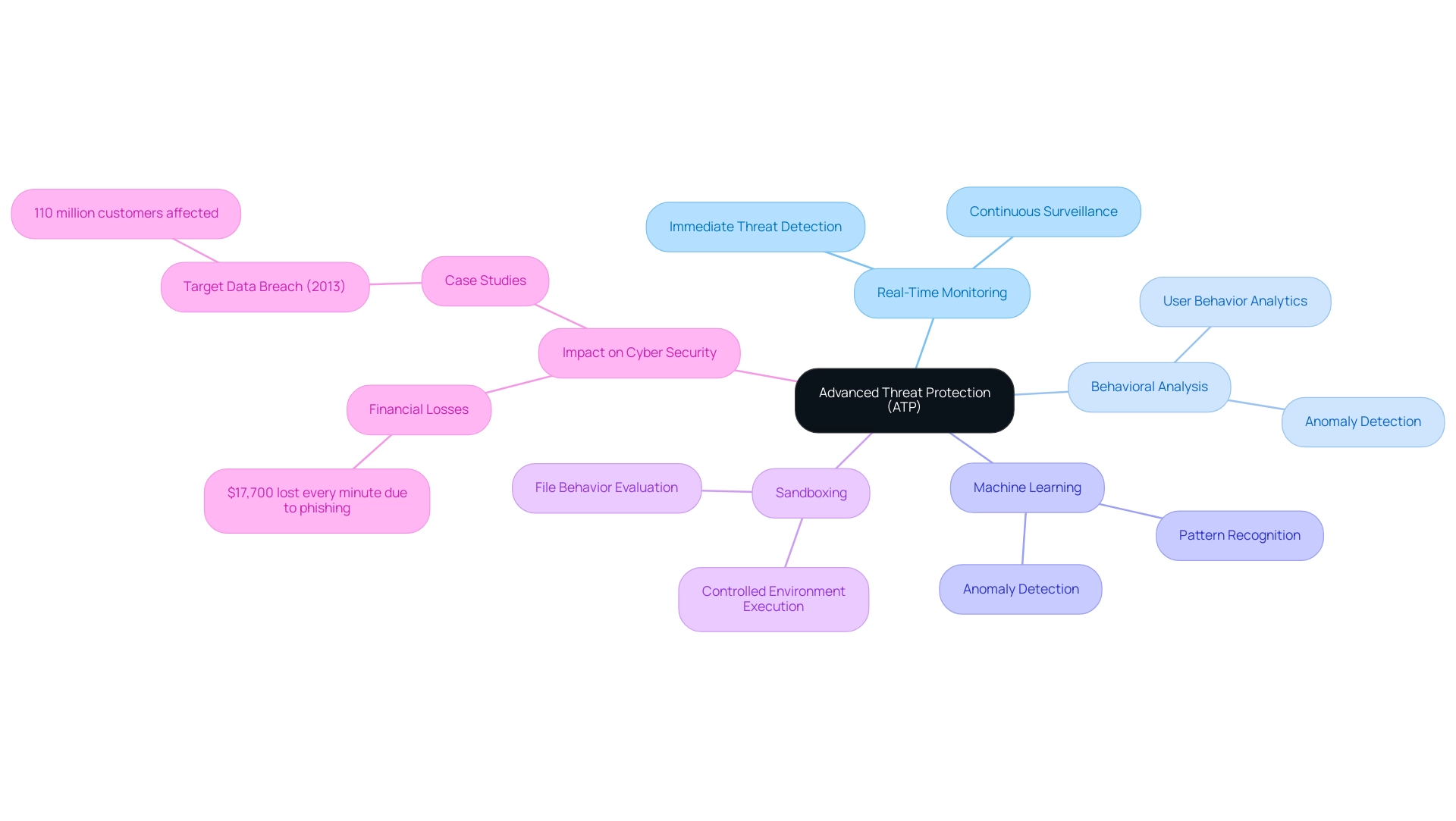
What is ATP in cyber security, as it utilizes a sophisticated multi-layered approach that includes real-time monitoring, intelligence on dangers, and behavioral analysis to protect entities from cyber risks? By utilizing machine learning algorithms, ATP solutions can help explain what is ATP in cyber security by identifying anomalies and detecting potential risks through analyzing patterns of behavior rather than solely depending on known signatures. This proactive approach significantly improves a company's capacity to react swiftly to dangers, thereby reducing the potential effect of assaults.
Furthermore, ATP systems frequently incorporate sandboxing capabilities, which allow for the execution of suspicious files in a controlled environment. This essential feature allows entities to evaluate file behavior prior to its interaction with crucial systems, ultimately strengthening their security stance. As the worldwide security market continues to expand—projected to exceed $32 billion by 2028, up from over $19 billion in 2020—leveraging machine learning and advanced methodologies becomes increasingly essential for effective threat detection and response.
With $17,700 lost every minute due to phishing attacks, it is essential to understand what is ATP in cyber security to address this urgent issue. The Target Data Breach of 2013, where cyber attackers used malware to compromise the information of approximately 110 million customers, serves as a stark reminder of the vulnerabilities entities face and raises the question of what is ATP in cyber security and the critical need for robust measures.
Benefits of Implementing Advanced Threat Protection
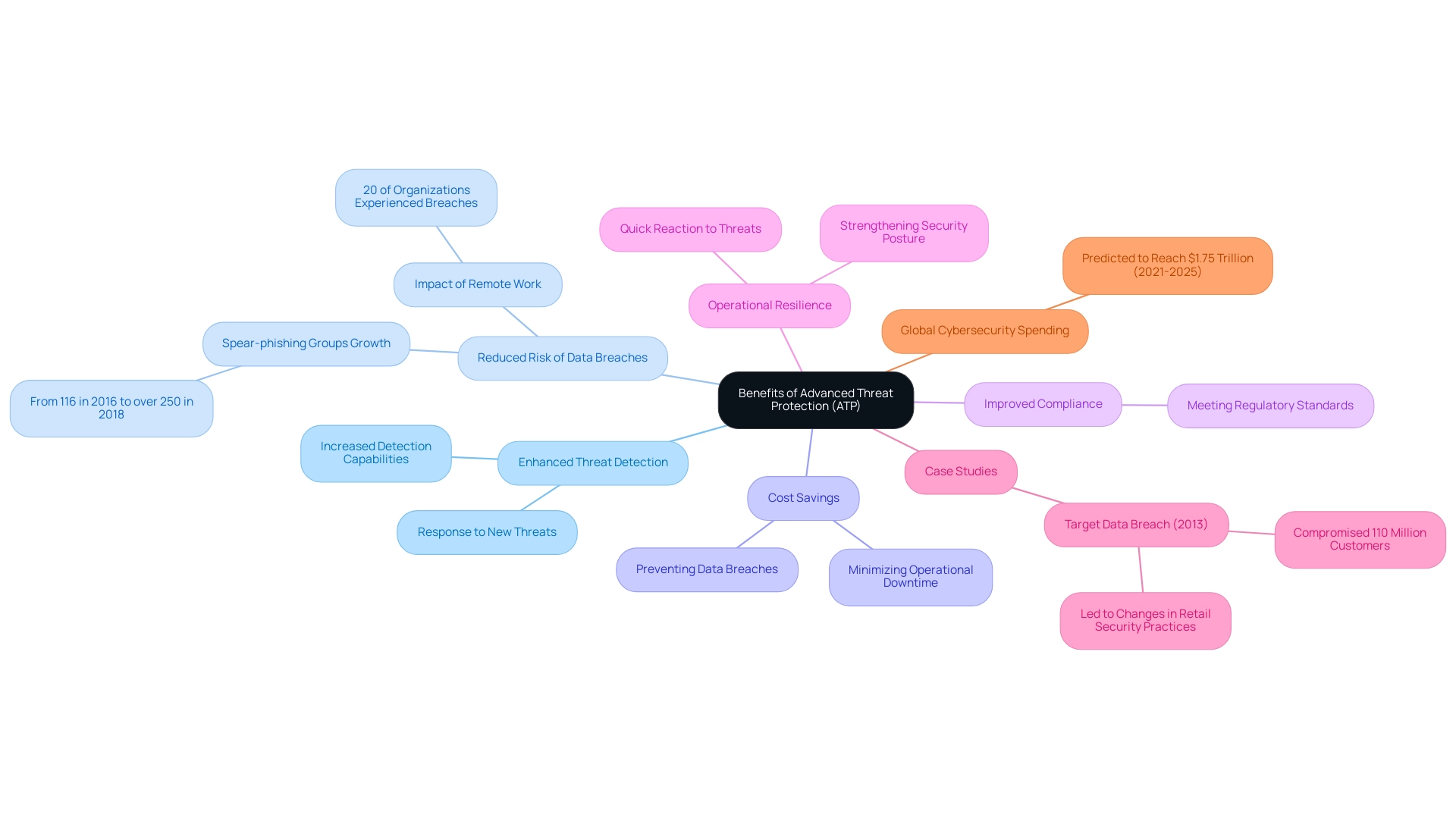
Understanding what is ATP in cyber security is essential, as the implementation of Advanced Threat Protection (ATP) brings a multitude of advantages that are crucial for contemporary entities navigating the complex cybersecurity landscape. ATP solutions enhance threat detection capabilities, significantly lowering the risk of data breaches and bolstering compliance with regulatory standards. As recent findings indicate, the number of known spear-phishing groups surged from 116 in 2016 to over 250 in 2018, underscoring the urgent need for effective protective measures.
Furthermore, the pandemic has highlighted vulnerabilities in remote work environments, with remote workers causing a security breach in 20 percent of businesses. Organizations that understand what is ATP in cyber security can drastically reduce the possibility of successful cyberattacks, thereby safeguarding sensitive data and preserving customer trust. A notable example is the Target Data Breach in 2013, where cyber attackers exploited vulnerabilities, compromising the information of approximately 110 million customers, which led to significant changes in retail security practices.
Additionally, ATP can result in substantial cost savings by preventing expensive data breaches and minimizing operational downtime linked to security incidents. The ability to quickly react to new dangers not only improves operational resilience but also strengthens a company's overall security stance, making it a vital investment for 2024 and beyond. In a study of 24 incidents, over 50% of supply chain attacks were linked to infamous cybercrime groups, underscoring the growing complexity of challenges that ATP is intended to address.
Moreover, with worldwide expenditure on cybersecurity products and services expected to hit $1.75 trillion from 2021 to 2025, understanding what is ATP in cyber security is becoming increasingly important for entities aiming to stay ahead of the evolving threat landscape.
Best Practices for ATP Implementation
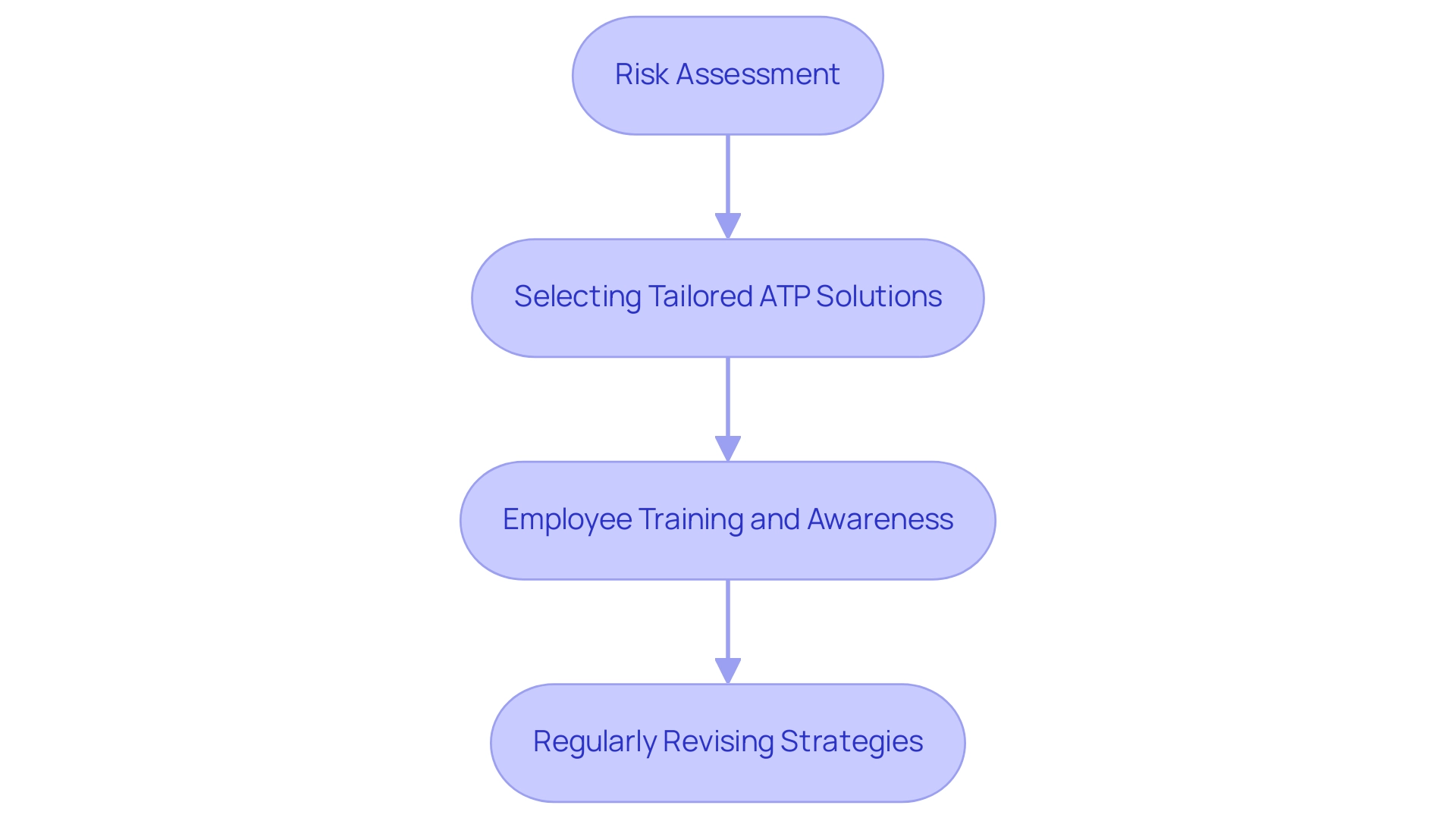
For entities aiming to understand what is ATP in cyber security and implement Advanced Threat Protection (ATP) effectively, adherence to best practices is paramount. Starting with a thorough risk assessment is crucial; this process not only identifies existing vulnerabilities but also allows entities to prioritize security enhancements. Given that endpoints are among the most targeted assets—81% of companies report having been affected by malware—this initial evaluation becomes a vital first step.
Additionally, the number of known spear-phishing groups has surged from 116 in 2016 to over 250 in 2018, highlighting the increasing sophistication of phishing attacks that organizations must contend with. Selecting ATP solutions that are tailored to specific security requirements and compatible with existing systems is essential for coherent integration. Moreover, ongoing training and awareness initiatives for employees cannot be overstated, especially as human error contributes significantly to security breaches.
In light of evolving tactics, such as the use of SSL certificates in phishing attacks and the prevalence of watering hole attacks—conducted by 14% of APT groups during the penetration stage—organizations must commit to regularly revising and enhancing their ATP strategies. This adaptability is essential for sustaining strong defenses against an increasingly sophisticated risk landscape, where an average smart home may face over 12,000 hacking attempts weekly. By incorporating these practices, organizations can enhance their cybersecurity posture and gain insights into what is ATP in cyber security to better protect themselves against advanced persistent threats.
Conclusion
Implementing Advanced Threat Protection (ATP) is crucial for organizations aiming to protect their digital assets in the face of escalating cyber threats. ATP solutions utilize a multi-layered approach, including real-time monitoring and machine learning, to effectively detect and respond to sophisticated attacks such as malware, ransomware, and targeted phishing schemes.
The severe consequences of inadequate cybersecurity, exemplified by incidents like the Target Data Breach, emphasize the urgent need for robust ATP measures. As threats become increasingly sophisticated, with a notable rise in spear-phishing groups and data breaches involving authenticated users, comprehensive ATP strategies are essential.
Adopting best practices for ATP not only strengthens defenses against advanced persistent threats but also cultivates a culture of cybersecurity awareness among employees. Regular training and assessments are vital for staying ahead of evolving threats. By investing in ATP solutions, organizations can significantly mitigate risks while ensuring operational resilience and protecting their reputations.
In conclusion, prioritizing Advanced Threat Protection is imperative for navigating the complexities of modern cybersecurity. Leveraging advanced technologies and implementing effective strategies allows organizations to enhance their defenses and remain resilient against sophisticated threats. Taking action now is vital, as the cost of inaction can far exceed the investment in protective measures.




