Introduction
In the digital age, where data breaches and cyber threats loom large, the importance of secure proxy servers cannot be overstated. These sophisticated tools serve as essential barriers between users and the vast expanse of the internet, effectively concealing identities and protecting sensitive information. By utilizing advanced encryption protocols, secure proxies not only enhance privacy but also play a crucial role in safeguarding data from potential eavesdroppers.
As organizations increasingly turn to these technologies to bolster their cybersecurity measures, understanding the various types of proxy servers, their operational mechanisms, and the inherent risks involved becomes paramount. This article delves into the multifaceted world of secure proxy servers, exploring their benefits, functionality, and the critical considerations that organizations must navigate in order to harness their full potential.
Defining Secure Proxy Servers: An Overview
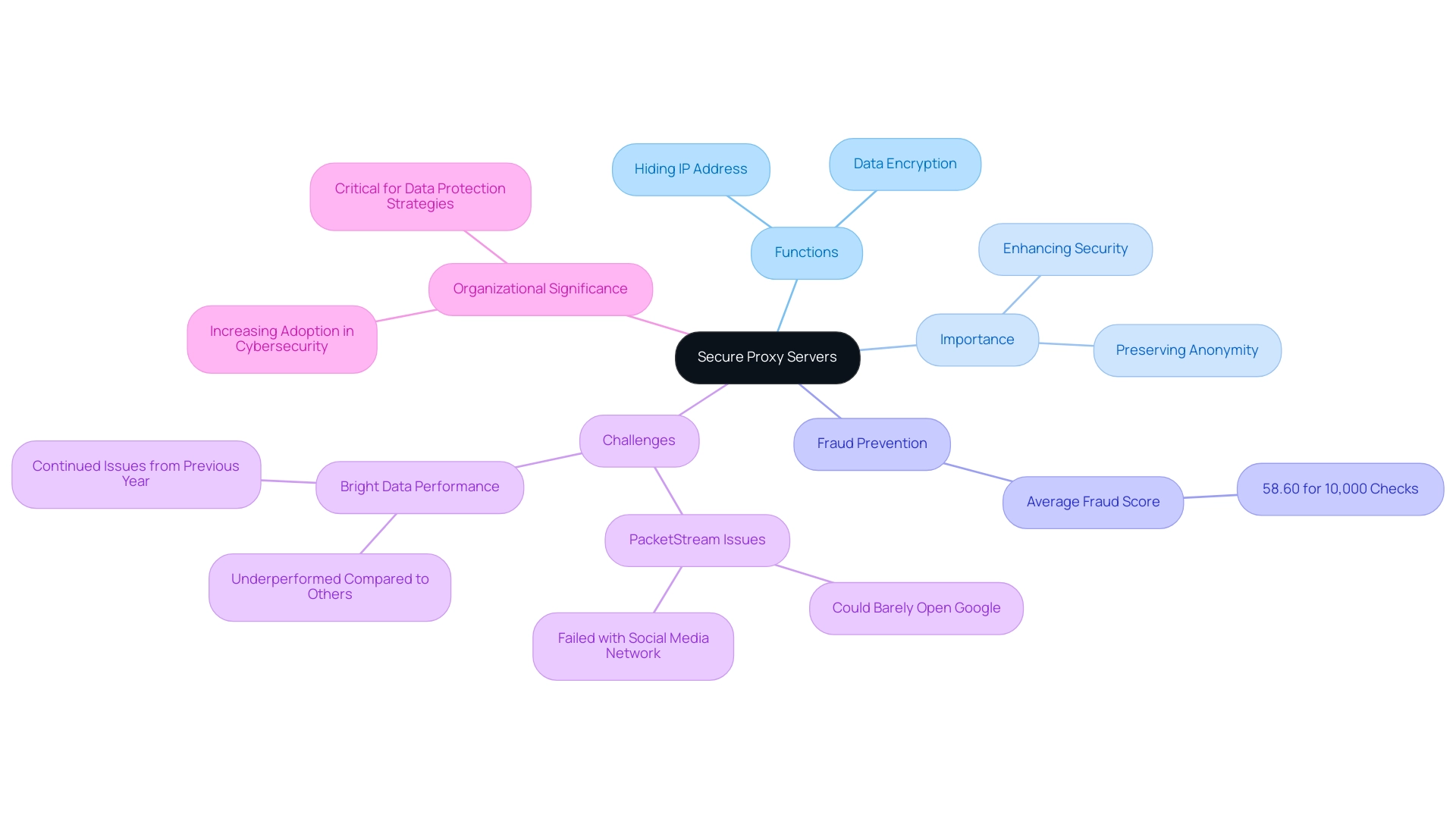
A secure proxy server serves as an essential link between an individual's device and the wider internet, greatly improving security and privacy by hiding the individual's IP address. By sending requests from clients to hosts and returning the hosts' responses, these intermediaries ensure that user identities remain confidential. Utilizing advanced encryption protocols, a secure proxy server acts as an intermediary system to protect data during transmission, making it essential for safeguarding sensitive information and preserving anonymity online.
In fact, the average fraud score for 10,000 checks per provider was 58.60, highlighting the significance of secure proxy servers in preventing fraud and improving protection. Their utility is paramount in environments where data security is critical—such as corporate networks or when accessing sensitive information over unsecured public Wi-Fi. For instance, PacketStream has faced challenges, as it could hardly open Google and failed completely with a social media network, highlighting the real-world difficulties some intermediaries encounter.
As organizations increasingly acknowledge the significance of strong data protection strategies, secure proxy servers are becoming vital instruments in the cybersecurity arena. This is further illustrated by the performance issues faced by Bright Data's mobile services, which continued to show problems similar to the previous year, indicating a need for improvement in a competitive market.
The Benefits of Utilizing Secure Proxy Servers
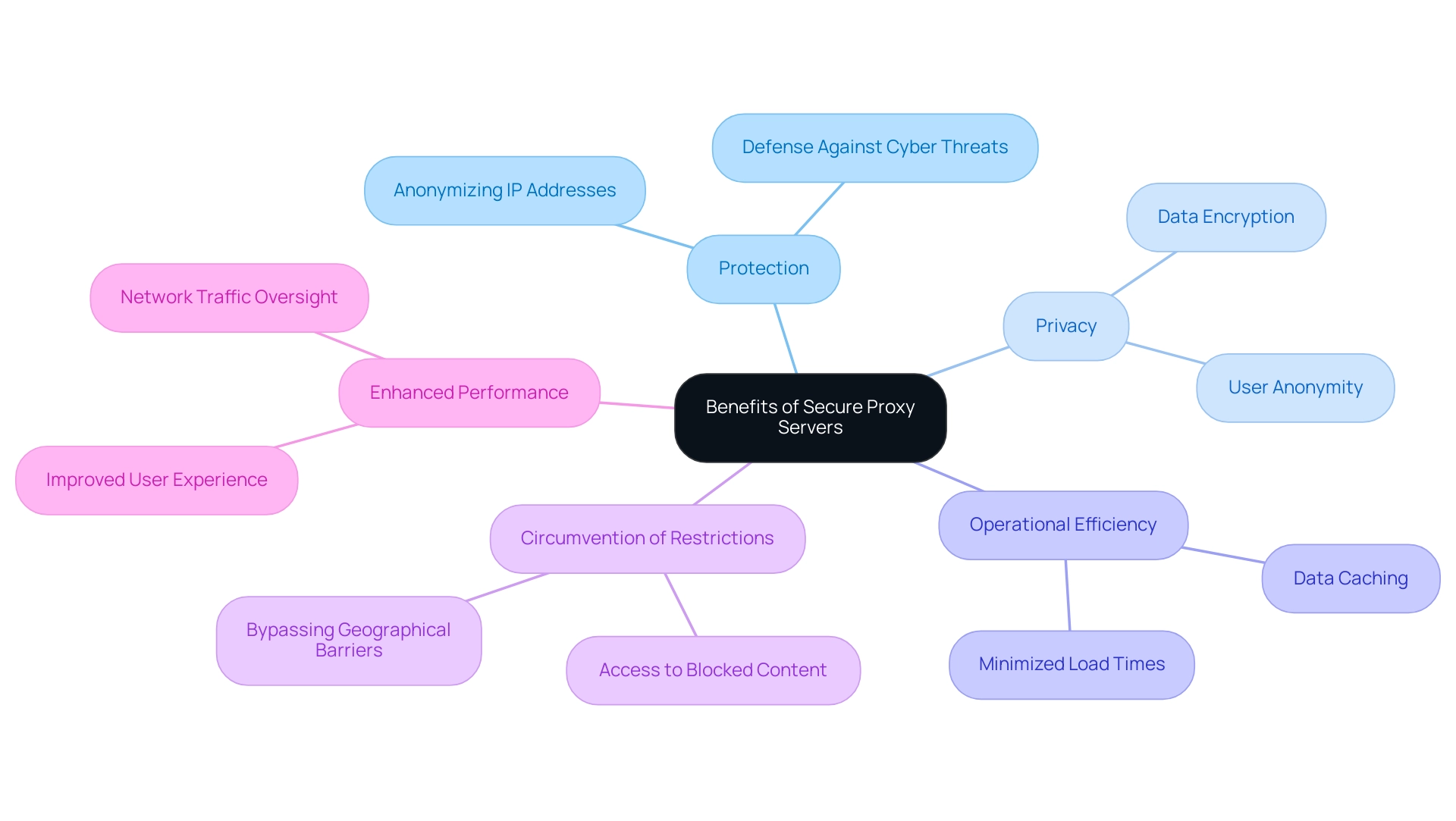
The implementation of a secure proxy server provides numerous benefits, especially in the areas of protection, privacy, and operational efficiency. By anonymizing individual IP addresses, a secure proxy server serves as a formidable defense against cyber threats, including hacking attempts and data breaches, effectively safeguarding sensitive information. However, it is essential to acknowledge that while intermediaries improve protection, they should not be the only dependence in a company's defense framework.
Additionally, these servers function as a secure proxy server, enabling individuals to circumvent geographical restrictions and granting access to content that may be otherwise blocked in certain locales. Beyond security and accessibility, a secure proxy server significantly enhances performance through data caching, which minimizes load times and contributes to a smoother user experience. As advancements in software-defined networking (SDN) progress alongside intent-based networking and integration with emerging technologies like 5G, organizations utilizing a secure proxy server can anticipate enhanced oversight over their network traffic.
A case study on Webshare Customer Support illustrates this point, showing that organizations utilizing a secure proxy server gain enhanced monitoring and management of data flows, fostering a more secure and efficient operational environment.
Exploring Different Types of Proxy Servers
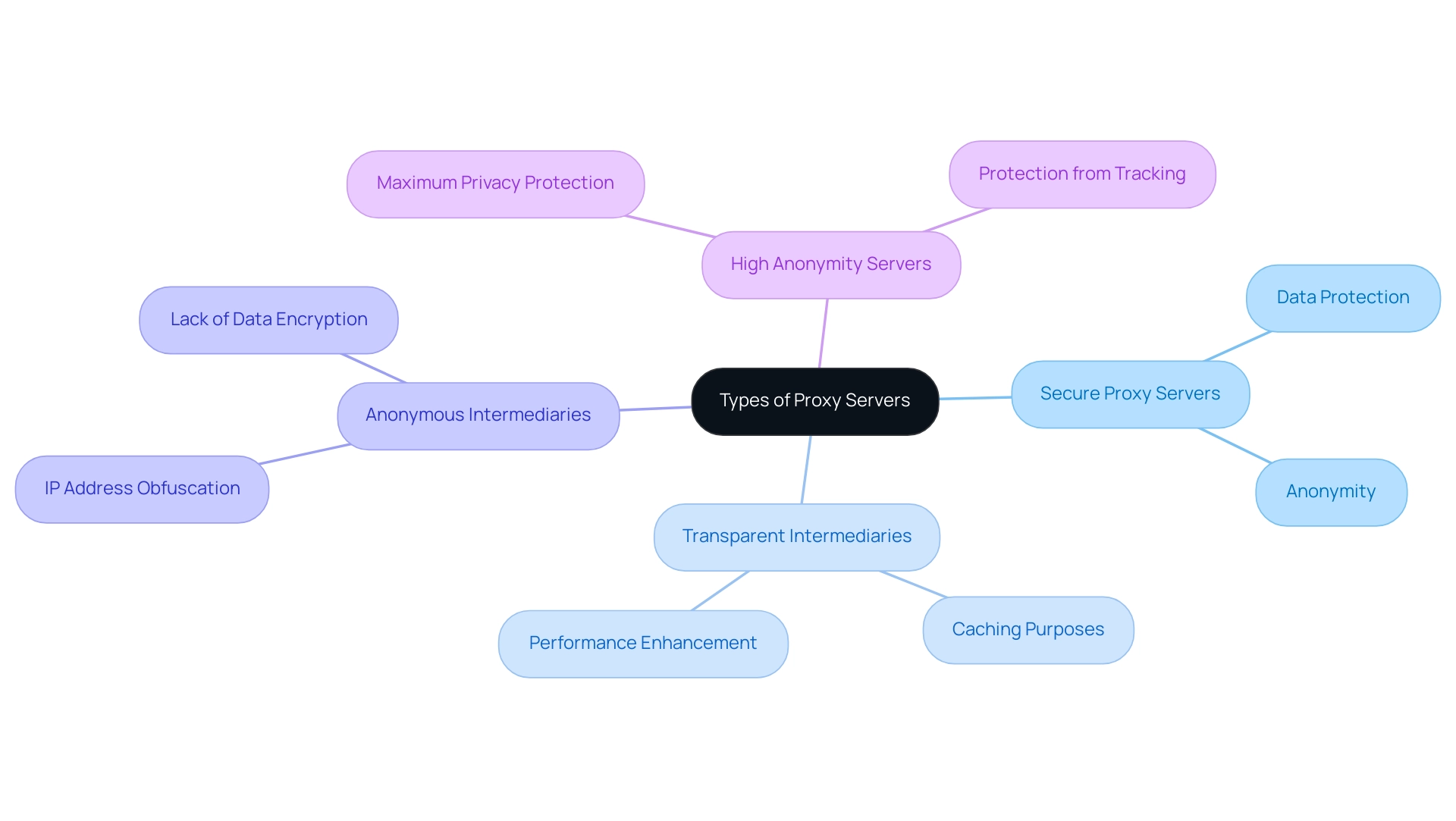
Proxy systems are categorized into several distinct types, each tailored to fulfill specific objectives within cybersecurity frameworks. Secure proxy servers serve as intermediary servers that prioritize data protection and individual anonymity, making them essential for organizations that handle sensitive information. In contrast, transparent intermediaries serve primarily for caching purposes without altering requests, thus enhancing system performance.
Anonymous intermediaries are designed to obscure user IP addresses; however, they may lack data encryption, which can leave users vulnerable. High anonymity servers elevate privacy standards further, providing maximum protection from tracking. The choice of the suitable intermediary type is essential for organizations, as it directly affects overall protection, system performance, and access to content.
As the Server Market is projected to grow at a CAGR of 7.03% from 2024 to 2031, understanding these distinctions will empower decision-makers to align their solutions with their specific operational needs and security requirements. According to the Research Methodology for Proxy Server Market Report by Verified Market Research, rigorous methodologies ensure reliable insights and market segmentation, which are essential for making informed decisions in this growing market. Jane Smith, CFO, mentions, 'We anticipate significant growth next quarter,' emphasizing the importance of choosing the appropriate representative type as organizations prepare for this expansion.
How Secure Proxy Servers Operate
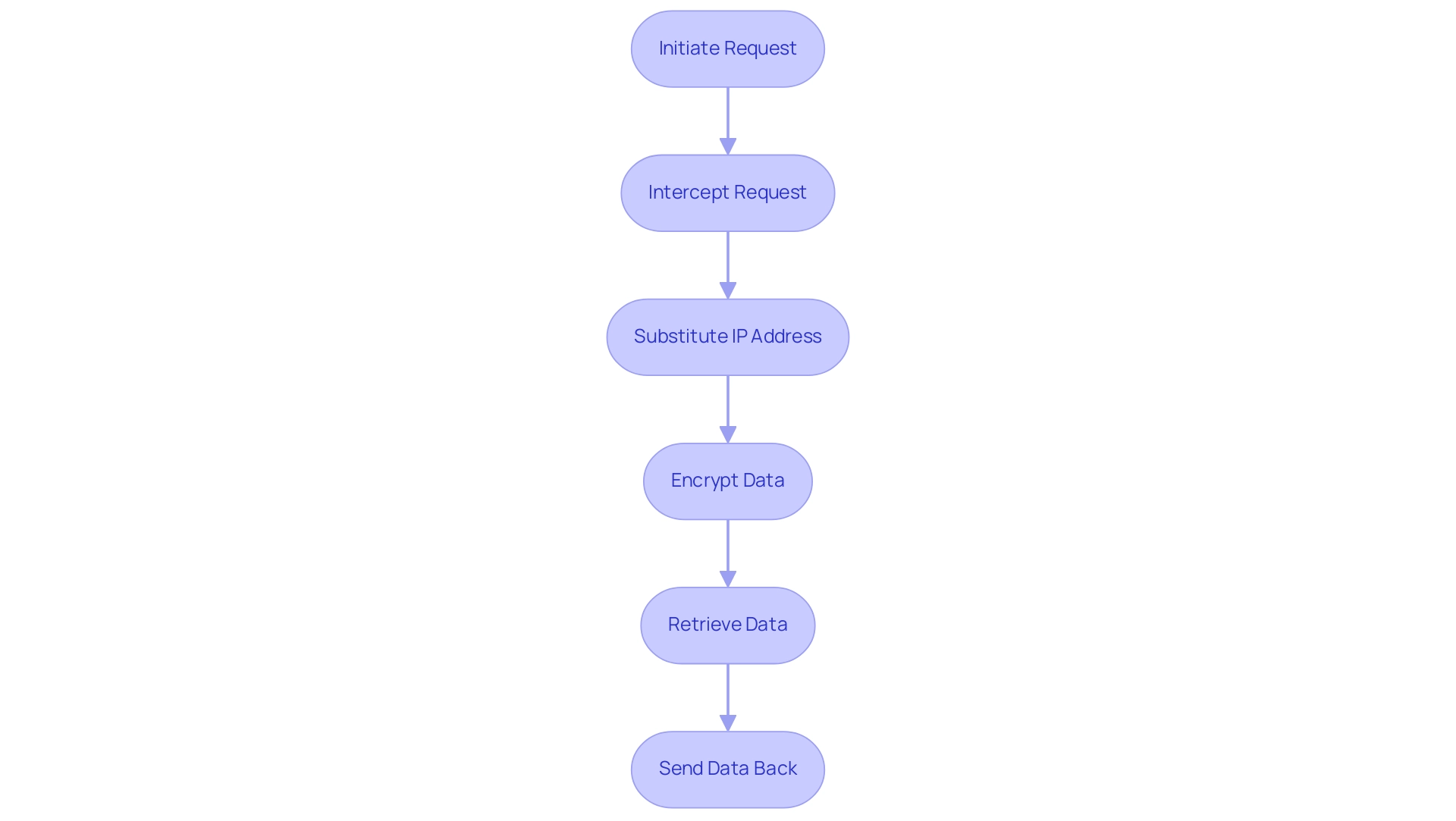
Secure proxy servers operate by seamlessly intercepting individual requests and relaying them to their intended destinations while ensuring that data remains encrypted during transit. Upon initiating a request, the secure proxy server effectively substitutes the individual's IP address with its own, thereby safeguarding the person's identity. This process not only enhances privacy but also fortifies security by utilizing a secure proxy server to protect sensitive data from potential eavesdroppers.
When the requested data is retrieved, it is sent back to the individual through the same secure channel, ensuring integrity throughout the exchange. Notably, protocols such as HTTPS play a critical role in maintaining encryption during the transaction, further shielding the data from interception. Recent advancements in encryption techniques have significantly enhanced the effectiveness of secure intermediaries, with statistics for 2024 indicating a marked increase in their use for protecting user data.
This trend is further underscored by the competitive landscape, as exemplified by Oxylabs cutting prices by 53% to 59%, making these services more accessible. A real-world example of this can be observed with Webshare, which has gained popularity among individuals and SMBs for its affordable and flexible solutions, ultimately being acquired by Oxylabs in 2022. In addition to these core functionalities, secure proxy servers can implement supplementary security measures, including content filtering and the blocking of malicious websites, to enhance overall cybersecurity.
However, challenges persist in the industry; as pointed out by PacketStream, 'PacketStream, in contrast, could hardly open Google, and it was entirely unsuccessful with the social media network,' emphasizing the reliability issues that certain service providers encounter. This multifaceted approach exemplifies the vital role that a secure proxy server plays in contemporary data protection strategies.
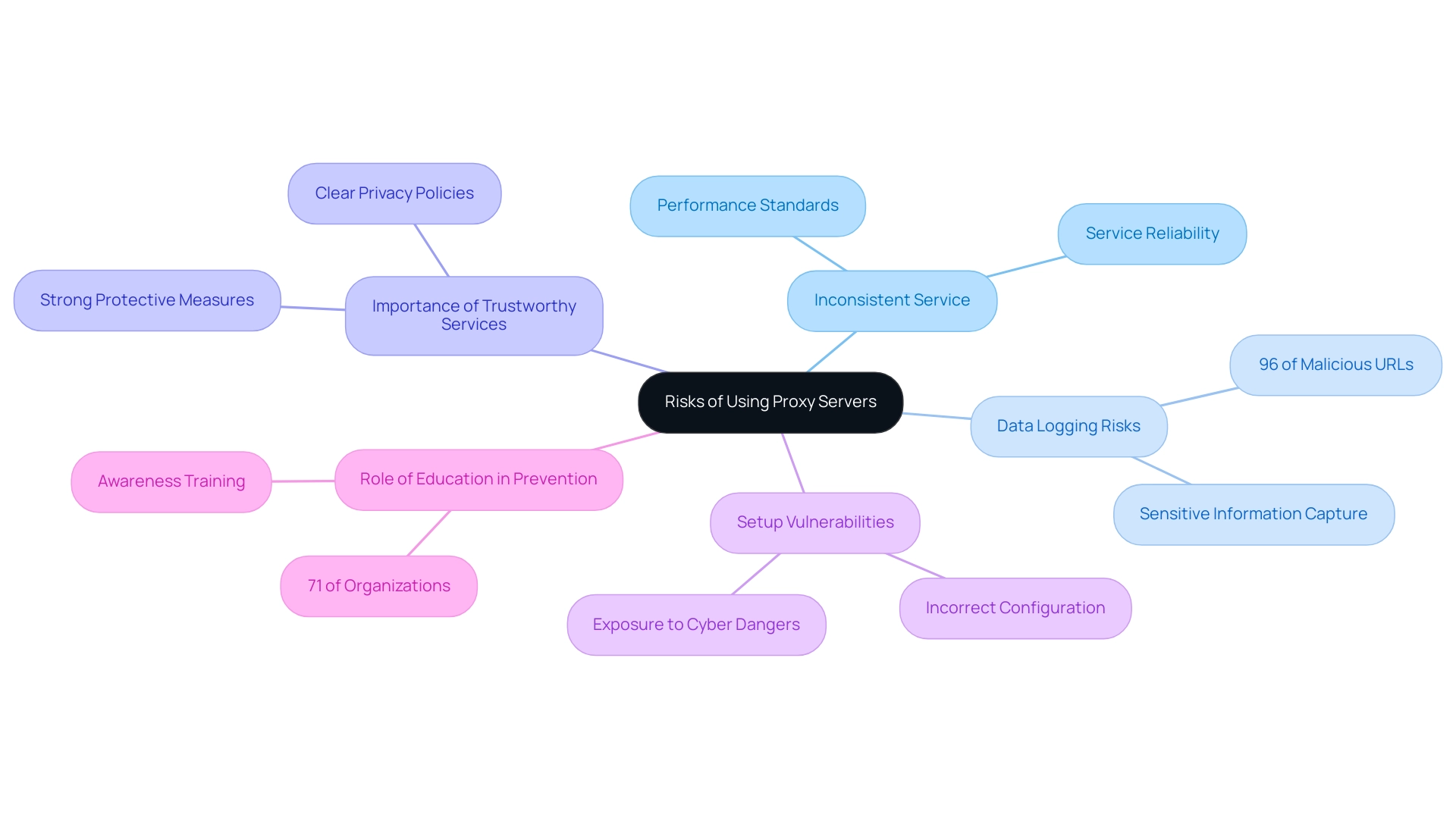
Understanding the Risks of Using Proxy Servers
While a secure proxy server offers significant benefits in improving online protection and privacy, it is not without risks. Users may encounter difficulties like inconsistent service, where certain intermediaries fail to provide the promised protection and performance standards. A significant concern is the potential for data logging by intermediary providers; with over 96% of malicious URLs utilizing obfuscation techniques, the risk of sensitive information being captured is elevated.
As a result, it is essential for individuals to choose trustworthy intermediary services that emphasize strong protective measures and uphold clear privacy policies. Furthermore, incorrect setup of intermediary systems can unintentionally introduce weaknesses, leaving users exposed to cyber dangers instead of protecting them. As the landscape of cybersecurity evolves, software-defined networking (SDN) is anticipated to play a vital role in improving the protection of intermediary servers, particularly with advancements in intent-based networking and network slicing.
To mitigate the risks related to intermediary usage, thorough research and due diligence are essential when choosing a secure proxy server as a solution. Organizations should also consider implementing effective awareness training, as 71% of those that faced data breaches indicated that enhanced training could have prevented such incidents. This emphasizes the importance of providing staff with the knowledge to identify and react to cyber threats, thus strengthening overall security when using intermediary services.
Furthermore, as sponsored name placement services focus on wealth management firms, understanding the implications of proxy server risks in this context becomes increasingly relevant.
Conclusion
The exploration of secure proxy servers reveals their indispensable role in enhancing cybersecurity and protecting sensitive information in the digital landscape. By acting as intermediaries that conceal user identities and encrypt data transmissions, secure proxies significantly mitigate the risks associated with online activities. Organizations that adopt these sophisticated tools not only bolster their defenses against cyber threats but also gain access to content previously restricted by geographical boundaries, thereby improving operational efficiency.
Understanding the different types of proxy servers is crucial for organizations aiming to align their cybersecurity strategies with their operational needs. Each proxy type offers unique benefits and limitations, making informed selection essential to maximize security and performance. As the market for proxy servers continues to grow, organizations must remain vigilant in choosing reliable providers that uphold stringent security measures and transparent privacy policies.
While secure proxy servers present numerous advantages, it is equally important to acknowledge the potential risks involved. Challenges such as unreliable service, data logging by proxy providers, and improper configurations can undermine the very protections these tools are designed to offer. Therefore, thorough research and due diligence are paramount when selecting secure proxy solutions. Additionally, implementing security awareness training for personnel can further fortify defenses against cyber threats.
In conclusion, secure proxy servers serve as vital components in modern cybersecurity frameworks, empowering organizations to navigate the complexities of the digital age with enhanced privacy and security. By leveraging these tools effectively, organizations can safeguard sensitive information, optimize performance, and stay ahead of evolving cyber threats.




