Introduction
In an era where cyber threats are increasingly sophisticated and pervasive, organizations must prioritize robust cybersecurity measures to safeguard their assets.
Managed vulnerability scanning services have emerged as a vital component of this strategy, systematically identifying and addressing potential weaknesses within IT infrastructures.
By leveraging advanced technologies and methodologies, these services not only enhance security posture but also align with broader business objectives, enabling organizations to navigate the complexities of the digital landscape effectively.
As the market for vulnerability scanning tools continues to expand, understanding the nuances of these services becomes imperative for organizations seeking to fortify their defenses against evolving threats.
With a focus on compliance, proactive threat management, and the integration of emerging technologies, the future of managed vulnerability scanning promises to be both dynamic and essential for maintaining resilience in the face of relentless cyber challenges.
Understanding Managed Vulnerability Scanning Services
Managed vulnerability scanning services are a crucial component of a strong cybersecurity plan, systematically designed to identify, evaluate, and prioritize weaknesses within a company's IT infrastructure. Managed vulnerability scanning services, typically delivered by specialized third-party providers, employ advanced tools and methodologies to conduct regular scans, ensuring that potential weaknesses are uncovered before they can be exploited by cybercriminals. The worldwide security scanning tools market, anticipated to expand at an impressive rate of 11.1% from 2024 to 2030, highlights the growing dependence on such services.
This proactive stance not only fortifies a company's security posture but also aligns seamlessly with broader business objectives. As entities traverse the changing terrain of cyber threats, prioritizing effective risk assessment becomes essential. For instance, the Software Bill of Materials (SBOM) is crucial for understanding the components within software and hardware, as seen in the Log4j incident, highlighting the importance of maintaining an accurate inventory of software components.
Additionally, organizations should prioritize:
- Patching based on potential impact
- Focusing on cloud security
- Implementing network segmentation to enhance their defense strategies
According to industry experts,
All things considered; it is anticipated that the long-term trend of growing cyberthreats will keep driving market expansion.
Moreover, key participants in the market, such as Acunetix, BeyondTrust, IBM, and McAfee, are essential in influencing the environment of managed threat assessment services.
Thus, adopting managed vulnerability scanning services is not just a recommended approach; it is crucial for sustaining resilience against new threats.
Key Benefits of Implementing Managed Vulnerability Scanning
Implementing managed risk assessment offers numerous advantages, especially in reducing dangers linked to cybersecurity threats. By enabling early identification of weaknesses, this proactive strategy significantly decreases the likelihood of data breaches and cyberattacks. A staggering statistic reveals that 4 out of 5 small businesses report malware has evaded their antivirus solutions, underscoring the critical need for vigilant monitoring.
Additionally, 81% of companies report that malware has successfully infected their endpoints, further highlighting the necessity of proactive measures. These services are crucial in assisting entities adhere to strict regulations, such as GDPR and HIPAA, by ensuring that protective protocols are not only established but also routinely updated. The current landscape of cybersecurity regulations necessitates robust compliance measures, as evidenced by the evolving requirements.
Ongoing monitoring facilitated by managed vulnerability scanning services allows entities to address weaknesses before they can be exploited, thus improving overall protective stance. This proactive threat management fosters trust among stakeholders and clients, reinforcing the entity's commitment to safeguarding sensitive information. Moreover, the increasing expenditure on protective measures, as shown by the case study on blockchain technology expansion, illustrates that companies acknowledge the significance of strong cybersecurity strategies.
Ultimately, the implementation of managed vulnerability scanning services not only strengthens defenses but also aligns with best practices for data breach reduction, positioning the organization as a leader in cybersecurity resilience.
Technologies and Methodologies Behind Vulnerability Scanning
Managed risk assessment utilizes a diverse range of technologies and methodologies to effectively identify security weaknesses. Central to these efforts are automated scanning tools that assess systems against established databases, such as the Common Vulnerabilities and Exposures (CVE). This approach ensures that entities are alerted to known vulnerabilities in a timely manner.
Methodologies generally follow established frameworks, including:
- The Open Web Application Application Project (OWASP) for web applications
- The National Institute of Standards and Technology (NIST) guidelines for wider practices
These structured methodologies ensure that scans are both thorough and methodical, providing actionable insights into a firm's protective stance. Furthermore, ongoing supervision and regular evaluations are crucial elements of managed vulnerability scanning services, allowing entities to react quickly to new threats as they emerge.
The rising prevalence of remote work has further highlighted the need for strong risk management; as noted by Malwarebytes, remote employees have caused a security breach in 20 percent of firms during the pandemic, illustrating the essential nature of proactive risk management strategies. Furthermore, 31% of Chief Information Security Officers (CISOs) indicate that projects have been postponed or eliminated because of insufficient funding, emphasizing the difficulties organizations encounter in executing effective risk management. Moreover, the rise in cyber insurance premiums, which grew by 50% in 2022, indicates the increasing financial strain of cyber threats, emphasizing the need for proactive risk management strategies.
Vulnerability Scanning vs. Other Security Measures
Managed vulnerability scanning services are a crucial component of a thorough cybersecurity strategy, yet they represent merely one aspect of a multi-layered defense approach. Penetration testing serves a supplementary function by mimicking real-world assaults to evaluate the efficacy of protective measures, while weakness scanning mainly detects recognized flaws within systems. Endpoint protection and network safeguards, including firewalls and intrusion detection systems, are critical for mitigating risks uncovered during managed vulnerability scanning services.
The significance of this layered protective strategy cannot be overstated, as it allows organizations to integrate various protective measures effectively. This holistic strategy not only improves the overall defense posture but also ensures that potential threats are addressed from multiple angles, thus providing a robust safeguard against evolving cyber threats. As mentioned by Abby Ross, Associate Partner at X-Force Red, "If they are unintentionally misled into purchasing the incorrect solution for their environment, a critical unknown weakness exposing a high-value asset could be overlooked."
Therefore, a thorough understanding of the distinctions between security scanning and penetration testing, along with managed vulnerability scanning services and an emphasis on layered security measures, is vital for any organization aiming to protect its assets against malicious attacks. Furthermore, the risk management market is projected to grow from USD 6.7 billion in 2020 to USD 15.86 billion by 2030, indicating the increasing importance of effective risk management strategies. This is emphasized by the situation of Microsoft weaknesses, where critical flaws like ProxyLogon and ProxyShell remain significant attack vectors, highlighting the ongoing risks associated with widely used software and the importance of timely remediation.
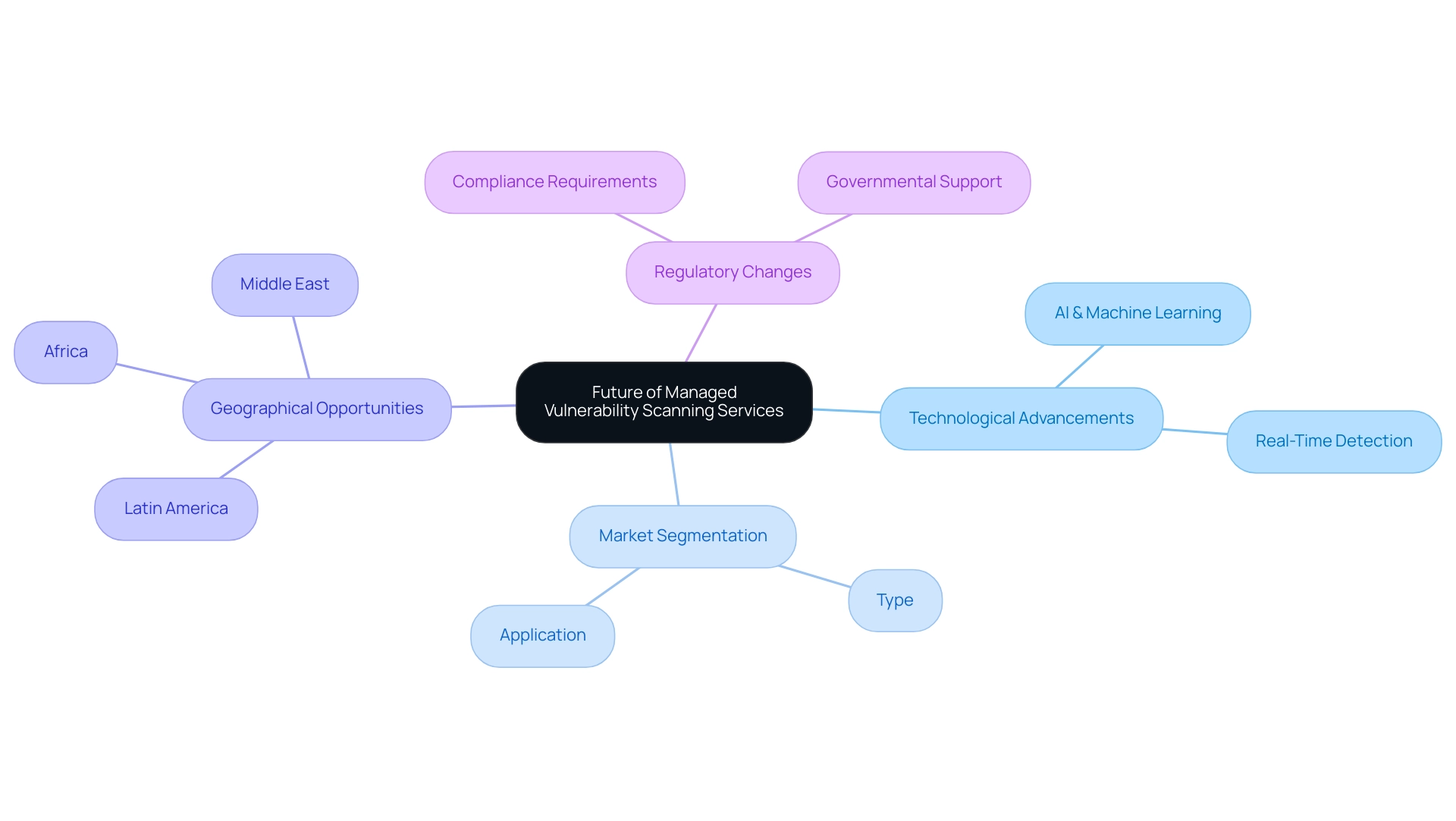
The Future of Managed Vulnerability Scanning Services
The landscape of managed vulnerability scanning services is on the brink of substantial transformation, fueled by rapid technological advancements and the escalating complexity of cyber threats. A notable trend is the integration of artificial intelligence and machine learning, which significantly enhances the accuracy and efficiency of flaw detection. These technologies enable organizations to detect weaknesses in real-time, thereby minimizing potential risks.
As cloud computing and IoT devices gain traction, vulnerability assessments will need to evolve to address the distinct challenges these technologies introduce. Regulatory transformations will further intensify the demand for managed vulnerability scanning services that are more robust and align with shifting compliance requirements. The market is segmented based on type, application, and geography, offering tailored solutions that cater to diverse organizational needs.
Notably, emerging economies in Latin America, Africa, and the Middle East present untapped potential for the Vulnerability Scan Service market, supported by increasing investments and governmental support. According to Jason Fitch, founder and CEO of PurpleSec,
Organizations that embrace these advancements will not only fortify their security posture but will also gain a competitive edge in the digital arena.
Staying ahead of these trends is essential for organizations aiming to safeguard their assets in an increasingly volatile cyber environment.
The future scope of the vulnerability scan service market indicates significant growth potential, driven by innovation in product offerings and a shift towards sustainable solutions, which are expected to shape the market's expansion.
Conclusion
Managed vulnerability scanning services are crucial for organizations aiming to enhance their cybersecurity posture in an environment rife with evolving threats. By systematically identifying and prioritizing vulnerabilities within IT infrastructures, these services enable organizations to mitigate risks effectively and comply with stringent regulatory requirements. The proactive approach offered by managed vulnerability scanning not only reduces the likelihood of data breaches but also fosters trust among stakeholders by demonstrating a commitment to safeguarding sensitive information.
The integration of advanced technologies such as artificial intelligence and machine learning promises to revolutionize the vulnerability scanning landscape, allowing for real-time detection and response to threats. As organizations increasingly adopt these innovative solutions, they position themselves to navigate the complexities of modern cyber risks more effectively. Furthermore, the growing importance of a layered security approach highlights the need for organizations to complement managed vulnerability scanning with other protective measures, such as:
- Penetration testing
- Endpoint protection
In conclusion, embracing managed vulnerability scanning is no longer a mere best practice; it is a fundamental necessity for organizations striving to maintain resilience against the relentless tide of cyber threats. By investing in these services, organizations not only bolster their defenses but also align their cybersecurity strategies with broader business objectives, ensuring they remain competitive in an ever-changing digital landscape. The future of managed vulnerability scanning is promising, and organizations that prioritize these services will be well-equipped to face the challenges of tomorrow.




