Introduction
In today's rapidly evolving digital landscape, the management of information technology resources has become a cornerstone of organizational success. Central to this management are IT policies and procedures, meticulously crafted guidelines that establish clear expectations and responsibilities regarding technology usage, data management, security protocols, and compliance with relevant laws and regulations. These policies not only align IT processes with business objectives but also play a pivotal role in risk mitigation and enhancing operational efficiency.
The advent of regulations such as the General Data Protection Regulation (GDPR) underscores the necessity of transparent and enforceable IT policies. For example, GDPR mandates explicit consent for data collection and processing, and grants EU citizens the 'Right to be Forgotten,' ensuring their data can be deleted upon request. Such regulations highlight the importance of robust IT governance frameworks that encompass risk assessment and management, ensuring that data protection, access controls, encryption, and incident response policies are thoroughly communicated and consistently applied.
Investment in IT is another critical aspect, with global spending on technology reaching into the trillions. This investment drives value creation and competitive advantage, making it essential for organizations to stay ahead of regulatory changes and adopt innovative solutions for data resilience and security. Effective IT policies and procedures provide the foundation for this, ensuring that technological resources are utilized efficiently and securely, aligned with both business goals and regulatory requirements.
What Are IT Policies and Procedures?
IT rules and procedures are crucial elements that direct how entities handle their information technology resources. 'These formalized guidelines delineate clear expectations and responsibilities concerning technology usage, information management, security protocols, and compliance with pertinent laws and regulations.'. By establishing a robust policy framework, organizations can ensure that IT processes are not only aligned with business objectives but also capable of mitigating risks and enhancing operational efficiency.
For instance, under the General Data Protection Regulation (GDPR), companies are mandated to obtain explicit consent before collecting, processing, or storing an individual's information, demonstrating the importance of transparent terms and conditions. Additionally, the GDPR's 'Right to be Forgotten' allows EU citizens to request the deletion of their data, ensuring that companies cease further dissemination and halt third-party data processing.
Moreover, IT governance includes extensive frameworks for evaluation and management of uncertainties. This proactive approach involves identifying risks, understanding their potential impact, and prioritizing mitigation steps, thereby providing a solid foundation for the entity's IT environment. Effective governance ensures that policies related to data protection, access controls, encryption, incident response, and regulatory adherence are clearly communicated and consistently enforced across the company.
'The importance of IT budgets and investments cannot be overstated, as they are crucial to the success of businesses worldwide.'. As digital transformation accelerates, the global spending of businesses and governments on tech goods and services has become a trillion-dollar industry. This investment in technology is crucial for value creation and maintaining a competitive edge in various sectors.
Moreover, the compliance landscape is continuously evolving, presenting new challenges for entities. A study by Cloudera revealed that 66% of IT decision-makers believe information is spiraling out of control within their enterprises, highlighting the complexity of managing multiple point solutions and the associated information integration tax. Therefore, it is imperative for entities to stay ahead of regulatory changes and adopt innovative solutions to enhance data resilience and security.
In summary, IT guidelines and procedures are essential for ensuring that a company's technology aligns with business objectives, mitigates risks, and enhances operational efficiency. By adhering to comprehensive guidelines and maintaining a proactive approach to governance and compliance, organizations can navigate the dynamic landscape of information technology with confidence and control.
Why Are IT Policies Important?
IT regulations play a crucial role in safeguarding organizational assets and maintaining data integrity. They provide a structured framework for decision-making, standardizing procedures, and ensuring accountability. By clearly defining roles and responsibilities, IT guidelines significantly reduce the risk of security breaches, enhance compliance with legal requirements, and foster a culture of responsibility towards information management.
'According to a study by Kaspersky, breaches of information security guidelines by employees are among the most significant challenges faced by companies, highlighting the importance of well-defined IT protocols.'. Furthermore, adhering to comprehensive compliance and regulatory measures not only ensures legal and ethical conduct but also positions entities for success in a rapidly evolving global landscape.
Effective IT policies also guide the development and maintenance of programs that safeguard information assets. This is vital as the loss of information can severely impact an organization's investment in personnel, time, finances, and property. Organizations must prioritize information categorization to comprehend the worth of their information and manage uncertainties effectively. As Pirzada points out, a strong data classification framework offers a clear route to secure data usage, storage, and transactions, which is crucial for informed decision-making and risk management.
Key Types of IT Policies
IT policies can be categorized into several key types, each playing a crucial role in safeguarding an organization's information assets and ensuring smooth operations:
-
IT Asset Management Policies: These guidelines are essential for tracking and managing IT assets throughout their lifecycle. Categorizing assets into consumable (e.g., printer toner) and non-consumable (e.g., software licenses) helps optimize usage, minimize costs, and maintain operational efficiency.
-
IT Software Management Policies: These rules govern the acquisition, deployment, and maintenance of software applications. Effective management ensures compliance with licensing agreements and enhances overall efficiency. As companies progressively utilize cloud services, revising these guidelines becomes essential.
-
IT Security Policies: Protocols designed to protect sensitive information and IT infrastructure from unauthorized access and cyber threats. Establishing a strong information categorization policy is essential, as it assists entities in reducing threats and overseeing information governance efficiently. According to Pirzada, “Without good, consistent classification of data, organizations are unable to answer important questions like what their data is worth, how they mitigate risks to their data, and how they effectively monitor and manage its governance.”
-
IT Emergency Response Policies: These procedures address IT emergencies, such as data breaches and system failures, ensuring business continuity. As numerous individuals keep working from distant sites, having an effective remote access guideline is becoming more vital to uphold security and operational integrity.
-
IT Employment Guidelines: Standards related to employee conduct regarding IT resources, including acceptable use regulations. These guidelines assist in managing the risks related to employee interactions with IT systems and ensure that IT resources are utilized properly.
To sustain a competitive advantage and safeguard their investments, entities must create and uphold these IT guidelines, taking into account their strategic and financial implications. As Vladimir Kroa, Associate Vice President at IDC, notes, “Sustainability regulations are not just rules to follow; they are pathways to innovation, efficiency, and long-term prosperity for businesses.”
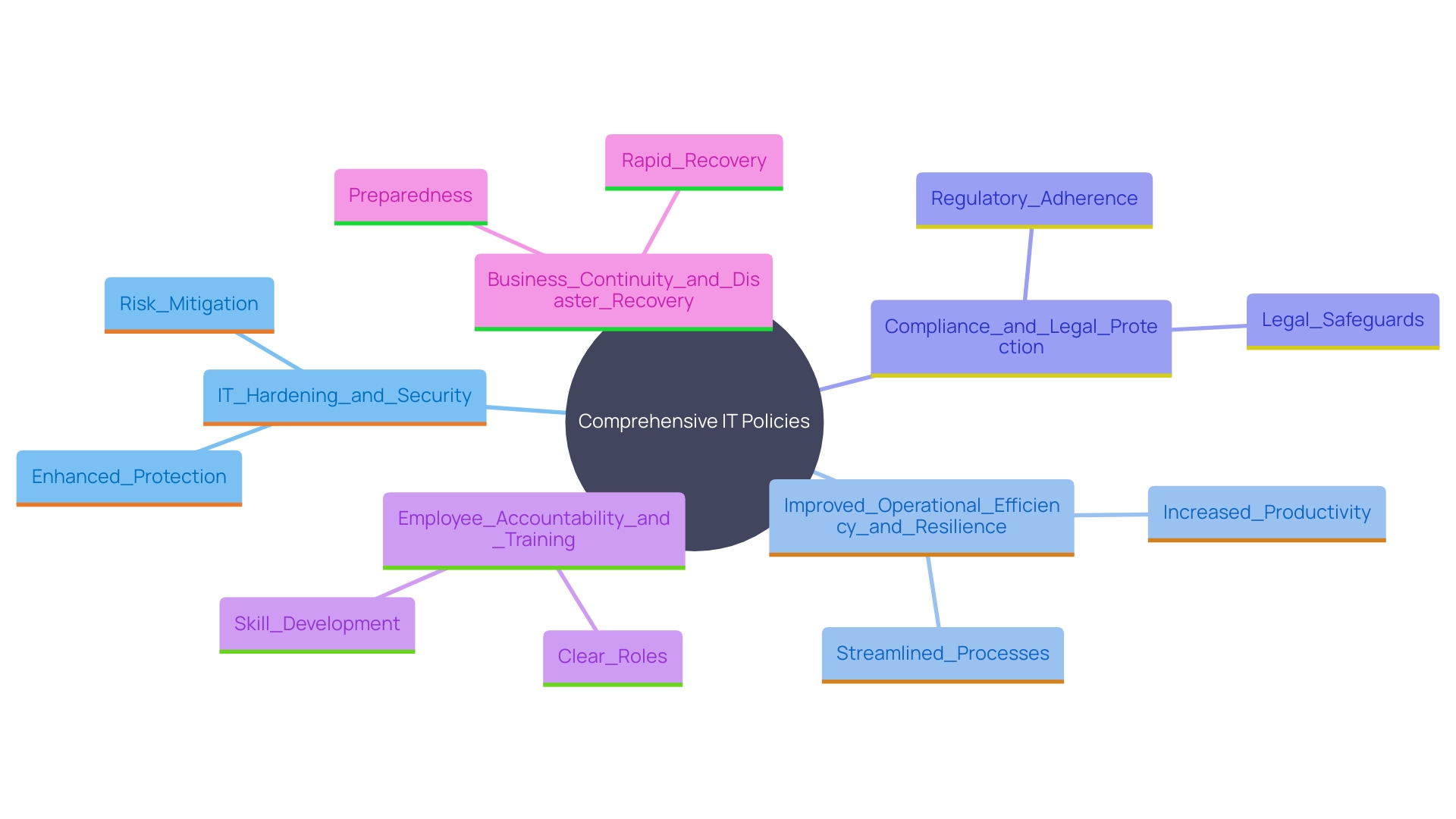
Benefits of Implementing IT Policies
Implementing comprehensive IT policies offers numerous benefits that are crucial for modern businesses and government institutions:
-
IT Hardening and Security: Strengthening the organization’s defenses against cyber threats through strict security protocols. This includes leveraging advanced threat management strategies and regularly updating security measures to combat evolving cyber risks. The recent sweeping executive order on artificial intelligence by President Biden highlights the emphasis on safety and privacy, requiring companies to notify the federal government about high-risk AI models and share safety test results.
-
Improved Operational Efficiency and Resilience: Streamlining IT processes, which leads to enhanced productivity and reduced downtime. Veeam, a leader in data resilience, exemplifies this by offering solutions that ensure data security, backup, and recovery, thus maintaining operational continuity across various environments. This radical resilience is vital for entities to bounce back swiftly after disruptions.
-
Compliance and Legal Protection: Ensuring adherence to industry regulations and legal standards, thereby safeguarding the entity from potential penalties. Amidst global political movements and rapid technological advancements, staying compliant with regulations, such as those governing AI applications, is essential to safeguard institutional integrity and avoid legal repercussions.
-
Employee Accountability and Training: Fostering a culture of responsibility and providing necessary training to employees on IT practices. Training programs assist employees in comprehending and reducing potential issues, ensuring that they are well-prepared to tackle IT challenges. This is particularly important as new technologies emerge, requiring continuous education and awareness.
-
Business Continuity and Disaster Recovery: Establishing plans and procedures that ensure the entity can recover swiftly from disruptions. Successful business continuity management includes comprehensive evaluations of potential threats and the creation of strong recovery plans. Insights from business impact analysis assist entities in recognizing and reducing unacceptable risks, ensuring readiness for various scenarios.
These benefits highlight the significance of thorough IT guidelines in maneuvering through the intricate terrain of contemporary technology, regulatory requirements, and operational demands.
Best Practices for Writing and Reviewing IT Policies
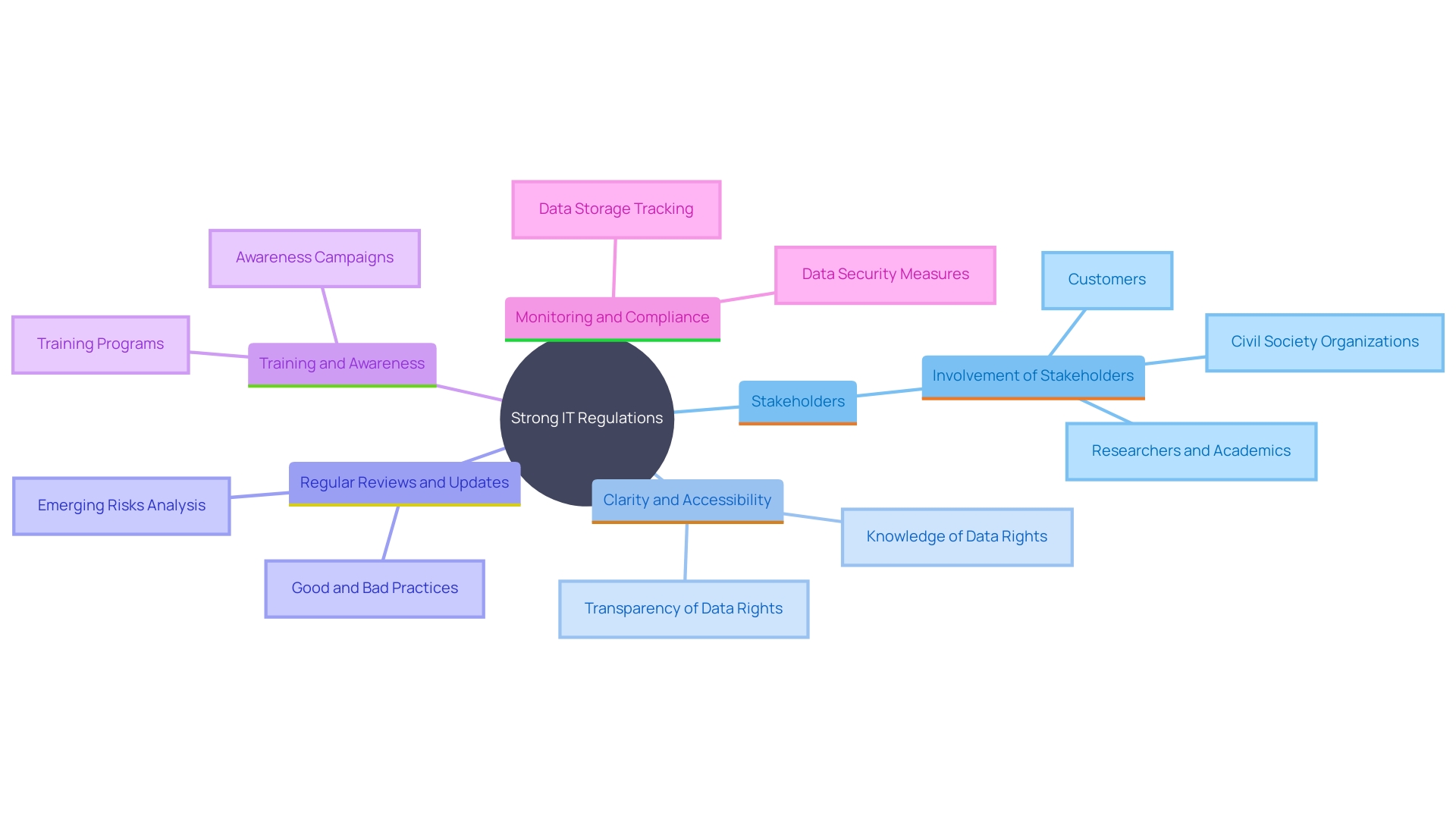
To create strong IT regulations, organizations should follow best practices that guarantee thorough, clear, and compliant guidelines.
-
Involvement of Stakeholders: Engage representatives from various departments to ensure the guidelines are well-rounded and have widespread support. This collaborative approach not only meets various departmental needs but also encourages a sense of ownership and dedication to the guidelines.
-
Clarity and Accessibility: Policies must be straightforward, concise, and readily accessible to all employees. This ensures that everyone understands their roles and responsibilities, enhancing compliance and reducing confusion. As Pirzada emphasizes, clear guidelines are crucial for making informed choices regarding uncertainties, especially when dealing with sensitive data.
-
Regular Reviews and Updates: With the rapid evolution of technology and business needs, it is essential to review and update guidelines regularly. This proactive approach assists in reducing risks linked to outdated regulations and ensures alignment with current technological advancements and operational requirements.
-
Training and Awareness: Conduct regular training sessions to educate employees on the significance and consequences of these guidelines. This not only reinforces the significance of compliance but also empowers staff to adhere to the guidelines effectively. Training is especially crucial in fields such as classification, as emphasized by Pirzada, to guarantee that employees can handle and safeguard sensitive information properly.
-
Monitoring and Compliance: Establish a robust process for overseeing adherence to guidelines and addressing violations promptly. Effective data governance, as mentioned, involves creating and maintaining guidelines that ensure data security and compliance, which is crucial for the overall integrity and usability of organizational data.
By incorporating these best practices, organizations can create IT policies that are not only effective but also adaptable to the dynamic technological landscape.
Conclusion
Establishing comprehensive IT policies and procedures is essential for organizations aiming to navigate the complexities of the modern digital landscape. These guidelines serve to align technology usage with business objectives, enhance operational efficiency, and mitigate risks associated with data management and security. By adhering to robust frameworks, organizations can ensure compliance with regulatory requirements such as GDPR, which mandates stringent data protection measures.
The significance of well-defined IT policies extends beyond compliance; they foster a culture of accountability and responsibility within organizations. By clearly outlining roles and responsibilities, these policies reduce the likelihood of security breaches and facilitate informed decision-making regarding data management. Additionally, they guide the development of essential programs that safeguard information assets, ultimately protecting the organization’s investment in technology and personnel.
Furthermore, implementing effective IT policies not only strengthens security measures but also streamlines operations, ensuring business continuity in the face of disruptions. The benefits of such policies are manifold, ranging from improved resilience to enhanced employee training and awareness. Regular reviews and updates of these policies are crucial to maintaining their relevance in an ever-evolving technological landscape.
In conclusion, the establishment and adherence to comprehensive IT policies and procedures are paramount for organizations seeking to thrive in today's digital age. By prioritizing these guidelines, organizations can navigate regulatory changes, protect their data, and drive operational success, thereby positioning themselves for sustained growth and innovation.




