Introduction
In an age where cyber threats are increasingly sophisticated and pervasive, organizations must prioritize their cybersecurity strategies to safeguard sensitive information. The CIS Controls, developed by the Center for Internet Security, provide a structured framework of best practices designed to enhance organizational security posture significantly.
With a staggering 97 percent of cyber threats motivated by financial gain, and a notable rise in spear-phishing attacks, understanding and implementing these controls has never been more critical. This article delves into the intricacies of the CIS Controls, offering insights into their essential components, implementation strategies, and comparative advantages over other cybersecurity frameworks.
As organizations navigate the complex landscape of cybersecurity, the CIS Controls emerge as a vital tool for mitigating risks and fortifying defenses against the evolving threat landscape.
Introduction to CIS Controls: Understanding the Framework
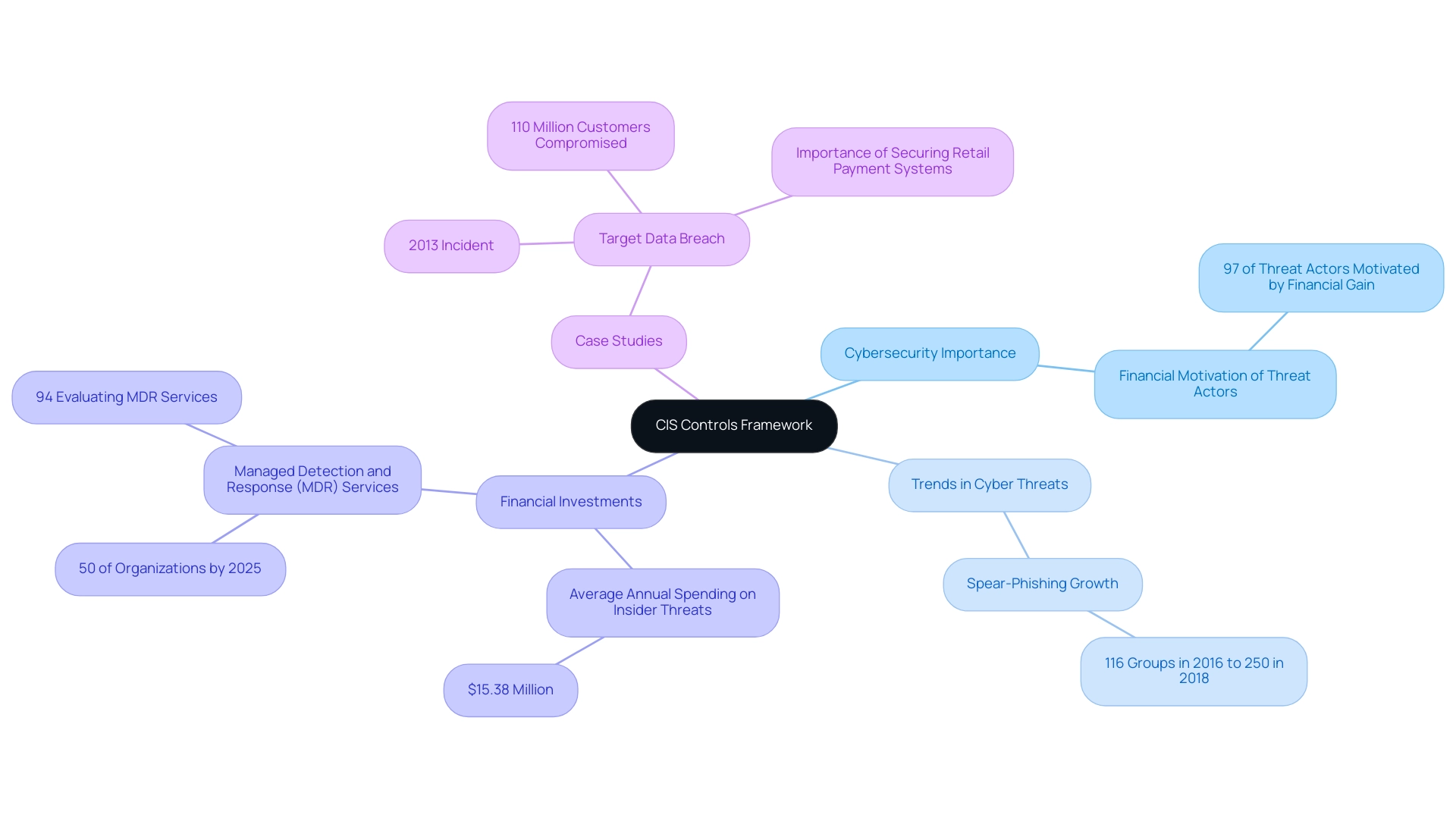
The Center for Internet Security (CIS) developed the CIS Controls as a structured set of best practices aimed at significantly enhancing organizational cybersecurity posture. This framework adopts a prioritized, actionable approach to cybersecurity, enabling entities to implement effective measures to mitigate risks associated with cyber threats. In 2023, a comprehensive data breach investigation report revealed that 97 percent of threat actors were financially motivated, underscoring the critical need for robust security measures.
Notably, the number of known spear-phishing groups grew from 116 in 2016 to over 250 in 2018, highlighting the evolving nature of cyber threats. The CIS guidelines are not only widely acknowledged within the cybersecurity community but also function as a fundamental component for entities attempting to protect their information systems against evolving threats. By addressing prevalent vulnerabilities, the CIS framework controls provide a clear roadmap for cybersecurity initiatives, making their understanding crucial for entities committed to fortifying their defenses.
As entities navigate the complexities of cybersecurity, the implementation of CIS framework controls has become increasingly essential, especially given that entities are currently investing an average of $15.38 million each year to address insider threats. Moreover, with Managed Detection and Response (MDR) services anticipated to be employed by 50% of organizations by 2025, the importance of the CIS framework controls in enabling effective protective measures cannot be overstated. A pertinent example is the Target Data Breach of 2013, where cyber attackers used malware to steal data from Target's point of sale systems, compromising information of approximately 110 million customers.
This incident emphasizes the importance of implementing robust cybersecurity measures, further reinforcing the critical role of the CIS guidelines.
The 18 Critical Security Controls: A Detailed Overview
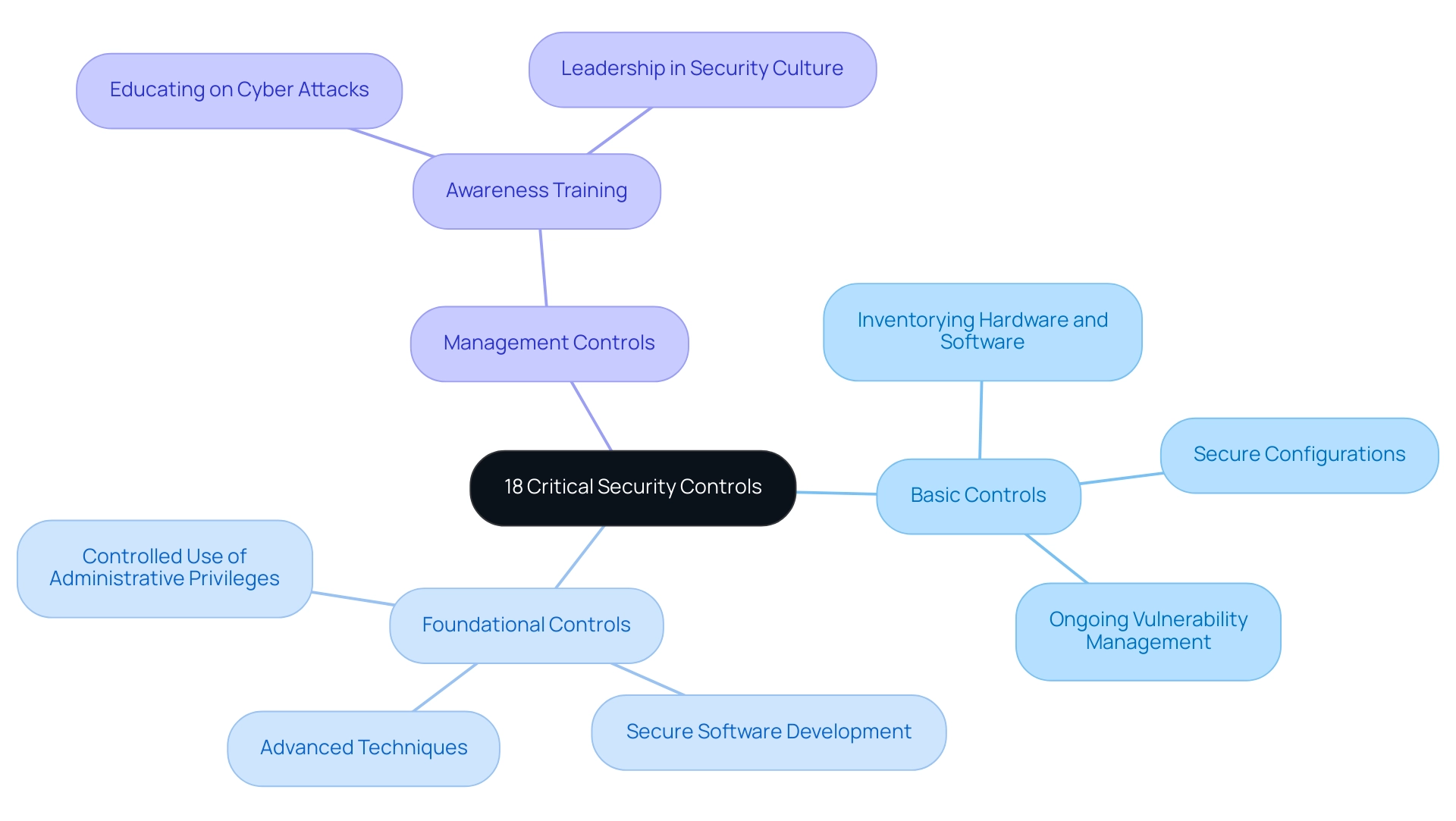
The 18 essential protective measures are encompassed within the CIS framework controls, which are carefully organized into three separate categories: basic, foundational, and organizational. CIS framework controls are crucial for establishing hygiene; they encompass practices such as:
- Thorough inventorying of hardware and software
- Implementing secure configurations
- Maintaining ongoing vulnerability management
These foundational elements establish the groundwork for robust protection.
Moving to the foundational controls, the CIS framework controls include advanced measures that encompass:
- Controlled use of administrative privileges
- Secure software development practices
- Other sophisticated techniques essential for modern cybersecurity
Finally, management controls highlight the importance of awareness training, where staff must be informed about different kinds of cyber attacks, including phishing and phone fraud, with research indicating that entities offering such training can decrease the likelihood of successful attacks by as much as 70%. Eric B. states, "It’s a great way to learn how to lead," emphasizing the crucial role of leadership in fostering a security-aware culture.
Furthermore, the implementation of the CIS framework controls, specifically CIS Control 3: Data Protection, involves developing procedures and technical controls to recognize, classify, manage, store, and dispose of data securely. Organizations that have adopted these practices have seen significant improvements in their ability to protect sensitive data throughout its lifecycle. This holistic implementation is critical, especially in light of recent developments, such as the discovery of a new exploit targeting the NTLM hash mechanism on Windows systems, highlighting the ongoing need for vigilance in cybersecurity practices.
Implementing CIS Controls: Best Practices for Organizations
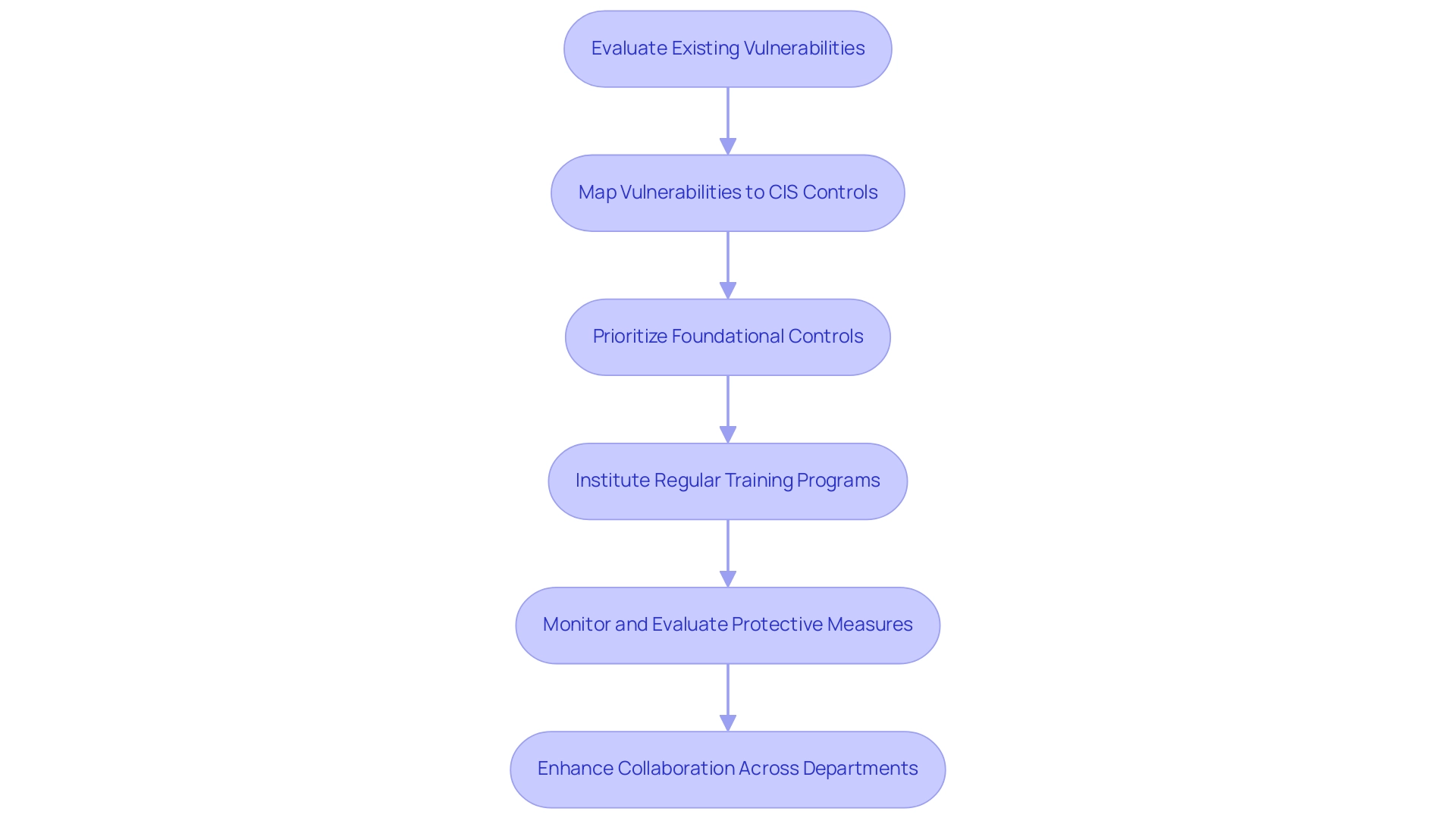
To efficiently execute CIS measures, entities must commence a thorough evaluation of their existing protective stance. This crucial first step involves the identification of existing vulnerabilities, including the recently discovered exploit targeting the NTLM hash mechanism on Windows systems, which poses a significant risk. These vulnerabilities should be systematically mapped to the relevant CIS Controls.
Prioritization is crucial; organizations are advised to start with the foundational controls, establishing a strong framework upon which to build. As Amit Yoran, CEO of Tenable, stated, 'Proactive measures and a strong foundation in protective controls are essential to mitigating risks in today's landscape.' To promote a culture of awareness regarding safety, regular training programs must be instituted, ensuring that all employees are well-informed of their responsibilities in maintaining safety.
Furthermore, continuous monitoring and evaluation of protective measures are necessary to remain agile against emerging threats. Collaborative efforts across various departments, as well as partnerships with external stakeholders, can significantly enhance the effectiveness of the CIS framework controls implementation strategy. For instance, the case study on Extreme Networks-SLX-OS illustrates how entities can tailor recommendations for protection through a CIS SecureSuite Membership, aligning with industry best standards and positioning themselves to respond proactively to the evolving cybersecurity landscape.
CIS Controls vs. Other Frameworks: Making the Right Choice
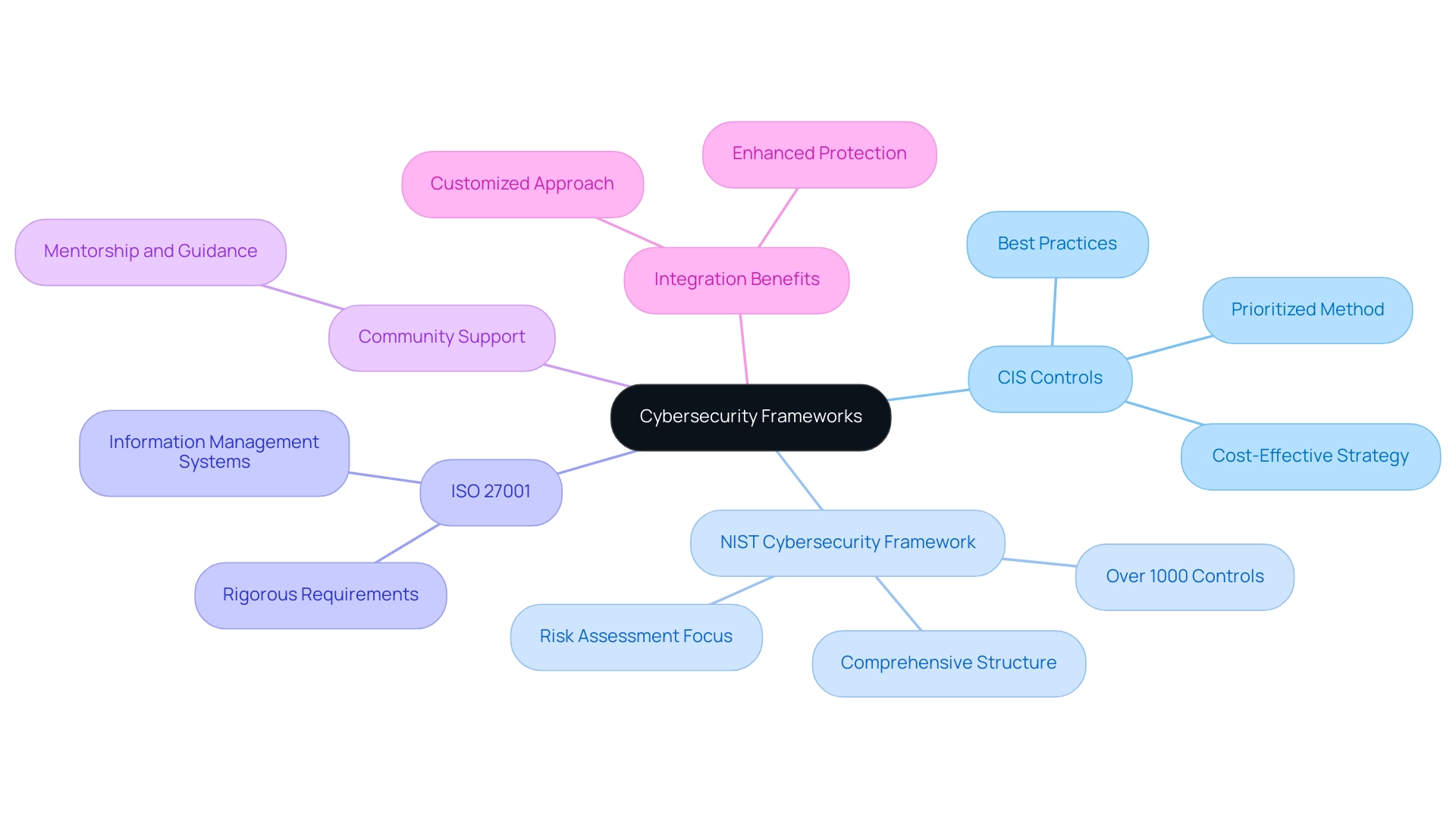
When assessing cybersecurity frameworks like the CIS framework controls, NIST Cybersecurity Framework, and ISO 27001, it is crucial for entities to evaluate their specific needs and regulatory responsibilities. The CIS framework controls provide a prioritized and practical method to cybersecurity that is especially advantageous for entities aiming to improve their protective stance effectively. In contrast, the NIST Cybersecurity Framework, which specifies more than 1000 controls, presents a more comprehensive structure, emphasizing risk assessment and management processes, which can be critical for larger organizations with complex infrastructures.
For entities that must adhere to specific compliance standards, ISO 27001 may offer a more suitable framework due to its rigorous requirements for information management systems. As Ethan6123, a member since 2009, reflects,
'I’m still early into my IT career and I ask questions a lot about stuff I don’t know. Rather than being shamed or ignored, I get helpful people reaching out looking to help in any way they can to help me get to a conclusion.'
This highlights the importance of community support in navigating these frameworks. Organizations can harness the strengths of each CIS framework controls through integration, allowing them to develop a customized approach that effectively addresses their unique protection challenges. Additionally, NIST's significant influence on cybersecurity standards, especially in comparison to its competitors like CIS and ISO, underscores its importance for infrastructure firms and the private sector.
As demonstrated by the case study on the Center for Internet Protection, when the CIS framework controls are applied effectively, they provide an economical approach that significantly improves overall protection measures. This customized method not only enhances protection but also aligns with the wider goals of the entity, making it a strategic selection in the changing environment of cybersecurity.
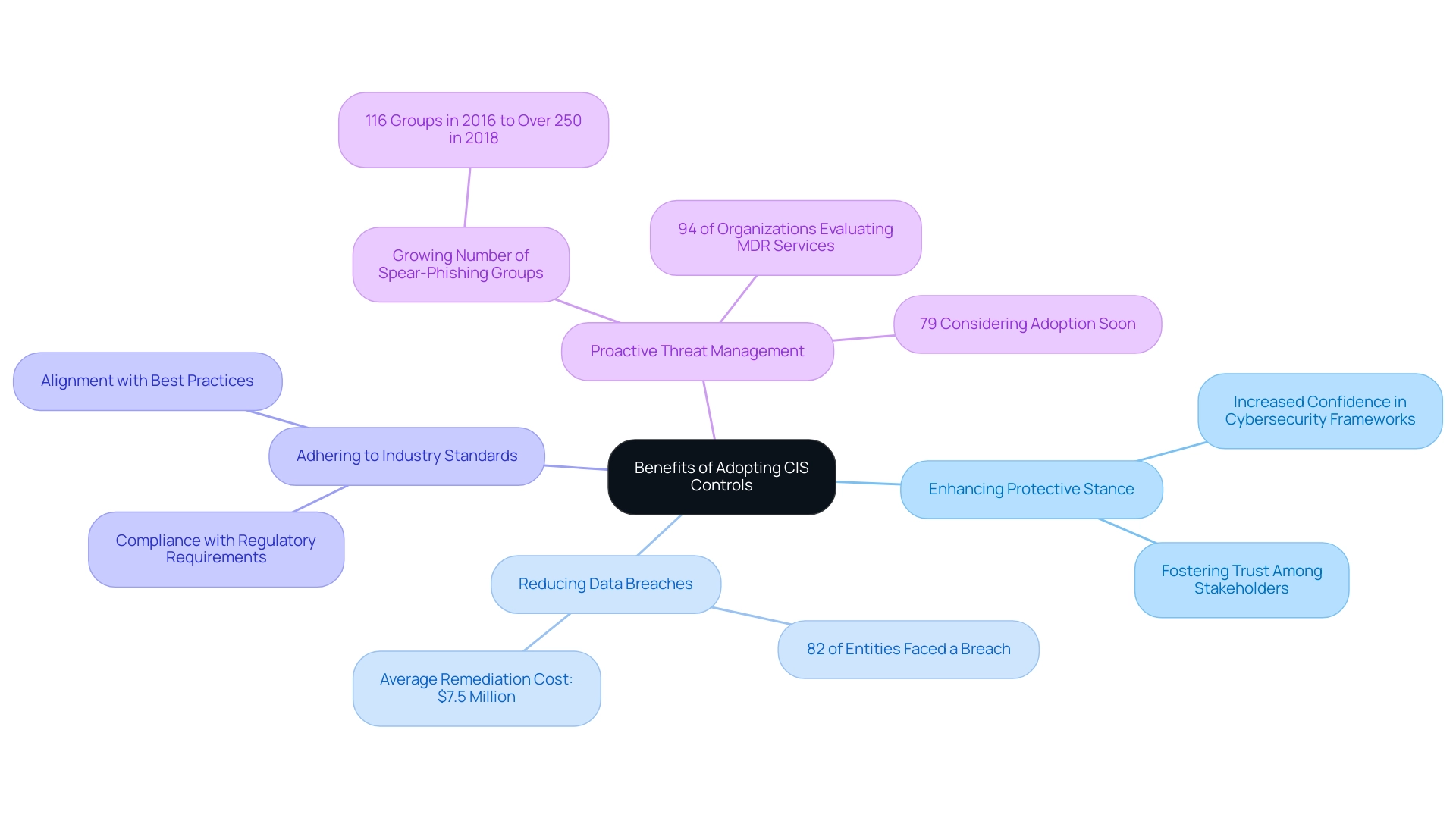
Benefits of Adopting CIS Controls: Enhancing Cybersecurity
Applying the CIS framework controls offers numerous benefits for firms, particularly in enhancing their protective stance, reducing the likelihood of data breaches, and ensuring adherence to industry standards. Recent statistics reveal that a staggering 82% of entities have encountered at least one third-party data breach, leading to average remediation costs of approximately $7.5 million. This underscores the necessity for robust security measures, as highlighted by Ayman Elsawah, a vCISO at Sprinto, who emphasizes,
Security is always going to cost you more if you delay things and try to do it later.
Furthermore, the count of known spear-phishing groups has increased from 116 in 2016 to over 250 in 2018, illustrating the changing landscape of cyber threats that entities face today. The CIS framework controls not only enhance the safeguarding of sensitive information but also enable entities to proactively tackle possible threats. By adopting these controls, entities can achieve ongoing security improvements which are essential in the face of such evolving challenges.
Remarkably, entities that have adopted CIS Practices report a significant increase in confidence regarding their cybersecurity frameworks, fostering greater trust among stakeholders and ensuring business continuity. Furthermore, with 94% of entities currently evaluating MDR services and 79% contemplating adoption soon, it is evident that the urgency for effective cybersecurity measures is acknowledged throughout the industry. The scrutiny following high-profile breaches, such as the Equifax incident that compromised the data of over 148 million individuals, has intensified the focus on data protection practices.
This incident serves as a stark reminder of the critical need for organizations to implement CIS framework controls, making it not just beneficial, but imperative for modern organizations.
Conclusion
In the face of increasingly sophisticated cyber threats, the implementation of CIS Controls has emerged as a fundamental strategy for organizations aiming to enhance their cybersecurity posture. This structured framework, developed by the Center for Internet Security, encompasses 18 critical security measures that address both basic and advanced vulnerabilities. By prioritizing these controls, organizations can establish a robust foundation for security, significantly reducing the risk of data breaches and ensuring compliance with industry standards.
The article has outlined the importance of proactive measures, such as regular security assessments and employee training, in fostering a culture of security awareness. Effective implementation of the CIS Controls not only mitigates risks associated with cyber threats but also builds confidence among stakeholders, reinforcing the organization's commitment to safeguarding sensitive information. As organizations allocate significant resources to combat insider threats and data breaches, the relevance of the CIS Controls cannot be overstated.
Ultimately, the adoption of CIS Controls represents a strategic choice for organizations navigating the complex landscape of cybersecurity. By integrating these best practices into their security frameworks, organizations position themselves to respond proactively to evolving threats, ensuring long-term resilience and security in an increasingly perilous digital environment. The imperative for robust cybersecurity measures is clear, making the CIS Controls an essential component of any organization's defense strategy.




