Introduction
In an age where cyber threats are increasingly sophisticated and pervasive, organizations must adopt a proactive stance to safeguard their digital assets. Threat hunting emerges as a critical strategy, empowering cybersecurity teams to actively search for potential threats within their networks before they can cause harm. Unlike traditional security measures that primarily react to alerts, threat hunting emphasizes the importance of a forward-thinking approach, enabling businesses to uncover vulnerabilities and mitigate risks effectively.
As the landscape of cybercrime continues to evolve, understanding the methodologies, benefits, and challenges associated with threat hunting is essential for any organization seeking to fortify its defenses and enhance its resilience against an array of cyber threats.
What is Threat Hunting and Why is it Essential?
Threat detection signifies an essential method in the field of proactive digital security, defined by the intentional pursuit of dangers within a company's network before their possible effects. This strategy stands in contrast to conventional security practices, which typically react to alerts generated by automated systems. By actively seeking out hidden threats, entities can uncover vulnerabilities that may otherwise remain undetected.
As Miranda McCurdy aptly states,
Proactive cybersecurity is more than a goal—it’s an essential mindset for organizational resilience.
Cultivating this proactive culture is paramount; it significantly enhances a company's security posture, thereby mitigating the risk of data breaches and other cyber incidents. Research shows that organizations that adopt risk searching can decrease their average time to identify breaches by 50%, illustrating the efficacy of this method.
For example, a financial organization recently employed risk detection methods, leading to the recognition and neutralization of a complex attack that could have jeopardized sensitive customer information. The ongoing need for such measures is underscored by the dramatic rise in cross-border payments, which surged to over $150 trillion in 2022.
The EvonSys Payments Platform exemplifies the implementation of proactive security measures, addressing the evolving landscape of financial transactions and highlighting the critical importance of safeguarding these processes against potential digital risks.
Exploring Threat Hunting Methodologies and Frameworks
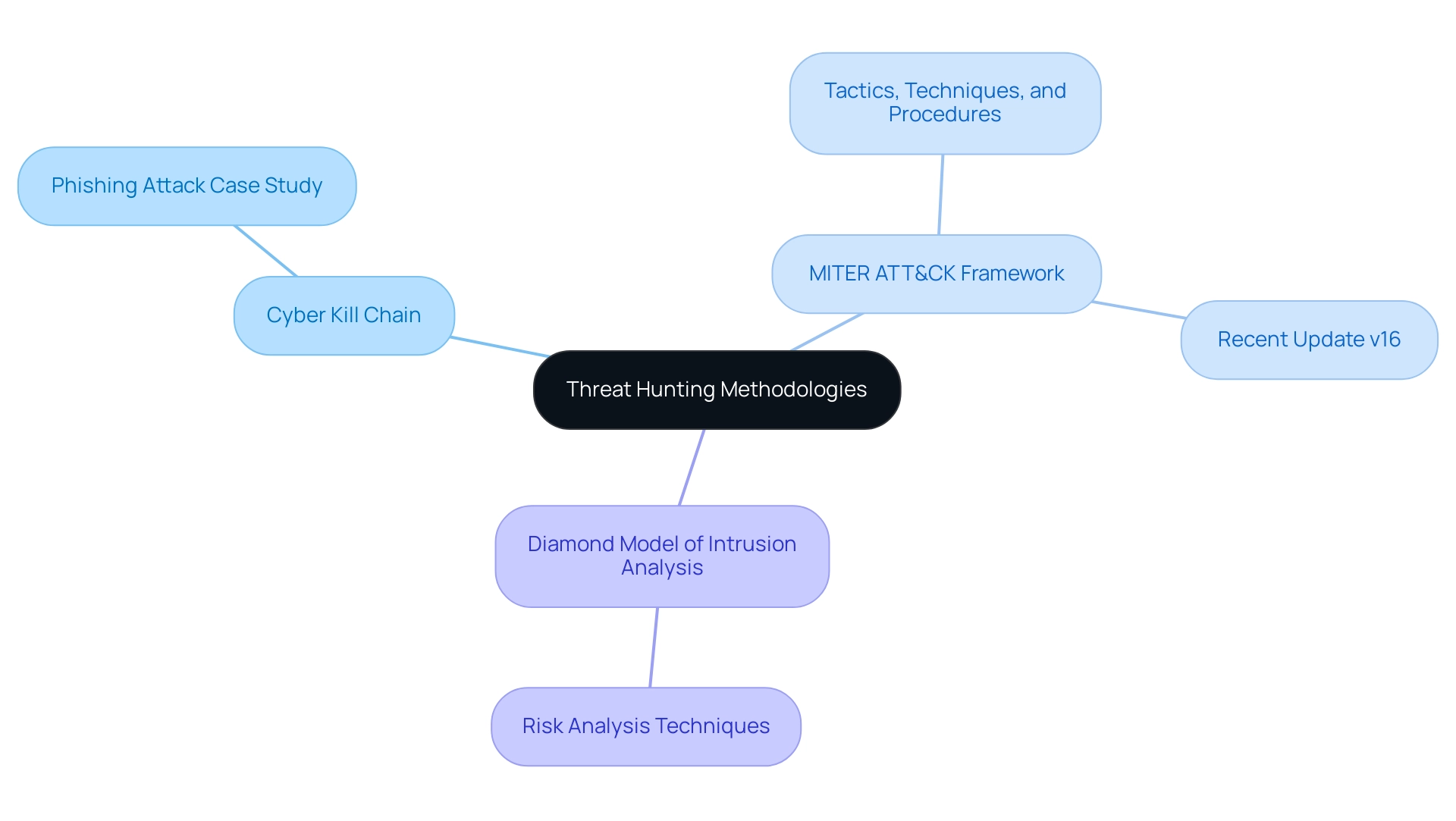
Threat detection efforts are guided by several methodologies, including the Cyber Kill Chain, the MITER ATT&CK framework, and the Diamond Model of Intrusion Analysis. These frameworks offer a systematic method for recognizing and examining risks within a company's security environment. According to recent industry reports, approximately 67% of organizations have adopted hunting frameworks, reflecting a growing recognition of their importance in proactive cybersecurity measures.
The MITER ATT&CK framework, specifically, classifies recognized attacker tactics, techniques, and procedures, which enables security experts to foresee possible risks and formulate effective countermeasures. For instance, in a recent case study, a company utilized the Cyber Kill Chain methodology to successfully thwart a phishing attack by identifying and disrupting the attacker's reconnaissance phase.
Notably, the recent October 2024 update to the MITER ATT&CK framework (v16) introduced significant enhancements, expanding the range of techniques and incorporating detection notes that reflect real-world adversary behaviors. This evolution highlights the framework's utility in enhancing risk identification and mitigation strategies.
Mastery of these methodologies is critical for security professionals, as they equip teams with the necessary tools to structure their threat-hunting activities, thereby enhancing the overall efficacy of security operations in 2024.
The Benefits of Implementing Threat Hunting Services
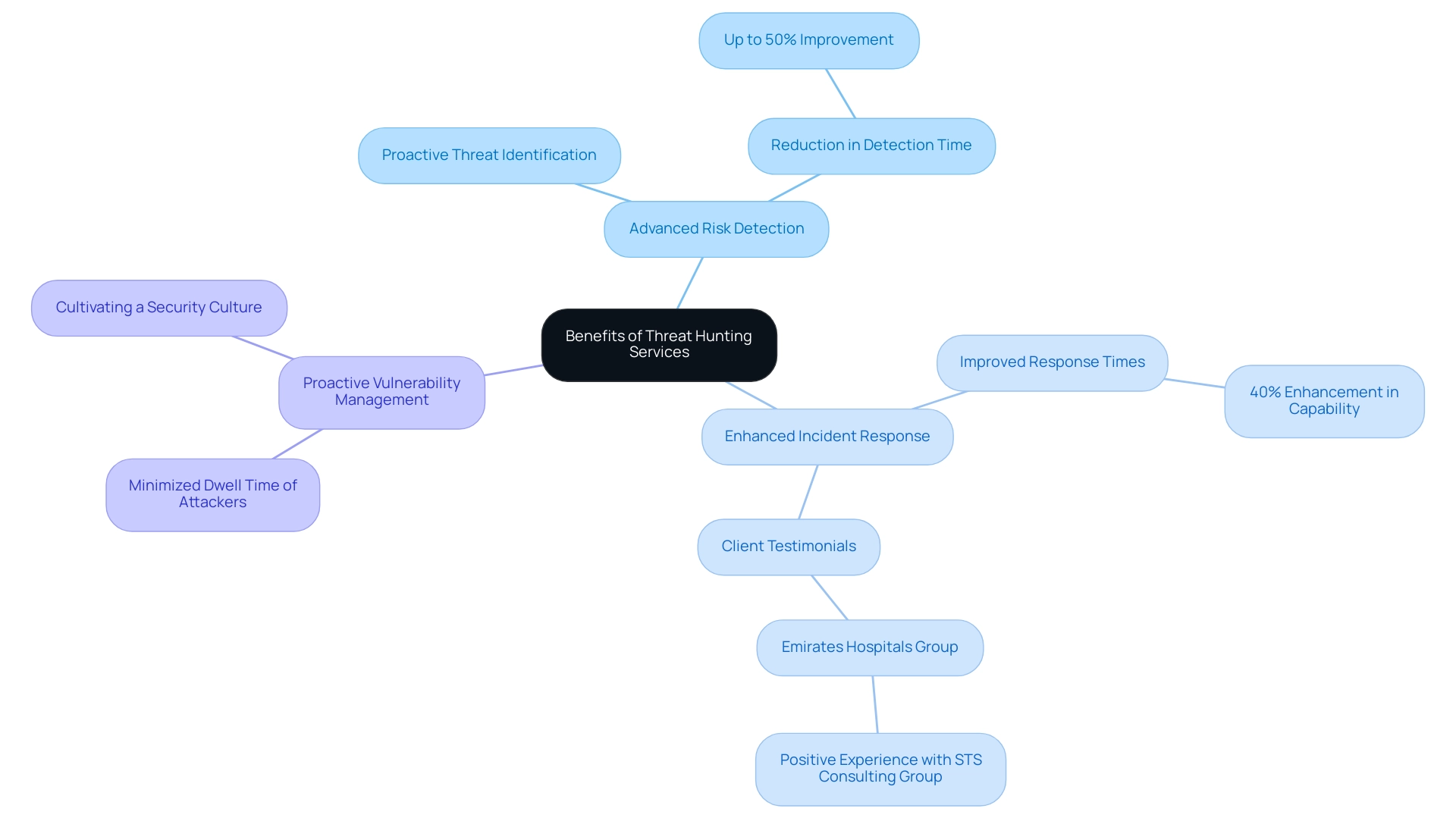
Introducing risk exploration services offers a variety of important benefits for businesses, especially in the area of advanced risk detection and incident response enhancement. Proactive risk identification can decrease the average time to discover an issue by up to 50%, which is vital in today's intricate cybersecurity environment. Based on industry specialists, entities that implement risk monitoring practices not only boost their detection abilities but also greatly enhance their incident response durations. By actively searching for dangers, organizations can identify and address vulnerabilities before they can be exploited, thereby enhancing their overall security posture. This proactive approach minimizes the dwell time of attackers within the network, creating a more resilient environment.
The significance of client testimonials cannot be exaggerated, as they offer valuable insights into the effectiveness of security services. Clients such as Emirates Hospitals Group have encountered directly the effects of strong risk detection services. As one client noted:
- "STS Consulting Group was the missing piece to my puzzle. From start to finish, they solved every problem and helped us achieve our goals in the most professional way possible."
This sentiment is echoed by many, who emphasize the helpfulness and knowledge of the STS Consulting Group team throughout the process. Their engineering team's expertise is instrumental in delivering valuable services that improve incident response times and capabilities. Clients consistently express trust in STS Consulting Group as a business partner, appreciating their deep understanding of cybersecurity needs and their ability to monitor multiple signals within complex environments.
In 2024, statistics suggest that entities utilizing hunting services report a 40% enhancement in their capacity to respond effectively to incidents. This highlights the tangible benefits of adopting such proactive measures. Additionally, as one satisfied client remarked:
- "Using STS Consulting Group helped me save weeks of work. Their delightful level of quality and service is consistent and one of a kind. I can't recommend STS Consulting Group enough."
This proactive approach cultivates a security culture within entities, fostering collaboration and the sharing of insights among teams. This collective method not only results in stronger protections against emerging cyber challenges but also places entities to remain ahead in a constantly shifting cyber environment.
Challenges in Threat Hunting: Navigating the Landscape
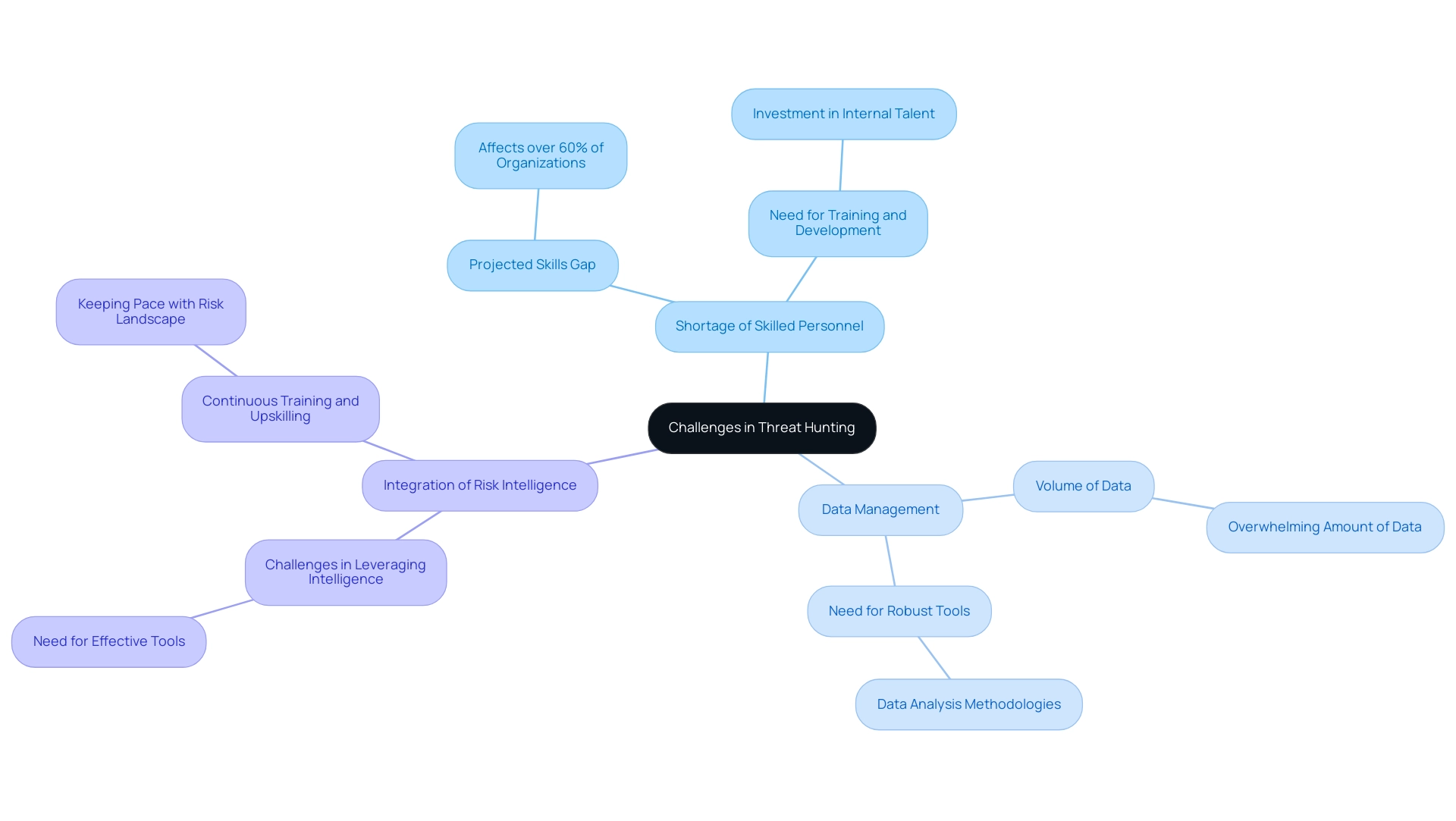
Threat detection presents considerable difficulties that entities must navigate to establish effective security operations. One of the foremost obstacles is the acute shortage of skilled personnel. As online security risks develop, the need for qualified experts who have the specialized abilities required for efficient risk hunting keeps exceeding supply. According to industry projections for 2024, the skills gap in cybersecurity is expected to affect over 60% of organizations, highlighting the urgency for companies to invest in training and development initiatives to cultivate their internal talent.
Additionally, effective data management is a critical concern. The sheer volume of data produced in contemporary IT settings can be overwhelming, making it increasingly difficult for teams to sift through and identify pertinent risks. Organizations must implement robust data analysis tools and methodologies to streamline this process.
Furthermore, integrating risk intelligence into hunting practices presents another layer of complexity. Without the right tools or resources, teams may struggle to leverage intelligence effectively, hindering their ability to respond to emerging challenges. Specialists such as Dr. Jane Smith, a cybersecurity analyst, stress that organizations must prioritize continuous training and upskilling to keep pace with the changing risk landscape.
Seven Step Consulting, a global cyber security risk and resiliency consultancy based in New Delhi, exemplifies the proactive approach required to tackle these challenges. Founded in 2009, the company specializes in creating enterprise-level applications across various industries, focusing on enhancing application security through rigorous vulnerability assessments and penetration testing. For instance, Company X implemented a comprehensive training program that reduced their skills gap by 30% within a year.
Tackling these complex challenges is crucial for entities seeking to build a thorough capability that not only recognizes risks but also actively reduces them.
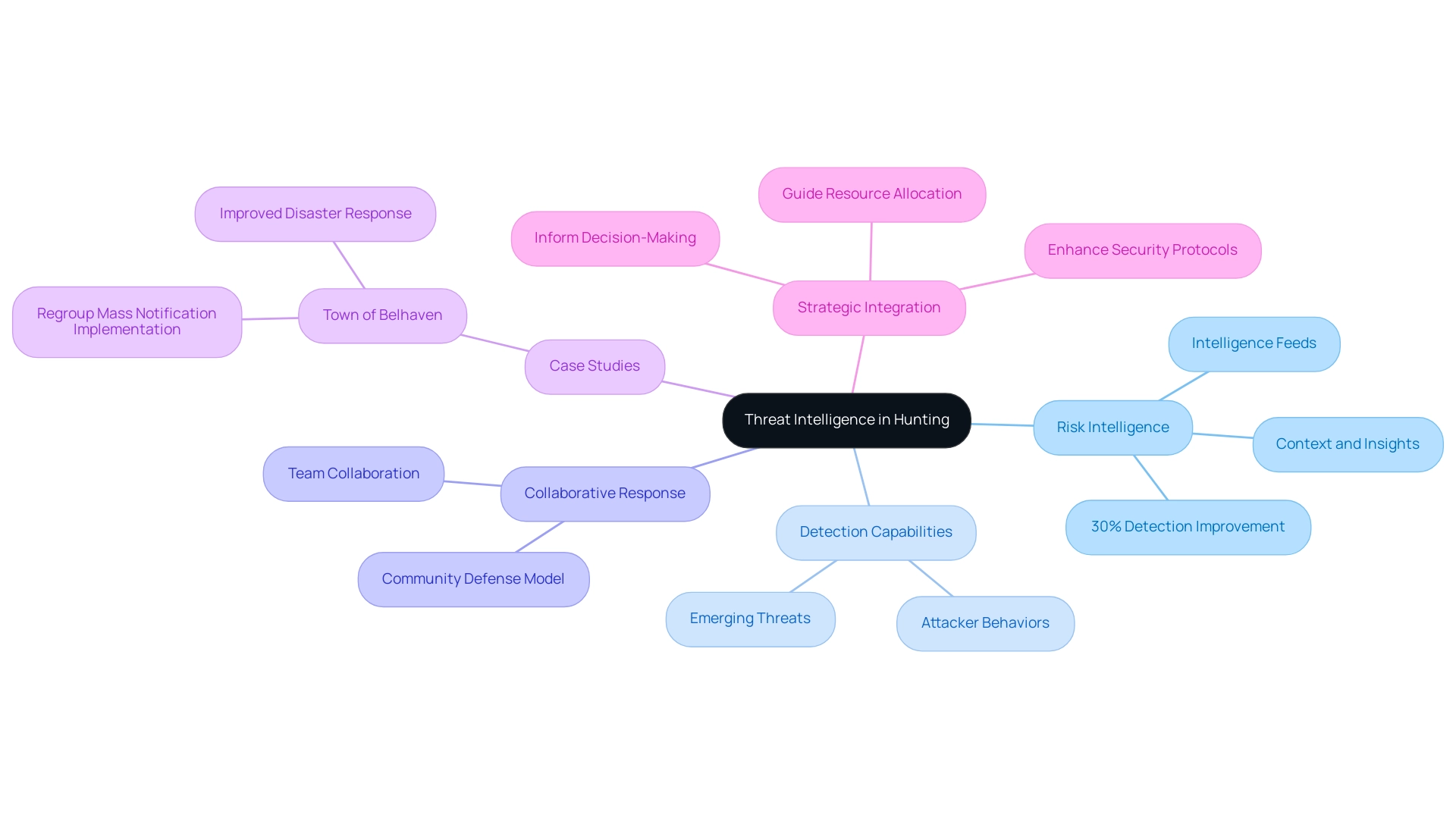
Leveraging Threat Intelligence for Effective Hunting
Risk intelligence serves as a cornerstone in hunting, delivering essential context and insights that shape effective strategies. According to recent statistics, organizations that utilize intelligence feeds have seen a 30% increase in their ability to detect emerging risks compared to those that do not. By utilizing these feeds, cybersecurity experts can swiftly recognize emerging dangers and analyze attacker behaviors, which is crucial for prioritizing targets during investigations.
As noted by Expert Insights, 'the wide-ranging impact of cyber intelligence, from incident response and risk analysis to focused penetration testing and compliance maintenance,' underscores its significance in enhancing security operations. This integration of risk intelligence into the hunting process allows teams to concentrate their efforts on the most pertinent challenges, significantly enhancing the prospects for successful detection and mitigation.
For example, in the case study of the Town of Belhaven, the implementation of Regroup Mass Notification systems enhanced their response capabilities, illustrating how prompt intelligence can shape effective reactions to potential attacks. Moreover, it promotes collaboration among different teams, ensuring that hunters are equipped with the latest data and insights essential for combating cyber risks effectively.
In the evolving landscape of cybersecurity, the role of threat intelligence in threat hunting is not merely beneficial—it is imperative for organizations aiming to stay ahead of potential attacks.
Conclusion
Threat hunting is an essential strategy for organizations looking to enhance their cybersecurity posture in an increasingly complex threat landscape. By proactively seeking out potential vulnerabilities and threats within their networks, organizations can significantly reduce the time to detect breaches and mitigate risks before they escalate into serious incidents. The application of established methodologies such as the Cyber Kill Chain and the MITRE ATT&CK framework provides structured approaches that empower cybersecurity teams to anticipate and respond effectively to emerging threats.
The benefits of implementing threat hunting services are clear. Organizations that adopt these practices not only improve their detection capabilities but also foster a culture of proactive security that enhances overall incident response times. Client testimonials highlight the transformative impact of threat hunting on operational efficiency and security resilience, showcasing the value of expertise in navigating the complexities of cybersecurity.
However, organizations must also confront the challenges associated with threat hunting, including the skills gap and data management issues. Investing in continual training and effective data analysis tools is crucial for overcoming these obstacles. Moreover, integrating threat intelligence into hunting practices is vital for ensuring that teams can respond to threats in a timely and informed manner.
In conclusion, as cyber threats continue to evolve, the importance of threat hunting as a proactive measure cannot be overstated. By embracing this approach, organizations can not only strengthen their defenses but also position themselves to thrive in an ever-changing digital landscape. The time to invest in robust threat hunting capabilities is now, as it is a critical component in safeguarding digital assets and ensuring organizational resilience against future threats.




