Introduction
In the realm of cybersecurity, incident response plays a crucial role in protecting organizations from the ever-evolving threats they face. A robust incident response strategy is not just a reactionary measure, but a proactive stance to safeguard an organization's digital assets, maintain operational integrity, and ensure resilience in the face of cyber adversity. From preparation to recovery, each phase of the incident response process is vital in effectively managing incidents and minimizing their impact.
This article explores the importance of incident response, the phases of the NIST Incident Response Life Cycle, the significance of preparation, the role of incident response policy and function, the tools and resources available, risk assessments and mitigation strategies, security measures and user training, detection and analysis techniques, identifying security incidents, containment and eradication methods, the recovery of systems, post-incident activities, and improving incident response capabilities. By understanding and implementing an effective incident response framework, organizations can establish themselves as trusted authorities in the field and ensure their resilience against cyber threats.
Why is Incident Response Important?
A strong strategy to address and handle unexpected events acts as the defense against the wide range of cybersecurity risks that contemporary organizations encounter. It is the disciplined methodology for managing the aftermath of security threats like data breaches or network intrusions. An Incident Response Plan (IRP) is a crucial resource that outlines the necessary steps for each stage of addressing an incident. It includes roles and responsibilities, communication strategies, and clearly articulated protocols to ensure clarity and minimize ambiguities. For instance, distinguishing between an 'event', an 'alert', and an 'incident' is vital for effective communication and action.
Understanding the landscape of your operational environment is paramount. This entails mapping out your organization's footprint, interconnections, information flows, continuity requirements, and identifying potential gaps in your cybersecurity posture. It is essential to establish efficient communication channels for both internal and external stakeholders to facilitate ready access to crucial information, fostering an environment of preparedness and adaptability.
Testing the IRP is just as crucial as its creation, revealing gaps and providing insights into the plan's effectiveness in real-world scenarios. To test your IRP, dissect it into its constituent processes, then prioritize them based on their criticality and the effort required to test each. Regular testing ensures that when a situation does happen, your reaction is quick and well-coordinated.
Moreover, the process of addressing occurrences is backed by a comprehensive framework for managing these events that regulates the coordination of these incidents. This framework includes predefined steps, such as identification, assessment, investigation, mitigation, and documentation, which are essential for minimizing downtime and rapidly restoring normal operations. Implementing a comprehensive event management platform customized to your organization's unique intricacies is essential for efficiently handling occurrences and sustaining operational stability.
Recent occurrences, like the Cloudflare outage caused by a misconfiguration, highlight the significance of a carefully designed and well-executed response plan. The outage's impact illustrates the significant business implications of downtime and the necessity of reliable incident handling solutions, as demonstrated by Charter's deployment of Squadcast to enhance their clients' operational reliability.
By utilizing resources like the Security Planning Workbook, entities can create security plans that are both adaptable and all-encompassing, addressing distinct organizational requirements while aligning with overarching business goals. This resource also offers insights into threat hunting, allowing companies to proactively search for potential vulnerabilities within their networks.
In brief, a thorough response plan integrated with a strong management framework is not only a reactive measure, but a proactive position to safeguard a company's digital resources, maintain its operational integrity, and guarantee its resilience in the face of cyber challenges.
The Four Phases of the NIST Incident Response Life Cycle
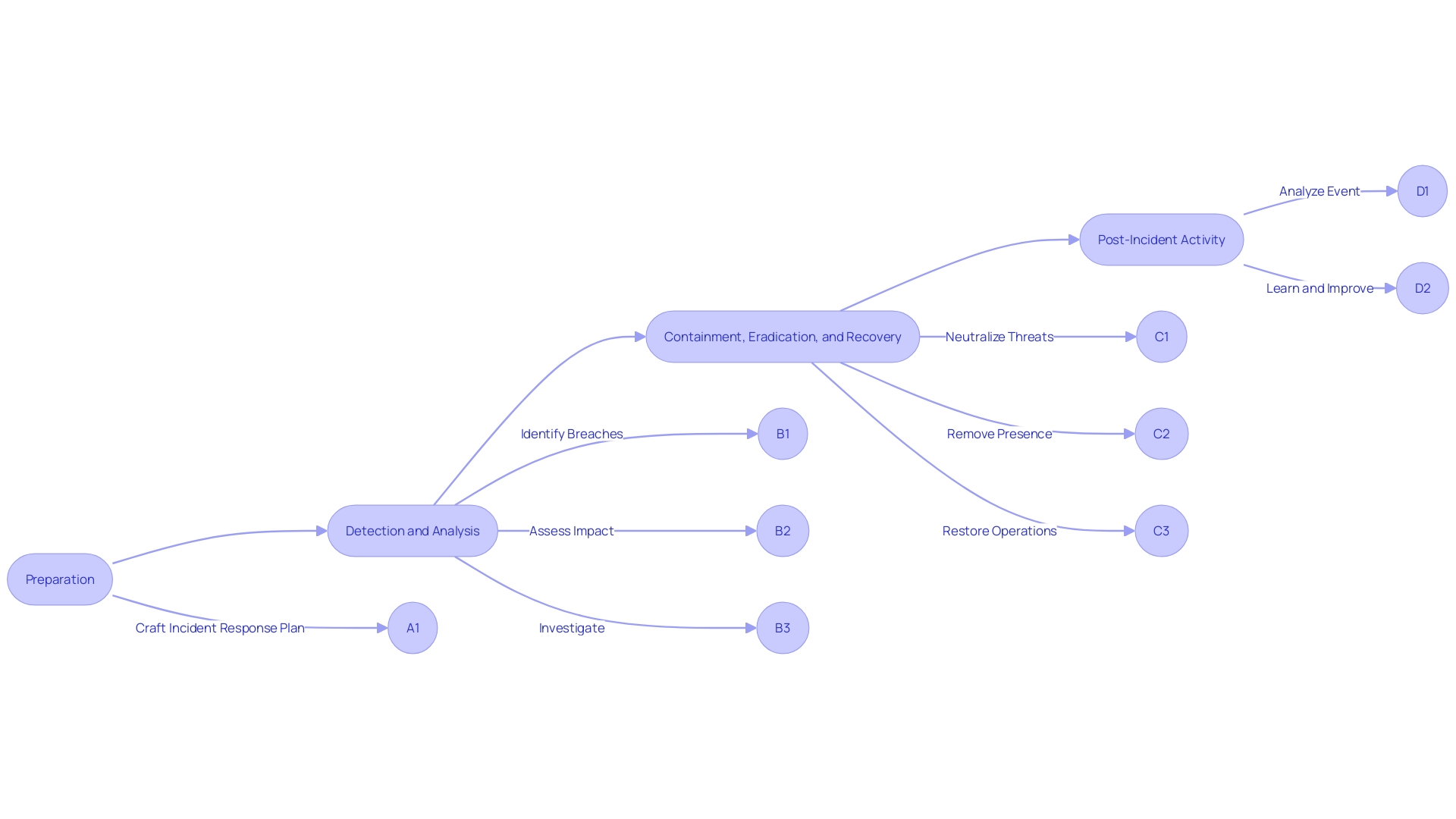
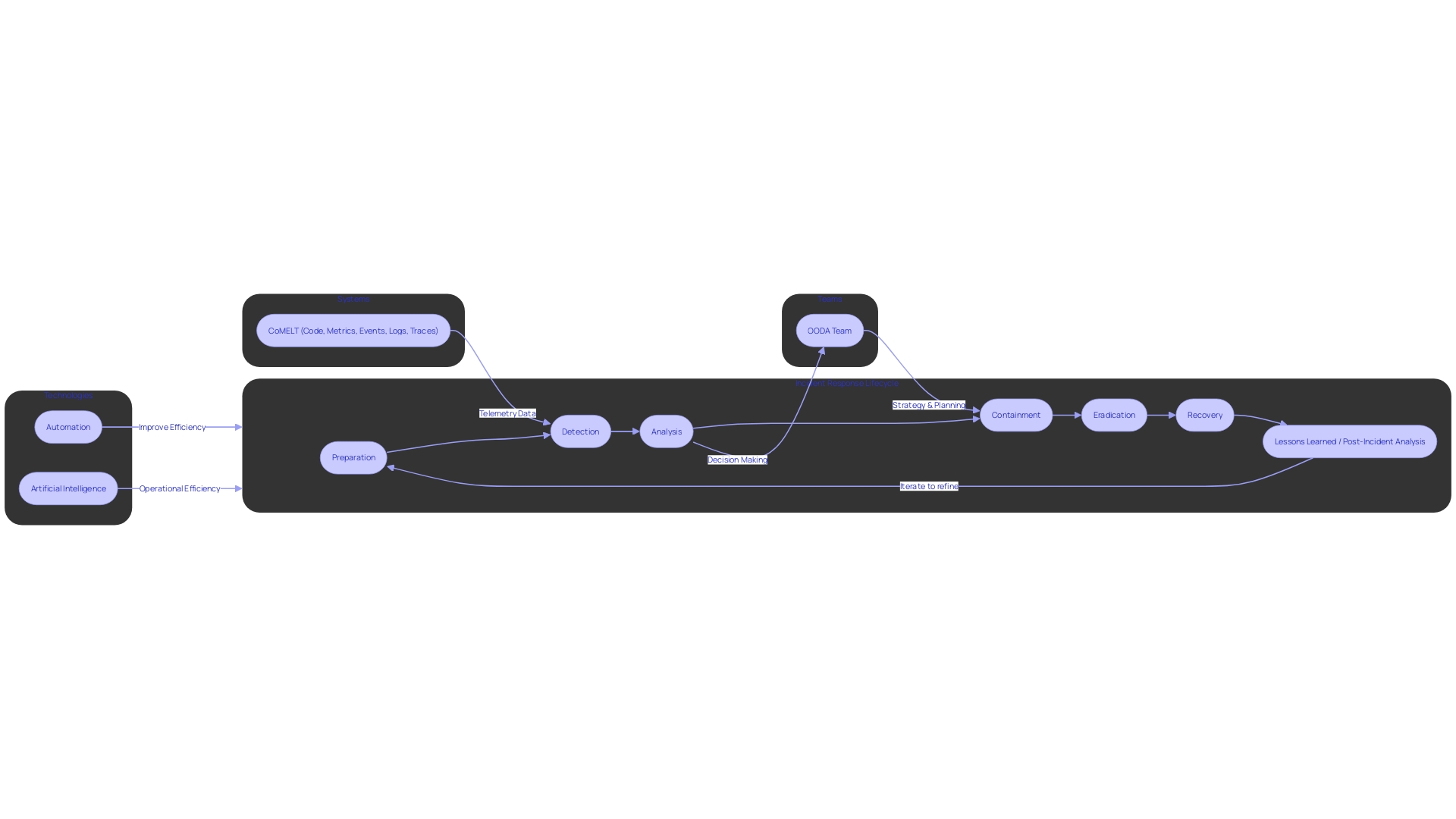
The NIST Incident Response Life Cycle is a strong framework that equips entities with the necessary procedures to effectively tackle security incidents across various phases. This comprehensive approach is not just about responding to adverse events; it's about ensuring the company can come back stronger and more secure. The cycle begins with Preparation, where organizations craft a well-documented Incident Response Plan (IRP) that clearly delineates roles, responsibilities, and communication strategies. This strategy should be clear and clear-cut, particularly when specifying commonly misunderstood terms such as occurrences, warnings, and situations.
The Detection and Analysis phase is crucial for identifying security breaches as quickly as possible. It's a technical and operational feat that involves logging events, assessing their impact and severity, and conducting a thorough investigation. For example, the Arab National Bank's digital transformation highlights the significance of modernized and efficient event detection in today's fast-evolving banking landscape.
Containment, Eradication, and Recovery are the next steps that focus on neutralizing threats, removing their presence from systems, and restoring normal operations. The main objective during these stages is to reduce the effect of the occurrence. This is achieved by meticulously executing a resolution plan and ensuring that all stakeholders are kept informed throughout the process.
Lastly, Post-Incident Activity involves a reflective analysis of the event. Questions like "Has this happened before?" and "How was it resolved?" guide entities to learn from previous experiences and refine their response strategies. This phase ensures continuous improvement, which is supported by the collection and examination of data to better understand the risk landscape and enhance security measures.
In general, the NIST Response Life Cycle promotes a culture of readiness, allowing entities to handle events systematically. It's about establishing a robust structure that adjusts over time, gaining knowledge from each occurrence to strengthen the defenses against the constantly evolving cybersecurity threats.
Preparation
Preparing the groundwork for an efficient reaction to cybersecurity occurrences is a crucial undertaking that encompasses beyond merely formulating an occurrence management guideline. It's about creating a robust framework that ensures all hands are on deck and that every team member knows their role. The preliminary stage requires careful organization, where the duties and obligations of the team responsible for addressing the situation are explicitly determined, in accordance with the organization's strategic approach to cybersecurity.
This preparation includes ensuring that the tools and resources necessary for a prompt and efficient answer are readily available. Whether it's a case of configuration drift, where a web server's settings have changed without authorization, or a complex cyber attack, the team must be equipped to handle any scenario. The plan for addressing problems must be thorough and practical, covering not just the main causes of issues but also the factors that can worsen the problem, like changes in code or problems with external services.
In the context of recent advancements in the cybersecurity field, where countries such as the US, Britain, and the European Union are working together on AI standards, the significance of a well-defined and practiced reaction to an unexpected event is emphasized. Such international agreements reflect the critical need for standardized approaches to event handling, which are integral to maintaining the resilience of organizations in today's interconnected world.
A successful occurrence resolution framework is constructed on a basis of a well-organized occurrence control workflow. This workflow is a sequence of steps designed to systematically manage the lifecycle of a situation from detection to resolution, ensuring minimal downtime and risk while promoting a quick return to normal operations.
Statistics from the latest reports, such as those by the SANS Institute, highlight the evolving nature of cybersecurity operations and the need for data-driven insights. These insights are crucial for the incident team to make informed tactical decisions and leverage technologies like automation and AI to optimize resource allocation.
The ultimate aim of the preparation phase is not only to have a plan in place but to have a dynamic and practiced reaction ready to be deployed. This preparedness is crucial for both the security of the company and the welfare of the team, preventing burnout and ensuring that the security operations center (SOC) runs efficiently without overwhelming its personnel. As the danger environment keeps on changing, the readiness for managing situations remains an essential component of a company's cybersecurity position.
Incident Response Policy and Function
The core of a policy for addressing cybersecurity threats is to express a company's procedural blueprint. This policy outlines the strategic goals, boundaries, and the range of activities that encompass event management. In practice, the response function activates this policy into action, coordinating and executing response efforts across the organization.
Incident Response (IR) is multifaceted, involving a synthesis of technical, operational, and management strategies to detect, contain, eradicate, and recover from security breaches or cyberattacks. The objectives are clear: minimize the impact of incidents, swiftly resume normal operations, and thwart future attacks. The concept of IR has evolved from a once spontaneous and reactive measure into a structured methodology, spurred by the escalating frequency and sophistication of cyber threats. This evolution was marked by the formation of Computer Emergency Response Teams (Certs) in the 1980s, signifying a landmark in collaborative cybersecurity efforts.
The effectiveness of IR hinges on a robust and tested plan, featuring predefined processes for an efficient and methodical reaction. Key steps include identification, assessment, analysis, mitigation, and resolution, each critical to maintaining operational stability during and after a cybersecurity event. These measures are bolstered by regular testing, which helps uncover any shortcomings in the handling of unexpected events and enhance its effectiveness.
After a crisis, like a production event, the composition of the response team becomes crucial. The main functions usually include a Reporter, Keymaster, and Fixerâeach playing a crucial part in navigating the situation lifecycle, from initial detection to final resolution. How a company reacts to such events is not only a manifestation of its operational strength but also a representation of its corporate values.
Understanding that incidents can have widespread implications, a comprehensive Business Continuity Management (BCM) plan is indispensable. It incorporates a risk assessment and business impact analysis to safeguard various organizational facets, including personnel, legal, finance, and reputation. Regular monitoring, reviewing, and updating of the BCM plan are critical to its effectiveness, ensuring the organization's preparedness for a diversity of disruptive events.
Tools and Resources for Incident Response
Incident response is a crucial aspect of organizational resilience, involving a structured process that combines strategic, operational, and technical efforts to tackle IT disruptions. Central to this is the Incident Response Plan, a detailed framework guiding the detection, containment, and remediation of cyber threats. A successful plan necessitates transparent communication channels, a proficient Response Team, and powerful tools for forensic analysis and event management.
The integration of advanced software and forensic tools is crucial for the key strategy, enabling teams to quickly identify and address security breaches. These tools must be complemented with comprehensive communication strategies, ensuring that relevant stakeholders are kept informed throughout the event cycle.
Furthermore, the contemporary framework for addressing unforeseen events is enhanced by partnerships with external entities like law enforcement and specialized firms for addressing unforeseen events. Such partnerships can greatly improve an organization's handling capabilities, providing additional expertise and resources when needed.
Dealing with incidents is not fixed; it adapts with the evolving environment of cyber dangers. As mentioned by Michael Nadeau, senior editor at CSO Online, readiness is essential, and it encompasses more than just establishing tools; it also involves educating teams and developing a plan for addressing emerging threats and technologies.
In the digital age, the concept of a "jump bag", as highlighted by a seasoned incident response professional, symbolizes readiness—a collection of essential tools and information to address cyber incidents effectively. This idea emphasizes the importance of being ready and being able to react quickly, which is essential in the digital realm where events can happen rapidly.
Finally, the response process is iterative, investigating the underlying reasons and contributing factors of an event—such as configuration drift or external service issues—to not only resolve the current situation but also to strengthen defenses against future threats. The ultimate goal is to reduce the effect of occurrences, rapidly restore regular operations, and utilize post-event analysis to strengthen the organization's cyber resilience.

Risk Assessments and Mitigation
To fortify defenses against security incidents, a thorough risk assessment is paramount. This assessment identifies possible system vulnerabilities and external risks, establishing the basis for strong security protocols and strategies to mitigate risks. By comprehending and handling the subtleties between dangers, vulnerabilities, and risk, establishments can greatly reduce the probability and impacts of security breaches.
A risk signifies a possible reason for an event that could lead to damage to a system or entity, whereas a weakness is a flaw that can be taken advantage of by a malicious actor. Risk is the potential for loss, damage, or destruction of an asset as a result of a threat exploiting a vulnerability. Efficient risk management is not just about recognizing these components but also about comprehending the connection between them and the influence they may have on a company's operations.
Drawing parallels from the California wildfires, where a limited number of utilities managing extensive infrastructures faced unpredictable and escalating wildfire risks, entities in the tech industry, particularly those working with AI, encounter similar challenges. The AI Risk Repository, with its extensive classification of over 700 distinct risks, serves as an exemplary model for comprehending and categorizing possible hazards in AI development and deployment. This repository aids organizations in anticipating and preparing for a diverse range of risks, ensuring they're not caught off guard.
Furthermore, case studies from the California utilities emphasize the importance of ongoing vigilance and adaptation. Just as utilities must continuously adapt to evolving wildfire risks and safety standards, technology companies must stay ahead of emerging dangers and vulnerabilities within their systems. This includes staying updated on the latest cybersecurity risks and implementing strategies that align with current risk landscapes, as indicated by the Security Planning Workbook.
The wisdom of consulting widely and making informed decisions, as highlighted in key literature, resonates with the need for diverse perspectives in risk assessment. This approach fosters a comprehensive understanding of potential risks and enhances the quality of decision-making. Ultimately, data from the Office of Homeland Security Statistics and recent surveys demonstrate the interrelatedness of hazards, such as cyber attacks and supply chain disruptions, emphasizing the need for a comprehensive risk management approach that can adjust to evolving dangers.
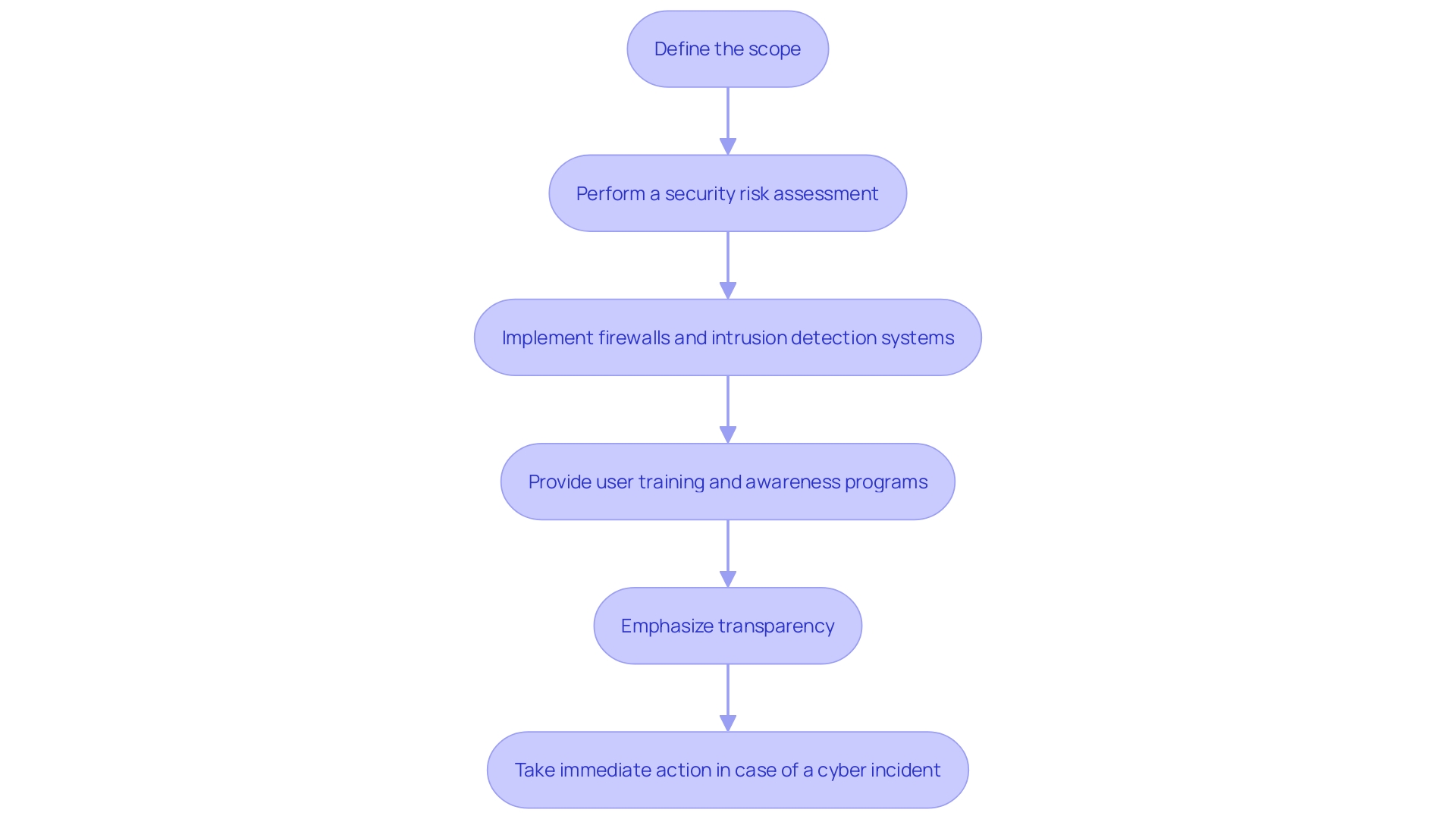
Security Measures and User Training
To bolster cybersecurity, a proactive stance is paramount. For example, the Savannah-Chatham County Public School System, serving over 35,000 students across 55 schools, has faced significant challenges in safeguarding the data of its staff and students with limited resources. Carl Eller, the Senior Director of Information Security and Technology Management, emphasizes the importance of protecting data to prevent it from being exploited. Similarly, the Arab National Bank, with its digital transformation, illustrates a commitment to becoming the first choice for delivering financial services while prioritizing security.
Emphasizing the need for security to be built into the design of products, a recent white paper has updated its core principles, urging manufacturers to take ownership of customer security outcomes, embrace transparency, and build appropriate organizational structures to support these goals. This approach aligns with the latest threat intelligence reports, such as the 2023 BlackBerry Global Threat Intelligence Report, which highlights the most prevalent malware families affecting various operating systems.
These principles are echoed in the forward-looking statements from the press release regarding the cybersecurity issue at an unnamed company, stressing the importance of enhancing system safeguards. The Toronto Zoo's reaction to a recent cyber incident also demonstrates the necessity of immediate and transparent action to mitigate the impact on affected individuals.
Incorporating these lessons, companies must implement strong security measures like firewalls, intrusion detection systems, and encryption, and couple these with regular user training and awareness programs. This will not only educate employees about security best practices but also prepare them to recognize and respond to potential risks effectively.
Detection and Analysis
Incident response is a critical aspect of maintaining cybersecurity in any organization. It involves a set of strategic steps and specialized tools deployed to identify and mitigate the effects of cybersecurity threats. One of the initial and most crucial stages in this process is the detection and analysis phase. During this phase, security teams vigilantly monitor systems and networks for signs of unauthorized or unusual activity. This entails a careful procedure of collecting and examining data to determine the extent and influence of any potential security event.
Example, a real-world event occurred over a month, demonstrating three distinct phases of malicious activity. The initial alert was triggered by an unauthorized AWS support case requesting an increase in email service limits—a service not in use by the client. This irregularity flagged the need for immediate investigation, as such requests can be indicative of an attacker's intent to use the platform for large-scale phishing or spam campaigns.
While analyzing the situation, it was discovered that a suspicious IAM user, known as DangerDev@protonmail.me, was the cause of the event. This finding prompted a deeper investigation into how the unauthorized access was obtained and emphasized the significance of maintaining a strong incident handling framework. The MITER ATT&CK framework was utilized to categorize the tactics, techniques, and procedures (TTPs) employed by the attackers, enhancing the understanding of the adversary's behavior, which is paramount in developing effective countermeasures.
The latest insights from industry leaders advocate for a proactive security posture. Cisco Talos Incident Response found that technology often detects malicious activity, but without an active approach to security—such as operating in blocking mode—threat actors are more likely to succeed in their attacks. This underscores the importance of not only having the right technology in place but also ensuring that it is configured and managed effectively to preempt breaches.
As the cybersecurity landscape develops, so does the complexity of dangers. For instance, the emergence of malware like SpyAgent, which targets Android devices to steal cryptocurrency recovery phrases from images, exemplifies the need for continuous vigilance and up-to-date security measures. As a result, platforms such as Splunk are consistently monitoring the security situation to create and provide security material that assists entities in recognizing and addressing vulnerabilities and cyber assaults.
To sum up, a successful reaction plan is supported by a clearly outlined strategy and a competent team prepared with the appropriate tools and expertise. The goal is to minimize downtime, mitigate risks, and restore operations swiftly. Every reaction to an unexpected event is a chance to gain knowledge, adding to a mindset of readiness and flexibility, guaranteeing a company's ability to withstand the constantly evolving risks in the digital realm.
Identifying Security Incidents
Recognizing security occurrences is a crucial initial stage in an organization's response plan, necessitating the incorporation of sophisticated surveillance systems and advanced risk detection methodologies. The utilization of intrusion detection systems (IDS) and security information and event management (SIEM) tools is essential. These technologies serve not just as a defensive mechanism but also as a platform for understanding adversarial behaviors, aiding in crafting a more resilient cybersecurity posture. For instance, the MITER Corporation's experience with a notable cyber incident resulted in the creation of the MITRE ATT&CK® framework, which highlights the importance of behavioral analysis in overcoming cyber challenges.
Moreover, the integration of Network Detection and Response (NDR) solutions offers a nuanced approach to threat detection, combining network traffic analysis with threat intelligence feeds to provide a comprehensive risk assessment. This method, supported by specialists, enables entities to give priority to alerts and adjust their reaction based on the seriousness and possible influence of the identified irregularities.
The challenges presented by the ever-expanding digital landscape, especially with the introduction of the Internet of Things (IoT), necessitate the adoption of scalable security solutions capable of adapting to the rapid pace of technological change. When confronted with such challenges, entities must not only utilize state-of-the-art tools but also cultivate a cooperative atmosphere among security experts to consistently enhance their incident response mechanisms.
Microsoft's Digital Defense Report further emphasizes the importance of utilizing AI and leveraging diverse data sources to predict and stay ahead of cyber threats effectively. With vast telemetry sources like Microsoft Defender for Endpoint and Microsoft Defender for Cloud Apps, organizations are equipped to gather actionable insights and improve their cyber resilience in an increasingly interconnected world.
Collecting and Analyzing Data
The immediate actions taken after detecting a security event are pivotal in mitigating its impact. Examining log files, analyzing network traffic, and scrutinizing system artifacts are actions that are not only theoretical best practices but are crucial in practice, as previous events have demonstrated. For instance, in a recent case, a data engineer with decades of experience was able to leverage his deep knowledge to manage and secure critical data assets. However, this expertise also made him a target for sophisticated attacks, illustrating that even the most experienced professionals can be vulnerable.
In another instance, an AWS situation highlighted the nuances of addressing when a seemingly harmless support case pointed to a bigger problem. The unauthorized request to increase SES sending limits signaled a potential compromise, given that the client did not use SES. This underscores the importance of understanding the context around data anomalies.
Data collection and analysis are not just reactive measures; they serve as a foundation for organizational security. As noted by industry experts, the struggle to decide what data to collect and store is intense because the time frame within which a breach is discovered can be highly variable. The agreement among security professionals is to gather extensive data to facilitate successful retroactive searching for potential dangers and situation resolution.
The extensive amount of data and the intricacy of contemporary cyber threats have required a multi-layered approach to addressing incidents, which involves readiness, surveillance, and steps oriented towards addressing. Case tracking and remediation represent the latter stages where confirmed issues are managed with coordinated actions and learning from past experiences is integral to improving future security measures.
Moreover, comprehending the industry's condition by inquiring about job openings, cybercrime losses, and the categories of entities most impacted by breaches can offer valuable insights. This understanding helps in creating a strong framework for handling incidents, as the character of cyber dangers persists in developing.
As we continue to witness significant data breaches and the escalation of cyber attacks, the importance of a comprehensive NIST-aligned Incident Response Framework cannot be overstated. By engaging in careful planning, effective communication, and a strong grasp of data gravity, entities can successfully navigate the intricacies of cybersecurity and bolster their capacity to withstand future occurrences.

Determining the Impact of the Incident
The core of a strong incident management structure lies not only in addressing dangers but also in grasping their impact on an organization's operations. An effective response hinges on a comprehensive impact assessment that evaluates the full extent of data breaches, system compromises, or service disruptions. For example, CloudFlare's management of an adversarial party's presence on their self-hosted Atlassian server during Thanksgiving 2023 demonstrates the necessity for such an evaluation. Despite the intrusion, their use of Zero Trust tools, firewall rules, and hard security keys prevented any lateral movement by the threat actor, ensuring that customer data and systems remained unaffected.
A thorough impact analysis, as demonstrated by Cloudflare, enables a prioritized and resource-efficient reaction. This mirrors the findings of a Ponemon Institute study, sponsored by IBM Security, which revealed that the average cost of data breaches reached an all-time high in 2023, making it more crucial than ever to manage security investments wisely.
Furthermore, the significance of evaluating and improving plans for addressing unexpected events is emphasized by a statement from an industry specialist, highlighting that the effectiveness of a plan for addressing unexpected events is only demonstrated through practical implementation and testing. Such testing assists in identifying and rectifying gaps in critical sub-processes, ensuring that the plan remains not just theoretical but practically applicable.
According to Barracuda's report in the first half of 2023, AI-driven detection played a crucial part in examining 95 billion security occurrences, emphasizing the importance of cutting-edge technology in managing security events. This analytical capability was crucial in identifying just under one million events as potential risks, showcasing the magnitude at which security operations must operate.
To summarize, the process of addressing an unforeseen event starts with a comprehensive comprehension of the threat environment, as exemplified by experienced security executives such as David Bradbury, Okta's Chief Security Officer. His experience across multiple security roles emphasizes the necessity of a thorough impact assessment. By integrating experiences from real-life scenarios, AI-powered analysis, and ongoing evaluation, organizations can enhance their readiness for and reaction to cybersecurity events with accuracy and effectiveness.
Containment, Eradication, and Recovery
In the domain of cybersecurity, the containment, eradication, and recovery phase is a vital component of handling an occurrence (IH), involving a series of well-orchestrated actions. These steps are critical for halting the spread of the incident, systematically removing any traces of the attackers or malware, and ultimately bringing affected systems back to full functionality. To illustrate, consider the response by CloudFlare to a danger detected on Thanksgiving Day 2023. Their security team promptly severed the intruder's access, leveraged Zero Trust tools to limit lateral movement, and engaged CrowdStrike for a thorough forensic analysis, ensuring their network remained uncompromised. Similarly, a global metal fabrication company's swift reaction to a network anomaly involved isolating and scrutinizing remote management software on their server, following a cybersecurity vendor's warning about a ransomware threat. The real-world examples underscore the necessity of a comprehensive IR strategy that encompasses automated and manual log analysis, digital forensics, and reverse engineering of malware to construct an adversary's capabilities and safeguard the organization.
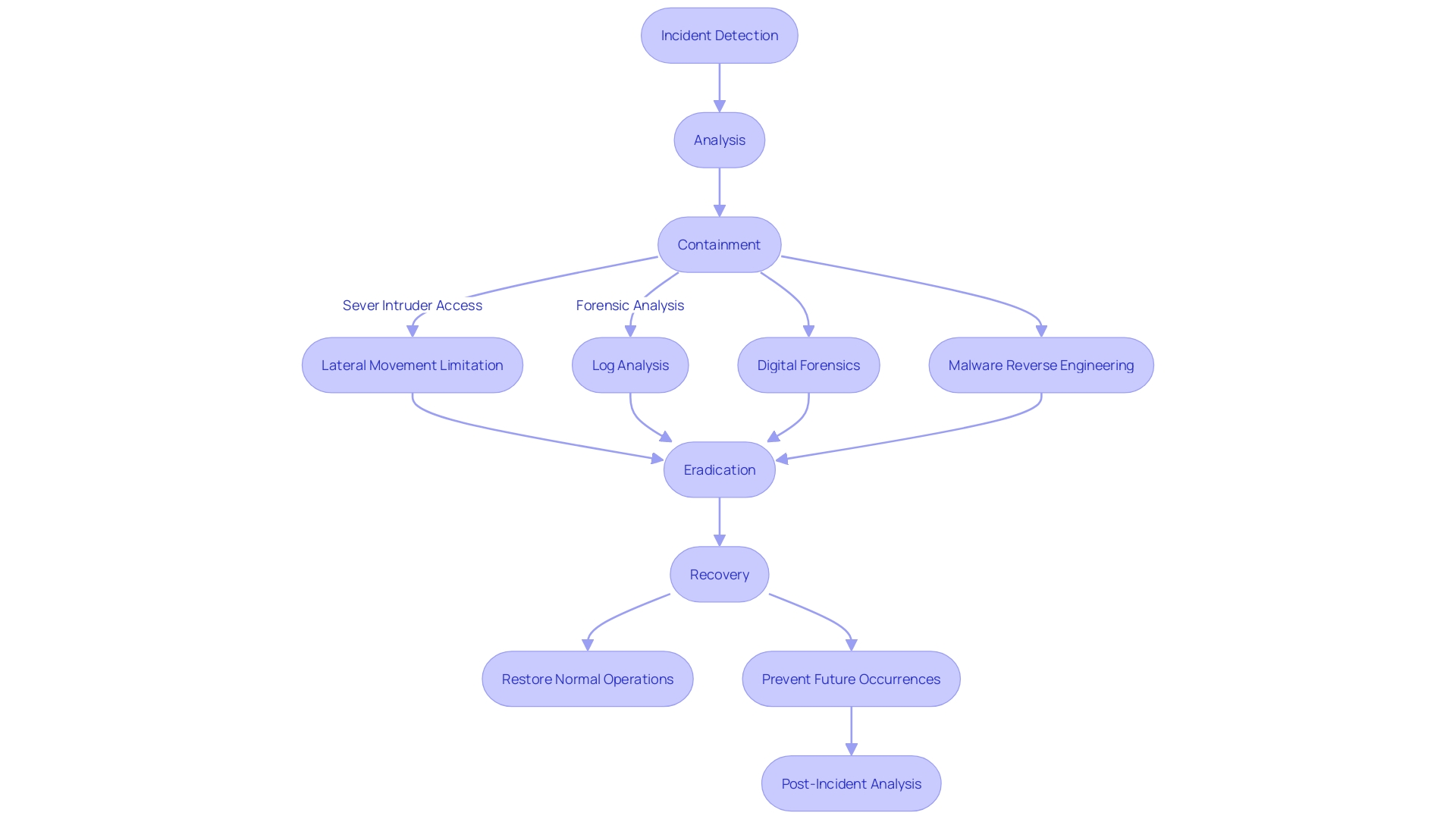
Containment Methods
Containment is a critical phase in the incident resolution process, requiring swift and decisive actions to limit the spread of an attack and mitigate its impact. In practice, this can mean disconnecting compromised systems from the network to stop the advancement of the danger. For example, CloudFlare's action towards a identified malicious actor in 2023 demonstrated containment by promptly revoking access and utilizing Zero Trust tools to hinder lateral movement within their systems. Similarly, access control measures, as emphasized in Retail Technology Review, are fundamental to ensuring that only authorized individuals can reach sensitive information. Implementing strong password protocols and strict firewall rules are examples of such preventive strategies. Additionally, response history instructs us that early computing's ad hoc measures have developed into today's strategic frameworks, such as the guidelines from Computer Emergency Response Teams, which advocate for a systematic and structured approach to cybersecurity incidents.
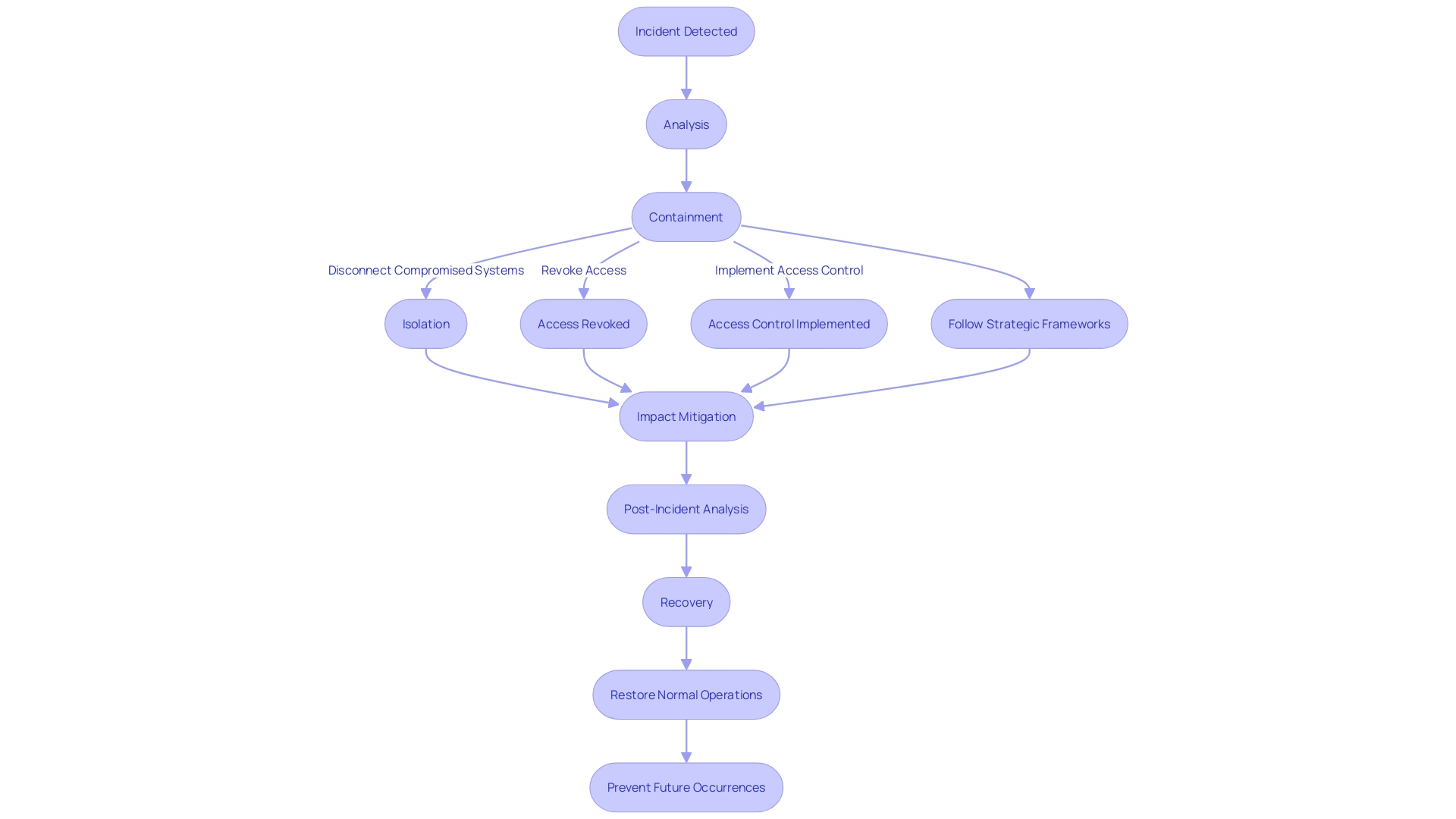
Eradication of Malicious Code
Eradicating malicious code is a multi-faceted process that extends beyond the use of antivirus software and patches. With the increase of advanced cyber risks, such as the recent phishing attacks via Microsoft Teams, organizations must consistently update their security practices. For instance, disabling External Access in Microsoft Teams, unless essential, is a strong preventative measure. Additionally, user training is critical to recognize the evolving forms of phishing beyond traditional emails.
The urgency of such measures is underscored by the aggressive cyberespionage campaigns by state-sponsored actors such as North Korea's Lazarus group, which targets aerospace companies to fund their missile programs. The group's Operation Dream Job is a stark example of how APT groups exploit human and technological vulnerabilities for espionage and financial gain.
Recent statistics reveal the overwhelming magnitude of the challenge: during a six-month timeframe in 2023, only 0.1% of 95 billion security events were identified as possible risks, with AI-powered detection playing a crucial part in recognizing and examining these occurrences. Furthermore, research conducted at Columbia University on blackmail scams identified by AI underscores the significance of AI in identifying and addressing cyber dangers.
As entities strive to safeguard their systems, adopting optimal measures for software security is crucial. These include holistically planning security requirements and designing software with security in mind from the outset. Furthermore, maintaining vigilance over the software supply chain is crucial, as attacks can occur through well-established distribution channels.
In this constantly changing environment, staying updated about the latest risks and utilizing advanced technologies such as AI for detection and pattern analysis is crucial for effective incident management. As we've observed, even a minor proportion of security incidents can indicate a substantial quantity of possible risks, necessitating that organizations uphold strong and flexible security strategies.

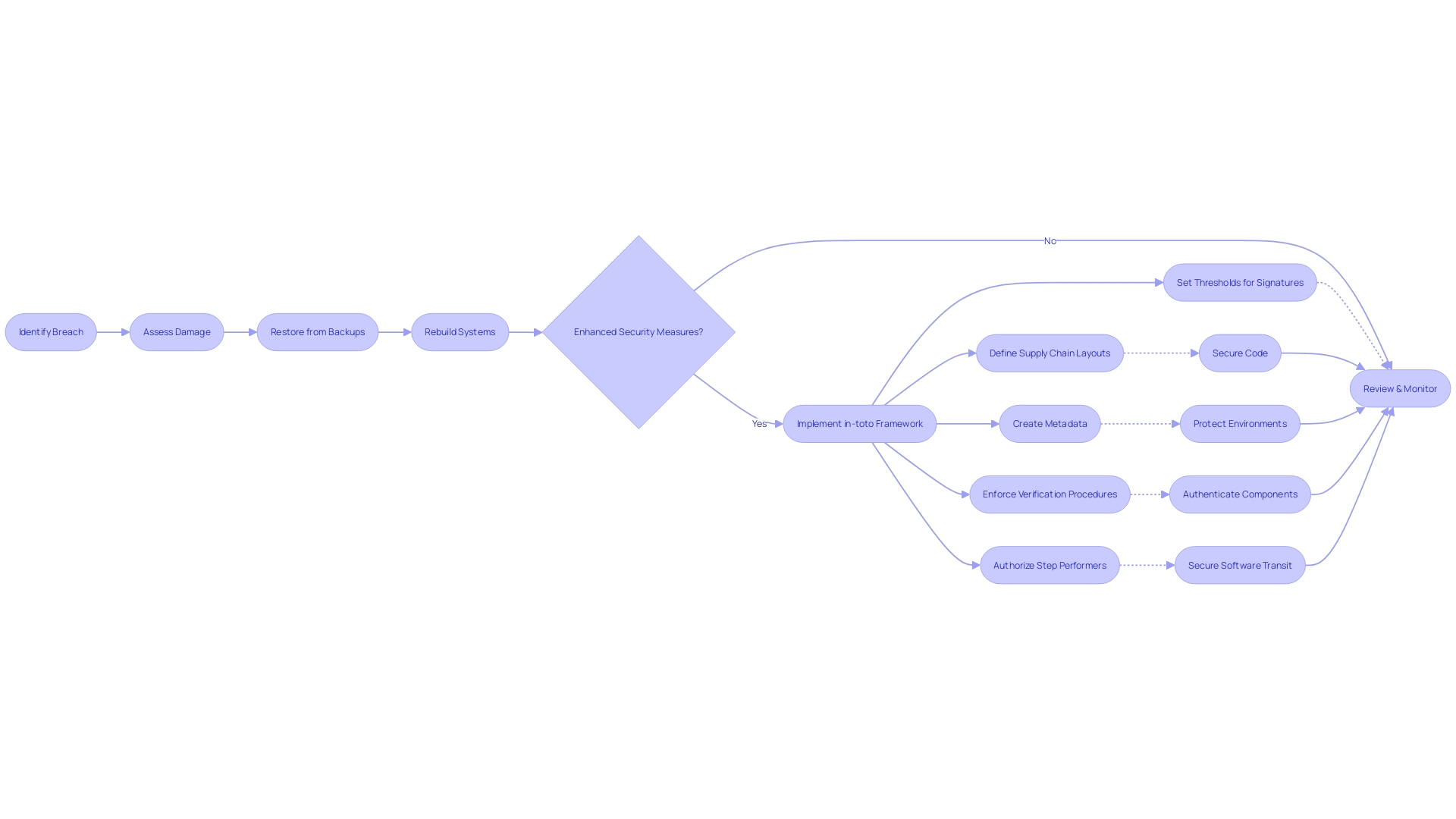
Recovery of Systems
Following the containment and eradication of a cybersecurity threat, attention shifts to the restoration of systems and services. This critical phase often includes restoring data from backups and rebuilding compromised systems. Equally important is the adoption of enhanced security measures to avert future breaches. A strategic approach to this recovery process can be seen in the implementation of frameworks such as in-toto. This open-source toolset plays a pivotal role by cryptographically securing the software supply chain, ensuring the integrity of each step from development to deployment. By employing cryptographically verifiable metadata and strictly defining the sequence of operations, in-toto establishes a robust defense against future incursions.
Recent occurrences, such as the security breach at Fortinet where unauthorized file access was detected, underscore the gravity of robust recovery protocols. Although the Fortinet event was promptly contained with no indication of customer impact, it serves as a stark reminder of the omnipresent risk to digital assets and the necessity of constant vigilance.
In these scenarios, preparedness is key. Embracing the 'jump bag' mindset, where vital tools for response are readily accessible, can save valuable time during a crisis. This concept has evolved from a physical kit to a metaphor for the immediate readiness required in today's cyber threat landscape. The possible harm from events, now frequently extending beyond data theft to destructive cyberattacks, requires a prompt and systematic recovery process to minimize operational and reputational damage.
The imperative to promptly restore services was exemplified by the Proximus data center fire in August 2023, which temporarily disrupted emergency service numbers. This situation demonstrated how every minute of downtime can have significant consequences, highlighting that an effective recovery strategy is not only about cost but can be a matter of life and death.
To summarize, when dealing with the consequences of cyber events, the emphasis on recuperation should be guided by comprehensive approaches and structures that guarantee the durability of systems against existing and upcoming dangers. The incorporation of frameworks like in-toto, along with a focus on cyber resiliency, can result in a more secure and dependable recovery pathway, ultimately protecting the mission and operations of the entity.
Post-Incident Activity
Post-incident activities are not simply a stage to conclude an event; they are a crucial phase where organizations distill valuable insights to enhance future resilience. This stage entails examining the occurrence, identifying the insights gained, and incorporating enhancements into the response framework. For example, when Graphite went through a brief outage, they not only provided a detailed report but also used the opportunity to strengthen their dedication to their community and customers, transforming a negative situation into a valuable learning experience.
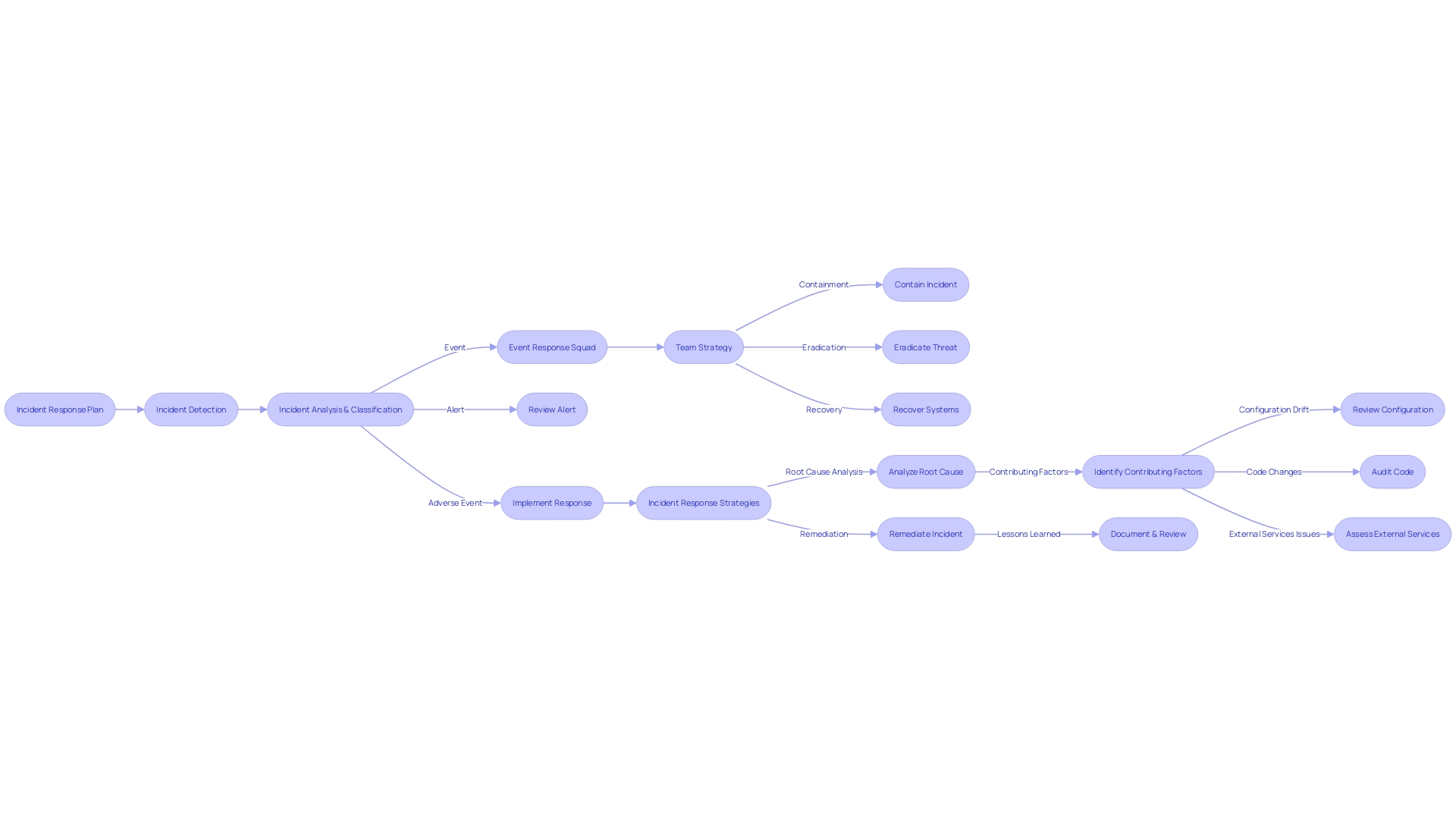
By analyzing events, such as the AWS SES limit increase request that was not initiated by the client, organizations can identify suspicious activities and take preventive measures against potential security breaches. This level of analysis is crucial to understand the contributing factors that led to the issue, such as configuration drift or unauthorized code changes, and why existing controls failed to catch these red flags.
The significance of a strong post-event examination is demonstrated by actual practices, such as keeping a 'jump bag' - a notion dating back to the early stages of handling unexpected situations, which includes all essential tools for prompt reaction. Today's digital 'jump bag' is essential for a quick and efficient response, aiming to minimize the harm and recover from cyber events rapidly.
Furthermore, companies such as Boeing show the importance of drawing lessons from occurrences by taking part in investigations like the Alaska Airlines flight 1282 case. Despite legal limitations, Boeing strives for transparency and applies learned insights across the company to enhance safety and operations.
Visual aids such as the Past Incidents heatmap offer a six-month look back on occurrences, assisting in identifying trends and occurrence rate, which are crucial in improving the reaction procedure. Furthermore, continuous testing and updating of the Incident Response Plan are vital to ensure its efficacy during actual emergencies. As industries evolve and threats diversify, organizations must regularly reassess and hone their reaction strategies, drawing from each experience to fortify their cyber defenses.
Post-Event Analysis and Lessons Learned
The process of thoroughly analyzing events in incident management is a meticulous procedure that examines the occurrence from various perspectives to determine the underlying cause, evaluate the consequences, and assess the efficiency of the reaction. It involves a comprehensive examination of occurrence reports, a deep dive into forensic data, and interviews with stakeholders. Through this analysis, crucial insights are gleaned, which inform the refinement of response strategies and protocols, ensuring continual improvement.
Digital Forensics and Incident Response (DFIR) experts, such as those involved in recent high-profile cases, understand the importance of readiness and having the right data at hand. When the unexpected happens, as with the BianLian ransomware group's activities or the large-scale data breach at Canadian firm Slim CD, the ability to swiftly and accurately determine the scope and scale of the breach is paramount. This involves evaluating the condition of impacted systems and data, which is crucial in effectively handling the situation.
As emphasized by the events involving our client's AWS situation, the importance of being forensic ready during a crisis cannot be emphasized enough. Surprises, like the unauthorized increase in SES sending limits, can signal deeper issues requiring immediate attention. Furthermore, the intricacy of response to unforeseen events intensifies during organizational changes such as mergers or restructuring, emphasizing the requirement for flexible and resilient Response Plans.
In the aftermath of an event, it's not just about understanding 'what went wrong,' but also about taking a constructive approach to future prevention and preparedness. This is echoed by the comprehensive report following the Robb Elementary School tragedy, which reconstructed a minute-by-minute timeline of the incident, offered recommendations for improvement, and honored the victims and survivors.
Ultimately, post-event analysis is an exercise in resilience, learning, and adaptation, aiming to fortify a company against future cybersecurity threats. It is a fundamental step in ensuring that lessons learned translate into concrete action, enhancing the overall security posture of the organization.
Improving Incident Response Capabilities
Improvements in addressing issues arise from a thorough comprehension of the lifecycle, from preparation to remediation. As we've delved into the Five Layers of Incident Response, the importance of a robust Case Tracking system becomes evident. It's the cohesive element that compiles all critical information, ensuring that each event is thoroughly documented and managed from detection to resolution. By implementing a well-defined Incident Response Plan (IRP), entities can streamline their response process, clearly delineate roles and responsibilities, and set forth communication protocols that are vital for effective management.
Reflecting on the insights from the Unit 42 report, it's clear that automation and AI are critical tools in preventing SOC burnout. These technologies allow for the reallocation of limited human resources to areas where their expertise is most impactful, improving operational efficiency. Moreover, through the examination of contributing factors like configuration drift or unauthorized code modifications, organizations can alleviate worsening problems that frequently accompany cyber events.
In order to gain valuable insights from previous occurrences, it is essential to inquire about the reasons behind the ineffectiveness of the existing preventive measures in addressing the underlying factors. This iterative questioning leads to the identification of underlying causes and aids in refining handling approaches. With advanced intelligence and analysis provided by teams like OODA, entities can receive tailored support in strategy, planning, and risk management, enhancing their overall security posture.
By implementing a design approach that focuses on the needs of individuals and is supported by influential figures in the field, it guarantees that the remedies are not only technologically viable but also in harmony with the individuals and procedures in the company. This alignment is crucial for building a resilient and responsive IT environment that can adapt to the evolving threat landscape and safeguard the organization's digital assets.
Appendix: Additional Resources for Incident Response
Organizations must be ready to quickly and efficiently address different events that can greatly impact the functioning, reliability, or accessibility of their information systems. Managing and mitigating the aftermath of security breaches, cyber attacks, or any other security-related occurrences is a critical aspect of cybersecurity, involving a structured approach. The secret to a prosperous occurrence reaction is in possessing a thorough, well-documented Incident Response Plan (IRP) that outlines distinct procedures for every phase of handling an occurrence.
The IRP should define roles and responsibilities, establish communication plans, and contain standardized response protocols to ensure clarity and efficiency. For example, during a situation, the central team usually consists of a Reporter who identifies the occurrence, a Keymaster who manages access to information, and a Fixer responsible for resolving the issue. It is also crucial to distinguish between occurrences, notifications, and situations within the plan to prevent confusion. Events are observed occurrences within a system or network, alerts are warnings triggered by specific events, and adverse events are confirmed events that require immediate attention.
Furthermore, an Event Response Squad (ERS) plays a crucial part in managing occurrences. This specialized group works collaboratively to identify, contain, and remedy the incident, minimizing its impact and restoring normal operations. The Incident Response Strategies they implement are tailored to the specific needs and objectives of the entity and are supported by the necessary tools to detect and counteract disruptive events effectively.
To maintain resilience against natural disasters, cyberattacks, or any disruptions, a strong Business Continuity Management (BCM) program is essential. BCM entails a proactive planning process that involves risk assessment, business impact analysis, and the development of policies and procedures to manage potential crises. The plan should cover various aspects such as people, facilities, legal responsibilities, financial implications, and reputation, ensuring the company's swift recovery.
Amidst the ever-changing security challenges, Security-as-a-Service has emerged as a valuable concept, allowing entities to acquire comprehensive security coverage and provide exceptional service through technological solutions. It represents an advanced approach in business continuity and crisis management, providing better value to stakeholders by leveraging technology for enhanced security operations.
When constructing an IRP, it is crucial to refer to industry standards, guidelines, and best practices for a more informed and effective plan. This involves comprehending the complexities of event handling processes, which steer entities through recognizing, categorizing, reacting to, and resolving occurrences. By incorporating these elements into their incident response strategies, organizations can ensure the continued resilience and security required in today's interconnected and technology-reliant world.
Conclusion
A comprehensive incident response strategy is crucial in the realm of cybersecurity. It serves as a proactive stance to protect organizations from evolving threats, maintain operational integrity, and ensure resilience. The NIST Incident Response Life Cycle provides a robust framework for effectively managing security incidents across various phases.
Preparation is key, involving the creation of a well-documented Incident Response Plan (IRP) that outlines roles, responsibilities, and communication strategies. Testing the IRP is equally important to ensure swift and well-coordinated responses. An incident response policy and function, supported by an incident management framework, govern the coordination and execution of incident response efforts.
Tools and resources such as advanced software, forensic tools, and partnerships with external entities enhance incident handling capabilities. Risk assessments and mitigation strategies help fortify defenses against security incidents, while security measures and user training work hand-in-hand to bolster cybersecurity. Detection and analysis techniques enable the timely identification and assessment of security breaches.
Identifying security incidents requires sophisticated monitoring systems and advanced threat detection methodologies. The containment, eradication, and recovery phases focus on halting the incident's spread, removing traces of attackers or malware, and restoring affected systems to full functionality. Post-incident activities involve reflective analysis, learning from past experiences, and integrating improvements into the incident response framework.
Finally, improving incident response capabilities requires a deep understanding of the lifecycle and the integration of automation, AI, and human-centered design approaches. By following these principles and utilizing additional resources, organizations can establish themselves as trusted authorities in the field and ensure their resilience against cyber threats.




