Introduction
In an era where cybersecurity threats are becoming increasingly sophisticated, the ability to respond effectively to incidents is paramount for any organization. An Incident Response Plan (IRP) serves as a critical component in this defensive strategy, providing a structured framework for detecting, responding to, and recovering from cybersecurity incidents. This article delves into the essentials of an IRP, explores the key components of the NIST Incident Response Framework, and highlights the importance of preparation, detection, containment, and continuous improvement.
By examining each phase of the NIST Incident Response Lifecycle, organizations can gain valuable insights into how to enhance their response capabilities. The focus will be on adopting best practices, leveraging advanced tools, and fostering a culture of continuous improvement to ensure a resilient cybersecurity posture. Understanding these elements is crucial for organizations aiming to minimize the impact of cybersecurity incidents and safeguard their critical assets.
What is an Incident Response Plan (IRP)?
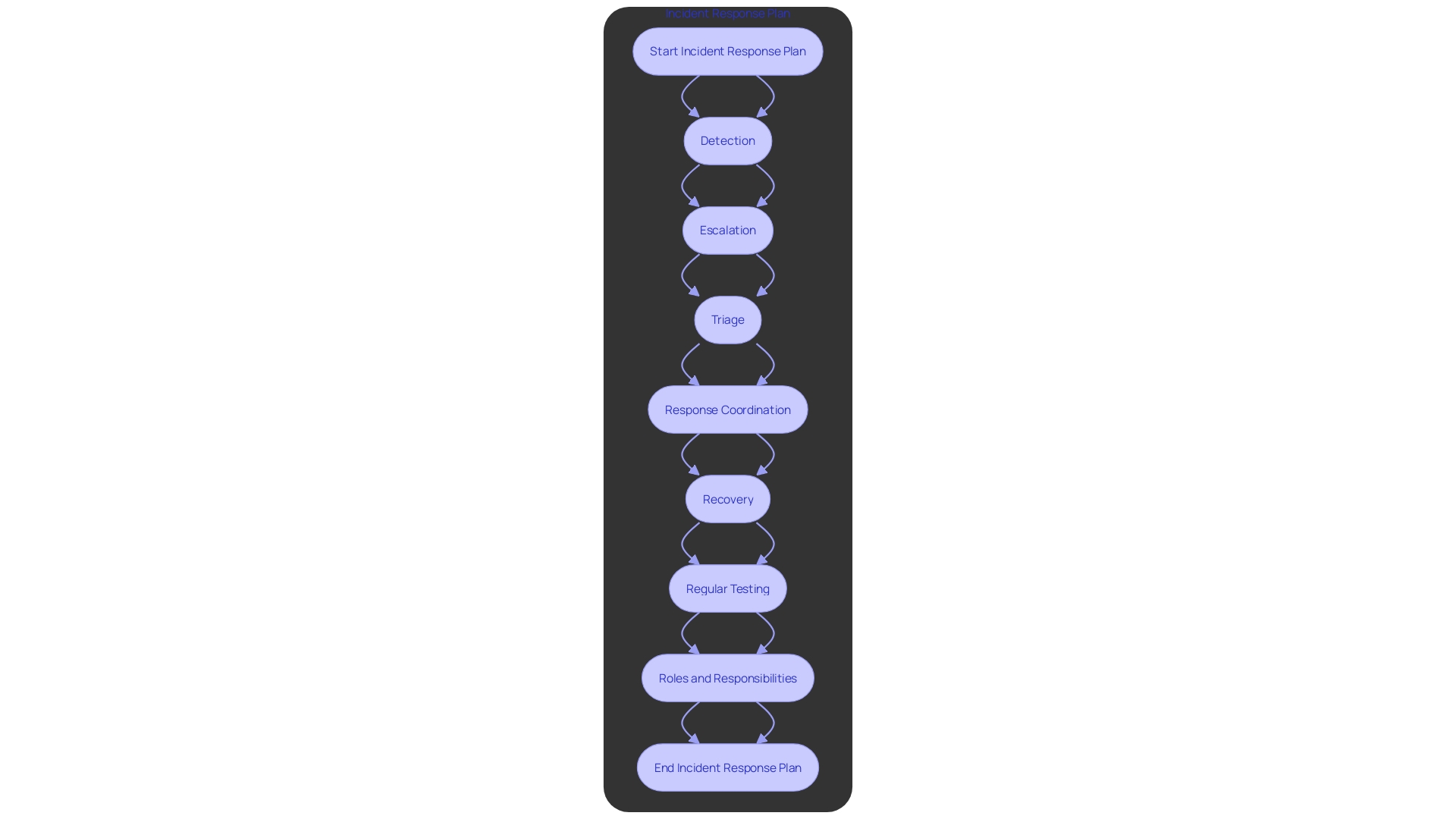
A Response Plan (IRP) is a recorded strategy that details extensive procedures for detecting, addressing, and recovering from cybersecurity events. This strategy is essential for entities to effectively handle events, reduce their effects, and guarantee a rapid restoration. It includes clearly defined roles and responsibilities, communication protocols, and escalation procedures, providing necessary clarity and structure during crises.
To enhance the effectiveness of an IRP, it is vital to regularly test its various sub-processes, such as escalation, triage, and alternative communication channels. By breaking down the plan into key processes and ranking them according to their criticality and testing effort, organizations can identify and address potential gaps. This guarantees the plan stays strong and executable during actual events.
Additionally, the IRP should use precise language to avoid ambiguities, especially in terms like 'event,' 'alert,' and 'incident.' Regular threat hunting and reviewing specific areas of the network for indicators of compromise can help in early detection and mitigation of potential threats. Collecting proof, coordinating responses, and developing timelines are crucial for efficient case monitoring and learning from previous events, ultimately enhancing the overall security stance.
Key Components of the NIST Incident Response Framework
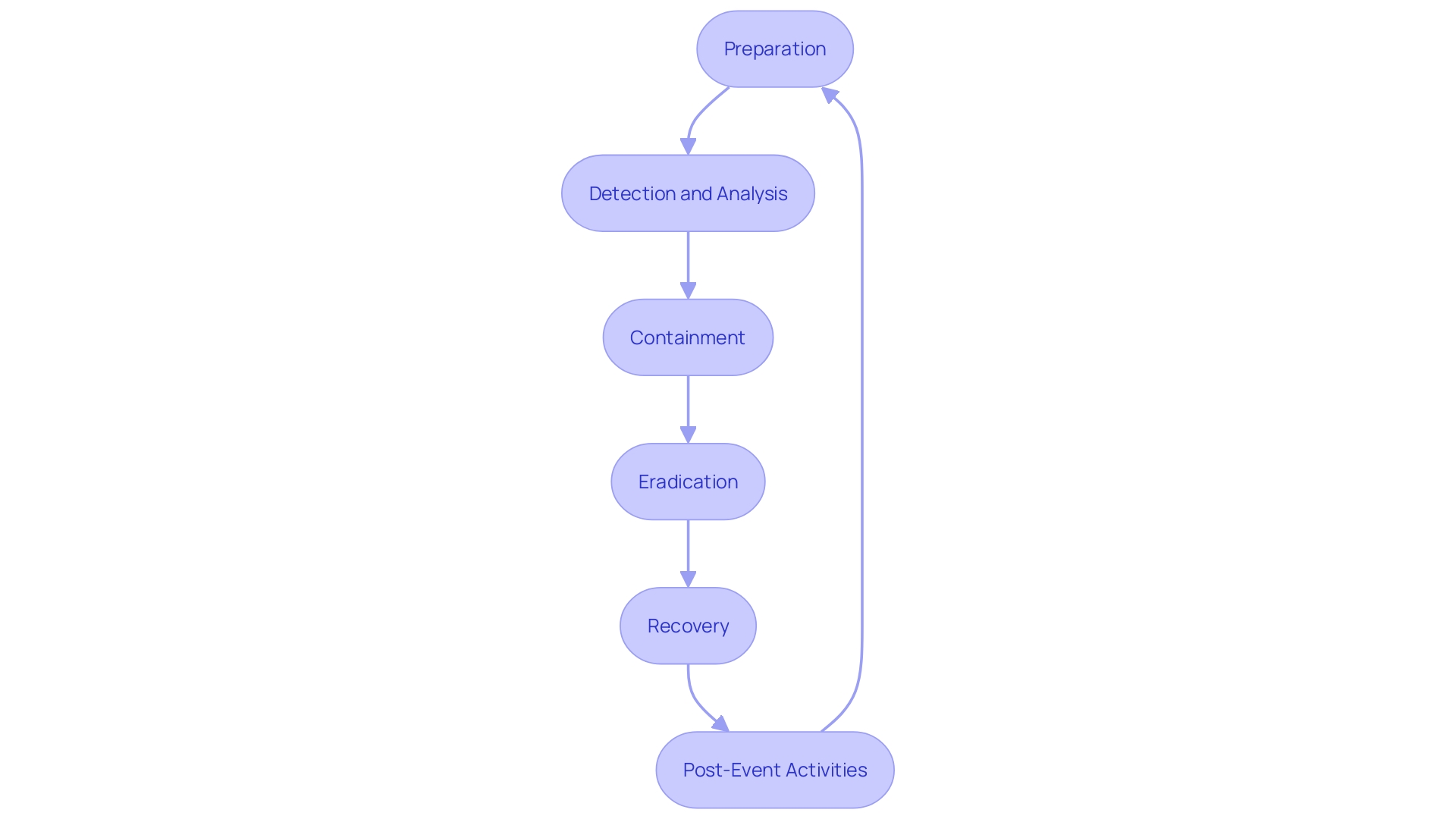
'The NIST Incident Response Framework is a structured approach that enables entities to manage cybersecurity incidents effectively.'. It is made up of several stages, each playing a pivotal role in reducing the impact of dangers. The initial stage, preparation, ensures that the organization is ready to respond at any moment. This involves planning, developing policies, and training personnel across various departments, including IT, legal, and HR.
Detection and analysis is the next critical phase, where the focus is on identifying potential threats and understanding their nature. This stage involves monitoring systems for unusual activities, such as spikes in network traffic or unauthorized access attempts, to promptly detect and analyze occurrences.
Once an incident is detected, the containment, eradication, and recovery phase begins. Here, the goal is to limit the damage, remove the threat, and restore normal operations. This stage requires a coordinated effort, utilizing documented plans, tools, and technologies to ensure a swift and effective reaction.
Ultimately, post-event activities include analyzing and gaining insights from the occurrence to enhance future actions. This cyclical process offers continuous learning and improvements, assisting entities in enhancing their strategies and better safeguarding against future events. The updated NIST Cybersecurity Framework 2.0 emphasizes governance and the importance of informed decision-making in cybersecurity strategy, reflecting the most recent challenges and best practices in the field.
Preparation and Prevention
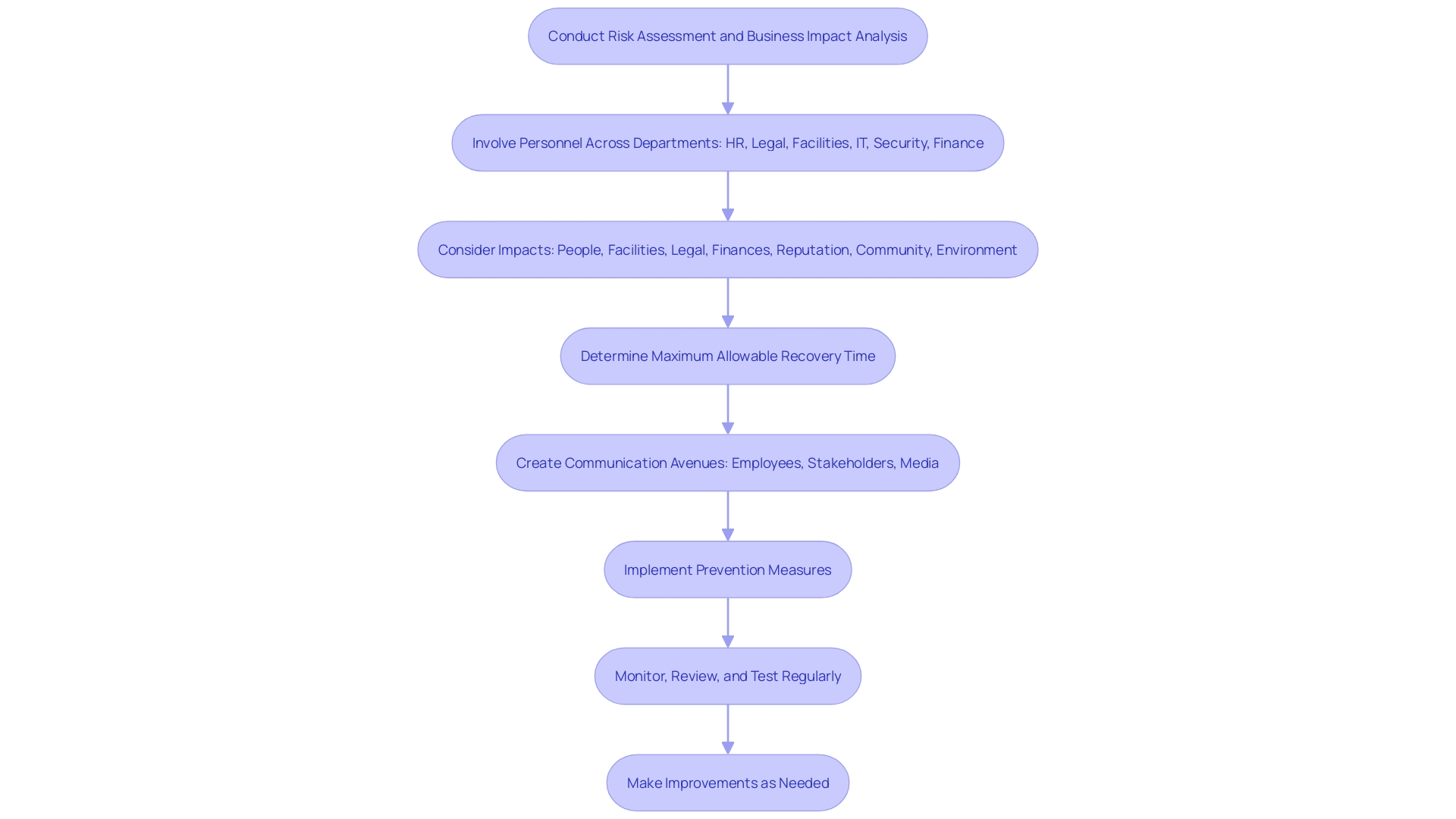
Creating and sustaining a proficient reaction ability is essential for any organization. 'This process begins with thorough risk assessments and business impact analyses, which help identify potential vulnerabilities and the maximum allowable time to recover from an event.'. Training personnel and conducting regular drills are essential steps to ensure readiness. Furthermore, creating a list of resources that may be aimed at during an event constitutes the foundation of a strong response strategy.
Prevention measures, such as vulnerability management and ongoing risk searching, are equally important. By proactively recognizing and tackling possible dangers, entities can significantly decrease the chance of occurrences happening. 'Access to services like Cisco Talos, which provides 24-hour emergency assistance capabilities, can further strengthen defenses and ensure rapid recovery in the event of a breach.'.
Integrating perspectives from different areas within the organization, such as IT, security, legal, and finance, can improve the overall efficiency of the response strategy. Regular monitoring, testing, and updating of the plan are crucial to adapt to evolving threats and maintain a state of preparedness.
Detection and Analysis
Detection and analysis represent pivotal stages in cybersecurity event management. During these phases, organizations utilize advanced monitoring and analytical tools to identify potential occurrences by scrutinizing security alerts and anomalies. 'This procedure involves a comprehensive analysis of information to determine the nature and extent of occurrences, facilitating informed decision-making for efficient action measures.'.
An AI-driven approach can significantly enhance these phases. For example, the incorporation of AI instruments such as Microsoft's Copilot for Security can enhance data examination, providing directed answers that speed up the recognition and comprehension of security issues. This is vital as the environment of cyber dangers keeps changing, requiring a strong and flexible framework for managing events.
The importance of thorough data analysis is echoed by industry experts. Organizing action plans and developing comprehensive schedules of events are crucial for efficient management of situations. This involves gathering artifacts and consolidating observations to build a comprehensive picture of the incident. Such meticulous tracking ensures that response actions are well-coordinated and effective.
Moreover, the role of risk intelligence cannot be overstated. Analysts must continually expand their knowledge of new and existing dangers, utilizing techniques to collect vital cyber risk intelligence. Identifying IP addresses used by malware, for example, can help update defenses and uncover related threat infrastructures.
Statistical data from recent studies reveal that entities only prevent 60% of attacks on average. This underscores the necessity of not only improving prevention measures but also enhancing detection capabilities. Healthcare institutions, recognized for their detection efficiency, act as a standard for other industries seeking to enhance their occurrence management strategies.
In summary, the detection and analysis phases are foundational to a proactive cybersecurity posture. Utilizing AI and comprehensive threat intelligence, along with careful event tracking, constitutes the foundation of a successful response strategy.
Containment, Eradication, and Recovery
Upon confirmation of an event, containment strategies are promptly executed to minimize its impact. This can involve isolating compromised systems or networks to prevent further damage. Once containment is achieved, the focus shifts to eradication, aiming to eliminate the root cause of the situation. For example, in one security operations center (SOC), unique stickers were used to mark each successfully intercepted red team, emphasizing the critical importance of identifying and neutralizing threats.
Following eradication, the recovery phase begins, where systems and services are restored to normal operations. This involves tackling any weaknesses to avert future occurrences. A notable initiative in this domain is the 'Business Continuity in a Box' developed by the Australian Cyber Security Center (ACSC), which provides a swift and secure way to re-establish critical business functions during or after a cyber event. Management must ensure that recovery plans are comprehensive, considering impacts on people, facilities, legal obligations, finances, reputation, and the environment. Regular reviews and updates of these plans are essential to maintain a resilient security posture.
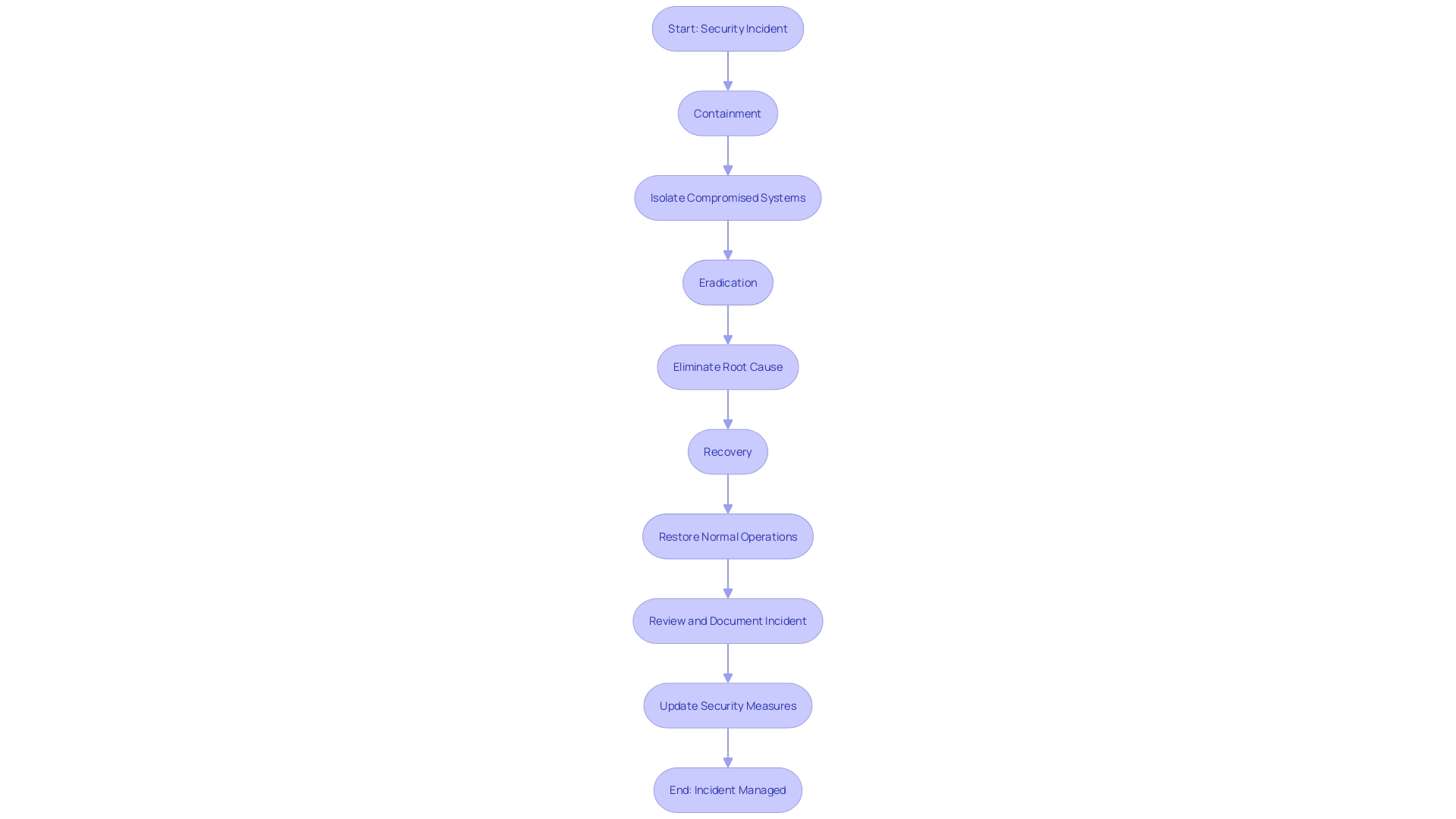
Post-Incident Activity
'Post-incident activities are critical for driving continuous improvement and strengthening a company's cybersecurity posture.'. This phase involves conducting a comprehensive review of the event, identifying lessons learned, and updating the Incident Response Plan (IRP) and security measures accordingly. Effective post-incident reviews (PIRs) offer a structured framework for transforming failures into valuable learning opportunities. According to industry experts, 'Incidents are unavoidable... what distinguishes successful entities is their method of managing and learning from them.'
Testing and refining the IRP is essential for identifying gaps and ensuring its effectiveness during actual events. By breaking down the IRP into key processes—such as escalation, triage, and activation of alternative communication channels—and ranking them by criticality, organizations can systematically test and enhance their capability to react. This repetitive method not only improves future situations handling but also adds to a stronger security stance.
Additionally, incorporating digital forensics and incident response (DFIR) techniques can provide deeper insights into the incident, revealing how attackers infiltrated networks and moved laterally. This data-driven analysis assists entities in understanding potential vulnerabilities and refining their defenses. As noted, 'A deep understanding of today’s threat landscape can help you guide your team and your entity to a strong and resilient security posture.' Embracing these post-event activities ensures that every occurrence becomes a stepping stone toward a more secure and prepared organization.
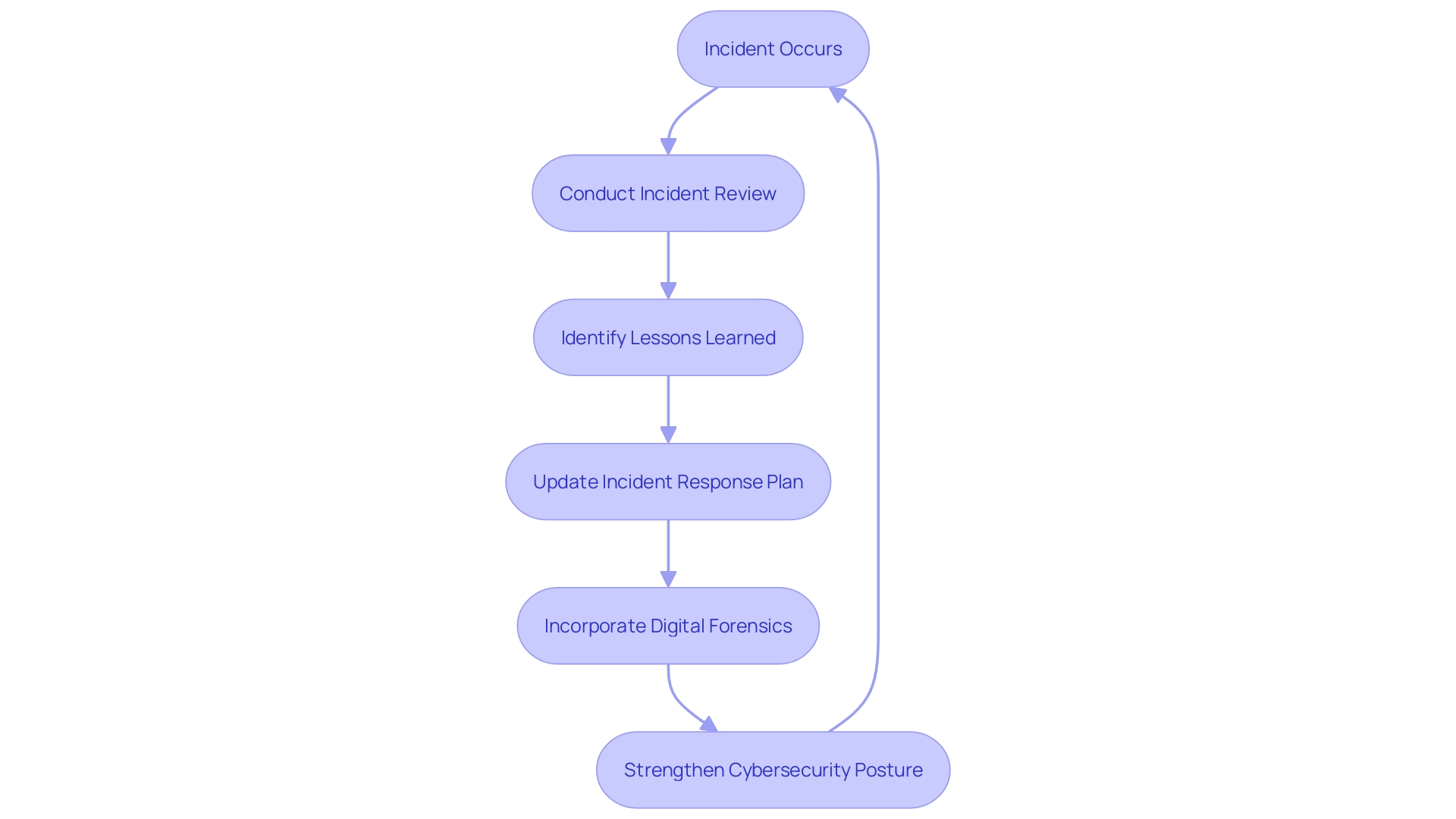
NIST Incident Response Lifecycle
The NIST Incident Management Lifecycle offers an organized method for handling cybersecurity events, highlighting an ongoing cycle of preparation, detection, reaction, and recovery. Preparation includes creating an event management strategy, utilizing available resources, and collaborating with the cybersecurity community. Detection and analysis require timely reporting and comprehensive analysis to understand the incident's scope and impact. Containment, eradication, and recovery focus on coordinated messaging, information sharing, and remediation efforts. Post-incident activities involve evidence preservation and lessons learned to enhance future actions. This flexible structure allows entities to develop their strategies based on previous experiences and new challenges, ensuring strong and resilient cybersecurity practices.
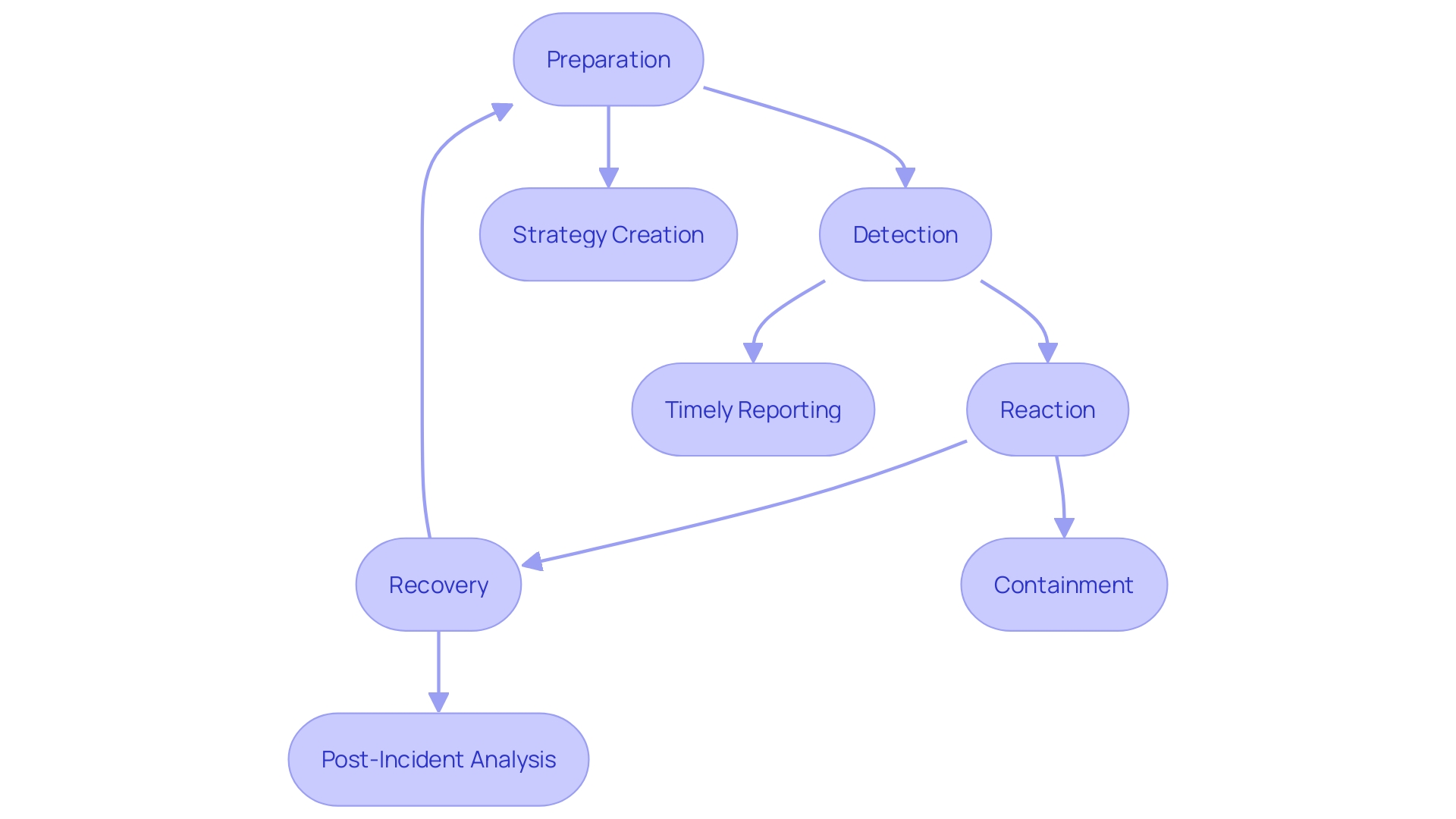
Importance of Continuous Improvement
Ongoing enhancement is essential for sustaining efficient and pertinent response abilities within a company. This process entails regularly assessing and updating the Incident Response Plan (IRP) based on insights gained from past incidents and evolving threat landscapes. For instance, Guthrie Clinic’s holistic approach in addressing community health through preventive care and wellness programs can serve as a blueprint for how entities should adapt and refine their cybersecurity measures. By fostering a culture that prioritizes feedback and innovation, entities can ensure that their cybersecurity practices remain dynamic and effective.
Incorporating both qualitative and quantitative metrics can significantly enhance communication and decision-making within the entity. As outlined in recent NIST publications, moving from vague risk descriptions to data-driven metrics helps bridge the understanding gap between technical teams and management. For instance, evaluating factors such as response time, resource allocation, and the impact on business operations can provide a clearer picture of the IRP's effectiveness.
Moreover, the adoption of comprehensive IT solutions and human-centered design approaches, as demonstrated by Charter's successful digital transformations, underscores the importance of aligning people, processes, and technologies. This alignment not only enhances operational performance but also updates business practices, allowing entities to respond efficiently and effectively to cybersecurity challenges. Promoting a culture that values continuous improvement and innovation in cybersecurity practices is essential for staying ahead in an ever-changing threat landscape.
NIST Cybersecurity Framework (CSF) and Incident Response
The NIST Cybersecurity Framework (CSF) significantly enhances the Incident Response Framework by providing comprehensive guidelines for managing cybersecurity risk across various functions. The recently updated CSF 2.0 now encompasses six key functions: Identify, Protect, Detect, Respond, Recover, and the newly added Govern. This addition underscores the importance of governance and leadership in cybersecurity management, ensuring that senior leaders consider cybersecurity as a critical enterprise risk alongside finance and reputation.
Incorporating the CSF with occurrence management procedures allows entities to create a more unified and data-oriented strategy for cybersecurity. By shifting from qualitative descriptions of risk to quantitative ones, groups can bridge gaps in understanding and enhance communication between technical teams and management. For instance, metrics on response times and resource allocation can offer valuable insights into the effectiveness and efficiency of incident handling.
Furthermore, the CSF 2.0's expanded scope now encompasses all entities, regardless of their cybersecurity sophistication, supporting the implementation of the National Cybersecurity Strategy. This makes the framework not only relevant to critical infrastructure but also applicable to a broader range of sectors, enhancing overall resilience against cybersecurity threats.
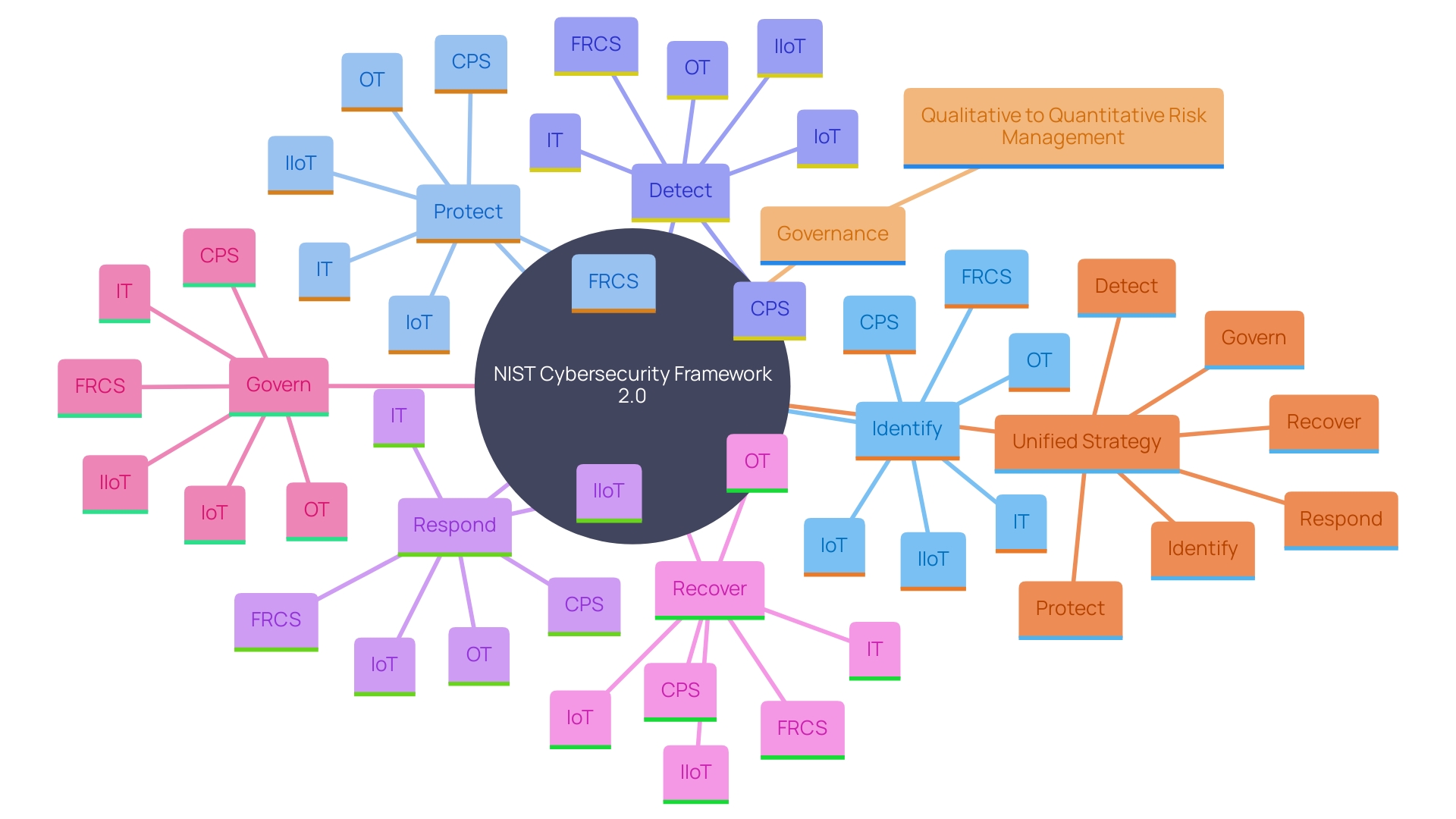
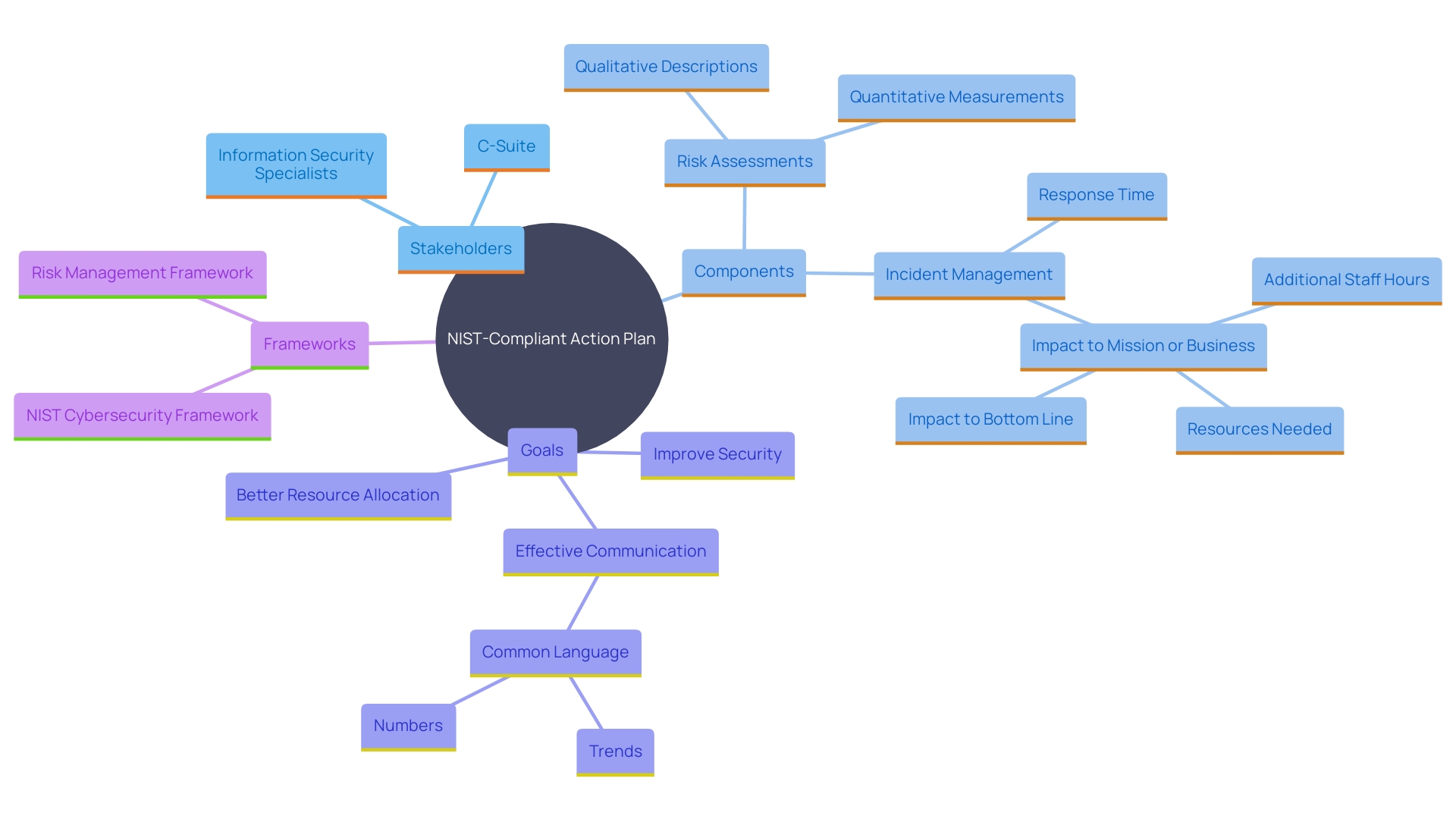
Building a NIST-Compliant Incident Response Plan
Creating a NIST-compliant action plan requires a thorough understanding of both NIST standards and the specific needs of the entity. Key stakeholders from various departments should be involved to ensure a holistic approach. Conducting risk assessments is crucial, as they provide data-driven insights into vulnerabilities and potential impacts. Regular testing and updates of the plan are essential to maintain its effectiveness and relevance.
A well-organized incident management strategy not only enhances the entity's capability to handle incidents effectively but also emphasizes a dedication to cybersecurity best practices. As NIST highlights, focusing on both qualitative and quantitative measurements aids in better communication of security status and resource allocation. Measurements such as reaction time, additional staff hours, and resource utilization can be crucial in evaluating the effect on the business and pinpointing areas for enhancement. This approach aligns with NIST’s guidance, which encourages moving from vague risk descriptions to clear, data-driven insights, enhancing both internal communication and decision-making processes.
For instance, NIST's Katherine Schroeder emphasizes the importance of using data over vague concepts, stating, “Our goal is to help people communicate with data instead of vague concepts.” By adhering to this principle, organizations can present a coherent and actionable picture of their cybersecurity posture, making it easier to communicate with both technical teams and management.
Best Practices for Incident Response Teams
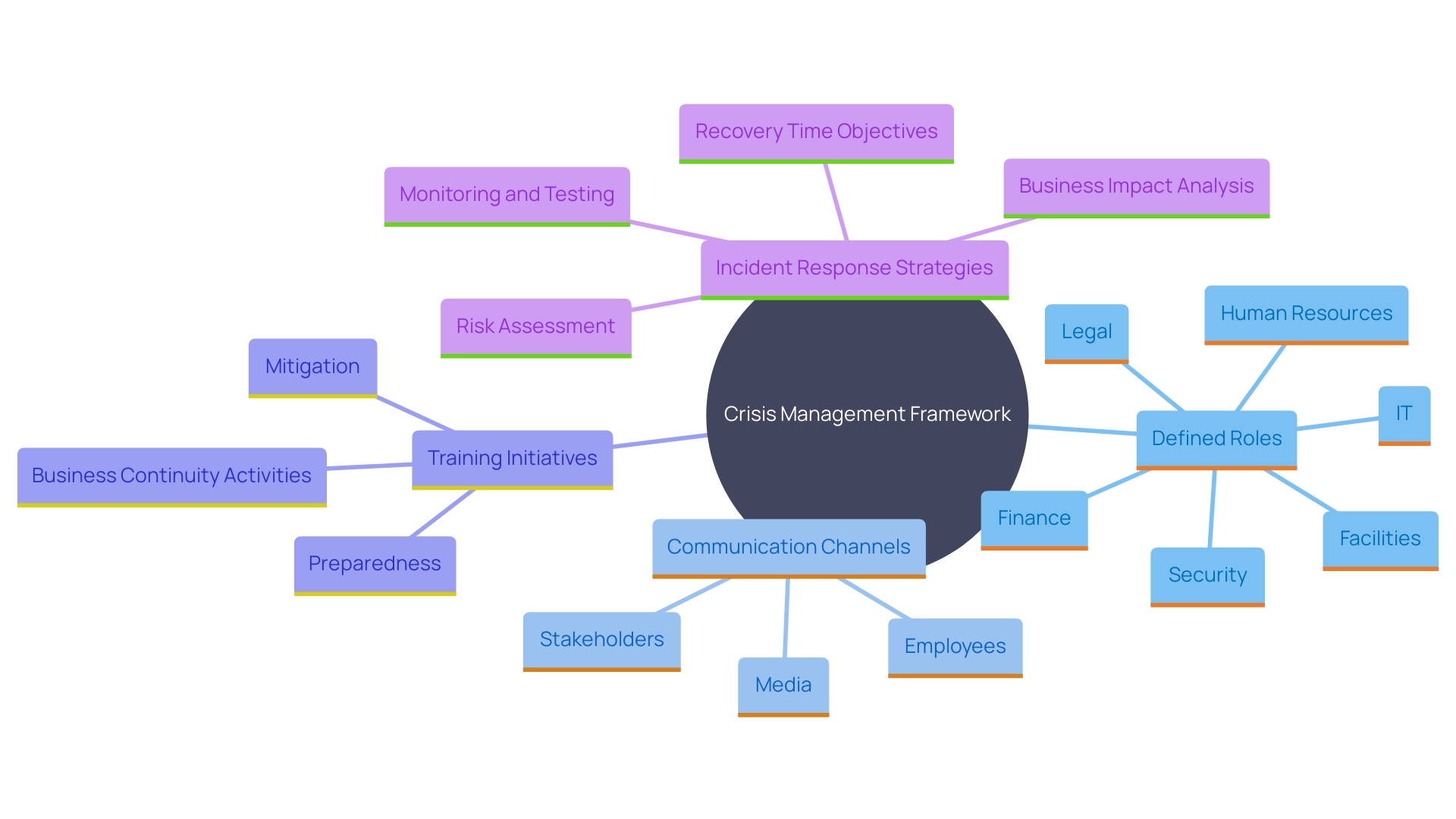
Efficient crisis management groups must function with accuracy, employing a clearly outlined organizational framework and thorough training. Key elements include clearly defined roles and responsibilities, robust communication channels, and continuous education initiatives. Regular training sessions and simulations are crucial for maintaining readiness and ensuring team members can act decisively. 'Collaboration across departments further strengthens the response mechanism, allowing for a coordinated and efficient approach to managing events.'.
Making sure every team member comprehends the differences among terms such as security event, security occurrence, and attack aids in avoiding expensive misconceptions. A security occurrence refers to a confirmed breach, while a security event may simply indicate unusual network behavior, such as a sudden spike in traffic. By defining these terms clearly within documented plans and playbooks, entities can streamline efforts and enhance overall efficiency.
A holistic approach that includes roles for senior management, legal teams, HR, and the wider IT department is essential. This strategy aligns with the broader principles of incident management, encompassing both preparation and response. Documented procedures, regular reviews, and the integration of advanced tools and technologies are fundamental to this process.
Consider a scenario where an organization detects an anomaly in network traffic. Incident responders, trained to apply deductive reasoning, would explore various hypotheses, such as a distributed denial of service (DDoS) attack or data exfiltration. By systematically assessing evidence, including data types, traffic timing, and external communications, responders can accurately determine the nature of the attack. This methodical approach ensures that threats are categorized and addressed appropriately, preventing escalation and mitigating impact.
Conclusion
The significance of a well-structured Incident Response Plan (IRP) cannot be overstated in today's cybersecurity landscape. Organizations must recognize that the ability to effectively detect, respond to, and recover from incidents is foundational to minimizing their impact. A comprehensive IRP not only delineates roles, responsibilities, and communication protocols but also emphasizes the importance of regular testing and updates to adapt to evolving threats.
The NIST Incident Response Framework serves as a robust guide for organizations, outlining essential phases such as preparation, detection, containment, eradication, and post-incident activities. Each stage is critical for establishing a proactive stance against cybersecurity threats. By fostering a culture of continuous improvement, organizations can learn from past incidents, refine their IRPs, and enhance their overall security posture.
Moreover, the integration of advanced technologies, such as AI-driven analysis tools, plays a pivotal role in enhancing detection and response capabilities. As the threat landscape continues to evolve, organizations must prioritize the alignment of their incident response strategies with established frameworks like the NIST Cybersecurity Framework (CSF). This alignment ensures a coherent approach to managing risks and reinforces the importance of governance in cybersecurity management.
Ultimately, the journey toward a resilient cybersecurity posture is ongoing. Organizations must remain vigilant, continuously assess their preparedness, and adapt their incident response strategies to meet emerging challenges. By investing in a comprehensive IRP and embracing best practices, organizations can navigate the complexities of cybersecurity incidents with greater confidence and effectiveness.




