Introduction
In the ever-evolving landscape of cybersecurity, incident response plays a pivotal role in safeguarding organizational assets and maintaining stakeholder trust. Effective incident response strategies not only mitigate the immediate impacts of security breaches but also fortify long-term resilience against cyber threats. Prioritizing incident response allows organizations to protect sensitive data, comply with regulatory requirements, and ensure continuous business operations.
This article delves into the critical components of an incident response plan, explores the NIST Incident Response Lifecycle, and provides actionable insights on implementing these guidelines to enhance your organization's cybersecurity posture.
Understanding the Importance of Incident Response
'Incident management is a critical component of a robust cybersecurity framework.'. The capacity to react efficiently to events can significantly reduce the effects of security breaches and other cyber threats. Entities that emphasize crisis management not only safeguard their confidential information but also uphold customer confidence and adhere to regulations. A well-defined incident response strategy ensures that organizations can quickly identify, analyze, and remediate incidents, minimizing downtime and resource loss. This involves a comprehensive plan that includes preparation, detection and analysis, containment, eradication, and recovery stages.
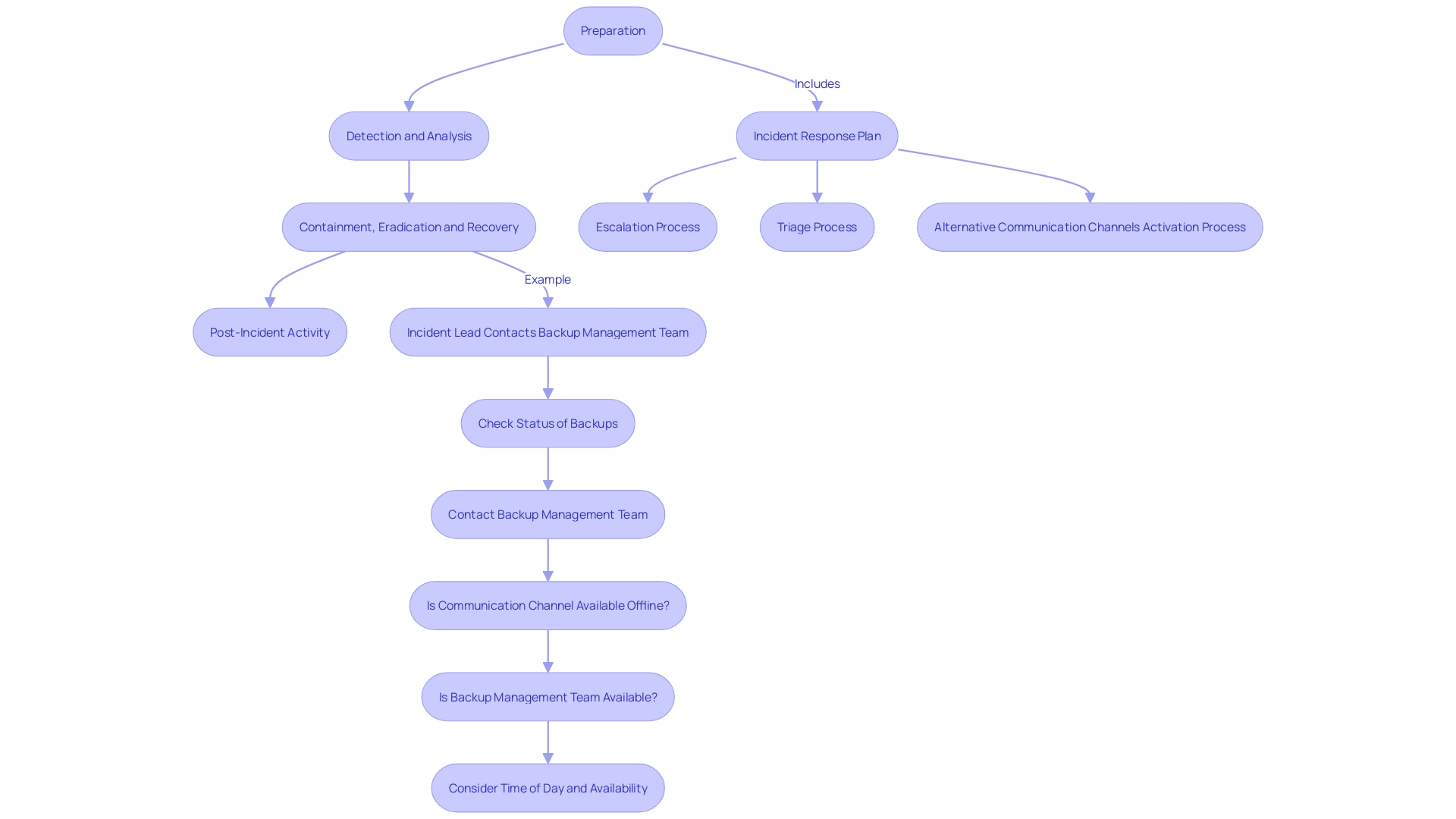
For instance, during the containment phase, it is essential to remove dangers as soon as they are recognized, even if other risks persist. This approach helps to prevent further spread and potential damage. As per SANS guidelines, the event management lifecycle includes ongoing surveillance and enhancement of security protocols to adjust to changing risks.
Moreover, regulations such as NIS2 require timely notifications of occurrences, often within 24 hours, necessitating a collaborative effort between technical and legal teams. Evaluating the occurrence management strategy frequently is crucial to guarantee its efficiency. It should include various sub-processes like escalation, triage, and activation of alternative communication channels.
Statistics indicate that data breaches are the most harmful category of cyber events, with an average loss of -1.3% (USD -1.9 billion) over the last decade. The health sector is notably sensitive, with an average loss of -5.21% (USD -1.2 billion) in data breaches. Consequently, possessing a strong plan for addressing issues is not only about quick action but also about strategic avoidance and enduring strength.
Key Components of an Incident Response Plan
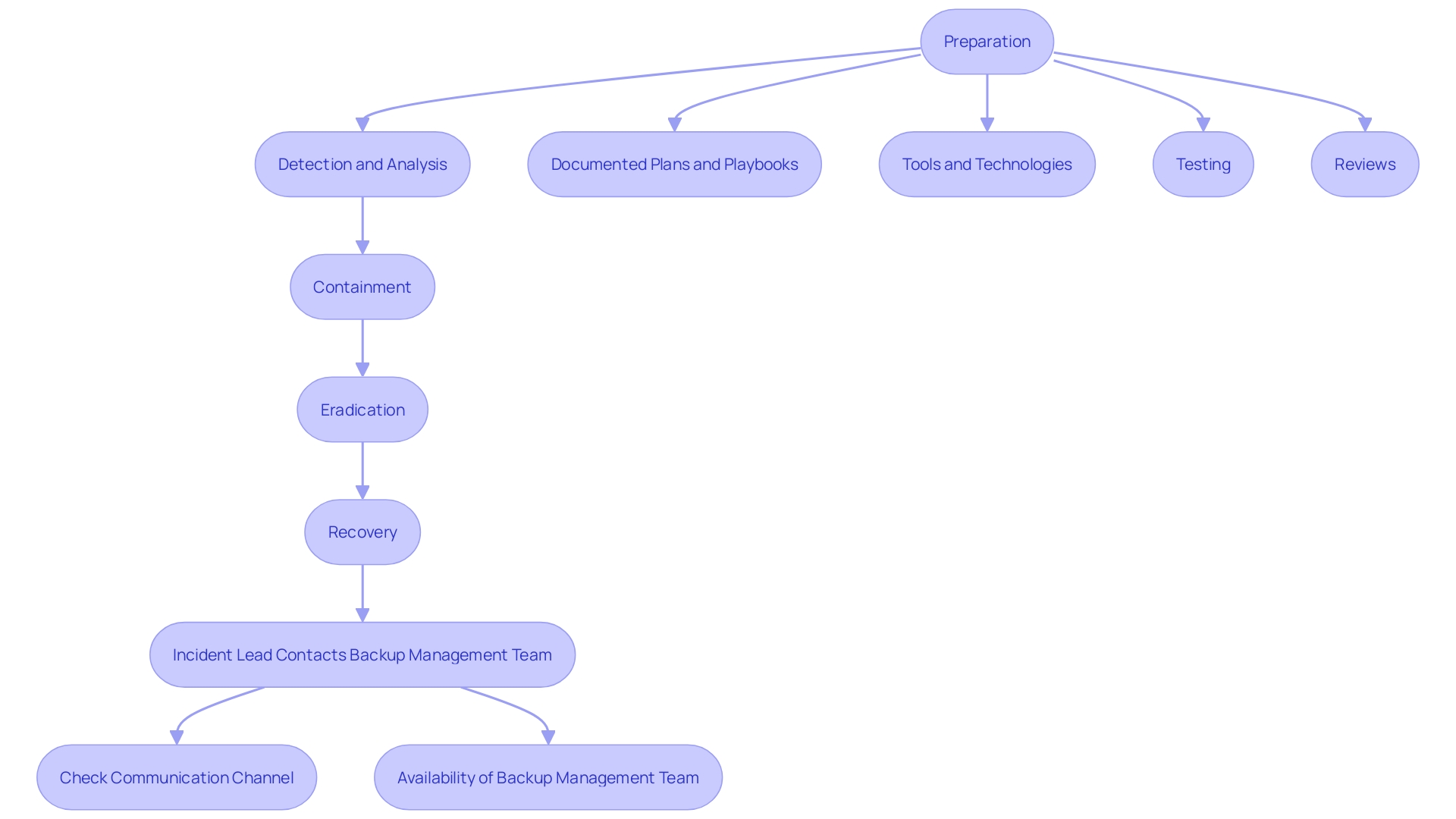
A successful crisis management strategy (CMS) is crucial for any organization aiming to handle and reduce the effects of cybersecurity events effectively. Key components of an IRP include preparation, detection, containment, eradication, recovery, and post-incident activities.
Preparation involves establishing detailed policies, procedures, and documented plans to ensure readiness. This phase includes assembling a diverse team from across the organization, such as senior management, legal representatives, and communication specialists. The executive sponsor, frequently a Chief Security Officer (CSO) or Chief Information Security Officer (CISO), plays a vital role in promoting the crisis management initiative and updating the executive team on progress. The event response manager organizes the overall strategy and activities, ensuring a cohesive approach.
Detection concentrates on recognizing possible occurrences through continuous monitoring and advanced threat intelligence. This step is crucial for timely intervention and involves utilizing state-of-the-art tools and technologies.
Containment aims to limit the damage caused by an event, employing strategies to isolate affected systems and prevent further spread. The containment stage is essential for preserving business continuity and reducing operational interruptions.
Eradication involves removing the danger from the environment, ensuring that the root cause of the incident is addressed. This phase works hand-in-hand with recovery, as both are necessary to restore normal operations.
Recovery ensures systems are brought back to normal functioning, with validated data integrity and system security. This step often includes restoring systems from backups and conducting thorough testing to confirm that the threat has been fully eliminated.
Post-event actions concentrate on gaining insights from the occurrence to enhance future reactions. This involves performing a thorough examination of the event, revising response plans, and improving strategies to boost overall resilience.
The IRP should be consistently evaluated and examined to adjust to changing risks and enhance effectiveness. By taking a comprehensive approach to event management, involving all relevant departments and stakeholders, organizations can ensure a robust defense against potential cyber threats.
The NIST Incident Response Lifecycle
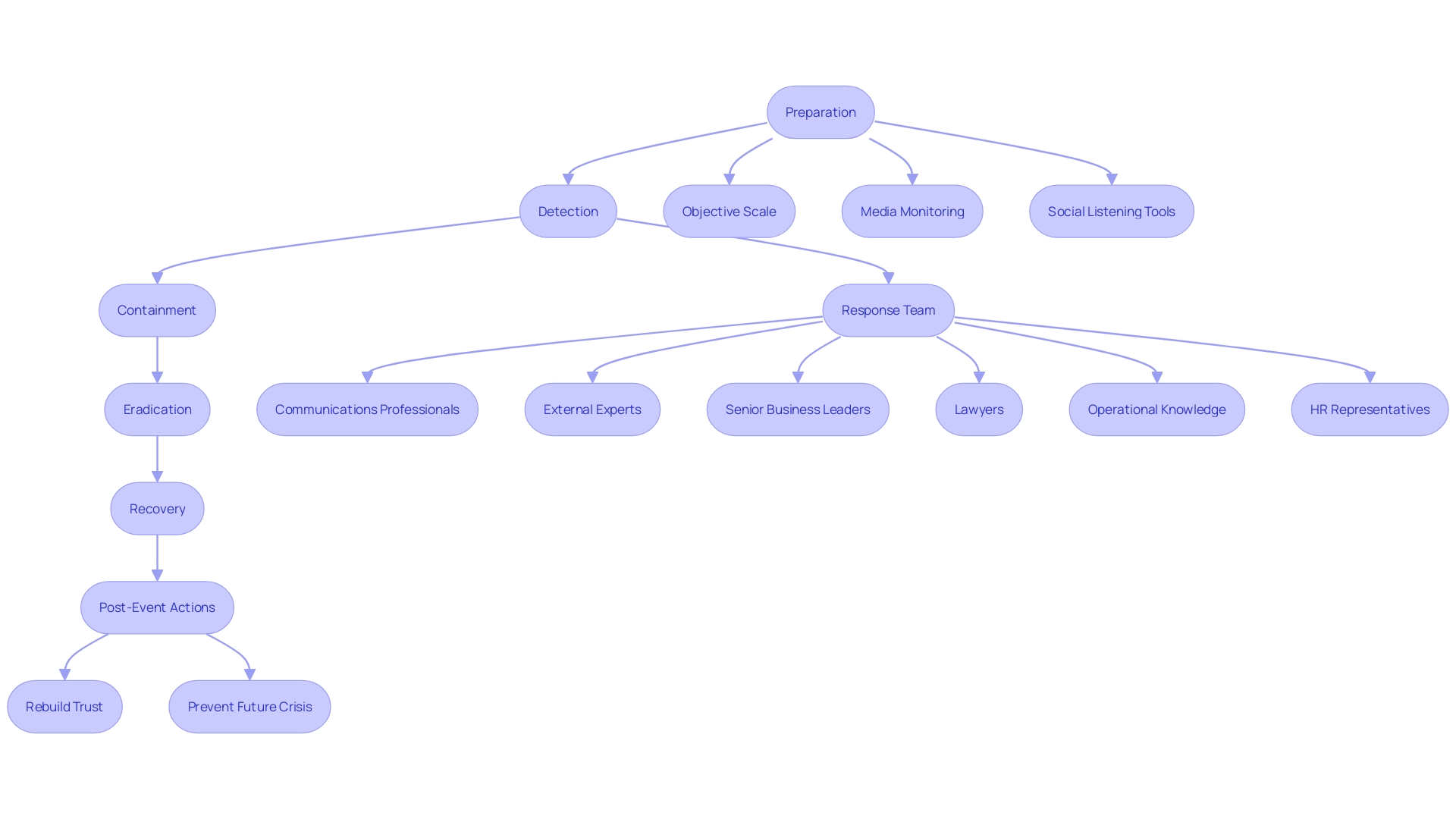
The NIST Incident Response Lifecycle provides a comprehensive framework to effectively manage and respond to security events. This organized method comprises four main stages: Preparation, Detection and Analysis, Containment, Eradication and Recovery, and Post-Incident Activity. Every stage is carefully crafted to lead organizations through a structured event management procedure, guaranteeing a swift and effective reaction to any security risks.
During the Preparation stage, organizations develop and enhance their reaction capabilities, including outlining roles and responsibilities, and ensuring essential tools and resources are available. This stage is essential for proactive risk management and establishes the foundation for a strong strategy.
The Detection and Analysis stage involves identifying and understanding the nature of the incident. This stage is critical for minimizing damage, as accurate and timely detection allows for quicker response actions. Employing advanced monitoring tools and intelligence about risks can significantly improve an organization's capacity to identify and examine possible dangers efficiently.
Once an occurrence is identified, the Containment, Eradication, and Recovery stages ensure that the threat is confined to prevent further damage, eliminated to remove the menace from the environment, and recovery actions are undertaken to restore normal operations. 'This stage requires a well-coordinated effort to mitigate the impact and ensure business continuity.'.
Ultimately, the Post-Incident Activity stage emphasizes gaining insights from the occurrence to enhance future action efforts. This requires comprehensive documentation, examination of the occurrence management process, and revising the event handling plan based on insights gained.
By following the NIST Incident Management Lifecycle, organizations can improve their overall handling abilities, ensuring a systematic and efficient method for managing security issues. This lifecycle not only aids in reducing the effect of events but also plays a crucial role in sustaining organizational resilience and trust among stakeholders.
Implementing NIST Guidelines in Your Organization
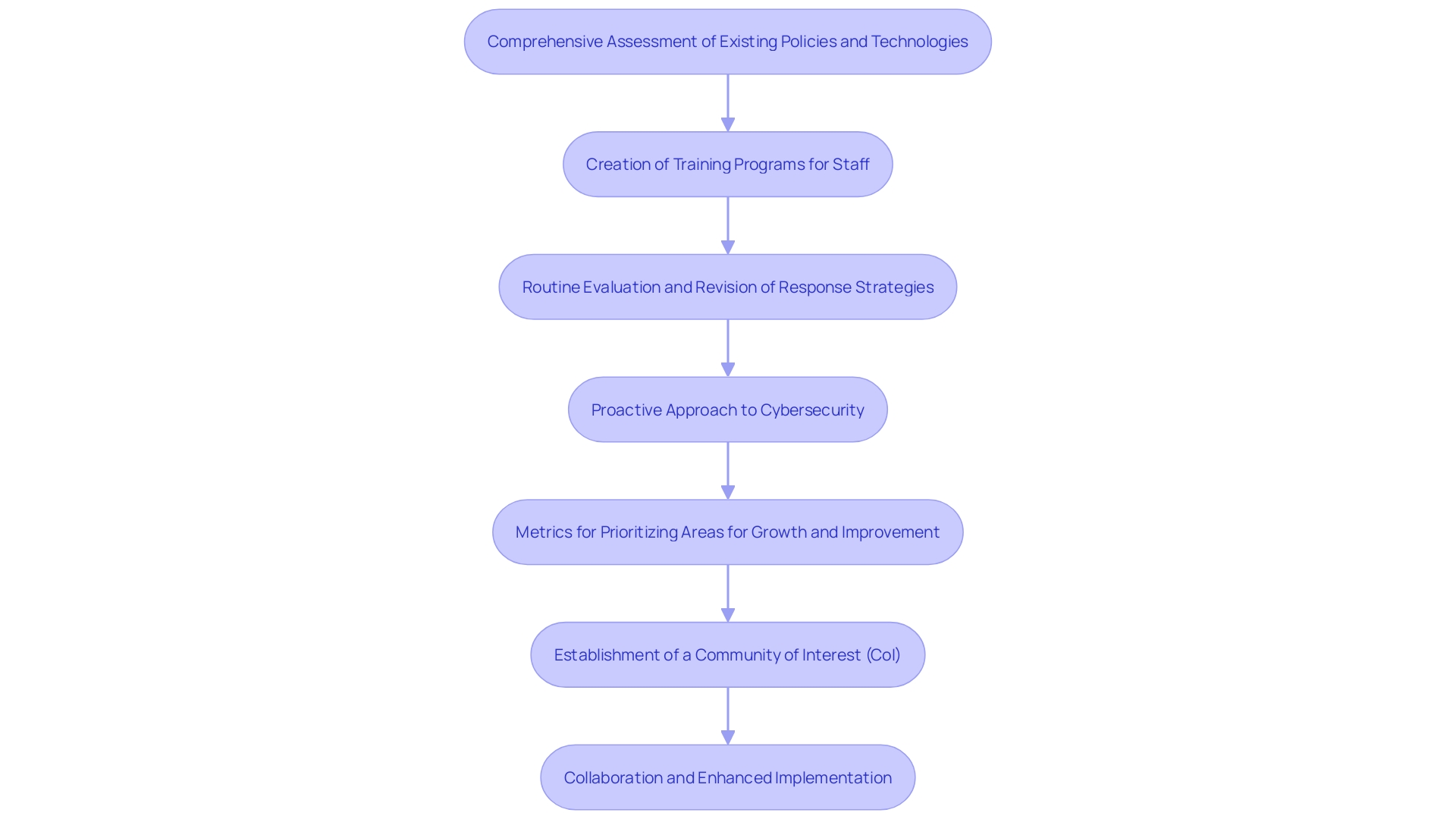
Implementing the NIST guidelines effectively requires a customized approach tailored to the unique business needs and risk profiles of an organization. Begin by conducting a comprehensive assessment of current policies, procedures, and technologies to identify gaps and areas for improvement. Subsequently, it is crucial to create and implement strong training programs, ensuring that all staff comprehend the event management plan and their specific responsibilities during a situation. Routine evaluation and revision of the response strategy are essential to address new dangers and weaknesses. This proactive approach ensures that the organization remains resilient against cyber incidents. According to NIST, metrics can play a vital role in this process by providing a common language for communication between technical teams and management, helping to evaluate the effectiveness and efficiency of controls and procedures. Establishing a Community of Interest (Coi) can further enhance this process by fostering collaboration and sharing of expertise among organizations.
Conclusion
Incident response is undeniably a cornerstone of effective cybersecurity management, integral to protecting organizational assets and maintaining stakeholder confidence. As explored throughout this article, a well-structured incident response plan encompasses multiple phases, including preparation, detection, containment, eradication, recovery, and post-incident activities. Each component plays a crucial role in minimizing the impact of security breaches while fostering a culture of resilience within the organization.
The NIST Incident Response Lifecycle provides a robust framework for organizations to systematically approach incident management. By adhering to its principles, organizations can enhance their preparedness and response capabilities, ensuring swift action against evolving cyber threats. Continuous monitoring, regular training, and updating of incident response strategies are essential to adapting to the ever-changing landscape of cyber risks.
Ultimately, investing in a comprehensive incident response strategy not only mitigates immediate threats but also builds long-term resilience. Organizations that prioritize incident response are better equipped to safeguard sensitive data, comply with regulatory requirements, and maintain operational continuity. By fostering collaboration and leveraging best practices, organizations can establish a formidable defense against potential cyber incidents, securing their position in an increasingly interconnected digital landscape.




