Introduction
In an age where digital interactions dominate the business landscape, the establishment of an Acceptable Use Policy (AUP) has become imperative for organizations striving to protect their technological resources and sensitive information. This foundational framework not only delineates acceptable behavior in the use of computers, mobile devices, and digital communication platforms, but it also serves as a critical tool for mitigating risks associated with cybersecurity threats.
As organizations face increasing challenges from evolving technologies and shifting work environments, understanding the nuances of AUPs is essential. This article delves into the significance of AUPs, outlining their role in safeguarding organizational integrity, compliance, and productivity while providing actionable steps for effective implementation.
Through an exploration of common challenges and future trends, businesses can better equip themselves to navigate the complex landscape of digital security and foster a culture of accountability and awareness among employees.
Defining Acceptable Use Policy: What Businesses Need to Know
An Acceptable Use Policy (AUP) emphasizes the importance of acceptable use policy by serving as a foundational framework that sets forth rules and guidelines governing acceptable behavior when utilizing a company's technological resources. These policies encompass various areas, including the use of computers, mobile devices, internet access, email, and other digital communication platforms. The primary objective of an AUP highlights the importance of acceptable use policy in safeguarding the entity's assets, data integrity, and reputation, ensuring that employees are acutely aware of their responsibilities when engaging with technology.
The importance of acceptable use policy is evident, as a robustly defined AUP not only mitigates risks associated with misuse, abuse, or illegal activities conducted via the entity's technology resources, but it also aligns with broader corporate strategies. Recent statistics indicate that over 40% of companies experience returns that are at least double their investments in privacy initiatives, underscoring the financial benefits of maintaining an effective AUP. Furthermore, with 48% of organizations reportedly entering non-public information into generative AI, the importance of acceptable use policy in contemporary settings is crucial and cannot be overstated.
The importance of acceptable use policy lies in its ability to inform staff about cybersecurity, enhance productivity, and ensure compliance with legal standards. For example, a case study titled 'Benefits of Implementing an AUP' illustrates how a well-defined AUP not only limits organizational liability in instances of misconduct but also helps control data backup costs. This case study emphasizes the importance of acceptable use policy, demonstrating that entities implementing AUPs experience enhanced staff awareness and adherence to cybersecurity practices, ultimately resulting in a more secure and compliant work environment.
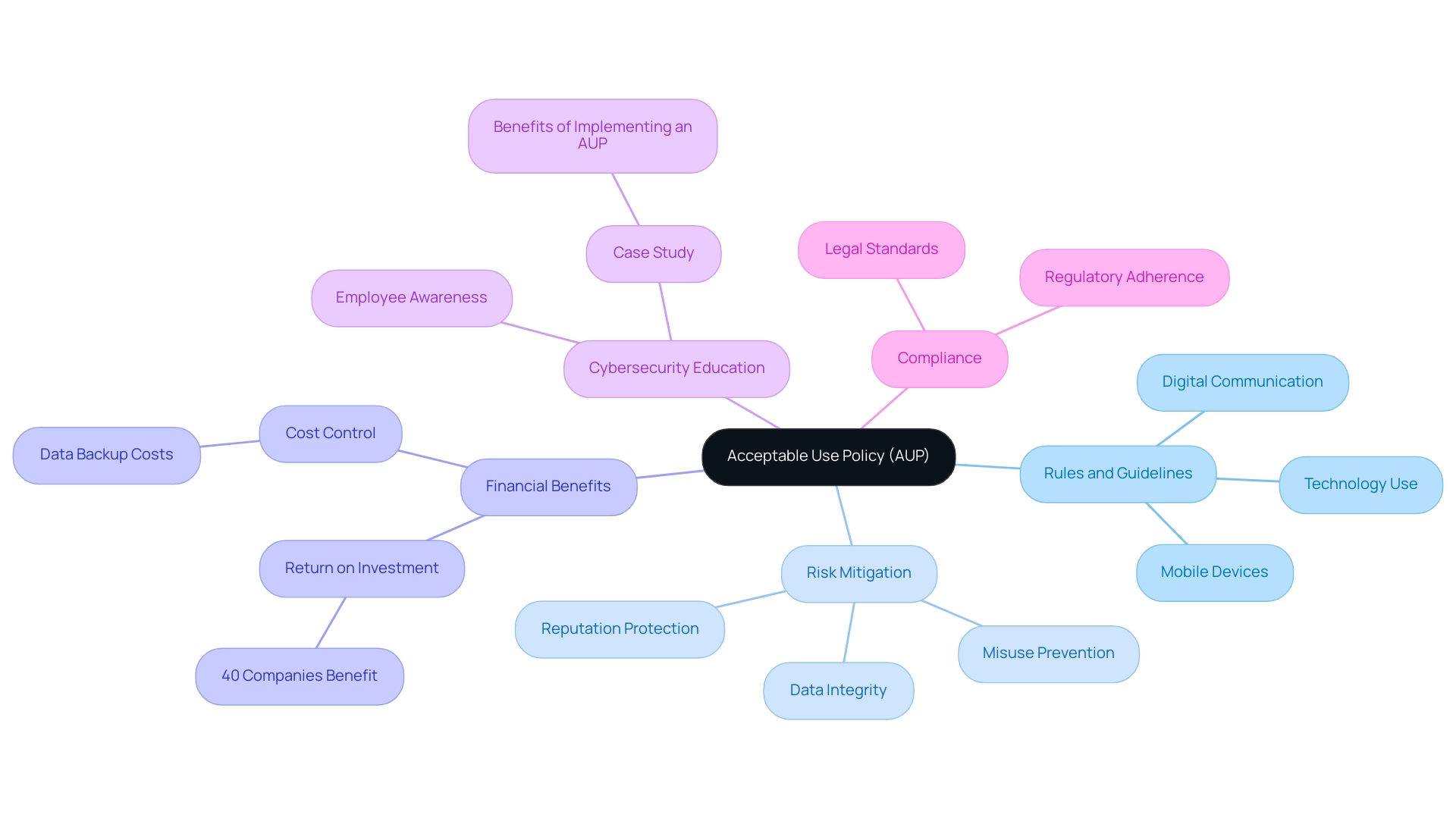
The Importance of Acceptable Use Policies for Business Security
The importance of acceptable use policy is crucial for organizations seeking to fortify their cybersecurity framework and ensure compliance. As emphasized by Aberdeen Research, "81% of businesses are not fully confident in their technology stack’s ability to support the needs of hybrid and remote workers," which underscores the importance of acceptable use policy. The key benefits of implementing an AUP include:
-
Protecting Sensitive Information: AUPs play a pivotal role in safeguarding sensitive data by preventing unauthorized access. They ensure that employees understand their responsibilities in data protection, thereby reducing the likelihood of breaches.
-
Mitigating Legal Risks: Clearly defined acceptable behaviors help reduce the potential for legal issues stemming from the misuse of technology resources. By outlining what constitutes acceptable use, entities can protect themselves from costly legal disputes.
-
Establishing Accountability: An effective AUP creates a framework of accountability within the entity. It delineates the consequences of violations, making it clear that breaches can result in disciplinary actions, thus reinforcing the seriousness of compliance.
-
Enhancing Cybersecurity: With cyber threats on the rise, particularly as 81% of businesses express uncertainty about their technology stack's capacity to support hybrid and remote work environments, AUPs are crucial. They offer clear guidelines on technology use, instructing staff about potential threats and safe practices, which significantly enhances a company's cybersecurity posture.
-
Promoting a Positive Work Environment: AUPs foster a culture of respect and professionalism. By setting clear expectations for behavior, they contribute to a productive and collaborative workplace atmosphere, ultimately enhancing overall employee morale and efficiency.
The implementation of AUPs not only secures the entity but also prepares it for potential challenges such as the anticipated Holiday Ransomware Storm, highlighting the importance of acceptable use policy in contemporary business security strategies. Moreover, a well-organized AUP can enhance productivity by restricting non-work-related internet use and ensuring adherence to regulations, as shown in the case study titled 'Benefits of an Acceptable Use Policy.' For CTOs seeking further insights, joining Spiceworks provides free access to an IT community, news, insights, research, and tools that can assist in developing effective AUPs.
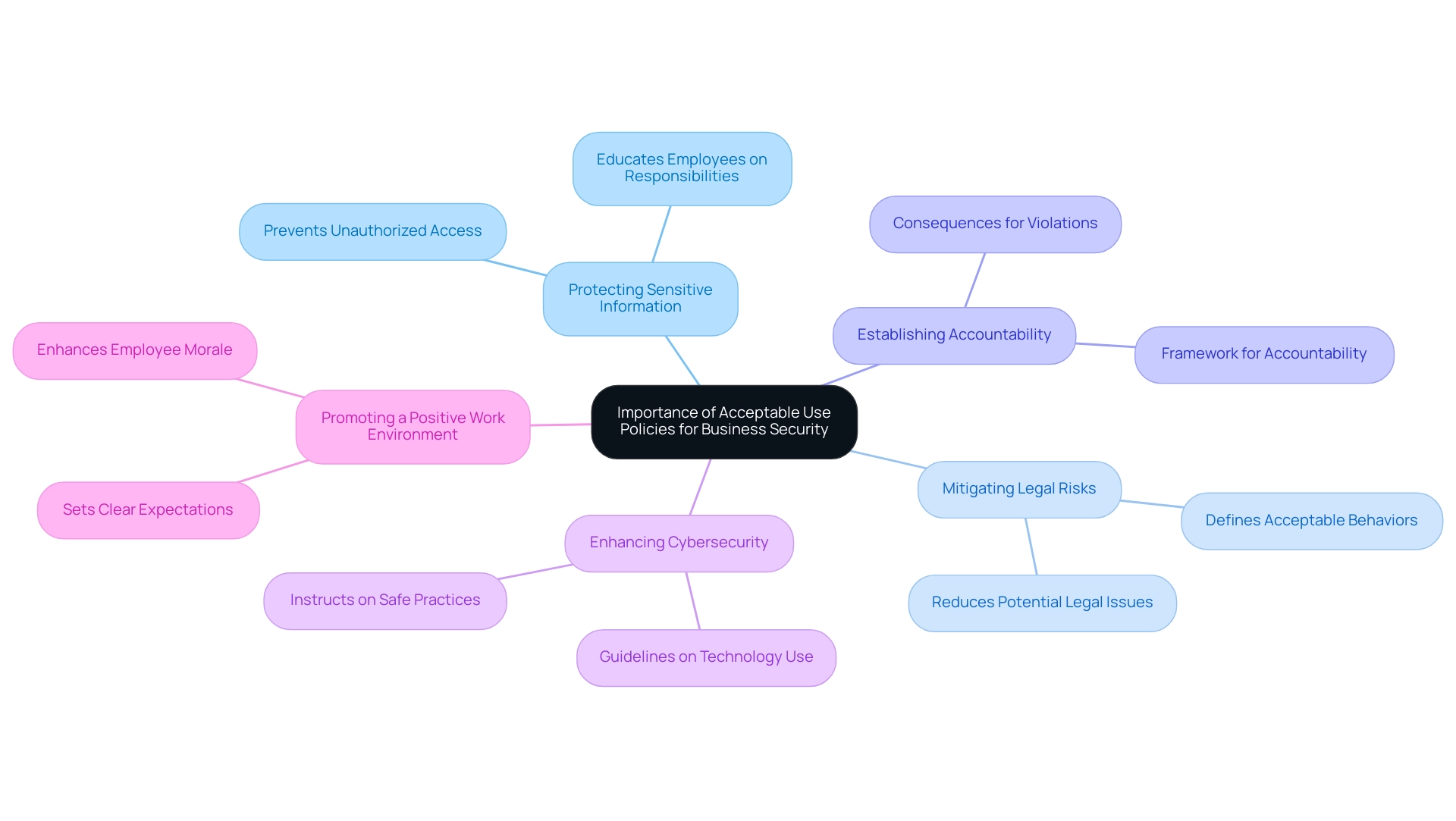
Steps to Implementing an Effective Acceptable Use Policy
To effectively implement an Acceptable Use Policy (AUP), the following steps should be meticulously followed:
-
Assess Organizational Needs: Begin by evaluating the specific requirements of your organization. Consider the nature of your business and the potential risks associated with technology use, which will inform the scope of your policy.
-
Draft the Policy: Create a comprehensive draft of the AUP that articulates acceptable and unacceptable behaviors clearly. This document should include the consequences for violations, such as verbal warnings, written warnings, suspension, or termination, and outline procedures for reporting misuse. Establishing a progressive discipline policy is crucial to reinforcing compliance and accountability.
-
Involve Stakeholders: Engage key stakeholders, including members from IT, Human Resources, and legal teams, in the development process. Their insights are crucial to ensure that the policy not only meets organizational goals but also complies with local laws and regulations. As noted, "X respects the individual’s privacy and complies with local laws and regulations." However, we reserve the right to log IT use and, in special circumstances, require access to an individual's email and files.
-
Educate Employees: Conduct training sessions to familiarize employees with the AUP, highlighting the importance of acceptable use policy and providing guidance on adherence. Highlighting examples of incidental personal use of IT resources, such as sending personal emails or streaming videos, can help clarify expectations.
-
Enforce the Policy: Develop robust procedures for monitoring adherence and addressing violations consistently. This enforcement is vital to reinforce the importance of acceptable use policy and ensure adherence throughout the entity.
-
Review and Update Regularly: Establish a routine for reviewing and updating the AUP to keep it relevant and effective in the face of evolving technology and organizational changes. Continuous improvement in your policy is essential for maintaining cybersecurity compliance and protecting sensitive data.
By following these best practices, organizations can enhance the importance of an acceptable use policy's effectiveness. For example, Organization X emphasizes the importance of protecting personal information entrusted by customers, members, employees, and partners. They have implemented secure processes for handling such data, demonstrating the profound impact an effective AUP can have on organizational integrity and adherence.
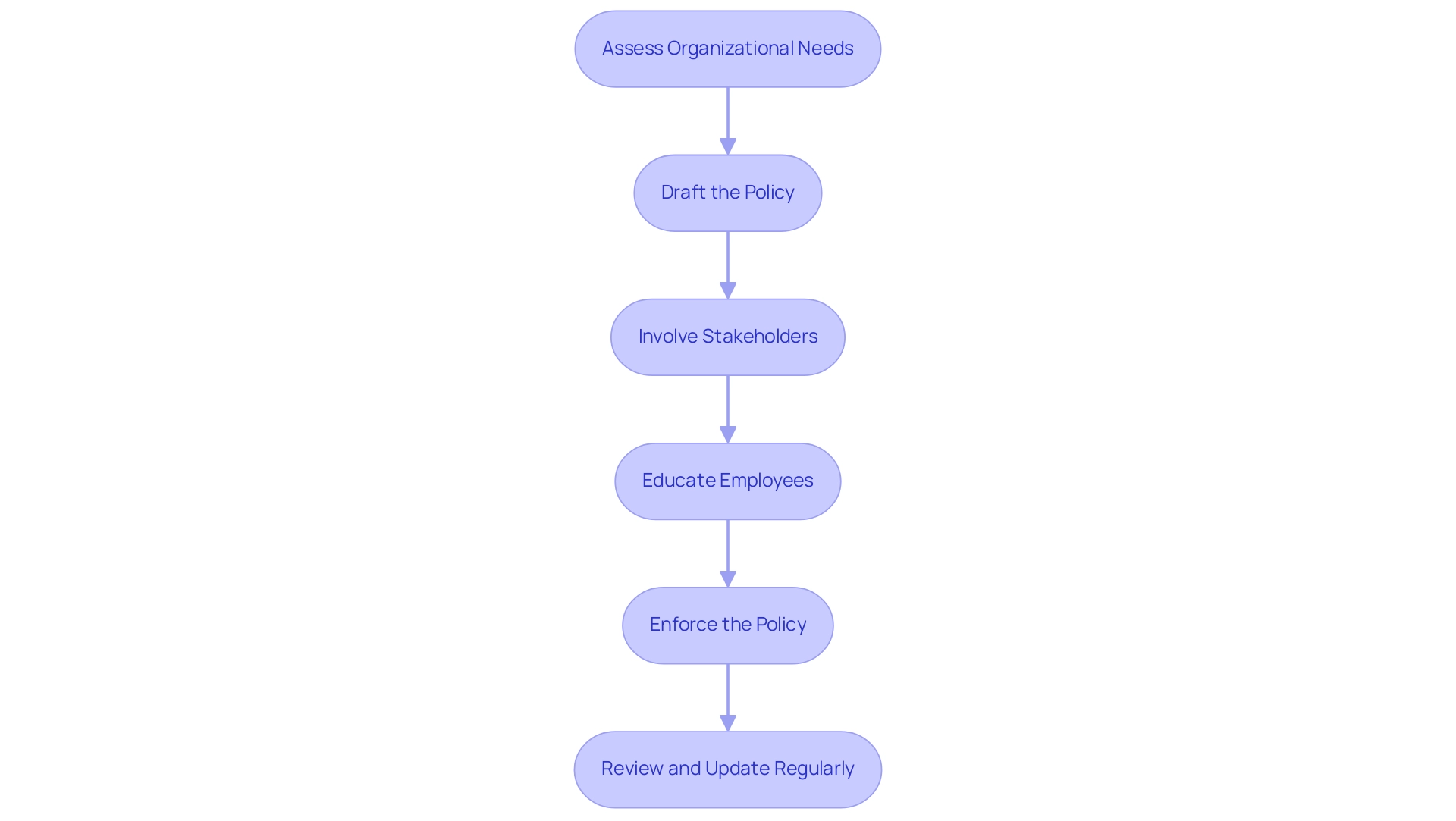
Common Challenges in Enforcing Acceptable Use Policies
Enforcing Acceptable Use Policies (AUPs) presents several significant challenges that organizations must navigate to ensure effective cybersecurity adherence. These challenges include:
-
Lack of Awareness: A considerable number of staff may not fully comprehend the AUP or its implications, resulting in unintentional violations.
Studies emphasize that numerous staff members are oblivious to crucial elements of these policies, which can threaten adherence efforts. -
Resistance to Change: Employees can often be resistant to new policies, viewing them as intrusive or unnecessary.
This resistance not only hinders implementation but can also create a culture of non-compliance if not addressed appropriately. -
Inconsistent Enforcement: The effectiveness of an AUP can be significantly undermined by inconsistent application.
When policies are enforced unevenly, it leads to confusion and frustration among staff, thereby diminishing overall adherence rates. -
Technological Limitations: Organizations may find that their existing technology does not adequately support effective monitoring and enforcement of the AUP.
This limitation can create obstacles to ensuring adherence, especially in rapidly evolving digital environments. -
Cultural Barriers: The prevailing organizational culture can greatly influence workers' willingness to adhere to the AUP.
If staff view the policy as at odds with established norms, adherence becomes progressively difficult. A case study named 'Racial and Ethnic Differences in Privacy Perceptions' emphasizes variations in privacy worries among various racial and ethnic groups, indicating that cultural elements can greatly influence adherence perspectives.
To tackle these challenges, institutions should establish thorough training initiatives that improve staff awareness of the importance of acceptable use policy and its impact. Clear and consistent communication regarding the policies is essential, as is the establishment of uniform enforcement practices. As Matthew Hall, Vice President for Information Technology and CIO at the University of Central Florida, states, 'We need to have our investments aligned to what is focused on our students and faculty, learning and teaching, our research and our mission.'
By promoting a culture of awareness and teamwork that aligns with institutional objectives, entities can significantly enhance adherence rates to the importance of acceptable use policy. Moreover, considering that IT consultants can cost hundreds of dollars per hour, the financial implications of non-compliance make effective enforcement even more critical.
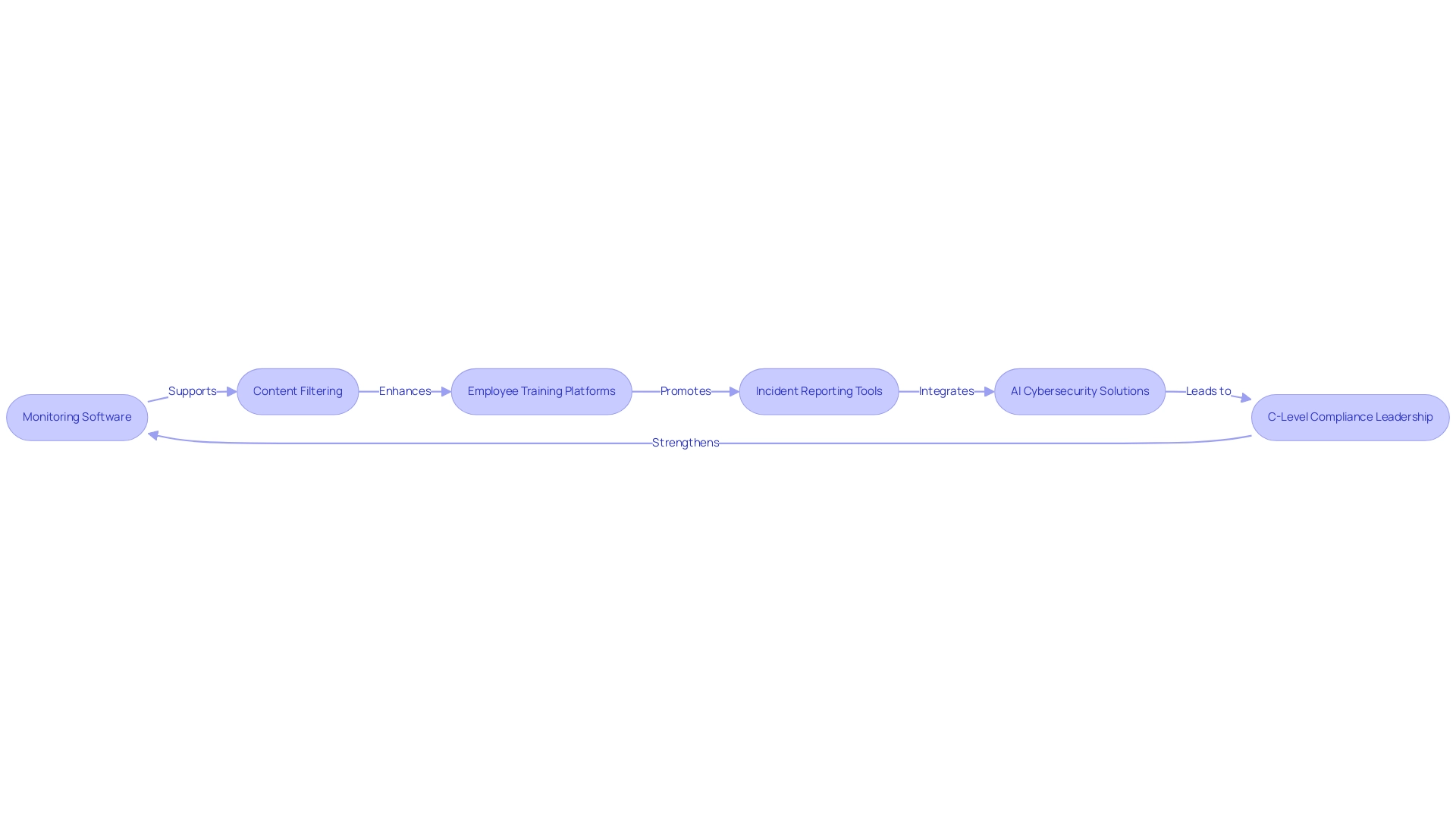
The Role of Technology in Supporting AUP Compliance
Technology is essential in ensuring adherence to Acceptable Use Policies (AUP), employing a range of sophisticated tools and solutions:
-
Monitoring Software: The adoption of advanced monitoring software enables companies to track staff activities effectively, ensuring compliance with AUP guidelines. This not only enhances compliance but also mitigates potential risks associated with policy breaches.
-
Content Filtering: Leveraging content filtering technologies is vital for restricting access to inappropriate websites and applications. This proactive measure highlights the importance of acceptable use policy by helping to minimize the risk of violations and reinforcing its integrity.
-
Employee Training Platforms: Online training platforms serve as pivotal resources for ongoing education about AUPs. By offering regular training sessions, organizations can ensure that staff remain informed about the importance of acceptable use policy and understand the implications of non-compliance.
-
Incident Reporting Tools: Establishing robust incident reporting tools empowers employees to report suspected violations confidently. This promotes a culture of accountability and transparency, which is essential for upholding regulations and improving overall security.
The importance of acceptable use policy is highlighted by conducting periodic audits of technology usage and compliance, which is essential for identifying areas needing improvement. Such audits not only strengthen compliance with the policy but also assist in adjusting to developing cybersecurity threats, as cybersecurity and IT constitute 19% of an entity's overall audit plan.
-
AI Cybersecurity Solutions: The integration of AI cybersecurity solutions is transforming cyber defense, enabling organizations to respond proactively to evolving cyber threats. These technologies enhance monitoring capabilities and improve the efficiency of regulatory efforts.
-
C-Level Compliance Leadership: The importance of having qualified cybersecurity professionals cannot be overstated. Designating a C-level regulatory leader can result in substantial financial advantages, with firms saving an average of $1.25 million in regulatory expenses. This real-world example emphasizes the importance of effective security and regulatory programs. By employing these technological solutions, organizations can significantly improve their adherence to the importance of acceptable use policy, ultimately resulting in more secure and efficient operations. As John Doe emphasizes, 70% of venture capitalists prefer companies that showcase SOC 2 adherence, highlighting the significance of strong cybersecurity practices. Additionally, Thoropass welcomes feedback and encourages users to reach out, reflecting a commitment to continuous improvement in cybersecurity standards.
Future Trends in Acceptable Use Policies
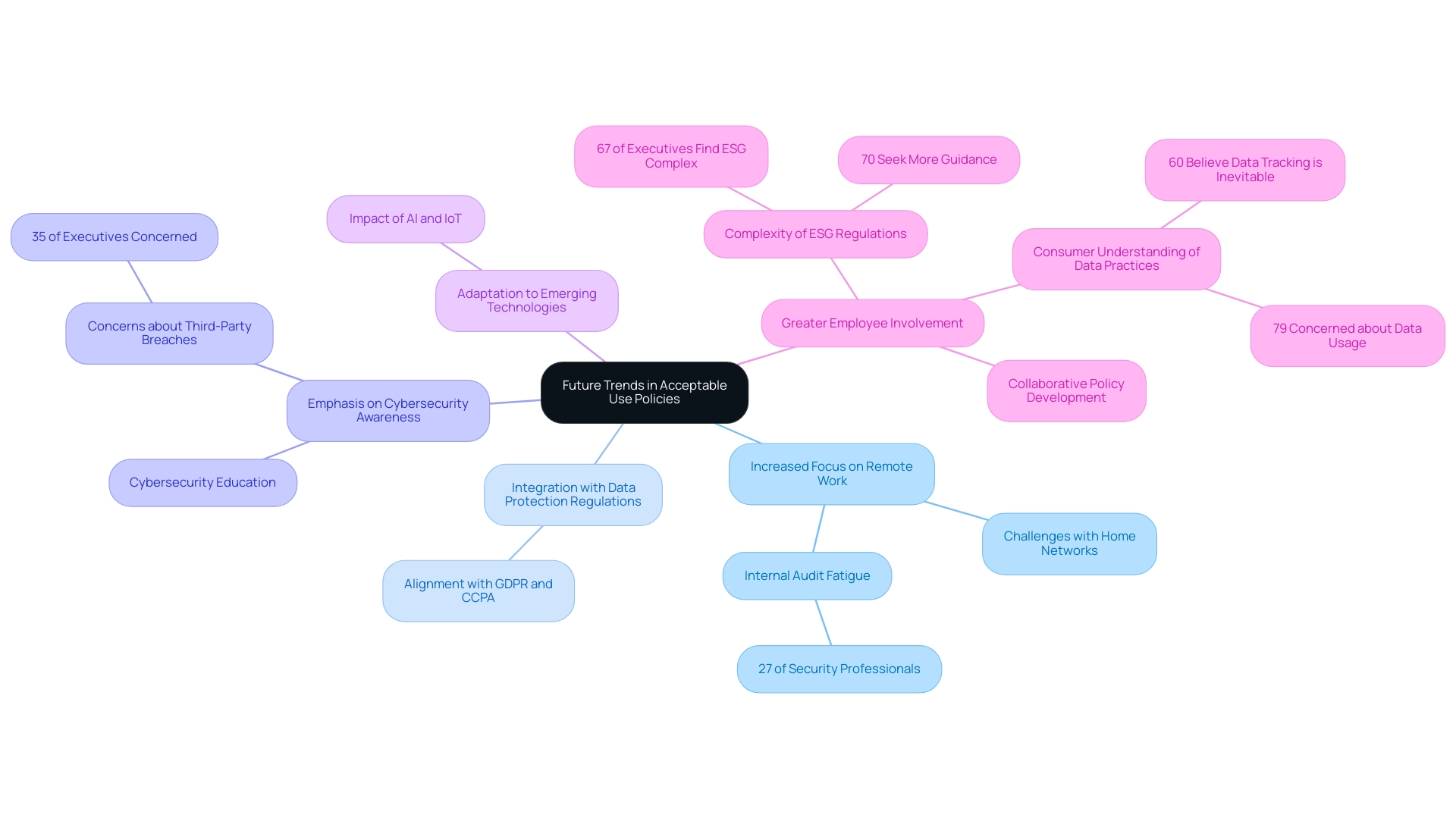
As technology continues to advance, the importance of acceptable use policy (AUP) is becoming increasingly significant. Future trends may include:
-
Increased Focus on Remote Work: The surge in remote work necessitates AUPs to tackle unique challenges associated with home networks and personal device usage, ensuring that employees remain compliant while working in diverse environments.
This shift also underscores the challenge of alleviating internal audit fatigue, with 27% of security and IT professionals identifying it as a top regulatory program challenge. -
Integration with Data Protection Regulations: Organizations will increasingly align AUPs with data protection laws, such as GDPR and CCPA, to enhance compliance and mitigate risks associated with data breaches.
-
Emphasis on Cybersecurity Awareness: A heightened focus on cybersecurity education within AUPs will be imperative, fostering a culture of vigilance among staff. In fact, a recent report indicates that 35% of business and tech executives view third-party breaches as one of the most concerning cyber threats, highlighting the need for proactive measures.
-
Adaptation to Emerging Technologies: As new technologies like artificial intelligence and the Internet of Things become more prevalent, AUPs must evolve to address their implications for acceptable use and security.
-
Greater Employee Involvement: Organizations are likely to involve employees more actively in the development and revision of AUPs, ensuring that policies reflect diverse perspectives and the practical realities of the workplace. This collaborative approach is essential in an era where 67% of global executives find ESG regulations complex, with many seeking clearer guidance from regulators. Additionally, a Pew Research study found that 60% of Americans feel it is impossible to live without having their personal data tracked, indicating a significant gap in consumer understanding of data practices.
By adapting AUPs to these trends, organizations can better navigate the changing cybersecurity landscape and recognize the importance of acceptable use policy in enhancing compliance efforts.
Conclusion
The establishment of an Acceptable Use Policy (AUP) is a crucial step for organizations striving to safeguard their technological assets and sensitive information in an increasingly digital landscape. AUPs provide a structured framework that outlines acceptable behaviors related to technology use, thereby mitigating risks associated with cybersecurity threats and ensuring compliance with legal standards. By implementing a robust AUP, organizations can protect sensitive data, reduce legal risks, and foster a culture of accountability and professionalism among employees.
The implementation process involves several key steps, including:
1. Assessing organizational needs
2. Drafting comprehensive policies
3. Engaging stakeholders
4. Educating employees
5. Enforcing compliance
6. Conducting regular reviews
Challenges such as lack of awareness, resistance to change, and inconsistent enforcement can impede the effectiveness of AUPs. However, these obstacles can be addressed through targeted training and consistent communication, ensuring that employees understand the importance of compliance.
Looking ahead, the evolution of AUPs will be driven by emerging trends such as:
- The increasing prevalence of remote work
- The integration of data protection regulations
- The need for heightened cybersecurity awareness
By adapting to these changes and leveraging technology to support compliance efforts, organizations can enhance their security posture and cultivate a proactive approach to digital interactions.
In conclusion, a well-defined Acceptable Use Policy is not merely a regulatory necessity but a strategic imperative that empowers organizations to navigate the complexities of digital security. By prioritizing the development and enforcement of AUPs, businesses can foster a secure, compliant, and productive work environment, ultimately contributing to their long-term success in a rapidly evolving digital world.




