Introduction
In an era where digital transformation is pivotal to business success, ensuring robust cloud security is more critical than ever. The Cloud Control Matrix (CCM), developed by the Cloud Security Alliance (CSA), serves as a comprehensive framework designed to address security controls within cloud computing environments. This article delves into the core aspects of the CCM, elucidating its features, benefits, and the security domains it encompasses.
By highlighting practical implementation and auditing guidelines, it underscores how organizations can leverage the CCM to enhance their cloud security posture and ensure compliance with international standards. As cybersecurity risks evolve, the CCM remains an indispensable tool for organizations striving to achieve operational efficiency and resilience in their cloud environments.
What is the Cloud Control Matrix?
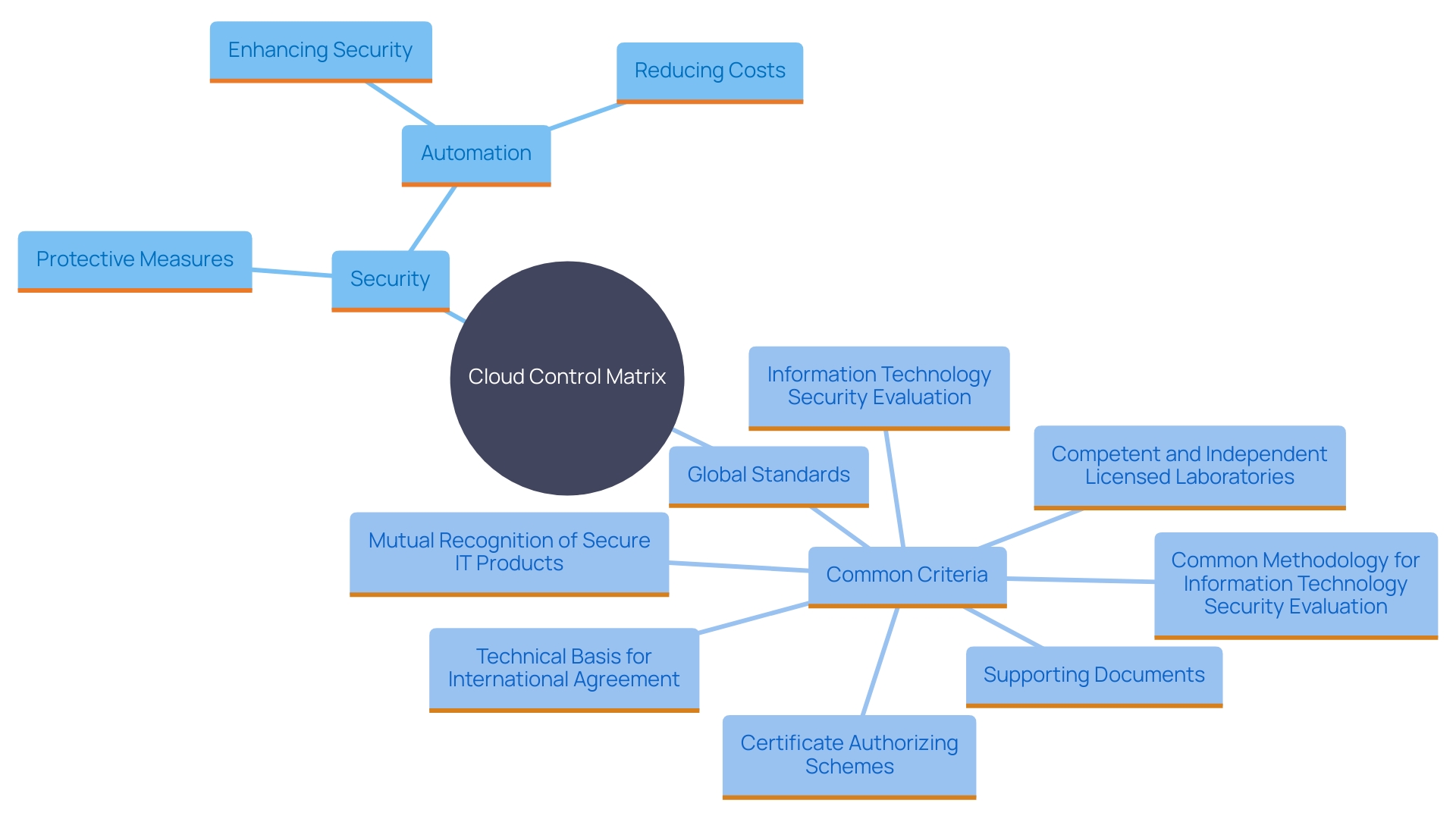
The Cloud Control Matrix (CCM) is a strong framework created by the Cloud Security Alliance (CSA) to tackle protective measures in online computing environments. By providing an extensive range of protective measures, the CCM assists entities in assessing their cloud service providers and guaranteeing their data remains safe. According to Shelly, a principal analyst at theCUBE Research, understanding and managing cybersecurity risks is crucial for any organization's digital transformation process. The CCM assists in this by offering standardized protective measures that simplify and consolidate safety efforts.
Furthermore, the CCM framework emphasizes the importance of automation in reducing human error and driving down costs, directly preventing data loss and business disruptions. Corey Quinn, in a recent interview, emphasized how effective online protection measures can simultaneously lower expenses and improve safety, underscoring the interconnected nature of these aspects.
'The importance of strong online protection measures is further highlighted by the Common Criteria for Information Technology Security Evaluation (CC), which offers an international standard for assessing and certifying the protective features of IT products.'. This guarantees a globally acknowledged criterion of protection that groups can depend on.
In the constantly changing realm of cloud protection, frameworks such as the CCM are essential instruments for entities striving to strengthen their cloud settings while ensuring operational efficiency and resilience.
Key Features of the Cloud Control Matrix
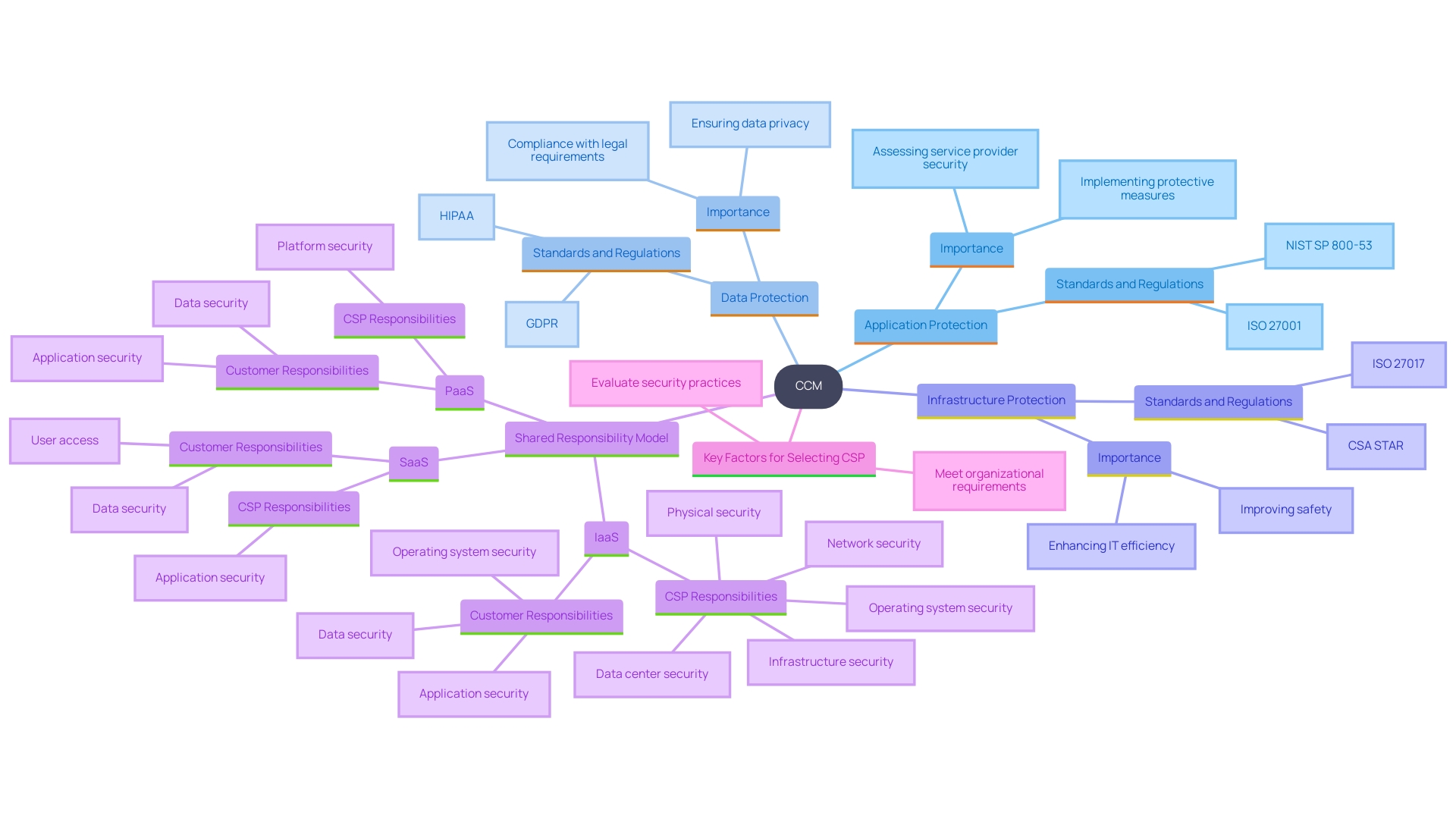
The Cloud Controls Matrix (CCM) offers pivotal features that significantly bolster its utility for organizations. It provides a comprehensive set of controls arranged across various protective domains, including application protection, data protection, and infrastructure protection. This matrix aligns with widely recognized standards and regulations, simplifying adherence to safety requirements. By offering a structured model, the CCM helps entities in assessing the protection stance of service providers and acts as a standard for applying efficient protective measures. As stated by Rob Joyce, NSA’s Director of Cybersecurity, 'Utilizing remote servers can make IT more efficient and more safe, but only if it is executed properly.' This essential guidance highlights the significance of strong remote infrastructure governance to reduce the risks linked with reliance on such services and improve resilience.
Benefits of Using the Cloud Control Matrix
Leveraging the Cloud Control Matrix (CCM) yields significant benefits for organizations. It standardizes evaluations of protection across diverse online environments, ensuring a consistent approach to risk management. For instance, Chess.com, which caters to over 150 million users and facilitates more than ten million games each day, depends on a strong IT framework that encompasses public hosting and on-site solutions. By employing structures such as the CCM, entities like Chess.com can identify vulnerabilities, prioritize enhancements, and increase clarity with service providers, promoting trust and responsibility.
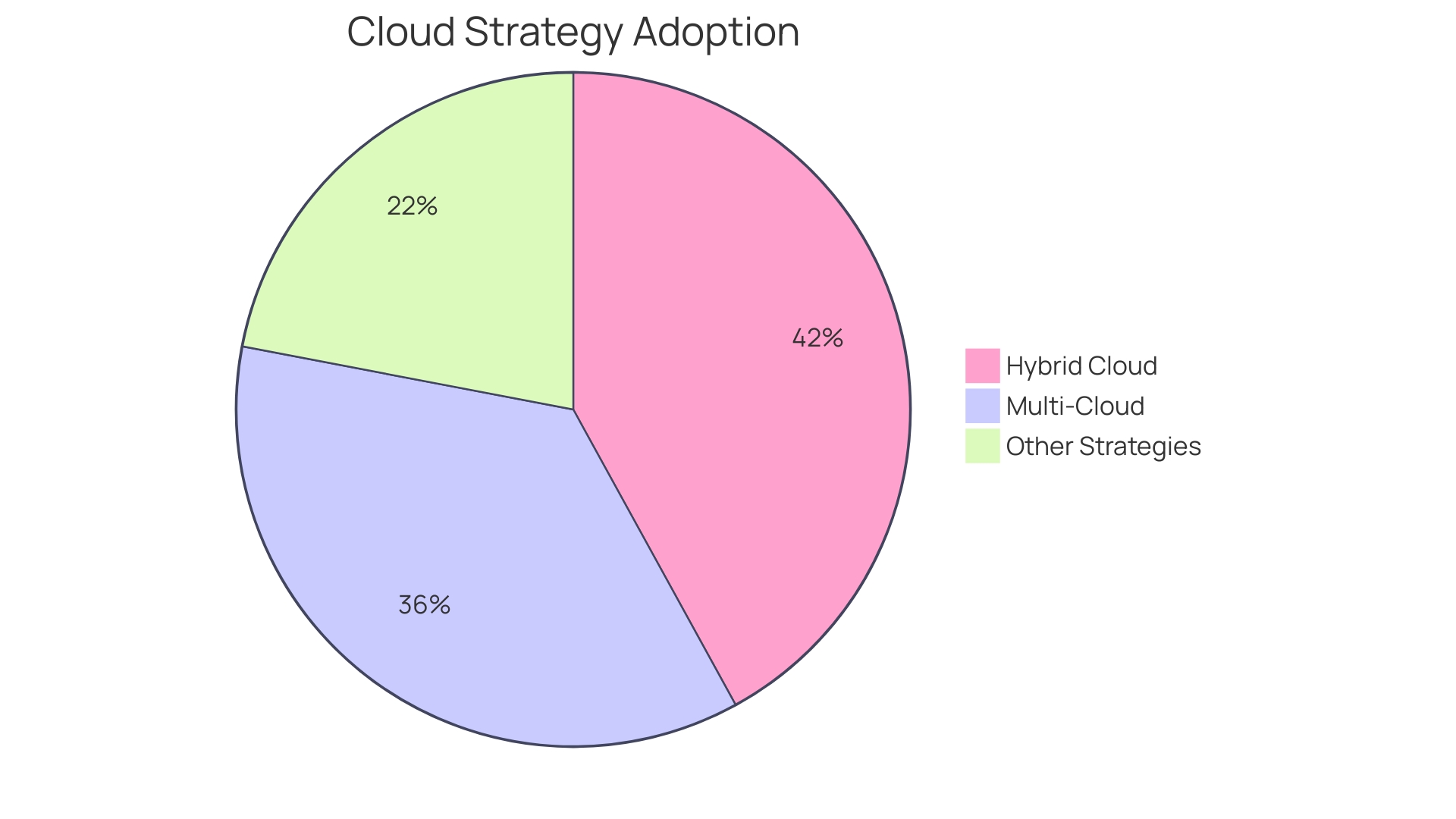
Anthony James, VP of Product Marketing at Infoblox, underscores the importance of such tools: "Using the cloud can make IT more efficient and more secure, but only if it is implemented right." This feeling is evident in present patterns, as 78% of entities embrace hybrid and multi-cloud approaches to enhance their protection and operational efficiencies. The Cloud Control Matrix is essential in directing these organizations to reach their safety objectives efficiently.
Security Domains Covered by the CCM
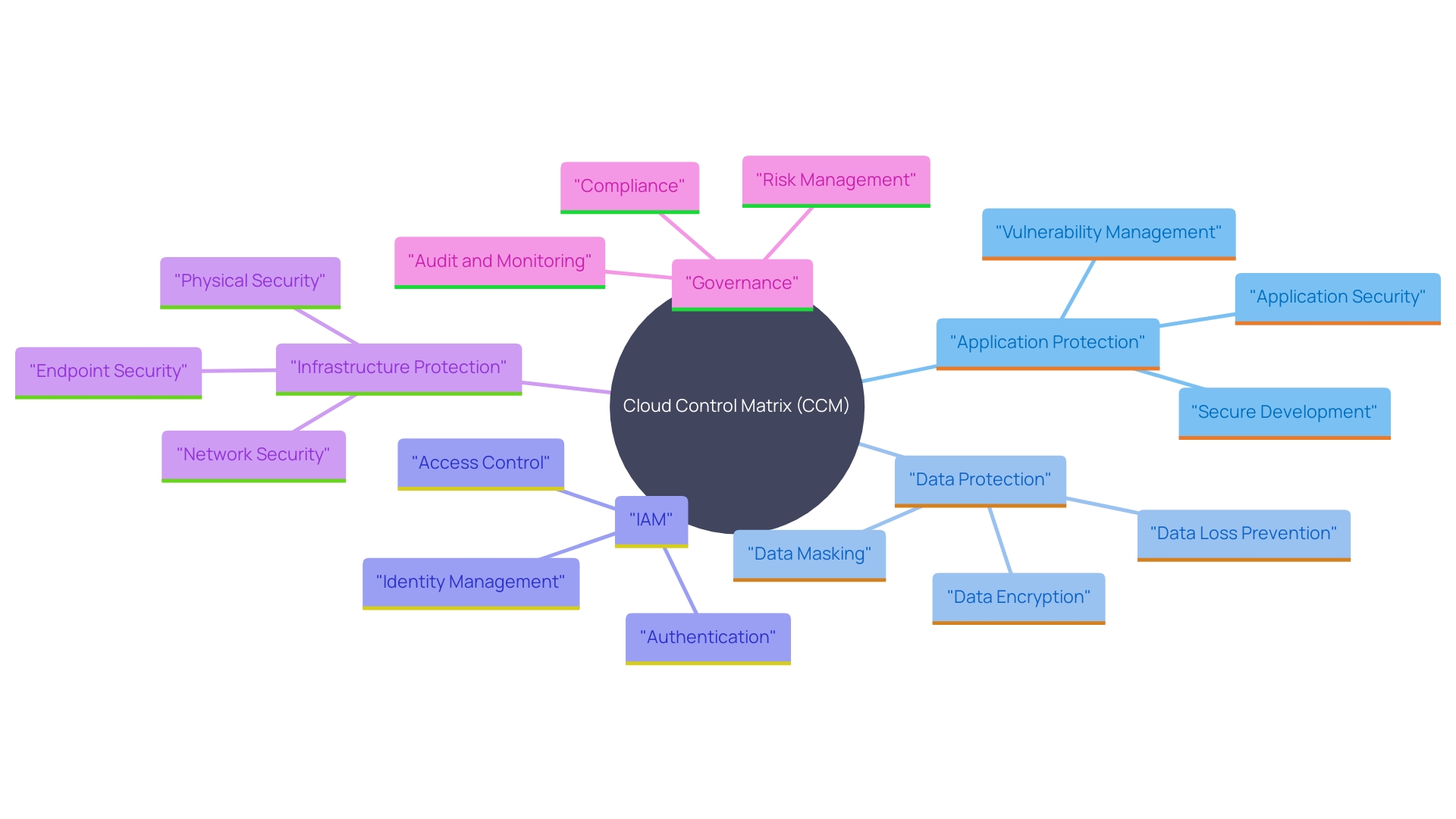
The Cloud Control Matrix (CCM) is a thorough structure created to guarantee strong online protection through various essential areas. Key areas consist of application protection, data protection, identity and access management (IAM), infrastructure protection, and governance of safety. Each domain contains tailored controls to mitigate specific risks associated with cloud computing.
Application protection concentrates on safeguarding cloud-based applications from vulnerabilities and threats. This domain includes controls for secure coding practices, vulnerability management, and application monitoring. Data protection includes measures to safeguard information at rest, in transit, and during processing. This includes encryption, data masking, and data loss prevention strategies.
IAM is essential for defining and managing user access to online resources. It involves authentication and authorization processes to ensure that only authorized users can access sensitive information. Infrastructure protection involves the physical and virtual elements of the online environment, including network safeguards, host protection, and incident response systems.
Governance in the protection domain offers the comprehensive policies, procedures, and frameworks to guarantee uniform and efficient management across all areas. It includes compliance with regulatory requirements, risk management practices, and continuous monitoring and improvement processes.
The CCM's comprehensive strategy for digital infrastructure protection guarantees that entities can efficiently handle and reduce threats in their online settings. By implementing these controls, organizations can achieve a more secure and resilient online infrastructure.
Implementation and Auditing Guidelines
'Implementing the Cloud Control Matrix (CCM) requires a systematic approach that involves evaluating current protection protocols, aligning them with CCM standards, and maintaining continuous compliance monitoring.'. Organizations should regularly evaluate their protective measures to ensure effectiveness within the online environment. The CCM provides thorough guidelines for these audits, helping organizations in sustaining a strong defense stance and adjusting to changing threats.
A notable example comes from Chess.com, which serves over 150 million users and hosts more than ten million games daily. As James Kelty, Head of Infrastructure at Chess.com, states, "Our mission is to serve chess, and to nurture the game’s growth and the bonds it forges between people everywhere." This commitment requires a stable IT infrastructure that combines public resources and on-premises solutions. By adhering to organized protective measures and frequent evaluations, Chess.com effectively oversees its extensive user community and confidential information, showcasing the effectiveness of strong management practices.
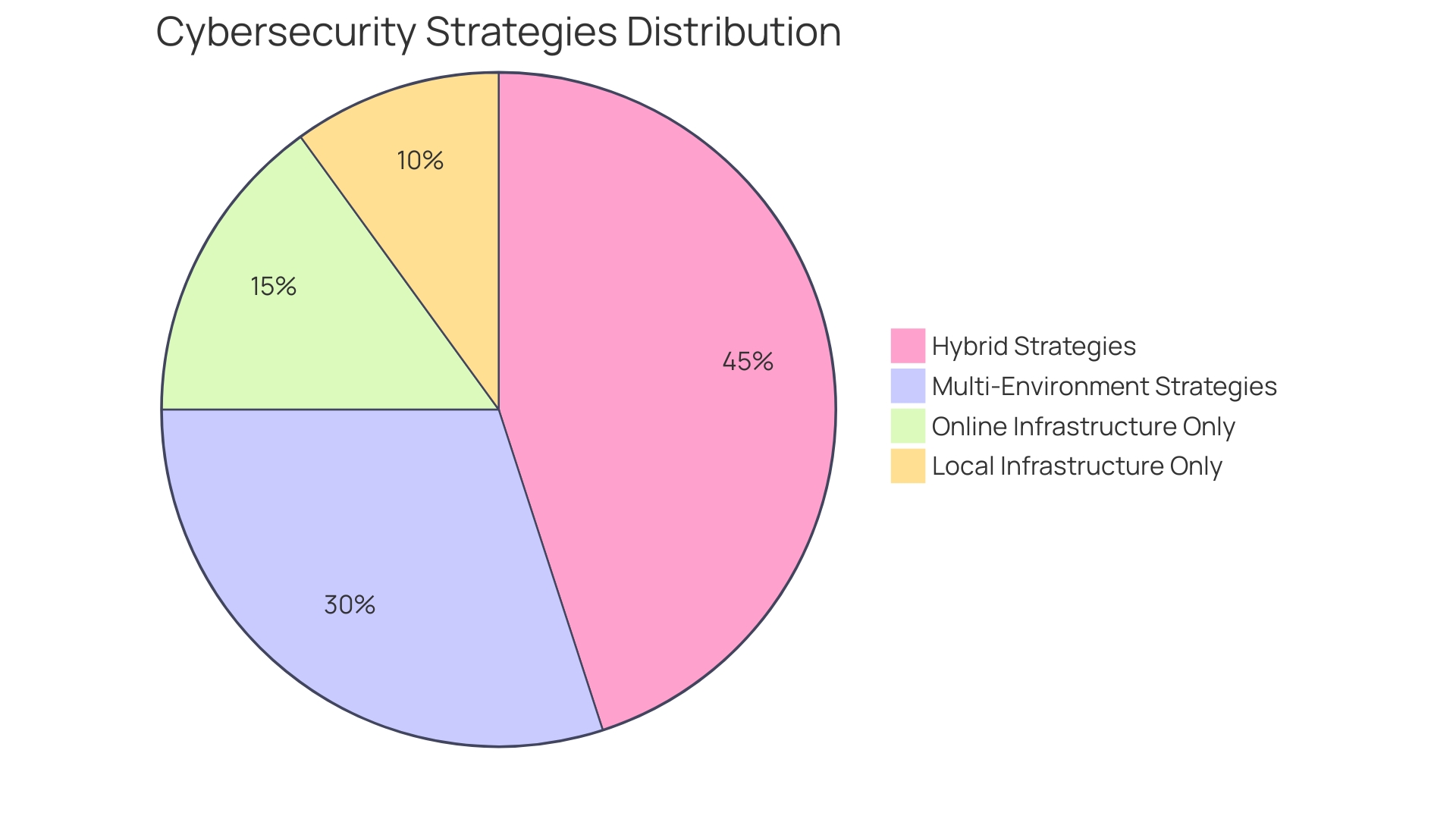
Based on a study of 927 cybersecurity experts, 78% of entities are currently implementing hybrid and multi-environment strategies, with 43% utilizing a mix of online and local infrastructure. This trend highlights the significance of a properly executed CCM, as it assists entities in managing the intricacies of hybrid settings while guaranteeing high-level protective measures are established.
Furthermore, utilizing resources such as the Center for Internet Security® (CIS®) can further improve programs for online protection. These resources offer valuable insights and best practices that entities can tailor to their specific needs, ensuring a custom fit that aligns with their business objectives. As online protection develops, remaining knowledgeable and anticipatory about these strategies is essential for upholding a strong defense stance.
How to Use the CCM for Cloud Security and Compliance
To effectively utilize the Cloud Control Matrix (CCM) for online protection and compliance, organizations should begin by aligning their current safety practices with the CCM controls. This process facilitates the identification of gaps and areas necessitating improvement, which is vital for robust data management. As data gathering, storage, and examination increase, categorizing information according to its sensitivity and risk level becomes essential, implementing strict protective measures to sensitive data. Utilizing the CCM can also significantly enhance risk management strategies, ensuring preparedness for regulatory requirements while safeguarding cloud environments.
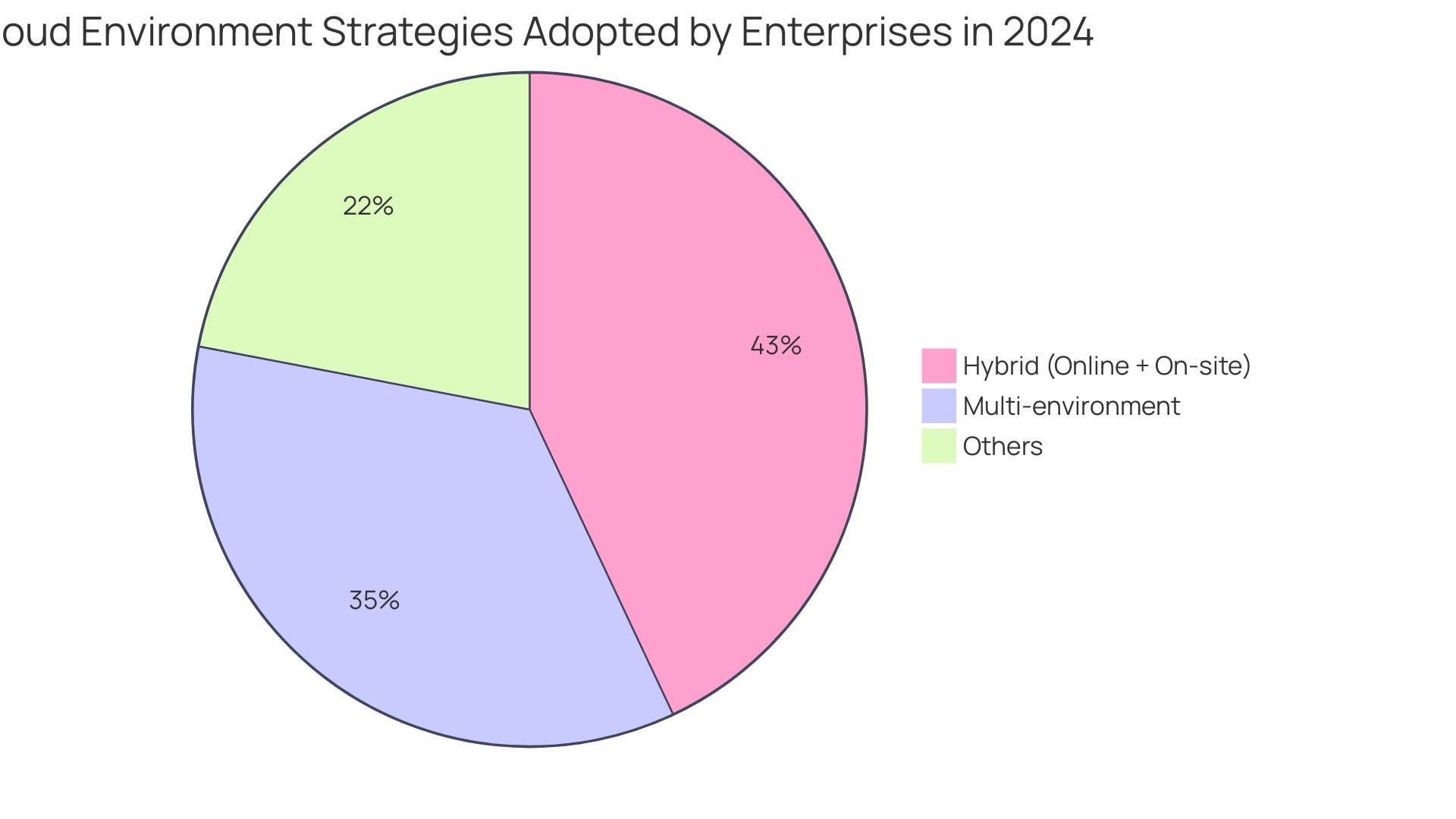
Adopting a Secure by Design approach, which incorporates protection into design and development processes from the beginning, is crucial in balancing agility and cost optimization with safety goals. This comprehensive approach can substantially mitigate vulnerabilities and strengthen the protection of products and services. In 2024, a majority of enterprises (78%) are adopting hybrid and multi-environment strategies, with 43% using a combination of online services and on-site infrastructure and 35% employing multi-environment strategies. This trend highlights the significance of efficient management and protective measures.
Leading experts, such as Anthony James, emphasize the importance of a deep understanding of technology to develop high-value, differentiated messaging and strategies. This viewpoint is essential as organizations maneuver through the intricacies of online protection. The insights from a survey of 927 cybersecurity professionals highlight that fewer than 20 globally active Cloud Service Providers (CSPs) dominate the market, offering world-class protection levels, while second- and third-tier CSPs pose higher risks. Thus, a thorough understanding and strategic application of the CCM are essential for maintaining cloud security and compliance.
Conclusion
The Cloud Control Matrix (CCM) is a critical framework for organizations aiming to strengthen their cloud security. By offering a structured set of controls across essential domains—such as application security, data security, and infrastructure security—the CCM facilitates compliance with regulations and enables effective evaluation of cloud service providers. Its emphasis on automation minimizes human error, enhancing overall resilience.
Adopting the CCM provides numerous benefits, including standardized security assessments and improved transparency with service providers. Organizations leveraging the CCM can identify security gaps and prioritize necessary improvements, fostering trust and accountability, as evidenced by implementations like Chess.com.
Additionally, the CCM's guidelines for implementation and auditing are vital in maintaining a robust security posture. Regular audits and alignment with CCM standards empower organizations to adapt to evolving threats while adhering to international benchmarks. As cloud strategies continue to develop, the significance of a well-implemented CCM remains essential for navigating the complexities of hybrid and multi-cloud environments.
In conclusion, the Cloud Control Matrix is an indispensable tool for organizations dedicated to achieving strong cloud security and compliance. By aligning security practices with the CCM, organizations can enhance resilience and effectively manage cybersecurity risks, ensuring the protection of sensitive data and maintaining stakeholder trust in a complex digital landscape.




