Introduction
In an increasingly interconnected world, the security of network infrastructures has never been more critical. Network firewalls serve as the first line of defense, employing a combination of hardware and software to monitor and control incoming and outgoing traffic based on established security protocols. As cyber threats grow in complexity and frequency, organizations must prioritize the implementation of robust firewall solutions.
Recent market trends reveal an impressive growth trajectory in this sector, emphasizing the urgent need for businesses to invest in advanced firewall technologies to protect sensitive data against unauthorized access. This article delves into the essential concepts of network firewall security, explores various types of firewalls, and highlights the key benefits they offer to enhance business security. By understanding the intricacies of firewall systems and their role in a comprehensive cybersecurity strategy, organizations can better navigate the evolving landscape of cyber threats.
Introduction to Network Firewall Security: Key Concepts and Importance
Protection measures involve the use of both hardware and software systems created to oversee and manage traffic based on established safety protocols. These security systems establish a crucial barrier between trusted internal networks and potentially harmful external networks, such as the internet. With North America leading in the web application security market due to high cyber-attack rates and stringent security regulations, the importance of robust protective solutions is underscored.
Recent market projections indicate an impressive growth trajectory, with expectations of an 18.92% CAGR from 2024 to 2031, highlighting the increasing recognition of protective systems' significance in safeguarding sensitive data from unauthorized access and cyber threats. This statistic serves as an essential reminder for organizations to invest in security technologies as part of their cybersecurity strategies.
The case study on web application security implementation reveals significant challenges, such as the increasing sophistication of cyber attacks and the potential for operational disruptions. These challenges highlight the importance of efficient management and operation of protective systems to guarantee both performance and safety. For instance, organizations must navigate the balance between strong protective measures and the risk of generating false positives that could disrupt operations.
Grasping key concepts such as packet filtering, stateful inspection, and application-layer filtering is crucial to fully understand the functionality and significance of protective systems within a comprehensive defense strategy. As cyber threats evolve, so must the technologies designed to counter them. A recent high-profile case involving a Russian cybercriminal associated with the Phobos ransomware scheme, who now confronts justice in the United States, illustrates the ongoing struggle against cybercrime and highlights the essential role protective barriers play in network protection. This case demonstrates the severe outcomes of insufficient protective measures and emphasizes the necessity for organizations to implement strict barrier safeguards.
With ongoing progress in firewall technology, encompassing hardware, virtual, and cloud-based solutions, as well as managed and professional services, organizations must remain updated and adjust their protective measures to guard against continuously changing dangers. Firewalls remain essential in the broader cybersecurity landscape, ensuring that sensitive data and system integrity are preserved against emerging risks.
Exploring Different Types of Firewalls and Their Security Benefits
Firewalls are essential tools in network protection, offering a variety of features to guard against cyber threats. Comprehending the various kinds of protective barriers and their advantages is essential for executing an effective defense plan:
-
Packet-filtering Systems: As the most basic type, these systems examine packets and permit or block them based on predefined rules. While they provide fundamental security, they do not offer advanced features. Practical uses, like small enterprises employing packet-filtering security systems to safeguard their systems, often consider them adequate for low-risk settings. However, their limitations can expose more sophisticated networks to vulnerabilities, particularly as cyber threats become more advanced.
-
Stateful Inspection Devices: These systems go beyond simple packet examination by monitoring the state of active connections and making decisions based on the context of the traffic. This method provides enhanced security in comparison to packet-filtering systems. For example, businesses utilizing stateful inspection systems benefit from enhanced protection against unauthorized access, as the system continuously evaluates the legitimacy of traffic.
-
Proxy Systems: Acting as intermediaries, proxy systems filter content and prevent direct access to the network. This additional layer of security is particularly effective in environments requiring stringent control over data flow and user activities.
-
Next-Generation Firewalls (NGFWs): NGFWs incorporate traditional firewall functions with advanced capabilities such as intrusion prevention, application awareness, and deep packet inspection. These features make NGFWs highly effective against complex dangers. Recent advancements in NGFW technology have enabled more precise threat detection and response, ensuring robust protection for modern business networks.
-
Unified Threat Management Firewalls (UTMFs): These systems combine various protective features from different types of barriers into a single solution, offering comprehensive defense. UTMFs simplify management of protections, making robust safeguarding accessible to businesses of all sizes. For example, a case study involving UTMFs illustrated how this comprehensive approach streamlined protective operations and enhanced overall system safety.
According to recent statistics, the market share for various types of protective barriers in 2024 indicates that NGFWs represent approximately 45% of the market, reflecting their increasing significance in contemporary cybersecurity strategies. Selecting the appropriate type and configuration of security system relies on an organization's specific security needs and the intricacy of its network. As threats continue to evolve, it is imperative to stay informed about the latest network security technologies and their capabilities to ensure optimal protection.
Key Benefits of Network Firewalls for Business Security
Network security systems provide numerous key benefits for businesses, including:
-
Protection Against Cyber Threats: Firewalls have been a cornerstone of network security for over 25 years, blocking unauthorized access and preventing data breaches. Regular evaluations of security rules, such as comparing current and previous rules and assessing the necessity of open ports, are critical in maintaining this protection. According to recent statistics, security systems have prevented approximately 80% of attempted cyber breaches in 2024, underscoring their effectiveness in safeguarding networks.
-
Enhanced Connectivity Efficiency: By filtering out unnecessary traffic, security systems improve overall performance, allowing legitimate data to flow more freely. This not only optimizes the user experience but also reduces the load on network resources.
-
Regulatory Compliance: In industries subject to stringent regulations, security systems are essential for meeting compliance requirements. Paul Koziarz emphasizes,
You have to evaluate compliance not as an expense, but as a money saver. Sure, managing compliance takes resources, but it’s nowhere near as expensive as the costs associated with a breach.
Firewalls safeguard sensitive data, helping organizations avoid costly penalties and reputation damage. Moreover, many experts believe that the implementation of robust firewall systems is a proactive measure that significantly contributes to achieving compliance with regulatory standards. -
Remote Access Security: With the rise of remote work, securing remote access connections has become increasingly important. Firewalls ensure that employees can work from anywhere without compromising the enterprise system, maintaining the integrity and security of the corporate infrastructure.
-
Monitoring and Logging: Firewalls provide valuable logging and monitoring capabilities, enabling businesses to track network activity and identify potential threats in real-time. A notable case study involves a financial institution that successfully thwarted a cyber attack by analyzing security logs, demonstrating the practical benefits of such systems in real-world scenarios. Comprehending network security operations and routinely examining reports, as emphasized in quarterly rule assessments, is essential for efficient management. This systematic approach helps maintain security and compliance, ensuring that the network remains resilient against evolving cyber threats.
Choosing the Right Firewall: Factors to Consider for Optimal Security
When choosing a security barrier, consider the following factors:
- Type of Firewall: Assess whether a hardware, software, or cloud-based solution best fits your organization’s needs.
- Scalability: Ensure that the security system can grow with your organization, accommodating increased traffic and additional features as needed.
- Performance: Assess the system's throughput and latency to ensure it can manage your network traffic efficiently without bottlenecking performance.
- Cost: Consider the total cost of ownership, including initial purchase, maintenance, and potential upgrades.
- Integration Capabilities: Ensure the protective system can seamlessly connect with your current safety framework and other technologies.
- Vendor Support: Seek vendors that provide dependable assistance and frequent updates to ensure optimal protection.
Enhancing Network Security: Beyond Traditional Firewalls
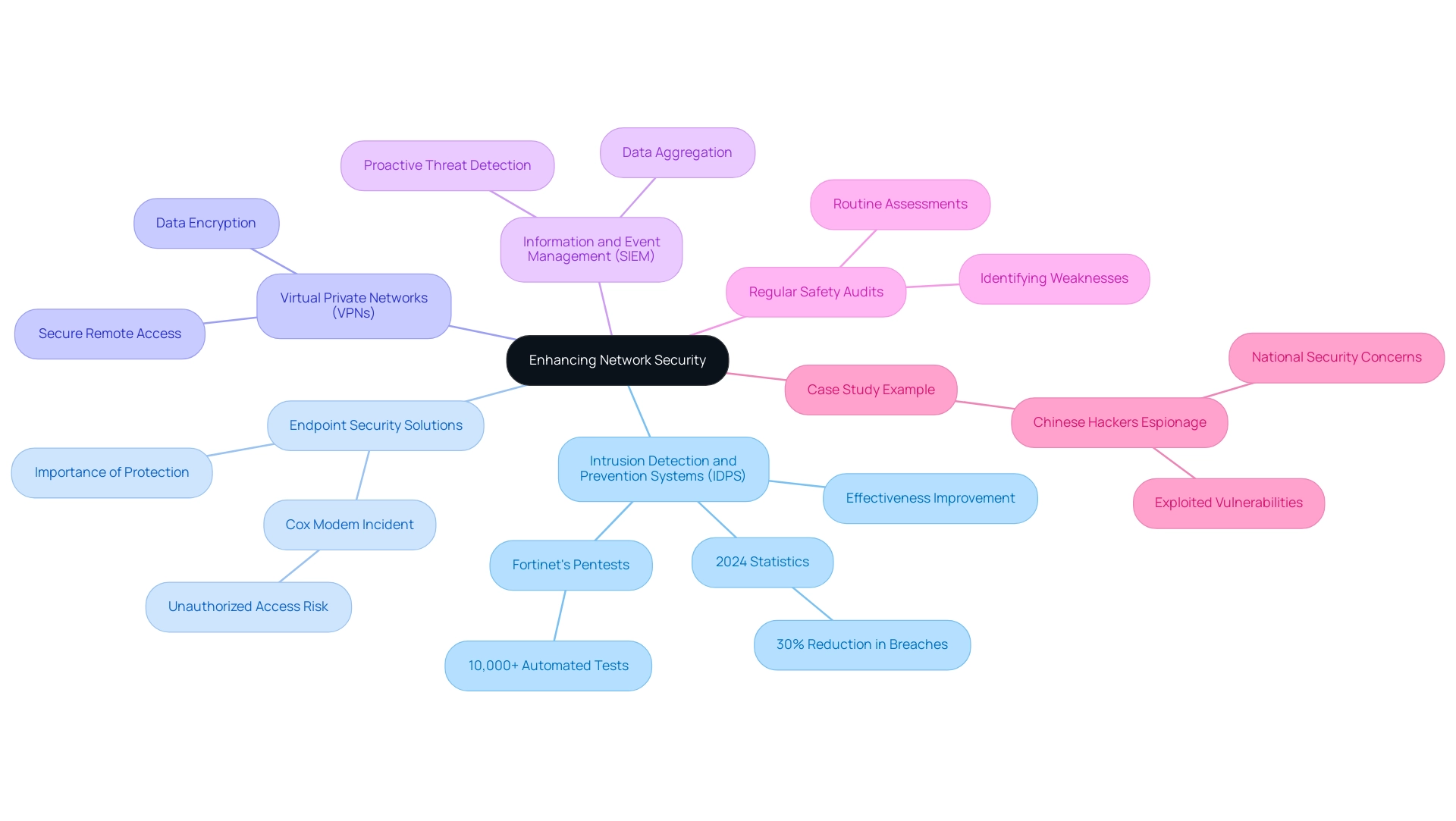
To further improve system protection beyond conventional firewalls, consider the following measures:
- Intrusion Detection and Prevention Systems (IDPS): These systems are essential for monitoring traffic and identifying suspicious activities. Recent advancements in IDPS technology have significantly improved their effectiveness, with statistics from 2024 indicating a 30% reduction in security breaches where IDPS are deployed. Notably, Fortinet's extensive infrastructure pentests have highlighted vulnerabilities that IDPS can mitigate effectively.
- Endpoint Security Solutions: Protecting individual devices connected to the network is paramount. Endpoint protection solutions ensure that vulnerabilities at the endpoint level do not compromise overall safety. Recent news revealed that flaws in Cox modems could have allowed unauthorized access and command execution, impacting millions of devices. This incident highlights the necessity for strong endpoint protection measures to tackle current threats.
- Virtual Private Networks (VPNs): VPNs encrypt data transmitted over the internet, providing secure remote access for employees. This is especially critical in protecting sensitive information from unauthorized access during transmission.
- Information and Event Management (SIEM): Implementing SIEM solutions aggregates and analyzes data from various sources, offering comprehensive visibility into potential incidents. This enables more proactive threat detection and response, enhancing overall system security.
- Regular Safety Audits: Conducting routine assessments of your network protection posture is essential to identify weaknesses and areas for improvement. As researcher Sam Curry noted, vulnerabilities can allow external attackers to gain unauthorized access and execute commands, as was demonstrated in recent findings with Cox modems. Regular audits ensure that your protective measures evolve alongside emerging threats.
- Case Study Example: A notable instance involves Chinese hackers exploiting vulnerabilities in T-Mobile and other U.S. telecom companies as part of a broader espionage campaign. This case highlights the importance of implementing comprehensive security measures, including firewalls, IDPS, and endpoint security solutions, to safeguard against such sophisticated attacks.
By integrating these advanced security measures, businesses can significantly enhance their network security, safeguarding against sophisticated cyber threats and ensuring the integrity of their operations.
Conclusion
In summary, the importance of network firewalls in safeguarding organizational infrastructure cannot be overstated. As the first line of defense, firewalls play a pivotal role in monitoring and controlling network traffic, thus protecting sensitive data from unauthorized access and cyber threats. The article highlights various types of firewalls, including packet-filtering, stateful inspection, proxy, next-generation, and unified threat management firewalls, each offering unique security benefits tailored to different organizational needs.
The advantages of implementing robust firewall solutions extend beyond mere protection. They enhance network performance, ensure regulatory compliance, and facilitate secure remote access, all while providing critical monitoring capabilities that allow for real-time threat detection. Furthermore, with the cyber threat landscape continuously evolving, organizations must remain vigilant and adaptable, investing in the latest firewall technologies and supplementary security measures to fortify their defenses.
Ultimately, prioritizing firewall security is imperative for any organization aiming to safeguard its digital assets. As cyber threats grow more sophisticated, the integration of advanced firewall solutions into a comprehensive cybersecurity strategy becomes not only beneficial but essential for maintaining the integrity and security of network infrastructures. By taking informed actions today, organizations can better prepare for the challenges of tomorrow's cybersecurity landscape.




