Introduction
Multi-tenant architectures play a pivotal role in cloud computing, enabling a single instance of software to serve multiple user groups or "tenants" while maintaining privacy and security. This article explores the key features, benefits, and challenges of multi-tenant architectures, as well as different types of multi-tenant designs. It delves into topics such as resource sharing, data isolation, scalability, customization, and performance optimization.
The article also addresses important considerations like security, compliance, and best practices for implementing multi-tenant architectures in multi-cloud environments. With insights from real-world examples and industry experts, this comprehensive guide provides valuable information for businesses aiming to leverage multi-tenant architectures and thrive in today's digital landscape.
What is a Multi-Tenant Architecture?
Multi-tenant framework is a structure that allows a single instance of software to serve multiple user groups or 'tenants', much like a shared apartment building with separate units but common infrastructure. This architecture is essential in computing environments, where it offers each tenant with privacy and the option for configuration customization while utilizing the same underlying resources. A tenant, in this context, could be an individual user, a group, or an entire organization. Despite the shared environment, the tenants' data and configurations are kept separate and secure, ensuring that the actions of one tenant do not impact the others. This separation is achieved through isolation mechanisms within the application, which are a cornerstone of multi-tenancy and a reason for its efficiency and security.
Companies such as Nubank have utilized multi-tenancy to expand internationally, catering to millions of customers by embracing a cloud-native strategy and constructing microservices that operate on a monolithic infrastructure. This approach emphasizes the significance of a standardized tech stack and consistent problem-solving methods, which are crucial in a shared environment. The industry that deals with cloud computing, experiencing a surge in demand, especially for AI applications, is poised to grow at a compound annual growth rate of 21.2% from 2024 to 2030. In such a landscape, the capacity to offer shared solutions is more relevant than ever, providing clients with flexibility and cost savings, as demonstrated by the numerous services provided by companies like AWS and the evolving privacy policies of tech corporations.
Key Features of Multi-Tenant Architectures
Multi-tenant structures are a foundation of cloud computing and SaaS applications, providing a way to serve multiple user groups or tenants through a single software instance. This approach not only ensures efficient resource utilization but also provides key benefits such as workload isolation, which addresses the issue of a "noisy neighbor" effect where one tenant's excessive resource use could impact others.
A real-world example of multi-tenancy's effectiveness can be seen in Dunelm Group plc, the UK's leading homewares retailer, which leverages its digital platform to handle over 400 million sessions annually, contributing to approximately 35% of the company's revenue. As companies like Dunelm grow, they often transition to designs that can accommodate multiple occupants in order to facilitate their expansion and efficiently manage online services that generate high revenue.
Furthermore, adopting solutions that serve multiple users simultaneously is not without its difficulties, as demonstrated by the experiences of businesses transitioning to multi-cloud environments. Approximately 18% of UK businesses are actively adopting multi-cloud strategies, driven by the flexibility and cost-effectiveness of such architectures. Nevertheless, they must navigate the complexities involved, including managing larger IT estates with more endpoints.
The shared resources in environments with multiple tenants, such as servers and storage, are utilized efficiently while maintaining the privacy and configuration customization for each tenant. This model is particularly beneficial for organizations with smaller IT departments, like IFCO, which partnered with Rackspace Technology to leverage their expertise in cloud transitions, emphasizing customer-centric solutions and alternative approaches.
As the structures that serve multiple companies continue to evolve, they play a crucial role in enabling companies to innovate and adapt to market demands. Snap Inc., the parent company of Snapchat, with 750 million users worldwide, heavily invests in technologies like augmented reality and AI-powered chatbots, which are supported by scalable and efficient infrastructures.
In conclusion, multi-tenant structures offer a path to scalability, efficiency, and customization, essential for businesses aiming to thrive in today's digital landscape.
Resource Sharing
In the rapidly evolving tech landscape, the idea of multi-tenancy in cloud structures stands out as a significant advancement. This design enables a sole instance of a software application to cater to different tenants—whether they are individual users, groups, or entire organizations—while guaranteeing the segregation and security of each tenant's information and settings. The effectiveness of a building with multiple residents sharing common infrastructure is comparable to an apartment building, where each resident has their own privacy. It's a design that not only maximizes resource utilization but also delivers cost efficiencies, as tenants utilize and pay for only the resources they need.
The importance of multi-tenancy is underscored by its pivotal role in the SaaS (Software as a Service) model and its applicability across diverse B2B contexts. For enterprise clients, this architecture facilitates essential requirements such as high availability, effective resource and cost management, and stringent data security. Additionally, the implementation of a shared approach streamlines development processes, reduces technical complexities, and facilitates scalable growth. Such benefits are clearly demonstrated in cases like Dunelm Group plc, where a robust multi-tenant platform underpins their high-traffic, revenue-generating digital platform.
Nevertheless, as institutions such as the Albert Einstein College of Medicine have found, adopting multi-tenancy in the computing environment presents its own set of difficulties. It involves intricate scheduling and resource allocation issues. However, when executed correctly, multi-tenancy in cloud environments enables organizations to leverage shared resources efficiently, echoing the sentiment that in the digital economy, 'time is money'. Ultimately, the decision between multi-tenant and single-tenant approaches depends on the particular needs and strategy of the organization, with each providing unique benefits in relation to customization, privacy, and resource allocation.
Data Isolation
Multi-tenant cloud structures are crucial for scalable applications, enabling efficient resource utilization while protecting each tenant's information. These architectures typically use different database design patterns to ensure isolation - an important factor in maintaining privacy and security. Postgres, for example, offers several approaches for multi-tenant database design. One such approach is creating separate databases for each customer, which maximizes isolation by potentially running distinct copies of the application for each tenant. This strategy aligns with the broader industry trend towards ensuring comprehensive residency of information, as demonstrated by Microsoft's EU Boundary for the Microsoft Cloud, which commits to local storage and processing of all personal data.
As companies progressively adopt cloud-based services for various needs, including virtual desktop infrastructure (VDI), the importance of information isolation grows. The shift towards remote work has brought into sharp focus the need for secure, device-agnostic access to corporate resources across laptops, phones, and other mobile devices. A strong multiple-user structure not only facilitates large-scale operations but also meets the needs of a dispersed workforce that depends on online services for data in motion, at rest, and in use.
Acknowledging the complexities of the physical world, it's essential to design multi-tenant systems that are prepared for expansion from the outset. The decision to segregate databases per customer is a testament to the industry's understanding that while time to market is crucial, so is the flexibility to scale and adapt without compromising on reversibility or security.
Scalability
Multi-tenant cloud structures represent an efficient pattern within cloud computing and SaaS applications, where a singular software instance can proficiently serve an array of user groups or 'tenants'. This paradigm ensures each tenant's data and configuration remains insulated, yet simultaneously capitalizes on shared core computing resources. The architecture's inherent scalability is a critical asset, particularly when addressing the variable demands of cloud-based applications. It is adept at dynamically expanding to accommodate new tenants or scale with the increasing demands of existing ones, a feature that is paramount in a landscape where user numbers can fluctuate markedly. Furthermore, the model that allows multiple tenants adeptly handles the 'noisy neighbor' issue by isolating workloads, ensuring one tenant's resource consumption does not adversely impact another. As businesses continue to evolve and seek innovative, efficient service delivery methods, the flexibility of shared data management becomes ever more valuable, particularly when aligning with strategic growth and adopting a multi-region presence as exemplified by Microsoft Azure's expansion.
Customization and Configuration
Multi-tenant designs are created to cater to multiple user groups or tenants within a single software instance, providing a harmonious blend of individual customization and shared infrastructure. For instance, Dunelm Group plc, the top homewares retailer in the UK, utilizes a shared infrastructure to effectively handle the heavy load on its digital platform, which contributes to around 35% of the company's earnings. This design pattern allows each tenant to experience a personalized interface and settings, while also benefiting from cost savings and resource pooling. Furthermore, multi-tenant architectures excel in isolating workloads, preventing the 'noisy neighbor' issue where one tenant's excessive resource use can negatively impact others. Such an approach is integral to cloud computing and SaaS applications, promoting service delivery with high efficiency.
This strategic sharing of computing resources, such as servers and storage, while maintaining isolated information and configurations for each tenant, is not only prevalent but essential in today's complex distributed systems. It addresses the challenges posed by complicated systems, which, according to studies by Tanriverdi, are more predictable and controllable due to their structured interconnections. Conversely, complex systems with unstructured interconnections, such as those seen in healthcare, are more susceptible to breaches. The model that serves multiple tenants mitigates these risks by reducing data transfer points and simplifying connections, resulting in a secure, scalable, and efficient framework for managing diverse customer needs in a multi-cloud environment.
Types of Multi-Tenant Architectures
Investigating the realm of shared infrastructures uncovers a range of design patterns, each customized to particular business requirements and scalability needs. For instance, taking a leaf from the playbook of Dunelm Group plc, we observe that high-traffic retail platforms may opt for a microservices-based approach to maintain agility in the front-end layer, thereby catering to their extensive customer base.
In the case of Nubank, a cloud-native stance from inception enabled the development of numerous microservices, supporting rapid scaling and a consistent technological framework. This harmonized approach underscores the importance of a standard tech stack, capable of evolving in unison with the organization's growth trajectory.
Azure's guidance on constructing Virtual Desktop structures for resiliency and availability exemplifies the strategic mindset required to ensure business continuity. It addresses the varying degrees of impact from local to region-wide disruptions, emphasizing the necessity for geo disaster recovery planning.
Furthermore, the observations from Hrishikesh Joshi at Okta emphasize the delicate equilibrium between system security and scalability, which is vital for enterprise-level multi-tenant structures.
A common pattern, especially within Postgres-based systems, is the allocation of a separate database for each customer, granting unparalleled isolation and the potential to run complete application instances independently. This method not only maintains data integrity but also allows for customized encryption protocols, ensuring client-specific security compliance.
The extensive collection of more than 6 million datapoints across various sectors, as specified by Juniper Research, emphasizes the importance of data-driven decision-making in design. This quantitative support provides a strong basis for CTOs to navigate the complexities of shared environments, aligning technology investments with business objectives and fostering innovation within their teams.
In brief, the combination of various tenant structures is determined by factors such as customer segmentation, needs for isolating information, and aspirations for scalability, all of which must be carefully considered to design solutions that can adjust and develop with the enterprise's progress.
Shared Database Architecture
In multi-tenant cloud structures, the idea of sharing a single database among different tenants is indeed resource-efficient, yet it brings forth certain pivotal challenges. The core of this structure is the rational division of every tenant's information within the database. Using distinct identifiers or schemas, it maintains integrity while capitalizing on shared resources. Nevertheless, this structure can face bottlenecks in terms of performance and scalability, as observed in environments like Grafana Cloud. Here, each customer's data is isolated in single-tenant databases on globally distributed servers. Despite the small size of these databases, usually less than 100 MB, the structure maintains workload isolation, which is critical to prevent the 'noisy neighbor' scenario where one tenant's excessive resource usage could impinge on others.
Comprehending the limitations of the physical world, as highlighted by specialists in distributed systems, is crucial when handling these structures. The ACID properties in a distributed environment—Atomicity, Consistency, Isolation, and Durability—must be carefully balanced against the limitations of network latency and hardware capabilities. Moreover, the intricate process of data migration to such systems necessitates the use of specialized tools and methodologies, like open-source utilities, customized scripts, and advanced features of databases like Snowflake, which offer parallel processing, efficient data compression, and incremental batch loading.
The compromises in handling shared infrastructures are not insignificant. They often involve a complex mesh of considerations encompassing compute, network, and warehouse costs, which demand meticulous planning and execution. As the industry advances, the adaptation and optimization of these systems are paramount, and CTOs must be skilled at navigating these challenges to harness the full potential of multi-tenant and single-tenant architectures within multi-environment.
Virtualization-Based Architecture
In the landscape of cloud computing, where the SaaS model is rapidly becoming the norm, the concept of multi-tenancy is gaining prominence. Multi-tenancy, akin to a shared apartment building with multiple distinct living spaces, allows numerous customers, or 'tenants,' to use a single instance of a software application. Importantly, while they share the core infrastructure and application code, their data and configurations remain private and secure, isolated from one another. This design is not only efficient but also bolsters security.
Virtualization plays a crucial part in facilitating this structure. Each tenant is provided with a virtual machine (VM) or container, offering a dedicated instance of the application in a consolidated environment. This method not only strengthens the isolation between tenants but also optimizes hardware use, streamlining operations and enhancing disaster recovery processes. With virtualization, companies like Rivian, who are pushing for sustainability and efficiency, can harness these benefits across their global operations, minimizing waste and adhering to their ambitious net-zero emissions goals.
The adoption of virtual environments facilitates better resource management and reduces capital expenditures, which is evident in the widespread use of virtualization in centers, as reported by Statista with a market value of approximately $6 billion in 2020. Moreover, it's not limited to large-scale IT; virtualization is increasingly vital in software development, providing developers with the versatility to test applications across various operating systems without the need for multiple physical machines.
In the industrial sector, although virtualization is less prevalent, the digital transformation is rapidly increasing the number of hardware resources, like PLCs and IPCs. This surge necessitates more efficient monitoring, updating, and troubleshooting methods. Virtualization offers a solution by allowing the consolidation of these discrete resources into a unified virtual environment, potentially reducing downtime and productivity losses.
As the industry changes, the decision between multi-tenant and single-tenant structures becomes crucial. Multi-tenant data management, where virtualization underpins the separation of tenants, aligns with the need for scalable, secure, and efficient cloud services. It's crucial for organizations to choose the structure that most suits their application needs, taking into account the technical and economic consequences of each model.
Containerization-Based Architecture
By utilizing containerization technologies like Docker, modern designs offer a strong answer to the difficulties of multi-tenant environments. These lightweight, portable containers encapsulate each tenant's application instance, ensuring a distinct, secure environment without the overhead of traditional virtualization. This approach not only streamlines deployment processes but also facilitates consistency across development teams and their varied tech stacks—such as Java, Scala, Nodejs, and Microsoft .Net—as demonstrated by Tabcorp's transformation from a fragmented deployment strategy to a more unified and automated one.
The significance of containerization in distributed systems cannot be overstated. It strikes the right balance between decentralization, fault-tolerance, and scalability, as underlined by the design principles of distributed systems. By enabling automation and fostering communication between nodes, container technologies are instrumental in the successful implementation of distributed systems. Moreover, as organizations like Catalogic Software recognize the potential of container backup solutions, the industry sees an uptick in adoption and innovation, signaling a trend towards on-premises and multi-cloud container management.
With the rapid evolution of software development, as captured in Docker's State of Application Development Report, it's evident that containers are pivotal in addressing the needs of developers. They facilitate effective software development and deployment in various environments, aligning with the current trend towards AI/ML, microservices, and proactive security measures. As container technologies continue to mature, their role in multi-cloud environments is expected to become even more prominent, offering a strategic advantage to organizations that harness their capabilities.
Benefits of Multi-Tenant Architectures
Multi-tenant structures are progressively becoming the foundation of cloud services, providing a range of benefits that cater to the dynamic requirements of businesses and end-users alike. These structures enable a single instance of software to serve multiple clients or 'tenants,' ensuring efficient resource utilization and streamlined management. Companies like Dunelm Group plc, which thrives on high website traffic and significant digital revenue, benefit from such architectures as they scale up their operations. By implementing a shared infrastructure approach, they are able to support growth without compromising on the frontend services that are critical to their revenue stream.
In contrast, organizations like IFCO have utilized partnerships with cloud experts such as Rackspace Technology to navigate their entry into cloud services, emphasizing the importance of customer-centric approaches and the capabilities of experienced professionals in ensuring a smooth transition to shared environments.
Furthermore, multi-tenancy plays a pivotal role in operational efficiency, as demonstrated by Delivery Hero's initiative to reduce IT bottlenecks. By tackling the problem of account lockouts through a shared cloud-based platform, they greatly reduced the amount of time employees spent unable to access their accounts, thus improving productivity across their large workforce.
Multi-tenant structures in the skies are not just a tactical reaction to current operational difficulties but also a future-oriented investment. In line with the perspectives of industry professionals like Rene Millman and Ollie Harding, businesses that are transitioning to shared cloud-based environments can anticipate overcoming conventional IT challenges, such as inflexible systems that impede flexibility and prolong the time it takes to deliver software.
The effect of multi-user designs is also reflected in data emphasizing the rapid transition to computing during the global pandemic. The flexibility of these structures in supporting a range of devices and facilitating remote work has led to a lasting change in the workforce's expectations and working patterns.
In the age of digital disruption, companies that are able to adapt and grow demonstrate the effectiveness of utilizing shared resources, customization, and privacy to achieve business success and foster innovation.
Cost Efficiency
Multi-tenant cloud architectures offer a compelling value proposition by leveraging shared resources to drive down costs. For example, Sirius Technologies, with a focus on the financial services industry, took advantage of a shared platform to oversee Cloud Development Environments (CDEs), thus improving efficiency and facilitating worldwide cooperation. These strategies demonstrate how systems that serve multiple users can democratize access to advanced technologies, enabling organizations like Delivery Hero to address operational challenges such as reducing the time spent on account recovery. This not only improves efficiency but also aligns with broader industry trends where operational efficiency is increasingly prioritized, as evidenced by companies like Pfizer and BlackRock emphasizing it in earnings calls. Furthermore, embracing multi-tenancy can lead to substantial cost savings. As per Enterprise Strategy Group, 86% of organizations utilize multiple cloud providers, however IDC highlights that up to 30% of spending on cloud is wasted. By utilizing multi-tenant structures, organizations can leverage economies of scale, allowing them to provide improved features at a fraction of the expense, which is vital in sectors aiming for operational excellence and cost control.
Scalability and Elasticity
Multi-user cloud structures offer a expandable response for businesses, as evident in the impressive growth of Nubank, which caters to millions of customers worldwide. Their cloud-native approach, with a focus on canonical solutions, allowed for efficient resource allocation and an adaptable infrastructure suitable for various regulatory environments. Such architectures offer the flexibility to scale operations in response to demand, optimizing resource usage and cost. However, this scalability is not without challenges. Technical complexities in scheduling and resource allocation, as well as financial considerations, can make multi-tenancy a controversial topic, as time translates directly into cost in cloud environments. Yet, with strategic implementation, the benefits of multi-tenant systems, including their inherent elasticity, can significantly outweigh these challenges.
Rapid Deployment and Updates
Multi-tenant design is a powerful pattern that enables simultaneous updates and feature rollouts to all users, enhancing the overall deployment process. By enabling a single instance of the software to cater to multiple user groups or tenants, this design ensures that each tenant gains immediate access to the latest enhancements without the need for individual updates. For instance, Dunelm Group plc, a prominent UK homewares seller, utilizes a shared system to effectively handle its substantial online sessions and income generation. Likewise, Purdue University, renowned for its academic prowess and creativity, employs a shared approach to uphold superior service standards throughout its IT infrastructure. This strategy not only optimizes resource utilization but also provides workload isolation, addressing the 'noisy neighbor' problem where one tenant's excessive resource consumption could impact others.
Collaboration and Community
Multi-tenant cloud structures not only optimize resource utilization but also catalyze a collaborative ecosystem among users. Tenants in such environments can tap into communal knowledge, exchanging insights and innovations. This collaboration is evident when tenants engage in activities like screen sharing—a feature indicative of a thriving cooperative space. Take the example of Dunelm Group plc, which has successfully scaled its digital platform to foster a community where integrations and enhancements are shared, driving value across its vast customer base. Similarly, the recent overhaul of the Microsoft Teams app exemplifies how a platform can evolve to support more efficient collaboration, boasting a twofold speed increase and halving memory usage. This progress underscores the importance of a robust 'operating system' within organizations—a framework that outlines how teams collaborate, innovate, and support one another. Such systems, as seen in the transformation of a Latin American bank's digital operations, provide the structure for teams to effectively contribute their skills, manage work processes, and adhere to a culture of constructive collaboration and continuous improvement, much like the Toyota Production System's impact on manufacturing.
Challenges and Limitations of Multi-Tenant Architectures
Mastering the intricacies of multi-tenant design necessitates a comprehensive grasp of both its capabilities and potential hurdles. In the realm of software as a service (SaaS), multi-tenancy enables a single instance of an application to cater to multiple customers or 'tenants'. This collaborative method utilizes the same infrastructure to serve diverse tenants, each retaining their unique information and customization settings. The architecture's cost-efficiency stems from the shared resources, resulting in reduced expenses per user.
However, implementing such systems is not without challenges. Tenant isolation is paramount, ensuring that each tenant’s data and resources remain segregated and secure within the collective environment. Achieving isolation demands robust structures within the SaaS framework to guard against unauthorized resource access. Furthermore, as organizations like Dunelm Group scale their digital platforms, transitioning to a distributed system like microservices on the backend becomes essential, particularly for front-end layers critical to revenue generation.
Resilience is another foundation of systems with multiple tenants, as emphasized by Azure's guidance on business continuity and disaster recovery (BCDR). The need for resiliency spans from local disturbances to region-wide events, with strategies in place for geo disaster recovery ensuring service restoration in alternate regions during crises.
Statistics from the 'State of Multi-cloud 2024' report emphasize the growing trend towards multi-cloud environments, reinforcing multi-tenancy's role in such strategies. As Hrishikesh Joshi of Okta illustrates, designing systems that scale securely is an ongoing challenge. This is especially true when complexity increases—such as post-merger system integrations—heightening vulnerability to breaches, as identified in healthcare systems studies.
In summary, the choice to embrace a shared hosting framework should be based on a thorough examination of particular requirements, difficulties, and recommended methods. As multi-cloud adoption continues to advance, informed by expert insights and reports, organizations must weigh the technical intricacies and economic implications of multi-tenancy against their unique use cases.
Data Security and Privacy
With the growing importance of cloud computing and Software as a Service (SaaS) models, the relevance of multi-tenant structures in the software landscape has increased. Multi-tenant architecture is a framework where a single instance of a software application serves multiple tenants—each tenant being an individual user, a group, or an entire organization. Despite tenants sharing the same infrastructure and application, their information, configurations, and preferences remain insulated and secure, akin to residents of separate apartments sharing the same building but with individualized spaces.
Data security and privacy within these multi-tenant environments are of paramount importance. Tenants must be assured that their information is safeguarded against unauthorized access and breaches. This requires the deployment of robust security measures like encryption and stringent access controls. Furthermore, the administration of these structures must be aware of the different regulations in various nations and areas that require particular procedures for managing and safeguarding customer information.
Recent events, such as the cyberattack on Microchip Technology's facilities and the vulnerabilities found in payment systems, underscore the necessity of prioritizing cybersecurity. The Cisco Cybersecurity Readiness Index has highlighted that nearly 60% of companies experienced a cybersecurity incident in the past year, with significant financial repercussions. This demonstrates the importance of implementing protective measures that not only prevent information leakage but also ensure compliance with regulatory standards.
Furthermore, the Ponemon Institute's report, sponsored by IBM Security, indicates that the average cost of breaches has reached an all-time high in 2023, emphasizing the financial implications of inadequate security measures. As such, it is essential for organizations to understand the potential for misconfigurations, such as those in widely used Amazon S3 buckets, and to maintain a comprehensive understanding of their multi-cloud environments from the identity layer down to the data layer to prevent breaches and uphold ethical standards.
Performance and Resource Allocation
Managing resources in an architecture with multiple tenants requires a nuanced approach to prevent performance issues such as degradation or resource contention among tenants. This complexity arises from the need to accommodate multiple user groups, or tenants, within a single instance of software. The challenge is to ensure that while these tenants share underlying computing resources, their performance remains consistently high.
The multi-tenant approach comes with several advantages, including workload isolation which addresses the "noisy neighbor" problem, where one tenant's overuse of resources can affect others. It enables providers to deliver services with efficiency and is widely used in SaaS applications and cloud computing.
For example, consider the Dunelm Group plc, the UK's leading homewares retailer, which experiences over 400 million website sessions annually and garners about 35% of its revenue from digital platforms. As the company scales, its software structure must evolve to support growth and manage high-revenue-generating frontend operations. A system that supports multiple users is one solution that enables resource sharing and operational efficiency while preserving data isolation and security.
The implementation of such an architecture can be seen in the recent updates from cloud providers, which focus on enabling app creators to build scalable applications. With tools like Azure Arc and updates to Power Apps, which is now used by over 25 million users monthly, managing environments with multiple tenants is becoming more streamlined. These updates facilitate collaboration between different developer roles and provide transparency for those who require a deeper understanding of the source code.
In practice, there are several design patterns for database design with multiple tenants, each suited to different use cases and scalability requirements. One common pattern is having separate databases per customer, offering maximum isolation and the option for individualized web applications. This approach can be beneficial for guaranteeing performance and security but necessitates careful deliberation concerning resource allocation and scheduling to evade typical challenges linked to multi-tenancy in the virtual environment.
Customization Constraints
In the changing landscape of cloud computing, multi-tenant structures are becoming more advanced, enabling a level of customization that can be finely adjusted to fulfill the diverse requirements of different user groups or tenants. This design pattern, where a single instance of software serves multiple tenants, strikes a delicate balance between customization and standardization. Each tenant's information and configuration are isolated, yet they share underlying computing resources such as servers and storage, streamlining operational efficiency and maximizing resource utilization.
Take, for instance, the case of Dunelm Group plc, a leading UK homewares retailer whose digital platform is crucial for their revenue generation. As they scaled, their transition to distributed systems showcased the need for a robust front end architecture that could accommodate their growth while maintaining high performance and customization. In the same way, IFCO's collaboration with Rackspace Technology highlighted the importance of leveraging expertise to navigate the complexities of cloud environments and optimize management for multiple users.
As organizations like Dunelm and IFCO have learned, effective multi-tenant data management is vital, especially when downtime events can impact business resilience. Providers like Microsoft Azure offer guidance on building Virtual Desktop designs that are resilient across local and region-wide events, including geo disaster recovery.
Adopting Infrastructure as Code (IaC) practices, such as the use of Terraform modules, further empowers organizations to manage and deploy cloud environments with greater scalability and efficiency. These modules serve as units of reusable code, promoting standardization across the infrastructure while allowing for necessary customizations.
The advantages of shared infrastructures go beyond mere effectiveness. They also address workload isolation, preventing the 'noisy neighbor' problem where one tenant's over-utilization of resources can affect others. However, providers must navigate the challenges that come with the territory, such as ensuring compliance with data protection regulations and maintaining the agility to adapt to tenant growth and service innovation.
To sum up, the utilization of shared resources in cloud-based systems presents an attractive framework for delivering services in environments with multiple clouds, striking a balance between the demand for customized services and the management of standardized infrastructure. As the technology and strategies around these structures evolve, providers will continue to refine their approaches to meet the customization demands of their clients while preserving the integrity and efficiency of their shared resources.
Multi-Tenant vs. Single-Tenant Architectures
Comprehending the complexities of cloud structures, particularly multi-tenant and single-tenant models, is crucial for those engaged in the strategic planning and implementation of cloud services. Multi-tenant design is similar to an apartment building, where resources are shared among multiple tenants—or, in this context, clients. A single database can serve multiple customers, with design patterns in systems like Postgres allowing for scalability should the client base expand significantly. On the other hand, single-tenant design offers a standalone environment, much like a detached house, with dedicated resources for a single client, providing maximum isolation and the potential for tailored encryption measures.
Agile methodologies, frequently used in software development, mirror the flexibility of environments with their focus on adaptability and rapid iteration. Nevertheless, as Agile encounters difficulties expanding in bigger companies, the decision between shared and dedicated structures also necessitates deliberation of company size, product delivery, and customer relationships. Enterprise design, as explained by Jeanne W. Ross, Peter Weill, and David C. Robertson, gives priority to comprehending these customer and product dynamics over internal company mechanisms.
In the realm of data, with over 6 million datapoints indicating the vast scale of technological deployment across sectors, the choice between multi-tenant and single-tenant structures is not trivial. It impacts not only the immediate IT infrastructure but also the broader capability for innovation and adaptation within an organization's technology strategy. As companies navigate their digital transformation journeys, the alignment of their selected cloud infrastructure with their overarching enterprise architecture is crucial for success in a technology-driven marketplace.
Resource Utilization
Multi-tenancy in cloud computing offers a significant advantage in terms of resource utilization by allowing various customers, or 'tenants', to share a single instance of an application or computing resource. Each tenant, whether an individual, a group of users, or an entire organization, utilizes the same infrastructure and application but maintains a private, secure environment for their information and configurations. The strength of multi-tenancy lies in its ability to efficiently share resources—akin to an apartment building with shared amenities but private living spaces—while ensuring that each tenant's data remains isolated and unaffected by others.
In contrast, single-tenant designs assign dedicated resources to one tenant exclusively. While this can provide a sense of security and control for the tenant, it often leads to a less efficient use of resources due to potential underutilization. Choosing between shared and dedicated environments involves assessing the requirement for efficiency and resource optimization while considering the preference for exclusive setups. As the digital landscape evolves, optimizing power use and growing sustainably become paramount, with practices such as power harvesting—that has reclaimed enough electricity to power millions of electric car miles—mirroring the efficiency goals of multi-tenancy. Embracing multi-tenancy can align with such sustainability efforts by maximizing the use and allocation of computational resources.

Cost
Understanding the intricacies of cloud structures is vital for organizations, particularly when taking into account the expense and administration consequences of multi-tenant and single-tenant environments. Multi-tenant structures provide a shared environment where resources are used by multiple tenants, resulting in potentially lower expenses and the opportunity to access advanced features without the higher price. On the other hand, single-tenant architectures provide a dedicated space for each tenant's resources, ensuring isolation and control but often at a higher cost.
In light of recent global shifts towards remote work, many organizations have had to rapidly adapt their IT infrastructure. During the pandemic, companies utilized public computing services to implement virtual desktop infrastructures (VDIs), enabling employees to work remotely from different devices, such as laptops and phones. This shift to the sky not only enabled immediate needs but also ignited a long term shift in work dynamics, with a significant number of employees favoring the flexibility of working from home.
The choice between single and multiple user architectures isn't just about upfront expenses but also entails evaluating the long-term worth and return on investment (ROI) of the computing platform. It's crucial to consider factors such as IT productivity, business innovation, and the incorporation of advanced technologies like generative AI, which can greatly enhance the value obtained from adopting new technologies. While multi-tenant solutions are typically more cost-effective due to resource sharing, organizations must assess their unique needs, such as security requirements, application sensitivity, and the necessity for collaboration across various organizational boundaries, as outlined by industry leaders.
Recent reports have emphasized the significance of planning and prioritizing investments in the digital realm to maximize ROI. Organizations are encouraged to develop comprehensive strategies, like creating detailed playbooks for information sharing and adopting a multiprovider approach, to navigate the complexities of cloud-based environments effectively. These strategies enable better decision-making regarding technology investments and the management of technical projects, ultimately driving an organization's technological vision forward in a multi-cloud landscape.
Security and Isolation
Single-tenant cloud structures are praised for their improved security and isolation capabilities. This design guarantees that every client or tenant possesses their own collection of dedicated resources, which inherently diminishes the possibility of breaches in information and unauthorized entry. For example, Sirius Technologies, a company focused on delivering financial services, transitioned to a single-tenant environment to manage their Cloud Development Environments. This shift was critical in addressing productivity challenges, intellectual property management, and facilitating secure global collaboration. Conversely, architectures that serve multiple users, while being effective and economical, require strict security measures to protect the privacy and integrity of information. Multi-tenancy is exemplified by Chess.com, which serves millions of users daily. Their Head of Infrastructure, James Kelty, emphasizes the importance of a robust IT infrastructure that can securely scale to accommodate a global audience. The adoption of zero-trust security models and consolidated security platforms is becoming increasingly prevalent in shared environments. These models operate on the assumption that breaches are inevitable and therefore require constant user authentication and strict access controls based on user identity. Such measures are crucial in scenarios with multiple tenants to ensure that each tenant's data remains private and secure.
Designing a Multi-Tenant Application
Crafting a multi-tenant SaaS application is a pivotal task that hinges on strategic planning to address distinct business requirements and to ensure readiness for potential expansion. The architecture must be robust enough to support service availability on a global scale, which may necessitate a multi-region design. This is especially true for applications that require constant uptime for a worldwide customer base. Furthermore, the concern of sovereignty over information is of utmost importance, requiring that customer information be kept within designated national borders in order to adhere to regulatory requirements. When considering multi-tenant database design patterns, particularly with Postgres, developers have several options. One prevalent method involves creating separate databases for each customer, offering the highest degree of isolation and the opportunity for individual information encryption. This approach, while providing maximum security and isolation, must be balanced against the need for rapid market deployment without locking the application into inflexible design choices that are challenging to undo. Leveraging over 6 million data points from Juniper Research, which cover a broad spectrum of sectors, it is evident that thorough market analysis can significantly inform these architectural decisions. Such information emphasizes the significance of designing scalable systems that can accommodate a diverse range of FinTech, Telco, and IoT market demands. Sharing resources like databases and servers among all clients in a shared system increases cost efficiency, resulting in reduced cost per user. The shared infrastructure, however, must maintain strict isolation to ensure privacy and security for each tenant. As articulated by industry experts, the selection between multi-tenant and single-tenant architectures is driven by scalability, cost, security, and customization requirements, each carrying its own set of advantages and challenges.
Data Isolation and Security
In the fast-evolving landscape of digital transformation, where the banking sector is rapidly adopting new technologies to meet all-digital customer experiences, isolation and security mechanisms have become paramount. M&T Bank, a long-standing organization with more than 21,000 employees, has embraced these changes by enforcing Clean Code standards to ensure software reliability and compliance—critical steps in safeguarding sensitive information and transactions. Similarly, companies like Snap have recognized the importance of robust security infrastructure with millions of users interacting daily on platforms like Snapchat and MyAI.
To reduce the risk of breaches, such as the ones that impacted AT&T and Change Healthcare in 2024, revealing personal and medical records of millions, it is crucial that organizations utilize advanced encryption methodologies, strict access controls, and efficient information segregation techniques. The Microsoft Digital Defense Report highlights that AI, while crucial in advancing cybersecurity, necessitates a wealth of information to effectively preempt potential threats. As emphasized by the IACS cyber-security management system guidelines, it is crucial to identify and map information flows, asset classifications, and their business value to fortify defenses against cyberattacks. This multifaceted approach ensures that customer data and sensitive business information remain secure in the face of ever-growing cyber threats.
Scalability and Performance
Creating scalable and high-performance applications is a key element of success in multi-tenant environments. As organizations like Chess.com experience exponential growth, with over ten million games played daily by a community surpassing 150 million users, the infrastructure must not only support this expanding user base but also maintain top-notch performance. James Kelty from Chess.com illustrates this by emphasizing the necessity for a strong IT infrastructure that can handle public computing and on-premises solutions seamlessly to deliver outstanding user experiences globally.
Similarly, Canara HSBC's COO, Sachin Dutta, underscores the significance of modernizing architecture to enhance developer efficiency and reduce manual intervention, aiming for instantaneous policy delivery and claim settlements. This level of efficiency is achieved through a transformative focus on technology, analytics, and mobility, enabling a more integrated organization that leverages automation.
Microsoft Azure exemplifies the strategic approach to scalability and performance in cloud computing. By expanding global footprints and diversifying Azure regions, Microsoft empowers businesses to build and manage applications with unparalleled performance, availability, and security, while also offering the flexibility of a multi-region growth strategy.
When considering database design for multiple tenants, especially in Postgres, it is essential to take into account the different approaches from the beginning, such as having separate databases for each customer to ensure maximum isolation and scalability. This strategic planning ensures readiness for massive scale demands and aligns with insights from experts in the field. For instance, the analysis of cloud-native systems and the challenges unique to their workloads suggest that careful planning and execution are required to achieve the desired scalability and performance.
Hence, for any organization aiming to excel in a multi-tenant environment, it's essential to embrace a forward-thinking framework that can accommodate rapid growth while delivering consistent, high-quality performance to every tenant.
Customization and Configuration
Designing a cloud structure that allows customization while maintaining the integrity of a shared system requires a strategic approach. Such a structure must enable individualized settings for each tenant, ensuring that modifications by one tenant do not disrupt the services of others. This principle of isolation is central to architecture that serves multiple user groups, each with their own secure and private environment, using a single software instance. Key benefits of this approach include efficient resource utilization and workload isolation, which prevents any single tenant from consuming excess resources to the detriment of others.
Infrastructure as Code (IaC) plays a pivotal role in achieving this delicate balance. By codifying infrastructure, organizations can automate provisioning and management, leading to consistent and replicable environments. Terraform, a widely recognized IAC tool, further streamlines this process through modules that encapsulate common infrastructure elements, fostering standardization and simplification. These modules can be quickly deployed and scaled, in line with the dynamic nature of shared systems and the changing landscape of cloud computing.
Recognizing the significance of well-organized shared environments, top players in the industry have adopted platform engineering to strengthen their infrastructure services. The flexibility provided by such platforms is clear in their extensive use across different sectors, from SaaS applications to internal corporate information systems. As market dynamics evolve, the pursuit of operational efficiency and compliance with protection regulations continues to stimulate innovation in the management of shared resources.
Managing Multi-Tenant Architectures in Multi-Cloud Environments
When navigating the complex terrain of multi-cloud environments, designs that accommodate multiple occupants are crucial. These structures accommodate multiple user groups through a single software instance, guaranteeing that the data and configurations of each tenant are isolated, while also utilizing shared computational resources such as servers and storage. Retail giant Dunelm, for instance, leverages this model to manage their immense digital platform effectively. Now, envision a housing complex as an apartment building where all occupants utilize shared infrastructure but reside in separate units; this is similar to how multi-user applications function, offering both safety and effectiveness.
Microsoft's strategy of leveraging multi-tenant and single-tenant integration across a wide network showcases the seamless connections between Azure, AWS, and GCP. With over 200 edge Pops and an extensive peering system, Microsoft ensures optimized Public IP connectivity, thanks to dedicated private network interconnects (PNIs) that deliver low latency and high reliability. Moreover, their Azure Arc solution facilitates multicloud orchestration, enabling businesses to apply Azure management services across various environments, thereby simplifying infrastructure management.
Multi-tenancy is not a one-size-fits-all solution, however. It's crucial to align the design with the application's needs, considering factors such as workload isolation, which prevents the 'noisy neighbor' issue where one tenant's excessive resource consumption affects others. Given the increasing significance of multi-tenancy in cloud-based computing and SaaS, the 'State of Multi-cloud 2024' report provides guidance on the intricacies of multi-cloud implementation, highlighting its inescapability. In the end, the combination of multiple tenant and single-tenant structures in multi-cloud settings requires a strategic method of management, guaranteeing effective resource allocation and meeting the requirements of all tenants without making any concessions.
Cloud Provider Selection
Choosing an appropriate cloud service provider is essential for ensuring seamless integration and compatibility across multi-cloud environments. Providers must offer a range of features and services that support multi-tenant systems and also cater to the specific requirements of your applications and business model. Multi-tenant architecture, where a single instance of software serves multiple user groups, is prevalent in computing, offering benefits such as workload isolation and operational efficiency.
As demonstrated by the strategic partnerships of enterprises like IFCO with Rackspace Technology, and the comprehensive support from NVIDIA Inception program for startups, it becomes clear that the expertise and customer-centric approach of providers significantly influence the success of cloud implementations. Moreover, with an astonishing 62% of organizations utilizing multi-cloud environments and an additional 18% in the transition phase, the choice of cloud provider becomes a critical decision for businesses looking to leverage the flexibility, agility, and cost-effectiveness of multi-cloud.
OVHcloud's report highlights that half of the organizations recognize the flexibility of multi-cloud as a core strength, with improved agility and reduced organizational risk following close behind. Furthermore, the implementation of a multi-region expansion approach, as recommended by Microsoft Azure, emphasizes the requirement for companies to have access to varied geographic regions for improved performance, availability, and security of their cloud-based solutions.
Considering these factors, the choice to collaborate with a cloud provider should be based on their ability to provide customized services on a shared infrastructure, ensuring isolation and security while taking advantage of operational efficiencies. The provider's commitment to adapting to customer growth and offering the flexibility required for a successful transition to cloud-managed services is of paramount importance for modern businesses navigating the digital landscape.
Data Replication and Backup
The utmost importance of resilience cannot be emphasized enough in today's digital economy, where information is often referred to as the new oil. In reality, studies indicate that 43% of companies that experience significant loss of information are unable to sustain their business operations. To combat this, implementing robust information replication and backup strategies is crucial. The process involves duplicating information across multiple platforms, which not only safeguards against the failure of a single provider but also reduces latency by positioning information closer to where it's processed or utilized, as demonstrated by Google's in-house transfer tool, Effingo.
The significance of such strategies is additionally highlighted by the high durability rates promoted by services provided by clouds, like the EBS of AWS with up to 99.999% durability and S3 with an impressive 99.999999999%. The key lies not only in preventing information loss but in minimizing its impact through swift recovery, which is measured by metrics like Mean Time to Resolution (MTTR) - the average duration between identifying and resolving an information incident.
Furthermore, with the transition from on-premises data centers to large-scale cloud solutions, the importance of information duplication and backups increases. With hyperscalers predicted to occupy over 60% of datacenter space by 2029, as stated by Synergy Research Group, and with the growing phenomenon of cloud repatriation due to cost and security concerns, the approach for managing information across multiple cloud environments becomes even more vital.
In summary, the implementation of a shared infrastructure can be a potent facilitator for expanding businesses. It allows for better resource optimization, cost reduction, and improved margins, essential for businesses aiming for growth. Therefore, duplicating data across several cloud platforms not only acts as a safeguarding measure but also facilitates the scalability and effectiveness intrinsic to multi-tenant business models.
Performance Monitoring and Optimization
To ensure that tenants consistently receive the performance they expect, it is essential for providers to integrate observability into their systems. This involves the strategic collection and analysis of telemetry data—logs, traces, and workflow details—to swiftly identify and mitigate performance bottlenecks. By doing so, providers can significantly reduce the mean time to resolution (MTTR), ensuring a seamless user experience.
Proactive performance management hinges on the ability to gain immediate insights from the right information. This is crucial given the common IT challenges that organizations face, particularly with rapid technological expansions and data-related complexities. A robust monitoring solution should be sophisticated enough to handle new database performance in-house and keep database DevOps performance risks in check. This is underpinned by the three tenets of high-performance IT: strong business-technology alignment, deep trust in the technology, and adaptability to changing technology capabilities. Firms adhering to these principles typically see faster growth and higher customer satisfaction.
Furthermore, the changing software development landscape, with a growing emphasis on service-oriented structures, requires careful monitoring setups. Understanding of system design and agreements become crucial in effectively managing services in the cloud. As a result, a monitoring solution that is good enough must ensure first insights are neither delayed nor obscured, allowing for immediate and continuous optimization.
Security Considerations in Multi-Tenant Architectures
Ensuring strong security is crucial in multi-tenant cloud systems, where a single infrastructure hosts multiple tenants, each with their own secure data and configurations. The structure, similar to an apartment complex with individual secure units sharing common infrastructure, must prioritize resiliency and availability. As such, building a resilient Virtual Desktop architecture is essential, allowing for business continuity and disaster recovery (BCDR) in the face of both local and region-wide events. Strategies for geo disaster recovery, where services recover in a remote Azure region, are critical components of a comprehensive BCDR plan.
Advanced threats and the evolution of cybersecurity necessitate sophisticated security measures. The Microsoft Digital Defense Report highlights the transformative role of AI in staying ahead of threats, supported by comprehensive security analysis. This is echoed by OODA's expertise in providing advanced intelligence, strategy support, and risk management. As enterprises navigate security in the digital domain, the transition from physical locks to internet-based service protection necessitates careful access controls to safeguard sensitive information. The proverbial question of verifying a person's identity over the internet underlines the complexity of modern security challenges. Ensuring that each tenant's information remains isolated and protected, while maintaining system efficiency, is a delicate balance that demands vigilant management and innovative solutions.
Data Encryption
To protect sensitive information, encryption is crucial both during storage and transmission. This ensures that information remains inaccessible to unauthorized entities. A robust encryption strategy involves the management of encryption keys, which must be secure and distinct for each tenant to prevent any potential overlap or security breaches. The application of End-to-End Encryption (E2EE) is particularly efficient as it encrypts information at the source and can only be decrypted by the intended recipient, thereby eliminating the risk of interception or unauthorized access during transit. Furthermore, real-time applications demand that encryption and decryption processes are not only secure but also swift enough to maintain the application's performance. The application of symmetric key encryption, secured with the public keys of all authorized participants, strikes a balance between security and efficiency. This approach guarantees that only individuals with the corresponding private keys can gain entry to the encrypted information.
The importance of such measures is emphasized by the alarming statistics indicating a 20% rise in breaches and a 70% increase in ransomware attacks in just the first nine months of the current year, compared to the entirety of the previous year. The gravity of these figures underscores the importance of robust encryption practices to protect against such threats. Security experts recommend constant-time programming to mitigate the risks posed by side-channel attacks on cryptographic operations. By ensuring that all operations take a consistent amount of time, this approach eliminates the possibility of attackers exploiting variations in execution time to extract sensitive information.
In light of the escalating concerns regarding information security and privacy, businesses are investing heavily not just in security infrastructure but also in the expertise required to manage these systems effectively. This requires a thorough plan that involves recognizing important information, classifying customer details, and using suitable tools while following different regional regulations like the General Data Protection Regulation in the European Union and the California Consumer Privacy Act in the United States. It is crucial for organizations to establish a clear differentiation between information loss, which refers to the irreversible loss of data, and information leakage, which pertains to the unauthorized dissemination of information beyond the control of the organization.
Access Controls
To maintain the integrity and security of multi-tenant cloud architectures, implementing robust access control measures is paramount. This is especially true as businesses scale and the complexity of authorization requirements grows. Role-based access control (RBAC) has emerged as an effective mechanism to enforce stringent access restrictions, ensuring that tenants have access only to their designated information and resources. This not only fortifies security but also aligns with the need for high-performance systems that can execute rapid authorization checks, as seen in demanding environments like advertising technology platforms.
For instance, in the advertising industry, every party involved from advertisers to ad exchanges handles significant volumes of information and includes numerous transactions. Reddit, when revamping its advertising platform's authorization system, underscored the necessity for low latency in authorization checks to prevent disruptions in service. Such sophisticated systems demand not only robust security but also the flexibility to accommodate diverse account structures and access privileges.
Moreover, as Tod Golding, a Senior Principal Cloud Architect, emphasizes, multi-tenancy is not solely about sharing infrastructure; it's about delivering a cohesive experience to customers. The underlying flexibility is crucial for a business's operational efficiency. By leveraging RBAC, organizations can reap the benefits of multi-tenancy, such as optimized resource utilization, reduced costs, and improved margins, while simultaneously catering to specific authorization challenges.
In the realm of cybersecurity, the dynamic interplay between authentication and authorization is critical for safeguarding user experience. The former verifies user identities, akin to entrance checks at Disneyland, while the latter dictates access levels within the system. This differentiation is crucial in settings involving sensitive information, such as healthcare, where secure protocols guarantee privacy during information processing, as emphasized in recent cybersecurity research.
Indeed, access control remains a cornerstone of security strategies. Findings from ASIS International's study, "The Essentials of Access Control," derived from a survey of over 1,000 security professionals, underscore the importance of deploying effective access control systems. These systems must be not only secure but also capable of adapting to varying requirements, reinforcing the imperative for sophisticated access control mechanisms like RBAC in multi-cloud environments.
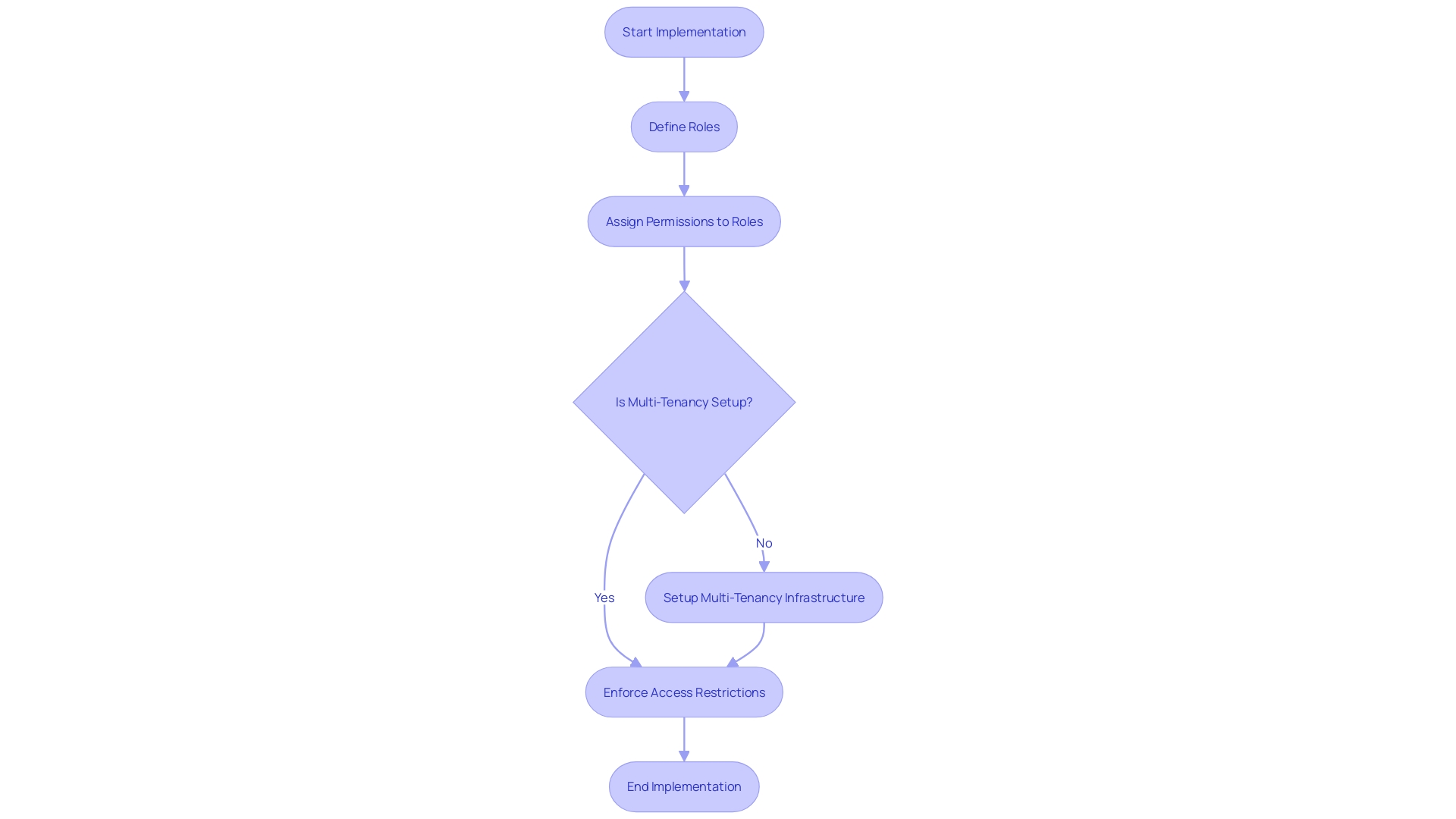
Compliance and Regulatory Requirements
Adherence to industry regulations and standards is crucial in multi-tenant cloud architectures, where a single infrastructure hosts multiple clients, each with their own set of information and configurations. This shared environment must maintain strict compliance to protect privacy rights and secure personal information. Regulations like the General Data Protection Regulation (GDPR) demand rigorous protocols, including information residency, which requires that personal information be processed within the European Economic Area (EEA) or in approved countries unless explicit consent is given. Data minimization and storage limitation are also critical, ensuring data is not collected or stored beyond necessity, and individuals retain the right of access to their personal data. Providers must demonstrate their capacity to uphold these standards, offering transparency and robust security measures to meet legal obligations and instill confidence in their customers. With the evolving landscape of cloud computing, particularly with the increased emphasis on artificial intelligence and cybersecurity, cloud service providers are urged to stay ahead of regulatory changes and proactively incorporate compliance into their design, as per insights from industry news and expert commentary.
Best Practices for Implementing Multi-Tenant Architectures
Navigating the intricacies of multi-tenant architectures is a sophisticated endeavor, requiring an informed strategy to excel. A fundamental aspect of this approach is the partitioning of a single software application to serve multiple user groups, or tenants, each with their own isolated information and configurations, while sharing core computing resources. Such a design is pivotal for Software-as-a-Service (SaaS) applications, promoting efficiency and data security.
To illustrate, consider the case of Dunelm Group plc, the UK's foremost homewares retailer. As their digital platform and superstores expanded, they faced the challenge of scaling their software structure. With a significant online presence generating considerable revenue, the importance of a robust frontend architecture became paramount. Adopting a multi-tenant approach, particularly for their high-traffic website, was a strategic move to accommodate their growth and maintain service quality.
When it comes to database design, a popular strategy, as discussed in the context of Postgres, is to initiate with separate databases for each customer. Such an approach offers maximum isolation and, when necessary, the option for individual encryption. This method is beneficial for organizations that prioritize data security and operational independence for each tenant.
On the other hand, organizations like IFCO, with a lean IT department, sought expertise from partners like Rackspace Technology during their transition to cloud services. Rackspace's customer-focused method and extensive expertise provided IFCO with alternative strategies and insights, illustrating the importance of experienced partners in navigating shared infrastructure deployments.
The importance of multi-tenant management cannot be overstated, considering that it underpins a wide array of business platforms. From commercial SaaS CRMs to internal corporate systems, multi-tenancy facilitates tailored services on shared infrastructure, enhancing both resource utilization and operational efficiency. However, this approach presses traditional data management strategies to their limits, necessitating a robust framework capable of separating and managing data across tenants and scaling in response to customer growth.
The 'State of Multi-cloud 2024' report accentuates these points, revealing that despite the similarities of major public cloud providers, nuances in their offerings can lead to significant challenges. The report, which gathers insights from 300 architects and engineering directors, as well as in-depth interviews with expert engineers, emphasizes the significance of comprehending the details of multi-cloud environments and embracing optimal approaches for application development with multiple users.
By incorporating these best practices, organizations can enhance their management of technology investments, supervise technical projects, and advance their technological vision in a multi-cloud landscape, all while ensuring their multi-tenant structure is efficient, secure, and scalable.
Clear Data Segregation
When designing cloud architectures, one of the paramount concerns is the secure and compliant management of information. As demonstrated by the partnership between Hazy and Nationwide Building Society, the importance of strong segregation mechanisms cannot be emphasized enough. In the case of Retail Bank, instead of using real customer transaction information, which presented considerable security risks and compliance obstacles, a strategic choice was made to utilize synthetic information. This groundbreaking approach not only followed the principles of minimizing information but also acted as a proactive step to avoid information leakage and maintain customer privacy. By using synthetic information generated by SynthGen's sophisticated algorithms, Retail Bank was able to replicate behaviors indicative of financial vulnerability without compromising individual privacy.
This case study is a testament to the effectiveness of logical information separation and isolation in preserving the integrity of the information. Using a dataset that encompasses more than 50,000 customers and 50 million transactions, the utilization of synthetic information reduced the risk of inappropriately accessing sensitive data. Furthermore, the recent legislative developments under the European Union's Data Act underscore the importance of such measures. The act aims to empower both individuals and businesses by ensuring fair information allocation, fostering a competitive information market, and enhancing information-driven innovation. It establishes the right for users to access and reuse information generated from their connected devices, which was traditionally harvested by manufacturers and service providers.
The establishment of isolated compartments, frequently caused by divergent systems or departmental boundaries, can impede the flow of information within an organization. Dismantling these barriers is vital in the era of digital transformation, where information sharing across disciplines is key. The objective is to standardize and combine information, making it accessible to analysts throughout the organization, thus unlocking potential synergies and fostering innovation. Therefore, it is crucial to establish distinct segregation mechanisms in cloud structures, especially in multi-tenant settings, to guarantee the confidentiality and protection of tenant information while facilitating the strategic utilization of information resources.
Regular Vulnerability Assessments
To maintain a robust and secure cloud framework, proactive security practices such as vulnerability assessments and penetration testing are indispensable. A meticulous approach to security testing is essential for identifying potential weaknesses before they are exploited. For instance, when scrutinizing a Linux system, rather than initially focusing on well-known vulnerabilities like setuid binaries or Unix sockets, which have likely been extensively examined, it is advantageous to target areas such as DBus. DBus serves as a client/server-based remote procedure call (RPC) framework, where a server can offer methods that clients can invoke, which could be a fertile ground for uncovering vulnerabilities.
Furthermore, as highlighted by recent advancements in automated penetration testing, the ability to conduct thorough and frequent security evaluations has become increasingly efficient and cost-effective. The advent of algorithm-based security validation solutions, like those offered by Pentera, has revolutionized the field by providing broad coverage and the ability to perform frequent checks, which are essential given the vast number of untested systems worldwide.
The necessity for security to be an integral part of the software design process cannot be overstated. From the earliest stages of requirement gathering, it is imperative to integrate security considerations to prevent system failures, data leaks, and other compromises that could have significant customer impacts. The latest Payment Card Industry Data Security Standard (PCI DSS) version 4.0.1 underscores this point by incorporating changes that reflect the evolving digital landscape and threat scenarios.
Moreover, the secure-by-design philosophy is gaining traction, advocating for manufacturers to take ownership of security outcomes, thus reducing the burden on consumers to manage vulnerabilities post-deployment. This aligns with the three core principles of radical transparency, accountability, and organizational leadership in achieving secure product delivery.
To sum up, security is not a characteristic that can be included as an afterthought but instead a fundamental component that must be integrated into the structure of design and administration, especially in multi-environments. Regular security analysis and embracing the latest advancements in automated testing are critical in safeguarding against the ever-evolving cyber threat landscape.
Continuous Monitoring and Incident Response
In the field of cloud computing, where software as a service (SaaS) models are widespread, the security and operational integrity of shared infrastructures are crucial. A multi-tenant structure is similar to an apartment building shared by multiple tenants, each with their own secure, private space despite the shared infrastructure. In this environment, continuous monitoring and a proactive stance towards incident response are not simply best practices but are essential to the architecture's security and the uninterrupted service provision to tenants.
Robust monitoring systems, such as those incorporating Prometheus, a metrics-based monitoring solution, offer comprehensive insights by aggregating information from various infrastructure components. This approach is particularly applicable to modern application stacks and can be extended with OpenTelemetry exporters to encompass application and business metrics. Real-time monitoring not only detects issues promptly but also helps in maintaining the system's integrity, ensuring that any delays in updates or potential disruptions are identified and addressed swiftly, minimizing the impact on tenants' operations.
This proactive monitoring is complemented by a structured incident response plan, which is critical in managing unplanned interruptions or quality degradations in IT services. As outlined by experts, the components of an efficient incident management process include the identification, categorization, and swift resolution of incidents to restore normal operations with minimal business disruption. By adhering to a well-defined incident response framework, organizations can manage incidents effectively, thereby maintaining the trust and confidence of customers and stakeholders.
According to the Microsoft Digital Defense Report, the digital domain's evolution necessitates innovative and collaborative defense strategies. Leveraging AI and a wealth of security data, organizations can stay ahead of threats and maintain cyber resilience. It's evident that an investment in security research and innovation, coupled with a deep understanding of cybersecurity trends, is indispensable for predicting and mitigating potential attacks.
In conclusion, the management of multi-tenant cloud architectures in a multi-cloud environment demands an integrated approach to monitoring and incident response, ensuring the security and availability of services for all tenants.
Conclusion
In conclusion, multi-tenant architectures offer numerous benefits for businesses aiming to thrive in today's digital landscape. These architectures enable a single instance of software to serve multiple user groups or "tenants," ensuring efficient resource utilization, scalability, and customization. By leveraging shared resources and workload isolation, multi-tenant architectures promote operational efficiency and cost savings.
They also facilitate collaboration and community building among tenants, fostering a sense of shared knowledge and innovation.
However, implementing multi-tenant architectures comes with challenges that must be carefully navigated. These include ensuring data isolation and security, managing resource allocation and performance, and addressing compliance and regulatory requirements. Organizations must also consider factors such as customization constraints, scalability, and the choice between multi-tenant and single-tenant architectures.
To successfully implement multi-tenant architectures, organizations should follow best practices such as clear data segregation, regular vulnerability assessments, continuous monitoring, and incident response. It is also crucial to select the right cloud provider that offers the necessary features and services for multi-tenant environments.
Overall, multi-tenant architectures provide businesses with scalability, efficiency, and customization, enabling them to thrive in the dynamic and competitive digital landscape. By leveraging the benefits of multi-tenancy and implementing best practices, organizations can optimize resource utilization, enhance security, and deliver exceptional services to their tenants.




