Introduction
In the rapidly evolving landscape of cybersecurity, MITRE ATT&CK emerges as an indispensable framework for comprehending and countering the myriad tactics, techniques, and procedures (TTPs) employed by cyber adversaries. Developed by the MITRE Corporation, this detailed knowledge base serves as a cornerstone for organizations striving to enhance their security posture. By offering profound insights into the behaviors and strategies of attackers, MITRE ATT&CK equips security teams with the tools necessary for a threat-informed defense.
The utility of this framework is underscored by real-world applications and evaluations, such as those conducted by MITRE itself. For instance, an incident in April 2024 highlighted the framework's effectiveness when an intrusion into MITRE’s research networks was swiftly addressed using insights derived from ATT&CK. Such experiences demonstrate how understanding adversarial TTPs can significantly bolster an organization’s ability to predict, detect, and mitigate potential threats.
Furthermore, MITRE ATT&CK's structured approach, encompassing tactics, techniques, and procedures, provides a comprehensive understanding of adversarial behavior. This enables organizations to not only anticipate and thwart attacks but also to drive innovation and collaboration within the cybersecurity industry. As security teams integrate this framework into their strategies, they transform their capabilities to defend against sophisticated cyber threats, ultimately fostering a more secure digital environment.
What is MITRE ATT&CK?
'The ATT&CK knowledge base serves as an essential tool in the cybersecurity field, providing a comprehensive structure to understand the tactics, techniques, and procedures (TTPs) employed by cyber adversaries.'. 'Created by the Corporation, this comprehensive knowledge base aids organizations in enhancing their security posture by providing insights into the behaviors and strategies utilized by attackers.'.
The structure acts as a foundation for threat intelligence, enabling security teams to better predict and counter potential cyber threats. In the context of a threat-informed defense, security teams need to scrutinize the TTPs of their adversaries, understand how these tactics can be thwarted or detected, and adjust their defenses accordingly. This approach aligns with the famous quote from Sun Tzu, “If you know the enemy and know yourself, you need not fear the result of a hundred battles.”
MITRE’s own experiences underscore the importance of such frameworks. In April 2024, the organization recognized an intrusion into one of its research and prototyping networks. Rapid response and forensic analysis were crucial in understanding the extent of the compromise and the techniques employed by the adversaries. 'This incident underscored the importance of the ATT&CK structure, as it permitted the organization to model, identify, and confront the hostile actions effectively.'.
The ATT&CK Evaluations further enhance this structure's utility by providing clear, objective insights into the defensive capabilities of participants. The evaluations use a “black box” methodology to emulate real-world scenarios, thus helping organizations identify gaps and areas for improvement. With eleven participants in the latest evaluation round, the results offer a wealth of data on effective defensive measures.
By utilizing ATT&CK, organizations can enhance their cybersecurity strategies, ensuring a strong defense against sophisticated threats. This structure not only empowers security teams with the knowledge to anticipate attacks but also drives innovation and collaboration across the industry, fostering a more secure digital environment.
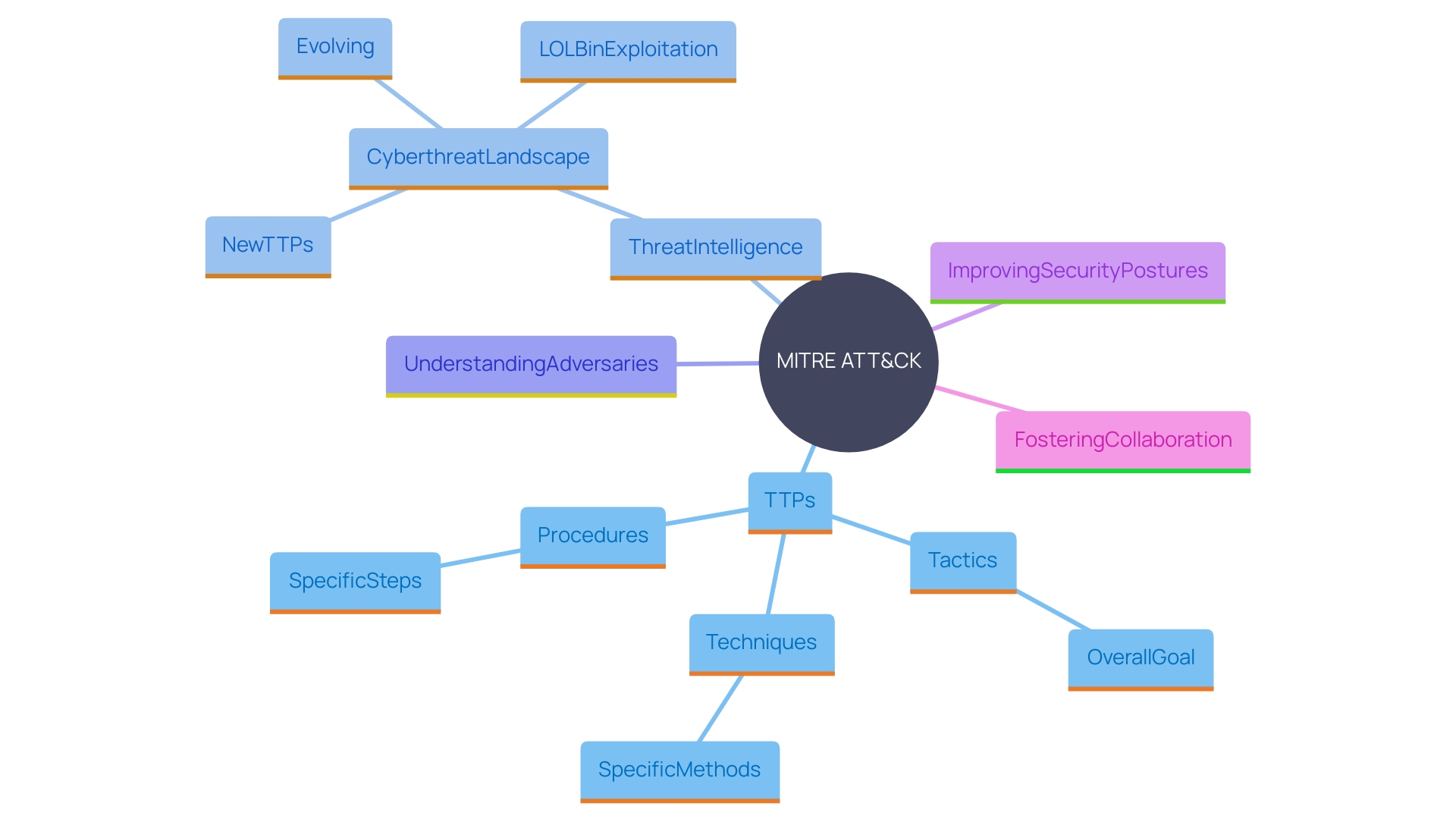
Components of MITRE ATT&CK: Tactics, Techniques, and Procedures (TTPs)
The MITER ATT&CK model is recognized globally for its comprehensive and structured approach to understanding adversarial behavior. It comprises three core components: Tactics, Techniques, and Procedures.
- Tactics denote the overarching goals an attacker aims to achieve during a cyber operation, such as stealing data or disrupting services. As one expert puts it, tactics are the high-level objectives, akin to an action or strategy carefully planned to achieve a specific end.
- Techniques are the methods employed to accomplish these objectives. They describe how attackers exploit vulnerabilities and manipulate systems to get what they want. This collaborative and iterative process involves the community to identify new procedures and enhance data sources and mitigations, reflecting the most effective defensive measures.
- Procedures provide real-world examples of these techniques in action, detailing the specific steps attackers take, including scripts, tools, and attack patterns. This practical insight assists organizations in examining and comprehending the complexities of cyber risks.
This dynamic structure has evolved over the past decade, expanding its scope to include not just Advanced Persistent Threat (APT) groups but also techniques used by cybercriminals. By cataloging and categorizing real-world adversary behaviors, ATT&CK empowers defenders with consistent, risk-informed resources, enabling them to stay ahead of evolving cyber dangers.
Practical Applications of MITRE ATT&CK
Organizations can leverage the MITER ATT&CK model to significantly bolster their cybersecurity measures in several practical ways. By incorporating ATT&CK into risk modeling and assessments, security teams can align recognized dangers to their existing security measures, thereby identifying and addressing vulnerabilities more effectively. The framework also improves the creation of detection and response strategies, allowing teams to quickly recognize and address risks. This is essential as cyber dangers continue to evolve, with advanced persistent risks like operations Dream Job, Wocao, WannaCry, and the SolarWinds Compromise presenting substantial challenges.
Furthermore, the ATT&CK framework facilitates comprehensive training and simulations, empowering personnel to recognize and respond to attack scenarios with greater accuracy. This continuous improvement is akin to the enhanced monitoring systems deployed during forensic investigations, which not only gather critical data but also improve long-term monitoring capabilities.
The framework's adaptability is evident in the way it catalogs and categorizes real-world adversary behaviors, helping organizations stay ahead of evolving threats. For instance, the recent ATT&CK Evaluations showcased the capabilities of Managed Security Service Providers (MSSPs) in detecting and reporting on adversary behaviors, providing valuable insights into defensive capabilities and areas for improvement.
The organization's own experience with cyber intrusions highlights the significance of exchanging information and improving defensive strategies. Just as the organization shared insights from its 2024 network intrusion to inform others, the collaborative and iterative process of updating ATT&CK techniques ensures that organizations are equipped with the most effective defensive measures. This collaborative initiative propels innovation and improves the overall security stance of the sector, making ATT&CK an essential resource in the battle against cyber risks.
Benefits of Using MITRE ATT&CK for Cybersecurity
The adoption of the MITER ATT&CK framework presents organizations with a myriad of benefits to enhance their cybersecurity posture. One of the primary advantages is the significant improvement in situational awareness. By understanding the tactics, techniques, and procedures (TTPs) utilized by malicious actors, security teams can develop proactive defense strategies and strengthen their incident response capabilities. This knowledge empowers organizations to stay ahead of potential threats, adapting their security measures in real-time to counteract evolving adversary behaviors.
Additionally, the ATT&CK model promotes a cooperative atmosphere among cybersecurity experts. By providing a common language and reference point, it facilitates clearer communication and more effective teamwork in addressing security challenges. This unified approach not only improves the overall security posture but also enhances the ability to share insights and best practices across the industry.
In practice, the organization's own experience with cyber incidents highlights the value of the model. For instance, when MITRE experienced an intrusion in April 2024, their immediate response included severing access to the threat actor and conducting a comprehensive forensic investigation. This incident emphasized the significance of comprehending adversary behavior, which ultimately aided in the creation of the ATT&CK system. Such real-world applications showcase the system's effectiveness in transforming industry practices and enhancing cybersecurity resilience.
Furthermore, the system's adaptability and continuous updates ensure that it remains relevant in the ever-changing threat landscape. As opponents develop their strategies, the ATT&CK structure broadens its reach, integrating new methods and data sources to remain proactive. This iterative process of enhancement, supported by community collaboration, ensures that organizations have access to the most effective defensive measures.
Statistics from the ATT&CK Evaluations also affirm the model's impact. For example, evaluations of managed security service providers (MSSPs) have revealed insights into defensive capabilities, driving innovation and identifying areas for improvement. This collaborative effort not only advances the security posture of individual organizations but also contributes to the overall security of the industry.
In conclusion, the MITRE ATT&CK framework is an invaluable tool for organizations seeking to enhance their cybersecurity measures. Its ability to provide situational awareness, foster collaboration, and adapt to evolving threats makes it a cornerstone of modern cybersecurity strategies.
Conclusion
The significance of the MITRE ATT&CK framework in the realm of cybersecurity cannot be overstated. By offering a structured approach to understanding the tactics, techniques, and procedures utilized by cyber adversaries, it empowers organizations to enhance their security posture. This framework serves as a foundational resource for threat intelligence, enabling security teams to anticipate and counter potential threats effectively.
The components of MITRE ATT&CK—tactics, techniques, and procedures—facilitate a comprehensive understanding of adversarial behavior. Through practical applications, organizations can leverage this knowledge to bolster their cybersecurity measures, improve incident response strategies, and conduct thorough training simulations. The real-world experiences shared by MITRE further illustrate the framework's effectiveness in addressing cyber threats and refining defensive measures.
The benefits of adopting MITRE ATT&CK extend beyond immediate tactical improvements. By fostering a collaborative environment among cybersecurity professionals, the framework enhances communication and teamwork, ultimately driving innovation within the industry. As adversaries continue to evolve, the iterative updates to the ATT&CK framework ensure that organizations remain equipped with relevant and effective defensive measures.
In summary, the MITRE ATT&CK framework is an essential tool for organizations committed to strengthening their cybersecurity defenses. Its structured approach, practical applications, and emphasis on collaboration make it a cornerstone of modern cybersecurity strategies, enabling organizations to navigate the complexities of the evolving threat landscape.




