Introduction
In an age where cyber threats are increasingly sophisticated and pervasive, the significance of firewalls in safeguarding network security cannot be overstated. These essential devices act as the frontline defense, meticulously monitoring and controlling the flow of data between trusted internal networks and the unpredictable landscape of the internet.
As organizations face mounting pressures from cyberattacks, particularly in sectors such as education and healthcare, understanding the multifaceted role of firewalls becomes paramount. This article delves into the various types of firewalls, their critical functions, and the best practices for managing firewall security, providing a comprehensive overview of how these tools can effectively mitigate risks and enhance an organization’s cybersecurity posture.
What is a Firewall and Its Role in Cybersecurity?
A protective barrier provides significant firewall benefits by acting as a crucial security tool that carefully oversees and regulates both incoming and outgoing data traffic based on set security protocols. Its fundamental purpose is to establish a protective barrier between a trusted internal network and untrusted external networks, such as the internet. By employing strict traffic filtering systems, one can realize the firewall benefits of effectively preventing unauthorized access, cyberattacks, and possible information breaches.
In the education sector, where it represented 13% of all data breaches during the first half of 2017, the role of firewalls becomes even more critical. Parachute highlights that ransomware attacks on this sector have resulted in $53 billion in downtime costs globally, underscoring the financial impact of security breaches. Firewalls can be deployed in various formats, including hardware or software, and the firewall benefits include preserving sensitive information and ensuring the integrity of network systems.
Furthermore, there was a 32% rise in ransomware incidents targeting energy and utilities companies in early 2020, suggesting an expanding threat environment that requires strong security measures. In the evolving landscape of cybersecurity, the firewall benefits of implementing such solutions are critical for organizations looking to mitigate risks and enhance their overall safety stance.
Key Benefits of Implementing Firewall Solutions
Implementing security solutions presents numerous advantages for organizations, including firewall benefits that significantly enhance their overall security posture while optimizing operational efficiency. Key benefits include:
-
The firewall benefits include serving as a critical barrier against external threats, effectively safeguarding sensitive data and systems from unauthorized access and potential breaches.
In fact, the number of known spear-phishing groups surged from 116 in 2016 to over 250 in 2018, underscoring the necessity of strong security measures. Additionally, a case study on watering hole attacks reveals that 14% of APT groups utilize this tactic during the penetration stage, further illustrating the threats that security systems help mitigate. -
Cost Efficiency: By preventing cyberattacks, security systems can deliver significant firewall benefits, leading to considerable cost reductions and alleviating expenses associated with information recovery and damage management. This is particularly pertinent given that 32% of vulnerabilities in internet-facing applications are classified as high or critical, which could result in significant financial repercussions if exploited.
-
Enhanced productivity is one of the key firewall benefits, as firewalls play a crucial role in managing and filtering internet traffic, thereby reducing employees' exposure to harmful websites and distractions. This focused approach not only minimizes risks but also promotes a more productive work environment.
-
Regulatory Compliance: With many industries facing stringent data protection regulations, the firewall benefits assist organizations in meeting these legal requirements, ensuring compliance while protecting customer data. As Agnė Srėbaliūtė, a Senior Creative Copywriter, notes, 'the IT field offers endless learning opportunities,’ highlighting the importance of staying informed about evolving threats and solutions. Moreover, with the blockchain market in manufacturing growing to $85.64 billion in 2022, the strategic deployment of firewalls benefits businesses aiming to thrive in the evolving cybersecurity landscape of 2024, as they are instrumental in preventing cyber attacks and facilitating a secure operational framework.
How Firewalls Enhance Network Security
Firewalls play a critical role in enhancing network security through a variety of essential functionalities:
-
Traffic Monitoring: Firewalls are designed to continuously monitor network traffic, scrutinizing data packets for signs of suspicious activity and potential threats. This proactive approach is vital, as it allows organizations to identify and respond to anomalies in real-time, showcasing the firewall benefits by significantly reducing the risk of breaches.
-
Access Control: Effective access control is a hallmark of network security technology. By enforcing predefined rules, security systems can permit or deny traffic, thereby blocking unauthorized users from accessing sensitive information. This feature not only enhances protection but also offers a systematic method for managing user permissions within the system.
-
Intrusion Prevention: Advanced security systems are equipped with intrusion prevention capabilities that can detect and thwart intrusion attempts. They notify administrators of possible safety incidents in real-time, enabling prompt measures to reduce risks and safeguard the integrity of the system.
-
VPN Support: Many contemporary security systems provide assistance for Virtual Private Networks (VPNs), enabling secure remote access to internal networks for employees working off-site. This functionality ensures that sensitive data remains protected, even when accessed from external locations, thereby reinforcing the overall safety stance of the organization.
Additionally, research by Liu, A., Gouda, M. emphasizes the importance of complete redundancy detection in firewalls, which further enhances their functionality in preventing unauthorized access. The importance of these features, particularly the firewall benefits, cannot be overstated, as they collectively contribute to a robust security architecture.
As Jai Vijayan notes, "The firewall benefits are essential for any organization aiming to fortify their network against potential breaches." A comprehensive analysis of the effectiveness of access control features in security implementations reveals that organizations reporting successful access control measures experience significantly lower rates of unauthorized access incidents. However, it is crucial to acknowledge the findings from the case study titled 'Limitations of Security Barriers,' which highlights that while such barriers help block malicious traffic, they do not guarantee complete protection against attacks or malware.
Users must stay alert and implement extra protective measures. In fact, the latest advancements in barrier technology continue to enhance traffic monitoring capabilities, solidifying barriers as a cornerstone of system protection strategies.
Exploring Different Types of Firewalls
Firewalls provide essential firewall benefits in network security, with various types tailored to meet specific needs. Understanding these types is essential for effective cybersecurity strategies:
-
Packet Filtering Systems: These foundational systems operate by filtering traffic based on predetermined rules.
They scrutinize packets and make decisions to allow or block them based on IP addresses and port numbers, serving as the first line of defense against unauthorized access. -
Stateful Inspection Systems: Offering a more sophisticated approach, stateful inspection systems maintain a record of active connections and assess traffic based on the context of these connections.
This capability offers a notably greater degree of protection compared to packet filtering, rendering these systems especially efficient in reducing threats. -
Proxy Systems: Functioning as intermediaries between users and the internet, proxy systems not only filter traffic but also cache data and enforce content filtering policies.
By concealing the user's IP address, they enhance anonymity and security, making them invaluable in protecting sensitive information. -
Next-Generation Firewalls (NGFW): These advanced systems combine traditional security functions with sophisticated features such as intrusion prevention systems, application awareness, and deep packet inspection.
They are designed to combat modern threats effectively, showcasing the firewall benefits that reflect the industry's shift towards comprehensive cybersecurity solutions.
Notably, North America currently dominates the global NGFW market, driven by technological advancements and a strong focus on cybersecurity.
As industries evolve, the healthcare sector is expected to grow at the highest CAGR in the NGFW market due to increased reliance on technology, stricter regulations, and the critical need to protect sensitive patient data.
Key players in the NGFW market, such as Barracuda Networks Inc., Check Point Software Technologies, and Cisco Systems, are instrumental in shaping the competitive landscape of network security technology.
Organizations must stay informed about the latest trends and capabilities in security technology to safeguard their networks effectively.
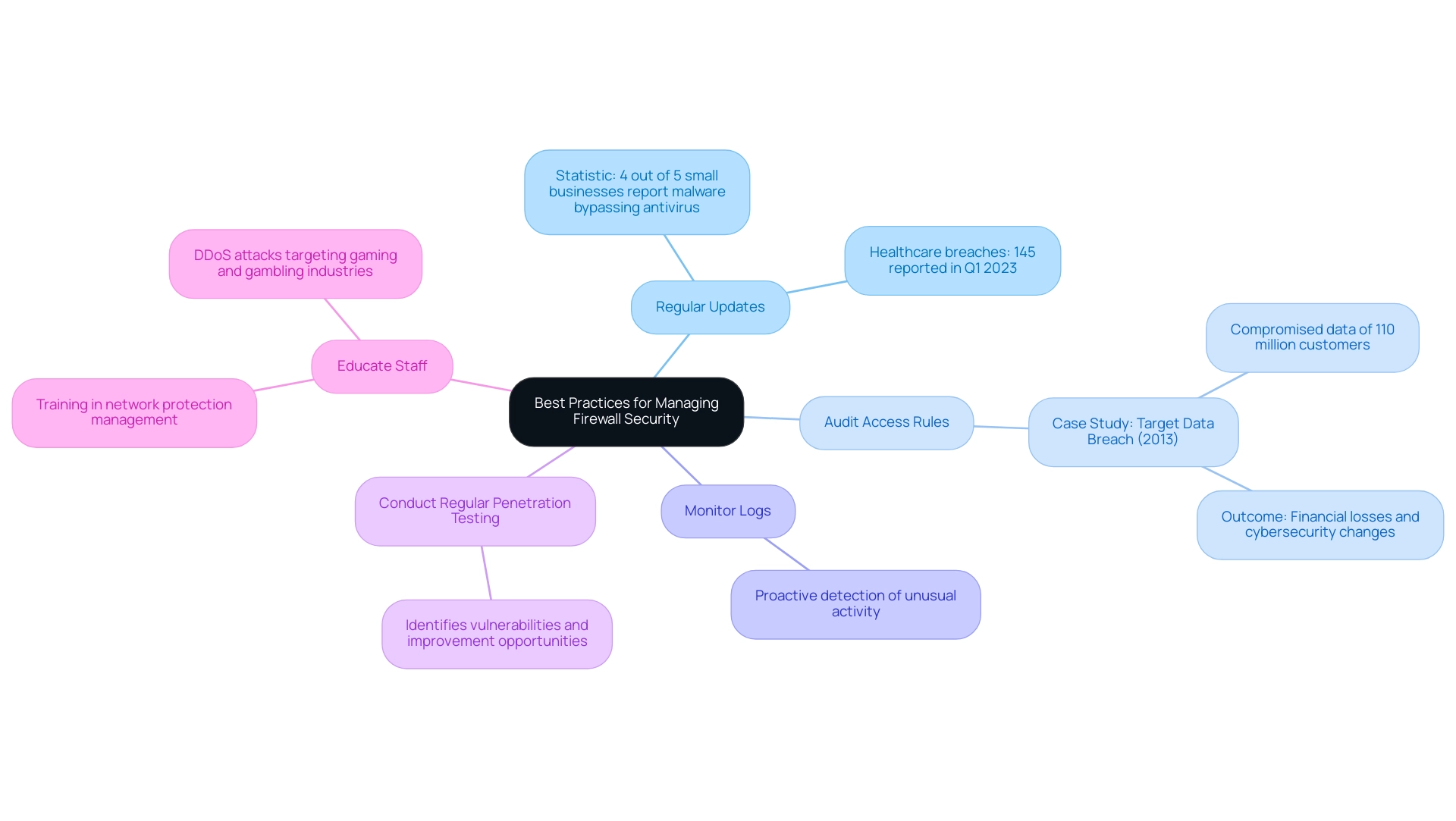
Best Practices for Managing Firewall Security
To ensure strong protection and achieve firewall benefits, organizations must adopt the following best practices:
- Regular Updates: Consistently refreshing system firmware and protection guidelines is essential for defending against emerging threats. Given that 4 out of 5 small businesses report malware has successfully bypassed their antivirus measures, staying current is essential.
Furthermore, regular updates are essential to enhance firewall benefits, particularly in light of the 145 breaches reported by healthcare firms in the first quarter of 2023, as highlighted by the U.S. government’s Office for Civil Rights (OCR).
- Audit Access Rules: Regularly reviewing and auditing access rules enables organizations to ensure alignment with evolving protection policies and business requirements.
An example of this necessity is illustrated by the Target data breach in 2013, where insufficient protective measures led to the compromise of approximately 110 million customers' data.
- Monitor Logs: Continuous observation of security logs is critical for detecting unusual activity.
This proactive method aids in identifying potential incidents before they escalate, showcasing the firewall benefits.
- Conduct Regular Penetration Testing: To uncover vulnerabilities, organizations should engage in penetration testing of their security defenses.
This not only identifies weaknesses but also provides opportunities for improvement.
- Educate Staff: Training IT personnel in effective network protection management and security protocols fosters a culture of security awareness within the organization.
As the landscape of cyber threats evolves, the importance of such training cannot be overstated. Notably, the gaming and gambling industries have been identified as the most targeted sectors by DDoS attacks, which emphasizes the firewall benefits of maintaining vigilant management across all industries.
Conclusion
The importance of firewalls in the realm of cybersecurity cannot be overstated. As the first line of defense against increasingly sophisticated cyber threats, firewalls play a pivotal role in monitoring and controlling network traffic, thereby safeguarding sensitive information and ensuring the integrity of network systems. This article has explored the various types of firewalls, including:
- Packet filtering
- Stateful inspection
- Proxy
- Next-generation firewalls
Each tailored to address specific security needs.
Understanding the benefits of implementing robust firewall solutions highlights the necessity for organizations to prioritize their cybersecurity strategies. From increasing security and enhancing productivity to ensuring regulatory compliance, firewalls are integral to mitigating risks associated with cyberattacks. Additionally, best practices such as:
- Regular updates
- Auditing firewall rules
- Continuous monitoring
are essential for maintaining a strong security posture.
As cyber threats continue to evolve, organizations must remain vigilant and proactive in their approach to firewall management. By leveraging the capabilities of firewalls and adhering to established best practices, businesses can effectively protect themselves from potential breaches and maintain the trust of their clients. In an era where data security is paramount, investing in comprehensive firewall solutions is not just a precaution; it is a necessity for any organization aiming to thrive in the digital landscape.




