Introduction
In the ever-evolving landscape of container orchestration, the Container Network Interface (CNI) stands as a critical component within Kubernetes, facilitating seamless network connectivity for containerized applications. As organizations increasingly adopt Kubernetes for its scalability and efficiency, understanding the intricacies of CNI becomes paramount.
This article delves into the fundamental aspects of CNI, exploring its role in managing pod communication, the various plugins available, and the essential configurations required for optimal network performance. Additionally, it addresses the implementation of network policies to enhance security and provides insights into troubleshooting common issues that may arise.
By equipping IT professionals with this knowledge, organizations can leverage the full potential of Kubernetes while ensuring robust and secure networking capabilities.
Introduction to Container Network Interface (CNI) in Kubernetes
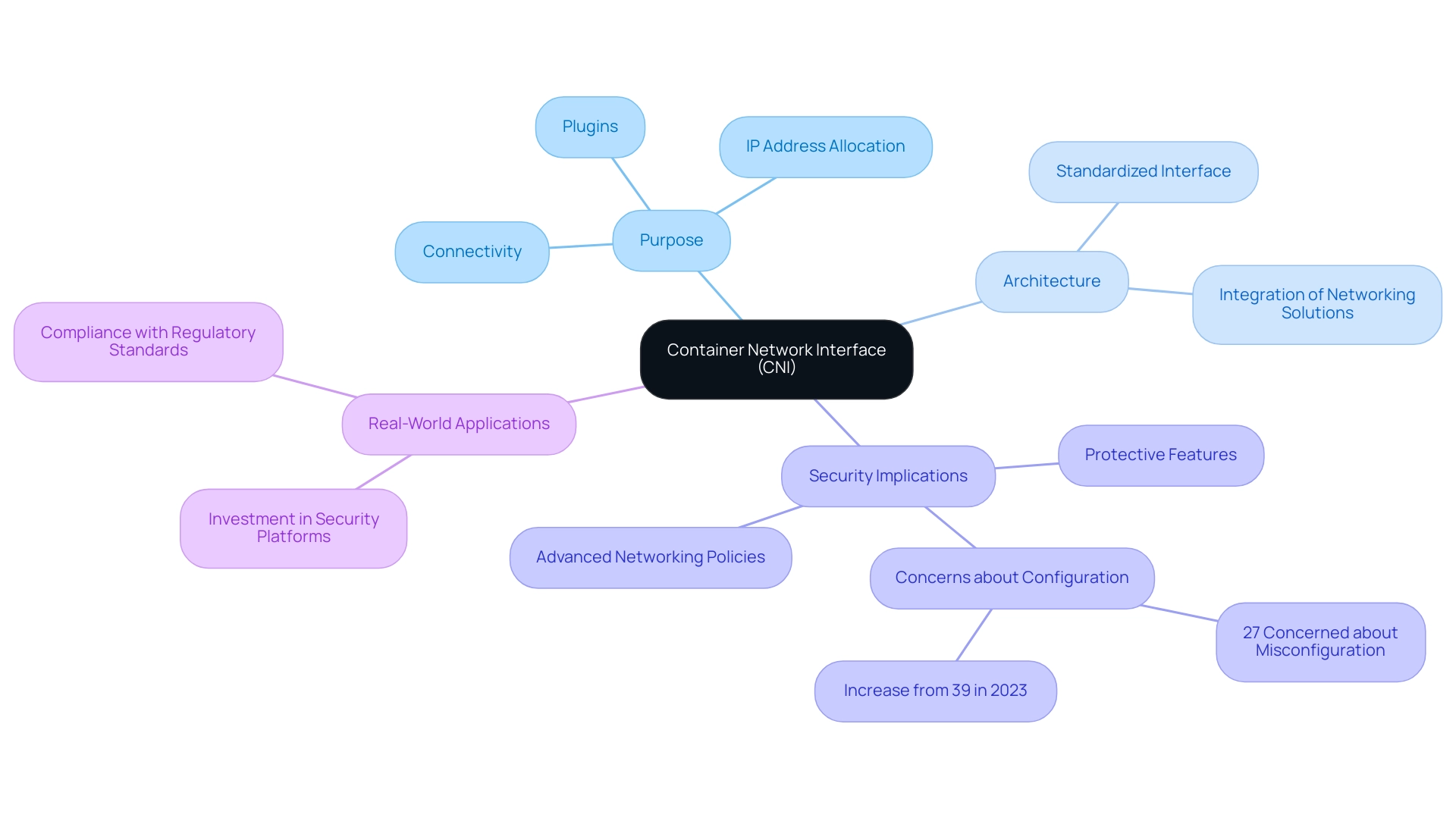
The Container Network Interface (CNI) is a fundamental component of the container orchestration system, facilitating connectivity for containerized applications. By providing a standardized interface for configuring interfaces in Linux containers, CNI ensures seamless communication between pods. In the Kubernetes ecosystem, each pod is allocated a unique IP address, with cni k8s managing the allocation and oversight of these addresses through a variety of plugins.
This comprehension of CNI is essential for effective configuration, as it determines how pods interact both with one another and with external services. The architecture of CNI supports the integration of multiple networking solutions, offering organizations the flexibility to select the most appropriate option for their specific use cases. Significantly, the advantages of adopting CNI go beyond fundamental connectivity; they encompass improved network performance, strengthened protective features, and the ability to enforce advanced networking policies.
As cyber threats continue to evolve, the emphasis on strong protective measures underscores the necessity for advanced tools like cni k8s in Kubernetes environments. In response to these evolving threats, many IT organizations are investing in advanced protection platforms and implementing collaborative, safety-focused processes to safeguard critical systems, workloads, and data. This is especially important considering that 27% of respondents voiced worry about improperly configured components, which can introduce critical vulnerabilities.
A real-world example of this investment in security platforms can be seen in organizations that have adopted cni k8s solutions, demonstrating their commitment to safeguarding sensitive data and complying with regulatory standards.
Configuring CNI: AWS VPC and Calico Plugins in Kubernetes
Configuring CNI in Kubernetes (k8s) in the orchestration platform is essential for optimizing network performance and ensuring secure communication. Among the most widely adopted plugins are AWS VPC CNI and Calico, each offering distinct advantages. Here’s a step-by-step guide for configuring each:
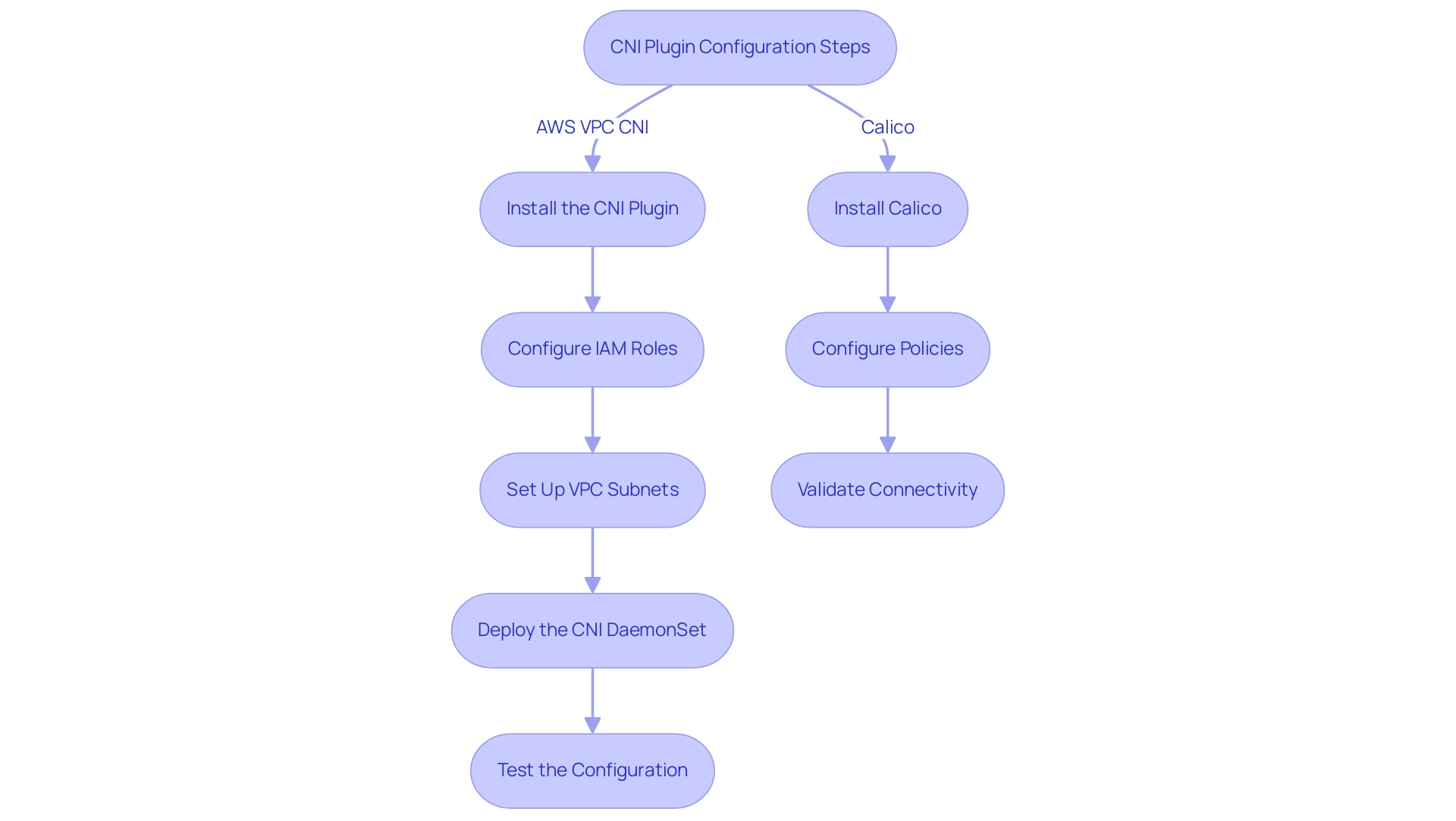
AWS VPC CNI Configuration Steps
- Install the CNI Plugin: Utilize the installation scripts provided by AWS to deploy the CNI plugin in your container orchestration cluster effectively.
- Configure IAM Roles: Assign the necessary IAM roles to ensure that your container orchestration nodes have the appropriate permissions to manage VPC resources effectively.
- Set Up VPC Subnets: Define specific subnets for your Kubernetes cluster that the CNI plugin will use for IP address allocation. This configuration is crucial for enabling optimal pod networking.
- Deploy the CNI DaemonSet: Create a DaemonSet to manage the CNI plugin across all nodes in your cluster, ensuring consistent connectivity behavior.
- Test the Configuration: Conduct thorough testing to verify that pods can communicate seamlessly with each other and with external services, ensuring a robust networking environment.
It’s important to note the recent enhancements in Amazon EKS 1.25, which require specific formatting changes in the AWS-auth ConfigMap for accurate parsing.
As highlighted by industry expert Lony, who has 7,690 points and holds 13 gold badges, 69 silver badges, and 106 bronze badges:
You definitely can, but you shouldn't. The AWS VPC CNI is restricted to the interfaces of an EC2 instance, which means you cannot have more pods than interfaces! This is a huge cost driver and therefore better to look for another CNI from the start.
Understanding these limitations is crucial for efficient resource management. Additionally, a case study on the updates to AWS IAM Authenticator emphasizes the need for specific formatting changes in the AWS-auth ConfigMap, as failure to make these changes can lead to authentication failures in the cluster.
Calico Plugin Configuration Steps
- Install Calico: Follow the comprehensive Calico installation guide to deploy the necessary components in your container orchestration cluster seamlessly.
- Configure Policies: Implement policies to regulate traffic flow between pods, thereby enhancing security and overall performance.
- Validate Connectivity: Ensure connectivity between pods is functioning as intended, confirming the effectiveness of the Calico system.
By adhering to these configuration steps, organizations can harness the strengths of each CNI plugin while optimizing performance and ensuring secure communications within their CNI k8s orchestration environments. Additionally, the performance metrics of Calico in container orchestration have shown promising results, making it a viable choice for many deployments. Furthermore, it's important to consider the role of low capacitance capacitors in circuits, as understanding all components of your infrastructure can lead to better overall performance.
Understanding CNI Plugins: Overview of Popular Options
Kubernetes provides a varied selection of CNI k8s plugins, each aimed at enhancing performance and safety. Here’s a closer look at some of the most widely adopted CNI plugins:
-
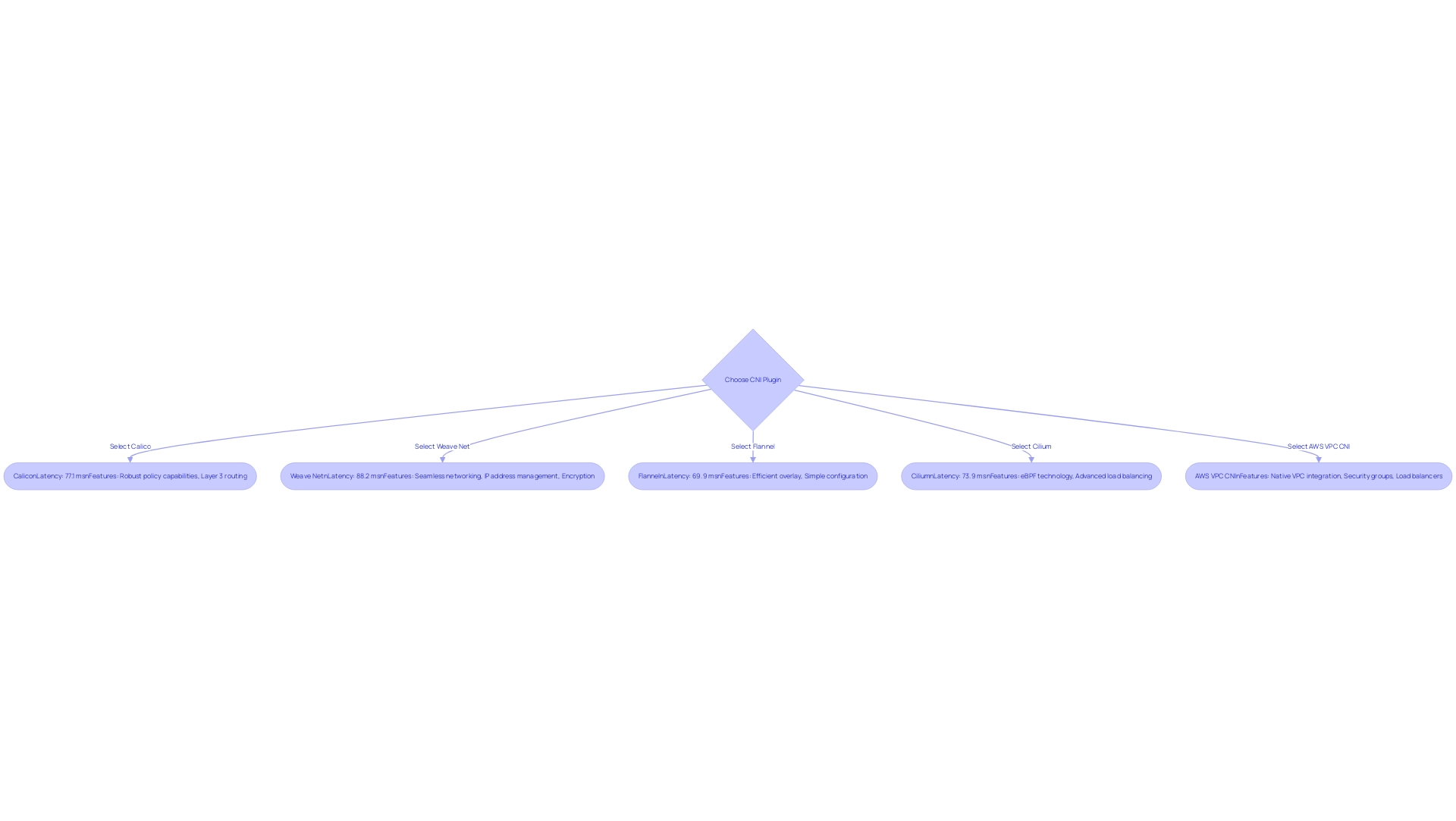
Calico: Renowned for its robust policy capabilities, Calico empowers administrators with fine-grained control over pod-to-pod traffic.
By supporting both Layer 3 routing and comprehensive policies, it is particularly well-suited for environments demanding high security and compliance standards. In terms of performance, Calico exhibited a latency of 77.1 ms in tests with MTU 1500. -
Weave Net: This plugin excels in providing seamless networking for containers across multiple hosts.
Weave Net automates IP address management and simplifies configuration, while also offering encryption to safeguard traffic between pods, making it a solid choice for security-conscious deployments. It demonstrated a latency of 88.2 ms, showcasing its effectiveness in various scenarios. -
Flannel: Frequently preferred for fundamental Kubernetes connectivity configurations, Flannel offers an efficient overlay system that enables pod communication across various hosts.
Its simplicity makes it an ideal choice for teams seeking straightforward network solutions without extensive overhead. Notably, Flannel achieved a latency of 69.9 ms, and in a recent case study on UDP latency performance, it was recognized as the top performer, illustrating its efficiency in real-world applications. -
Cilium: By harnessing the power of eBPF technology, Cilium delivers advanced networking and protection functionalities, including sophisticated load balancing and monitoring capabilities.
This plugin is particularly beneficial for large-scale deployments that require detailed and granular protection policies. Cilium recorded a latency of 73.9 ms in the same tests, reflecting its competitive performance. -
AWS VPC CNI: Specifically designed for Amazon EKS, this plugin connects container orchestration networking directly with AWS VPC infrastructure.
It enables pods to utilize native VPC features like security groups and load balancers, thereby optimizing cloud-native networking setups.
Selecting the suitable CNI k8s plugin is essential for enhancing performance, security, and compliance within container orchestration environments. As the landscape of CNI plugins evolves, understanding their distinct capabilities, supported by quantitative insights and expert opinions, will enable organizations to make informed decisions that align with their operational needs and strategic goals. As noted by J.R., while Andrea regularly demonstrated superior performance in TCP bandwidth for larger packet sizes, Flannel excelled in TCP latency, albeit still trailing behind physical network configurations.
Implementing Network Policies with CNI
Network policies in container orchestration empower administrators to meticulously regulate traffic flow between pods based on predefined rules, thereby minimizing the attack surface and isolating applications. Implementing these policies using cni k8s involves several critical steps:
-
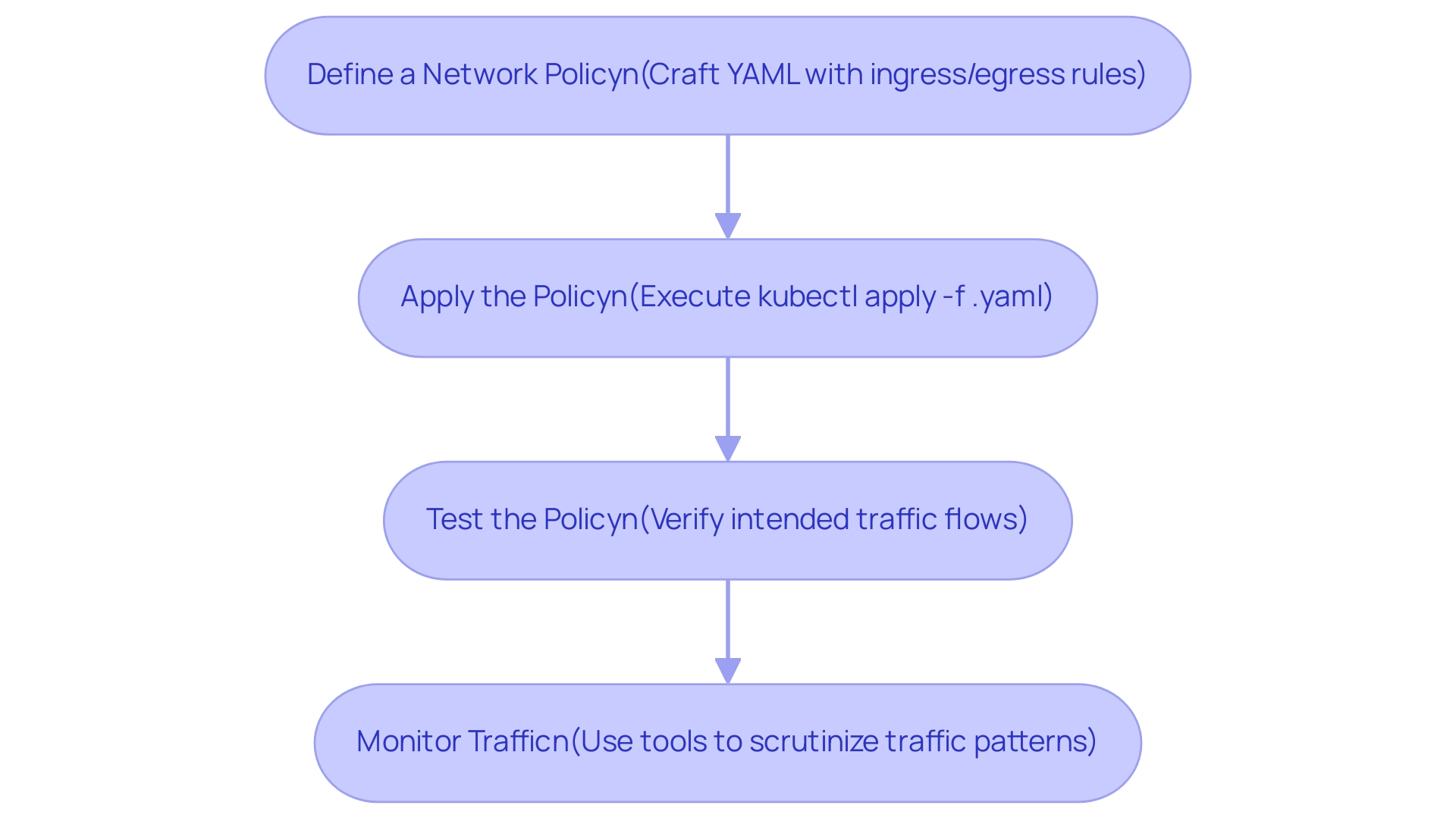
Define a Network Policy: Begin by crafting a YAML file that outlines your desired ingress and egress rules.
For instance, you can create a policy that limits traffic to specific namespaces, improving your protective stance. -
Apply the Policy: Execute the command
kubectl apply -f <policy-file>.yamlto enforce the defined connectivity policy across your container orchestration cluster seamlessly. -
Test the Policy: Ensure the effectiveness of your policy by verifying that only the intended traffic flows between pods. Attempt to connect from various sources to confirm that the policy is functioning as expected.
-
Monitor Traffic: Utilize advanced monitoring tools to scrutinize traffic patterns, ensuring that your system policy is operational and aligns with your protection requirements.
Implementing system policies is not merely a best practice; it is imperative for bolstering safety within your container orchestration environment. For debugging and validation purposes, as noted by Abhinav Mishra in the blog post dated August 5, 2022, 'admins or developers would want to be able to go back in time and check how their configuration and flows look, but enabling this kind of functionality today is burdensome.' Therefore, addressing the challenges of operationalizing policies—such as running them at scale, controlling access, and enforcing a Zero-Trust model—is critical for effective security and policy management in cni k8s projects across diverse container orchestration environments.
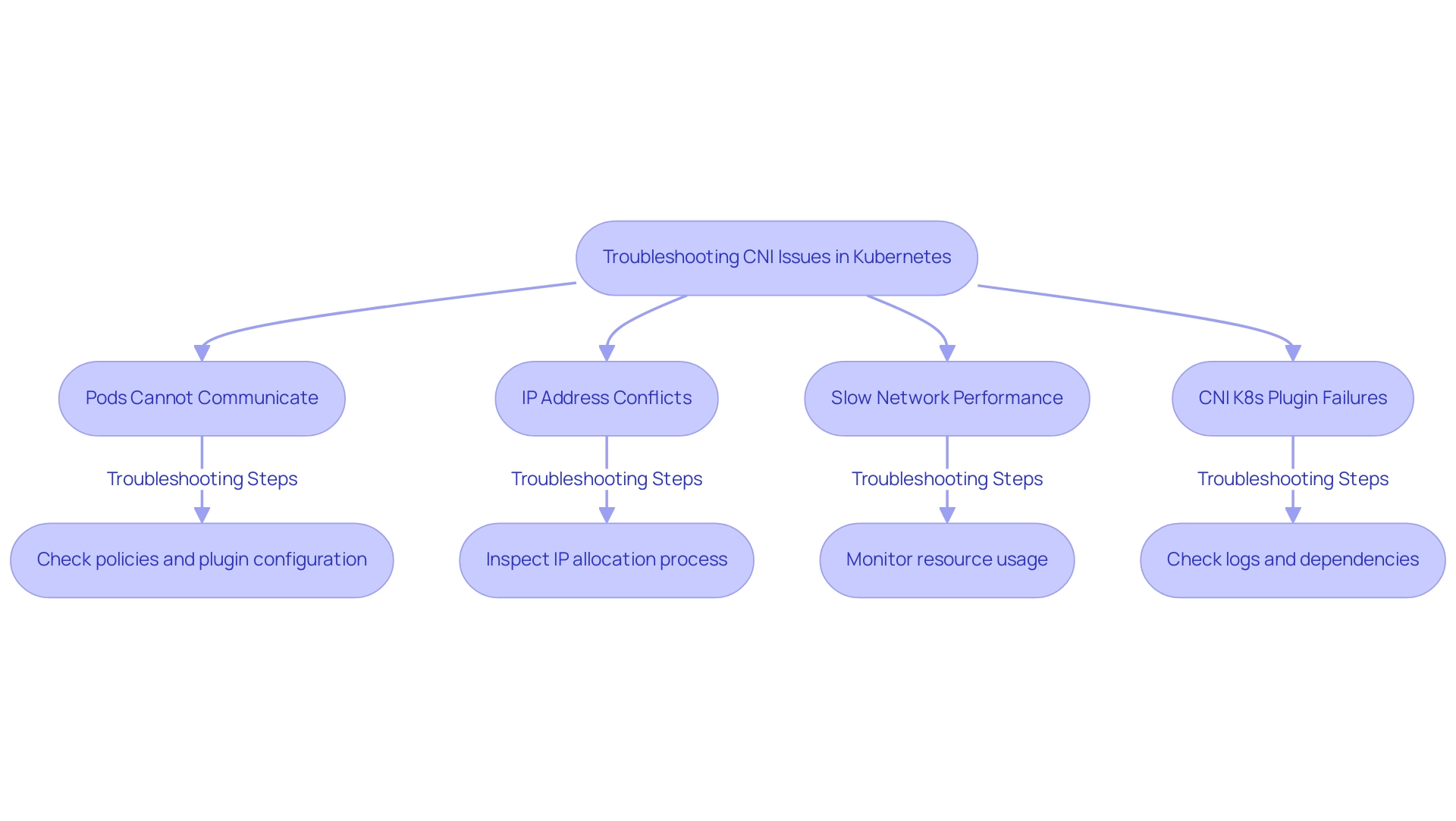
Troubleshooting Common CNI Issues
When engaging with cni k8s in Kubernetes, various challenges may arise. As Betty Williams aptly stated, discussing a problem is futile unless we also address potential solutions. Below are some prevalent issues along with actionable troubleshooting steps:
- Pods Cannot Communicate: In situations where pod communication fails, it is crucial to examine the policies to ensure they are not overly restrictive. Additionally, verify the correct installation and configuration of the cni k8s plugin.
- IP Address Conflicts: To address IP address conflicts, inspect the allocation process to ensure no two pods share the same address. Reviewing the cni k8s configuration is essential to confirm that the designated IP ranges do not overlap.
- Slow Network Performance: If network performance is suboptimal, monitor resource usage—both CPU and memory—of the cni k8s plugin. Consider optimizing the configuration or potentially transitioning to a more efficient plugin as needed.
- CNI K8s Plugin Failures: In cases where the CNI K8s plugin fails to initialize, check the logs for any startup errors. It is also vital to confirm that all required dependencies are installed and that the Kubernetes version is compatible with the chosen cni k8s plugin.
By systematically following these troubleshooting steps, Kubernetes administrators can effectively identify and resolve common issues related to cni k8s, ensuring a stable and efficient networking environment. As Herm Albright noted, while a positive attitude may not solve all problems, it can provide the motivation needed to tackle challenges head-on, reinforcing the necessity of proactive troubleshooting.
Conclusion
The Container Network Interface (CNI) plays a pivotal role in the Kubernetes ecosystem, enabling seamless communication between containerized applications through a variety of networking solutions. By understanding the intricacies of CNI, IT professionals can optimize network configurations, enhance security, and ensure robust performance for their Kubernetes deployments.
The article outlined essential aspects of configuring CNI plugins, such as AWS VPC and Calico, each offering unique advantages tailored to specific use cases. A careful selection of the appropriate CNI plugin can significantly improve network performance and security, thereby aligning with organizational goals. Furthermore, implementing network policies is crucial for managing traffic flow and fortifying defenses against potential threats, highlighting the importance of proactive security measures in today’s complex cyber landscape.
Additionally, troubleshooting common CNI issues is vital for maintaining a stable networking environment. By addressing challenges such as communication failures, IP address conflicts, and performance bottlenecks, Kubernetes administrators can ensure their systems remain efficient and reliable.
In conclusion, mastering the nuances of CNI not only empowers organizations to leverage the full potential of Kubernetes but also establishes a foundation for secure and efficient networking. As the demand for container orchestration continues to grow, the importance of understanding and implementing CNI effectively cannot be overstated. Organizations that prioritize these aspects will be well-positioned to navigate the complexities of modern application deployment while safeguarding their critical data and infrastructure.




