Introduction
Dubai's rapid digital transformation has firmly established it as a global business hub, attracting substantial investments and fostering groundbreaking innovation. However, this accelerated growth has also heightened the risk of cyber threats, endangering sensitive data, financial assets, and operational integrity. With over 2,200 cyberattacks occurring daily, the threat landscape is becoming increasingly sophisticated, necessitating robust cybersecurity measures.
Major financial institutions such as the Commercial Bank of Dubai and the Arab National Bank in Saudi Arabia have recognized the critical need for stringent security protocols to protect their assets and maintain customer trust amidst their digital transformations. Recent reports further highlight the Middle East's vulnerability to cyber threats, including activities by hacktivists and initial access brokers exploiting corporate network entry points.
In this dynamic environment, fortified cybersecurity frameworks are essential for regulatory compliance and preserving customer trust. Experts at the World Economic Forum's Annual Meeting in Davos emphasized the intensifying race between cyber defenders and attackers, underscoring the need for proactive and sophisticated cybersecurity strategies to ensure sustained business success.
Why Cybersecurity is Crucial in Dubai
Dubai's rapid digital transformation has firmly established it as a hub for businesses, driving substantial investments and fostering innovation. This growth, however, has brought an elevated risk of cyber dangers, posing significant hazards to sensitive data, financial assets, and overall operational integrity. Cybercrime, encompassing data damage, financial theft, embezzlement, fraud, business disruption, and reputational harm, is on the rise. With over 2,200 cyberattacks occurring daily, equating to more than 800,000 attacks annually, the threat landscape is becoming increasingly sophisticated.
The significance of robust cybersecurity measures cannot be overstated. For instance, Commercial Bank of Dubai, a prominent bank in the UAE, has adopted technological advancements to improve its operations and customer service. Yet, this evolution also necessitates stringent security protocols to safeguard critical assets and maintain customer trust. Likewise, Arab National Bank in Saudi Arabia experienced a substantial digital transformation, acknowledging the necessity for improved online security to facilitate its growth and safeguard its stakeholders.
Recent reports highlight the Middle East's vulnerability to cyber threats, including the activities of hacktivists and initial access brokers who exploit entry points into corporate networks. The urgency for enhanced digital security frameworks is underscored by high-profile breaches, such as the theft of tens of thousands of emails from US State Department personnel.
In this dynamic environment, digital security is pivotal in ensuring regulatory compliance and preserving customer trust. As experts at the World Economic Forum's Annual Meeting in Davos emphasized, the race between cyber defenders and attackers is intensifying. 'With fewer than one in ten global executives believing generative AI will favor defenders over attackers in the next two years, staying ahead in digital security is crucial for sustained business success.'.
Top 10 Cybersecurity Companies in Dubai
Multiple firms have arisen as frontrunners in offering security services customized to the distinct challenges encountered by enterprises in Dubai. For instance, CrowdStrike, recognized by Gartner for its innovative approach, offers comprehensive threat intelligence and defense solutions. Their acknowledgment by Gartner highlights their dedication to excellence in digital security.
Another notable example is SecurityScorecard, a global leader in online security ratings. Headquartered in New York, SecurityScorecard continuously rates over 12 million companies worldwide, ensuring robust security postures against evolving threats. 'Their extensive global reach, operating in 64 countries, highlights their capability to address diverse digital security needs effectively.'.
The Arab National Bank (anb) in Saudi Arabia illustrates the effective execution of security protocols as part of its wider technological transformation approach. By adopting advanced security solutions, and has significantly enhanced its operations, ensuring the safety and trust of its clients. As Ala Asali, the Chief Security Officer of and, stated, 'We’re proud of our history working with retirees, but we can do more. Now we serve everyone, everywhere, any time.'
These companies are at the forefront of addressing the security needs of businesses in Dubai, ensuring a secure digital environment that fosters growth and innovation.
Gulf IT - Comprehensive Cybersecurity Solutions
Gulf IT provides comprehensive cybersecurity services, including threat intelligence, incident response, and risk assessment, to safeguard organizations against evolving cyber threats. By leveraging cutting-edge technology and deep industry expertise, Gulf IT empowers businesses to enhance their security posture and mitigate risks effectively.
For instance, Arab National Bank (anb) embarked on a digital transformation journey, significantly improving its operations and expanding its growth. This shift allowed and to stay ahead of emerging threats and protect its critical assets. Gulf It's dedication to integrity and innovation, recognized among Ethisphere’s World’s Most Ethical Companies for 16 consecutive years, ensures that clients receive not only top-tier security solutions but also ethical and trustworthy service.
According to recent statistics, the average organization faces over 300 new services added to their attack surface monthly, contributing to 32% of new high or critical exposures. This dynamic landscape necessitates robust digital security measures. Gulf It's proactive approach helps organizations navigate these complexities, providing them with the tools and knowledge needed to defend against sophisticated cyber attacks.
In a swiftly evolving technological realm, collaboration is key. Gulf IT collaborates with top technology suppliers and utilizes worldwide knowledge to offer customized security solutions. By merging technology with human creativity, Gulf IT assists clients in constructing robust protection frameworks, guaranteeing their business continuity and success in a progressively technological environment.
Help AG - Full-Scale Cybersecurity Services
'Help AG distinguishes itself as a leading cybersecurity provider, offering extensive solutions customized for contemporary online risks.'. Our services include strong network protection, advanced cloud safeguarding, and meticulous compliance management. In a world where cybercrime is becoming increasingly professionalized, with digital identities being a prime target, our integrated approach ensures that organizations can stay ahead of potential threats. 'We utilize our vast knowledge in cybersecurity to safeguard endpoints and oversee network defenses, assisting organizations in responding to incidents almost instantly, as demonstrated by our use of standardized platforms like Palo Alto Networks.'. Our commitment to security efficacy is further demonstrated by our 100% detection rate and zero false positives in SE Labs' recent Endpoint Security test. By merging advanced technology with unmatched industry expertise, Help AG is committed to safeguarding the online futures of our clients.
DTS Solution - Cybersecurity Strategy and Operations
DTS Solution excels in creating tailored security strategies and implementing robust operational measures to bolster business defenses. Our approach is rooted in understanding the unique challenges and goals of each client, enabling us to develop solutions that are both effective and adaptive.
A prime example of our expertise can be seen in our collaboration with Arab National Bank (anb), one of the oldest banks in Saudi Arabia. Historically serving pensioners and retirees, and sought to modernize and expand its operations. By collaborating with DTS Solution, and initiated a bold digital transformation strategy, strengthening its security stance to support its evolving business model.
Our dedicated team utilizes advanced technology and industry best practices to provide comprehensive digital security services. This encompasses formulating and evaluating incident response strategies, performing simulated activities like tabletop drills, and establishing comprehensive communication plans to guarantee coordinated reactions to cyber risks.
As highlighted in a recent IBM report, the average cost of a data breach continues to rise, with lost business costs reaching $1.47 million in 2024, up from $1.3 million in 2023. This underscores the importance of robust cybersecurity measures to protect against reputational damage and loss of sensitive data.
We also stay ahead of emerging threats, such as ransomware, which has evolved to include sophisticated techniques like supply chain attacks and insider threats. Our latest Ransomware: True Cost to Business report highlights that 41% of bad actors gain access via the supply chain, emphasizing the need for comprehensive protection strategies.
By merging our profound knowledge with a dedication to generating 360° value, DTS Solution assists companies in managing the intricacies of digital security, protecting their assets, and preserving their competitive advantage in a progressively digital environment.
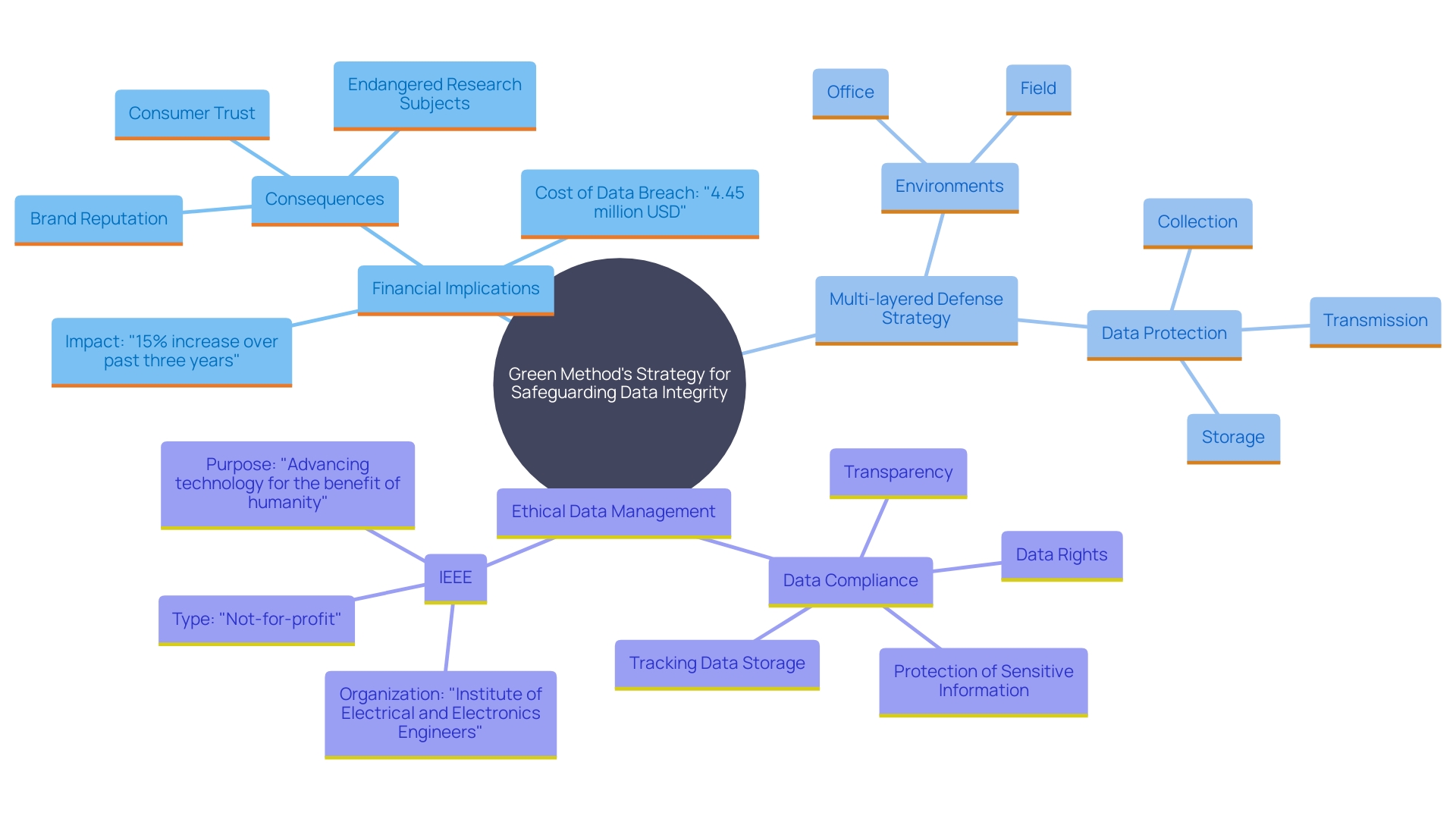
Green Method - Data Protection and Application Security
Green Method emphasizes a comprehensive approach to safeguarding data integrity and fortifying applications against vulnerabilities. Given that data has become the lifeblood of modern organizations, the stakes for securing it are higher than ever. According to recent research by IBM, the global average cost of a data breach has surged to $4.45 million, underscoring the severe financial and reputational damages that can occur. This heightened risk necessitates robust data management practices across all stages, from collection to storage and transmission.
To mitigate these threats, Green Method employs rigorous security protocols tailored to the unique risks associated with various devices and databases. Whether data resides on mobile devices, laptops, or cloud servers, each environment is fortified against potential breaches. This multi-layered defense strategy not only safeguards sensitive information but also ensures adherence to evolving regulations related to online security, such as the European Union's NIS2 Directive.
Moreover, Green Method's approach includes ethical data management practices, such as obtaining informed consent and ensuring the anonymity and confidentiality of respondents. By adhering to these high ethical standards, organizations can maintain trust and integrity while effectively managing their data. This holistic strategy ensures that data remains secure and that its integrity is preserved, allowing organizations to leverage their data assets confidently and effectively.
Osi Infotech - Advanced Network and Cloud Security
Osi Infotech provides cutting-edge solutions crafted to protect network infrastructures and cloud environments, allowing organizations to shift effortlessly to online platforms. Utilizing advanced security measures, Osi Infotech tackles the growing challenges presented by more sophisticated digital threats, ensuring strong protection for online initiatives. This approach aligns with industry trends, such as the shift towards Secure Access Service Edge (SASE) architectures, which integrate security into cloud-delivered services to provide exceptional user experiences and secure access from any device, anywhere.
Intertec Systems - Cybersecurity Resilience and Governance
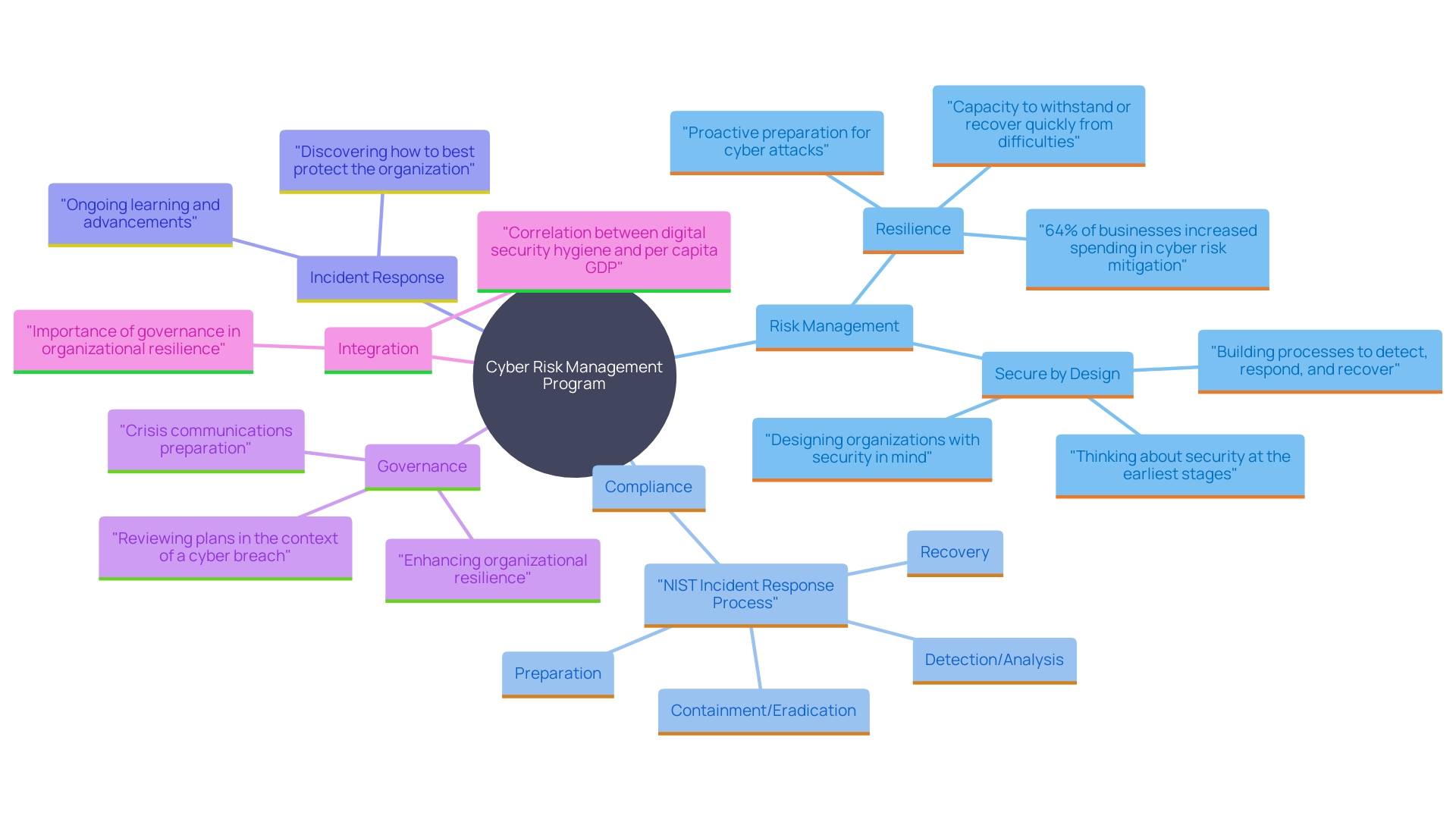
Intertec Systems places a strong emphasis on resilience by implementing robust governance frameworks that meticulously address risk management, compliance, and incident response. A cornerstone of this effort is the Cyber Risk Management Program (CRMP) framework, which is detailed extensively in our publication, "Building a Cyber Risk Management Program." This framework provides a structured and comprehensive approach to digital security, aligning with regulatory requirements from bodies such as the SEC. The CRMP framework is designed to help organizations not only meet compliance mandates but also strategically balance risk and reward in their digital transformation journeys.
The CRMP framework is built on four core components that facilitate a defendable approach to risk management in the digital realm, ensuring alignment with a variety of authoritative sources. Additionally, Intertec integrates the NIST incident response process, which is a continuous cycle of preparation, detection and analysis, containment and eradication, and recovery. This cyclical nature ensures ongoing learning and improvements to protect the organization effectively.
Integrating these frameworks enables Intertec Systems to offer a robust security stance, customized to fulfill both regulatory requirements and strategic business goals. Recent insights into global cyber hygiene underscore the importance of such frameworks, revealing a strong correlation between a region’s digital security hygiene and its per capita GDP. This further highlights the critical need for robust governance in mitigating cyber risks and enhancing organizational resilience.
Microminder - Cyber Risk Management and Penetration Testing
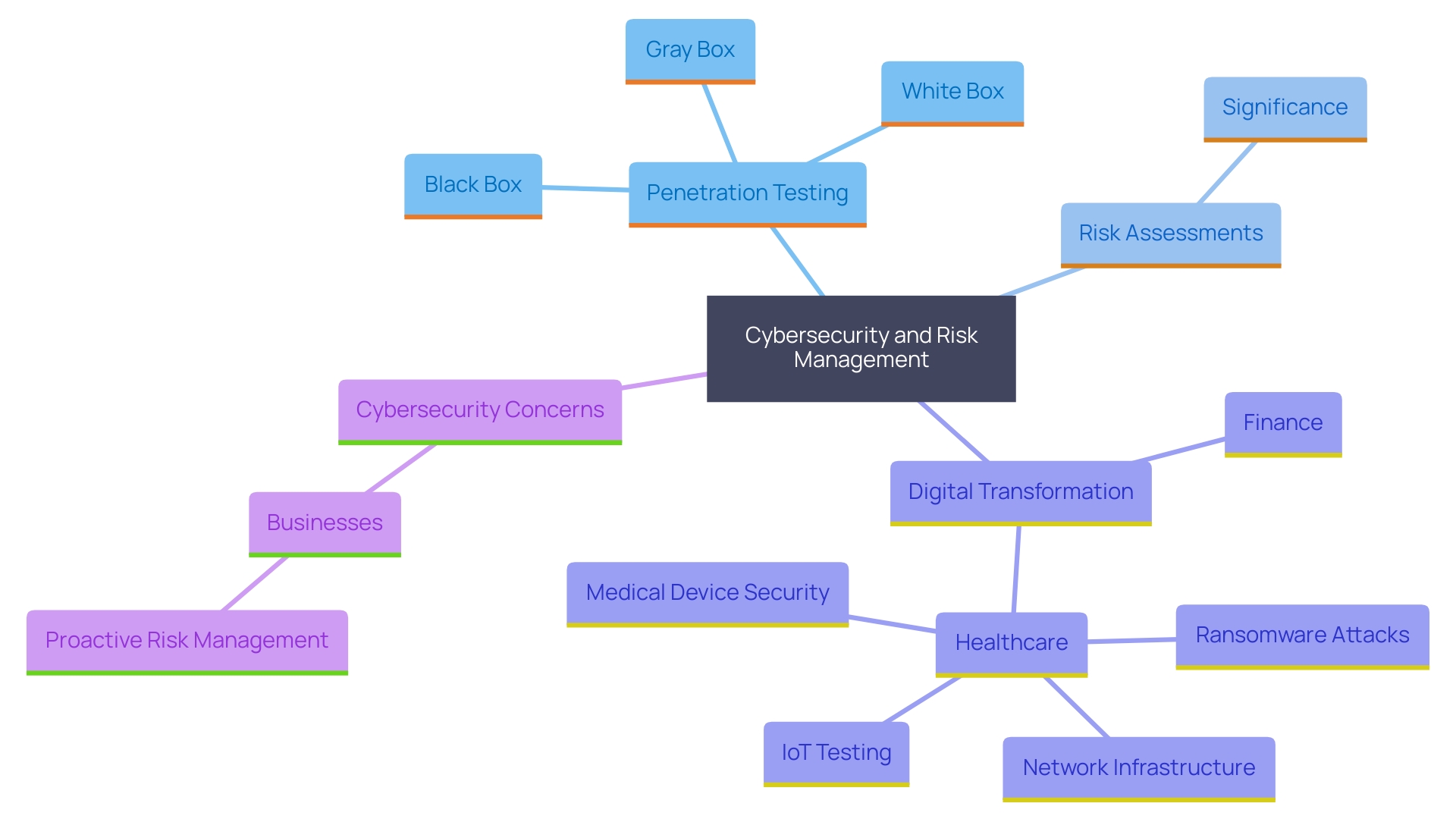
Microminder excels in identifying vulnerabilities through comprehensive penetration testing and risk assessments, ensuring proactive measures are in place. A clear project plan is essential, outlining the scope of testing, specific systems, timeline, and objectives. Selecting the right testing methodology, such as Black Box, White Box, or Gray Box, is crucial. For instance, social engineering or API Fuzzing techniques can be deployed based on organizational needs. The financial sector is increasingly embracing digital transformation, as seen with Arab National Bank's ambitious strategy to enhance operations and growth. Similarly, Guthrie Clinic's holistic IT solutions underscore the importance of comprehensive healthcare. At the same time, the increase in online risks among UK small and medium-sized enterprises underscores the necessity for strong protective measures. Nearly 38% of businesses are more concerned about cyber security threats than a year ago, with 30% facing malware and data loss incidents. This underscores the importance of effective risk management plans. According to Gartner, a strong security management plan involves identifying risks, assessing their impact, and planning responses, enabling businesses to confidently leverage emerging solutions. This proactive strategy is crucial in today's online environment, where upholding a robust security stance is vital.
IBT - Tailored Cybersecurity Solutions
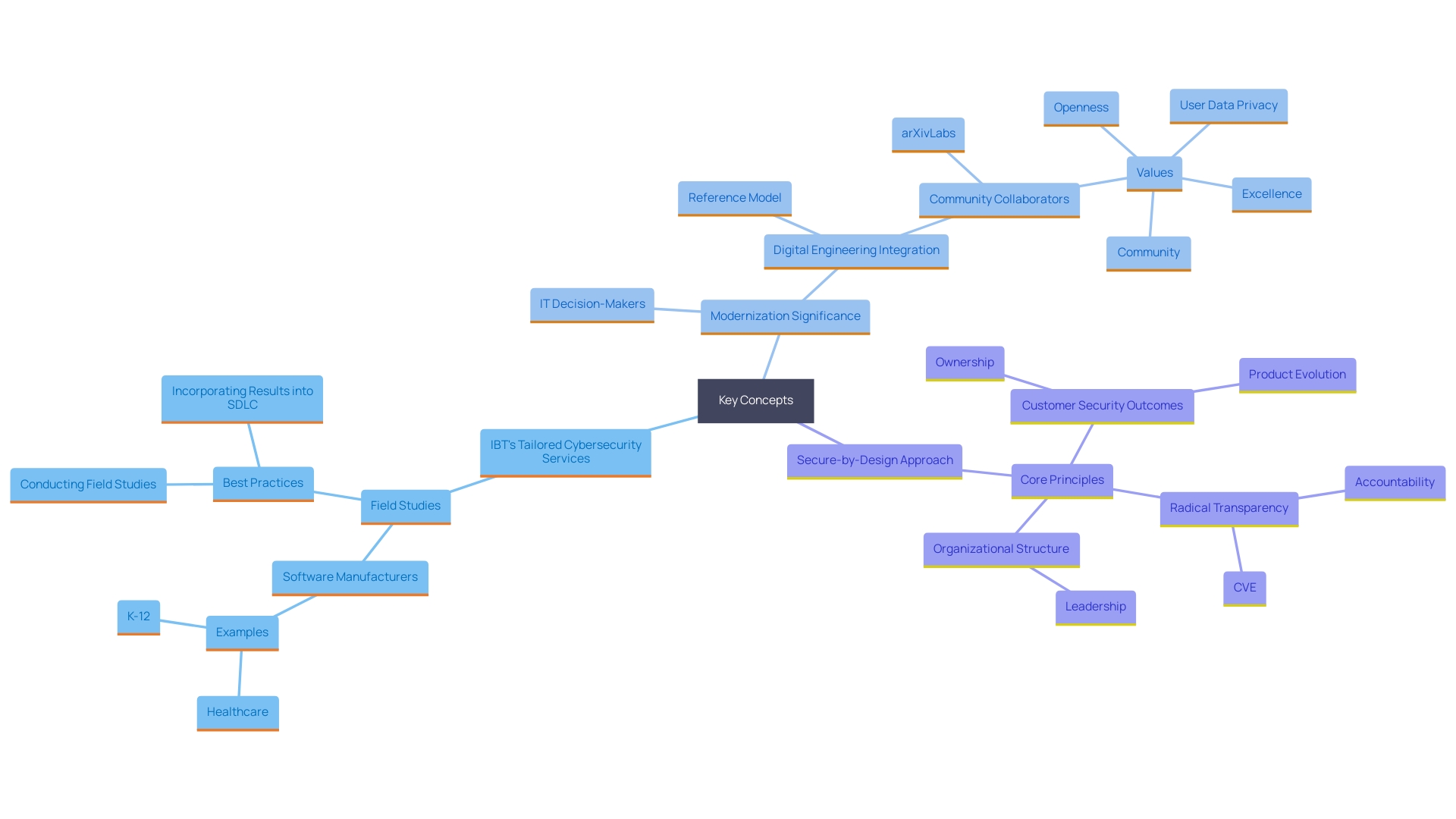
IBT's cybersecurity services are meticulously crafted to address the unique challenges faced by each organization, ensuring a customized strategy that safeguards critical assets. By leveraging advanced technologies and a deep understanding of various industries, IBT provides comprehensive solutions that integrate seamlessly with existing infrastructures. For instance, Arab National Bank, one of Saudi Arabia's oldest financial institutions, successfully modernized its operations and expanded its growth potential through a tailored digital transformation strategy. This demonstrates the importance of bespoke solutions in achieving business objectives.
Moreover, a recent survey highlights that 69% of IT and security decision-makers believe modernization is crucial for meeting business goals, despite challenges such as security concerns and talent shortages. This underscores the need for customized cybersecurity services that not only protect but also enable organizations to thrive in a rapidly evolving technological landscape.
IBT's method is consistent with the principles of secure-by-design, where products are constructed to withstand cyber risks from the outset. This proactive stance is crucial, as emphasized by industry experts who advocate for safety to be a core business priority. By adopting these practices, IBT ensures that its clients are not just compliant with regulations but are also resilient against emerging challenges, thus driving long-term success and innovation.
IT SEC - Managed and Offensive Security Solutions
'IT SEC provides extensive managed protection services and advanced offensive tactics aimed at safeguarding businesses against today's sophisticated cyber threats.'. In a time when cyberattacks are becoming more intricate and common, IT Sec's solutions offer a strong defense by incorporating comprehensive protective measures that remove vulnerabilities and improve the overall protective stance.
For example, IT SEC's method corresponds with industry leaders who are moving away from fragmented protective tools towards unified, comprehensive strategies. This method not only reduces costs but also improves efficiency and effectiveness in managing cyber risks. As observed in the instance of ING, one of Europe’s largest banks, a comprehensive protection strategy allowed the firm to safeguard its extensive digital assets, ensuring the safety of its 38 million customers across 40 nations.
Furthermore, IT SEC's offensive measures, such as penetration testing and red teaming, proactively identify vulnerabilities before they can be exploited by attackers. This proactive stance is crucial in staying ahead of regulatory demands and the constantly changing risk landscape. 'With more than 250 new regulatory updates each day, and an expanding workforce gap in digital protection, IT Sec's solutions assist in overcoming these challenges by offering smooth integration and management of protective tools, thereby strengthening an organization's defenses against both existing and upcoming dangers.'.
By leveraging AI and extensive security data, IT SEC is uniquely positioned to predict and mitigate potential cyber risks, ensuring that businesses remain resilient in the face of cyber adversities. This proactive and comprehensive approach to cybersecurity is essential for any organization aiming to protect its digital assets and maintain trust with its stakeholders.
Digiport Technologies - Cybersecurity Intelligence and Threat Detection
Digiport Technologies utilizes advanced detection and intelligence techniques to remain ahead of potential cyber incidents. By utilizing advanced analytics, the company can foresee and reduce risks before they arise. 'This proactive approach is essential in today's complex cybersecurity landscape, where understanding and adapting to new and ongoing risks is paramount.'. For instance, IP addresses utilized by malware for command and control operations are meticulously analyzed to update defenses and identify actor infrastructure. This approach is not solely focused on immediate risk management but also on developing a thorough comprehension of the risk landscape.
The company places significant emphasis on the integrity and compliance of its data analytics processes. Each dataset used is meticulously curated to ensure compliance with legal standards, thereby safeguarding user privacy and adhering to regulatory requirements. This dedication to adherence is highlighted by the difficulties encountered in educating and utilizing machine learning models, which are essential for effective danger detection.
Furthermore, Digiport Technologies' collaborative approach, involving cross-functional teams of security analysts, developers, and stakeholders, enhances the robustness of their protective measures. This teamwork is vital for continuously adapting strategies and tools in response to evolving threats, ensuring that the organization remains at the forefront of digital security innovation.
Choosing the Right Cybersecurity Company in Dubai
When choosing a digital security partner in Dubai, it's essential to assess several key factors. First, assess the partner's industry experience. 'An exemplar is Arab National Bank (anb), which successfully embarked on a digital transformation by leveraging experienced security services to secure its operations.'.
Next, scrutinize the service offerings. According to Gartner's research, different partners provide varying levels of protection services, and it is important that these offerings match your specific requirements, whether it's compliance, threat detection, or incident response.
Customer testimonials provide invaluable insights into the effectiveness of a security partner. For instance, testimonials from clients in the education sector highlight the importance of robust network protection to safeguard sensitive data and ensure compliance with regulatory requirements.
Lastly, the ability to provide tailored solutions is paramount. A cybersecurity partner should align their solutions with your business objectives, adapting to the evolving threat landscape and technological advancements. As noted by a CISO from a global financial services company, engaging and interactive security exercises can educate senior leadership about the impact of security breaches, emphasizing the need for adaptable and forward-thinking security solutions.
Conclusion
The rapid digital transformation in Dubai has positioned the city as a prominent global business hub, but this progress comes with significant cybersecurity challenges. With over 2,200 cyberattacks occurring daily, organizations are increasingly vulnerable to sophisticated threats that can compromise sensitive data and disrupt operations. Major financial institutions have recognized the urgent need for robust security protocols to protect their assets and maintain customer trust, underscoring the critical importance of a comprehensive cybersecurity framework.
Leading cybersecurity companies in Dubai, such as CrowdStrike, Help AG, and Gulf IT, are at the forefront of addressing these challenges. They provide tailored solutions that enhance security postures and mitigate risks, ensuring businesses can thrive in an increasingly digital environment. By leveraging advanced technologies and industry best practices, these organizations help clients navigate complex threat landscapes while adhering to regulatory compliance.
Ultimately, the necessity for effective cybersecurity measures cannot be overstated. As the race between cyber defenders and attackers intensifies, organizations must prioritize their cybersecurity strategies to safeguard their operations and maintain stakeholder confidence. Engaging with experienced cybersecurity partners who offer customized solutions will be essential for businesses aiming to secure their digital futures in this dynamic landscape.




