Introduction
As organizations increasingly turn to cloud solutions to enhance efficiency and scalability, the importance of cloud migration security cannot be overstated. With the public cloud market projected to reach $825 billion by 2025, the need to protect sensitive data and applications during this transition has become paramount.
This article delves into the critical concepts surrounding cloud migration security, addressing the top challenges organizations face, such as:
- Data breaches
- Insufficient access controls
- Compliance risks
Furthermore, it highlights best practices for mitigating these risks and emphasizes the role of change management and emerging technologies in strengthening security measures.
By prioritizing security throughout the migration process, organizations can not only safeguard their data but also foster trust and reliability in their cloud environments.
Understanding Cloud Migration Security: Key Concepts and Importance
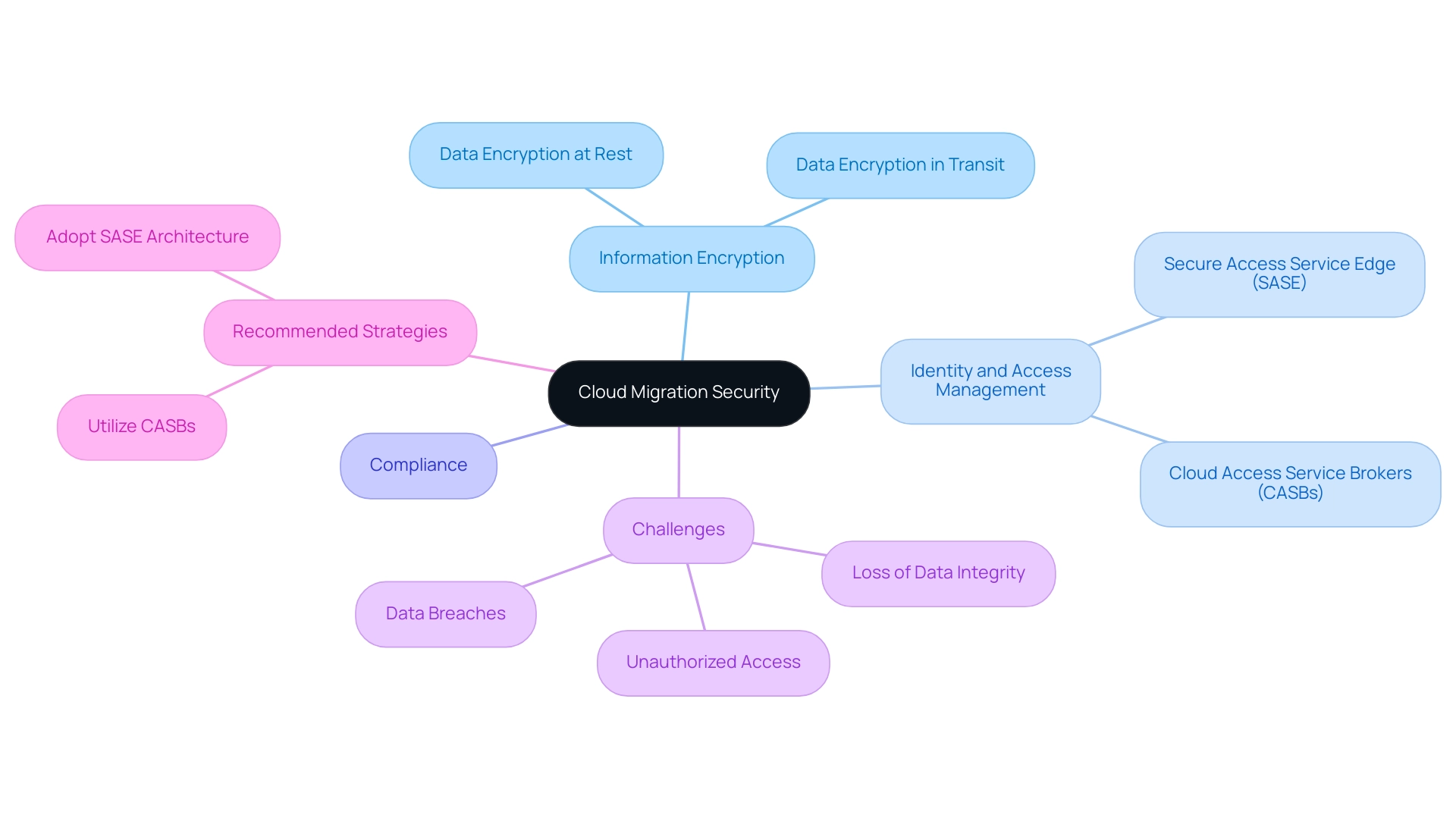
Migration protection includes a thorough framework of measures and practices vital for safeguarding sensitive information and applications, particularly in addressing cloud migration security challenges during the shift to online environments. As the public computing market surpassed $561 billion in 2023 and is projected to reach $825 billion by 2025, organizations are increasingly adopting computing solutions to enhance operational efficiency and scalability. This significant growth trajectory underscores the necessity for robust security measures to address cloud migration security challenges, especially as 56% of IT decision-makers do not fully understand their cloud provider's plans for AI integration, highlighting the urgent need for improved transparency in cloud services.
Key concepts include:
- Information encryption
- Identity and access management
- Compliance with regulatory standards
As emphasized by SentinelOne, organizations should aim to adopt a Secure Access Service Edge (SASE) architecture and utilize Cloud Access Service Brokers (CASBs) to manage excessive permissions effectively. The adoption of SASE architecture is particularly crucial as organizations face cloud migration security challenges related to managing permissions and ensuring secure access to sensitive information.
By prioritizing security in digital transitions, organizations can significantly reduce risks related to:
- Data breaches
- Loss of data integrity
- Unauthorized access
This proactive strategy guarantees a smoother transition that aligns with broader business objectives, ultimately fostering trust and reliability within digital environments.
Identifying the Top Security Challenges in Cloud Migration
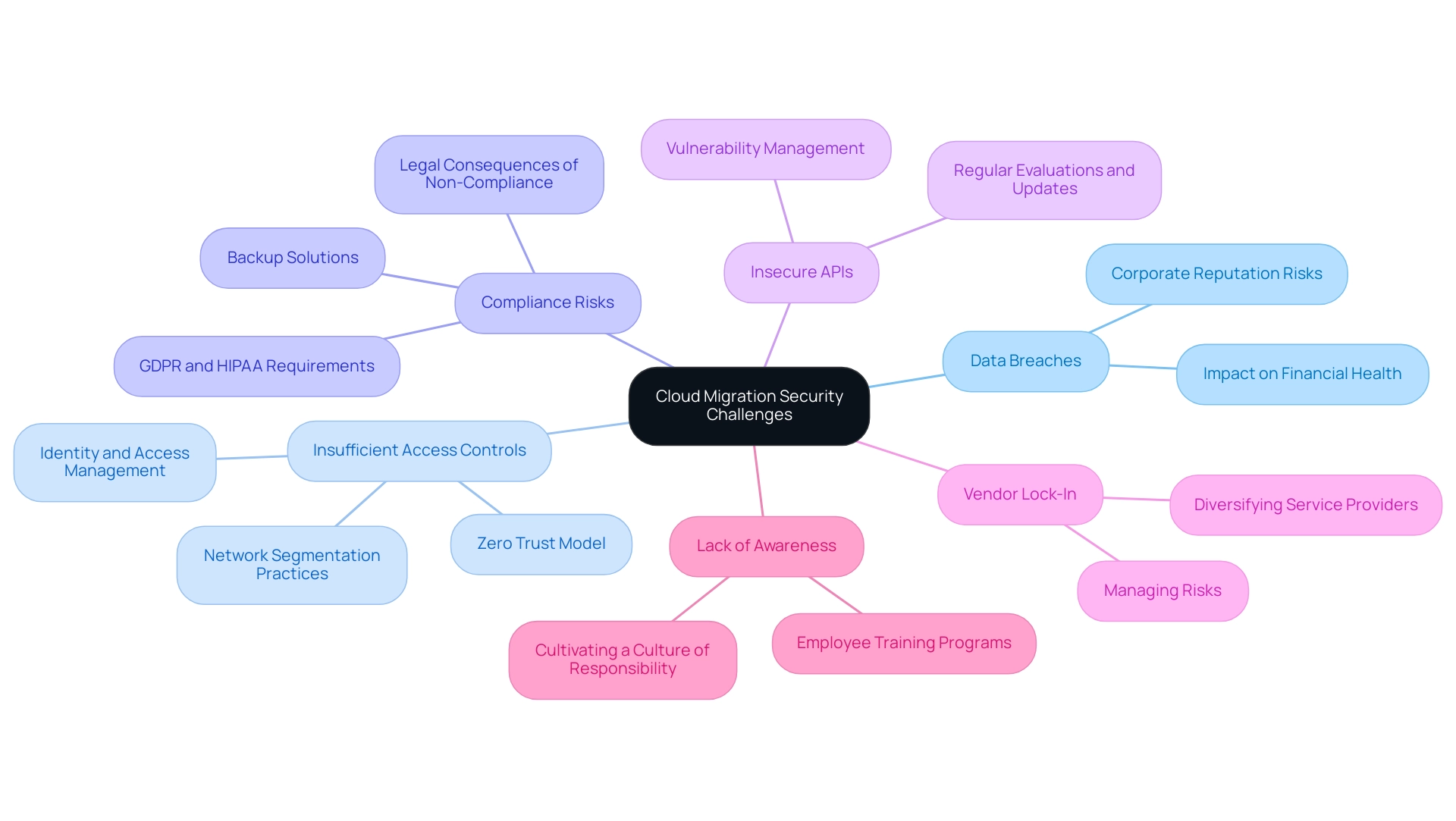
- Data breaches represent one of the most critical cloud migration security challenges during the migration to online services, with severe implications for both financial health and corporate reputation. When protective protocols are inadequately implemented, sensitive information is vulnerable to exposure. A staggering statistic reveals that 89% of businesses impacted by misconfigurations in the network were startups, according to SentinelOne. This emphasizes the urgency for strong protective measures. Investing in zero-trust security models not only mitigates this risk but can also lead to savings exceeding USD 1 million per incident, thus promoting a more secure network environment.
Insufficient Access Controls: The lack of effective identity and access management can result in unauthorized entry to online resources, posing a significant risk to information integrity. Organizations are urged to establish stringent access control measures to ensure that only authorized personnel can access critical data. The zero trust model, emphasizing strict access controls and continuous verification, is pivotal in enhancing online security. Moreover, implementing network segmentation practices and defining software-based micro-segmentation are essential components of this model, further protecting environments.
Compliance Risks: Navigating the regulatory environment is crucial during data transfer, as organizations must adhere to various requirements, such as GDPR and HIPAA. Non-compliance can result in substantial fines and legal consequences. Companies must be proactive in understanding these regulations and integrating compliance strategies into their cloud transition plans to avoid pitfalls that could jeopardize their operations. The risk of information loss during migration highlights the cloud migration security challenges that arise from potential misconfigurations or human errors. Implementing robust backup solutions is paramount to safeguard against such risks. Organizations should ensure that comprehensive information recovery strategies are in place to prevent irreversible damage during the transition process.
Insecure APIs: Application Programming Interfaces (APIs) are integral to cloud services but can also serve as vectors for attacks if not secured properly. It is crucial to ensure that APIs are fortified against vulnerabilities to maintain information integrity and protect against potential breaches. Regular evaluations and updates play a vital role in securing these interfaces.
Vendor Lock-In: Significant dependence on a sole service provider can lead to vulnerabilities, as organizations may lose control over their information and encounter difficulties in managing risks. To mitigate this, diversifying service providers is advisable, allowing organizations greater flexibility and control over their environments.
Lack of Awareness: Employees are a crucial line of defense in maintaining protection during cloud migration. A deficiency in training and awareness can lead to human errors that significantly compromise safety, which is one of the cloud migration security challenges. Organizations must invest in comprehensive training programs to cultivate a culture of awareness and responsibility among their workforce.
Case Study - The Zero Trust Approach: This case study emphasizes the importance of adopting a zero trust architecture. By implementing strict access controls and continuous verification, organizations can significantly enhance their security posture. The outcome of investing in such architecture can lead to savings exceeding USD 1 million per incident, promoting a more secure network infrastructure.
Best Practices for Mitigating Cloud Migration Security Challenges
-
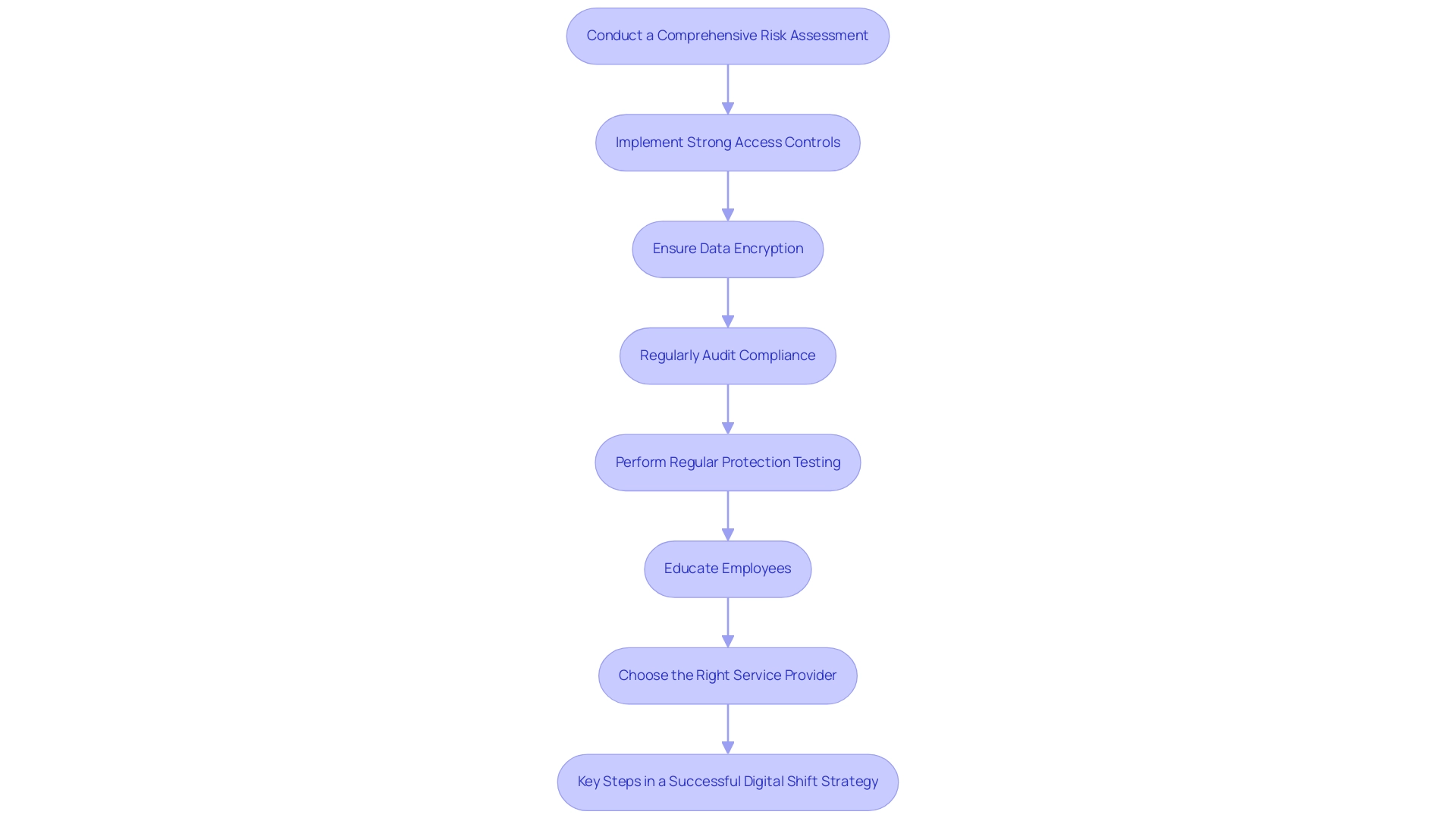
Conduct a Comprehensive Risk Assessment: Before starting a transition to a virtual environment, it is crucial for organizations to perform a thorough risk evaluation. This process helps identify potential vulnerabilities within the existing infrastructure and allows for the development of tailored strategies to mitigate these risks. Highlighting the importance of this step, NVIT states,
By following these best practices, organizations can successfully navigate the complexities of online adoption and achieve their business objectives in the ever-evolving digital landscape.
As data migration continues to drive digital transformation in 2024 and beyond, this foundational step becomes even more critical. -
Implement Strong Access Controls: Employ role-based access control (RBAC) to ensure users have the minimum necessary access for their roles. This practice significantly reduces the risk of unauthorized access, thus enhancing security within the online environment.
-
Ensure Data Encryption: Protect sensitive data through robust encryption protocols, both in transit and at rest. This crucial step is essential to address cloud migration security challenges by protecting information from unauthorized access and potential breaches, which is increasingly important as organizations move to online solutions.
-
Regularly Audit Compliance: Establish a routine for auditing compliance with regulatory requirements. Regular compliance audits ensure that all necessary measures are in place to avoid legal complications, thereby reinforcing the integrity of operations.
-
Perform Regular Protection Testing: Conduct consistent assessments, including penetration testing and vulnerability scanning, to proactively identify and address weaknesses within the cloud infrastructure. Staying ahead of potential threats is vital in a dynamic digital landscape.
-
Educate Employees: Ongoing training for employees is essential to increasing awareness about potential threats and instilling best practices for maintaining safety throughout the migration process. A well-informed workforce is a critical line of defense against breaches, especially when navigating cloud migration security challenges.
-
Choose the Right Service Provider: When selecting a service provider, it is crucial to evaluate their security offerings, compliance certifications, and overall reputation. A thorough assessment of these factors will contribute significantly to a secure and successful transition process.
-
Case Study: Key Steps in a Successful Digital Shift Strategy: A manageable digital transition strategy involves several key steps: defining the strategy, planning, adopting governance, managing the process, and innovating. Following these steps assists organizations in successfully moving to the digital environment and enhancing their operations.
The Role of Change Management in Cloud Migration Security
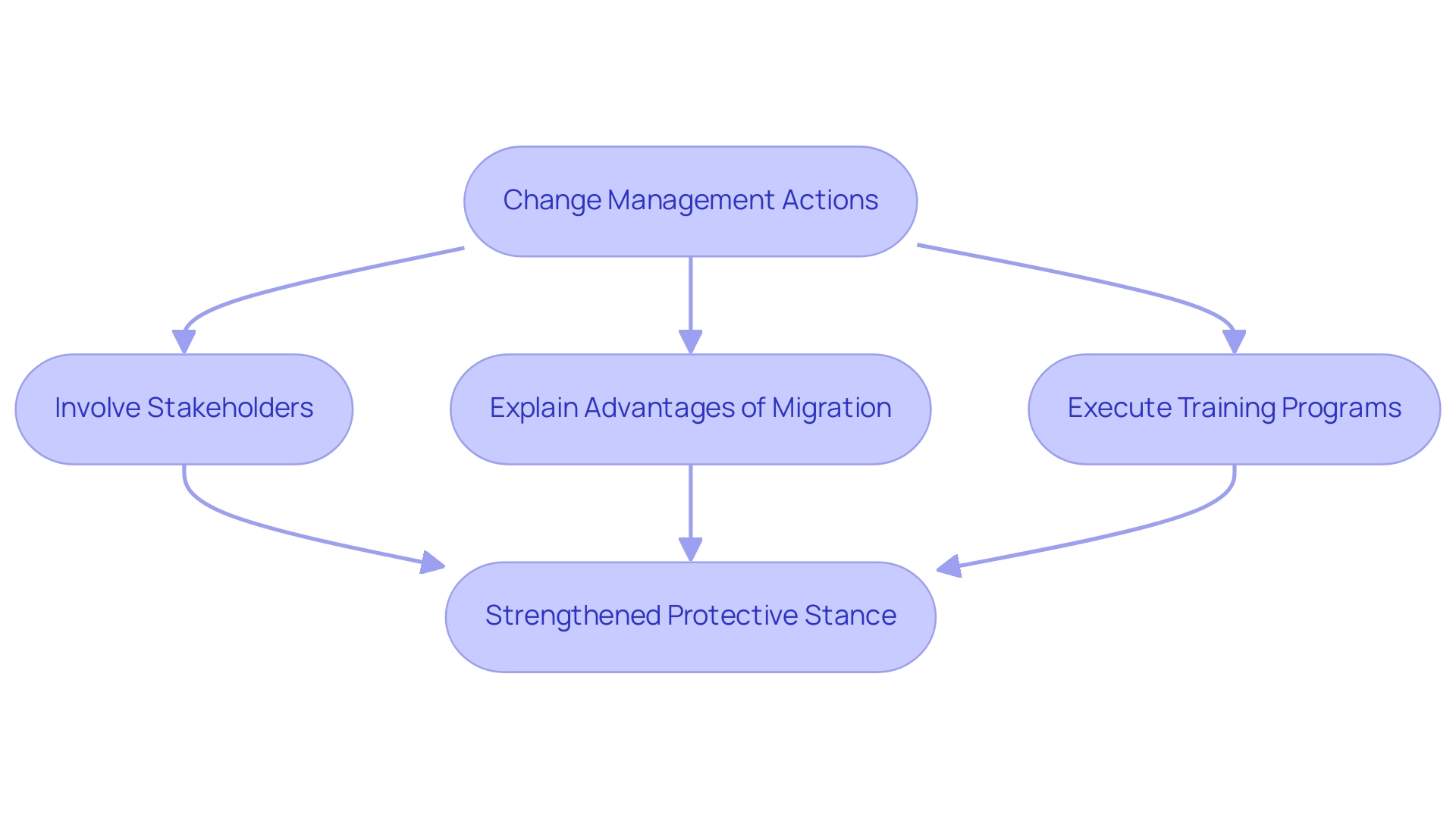
Change management is a crucial factor of online transition protection, tackling the substantial organizational and cultural shifts that come with this change. Successful transition to the digital infrastructure goes beyond simple technological changes; it requires a strong dedication to fostering a security-aware culture across the organization. This entails:
- Actively involving stakeholders
- Explaining the advantages of migration
- Executing extensive training programs to guarantee that all employees are well-informed of their roles in maintaining safety standards
As highlighted by Davidson Technology Consulting, 'The project lowered overall AWS expenses by approximately 40% during the non-production phase, and spending on online services by nearly 50% in the subsequent two months.' A pertinent example is highlighted by a leading Australian banking institution that consolidated its customer relationship management systems into a single cloud-based solution on Amazon Web Services (AWS). This initiative not only improved operational efficiency and customer service but also demonstrated the effectiveness of advocating optimal practices, as it fostered collaboration between teams and encouraged compliance with safety protocols.
By emphasizing change management, organizations can encourage greater user acceptance, reduce opposition to new processes, and ultimately strengthen their protective stance throughout and after the transition.
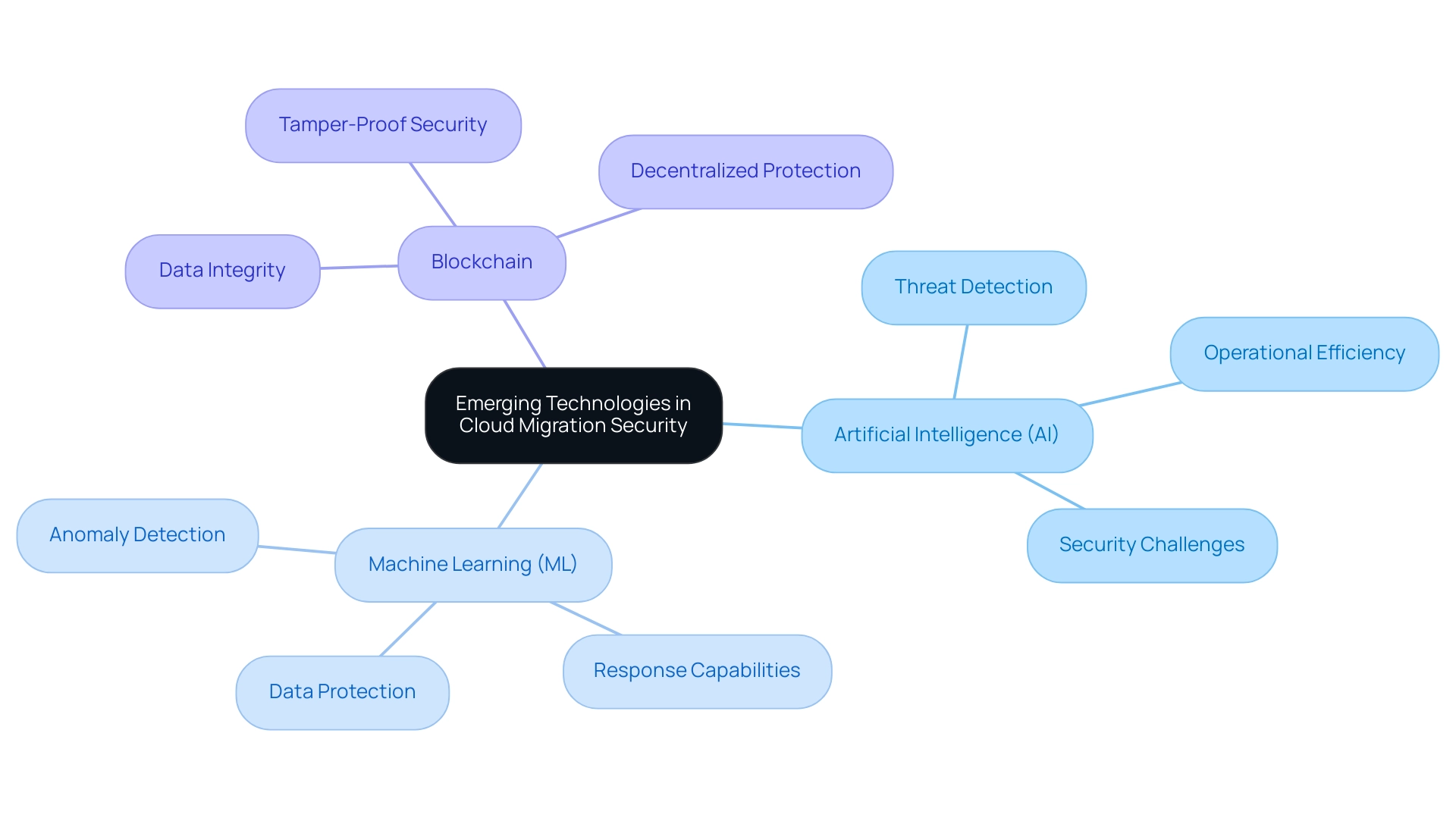
Emerging Technologies and Their Impact on Cloud Migration Security
Emerging technologies, such as artificial intelligence (AI), machine learning (ML), and blockchain, are transforming cloud migration protection. With end-user spending for Platform as a Service (PaaS) expected to attain $176.5 billion in 2024, indicating an impressive 21.5% growth, the necessity for strong protective measures cannot be overstated. AI and ML significantly improve threat detection and response capabilities by sifting through vast datasets to identify anomalies and potential breaches in real time.
As noted by SentinelOne,
Misuse of identity and access management keys is one of the top reasons behind online account misconfigurations, highlighting the critical need for sophisticated security frameworks.
Nevertheless, a recent case study named 'Understanding AI Integration Plans' indicates that 56% of IT decision-makers express a lack of clarity concerning their service provider's strategies for AI integration, highlighting the necessity for enhanced transparency in transition approaches. While online transition provides chances for scalability and digital transformation, it also poses cloud migration security challenges related to IT infrastructure adjustment and information protection.
Furthermore, blockchain technology offers a decentralized method for data integrity, ensuring that data remains secure and tamper-proof throughout the transfer process. Organizations that strategically adopt these technologies stand to enhance their security posture, streamline operations, and effectively protect against the evolving landscape of threats in the digital environment. The integration of these advanced technologies not only mitigates risks associated with cloud migration security challenges but also enhances overall operational efficiency.
Conclusion
The landscape of cloud migration security is increasingly complex, yet the importance of robust security measures cannot be overstated. As organizations transition to cloud environments, they face critical challenges such as:
- Data breaches
- Insufficient access controls
- Compliance risks
Recognizing these threats is vital, as they can have far-reaching implications for both financial health and reputational integrity.
Mitigating these risks requires a proactive approach, including the implementation of:
- Strong access controls
- Comprehensive data encryption
- Regular compliance audits
By adopting best practices such as conducting thorough risk assessments and investing in employee training, organizations can create a security-conscious culture that is integral to the success of their cloud migration efforts.
Furthermore, the integration of emerging technologies like artificial intelligence and blockchain can significantly enhance security measures, offering advanced threat detection and ensuring data integrity. As organizations navigate this transformative process, prioritizing change management is essential to foster user buy-in and facilitate a seamless transition.
In conclusion, cloud migration security is not merely a technical consideration; it is a fundamental component that underpins the trust and reliability of cloud environments. By addressing the challenges head-on and adopting a comprehensive security strategy, organizations can safeguard their data and applications, ultimately leading to successful and secure cloud adoption.




