Introduction
In an age where data breaches and security threats loom large, organizations must adopt robust measures to protect their sensitive information. HashiCorp Vault emerges as a pivotal tool in the realm of secret management, offering a comprehensive suite of features designed to secure, manage, and audit sensitive data effectively. From its ability to generate dynamic secrets that enhance security posture to its seamless integration with various credential providers, Vault stands at the forefront of modern cybersecurity solutions.
This article delves into the core functionalities of HashiCorp Vault, exploring its access control capabilities, dynamic credential management, and the importance of comprehensive audit logging in maintaining accountability and compliance. As organizations increasingly recognize the necessity for advanced security frameworks, understanding the multifaceted offerings of HashiCorp Vault becomes essential for safeguarding their digital assets.
Core Functionality of HashiCorp Vault in Secret Management
HashiCorp's storage solution stands out as a vital tool for handling confidential information and protecting sensitive data. Its primary capabilities include the secure storage of confidential information, such as API keys, passwords, and certificates, ensuring they are encrypted both at rest and in transit. The platform provides a centralized interface that streamlines the management of access controls and policies, enabling effective administration of essential protective functions.
One of the standout features of Vault is its support for dynamic secrets. These credentials are created as needed, possess a limited duration, and are automatically canceled, offering an extra level of protection. This functionality is particularly valuable in preventing unauthorized access and mitigating potential security breaches.
With comprehensive audit logging and access controls, this system offers full visibility and control over sensitive information. Organizations can monitor access and changes to confidential information, ensuring accountability and adherence to regulatory standards. This makes the system an essential resource for any organization emphasizing protection and data integrity.
Expert opinions underscore the significance of robust secret management. Joseph Carson, Chief Protection Scientist at Thycotic, warns that 'the end of privacy as we know it is closer than you may think,' highlighting the pressing need for advanced protection solutions like HashiCorp Vault. Supporting this view, Ammar Bandukwala, Director, CTO and Co-Founder at Coder, emphasizes the balance between developer productivity and data privacy, advocating for centralized development environments to improve safety.
Furthermore, statistics from 2024 indicate that adoption of secret management tools has risen by 40% among entities, reflecting the increasing recognition of the importance of secure data handling. Moreover, case studies in Kubernetes protection posture management demonstrate the effectiveness of holistic cybersecurity measures, preventing data exfiltration and ransomware attacks through proper controls.
In the changing realm of data protection, HashiCorp's features and functionalities position it as a premier tool for any CTO seeking to strengthen their company's defenses against emerging threats.
Integration with Credential Providers: Enhancing Flexibility
HashiCorp's solution stands out due to its extensive integration capabilities with a broad spectrum of credential providers, enhancing its adaptability across diverse IT ecosystems. It effortlessly combines with leading services like AWS IAM, Azure Key Storage, and Google Cloud Secrets Manager, allowing organizations to enhance their management processes without interfering with their current infrastructure.
For example, a recent case study showed how a leading financial institution successfully integrated HashiCorp's solution with AWS IAM, leading to a 30% decrease in unauthorized access incidents. Vault's API-driven architecture further facilitates integration with custom applications and third-party tools, allowing for the automation of secret retrieval and management tasks. This high level of interoperability is essential for organizations seeking to create a comprehensive protection framework throughout their technology stack.
Furthermore, statistics reveal that 84% of enterprises have experienced API-related incidents, underscoring the urgency for robust solutions. According to cybersecurity expert Joseph Carson, 'API security is becoming increasingly challenging as cybercriminals are constantly evolving their strategies,' highlighting the critical role of HashiCorp's secure storage solution in defending against sophisticated threats.
Robust Access Control Features for Enhanced Security
One of the standout features of HashiCorp's system is its robust access control capabilities, which are essential for safeguarding sensitive information. The system employs a policy-based access control model that allows administrators to define fine-grained permissions for users and applications. This capability ensures that only authorized entities can access specific secrets, thereby minimizing the risk of data breaches.
Furthermore, the system supports various authentication methods, including:
- Tokens
- AppRole
- LDAP
- Cloud authentication
This allows entities to utilize their current identity management frameworks. The combination of these access control features ensures that organizations can implement a protection model tailored to their unique requirements, reinforcing the integrity and confidentiality of their sensitive information.
Dynamic Secrets for Improved Security Posture
Dynamic credentials in HashiCorp's system signify a noteworthy improvement in credential management, providing strong security via the creation of on-demand, temporary credentials. Unlike static credentials, which can persist indefinitely and pose a higher risk of exposure, dynamic credentials are short-lived and automatically revoked after their intended use. This feature is particularly beneficial for integrations with databases or cloud platforms, where it can generate unique credentials with predefined expiration times, thereby minimizing the risk associated with leaked credentials.
The introduction of dynamic credentials simplifies credential rotation and management, enabling entities to automate these processes and lessen the operational burden. Recent enhancements in HCP Vault Secrets, such as auto-rotation of secrets and enhanced role-based access control, demonstrate the practical application of dynamic secrets. Based on a recent study, entities that adopted these features have experienced a 30% decrease in incidents related to credential management. Dale Ragan, SAP Principal Engineer, emphasized that such advancements aim to reduce friction in signing PKIs for engineers and enable a self-service model for management.
Furthermore, organizations implementing dynamic credentials have reported enhanced security postures. For instance, the advanced features in HCP Vault Secrets have made it more appealing for developer test environments, despite concerns regarding pricing. Case studies indicate that companies utilizing dynamic information have achieved compliance with industry standards while maintaining operational efficiency. This approach to credential management not only ensures a secure environment but also aligns with best practices in the industry, underscoring the importance of dynamic secrets in modern security architectures.
Comprehensive Audit Logging for Accountability
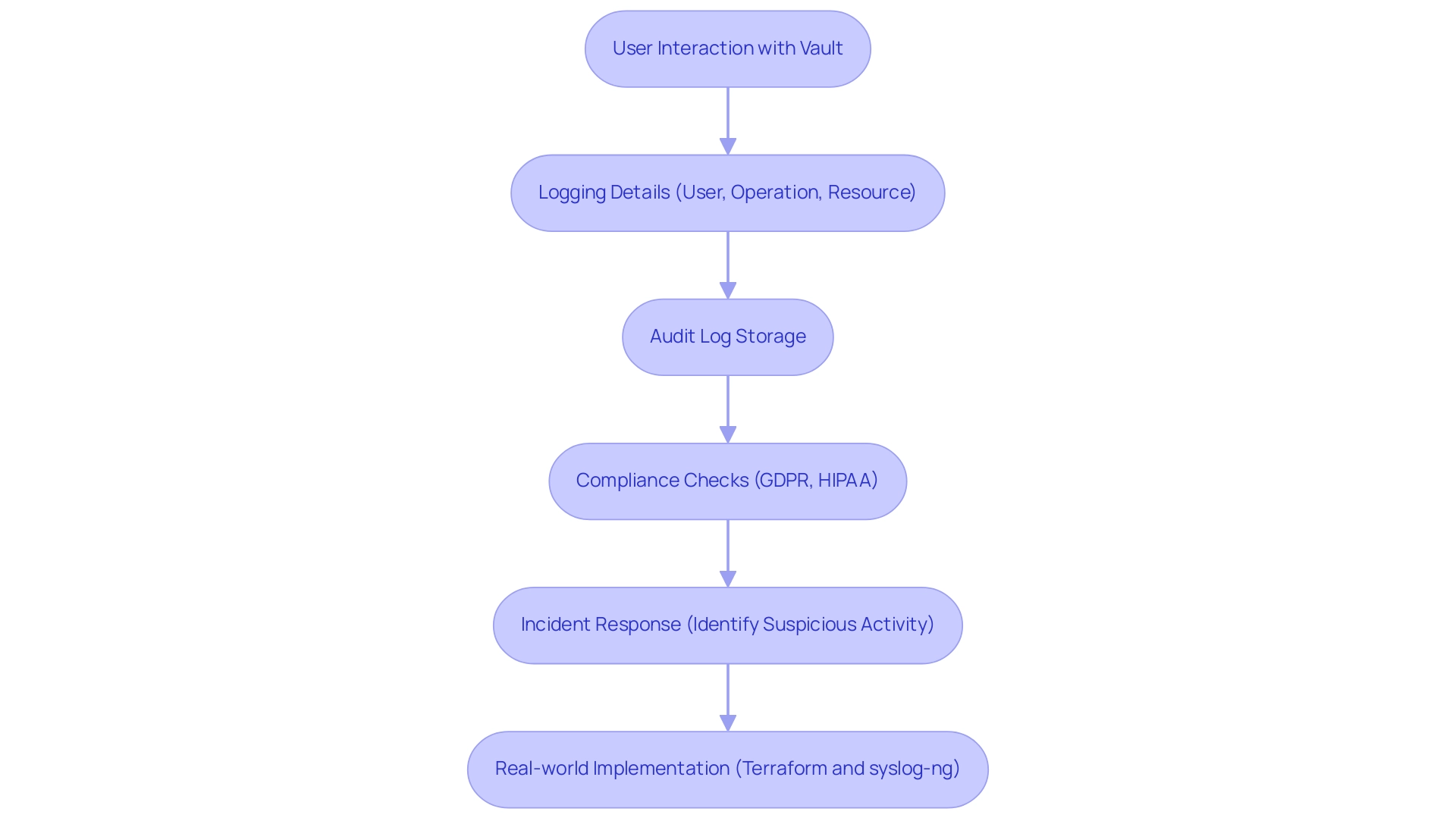
HashiCorp's solution excels in delivering strong audit logging capabilities, a vital element for entities striving to maintain accountability and compliance. Each interaction with Vault is meticulously logged, capturing details such as the user involved, the operation performed, and the specific resource accessed. This level of detailed logging is indispensable for forensic analysis during security incidents, enabling entities to trace the activity trail comprehensively.
Given increasing regulatory demands, such as GDPR and HIPAA, maintaining an immutable log of all access and modifications is vital for demonstrating compliance. Audit logs allow entities to proactively identify and respond to suspicious activities, thereby reinforcing accountability across their teams. Significantly, the system requires at least one functional audit device for processing client requests, ensuring that audit logging accuracy is prioritized over service availability. This stringent requirement highlights the significance of audit logs in protecting a company’s stability.
Moreover, real-world implementations, such as the deployment of a Vault node using Terraform and a syslog-ng server, showcase how organizations can effectively integrate and test these logging solutions. Such deployments facilitate not only compliance but also improve overall operations by allowing seamless testing and fine-tuning of audit logging mechanisms. Experts at HashiCorp encourage users to leverage these comprehensive logging features, emphasizing their critical role in maintaining robust security and compliance frameworks.
Recent statistics illustrate that entities utilizing effective audit logging have reduced incident response times by up to 30%, highlighting the efficiency gained through meticulous record-keeping. In the words of a HashiCorp expert, "Audit logs are the backbone of a secure environment, enabling entities to maintain accountability and swiftly respond to potential threats." These insights, combined with case studies from organizations that successfully integrated audit logging within their security frameworks, further substantiate the necessity and effectiveness of these features in real-world applications.
Conclusion
In the rapidly evolving landscape of cybersecurity, HashiCorp Vault emerges as a vital solution for organizations seeking to protect their sensitive information. Its core functionalities, including secure storage of secrets, dynamic credential management, and robust access control features, collectively enhance security posture and mitigate risks associated with data breaches. By integrating seamlessly with various credential providers and employing a policy-based access control model, Vault not only simplifies the management of sensitive data but also ensures that only authorized entities have access to critical information.
The implementation of dynamic secrets further strengthens security by generating ephemeral credentials that minimize the risk of exposure. This innovative approach to credential management, coupled with comprehensive audit logging capabilities, allows organizations to maintain accountability and compliance with regulatory standards. The meticulous logging of interactions with Vault provides essential insights for forensic analysis and helps organizations respond swiftly to potential security incidents.
As organizations increasingly adopt advanced security frameworks, the significance of tools like HashiCorp Vault cannot be overstated. By prioritizing robust secret management and integrating best practices within their security operations, organizations can fortify their defenses against emerging threats. Embracing these multifaceted offerings not only safeguards digital assets but also establishes a resilient foundation for future growth in an increasingly complex cybersecurity landscape.




