Introduction
In an era where cyber threats continually evolve, safeguarding digital assets is paramount for organizations. Microsoft Threat Protection offers an integrated suite of advanced security features designed to address this critical need. By leveraging machine learning and behavioral analytics, it provides real-time threat detection and neutralization.
Automation of investigation and remediation processes significantly reduces the burden on security teams and accelerates incident response times. Centralized security management enhances visibility and control across various platforms, while seamless integration with Microsoft 365 ensures robust security without compromising usability. This comprehensive approach not only streamlines security management but also fortifies the organization's defenses against a broad spectrum of cyber threats.
Key Features of Microsoft Threat Protection
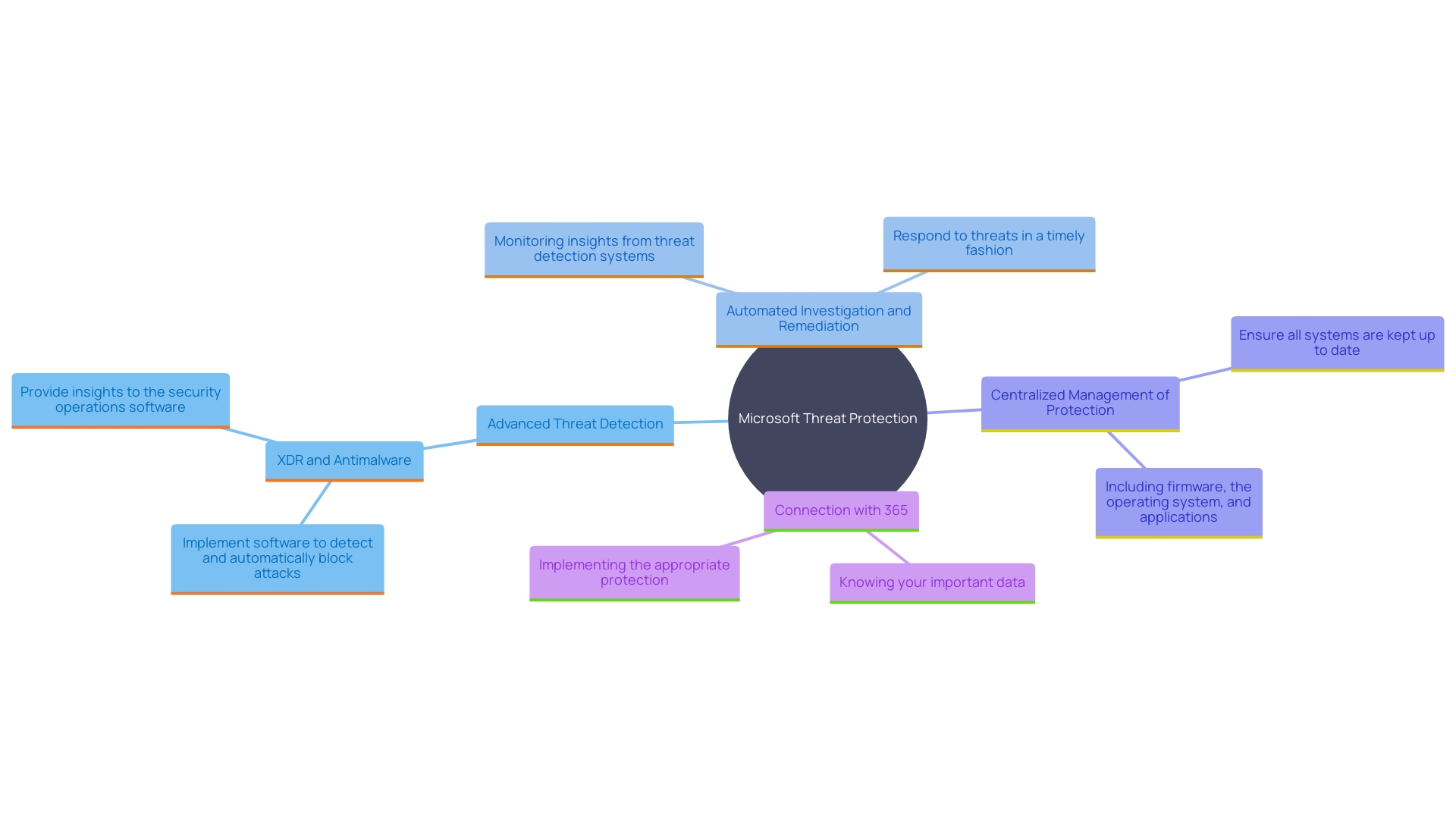
Microsoft Threat Protection delivers an integrated suite of advanced security features designed to safeguard your organization's digital assets. Key capabilities include:
-
Advanced Threat Detection: Harnesses the power of machine learning and behavioral analytics to identify and neutralize threats in real-time. This proactive approach ensures that potential breaches are detected and managed promptly, minimizing risk.
-
Automated Investigation and Remediation: Streamlines the threat response process by automating investigations and remediation tasks. This lessens the manual workload on protection teams and speeds up the time to resolution. For instance, ING, one of Europe's largest banks, has utilized this feature to improve its protective stance by merging its safety tools into a unified end-to-end solution, safeguarding its operations and its 38 million customers across 40 nations.
-
Centralized Management of Protection: Offers a unified dashboard that provides comprehensive visibility and control over protection across multiple platforms, including endpoints, email, and cloud services. This centralized method streamlines the oversight of intricate protective settings, allowing entities to identify and react to dangers more effectively.
-
Connection with 365: Improves the protection of the whole 365 environment by using available instruments and information. By merging effortlessly with the 365 suite, companies can utilize familiar interfaces and processes, ensuring strong protection without sacrificing usability.
These features collectively contribute to a more streamlined and effective security strategy, enabling entities to better manage risk and protect their critical assets.
Benefits of Implementing Microsoft Threat Protection
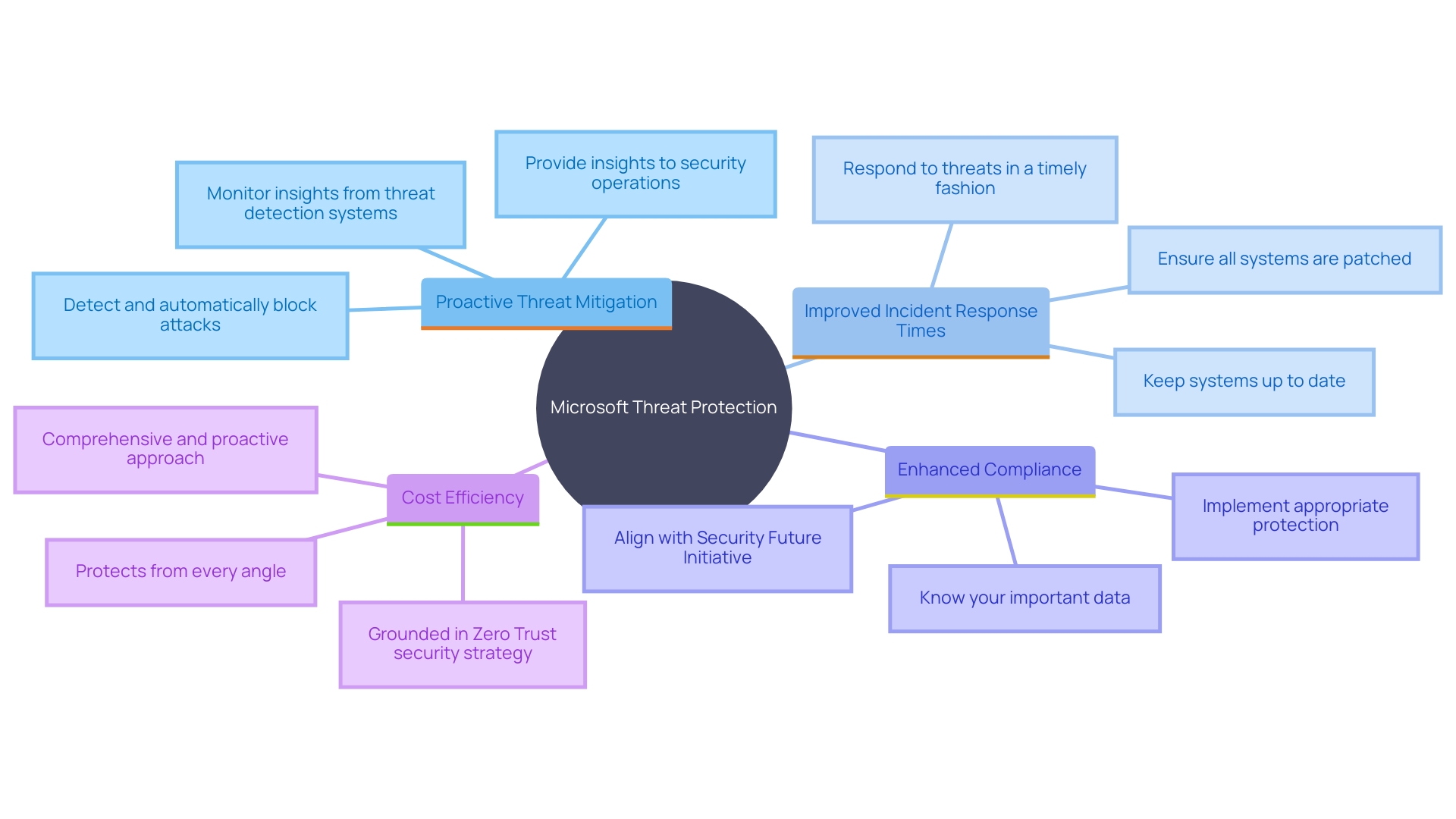
Introducing Threat Protection from the software company provides numerous benefits for organizations looking to strengthen their cybersecurity measures. These benefits include:
-
Proactive Threat Mitigation: With advanced AI and automation, Microsoft Threat Protection identifies and neutralizes threats before they can cause harm. This proactive approach significantly reduces the risk of data breaches, as evidenced by the 50% reduction in employee susceptibility to phishing through simulation training.
-
Improved Incident Response Times: Automation and centralized management streamline incident response, enabling quicker remediation. Companies like ING have experienced enhanced protection by consolidating their protection tools into a single, cohesive system, ensuring rapid response across all environments.
-
Improved Compliance: Microsoft’s protective solutions assist entities in meeting stringent regulatory requirements by offering strong protective measures and thorough documentation. This guarantees that all systems stay current and compliant, tackling the main reason many entities become targets of attacks—unpatched and outdated systems.
-
Cost Efficiency: By integrating various protective solutions into one, organizations can reduce operational costs. This end-to-end approach not only streamlines management but also reduces costs related to maintaining multiple products. ING's integration of protection tools is a prime example of achieving cost efficiency while enhancing safety.
These advantages highlight the importance of a unified protection strategy in today's complex threat landscape. As the tech giant continues to innovate, incorporating AI and automation, enterprises can anticipate even greater improvements in their cybersecurity stance.
Best Practices for Enhancing Microsoft 365 Security
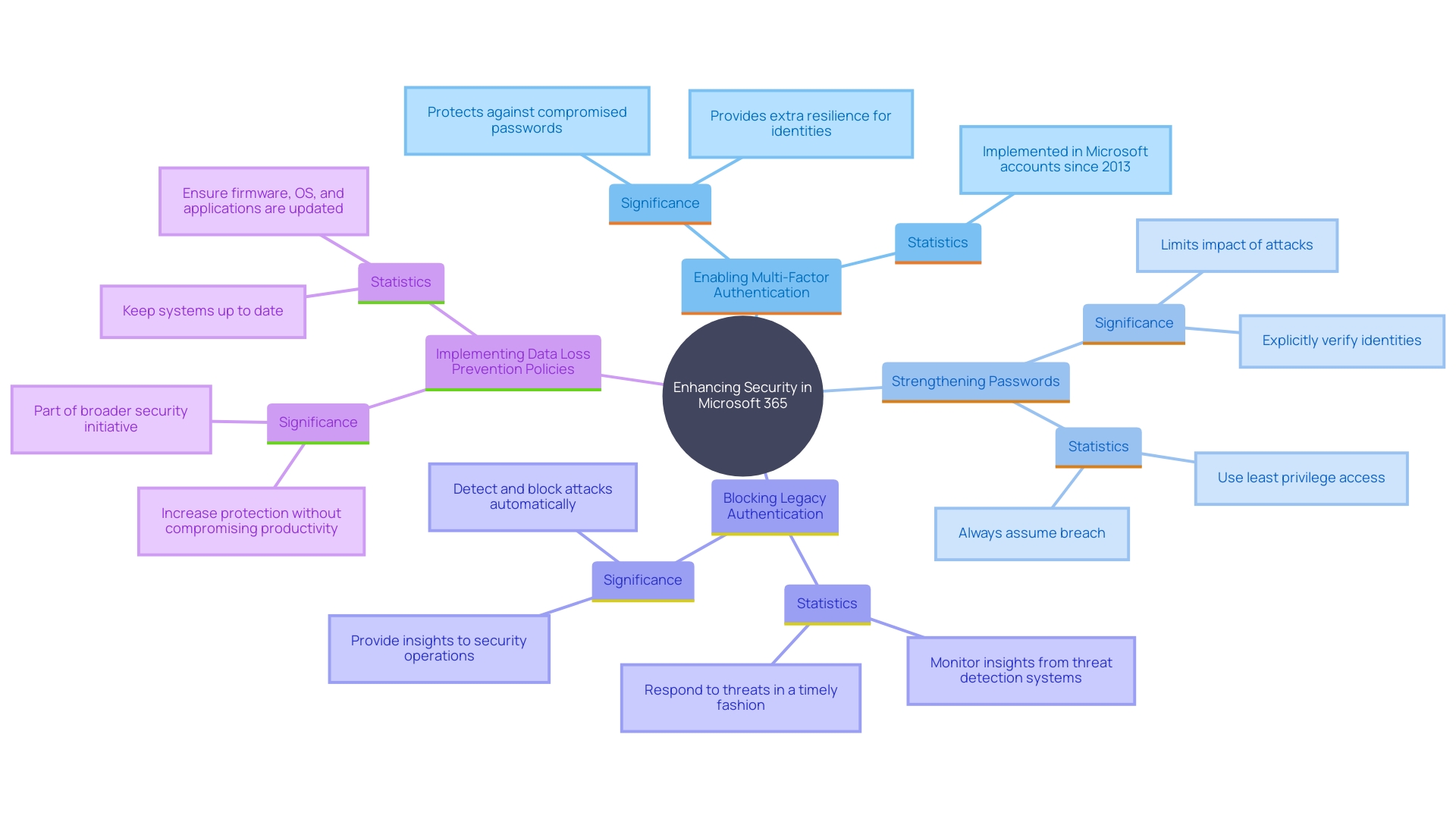
To maximize the effectiveness of Microsoft Threat Protection within Microsoft 365, organizations should adopt the following best practices:
-
Enabling Multi-Factor Authentication (MFA): Adding an extra layer of security by requiring users to verify their identity through multiple means is crucial. This approach has proven effective in maintaining safety, especially against sophisticated nation-state threat actors. Research indicates that multiple layers of defenses, such as MFA, can significantly reduce exposure to attacks.
-
Strengthening Passwords and Blocking Legacy Authentication: Ensuring strong password policies are in place and disabling legacy authentication protocols are essential steps to reduce vulnerabilities. Statistics reveal that critical vulnerabilities were found in several IoT and OT operating systems, highlighting the importance of robust password practices. Additionally, in just 45 days, numerous devices were found using the default password “admin,” emphasizing the need for stringent password policies.
-
Implementing Data Loss Prevention (DLP) Policies: Protecting sensitive data by establishing policies that govern data sharing and access is vital. The Great SaaS Data Exposure report disclosed that almost 6 out of 10 inactive guest users continue to be active after 90 days, presenting considerable risks. Enforcing DLP policies assists in reducing these risks by ensuring data integrity and protection.
Implementing these practices corresponds with a thorough end-to-end protection strategy, which emphasizes safeguarding the complete digital environment before and after an incident. This method, based on a Zero Trust protection strategy, incorporates multiple layers of defense, offering a unified user experience and comprehensive risk awareness.
Automating Threat Detection and Remediation
Automation is pivotal in enhancing modern cybersecurity strategies, and Microsoft Threat Protection exemplifies this with its sophisticated capabilities. By automating risk identification and resolution, organizations can greatly enhance their protective stance.
One of the key features is the ability to configure alerts for specific threat indicators. This means setting up automatic alerts for suspicious activities, ensuring timely responses and mitigating potential damages. Utilizing built-in playbooks for incident response further streamlines operations by automating common response actions, thus decreasing the workload on teams and allowing them to concentrate on more complex tasks.
Ongoing oversight and adjusting protective policies are also essential. Regular updates to automation rules and thresholds, informed by emerging threats and organizational changes, ensure that the system remains robust and responsive. As highlighted by Ing's implementation of an end-to-end security approach, consolidating security tools into a unified solution can simplify management and enhance protection across diverse environments.
Furthermore, the impact of AI in cybersecurity cannot be overstated. In 2019, global enterprise spending on AI-based cybersecurity applications reached $265 million, underscoring their importance. AI-powered tools have shown impressive success rates, with 44% of organizations reporting success rates over 80% for these tools. This signifies a considerable benefit in utilizing AI to standardize hunting practices and enhance precision and innovation in risk management.
To illustrate, ING, one of the largest banks in Europe, successfully consolidated a fragmented mix of protective tools into a comprehensive protective approach, safeguarding its operations and 38 million customers across 40 countries. Such integration not only streamlines management of protections but also boosts the overall efficiency and effectiveness of risk defense.
In summary, automating threat detection and remediation through solutions like Microsoft Threat Protection, coupled with the strategic use of AI, provides a formidable defense against evolving cyber threats, ensuring that organizations can maintain a strong security posture in an increasingly complex digital landscape.
Conclusion
The comprehensive capabilities of Microsoft Threat Protection make it an essential tool for organizations seeking to enhance their cybersecurity defenses. By integrating advanced threat detection powered by machine learning and behavioral analytics, it proactively identifies and neutralizes potential threats, significantly reducing the risk of data breaches. The automation of investigation and remediation processes not only alleviates the workload on security teams but also accelerates incident response times, ensuring that organizations can effectively manage threats as they arise.
Implementing Microsoft Threat Protection offers numerous benefits, including improved compliance with regulatory requirements and cost efficiency through the consolidation of disparate security solutions. Organizations can expect a streamlined security strategy that enhances their overall posture against cyber threats. Adopting best practices, such as enabling multi-factor authentication and implementing data loss prevention policies, further strengthens the security framework, safeguarding sensitive information and reducing vulnerabilities.
Ultimately, the integration of automation and artificial intelligence within Microsoft Threat Protection positions organizations to respond effectively to the ever-evolving threat landscape. By embracing this holistic security approach, organizations can fortify their defenses, ensuring robust protection for their digital assets while maintaining operational efficiency. As the cybersecurity landscape continues to evolve, leveraging such advanced solutions will be paramount in maintaining a resilient and secure organizational environment.




