Introduction
In an age where data breaches and cyber threats loom large, organizations must prioritize the secure management of sensitive information. HashiCorp Vault emerges as a powerful tool in this landscape, offering robust solutions for:
- Secrets management
- Dynamic secrets
- Encryption services
By understanding its core concepts and functionalities, organizations can effectively safeguard their critical data while navigating the complexities of modern security challenges. This article delves into the intricacies of HashiCorp Vault, exploring its:
- Authentication methods
- Configuration processes
- Best practices
- Advanced integration strategies
All aimed at enhancing security frameworks and building a resilient infrastructure against potential vulnerabilities.
Understanding HashiCorp Vault: Core Concepts and Functionality
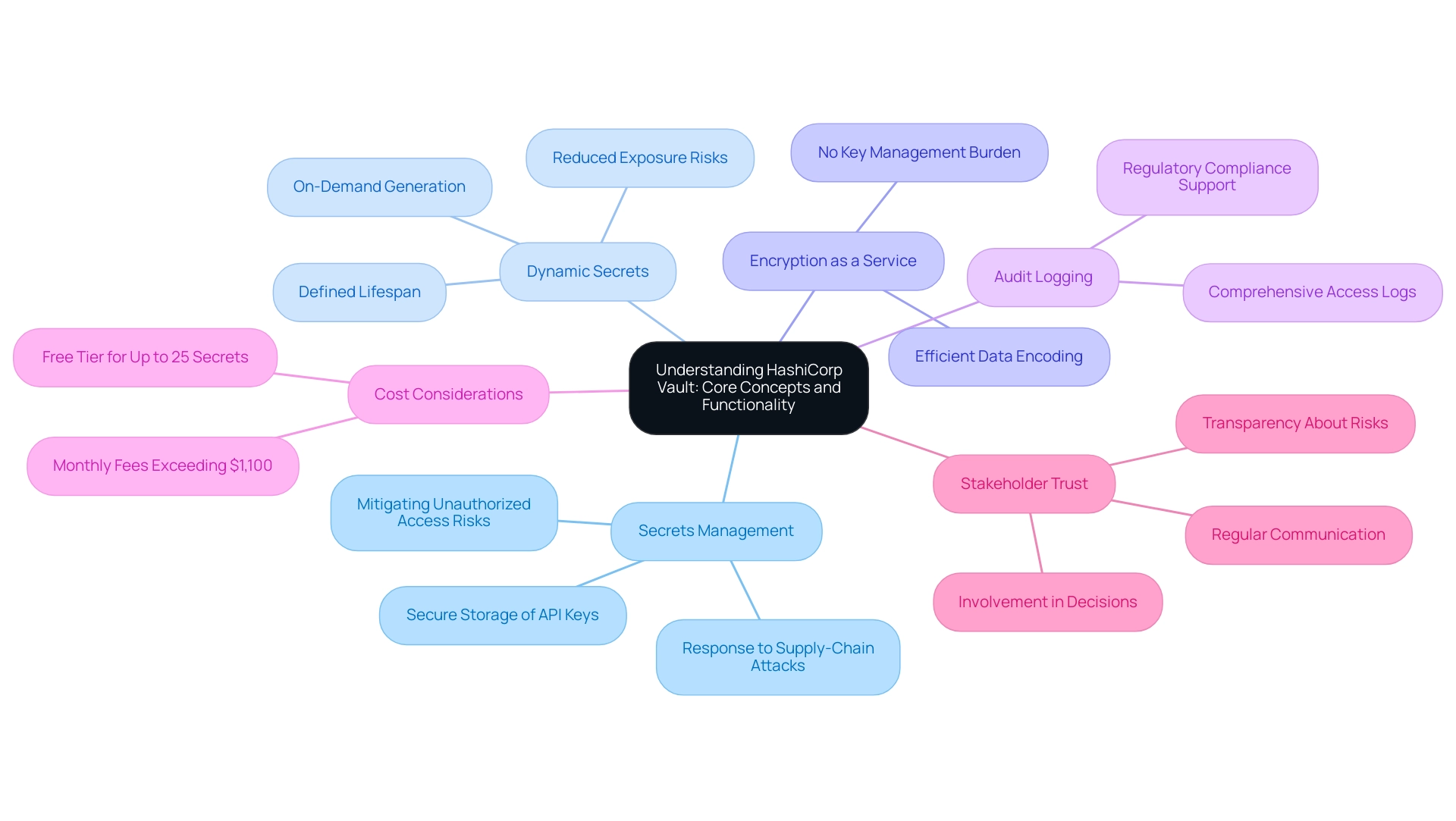
HashiCorp's system serves as a robust solution for the secure management of secrets and sensitive data within organizations. Operating on a client-server architecture, the secure storage server is responsible for keeping secrets, while the secure storage client facilitates communication with the server. Key concepts integral to understanding the system's functionality include:
- Secrets Management: The system ensures a secure method for storing and accessing critical information such as API keys, passwords, and certificates, thereby mitigating the risks associated with unauthorized access. In today’s landscape, organizations narrowly escaped sophisticated supply-chain attacks that could have compromised countless systems, underscoring the need for effective secrets management.
- Dynamic Secrets: A significant advancement over static secrets, dynamic secrets are generated on demand and possess a defined lifespan. This characteristic significantly reduces the potential for exposure, improving protective protocols within the organization.
- Encryption as a Service: The system offers encryption services that enable organizations to encode their data efficiently, without the burden of managing encryption keys, thus streamlining protective processes.
- Audit Logging: The system maintains comprehensive logs detailing all access and operational activities. This feature not only enhances protective measures but also assists in adhering to regulatory requirements.
Additionally, it's important to note that HashiCorp's solution has a free tier for up to 25 secrets, but can become costly with monthly fees surpassing $1,100 for extra features. A comprehensive understanding of these fundamental ideas is crucial for the efficient execution and oversight of access controls in relation to HashiCorp Vault auth methods, especially as organizations increasingly emphasize safety in their operations. As highlighted by industry experts, establishing trust with stakeholders during implementations involves communicating regularly, including them in decisions, and being transparent about risks.
Exploring Authentication Methods in HashiCorp Vault
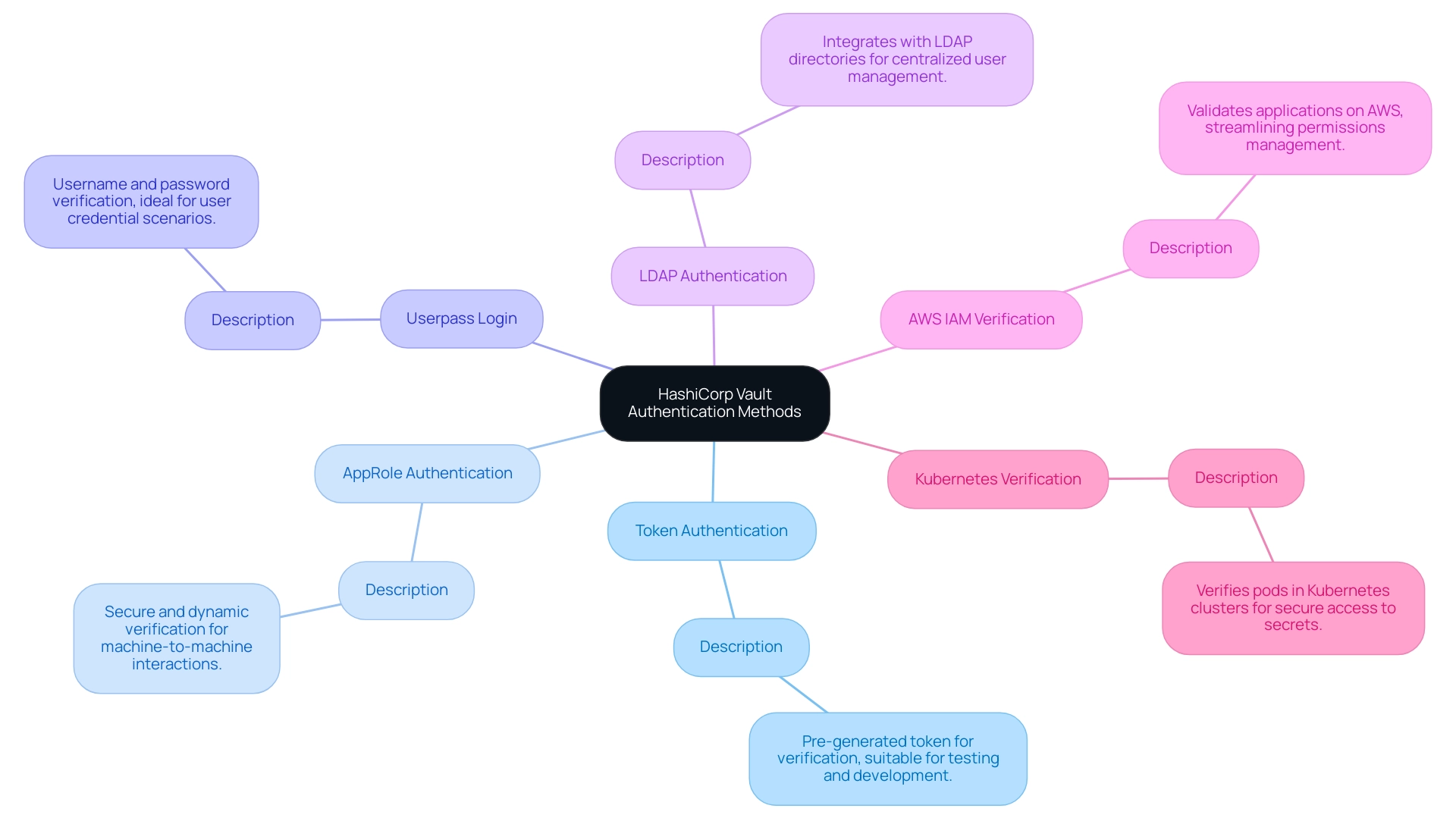
HashiCorp Vault provides a varied selection of verification techniques, including hashicorp vault auth methods, allowing organizations to effortlessly integrate it into their protective frameworks. A comprehensive grasp of these techniques is crucial for choosing the most efficient verification approach that incorporates hashicorp vault auth methods tailored to particular security needs. The primary verification methods include:
- Token Authentication: This straightforward method enables clients to utilize a pre-generated token for verification. It is particularly suitable for testing and development environments, ensuring ease of access without compromising security.
- AppRole Authentication: Specifically designed for machine-to-machine interactions, AppRole enables secure and dynamic verification for applications, promoting a robust protection stance in automated workflows.
- Userpass Login: Using a username and password, this approach is ideal for situations where user credentials are necessary, offering a familiar and easily applied verification mechanism.
- LDAP Authentication: By integrating with existing LDAP directories, this approach enables users to verify their identity using their directory credentials, streamlining user management and improving safety through centralized authentication.
- AWS IAM Verification: This approach utilizes AWS Identity and Access Management, enabling the validation of applications operating on AWS and streamlining the administration of permissions and access controls.
- Kubernetes Verification: Designed for containerized settings, this approach verifies pods within Kubernetes clusters, thus streamlining the management of secrets and guaranteeing secure access to sensitive data.
As organizations progressively move to cloud environments, comprehending hashicorp vault auth methods is crucial for reducing risks and improving overall security frameworks. In fact, with 66% of organizations indicating higher cloud expenditure, the necessity for efficient verification techniques becomes even more vital in managing resources and reducing risks linked to cloud waste. Moreover, the system's ability to manage requests is measured through a count metric, demonstrating its efficiency in processing access requests.
As highlighted by Bitwarden, roughly 41% of developers are prioritizing 2FA adoption over any other area of security, emphasizing the trend towards stronger verification techniques, which aligns with the significance of understanding various access strategies.
Step-by-Step Guide to Configuring Authentication Methods
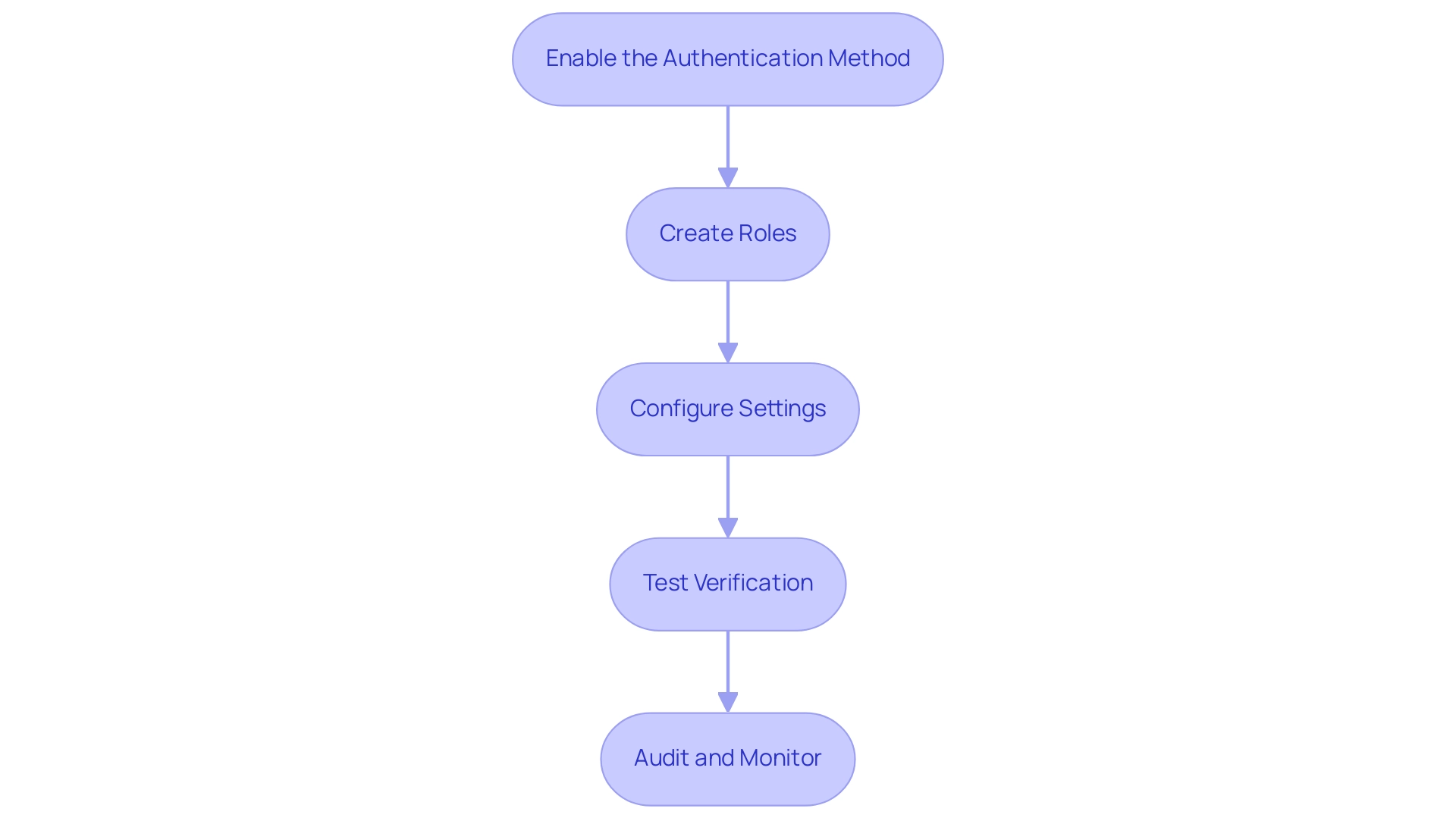
Setting up hashicorp vault auth methods in HashiCorp Storage is a crucial task that guarantees secure entry to your secrets. Significantly, you can set up OIDC on Google Workspace for secure access to HCP Storage, which can improve your security stance. Follow these detailed steps to establish verification effectively:
-
Enable the Authentication Method: Begin by using the Vault CLI to activate the desired identity backend. For instance, to enable AppRole, execute:
bash vault auth enable approle -
Create Roles: Establish roles that outline specific permissions linked to your verification process. For the AppRole, you would run:
bash vault write auth/approle/role/my-role policies=my-policy -
Configure Settings: Tailor settings pertinent to your verification approach, such as the token Time-To-Live (TTL) or permitted policies. For AppRole, adjust your role with:
bash vault write auth/approle/role/my-role token_ttl=1h
Keep in mind that when an authentication method is disabled, all users authenticated via that method are automatically logged out, which is crucial for managing user access effectively. -
Test Verification: It's essential to confirm that the method operates correctly. For AppRole, you can test authentication by executing:
bash vault write auth/approle/login role_id=<role_id> secret_id=<secret_id>
A practical example of logging into the Vault Web UI can be done using the Root Token saved during the setup, which allows users to gain access to the Vault web interface, enabling further management of secrets. -
Audit and Monitor: Establish auditing systems to record access attempts, which is essential for maintaining adherence to safety regulations. Monitoring these logs will help identify any unauthorized access attempts and maintain the integrity of your system. As Biswanath Giri, a Cloud & AI Architect, mentions, 'Qwiklabs offers genuine cloud settings that assist developers and IT experts in mastering cloud platforms and software…' This highlights the significance of practical experience in setting up and managing login processes efficiently.
By following these steps, you will create a strong setup for your selected access control system using HashiCorp Vault auth methods, improving both protection and functionality.
Best Practices for Securing Authentication in Vault
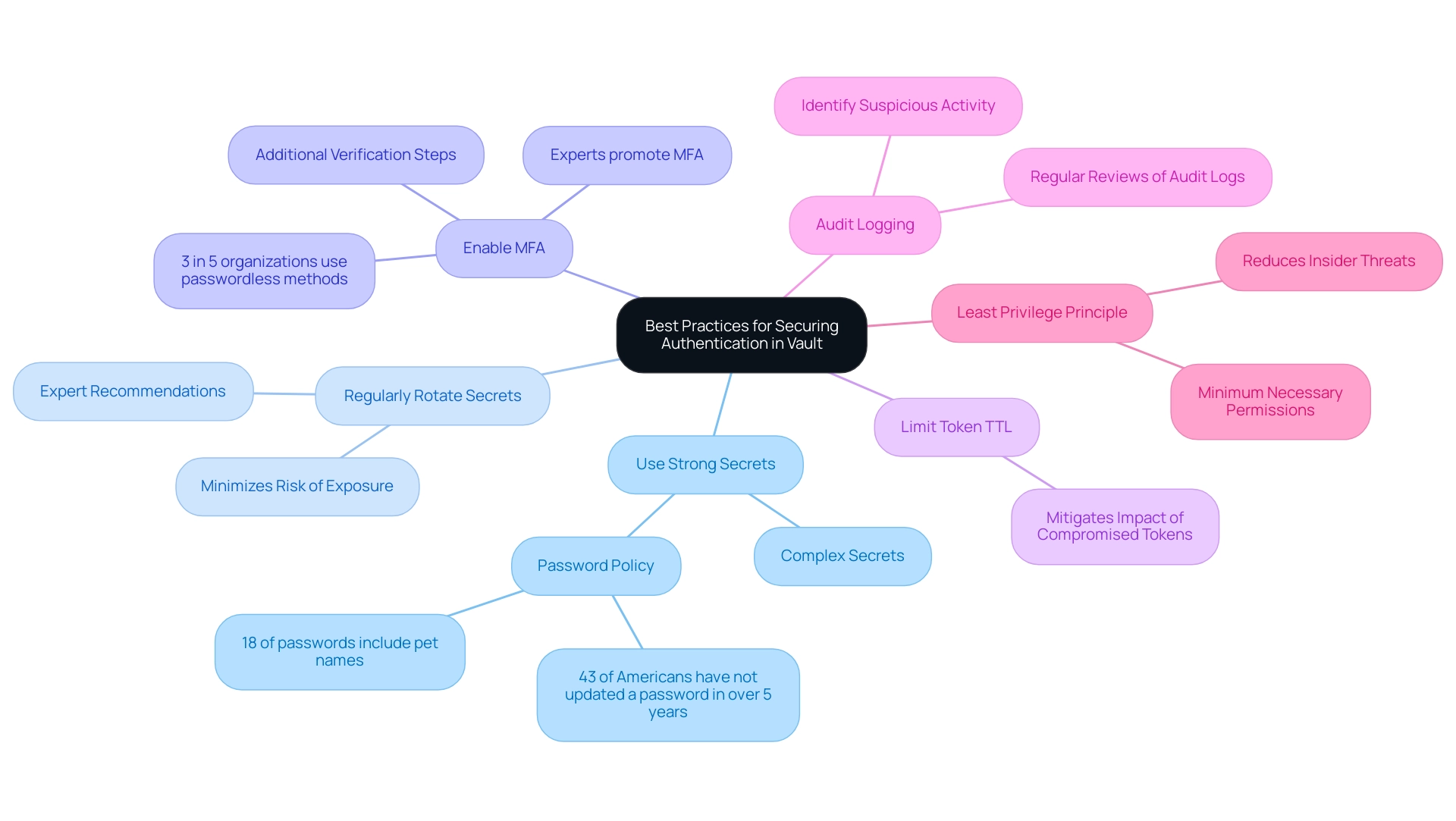
Securing hashicorp vault auth methods is essential for safeguarding sensitive data and maintaining organizational integrity. To enhance your protection stance, consider the following best practices:
- Use Strong Secrets: Implement complex and hard-to-guess secrets or tokens. Establish robust password policies that reflect the growing concern over password protection—currently, 43% of Americans have not updated a password in over five years, and 18% of passwords include the name of the user’s pet, highlighting common pitfalls in password safety. As one expert noted, 'The strength of your secrets is the first line of defense against unauthorized access.'
- Regularly Rotate Secrets: Regular rotation of access tokens and secrets is crucial. This routine minimizes the risk of exposure and aligns with expert recommendations for maintaining a secure environment. According to industry professionals, 'Rotating secrets regularly is not just a best practice; it's a necessity in today’s threat landscape.'
- Enable MFA (Multi-Factor Authentication): Adding MFA significantly improves protection by requiring additional verification steps, thus making unauthorized access exponentially more difficult. Notably, recent data shows that only 3 in 5 organizations utilize passwordless methods for accessing IT infrastructure, indicating a gap that can be addressed through MFA. Experts promote MFA as an essential layer of protection, stating, 'Incorporating MFA is a game changer for safeguarding sensitive information.'
- Limit Token TTL (Time-To-Live): Setting appropriate TTL values for tokens is vital. Shorter TTLs can mitigate the potential impact of compromised tokens, ensuring that any unauthorized access is time-sensitive.
- Audit Logging: Conduct regular reviews of audit logs to identify suspicious activity and unauthorized access attempts. This proactive approach is paramount in maintaining a secure environment.
- Least Privilege Principle: Adhering to the principle of least privilege, assign the minimum necessary permissions to users and roles. This limits exposure to sensitive data and reduces the risk of insider threats.
Moreover, the case study titled 'Openness to Password Manager Adoption' shows that over 75% of non-users indicated a readiness to adopt a password manager if it offers the right balance of usability, protection, and affordability. This insight underscores the importance of promoting strong secrets and effective password management practices. By applying these best practices, organizations can greatly improve the protection of their access techniques using HashiCorp Vault auth methods, thereby effectively safeguarding their vital information from emerging threats.
Advanced Integration and Management of Authentication Methods
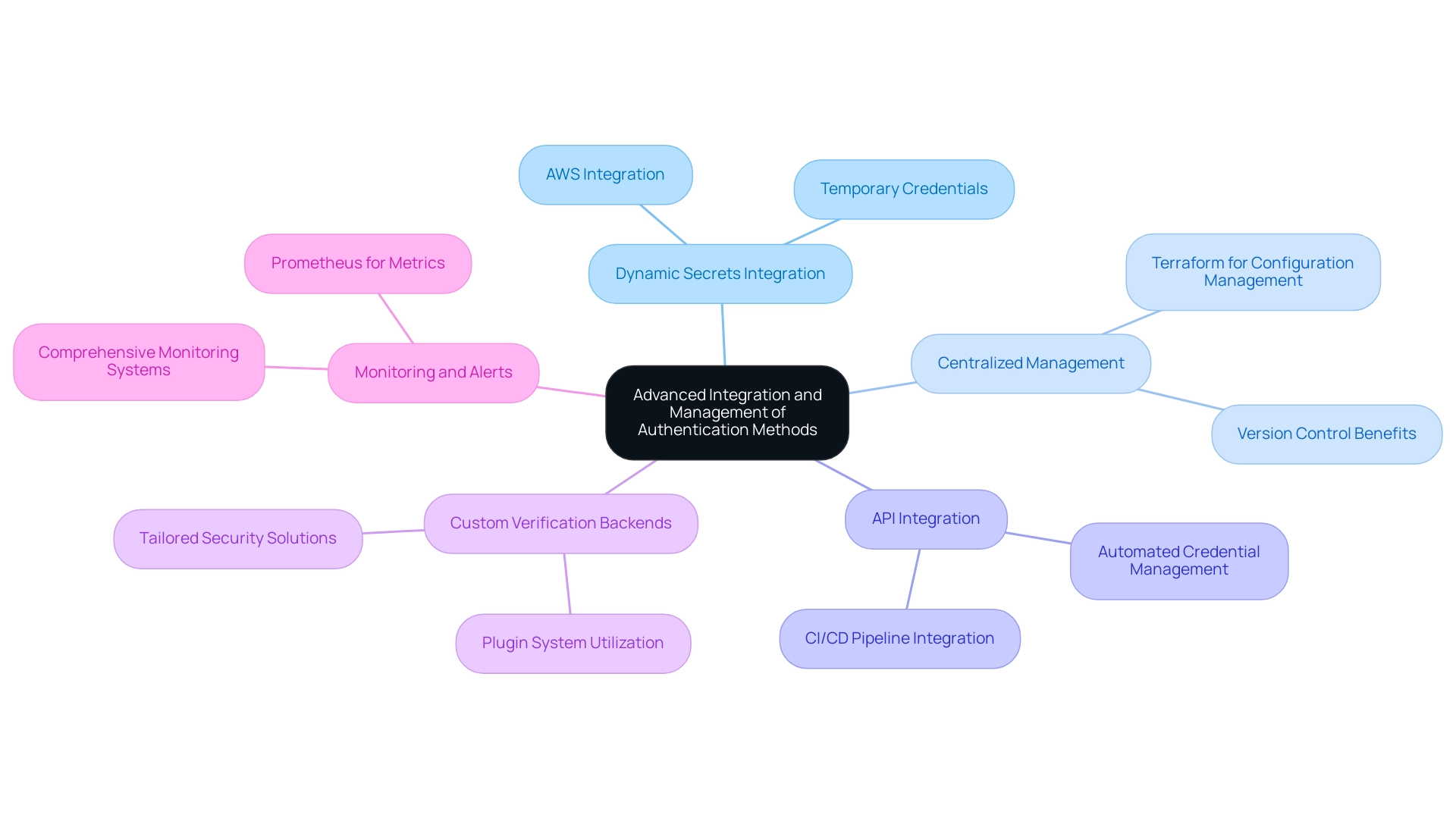
Incorporating sophisticated verification techniques in the HashiCorp Vault auth methods is crucial for improving your organization's security stance. Here are effective strategies for optimizing authentication management:
- Dynamic Secrets Integration: Implement dynamic secrets wherever possible to mitigate the risk of secret exposure. For instance, by integrating HashiCorp's secret management tool with AWS, organizations can generate temporary credentials that are automatically rotated, thereby minimizing the window of vulnerability.
- Centralized Management: Utilize tools such as Terraform for managing configurations as code. This approach not only facilitates version control but also simplifies the replication of configurations across different environments, promoting consistency and efficiency. In fact, statistics show that centralized management tools can significantly reduce operational overhead, making them a worthy investment.
- API Integration: Utilize the strong API to handle access methods programmatically. This enables automation in credential management and seamless integration with Continuous Integration/Continuous Deployment (CI/CD) pipelines, enhancing operational efficiency through the use of HashiCorp Vault auth methods.
- Custom Verification Backends: When existing backends do not align with specific organizational needs, consider developing custom verification solutions using HashiCorp Vault auth methods and its plugin system. This flexibility enables customized protective measures that satisfy distinct needs.
- Monitoring and Alerts: Establish a comprehensive monitoring system for access techniques to promptly detect anomalies or unauthorized entry attempts. Utilizing tools such as Prometheus can assist in monitoring essential metrics and sending notifications based on established thresholds, thereby ensuring proactive management.
As Bill Whyman highlights, "The time is suitable for a national initiative on a public-private technology training collaboration..." This emphasizes the need for skilled personnel to effectively handle advanced verification techniques, which is essential to your overall safety stance. By implementing these advanced integration strategies and utilizing HashiCorp Vault auth methods, organizations can significantly enhance their management practices, streamline operations, and protect sensitive data more effectively. Furthermore, as highlighted by the OpsRamp survey, 94% of IT professionals reported reduced startup costs when utilizing multi-cloud strategies, illustrating the financial advantages of adopting such approaches.
As 78% of companies prioritize hybrid/multi-cloud setups for enhanced security and cost savings, adopting robust authentication methods is not only prudent but essential.
Conclusion
The exploration of HashiCorp Vault reveals its multifaceted capabilities, particularly in the realm of secure data management. By offering comprehensive solutions such as:
- Secrets management
- Dynamic secrets
- Encryption services
Vault empowers organizations to safeguard their sensitive information against an array of cyber threats. The article delves into essential components, including various authentication methods, configuration steps, best practices, and advanced integration strategies, all aimed at fortifying security frameworks.
Understanding the diverse authentication methods available in Vault is critical for organizations seeking to tailor their security measures effectively. From token authentication to integration with cloud services like AWS and Kubernetes, the ability to choose the right method enhances operational efficiency and security posture. Furthermore, the configuration process outlined provides a clear roadmap for implementing these methods, ensuring that organizations can establish secure access to their secrets with confidence.
Best practices play a pivotal role in maintaining the integrity of authentication processes. Emphasizing:
- Strong secrets
- Regular rotation
- Implementation of multi-factor authentication
not only mitigates risks but also aligns with industry recommendations for robust security. Additionally, advanced integration strategies, such as dynamic secrets and centralized management, pave the way for streamlined operations and enhanced protection of sensitive data.
In conclusion, HashiCorp Vault stands out as a vital tool for organizations aiming to navigate the complexities of modern security challenges. By adopting its core functionalities and adhering to best practices, organizations can build a resilient infrastructure that effectively safeguards critical data, ultimately fostering trust and security in an increasingly digital landscape.




