Introduction
Cloud computing has revolutionized the way organizations manage their IT ecosystems, offering flexibility, scalability, and cost-effectiveness. Leveraging the internet, businesses can access a wide range of computing resources, from servers to software applications. This transformative approach has led to a cultural shift, decentralizing architectures and promoting resilient systems.
However, as with any technology, there are challenges to overcome, such as data security, compliance, and cost management. In this article, we will explore the key concepts, benefits, challenges, and best practices of cloud infrastructure management, as well as the importance of security and employee training. Join us as we delve into the world of cloud computing and discover how it can drive innovation and improve business outcomes.
Understanding Cloud Computing Concepts
The core of computing represents a transformative approach to the way organizations deploy and manage their IT ecosystems. The core concept involves leveraging the internet to access a suite of computing resources, including but not limited to servers, storage solutions, databases, and various software applications. This model promotes efficiency and agility, allowing businesses to dynamically scale resources in alignment with their evolving needs. At the core of overseeing the cloud, it is important to acknowledge that services are no longer tied to physical hardware, but rather flexible and reachable, similar to books in a public library that are accessible to readers.
To clarify, computing in the sky mirrors the experience of renting a computer at a cybercafe, where the infrastructure is already in place for immediate use. In the same way, services provided through the internet offer users with strong computing capabilities on a pay-as-you-go basis, getting rid of the substantial capital expenditures of conventional IT deployments while introducing a need for careful operational cost management to prevent budgetary overruns.
As companies navigate through the intricacies of cloud implementation, partnerships with experienced service providers have proven invaluable. For example, IFCO Systems benefited from Rackspace Technology's expertise, which provided insightful alternatives and a customer-centric approach during their transition to the 'cloud'. This illustrates the significance of selecting a partner with a robust track record and a profound understanding of the cloud landscape.
Further evidence of computing's expansive reach is witnessed through platforms like Chess.com, which has masterfully leveraged infrastructure to connect a global community of millions of chess enthusiasts, transcending geographical barriers and fostering connections through the beloved game.
In the field of innovation, the rise of generative AI is ready to advance the market's expansion, as mentioned by John Dinsdale from Synergy Research Group. The integration of AI into cloud-based services is anticipated to spur enterprise investment, sustaining the momentum of the market.
A meaningful reflection on the evolution of technology in the sky comes from the Software Engineering Daily podcast, where Oxide's CTO, Bryan Cantrill, emphasized the need for systemic, holistic thinking in the design of data centers. Oxide's development of a 'commercial cloud computer' emphasizes a shift towards merging the benefits of distributed computing with the control of on-premises solutions.
In summary, computing in the sky is a strategic enabler, offering a flexible, scalable, and cost-effective alternative to conventional IT infrastructure. It demonstrates not only a technical change but also a cultural change towards more robust, decentralized architectures, as exemplified by blockchain's commitment to secure, distributed data control without a single point of weakness. As businesses and technology leaders continue to embrace the paradigm of hosting data and applications remotely, it becomes imperative to understand its foundational principles for effective management and future innovation.
Key Components of Cloud Architecture
Implementing a comprehensive infrastructure involves integrating vital elements that collectively support the delivery of resilient and adaptable services. To illustrate, consider a complex scenario where an e-commerce enterprise aims to establish an online portal catering to African consumers. This portal must exhibit minimal latency, secure and swiftly retrievable relational user data, accommodate product images, and maintain high fault tolerance and availability. Achieving these objectives while adhering to a constrained budget requires meticulous planning and execution.
For instance, virtualization is not merely a cost-saving strategy; it is instrumental in creating isolated and flexible computing environments to comply with diverse regulatory demands across different countries. Networking must not only provide low latency connections but also ensure data sovereignty by enabling region-specific deployment. Storage solutions are tasked with swiftly accessing relational databases and handling multimedia content efficiently, while robust security measures safeguard data integrity both at rest and during transmission.
The architecture's design is influenced by the overarching business goals and must be agile enough to incorporate the continual evolution of technology. This means avoiding early commitments to a single provider and instead prioritizing a design that supports multi-strategies. As affirmed by seasoned professionals in the field, these design principles, though not universally applicable, have repeatedly demonstrated their value in distributed systems across both academic and industrial contexts.
Considering industry trends, the growing reliance on artificial intelligence and the adoption of cloud computing are driving a surge in data center utilization. This necessitates architectures that can scale efficiently, with predictions for the data center industry in 2024 indicating a continued emphasis on these capabilities. In the end, the structure must not only fulfill the current operational needs but also be ready to adjust to the fast market changes predicted by organizations like the World Economic Forum, which emphasizes the crucial role of computing in driving the next era of technological progress.
Benefits of Cloud Infrastructure Management
The landscape of infrastructure management is dynamic and crucial for enhancing business operations. Organizations that implement web-based solutions can scale their resources effectively, responding agilely to market demands. This scaling facilitates cost optimization while bolstering operational efficiency. The inherent flexibility of computing empowers employees with ubiquitous access to resources, fostering a collaborative work environment unrestricted by geographical barriers.
Case studies from industry leaders underscore the importance of strategic partnerships in managing cloud services. IFCO Systems, for instance, leveraged Rackspace's expertise to navigate its journey to the skies, benefiting from Rackspace's robust customer focus and deep knowledge pool. Similarly, Sirius Technologies' adoption of a cloud-based platform for Cloud Development Environments led to transformative outcomes in productivity and global collaboration, particularly in the financial services sector.
In the aftermath of unforeseen cost increases, like those encountered by Wowza's customers, the value proposition for managed services in the cloud becomes even more convincing. Companies are increasingly recognizing the need for specialized expertise to deliver high-quality, real-time content to a global audience. A case in point is a customer's shift to Ceeblue's managed services, which validated the advantages of such an approach.
Supporting this narrative, recent news highlights innovative strides in infrastructure, such as Oxide's launch of a commercial computer. This development aims to reconcile the on-premises vs. on-site conundrum, backed by substantial Series A funding to drive adoption. Furthermore, the Software Engineering Daily podcast shed light on the silent operation of Oxide's servers, symbolizing a thoughtful reimagining of data center acoustics.
The economic impact of advanced cloud administration is quantified in reports revealing an average 334% ROI for Infoblox users. This encompasses a 75% surge in operational efficiency and the capacity to operate effectively with a smaller workforce, alongside a 79% reduction in operational costs. These metrics emphasize the strategic importance of managing the cloud in driving innovation and maintaining a competitive edge.
To clarify the essence of computing in the sky, analogies are made to a public library where resources, similar to books, are accessible remotely, eliminating the need for extensive personal collections. This transition from traditional local infrastructure to a model of convenience and efficiency exemplifies the transformative power of online services.
To sum up, while organizations navigate the intricacies of shifting to the cloud, the significance of well-informed choices, strategic alliances, and the adoption of innovative solutions cannot be emphasized enough. The collective experience of industry leaders, supported by impactful statistics and insightful analogies, provides a roadmap for successful cloud integration, ultimately leading to improved business outcomes.
Challenges in Cloud Infrastructure Management
Cloud management is a complex landscape, encompassing numerous advantages and corresponding challenges. Key challenges include safeguarding data security and compliance, managing costs, and maintaining system performance and availability. The experiences of companies like IFCO and Chess.com illustrate the nuances of these challenges. IFCO, with its small IT department, collaborated with Rackspace Technology to utilize their extensive cloud knowledge, enhancing their capability to manage cloud systems. Similarly, Chess.com, with over ten million daily chess games, relies on a strong IT infrastructure, blending public computing and on-premises solutions to ensure smooth performance and global connectivity.
The threats highlighted by the Cloud Security Alliance's report 'Top Threats to Cloud Computing 2024' emphasize the necessity for vigilance and strategic planning. As ecosystems in the sky become more intricate, the attack surface widens, necessitating comprehensive security measures that include vendor and partner networks. With 78% of organizations adopting hybrid and multi-cloud strategies, the significance of a resilient and adaptable cloud infrastructure becomes evident. This includes the ability to contain and recover from incidents with minimal impact, as well as evolving to mitigate future risks.
In this dynamic environment, scalability is paramount. The design, testing, and deployment of software in the sky must be architected with scalability in mind. This foresight guarantees that online services can effectively scale capacity to meet fluctuating demands. Moreover, the complexity of software products today necessitates platforms like Azure to function at their best across various servers, VM types, and operating systems. Optimization algorithms play a critical role in achieving near-optimal solutions within reasonable timeframes and resource constraints.
Understanding the certification programs offered by Cloud Service Providers (CSPs) is also crucial. These programs, which explore the fundamentals of modern continuous delivery methods and system monitoring, emphasize the significance of specialized expertise in handling and transferring data to the sky. Staying informed about the latest developments, such as the intersection of cloud and artificial intelligence, is crucial for effective administration of cloud systems.
Security and Compliance in Cloud Infrastructure
To guarantee the secrecy, reliability, and accessibility of data within cloud environments, it is crucial to establish a thorough protective structure and comply with conformity standards. For instance, the GDPR mandates stringent protocols for data handling within the EU, including data residency, minimization, and storage limitation. Such regulations have a significant impact on data management and require a strategic approach to compliance, regardless of whether the data is stored on-premises or in the sky.
One of the main factors to take into account in the Shared Responsibility Model for safeguarding the network is the division of responsibilities. This structure defines the security responsibilities between service providers and their customers. For instance, while service providers are responsible for securing the underlying infrastructure, customers are accountable for safeguarding their data, managing configurations, and controlling user access.
To strengthen environments, it is recommended to utilize strong Identity and Access Management (IAM) practices that guarantee only essential access is provided to users, as per the principle of least privilege. Furthermore, the deployment of multi-factor authentication (MFA) can greatly enhance safeguarding by authenticating user identities prior to allowing entry to sensitive resources.
Recent advancements in the technology sector demonstrate the importance of strong measures for protecting data in the online environment. Microsoft, for example, has started a transformative cybersecurity approach that utilizes automation and AI to enhance service protection, deal with vulnerabilities more quickly, and strengthen infrastructure against potential threats.
An actual case in the real world highlights the significance of conducting proper investigation in cloud safety, which involved a doubtful AWS support case that was essentially an unauthorized appeal to enhance email service limits for the purpose of spamming. This incident emphasizes the importance for customers to carefully examine and secure their online resources, similar to a property owner making sure their rental's doors and windows are locked, as indicated by the online marketplace comparison for online transactions.
In summary, organizations must acknowledge that preserving a protected online atmosphere is a continual undertaking that necessitates consistent assessment and adjustment of safety approaches. By acknowledging the ever-changing nature of security and compliance in the digital environment, businesses can enhance the protection of their digital assets from evolving cyber threats.
Cost Optimization Strategies
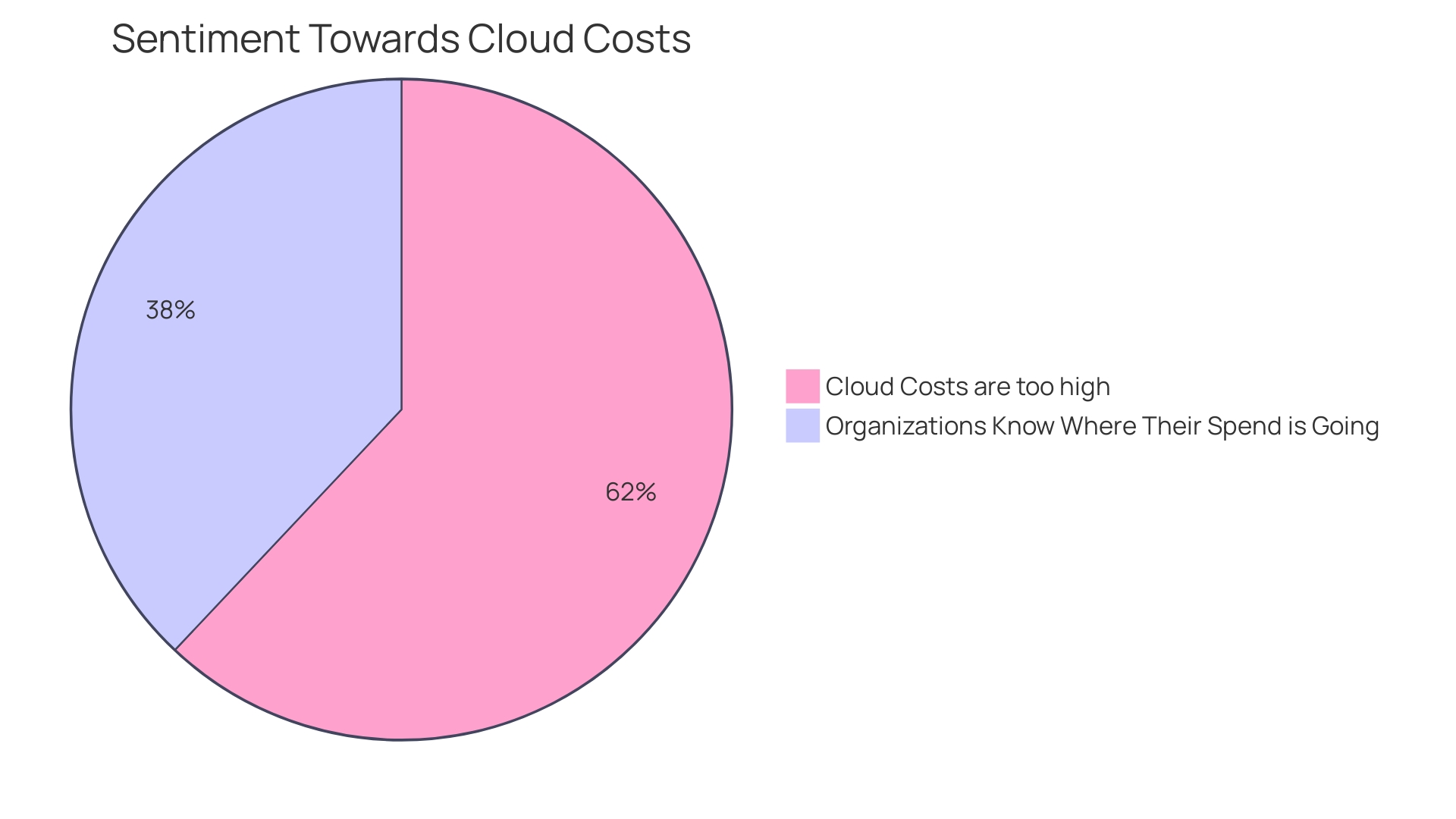
Optimizing cloud infrastructure costs is not just about saving money; it's about enhancing financial and operational efficiency to deliver business outcomes. The Cost Optimization pillar of the Well-Architected Framework emphasizes this by focusing on financial control, resource provisioning, data supervision, and cost monitoring. For instance, enabling AWS's Cost Explorer in the AWS Management Console offers immediate visibility into expenditure, which is crucial for informed decision-making. Moreover, organizations that cooperate across finance and technology departments establish a more integrated approach to cost control. CFOs, financial controllers, and technology leads must collaborate, comprehending the intricacies of cloud consumption and billing to align technology spending with business goals.
Financial management isn't just about tracking costs, but also about understanding the value behind those costs. This includes evaluating IT productivity, business innovation, and the implementation of advanced technologies like generative AI, which has been highlighted as a key area for expanding value. By balancing investments in the cloud with the advantages they offer, companies can strategically plan their migration efforts to the cloud and maximize the return on investment. However, it's essential to recognize that cost optimization is an ongoing process, requiring continuous refinement throughout a workload's lifecycle. Recognizing patterns, such as the typical 'shark's fin' shape in architecture expenses, can indicate the areas where optimization should focus to efficiently handle expenditure.
In light of the State of FinOps 2023 survey, it's clear that cost optimization remains a priority for organizations. However, in the midst of the excitement surrounding AI, the fundamental practices of cost optimization still remain crucial in guaranteeing the financial well-being and achievement of endeavors.
Infrastructure as Code (IaC) for Efficient Management
The notion of Infrastructure as Code (IAC) goes beyond the traditional manual provisioning and management of cloud resources, providing an automated, consistent, and scalable approach. By systematizing the underlying framework, teams can utilize machine-readable scripts to automate the setup and maintenance of their IT systems. This shift not only reduces human error but also facilitates easy version control and rollback capabilities. For example, the shift to IAC by a company in 2017 showcases the change from manual tasks to efficient, standardized scaling with minimal effort, thanks to tools like Terraform.
Furthermore, the implementation of IAC in groundbreaking initiatives, like Bosch's solid oxide fuel cell systems, demonstrates the collaboration between tangible systems and digital administration. Here, a digital twin supports the SOFC by visualizing and optimizing process parameters, demonstrating the long-term value of IaC in managing complex, scalable systems.
The utilization of tools like Pulumi further demonstrates the flexibility of IaC, enabling control over multiple cloud and SaaS products using well-known languages like TypeScript, Python, and Go. This approach not only utilizes current developer abilities but also simplifies the shift from manual to automated systems.
In the context of rapid technological advancement and the need for swift, secure scaling, IAC stands out as an essential practice. A recent global survey underscores its widespread adoption, with significant usage across multiple industries, notably retail & e-commerce, finance & banking, and software. The integration of AI with IAC, termed Generative IAC, is poised to heighten efficiency and innovation, paving the way for AI-driven automation in control.
Considering the advancements in data centers and the viewpoints of the industry in 2023, it's clear that IAC has a vital function in meeting the requirements for swift deployment and administration of IT systems. As businesses face the challenges of the coming years, the strategic implementation of IAC will be integral to maintaining a competitive edge in the fast-paced tech landscape.
Best Practices for Cloud Configuration Management
Efficiently controlling the arrangement of online resources is crucial for companies to guarantee optimal performance within their virtual system. By integrating industry best practices such as version control, utilization of automated configuration management tools, and ongoing monitoring and testing, businesses can achieve consistency, reliability, and superior performance.
A migration strategy, essential for transitioning infrastructure, data, applications, and services to cloud platforms, brings forth benefits like reduced IT costs, increased business agility, improved security, and the opportunity for digital transformation. Nevertheless, the distinctiveness of every organization's journey to the cloud requires a customized strategy, taking into account the specific cost, performance, and complexity of individual IT assets and the appropriateness of workloads for migration.
For instance, IFCO's partnership with Rackspace exemplified the advantages of leveraging expertise in cloud transitions, as they were able to draw on Rackspace's extensive experience with other customers. Similarly, Sirius Technologies' collaboration with Strong Network to manage Cloud Development Environments resulted in enhanced productivity and global collaboration, driving transformation in the financial services industry.
LF Leadership & Optimal Approaches offers a hub for communities to access resources that support open source journey administration. The Linux Foundation's projects promote a deeper comprehension of open source administration, implementation, and contribution, which are crucial in achieving the complete potential of open source within organizations.
Software configuration control (SCC) is an essential discipline that governs changes to software artifacts throughout their lifecycle, as outlined in the Software Engineer Book of Knowledge (SWEBOK). It ensures the integrity of products by managing their configurations, including source code and libraries, and facilitates parallel development processes.
Effective strategies for overseeing cloud infrastructure must prioritize security as a primary consideration. The Director of Cybersecurity at the National Security Agency, Rob Joyce, emphasizes the necessity of proper implementation of cloud technology to prevent becoming an attractive target for adversaries. A comprehensive approach to managing the cloud involves not only ensuring IT efficiency but also safeguarding critical data.
In conclusion, achieving a high return on investment from programs in the cloud requires a balance between investments in cloud technology and the anticipated benefits. This equilibrium can be further modified through the integration of cutting-edge technologies like generative AI, as mentioned in a report examining the real worth of computing across different sectors and regions.
Implementing a Layered Security Approach
In the constantly changing environment of cloud infrastructure management, a strong protection plan is not only advised, it is essential. As we traverse through a world where distributed computing is no longer limited to office spaces but extends across the globe, the requirement for comprehensive protection measures becomes more pronounced. Implementing a multi-layered strategy to safeguarding is a crucial tactic in the defense against a wide range of cyber threats.
The multi-layered protection approach involves an integration of diverse controls including network safety, identity and access management (IAM), encryption, and intrusion detection systems (IDS). The implementation of such controls must be dynamic and adaptable to the changing threat landscape. For instance, the AWS incident that spurred a call for support on a seemingly innocuous Friday afternoon, highlighted the vulnerability of even the most unexpected features like the Simple Email Service (SES) to nefarious exploitation. It was not until an unusual request to increase SES sending limits, a service the client did not use, that an alert was raised.
This incident underscores the importance of continuous vigilance and the adoption of comprehensive protection frameworks like Cisco's Hypershield, which leverages AI to achieve safety outcomes previously unattainable by human efforts alone, as echoed by Cisco Chair and CEO, Chuck Robbins. Similarly, Microsoft's dedication to maintaining a comprehensive inventory across its production systems and retaining security logs for efficient investigation and threat hunting establishes a benchmark for proactive defense mechanisms.
Security Lifecycle Management (SLM) is another key aspect that organizations should embrace. It calls for a zero-trust, identity-based access architecture that is essential for the protection, inspection, and connection of an organization's digital estate. A central system of record for all credentials and secrets, supplemented by secrets rotation and dynamic secrets, can significantly mitigate risks associated with long-lived credentials.
Furthermore, the mutual accountability framework between service providers (CSPs) and clients clarifies the allocation of responsibilities when it comes to safeguarding computing environments. This model ensures that while CSPs like AWS, Azure, or GCP secure the infrastructure, clients must safeguard their data, a concept analogous to the responsibilities shared between an online marketplace, a property owner, and a renter in a vacation rental transaction.
Considering the appealing objective that online services represent for enemies because of the consolidation of crucial data, it is crucial to listen to the fundamental guidance given by Rob Joyce, NSA's Director of Cybersecurity, to prevent being a target. The ongoing threat of data breaches, Dos attacks, and other cyber crimes necessitates a steadfast and sophisticated approach to safeguarding data in the cloud, one that adheres to industry guidelines, regulatory criteria, and ensures compliance with data protection laws.
In conclusion, a layered protection approach is not only crucial but also complex, requiring a combination of advanced technologies, vigilant practices, and a deep understanding of both the capabilities and limitations of cloud-based infrastructures. As we continue to depend on online services for an increasing part of our data storage and management requirements, the complexity and comprehensiveness of our protective measures must develop in parallel to safeguard our most valuable resources.
Educating and Training Employees on Cloud Security
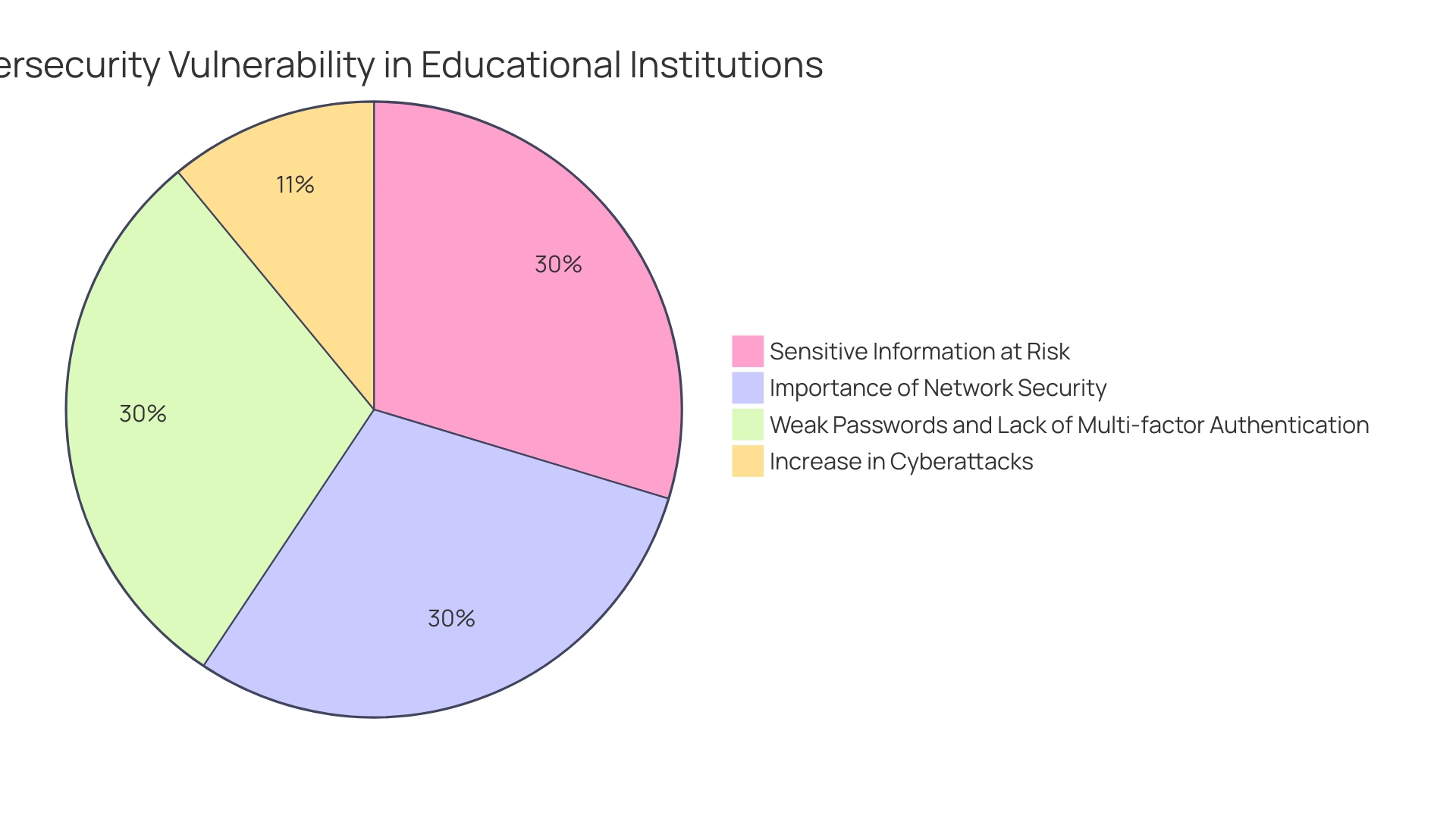
To ensure the future of our students and uphold the integrity of educational institutions, it is crucial that we invest in comprehensive training for all staff to protect against online threats. With schools becoming a prime target for cyberattacks, as highlighted by the rise in ransomware incidents from 56% in 2021 to 80% in 2022, the vulnerability of educational systems is alarmingly evident. The low sophistication of these attacks underscores a pressing need for stronger safeguards akin to those utilized by leading banks and tech companies.
The case of the Savannah-Chatham County Public School System (SCCPSS) illustrates the critical nature of this issue. Despite resource constraints, the dedication to protecting the data of staff and students is paramount. Their approach, which involves utilizing solutions that operate autonomously, showcases the potential to enhance safety while effectively managing resource constraints.
Moreover, adherence to regulations such as FERPA in the US, and global tightening of data privacy due to GDPR, requires educational institutions to implement stringent access controls, especially following the zero-trust model. Educators must understand the principles of data sharing and the heightened risks associated with third-party cloud providers.
To navigate this intricate and constantly changing threat landscape, where three-quarters of professionals acknowledge heightened challenges over the past five years, comprehensive training is essential. Such training empowers staff to recognize and mitigate potential risks, ensuring the secure use of web-based resources. As organizations increasingly adopt hybrid and multi-cloud strategies, with 78% of organizations opting for such approaches in 2024, the significance of cloud protection skills is more pronounced than ever.
In conclusion, through comprehensive training programs, we not only safeguard our educational infrastructure but also foster a culture of security mindfulness that extends beyond the classroom.
Conclusion
In conclusion, cloud computing has revolutionized IT ecosystems by offering flexibility, scalability, and cost-effectiveness. Strategic partnerships with experienced cloud service providers are crucial for successful cloud infrastructure management. Integrating vital elements such as virtualization, networking, and storage solutions is key to implementing a comprehensive cloud infrastructure.
The benefits of cloud infrastructure management include effective resource scaling, increased operational efficiency, and global collaboration. Maintaining a secure cloud environment requires implementing a comprehensive security framework and adhering to compliance standards. Cost optimization strategies enhance financial and operational efficiency, maximizing return on investment.
Infrastructure as Code (IaC) automates and scales cloud infrastructure management, reducing errors and facilitating easy version control. Effective cloud configuration management involves industry best practices. Educating and training employees on cloud security is vital to protect data and maintain the integrity of educational institutions.
In conclusion, informed decisions, strategic partnerships, and innovative solutions are crucial for successful cloud migration and management, driving innovation, enhancing business outcomes, and ensuring the security and efficiency of IT ecosystems.




