Introduction
Securing and optimizing Kubernetes environments is paramount for any organization aiming to maintain robust IT infrastructure and safeguard against potential threats. This article delves into the best practices for Kubernetes security, infrastructure management, scalability, resilience, logging, monitoring, training, and documentation. By exploring essential strategies such as Role-Based Access Control (RBAC), Infrastructure as Code (IaC), Horizontal Pod Autoscaler (HPA), and comprehensive logging solutions, the article provides a holistic approach to managing Kubernetes clusters effectively.
Additionally, it underscores the importance of continuous learning and thorough documentation to ensure teams are well-equipped to handle the dynamic nature of Kubernetes. Through these insights, organizations can enhance their Kubernetes operations, ensuring security, efficiency, and scalability.
Security Best Practices
Securing a container orchestration environment requires a multi-faceted approach to safeguard applications, data, and infrastructure from potential threats. Role-Based Access Control (RBAC) is essential for enforcing least privilege policies, ensuring users and applications possess only the necessary permissions. This is similar to a system in a busy office where employees can reach only pertinent areas, thus reducing risk factors.
Regular updates and patches to container orchestration components are vital to address vulnerabilities swiftly. This proactive measure, as emphasized in the research on Kubernetes protection, helps maintain the integrity of the cluster against emerging threats.
'Network policies play a crucial role in controlling traffic flow and segmentation, enhancing the overall defense posture.'. By meticulously managing the network, one can significantly reduce the attack surface, making it harder for unauthorized entities to exploit vulnerabilities.
Incorporating tools such as Open Policy Agent (OPA) for policy management can offer an extra level of protection. OPA aids in the development and implementation of detailed regulations, guaranteeing that protective measures are uniformly enforced throughout the network. Additionally, maintaining comprehensive audit logs is critical for tracking access and changes, offering transparency and accountability.
The intricacy of orchestration systems, made up of diverse elements and services, requires a comprehensive perspective on security. By applying these best practices, organizations can effectively reduce risks and safeguard their container orchestration environments from unauthorized access and data breaches.
Infrastructure Configuration and Management
Efficient management of systems is crucial for optimizing Kubernetes clusters. Leveraging Infrastructure as Code (IAC) tools like Terraform and Ansible can automate and version control configurations, significantly enhancing consistency and enabling rapid recovery from failures. By managing systems with the same rigor as application code, IAC minimizes human error and guarantees reproducibility. For instance, Terraform's declarative approach, which outlines the desired condition of the system, facilitates seamless scaling and management across various environments. Regular audits of configurations are crucial to maintain compliance with best practices and ensure all nodes are correctly configured, minimizing the risk of discrepancies that could lead to downtime. Terraform's versatility in managing both cloud and on-premises environments underscores its value in a robust IAC strategy.
Scalability and Resilience
The system is designed to enable scalability and resilience, crucial for sustaining a strong IT framework. Implement the Horizontal Pod Autoscaler (HPA) to dynamically adjust pod replicas based on resource usage, ensuring smooth and efficient operations. For minimal downtime during updates, utilize rolling updates and blue-green deployments. Persistent storage solutions should also be leveraged to dynamically adapt to workload variations and guarantee data availability during failures.
A practical example of effective Kubernetes implementation can be seen in Chess.com, which hosts over ten million chess games daily and supports a community of more than 150 million users. 'James Kelty, Head of Operations at Chess.com, emphasizes the importance of a stable IT system, incorporating public cloud, on-premises solutions, and essential connections.'. This comprehensive approach has enabled Chess.com to scale its operations and cater to a global audience seamlessly.
Scaling strategies and methodologies should be carefully chosen to meet specific structural needs, much like expanding a house to accommodate a growing family. This involves a balance of the right architecture, database solutions, and tools to ensure that the application not only supports current demands but is also prepared for future growth.
In essence, scalability in this system is about managing growth smartly and sustainably, ensuring that your infrastructure can handle increased loads gracefully while maintaining optimal performance.
Logging and Monitoring
Implementing comprehensive logging and monitoring is crucial for maintaining the health and performance of Kubernetes environments. Start by instrumenting your applications, embedding tracing, logging, and metrics functionalities directly into your code. This foundational step helps generate the necessary metrics to identify performance bottlenecks and issues.
For monitoring, tools like Prometheus offer powerful capabilities to track various metrics of the system, while Grafana provides robust visualization to make sense of this data. Together, they form a solid base for real-time insights into cluster performance. Enhance this setup with OpenTelemetry to achieve end-to-end observability, connecting different system parts to get a holistic view of performance.
On the logging front, use centralized logging solutions such as Fluentd or the ELK stack (Elasticsearch, Logstash, Kibana). These tools collect, process, and visualize logs efficiently, enabling quick troubleshooting and in-depth performance analysis. Structured logs (e.g., JSON or XML) are particularly beneficial as they can be parsed and correlated programmatically, enhancing their utility in monitoring and analysis tools.
Set up alerts for critical thresholds to proactively address potential issues before they impact service availability. This proactive approach ensures that you can maintain high service levels and respond swiftly to any anomalies. As Kelsey Hightower observes, the maturity of cloud-native projects highlights the significance of stability and standardized protocols, making robust observability practices essential for contemporary infrastructure management.
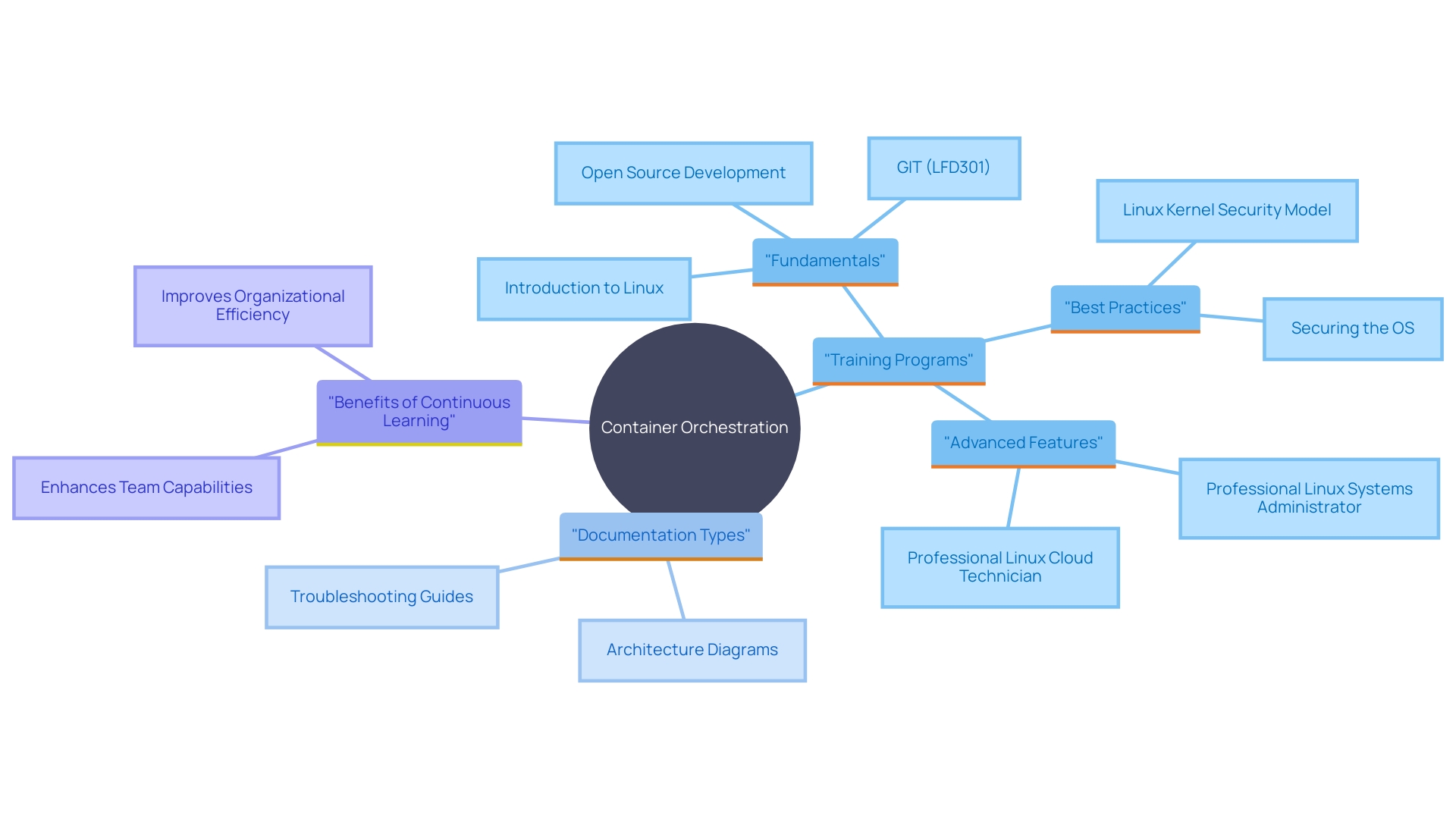
Training and Documentation
Ensuring long-term success with container orchestration requires a robust investment in training and thorough documentation. Creating a structured training program that includes container orchestration fundamentals, best practices, and advanced features is crucial. This approach not only equips teams with essential skills but also fosters a deeper understanding of the platform's capabilities and limitations. A comprehensive training course, akin to those observed in Linux and Open Source Development, can offer valuable insights into securing the container orchestration environment and managing complex deployments.
Equally important is maintaining detailed and accessible documentation. 'This should include architecture diagrams, deployment processes, and troubleshooting guides, ensuring that teams can efficiently manage and scale their container orchestration infrastructure.'. As noted in various industry reports, having quick access to accurate information significantly reduces downtime and enhances productivity. The Kubernetes ecosystem is constantly evolving, making it vital for teams to stay updated with the latest changes and best practices. By investing in continuous learning and up-to-date documentation, organizations can empower their teams to adapt swiftly to new technologies and maintain a competitive edge.
Conclusion
Securing and optimizing Kubernetes environments requires a multifaceted strategy. Role-Based Access Control (RBAC) is essential for enforcing strict permission protocols, while regular updates and effective network policies enhance security. Tools like Open Policy Agent (OPA) and comprehensive audit logging further strengthen accountability.
Infrastructure management benefits from Infrastructure as Code (IaC) tools like Terraform and Ansible, which automate configurations and reduce human error. Regular audits are necessary to maintain compliance and operational integrity.
Kubernetes is designed for scalability and resilience, facilitated by mechanisms such as the Horizontal Pod Autoscaler (HPA) and rolling updates. These strategies allow organizations to adapt to growing demands without sacrificing performance, as demonstrated by successful implementations in companies like Chess.com.
Effective logging and monitoring are critical for maintaining cluster health. Integrating tools like Prometheus and Grafana, along with centralized logging solutions, provides real-time insights and enables swift troubleshooting. Proactive alerting mechanisms help address potential issues before they impact operations.
Lastly, investing in training and documentation is vital for long-term success. A structured training program, combined with comprehensive documentation, equips teams to navigate Kubernetes complexities effectively. Continuous learning ensures organizations can adapt to evolving challenges.
In conclusion, a holistic approach to Kubernetes security, infrastructure management, scalability, logging, and team training is essential for maximizing the platform's potential. Implementing these best practices enhances operational efficiency and fortifies defenses against threats, leading to a more resilient IT infrastructure.




