Introduction
In an increasingly digital landscape, the security of business operations hinges upon the establishment of robust IT policies. These policies not only serve as a framework for protecting sensitive data but also ensure compliance with regulatory standards and foster a culture of security awareness within organizations.
As cyber threats continue to evolve, the imperative for businesses to implement and regularly update comprehensive IT policies has never been more critical. This article delves into the significance of IT policies, outlines essential policies every organization should adopt, and provides a structured approach to developing and maintaining these vital guidelines.
By prioritizing IT policy implementation, businesses can safeguard their assets and enhance operational efficiency in a rapidly changing technological environment.
Understanding the Importance of IT Policies for Business Security
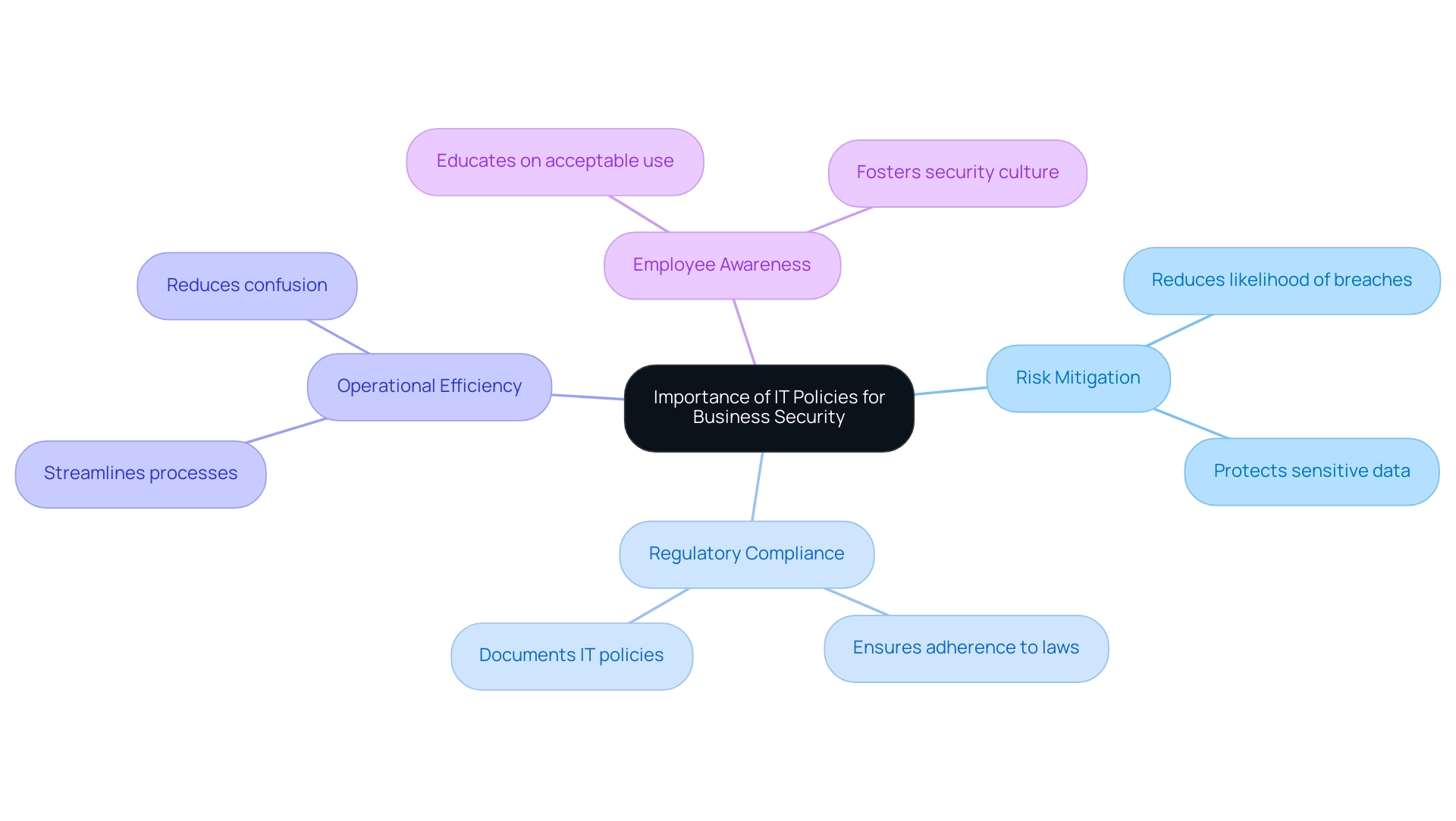
IT guidelines act as the foundation of a safe corporate environment. They define the rules and guidelines for technology use within an organization, which are included in the list of IT policies, helping to protect sensitive data and maintain compliance with legal standards. Key reasons for implementing IT guidelines include:
- Risk Mitigation: Establishing clear protocols reduces the likelihood of security breaches and data loss.
- Regulatory Compliance: Many industries face strict regulations that necessitate a documented list of IT policies.
- Operational Efficiency: Well-defined guidelines streamline processes, reduce confusion, and ensure consistent technology usage across the organization.
- Employee Awareness: Guidelines educate employees about acceptable use and security practices, fostering a culture of security awareness.
By understanding these fundamentals, organizations can appreciate the necessity of robust IT guidelines to safeguard their operations.
Key IT Policies Every Business Should Implement
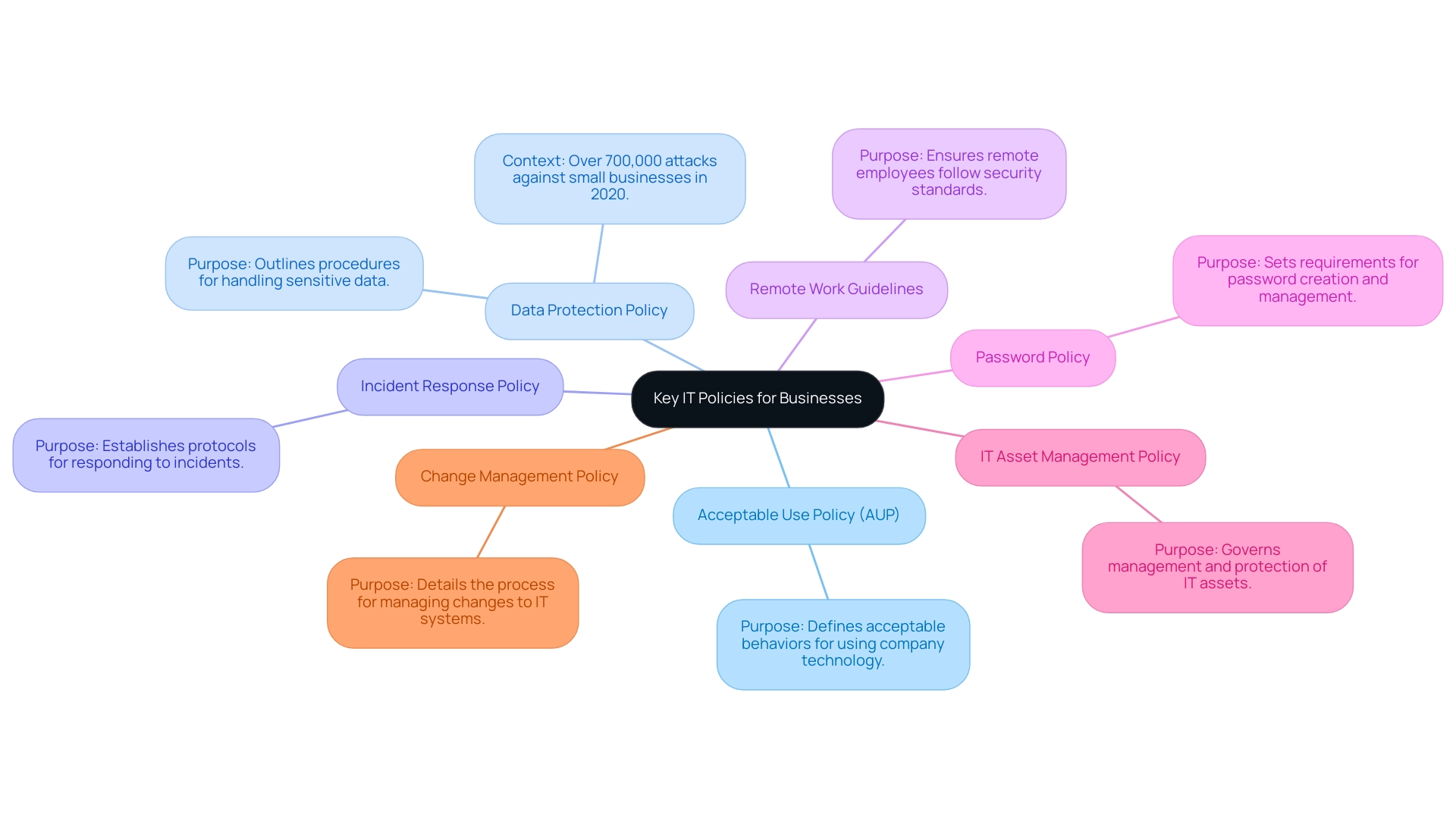
Implementing strong IT regulations is essential for safeguarding business operations and ensuring data integrity. Here are key IT policies that every organization should consider:
-
Acceptable Use Policy (AUP): This policy delineates acceptable behaviors for utilizing company technology and resources, fostering a secure digital environment.
-
Data Protection Policy: This outlines the procedures for handling sensitive data, ensuring compliance with data protection laws. Considering that over 700,000 attacks were reported against small enterprises in 2020, resulting in $2.8 billion in damages, effective data management is critical. As Komron Rahmonbek, SEO Manager, stated, "In 2020 alone, there were over 700,000 attacks against small businesses, totaling $2.8 billion in damages."
-
Incident Response Policy: Establishes clear protocols for responding to incidents. This minimizes damage and aids in the swift restoration of operations, which is vital in today’s threat landscape.
-
Remote Work Guidelines: As the trend of remote work continues to rise, these measures address necessary precautions and instructions, ensuring that remote employees follow the same standards as in-office staff.
-
Password Policy: This sets stringent requirements for password creation and management, reinforcing security practices to protect against unauthorized access.
-
IT Asset Management Policy: Governs the management and protection of IT assets throughout their lifecycle, ensuring accountability and minimizing risks associated with asset misuse.
-
Change Management Policy: Details the structured process for managing changes to IT systems, aimed at minimizing disruptions and associated risks.
Executing these guidelines not only establishes a framework for securing organizational operations but also corresponds with the 64% of respondents who believe the primary purpose of AI is to assist, enhance, and empower consumers. Furthermore, in 2021, 22% of small enterprises increased their cybersecurity spending while 67% maintained their spending levels from 2020, illustrating a mixed response to the evolving cybersecurity landscape. By creating a list of IT policies, entities can enhance adherence to acceptable use standards and strengthen their overall security stance.
Furthermore, with 74% of business owners anticipating AI to produce replies to customers, like chatbots, the significance of these guidelines in an increasingly technological environment cannot be overstated.
How to Develop and Implement Effective IT Policies
To create and execute efficient IT guidelines, companies should follow the subsequent organized method:
-
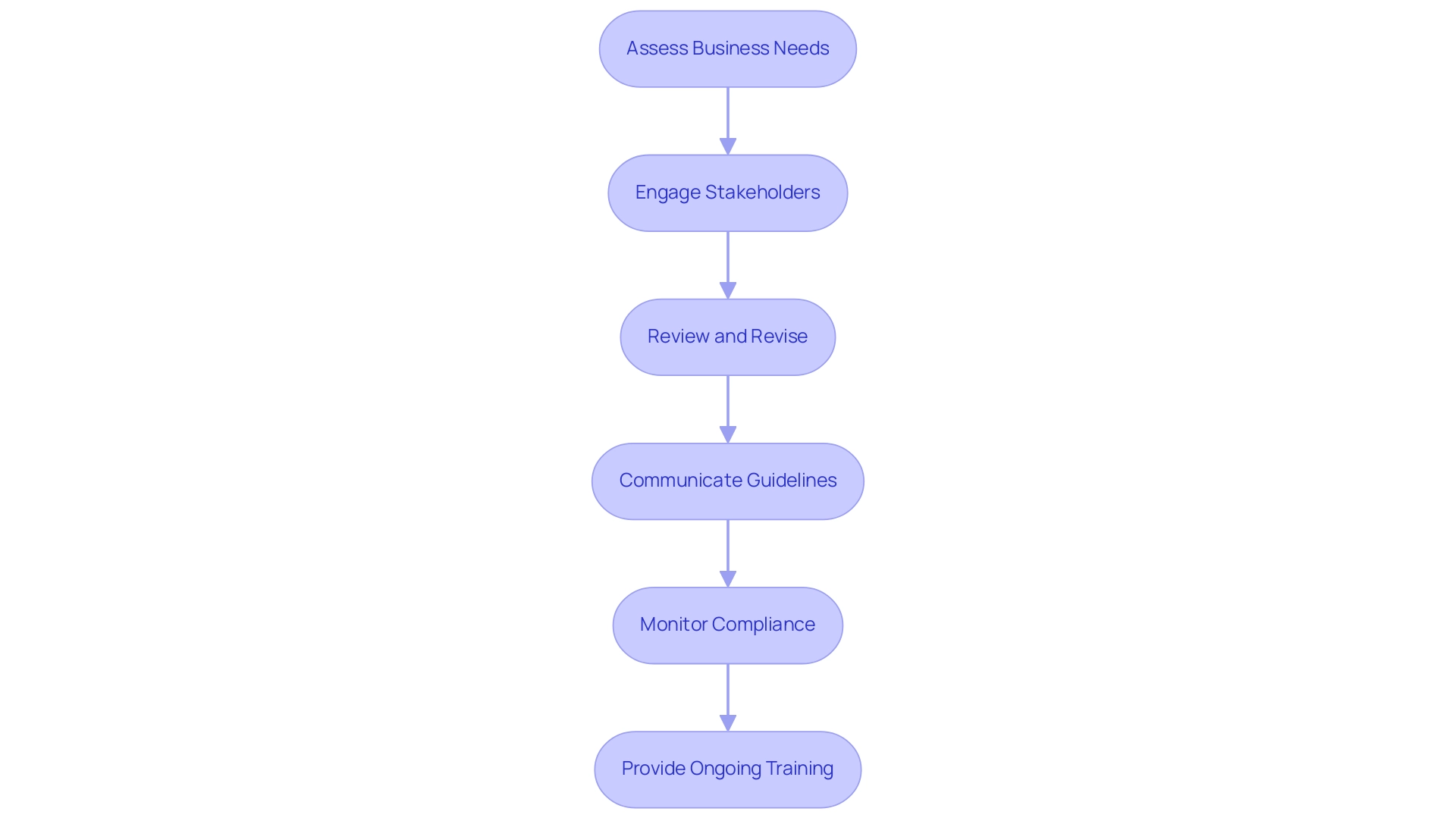
Assess Business Needs: Conduct a thorough evaluation of the specific technology requirements and potential risks that your entity faces. Grasping these factors is essential to customizing strategies that effectively reduce risks. As emphasized by the fact that over fifty percent of U.S. adults indicate involvement in gun violence-related incidents, organizations must acknowledge the wider implications of their practices on community safety and engagement.
-
Engage Stakeholders: Actively involve key stakeholders from across various departments in the development process. This collaborative approach is crucial, particularly considering the need for fair strategies in implementation, as highlighted in recent discussions on gun violence prevention. Involving historically marginalized groups ensures that the strategies not only meet operational needs but also cultivate a sense of ownership and commitment among all parties involved. Draft a list of IT policies that includes clear and concise guidelines which are straightforward and devoid of ambiguous language. Utilizing plain language is essential to enhance comprehension and adherence among all employees. This clarity is especially crucial in situations where the regulations may directly affect community safety.
-
Review and Revise: Gather feedback from stakeholders and use it to refine draft proposals. This iterative process promotes clarity and effectiveness, ensuring that the final guidelines resonate well with all relevant parties. The case study on exposure to gun violence illustrates how feedback from diverse groups can lead to more effective and inclusive policies.
-
Communicate Guidelines: Implement a comprehensive rollout strategy for the guidelines through various channels, including training sessions, internal communications, and documentation. Effective communication is essential for ensuring that all employees are informed and comprehend the guidelines. As one quote states, 'More than half of all adults in the U.S. report that they, or a family member have been involved in a gun violence-related incident,' emphasizing the importance of clear communication in sensitive areas.
-
Monitor Compliance: Create robust mechanisms to oversee adherence to the regulations in place. Promptly addressing any violations is essential to maintaining the integrity of the guidelines and ensuring continued compliance.
-
Provide Ongoing Training: Offer regular training sessions for employees, particularly when guidelines are updated or new technologies are introduced. Ongoing education is essential to strengthen comprehension and guarantee that personnel are prepared to adhere to the latest standards.
By implementing these actions, organizations can establish a robust framework that not only improves safety and compliance but also fosters a culture of responsibility and adaptability to changing technological requirements, all while taking into account the wider social context of their guidelines.
The Importance of Regularly Reviewing and Updating IT Policies
Regularly reviewing and updating IT guidelines is crucial for several compelling reasons:
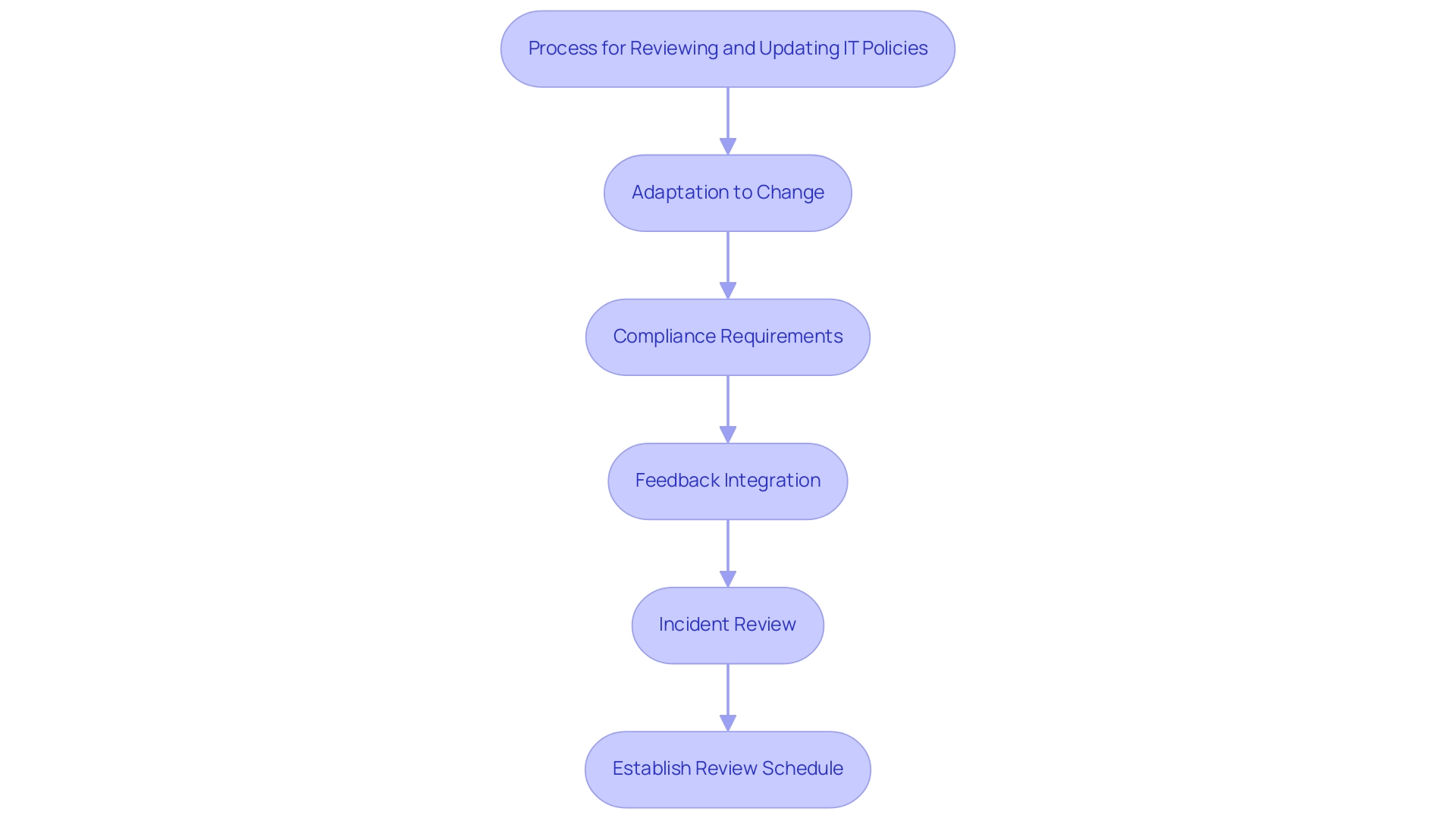
- Adaptation to Change: The rapid evolution of technology and emerging security threats necessitate that regulations reflect current best practices and technologies to safeguard organizational assets effectively. As John E. Lee, program manager at the Genetic Counseling Clinic at Cedars-Sinai, observes, 'Currently these tests are restricted,' emphasizing the necessity for ongoing adjustments in diverse areas, including IT.
- Compliance Requirements: As regulatory environments experience constant transformation, it is crucial to revise the list of IT policies to ensure compliance and minimize the risk of penalties. Data indicate that entities that proactively revise their list of IT policies can considerably improve compliance rates, highlighting the significance of staying ahead of regulatory shifts.
- Feedback Integration: Seeking input from staff is vital, as it can uncover possible areas for enhancement within current protocols. Involving employees in the evaluation process encourages a culture of openness and responsibility.
- Incident Review: After any safety incidents, a comprehensive examination of relevant guidelines is essential to determine modifications that can avert similar events in the future. Learning from past incidents can strengthen the organization’s overall security posture. This reflects the insights from the case study on genetic testing, where the author recognizes the need for improved support and counseling for individuals receiving potentially life-altering results, highlighting the importance of accurate and supportive implementation of guidelines.
To facilitate this process, establish a regular review schedule—whether annually or bi-annually—to assess practices and implement necessary updates. Involve key stakeholders in these discussions to ensure that the list of IT policies aligns with business objectives and adheres to industry standards.
Conclusion
Establishing robust IT policies is essential for businesses navigating the complexities of the digital landscape. These policies not only safeguard sensitive data but also ensure compliance with regulatory standards, mitigate risks, and foster a culture of security awareness among employees. The implementation of key policies—such as Acceptable Use, Data Protection, Incident Response, and others—provides a comprehensive framework that enhances operational efficiency and aligns with the evolving cybersecurity landscape.
Moreover, developing and maintaining effective IT policies requires a structured approach that includes:
- Assessing business needs
- Engaging stakeholders
- Ensuring clear communication
Regular reviews and updates are equally vital, allowing organizations to adapt to technological advancements and emerging threats while integrating valuable feedback from staff. This proactive stance not only strengthens the organization’s security posture but also promotes a culture of accountability and responsiveness.
In summary, prioritizing the establishment and refinement of IT policies is not merely a best practice; it is a critical investment in the future security and integrity of business operations. By committing to these guidelines, organizations can navigate the ever-changing technological environment with confidence, safeguarding their assets and ensuring sustained compliance in a world where cyber threats are increasingly prevalent.




