Introduction
In an age where digital communication is integral to both personal and professional interactions, the vulnerabilities associated with email security have become increasingly alarming. Cybercriminals are employing sophisticated tactics to exploit unsuspecting users, particularly through phishing schemes that can compromise mobile devices and sensitive information. As statistics reveal a significant rise in email-related attacks, understanding the risks and implementing robust security measures is paramount.
This article delves into the various threats posed by email, outlines essential strategies for safeguarding mobile devices, and highlights the importance of utilizing secure email services to protect against evolving cyber threats. By equipping oneself with knowledge and proactive defense mechanisms, individuals and organizations can fortify their defenses in the face of an ever-changing digital landscape.
Understanding the Risks: How Email Can Compromise Your Phone
Email remains a primary attack vector for compromising mobile devices, with hackers frequently deploying sophisticated phishing tactics. These assaults frequently include messages crafted to seem authentic, luring users to click on harmful links or download dangerous attachments. For instance, a frequent tactic includes sending seemingly reliable messages from recognized services, encouraging recipients to provide sensitive information or install malware.
A critical vulnerability, such as StrandHogg, highlights the risks associated with mobile technology, allowing malicious apps to masquerade as legitimate ones. Furthermore, even legitimate apps linked to compromised email accounts can become conduits for unauthorized access. The integration of IoT devices and the misuse of AI and machine learning are anticipated to escalate the complexity of these attack vectors, underscoring the necessity for proactive defense strategies and real-time threat intelligence.
One notable case study is Angler fraud, a relatively new and insidious attack vector that leverages social media interactions. Scammers exploit customer complaints directed at organizations, hijacking responses to trick individuals into divulging personal information. As Prorganiq aptly states, 'It’s alarming to see how sophisticated these scams have become, especially the targeted nature of spear attacks and the cunning use of social media in angler schemes.'
It is vital to observe that data from 2024 show that electronic scams have risen by 30% in comparison to the prior year, with mobile gadgets being the main focus in 65% of these occurrences. Recognizing these risks is crucial in safeguarding mobile devices from email-related threats. A thorough comprehension of phishing strategies and social engineering techniques, combined with advanced protective measures, is crucial for preventing unauthorized access and ensuring strong communication protection.
Essential Steps to Safeguard Your Phone from Email Hacks
To safeguard your phone from email hacks, implement these critical measures:
-
Enable Two-Factor Authentication (2FA): Implementing 2FA on your messaging accounts significantly improves protection. This feature requires a verification code in addition to your password, making unauthorized access much more difficult. Cybersecurity experts emphasize 2FA as one of the most effective strategies to prevent hacks.
-
Use Strong Passwords: Create complex passwords that incorporate a mix of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information such as birthdays or common words. According to a recent study, 81% of data breaches are caused by weak or stolen passwords. Password management tools, as shown in a case study on password management tools, can aid in creating and storing strong passwords, ensuring both protection and accessibility.
-
Be Cautious with Links and Attachments: Exercise caution when dealing with links and attachments from unknown senders. Always verify the sender’s email address and be alert for signs of phishing. Clicking on malicious links or downloading harmful attachments can lead to significant privacy breaches.
-
Regularly Update Your Software: Ensure your phone's operating system and applications are consistently updated to the latest versions. Software updates often contain patches that address vulnerabilities and safeguard against emerging threats.
-
Install a Reputable Protection App: Utilize a trusted mobile protection application that offers features like anti-phishing protection and malware scanning. These apps can significantly bolster your phone’s defenses against various cyber threats.
-
Educate Yourself on Online Scams: Stay informed about the latest phishing tactics and online scams. Awareness and education are essential for recognizing and avoiding attempts to compromise your phone's protection. As former FBI Special Agent John Iannarelli emphasizes, "Staying informed is the best defense against becoming a victim in the cyber world."
By adopting these practices, you can greatly reduce the risk of your phone being hacked through messages, ensuring a more secure digital environment.
Regularly Monitor Your Email Account Activity
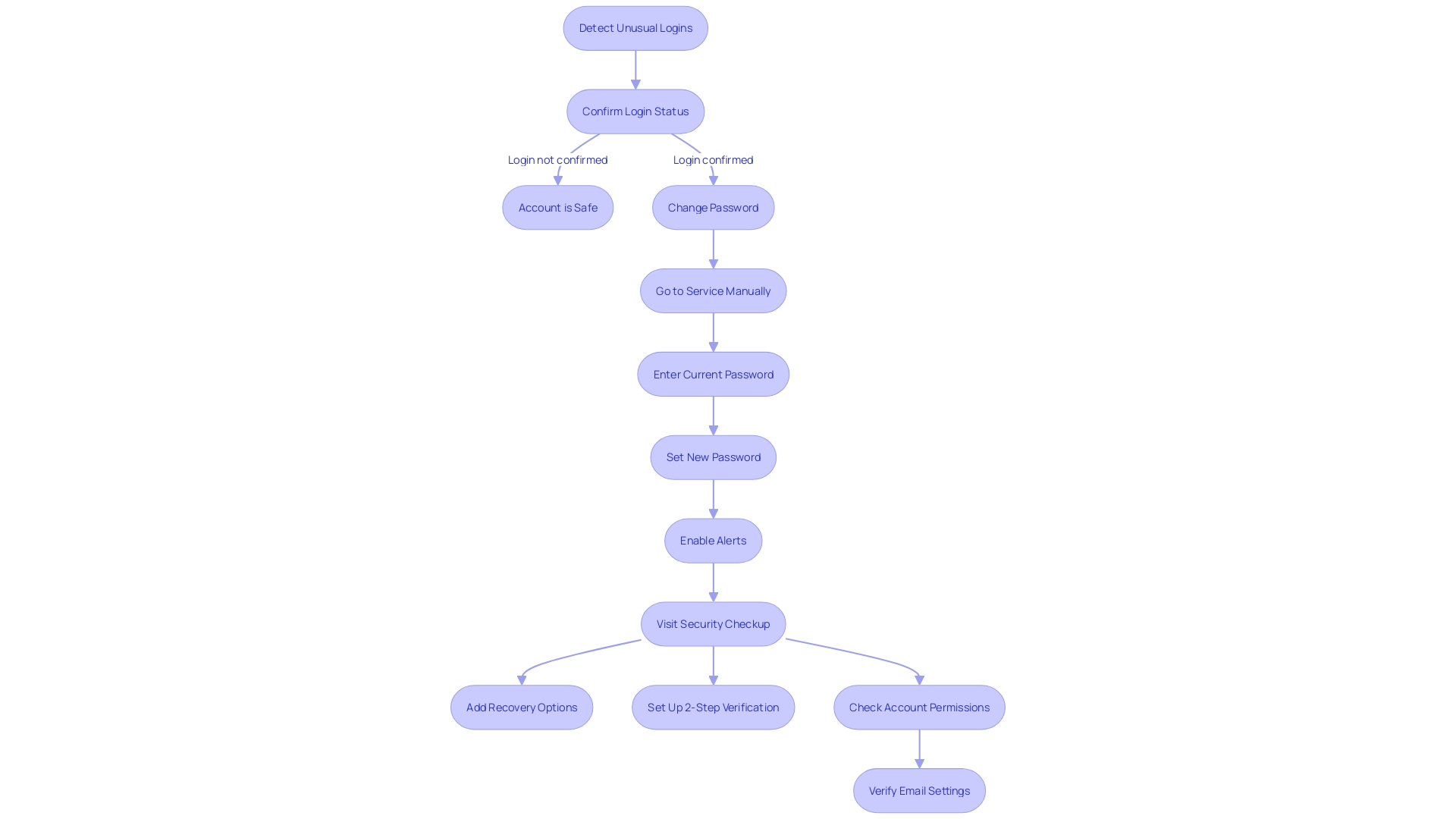
Maintaining vigilance over your messaging account is crucial for security. Regularly checking for any unusual activity, such as login attempts from unfamiliar gadgets or locations, is essential. Recent reports indicate that approximately 60% of breaches are detected through unusual account activity alerts, highlighting the importance of this practice. Most communication services provide a dedicated security section where you can examine recent sign-ins and linked equipment.
Cybersecurity professionals advise taking immediate action if you notice any suspicious activity, such as logins from unrecognized locations. For instance, in a case study involving a mid-sized firm, unauthorized logins from a foreign IP address prompted a swift password change, successfully averting a potential breach. In such cases, change your password immediately and scrutinize your recent emails for any signs of unauthorized messages. Real-world examples demonstrate that prompt responses to these alerts can prevent further breaches and mitigate potential damage.
Additionally, it’s advisable to set up alerts for unusual activities, such as account logins from new devices. This proactive measure ensures you remain informed of any activities that may indicate a breach of safety. Experts emphasize that such monitoring is not only a preventive measure but a critical component of a strong protection strategy. By routinely monitoring your account and establishing notifications, you can greatly improve your communication protection stance and safeguard confidential information.
Utilizing Secure Email Services
When protecting your communications, selecting services that emphasize safety and privacy, like ProtonMail or Tutanota, is crucial. These platforms utilize advanced end-to-end encryption, ensuring that only you and your intended recipient can access the content of your messages.
ProtonMail is a leading option for individuals looking for a secure messaging service that integrates smoothly with a wider range of privacy and protection products. Famous for its strong encryption and easy-to-use interface, it keeps drawing users who prioritize safety. In contrast, Tutanota provides superior value, especially through its proprietary encryption that protects both message contents and subject lines. With features like self-destructing messages and anonymous sign-ups, Tutanota ensures comprehensive protection for your communications.
Moreover, Tutanota is creating desktop clients for Windows, Linux, and Mac OS, which will support offline mode and include advanced features like conversation view and message import, significantly enhancing usability and security.
Case studies have consistently highlighted Tutanota as a superior alternative to ProtonMail, owing to its extensive features, stronger privacy protections, and commitment to sustainability. This has led to recommendations for Tutanota as the most secure messaging service on the market, appealing to both private and business users.
Switching to a secure messaging service like ProtonMail or Tutanota can significantly reduce the risk of your communications being compromised, thus safeguarding your organization from potential messaging-based threats. Recent statistics indicate a 30% growth in the adoption of end-to-end encryption in messaging services over the past year, reflecting the increasing awareness and necessity of robust communication security in 2024. Such advancements in email encryption technologies underscore the critical benefits of adopting these secure services to safeguard your digital communications.
Conclusion
Email security is an increasingly vital concern in the modern digital landscape, particularly as mobile devices become primary targets for cybercriminals. The article outlines the multifaceted risks associated with email, including sophisticated phishing tactics and vulnerabilities that can lead to unauthorized access. With statistics showing a significant rise in email-related attacks, it is imperative for both individuals and organizations to be acutely aware of these threats and to take proactive measures to mitigate them.
To safeguard mobile devices against email hacks, implementing essential strategies such as enabling two-factor authentication, utilizing strong passwords, and being cautious with links and attachments is crucial. Additionally, regular software updates and the installation of reputable security applications can greatly enhance defenses against emerging threats. Monitoring email account activity allows users to detect unusual behavior promptly, which is a key component of maintaining robust security.
Furthermore, transitioning to secure email services like ProtonMail or Tutanota provides an added layer of protection through advanced encryption methods. These services not only safeguard communications but also reflect a growing awareness of the importance of privacy and security in email interactions. By adopting these practices and utilizing secure platforms, individuals and organizations can effectively fortify their defenses against the evolving landscape of cyber threats.
In conclusion, the need for vigilance and proactive security measures cannot be overstated. As cyber threats continue to grow in sophistication, taking the necessary steps to protect sensitive information is essential. By prioritizing email security and remaining informed about potential risks, users can significantly reduce their vulnerability and contribute to a safer digital environment.




