Introduction
In an age where cyber threats loom larger than ever, organizations must prioritize their cybersecurity strategies to safeguard sensitive information and maintain operational integrity.
The CIS Top 18 Controls, developed by the Center for Internet Security, offer a comprehensive framework designed to assist organizations in fortifying their defenses against the most prevalent cyber risks.
This article delves into the significance of these controls, providing a detailed guide on their implementation, assessment of organizational readiness, and the ongoing monitoring necessary to measure effectiveness.
By embracing these best practices, organizations can enhance their security posture, ensuring resilience in an increasingly complex digital landscape.
Understanding the CIS Top 18 Controls: An Overview
The collection of best practices known as the CIS Top 18 Controls is aimed at assisting entities in enhancing their cybersecurity posture. Created by the Center for Internet Security (CIS), the CIS Top 18 Controls provide a prioritized framework to reduce the most prevalent cyber threats. Grasping these regulations is vital for companies aiming to improve their protective measures.
The measures encompass various domains, including:
- Inventory oversight
- Access regulation
- Continuous vulnerability management
- Incident response
Each measure is aimed at addressing specific safety challenges. By applying these measures in line with the CIS Top 18 Controls, entities can greatly lessen their risk of breaches and enhance their overall resilience against cyber dangers.
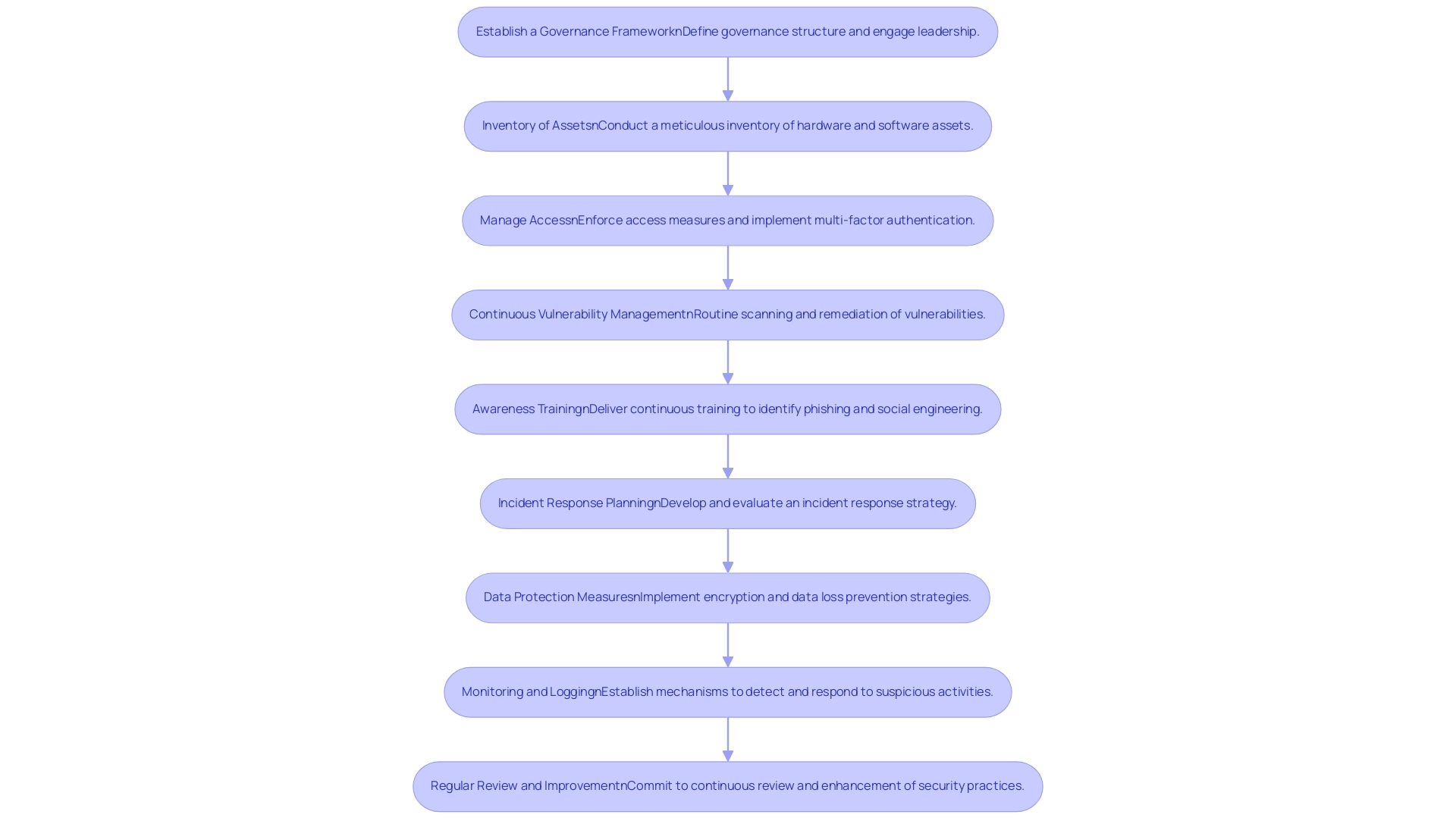
Step-by-Step Implementation of the CIS Top 18 Controls
-
Establish a Governance Framework: Initiate the process by defining a comprehensive governance structure that clearly delineates roles and responsibilities concerning cybersecurity. Engaging leadership is essential; their support will enable the effective execution of the CIS measures, ensuring alignment with organizational objectives. As emphasized in a recent case study, the Balanced Scorecard model connected essential security measures from the CIS, showcasing its effectiveness for overseeing and managing security protocols in entities utilizing information technologies.
-
Inventory of Assets: Conduct a meticulous inventory of all hardware and software assets within the organization. This process should prioritize the identification of critical assets that necessitate protection, as a well-defined asset inventory is essential in understanding what needs safeguarding.
-
Manage Access: Enforce rigorous access measures to ensure that only authorized personnel can access sensitive data and systems. Implementing multi-factor authentication is highly recommended to enhance protection further.
-
Continuous Vulnerability Management: Establish a routine for scanning vulnerabilities in systems and applications. Prioritize the remediation of known vulnerabilities based on a thorough risk assessment, which will fortify your defenses against potential threats. Implementing CIS controls effectively has demonstrated significant results, with entities achieving a score of 98.26% after enabling additional CIS Group Policy settings.
-
Awareness Training: Create and deliver continuous awareness training for employees, enabling them to identify phishing attempts and other social engineering methods. This training is essential for promoting a culture of safety within the establishment.
-
Incident Response Planning: Develop and consistently evaluate an incident response strategy to ensure your organization is well-prepared to react effectively to breaches. This plan should encompass clear communication protocols and recovery procedures to minimize impact.
-
Data Protection Measures: Implement robust data protection measures, including encryption and data loss prevention strategies, to safeguard sensitive information from unauthorized access and breaches.
-
Monitoring and Logging: Establish comprehensive monitoring and logging mechanisms to detect and respond to suspicious activities in real-time. This proactive approach is essential for maintaining awareness of potential threats.
-
Regular Review and Improvement: Commit to the continuous review and enhancement of your security practices and controls in response to evolving threats and vulnerabilities. This adaptability is vital for ensuring that your cybersecurity posture remains resilient in a dynamic landscape. As William Rogelio Marchand Niño stated, "Como resultado del estudio se formula un modelo de Cuadro de Mando Integral que vincula a los controles criticos de seguridad del CIS, soportado además por un aplicativo de ofimatica como una herramienta preliminar que facilite la presentación de resultados."
By adhering to these steps, entities can systematically implement the CIS top 18 controls, thereby significantly enhancing their cybersecurity framework and mitigating the risk of cyber incidents.
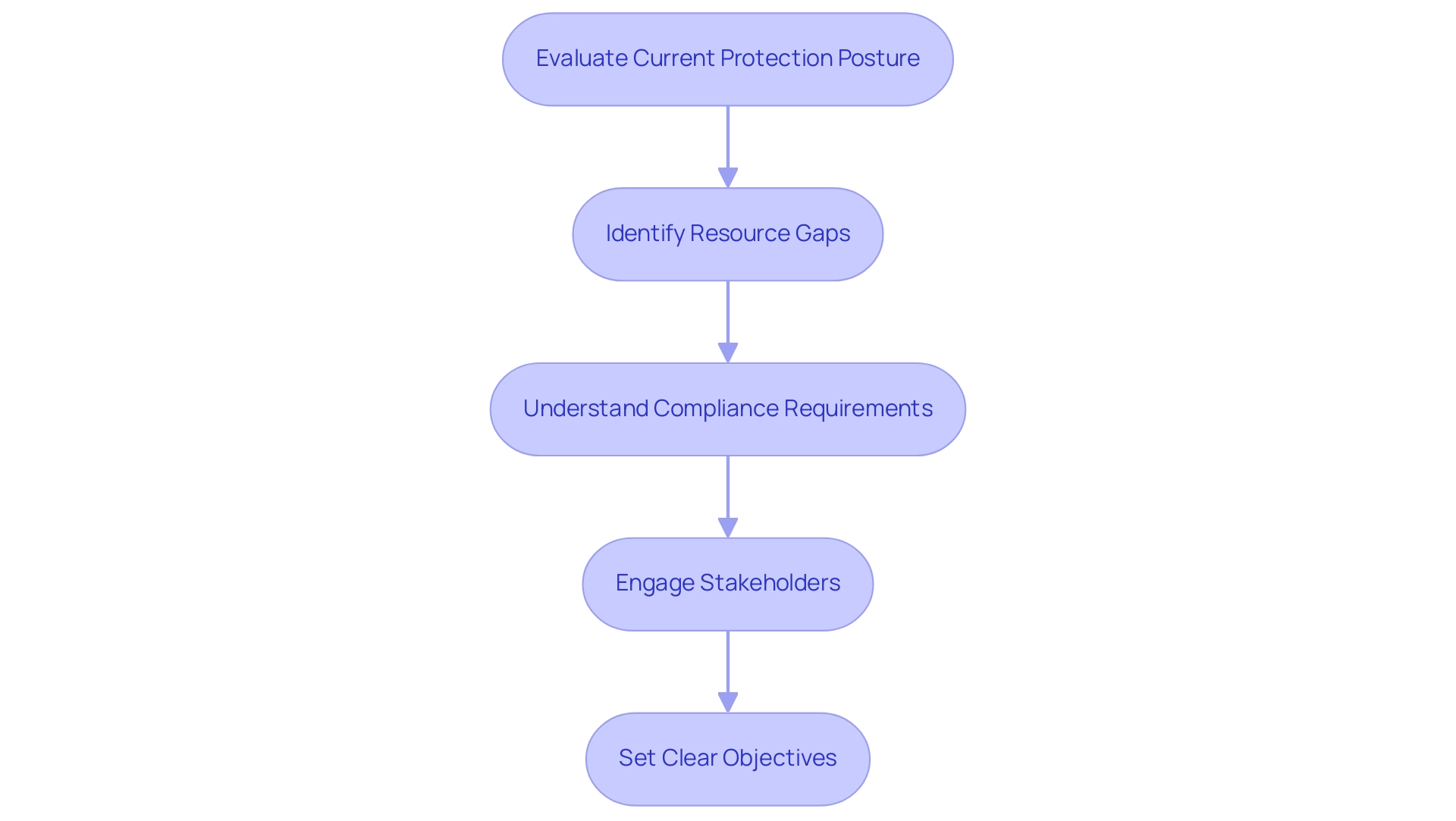
Assessing Organizational Readiness for Implementation
Before implementing the cis top 18 controls, entities should conduct a readiness assessment. This involves:
- Evaluating Current Protection Posture: Review existing policies, procedures, and technologies to identify strengths and weaknesses.
- Identifying Resource Gaps: Evaluate if the entity possesses the required personnel, tools, and budget to implement the measures efficiently.
- Understanding Compliance Requirements: Determine any regulatory or compliance obligations that may impact the implementation of the cis top 18 controls.
- Engaging Stakeholders: Involve key stakeholders from various departments to ensure a comprehensive understanding of the entity’s security needs and to garner support for the initiative.
- Setting Clear Objectives: Define specific, measurable goals for the implementation of the CIS guidelines that align with the entity’s overall business objectives.
By thoroughly assessing readiness, entities can identify potential challenges and develop strategies to address them, ensuring a more effective implementation process.
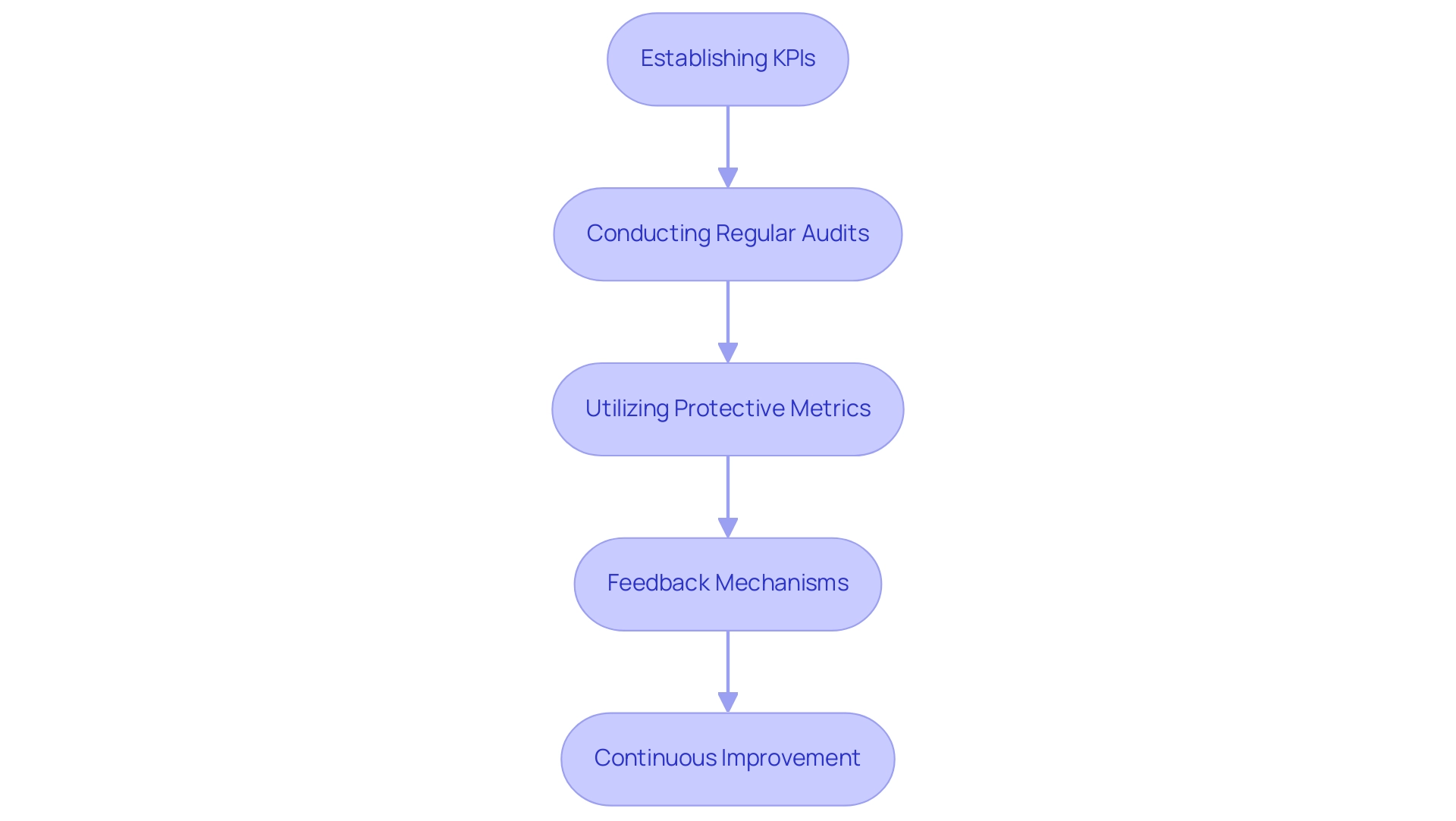
Monitoring Progress and Measuring Effectiveness
Once the CIS Top 18 controls have been implemented, organizations must monitor progress and measure effectiveness through:
-
Establishing Key Performance Indicators (KPIs): Define KPIs that align with the objectives set during the readiness assessment, such as the number of vulnerabilities identified and remediated.
-
Conducting Regular Audits: Schedule periodic audits to evaluate compliance with the CIS controls and identify areas for improvement.
-
Utilizing Protective Metrics: Analyze protective metrics such as incident response times, user access logs, and threat detection rates to gauge the effectiveness of the implemented controls.
-
Feedback Mechanisms: Create channels for employees to provide feedback on the effectiveness of protective measures and any challenges encountered.
-
Continuous Improvement: Leveraging the insights obtained from observation efforts, make modifications to policies and practices to enhance overall effectiveness.
By actively tracking progress and evaluating the effectiveness of the CIS Top 18 controls, entities can ensure that their cybersecurity strategies remain robust and responsive to evolving threats.
Fostering a Culture of Cybersecurity Awareness
To foster a culture of cybersecurity awareness, organizations should:
- Implement Regular Training Programs: Offer ongoing training sessions that cover current cybersecurity threats, best practices, and the significance of the CIS Top 18 controls.
- Promote Open Communication: Encourage employees to report incidents or concerns without fear of repercussions, fostering a culture of transparency.
- Recognize and Reward Good Practices: Acknowledge employees who demonstrate good cybersecurity practices, reinforcing positive behavior and encouraging others to follow suit.
- Engage Leadership: Ensure that leadership actively participates in cybersecurity initiatives and communicates the significance of protection to the entire organization.
- Utilize Real-World Scenarios: Incorporate real-world examples of security breaches and their impacts to help employees understand the relevance and urgency of cybersecurity efforts.
By creating a culture of cybersecurity awareness, organizations can empower employees to be proactive in protecting their digital assets and contribute to a more secure environment overall.
Conclusion
Implementing the CIS Top 18 Controls is essential in today's digital landscape, where organizations face an array of cyber threats that can jeopardize sensitive information and operational integrity. By understanding and adopting these best practices, organizations can significantly bolster their cybersecurity posture. The structured approach to implementation, assessment of readiness, and continuous monitoring outlined in this article serves as a roadmap for achieving robust defenses against potential breaches.
The process begins with:
- Establishing a governance framework
- Conducting a thorough inventory of assets, ensuring that organizations know what needs protection
Access control, continuous vulnerability management, and incident response planning are critical components that not only safeguard data but also prepare organizations to respond effectively to incidents. Furthermore, fostering a culture of cybersecurity awareness through training and open communication reinforces the importance of these measures.
Ultimately, the commitment to the CIS Top 18 Controls is not a one-time effort but an ongoing journey. Regular audits, performance evaluations, and a dedication to continuous improvement are vital to adapting to the ever-evolving cyber threat landscape. By prioritizing these controls, organizations can enhance their resilience, protect their assets, and build trust among stakeholders, ensuring a secure operational environment in an increasingly complex digital world.




