Introduction
In an increasingly interconnected world, organizations face the imperative of establishing clear guidelines governing technology use among their users. Acceptable Use Policies (AUPs) serve as critical instruments in this endeavor, delineating acceptable behaviors and safeguarding both organizational assets and user rights. As concerns about data privacy and cybersecurity mount, particularly with the rise of generative AI, the importance of a robust AUP cannot be overstated.
This article delves into the fundamental components of an effective AUP, the benefits of utilizing AUP generators, and the steps necessary for organizations to customize their policies to meet specific needs. By prioritizing these aspects, organizations can foster a secure digital environment that promotes responsible technology use and enhances compliance with legal standards.
Understanding Acceptable Use Policies: Importance and Purpose
An acceptable use policy generator serves as a foundational framework regulating the behaviors and practices of individuals within a technological environment of a company. Its importance cannot be overstated; an effective acceptable use policy generator not only safeguards the entity and its users but also outlines the limits between acceptable and unacceptable use of technology resources. With 69% of entities expressing concern that generative AI might compromise their legal rights, a robust AUP becomes even more critical in the evolving landscape of cybersecurity.
A well-defined acceptable use policy generator addresses these concerns by outlining specific guidelines for the use of AI technologies, thereby safeguarding the entity’s legal interests. Mok emphasizes that 'the quality and security of their information assets should be a very high priority for all entities, right across the sector.' Furthermore, in the 'Age of Information,' where trust is paramount, organizations must prioritize data privacy to foster confidence among individuals.
For instance, the case study on privacy policies for clothing websites illustrates how clearly articulated acceptable use policy generators can help maintain trust and ensure legal compliance, particularly in sectors where data privacy is critical. By articulating these guidelines, the acceptable use policy generator mitigates risks associated with data breaches and cyber threats while ensuring compliance with legal regulations. Moreover, it fosters a culture of responsibility and accountability among participants, reinforcing the understanding that each individual plays a vital role in maintaining a secure and efficient technological environment.
As we approach 2024, the necessity for comprehensive acceptable use policy generators is more pronounced than ever, particularly due to recent discussions on data privacy and trust.
Step-by-Step Guide to Creating Your Acceptable Use Policy with a Generator
-
Choose a Reliable AUP Generator: Begin by selecting a dependable AUP generator that offers customizable templates and is user-friendly. Leasing options in 2024 include [Generator Name 1] and [Generator Name 2], known for their versatility and positive user feedback.
-
Compile Necessary Information: Before utilizing the generator, gather essential information pertaining to your entity's technology usage. This should encompass details about the devices, software, and internet services used within your company. Aim for a contaminant frequency target of less than 3% to ensure that your approach is not only comprehensive but also effective in managing risks.
Input Basic Organizational Details: Enter your entity's name, contact information, and any additional required specifics into the generator to ensure clarity and accuracy in the policy.
Select Appropriate Options: Review and choose from the available options that best suit your organization's requirements. Consider aspects such as restrictions on personal use, guidelines for internet usage, and defined consequences for rule violations. As M. Bianco stated regarding locoregional techniques, effective management of technology use can improve outcomes and reduce adverse effects, similar to pain management in medical contexts.
-
Review and Refine the Draft: After generating the initial policy draft, meticulously review the document for clarity and comprehensiveness. Make necessary adjustments to ensure the final product accurately reflects your entity's values and operational requirements. Just as timely intervention is crucial in medical cases, regular reviews and updates of the AUP are essential to maintain compliance and effectiveness.
-
Finalize and Secure the Document: Once you are satisfied with the content of the AUP, finalize the document and save it in a secure location. For ease of distribution and accessibility, consider exporting the AUP to a PDF format.
Customizing Your AUP: Tailoring Policies to Fit Your Business
It is critical to use an acceptable use policy generator to customize your Acceptable Use Policy (AUP) so that it effectively aligns with the specific needs of your entity. Here are crucial areas to concentrate on during the customization process:
- Scope of the Guidelines: Clearly define the individuals the guidelines apply to, encompassing employees, contractors, and third-party vendors to ensure comprehensive coverage.
- Technology Usage: Specify the types of technology and services encompassed by the guidelines, including email, internet access, and devices issued by the company, to provide clarity on expectations.
- Behavioral Expectations: Articulate acceptable and unacceptable behaviors in detail, addressing issues such as social media usage during work hours and restrictions on accessing inappropriate content.
- Reporting Violations: Establish a well-defined process for reporting guideline violations, reinforcing a culture where employees can report concerns without fear of retaliation.
- Review and Update Procedures: Create a schedule for regularly reviewing and updating the acceptable use policy generator, ensuring that it remains relevant as technological advancements and institutional needs evolve.
As entities increasingly shift towards first-party data strategies—61% of high-growth companies are adopting such approaches—it's essential to recognize that 48% of respondents are also focused on developing and improving traditional channels. This dual focus highlights the need for a UPs that can adapt to both emerging and established data strategies. Additionally, consider the financial impact highlighted by the case study titled 'Cost of BYOD Problems,' where a doctor lost a laptop containing sensitive information, leading to approximately $1.5 million in fines for his company.
Such examples underscore the potential consequences of inadequate policies generated by an acceptable use policy generator. Furthermore, the trend towards personalized approaches in various sectors is evident, as reflected in the quote from Statista that personalized beauty startups raised over $1 billion in funding in 2021. By addressing these key areas, you can enhance your entity's cybersecurity posture and compliance readiness, ensuring a robust framework that adapts to future challenges.
Essential Components of an Effective Acceptable Use Policy
An effective Acceptable Use Policy (AUP) is foundational for fostering a secure digital environment and should encompass several essential components:
- Purpose Statement: This section articulates the underlying goals of the AUP, emphasizing its critical role in safeguarding assets and promoting ethical use of technology.
- Definitions: Clear definitions of key terms are necessary to eliminate ambiguity throughout the policy, ensuring that all individuals have a mutual understanding of its provisions.
- Acceptable Use Guidelines: The acceptable use policy generator must provide detailed guidelines that delineate acceptable behaviors regarding the use of technology resources, encompassing internet browsing, email communication, and software applications to mitigate risks associated with misuse.
- Prohibited Activities: An acceptable use policy generator should provide a comprehensive list of prohibited activities, specifying actions such as illegal downloads, accessing inappropriate content, and unauthorized sharing of confidential information, which may expose the entity to significant security threats.
- Enforcement and Consequences: This segment describes the ramifications of policy violations, including potential disciplinary actions and legal consequences, emphasizing the role of an acceptable use policy generator in maintaining a secure and respectful work environment.
- Acknowledgment: To reinforce accountability, a section for acknowledgment should be integrated within the acceptable use policy generator, confirming that individuals have read and understood the AUP. Statistics indicate that entities with clear acknowledgment processes report higher compliance rates, supporting a culture of digital responsibility. In fact, given that 81% of businesses are not fully confident in their technology stack’s ability to support the needs of hybrid and remote employees, a well-implemented AUP can significantly enhance confidence in technology use.
Dimitar Kostadinov notes that AUPs not only cover broader computing resources but also emphasize etiquette and respect, which is vital in multi-user environments. Moreover, the adaptability in the scope of the acceptable use policy generator enables entities to customize guidelines to address particular departmental or user requirements, thus improving their effectiveness and relevance in today's evolving cyber environment.
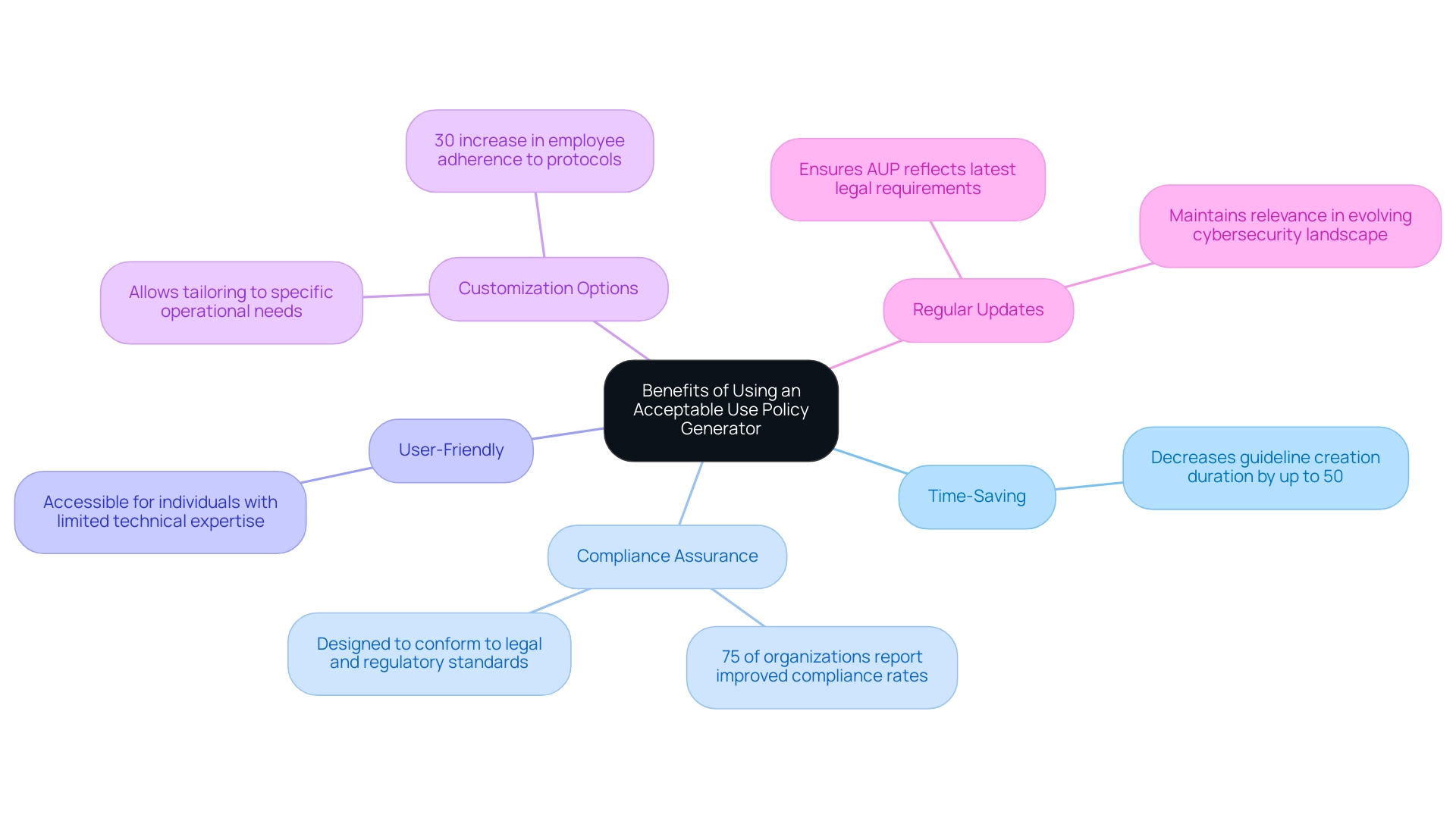
Benefits of Using an Acceptable Use Policy Generator
Utilizing an acceptable use policy generator offers numerous advantages essential for entities aiming to enhance their cybersecurity posture. The key benefits include:
- Time-Saving: AUP generators significantly streamline the creation process. By providing pre-designed templates, entities can swiftly develop an AUP without the extensive time investment typically required to draft one from scratch. In fact, studies indicate that entities utilizing an acceptable use policy generator can decrease the duration of guideline creation by as much as 50%.
- Compliance Assurance: Numerous these generators are particularly crafted to conform to legal and regulatory standards, thus reducing the risk of non-compliance. As emphasized by the AICPA,
The financial benefit is not worth the many negatives arising from such arrangements, including primarily that they likely will compromise the integrity of the tax system.
This highlights the significance of following established guidelines in formulation. A recent survey indicated that 75% of organizations that utilized an acceptable use policy generator reported improved compliance rates. - User-Friendly: AUP generators are crafted with user experience in mind, ensuring that even individuals with limited technical expertise can effectively create a comprehensive guideline.
- Customization Options: These tools offer flexibility for customization, allowing organizations to tailor documents to meet their specific operational needs and unique circumstances, thereby enhancing relevance and applicability. For instance, a case study on the implementation of an acceptable use policy generator at a mid-sized tech firm revealed that customized guidelines led to a 30% increase in employee adherence to cybersecurity protocols.
- Regular Updates: With the landscape of cybersecurity evolving continuously, many generators provide regularly updated templates. This ensures that your AUP reflects the latest legal requirements and best practices, thus maintaining its relevance in 2024 and beyond. Experts agree that staying updated with the latest trends in cybersecurity is vital for organizational resilience.
Overall, using an acceptable use policy generator not only simplifies the policy creation process but also strengthens compliance efforts, making it an essential tool in contemporary cybersecurity strategies.
Conclusion
Establishing a robust Acceptable Use Policy (AUP) is crucial for organizations navigating the complexities of technology use in today's digital landscape. A well-crafted AUP serves as a foundational tool that delineates acceptable behaviors, mitigates risks associated with data breaches, and fosters a culture of responsibility among users. As highlighted, the importance of AUPs has intensified with the rise of generative AI and growing concerns regarding data privacy and cybersecurity.
The step-by-step guide to creating an effective AUP emphasizes the significance of customization to align with an organization's unique needs. By employing reliable AUP generators, organizations can streamline the policy creation process, ensuring compliance with legal standards while saving valuable time. Furthermore, the comprehensive components of an effective AUP—including:
- Clear definitions
- Acceptable use guidelines
- Enforcement mechanisms
are essential for fostering a secure digital environment.
Ultimately, prioritizing the development and implementation of a robust AUP not only protects organizational assets but also enhances user trust and accountability. In an era where technology plays an integral role in operations, investing in a well-defined AUP is not merely a best practice but a necessity for safeguarding both the organization and its users. By committing to these principles, organizations can navigate the evolving landscape of technology with confidence and resilience.




