Introduction
In today's digital landscape, the importance of robust web application security cannot be overstated. To safeguard sensitive data and maintain the integrity of online systems, organizations must adopt comprehensive penetration testing strategies. This article delves into the essential steps of penetration testing, from meticulous planning and reconnaissance to vulnerability analysis and exploitation.
Each phase is designed to uncover and address potential security weaknesses, ensuring that applications remain resilient against cyber threats. By understanding and implementing these critical steps, organizations can enhance their security posture, protect their reputation, and build trust with stakeholders and customers.
Step 1: Planning and Preparation
Before starting a penetration assessment engagement, it is essential to establish a clear scope and set specific objectives. Begin by identifying the primary goals of the test, such as compliance verification, risk assessment, or vulnerability identification. Ensure alignment with organizational policies and obtain necessary permissions from key stakeholders and decision-makers.
Next, create a detailed project plan that outlines the scope of the evaluation, including specific systems and assets to be assessed, the timeline, objectives, and expected outcomes. This plan should also specify the evaluation methodology to be employed, such as Black Box, White Box, or Gray Box approaches, depending on the scope and needs of the organization. Additionally, consider whether social engineering, API fuzzing, or examination of external-facing web applications will be included.
Identify the protection leaders engaged in the intrusion assessment initiative, and define distinct roles and responsibilities. Identify a main point of contact or central organizer to ensure smooth coordination and communication throughout the process.
Consider the support required for the security team, including expertise, resources, and budget. Determine if the project will be managed in-house or if an outside penetration evaluation service provider is required. When selecting an external provider, inquire about their core business focus, certifications such as ISO 9001 or CREST, and how they stay current with the latest vulnerabilities and exploits.
By adhering to these procedures, organizations can guarantee a comprehensive and efficient penetration evaluation process, ultimately improving awareness of risks, safeguarding their reputation, and fostering trust with clients and collaborators.
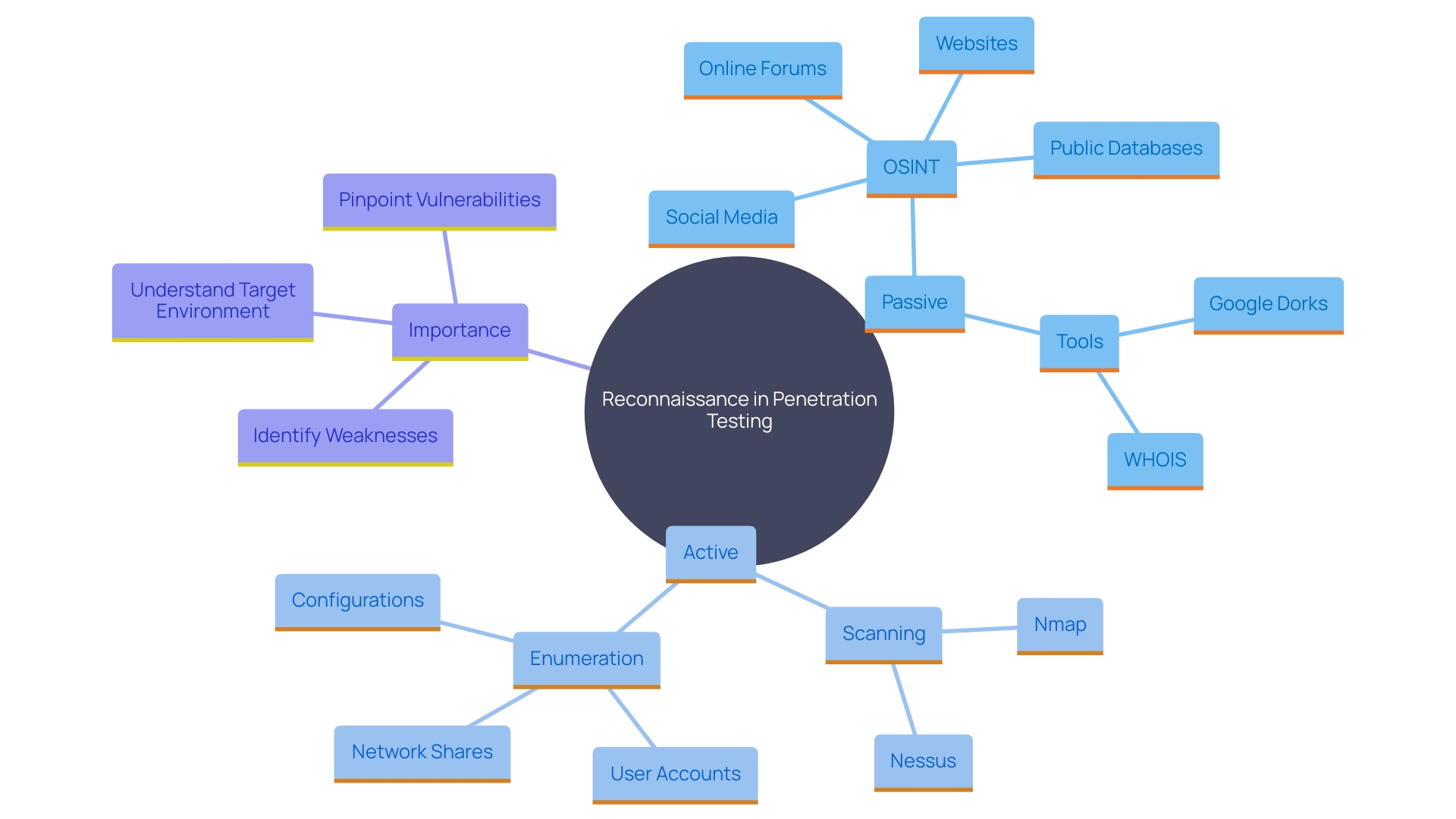
Step 2: Reconnaissance - Information Gathering
'Starting with reconnaissance is a fundamental step in penetration testing and web security assessment.'. This phase involves gathering as much information as possible about the target website using both passive and active techniques. Passive reconnaissance includes mining publicly available information from sources such as social media, websites, and public databases, often referred to as Open-Source Intelligence (OSINT). Tools like WHOIS can provide critical domain information, while Nmap can reveal IP addresses and server details.
Active reconnaissance, conversely, entails direct engagement with the target system to gather information on its software structure and infrastructure. This method provides a more comprehensive understanding of possible weaknesses. Utilizing reconnaissance frameworks helps build a comprehensive profile of the application and its environment. Advanced strategies such as filetype operators can uncover hidden sensitive files and documents that pose significant risks if exposed, as has been consistently observed during training sessions.
Understanding the intricacies of the target's digital footprint, including domain names, IP addresses, employee details, and organizational structure, provides a blueprint for identifying critical assets and potential attack vectors. This meticulous approach is vital for ethical hackers to preemptively identify weaknesses before they can be exploited by malicious actors. The Open-Source Intelligence (OSINT) market is anticipated to grow by 25.44% from 2022 to 2030, underscoring the increasing importance of thorough reconnaissance in cybersecurity.
Step 3: Vulnerability Scanning and Enumeration
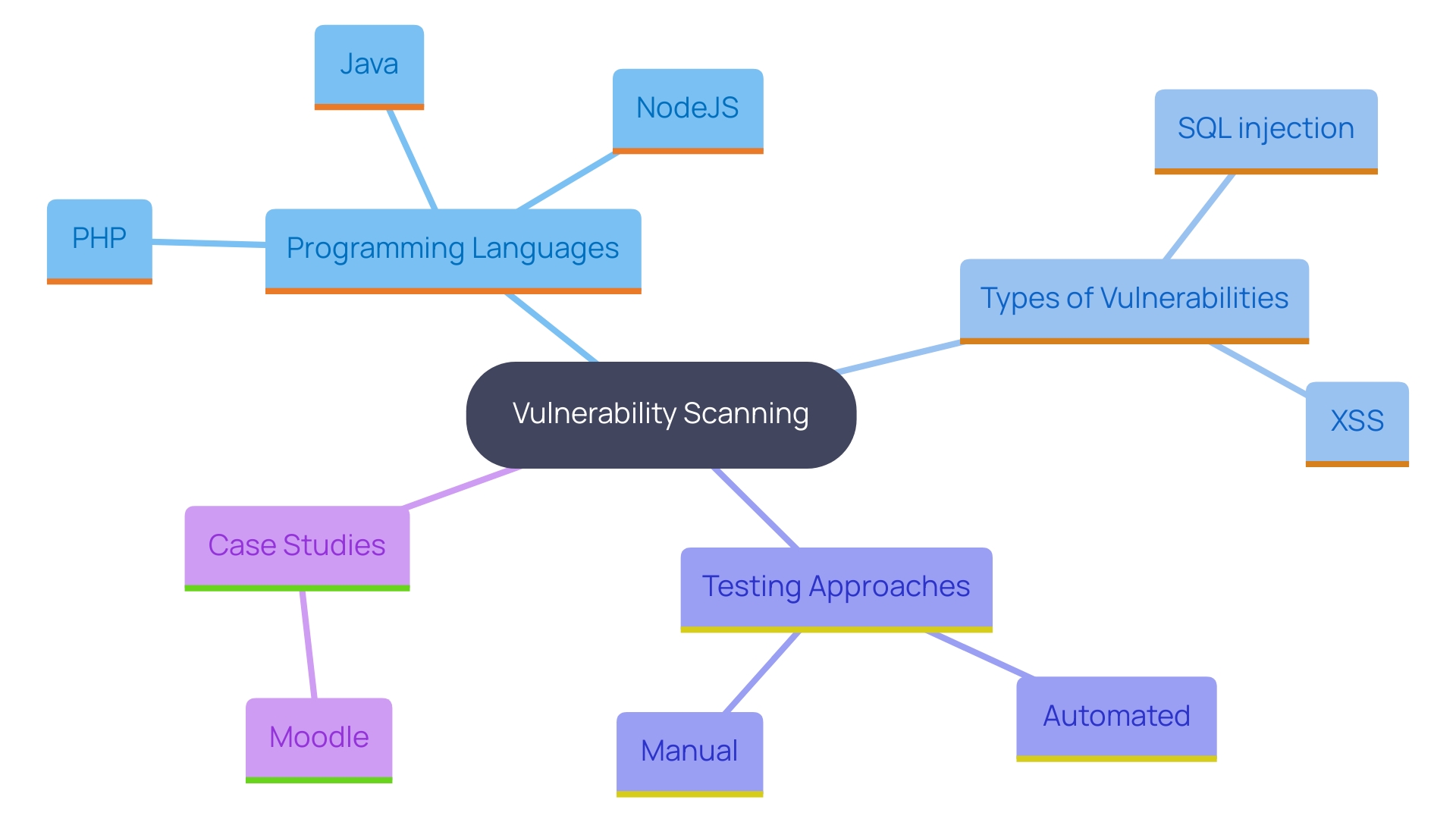
After gathering the necessary information, the next step is vulnerability scanning. Employing automated tools is crucial to detect possible vulnerabilities in the web system, such as SQL injection, cross-site scripting (XSS), and insecure configurations. Statistics from 2021–2023 show that most web applications assessed were written in Java (44%), followed by NodeJS (17%) and PHP (12%). Additionally, over a third (39%) used microservice architecture. Thingiverse landscape underscores the importance of using comprehensive scanning tools.
Automated scans can swiftly identify a wide array of weaknesses, but they may not recognize every problem. Consequently, manual counting is essential for confirming automated results and uncovering weaknesses that tools may overlook. Information from recent evaluations shows that black and gray box examinations usually uncover an average of 23 weaknesses per software, while white box analysis identifies about 30. This highlights the need for a multi-faceted approach to thoroughly assess an application’s security.
One notable case involved the Moodle learning platform, where a weakness in the quiz functionality was exploited. This example emphasizes the importance of detailed manual testing to uncover complex issues that automated tools might overlook.
Recording all recognized weaknesses is essential for additional examination and correction. This process ensures that security teams can prioritize and address the most critical issues effectively, ultimately strengthening the overall security posture of the web application.
Step 4: Vulnerability Analysis and Prioritization
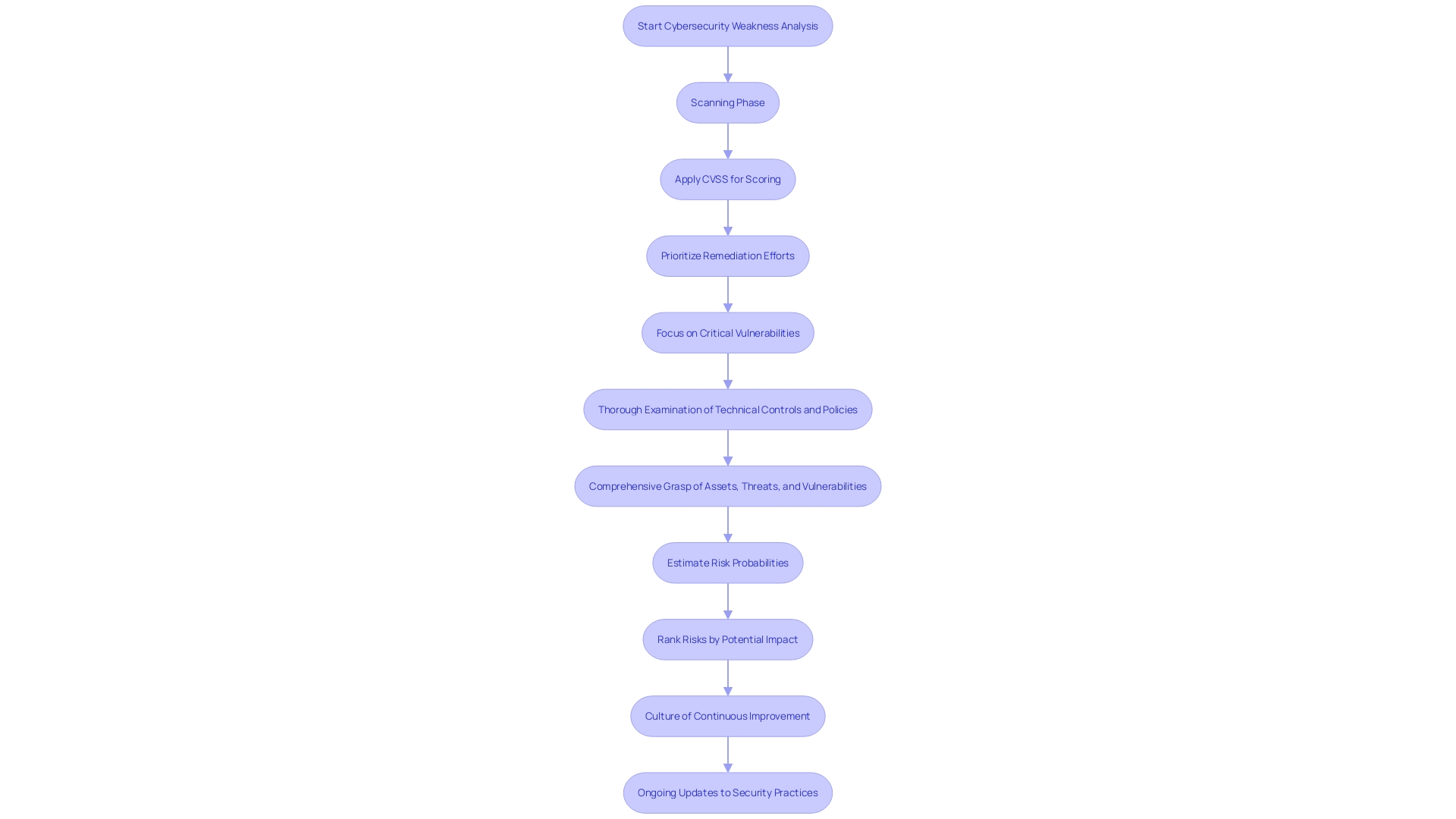
After scanning, it is critical to analyze identified weaknesses based on their severity and potential impact on the organization. Utilizing a standardized scoring system, such as the Common Vulnerability Scoring System (CVSS), allows for a consistent and objective evaluation. CVSS version 4.0 provides a more nuanced representation of exploitability, facilitating more effective prioritization of fixes. As cybersecurity expert highlights, 'Overall, CVSS is supposed to help enterprises evaluate weaknesses at a glance, so they can effectively prioritize fixes,' which underscores the importance of a structured approach.'. Attention should be directed toward weaknesses that present the greatest danger to the application, particularly those that are easily taken advantage of or have serious repercussions. This approach aligns with the findings of Corren McCoy et al., emphasizing the need to concentrate remediation efforts on weaknesses likely to be exploited. Furthermore, addressing 'Security Alert Fatigue' is essential by ensuring tools not only aggregate but also prioritize risks effectively. By doing so, organizations can avoid the overwhelm of extensive risk lists and concentrate on the most pressing threats.
Step 5: Exploitation and Validation
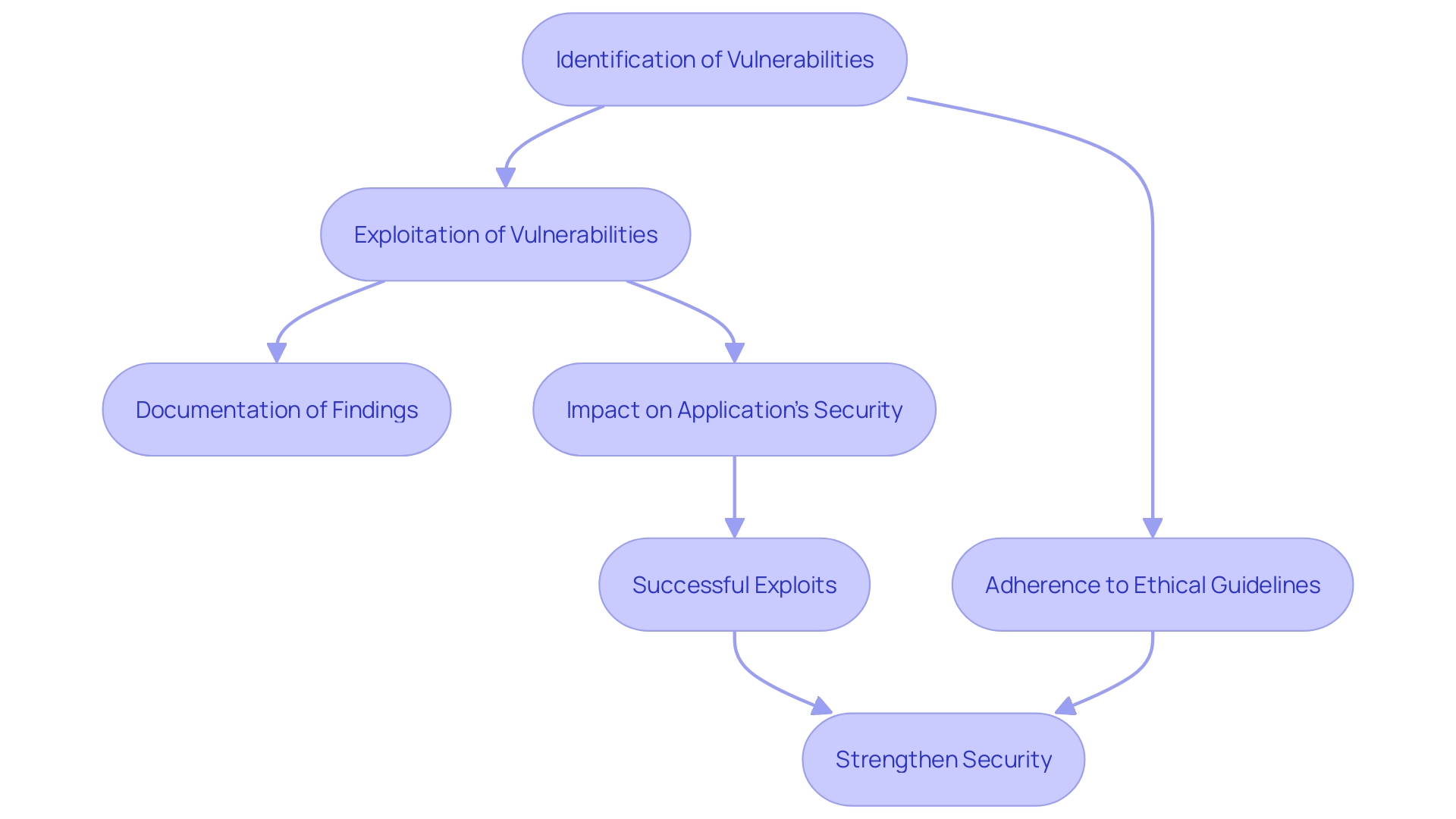
During this phase, the goal is to exploit identified vulnerabilities to confirm their existence and understand their potential impact. Ethical hacking techniques are employed to rigorously test the software's defenses without causing damage. Adhering to agreed-upon scope and ethical guidelines is crucial throughout this process. Each successful exploit is thoroughly documented, detailing its effects on the application's protection stance.
For example, during a recent penetration test on Moodle, a well-known learning management system, several weaknesses were identified. One notable finding was that users with the 'trainer' role could execute Cross-Site Scripting attacks by design, highlighting the complexity and inherent risks of the platform. Such findings highlight the significance of confirming weaknesses to comprehend their true effect.
Moreover, as emphasized by Etay Maor, Sr. Director of Security Strategy, tools like Mimikatz are prevalent and can swiftly extract passwords, allowing attackers to gain significant access if they obtain administrative credentials. This type of exploitation can lead to extensive network compromise over time, often undetected.
Penetration testing, similar to employing a thief to assess a bank's defenses, offers essential understanding of system weaknesses. It is essential to conduct these tests with minimal prior knowledge of the system to uncover blind spots. This approach guarantees thorough evaluations of protection measures, directing essential enhancements to strengthen defenses.
Step 6: Post-Exploitation and Data Analysis
After a successful exploitation attempt, it is crucial to thoroughly analyze the data and access obtained. This step is vital for assessing the breach's scope and pinpointing the data at risk. According to Schrader (2021), legacy systems often lack sufficient cybersecurity measures, heightening their exposure to threats. Proper documentation of findings is essential to assist in effective remediation efforts. Automated attack investigation systems can aid in this process by collecting data, tracking events, and providing interpretable summaries, thereby easing the burden on analysts. CloudFlare's introduction of AI auditing tools exemplifies current efforts to enhance protective measures and mitigate risks efficiently.
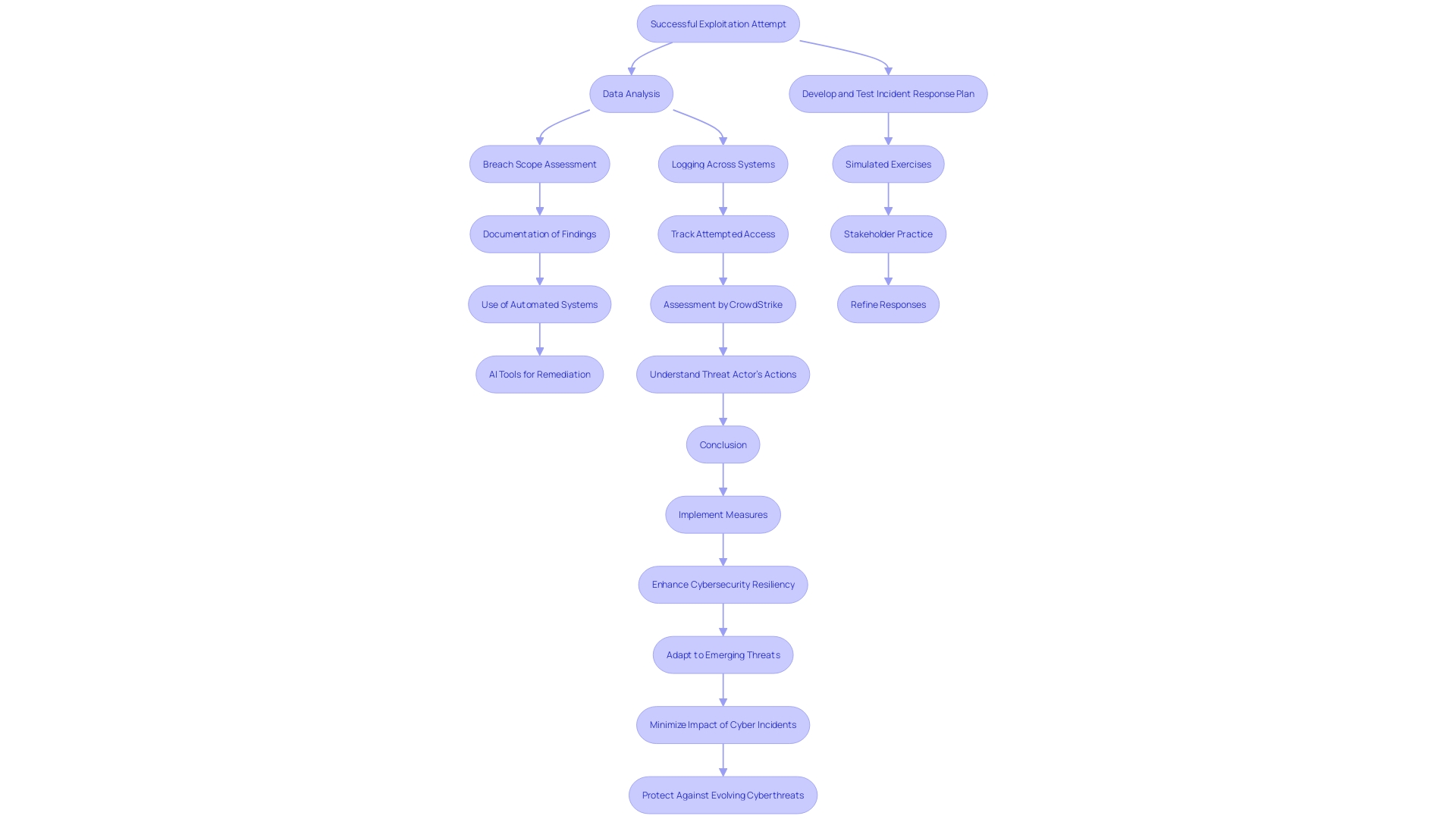
Step 7: Reporting and Remediation
Compile a comprehensive report detailing the findings of the penetration test. The report should include an executive summary, detailed descriptions of weaknesses, evidence of exploitation, and actionable remediation recommendations. Present the report to stakeholders, ensuring clarity and understanding. Collaborate with the development team to address identified issues and enhance the security posture of the web application.
Key findings from our recent analysis highlight the dynamic nature of attack surfaces. On average, organizations see over 300 new services each month, contributing to nearly 32% of new high or critical exposures. The media and entertainment industry alone adds more than 7,000 services monthly, underscoring the need for continuous monitoring and adaptation.
Presenting the findings should not only communicate the current state of weaknesses but also provide a roadmap for remediation. Evidence of exploitation, such as logs and forensic data, should be included to substantiate the findings. This aligns with the Gartner® best practices for cyber-risk management, which emphasize the importance of planning, securing, and monitoring the entire lifecycle of cybersecurity efforts.
Statistics show that more than half of organizations (51%) have only moderate visibility into their vulnerabilities. Regular evaluations, carried out monthly or quarterly, are essential for sustaining a strong defense posture. These assessments help in identifying potential risks and planning appropriate responses, as highlighted by the NIST CSF guidelines.
Moreover, the Managed Services evaluations stress the importance of providing clear, objective insights into the defensive capabilities of participants. This collaborative method assists in recognizing gaps and fostering innovation, ultimately enhancing the overall protection stance of the industry.
Use forensic investigation tools such as EnCase and FTK to gather and analyze evidence during the penetration test. These tools are essential for a thorough investigation and remediation process. According to the Bureau of Labor Statistics, the demand for cybersecurity analysts and consultants is projected to grow significantly, highlighting the critical need for skilled professionals in this field.
Finally, address the findings collaboratively with the development team to ensure that identified vulnerabilities are mitigated effectively. This collaborative effort is essential for enhancing the protective stance of the web application and ensuring long-term resilience against cyber threats.
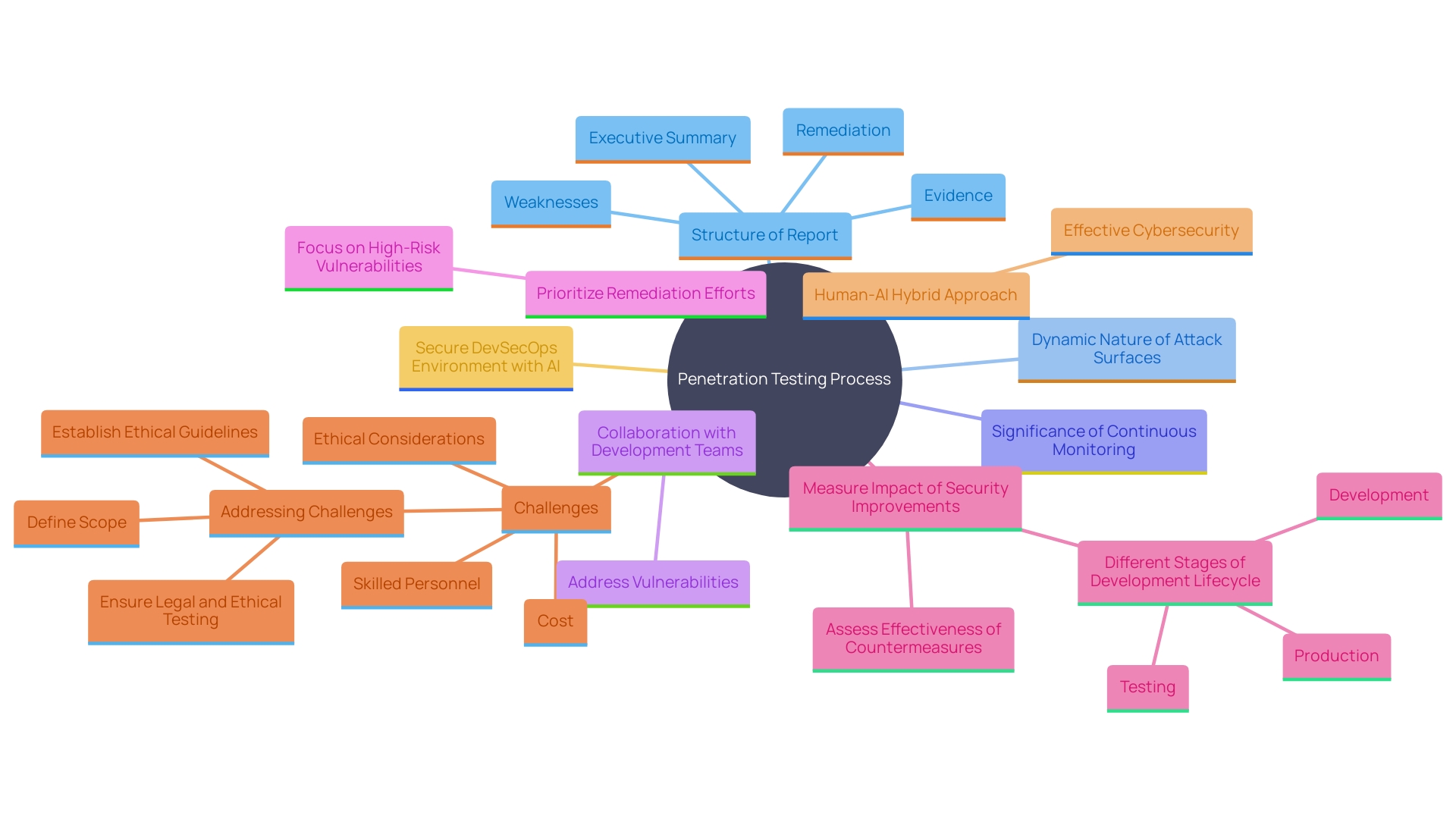
Choosing the Right Web Application Penetration Testing Vendor
Choosing the appropriate penetration assessment provider is essential for guaranteeing strong protection and upholding your organization's image. Begin by evaluating the vendor's expertise and experience. Seek companies with certified penetration specialists who focus on your sector and the particular kind of assessment you need. This is essential as it demonstrates their ability to manage your unique protection needs effectively.
Reputation and references should also be a key consideration. Research the vendor's standing in the industry and seek references from previous clients. This will help you gauge their track record in delivering high-quality services. For instance, companies that regularly conduct penetration tests are more likely to have a stable and trustworthy reputation, which is vital for building trust with customers and partners.
Inquire about the vendor's methodology and frameworks. Ensure they adhere to industry best practices and follow comprehensive frameworks. This guarantees that their testing processes are thorough and reliable. Moreover, customization and flexibility are paramount. Choose a vendor that offers tailored solutions to fit your organization's specific requirements and budget constraints.
Additionally, comprehensive reporting is critical. Ensure the vendor provides detailed reports that include actionable recommendations for remediation. Such reports are crucial for tackling recognized weaknesses efficiently and improving your overall defensive stance.
To assist the protection team internally, determine if the project can be managed within the organization or if outside expertise is needed. Engaging with the vendor involves asking pertinent questions about their core services, certifications like ISO 9001 or CREST, and their approach to staying current with the latest vulnerabilities and exploits.
By evaluating these elements, you can choose a trustworthy penetration assessment provider that matches your organization's objectives, thus promoting a successful collaboration and aiding in improved awareness among staff.
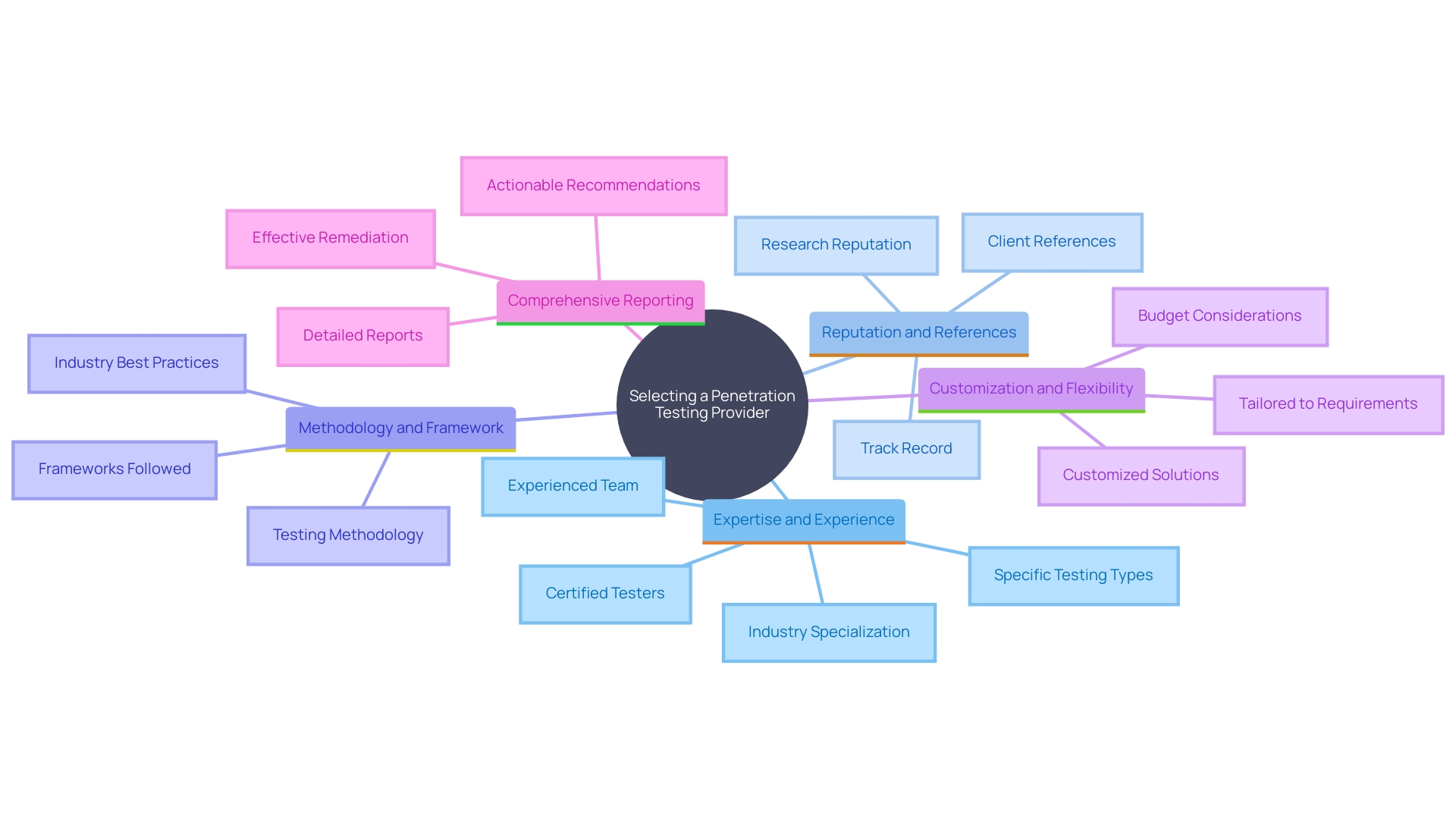
Continuous vs. Point-in-Time Web Application Penetration Testing
Selecting between continuous and point-in-time penetration assessments is crucial for aligning with your organization's security strategy. Constant evaluation offers continuous reviews, essential for detecting weaknesses in ever-changing settings. This approach is essential for managing risks associated with rapidly evolving threat landscapes, where traditional methods often fall short.
Point-in-time testing, on the other hand, is beneficial for periodic evaluations but may overlook vulnerabilities introduced between tests. According to Schrader (2021), legacy systems often receive minimal updates, focusing on functionality rather than security, which can exacerbate these gaps.
Evaluate your organization's risk tolerance and compliance requirements to determine the most suitable approach. For instance, managing shadow IT in the age of SaaS application sprawl necessitates a proactive stance. Ongoing evaluation can address these challenges by providing real-time insights into potential vulnerabilities.
Furthermore, protecting your organization's reputation and building trust with stakeholders hinges on demonstrating a commitment to security. Regular penetration assessments, whether ongoing or conducted at a specific moment, highlights this commitment. Choosing a penetration evaluation firm with a demonstrated history, including knowledge in your sector and compliance with industry standards, is essential. Customization and flexibility in testing solutions also ensure that your unique requirements are met effectively.
Conclusion
The significance of robust web application security is underscored throughout the outlined steps of penetration testing. Beginning with meticulous planning and preparation sets the foundation for a thorough examination of potential vulnerabilities. The importance of reconnaissance, both passive and active, highlights the necessity of gathering comprehensive information about the target environment, which is critical in identifying attack vectors.
Subsequent phases, including vulnerability scanning and enumeration, followed by thorough analysis and prioritization, demonstrate the need for a multi-faceted approach in assessing an application’s security. The insights gained from exploitation and validation are invaluable, as they not only confirm the existence of vulnerabilities but also elucidate their potential impacts. Documentation and reporting play crucial roles in enabling organizations to address identified issues effectively and enhance their overall security posture.
In choosing the right penetration testing vendor, organizations must prioritize expertise, reputation, and adherence to best practices. The decision between continuous and point-in-time testing further emphasizes the need for a tailored approach based on specific organizational requirements. By implementing these comprehensive penetration testing strategies, organizations can fortify their defenses, protect sensitive data, and maintain trust with stakeholders, ultimately contributing to a resilient cyber security framework.




