Introduction
In an age where digital transformation is paramount, organizations leveraging Office 365 must prioritize security to safeguard their sensitive data against an array of evolving threats. The increasing frequency of cyberattacks, particularly phishing incidents that have doubled in recent years, underscores the urgency for comprehensive risk assessments. These evaluations not only help identify vulnerabilities but also ensure compliance with critical regulatory standards such as GDPR and HIPAA.
By systematically addressing potential risks and implementing robust security measures, organizations can enhance their resilience against unauthorized access and data breaches. This article provides a structured approach to conducting risk assessments, highlights common risks associated with Office 365, and outlines best practices for effective risk mitigation, ultimately reinforcing the security posture necessary for today’s dynamic digital landscape.
The Importance of Risk Assessments for Office 365 Security
Carrying out a thorough evaluation of the office 365 security risk assessment is vital for numerous important reasons. Primarily, it enables entities to identify potential vulnerabilities that may be exploited by malicious actors, especially in light of rising phishing traffic, which has surged from 1 million incidents in 2021 to 2 million in 2023. This concerning rise emphasizes the critical necessity for entities to carry out comprehensive office 365 security risk assessments to protect against such dangers.
Furthermore, regular assessments are crucial for ensuring compliance with regulatory frameworks such as GDPR and HIPAA. This illustrates a group's commitment to safeguarding sensitive data and adhering to legal obligations. As emphasized by industry specialists,
- 'entities often depend on predictable human actions such as choosing easy-to-guess passwords, reusing them across multiple sites, and succumbing to phishing attacks,'
- which can expose them to considerable dangers.
A comprehensive evaluation, such as an office 365 security risk assessment, not only assists in adherence but also guides strategic decision-making concerning investments in safety, enabling entities to distribute resources efficiently to alleviate identified threats. For instance, a case study named 'Proactive Measures Against Ransomware' demonstrates that entities applying a multilayered protective approach, including routine vulnerability evaluations and user awareness training, can greatly lower the risk of unauthorized access and improve recovery abilities in the case of an attack. By emphasizing these evaluations, organizations can greatly improve their overall defense stance, ensuring strong protection for their digital assets in a progressively dangerous cybersecurity environment.
Furthermore, recent documents regarding vulnerabilities, like the critical problem revealed by Microsoft impacting multiple versions of Microsoft Outlook (CVE-2024-21413), highlight the necessity of conducting an office 365 security risk assessment to adopt a proactive approach to evaluations. This commitment can ultimately lead to enhanced recovery capabilities and a fortified defense against potential ransomware attacks, illustrating the extensive advantages of conducting an office 365 security risk assessment in the Office 365 environment.
Step-by-Step Guide to Conducting an Office 365 Security Risk Assessment
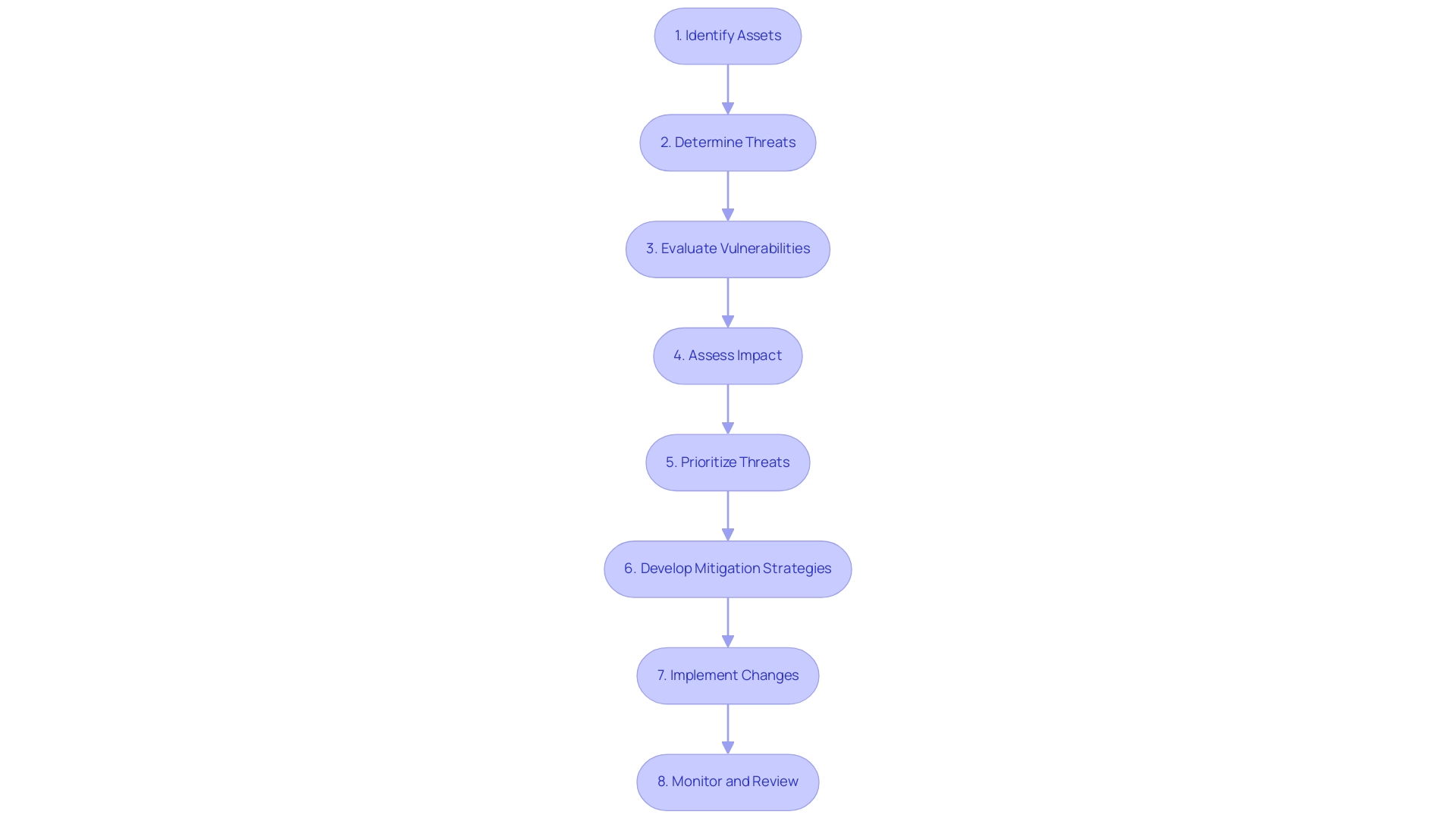
Carrying out a comprehensive Office 365 security risk assessment is essential for protecting your organization from emerging threats. Follow this structured approach to ensure comprehensive coverage:
- Identify Assets: Start by cataloging all Office 365 assets, including user accounts, sensitive data, and applications.
A precise inventory is crucial for comprehending possible hazards and setting a foundation for protective measures.
-
Determine Threats: Assess potential threats to your assets, including phishing attacks, unauthorized access, and data breaches. Both internal and external threats should be considered to create a holistic risk profile.
-
Evaluate Vulnerabilities: Examine the vulnerabilities within your Office 365 configuration. This involves scrutinizing user permissions, reviewing data sharing settings, and assessing security configurations to identify weaknesses that could be exploited.
-
Assess Impact: For each identified threat, evaluate the potential effect on your entity.
This includes considering financial repercussions, reputational damage, and operational disruptions that may arise if a threat materializes. Implementing Data Loss Prevention (DLP) policies can significantly help prevent sensitive information from being shared outside your organization, thus mitigating potential risks.
- Prioritize Threats: Rank the identified threats based on their likelihood of occurrence and potential impact.
This prioritization allows attention to be directed towards the most crucial areas that need urgent focus, thus enhancing efficiency in management efforts. Establishing different levels of due diligence based on vendor classification can further enhance this efficiency and consistency.
- Develop Mitigation Strategies: Formulate actionable plans to address the identified risks.
Effective strategies may involve implementing multi-factor authentication, conducting user training sessions, or adjusting security settings to enhance protection. Regular backup and restore testing is crucial for mitigating data loss from incidents like ransomware attacks, ensuring that your entity can recover effectively when needed.
-
Implement Changes: Execute the mitigation strategies and ensure that all modifications are meticulously documented for future reference and compliance.
-
Monitor and Review: Continuously observe your Office 365 environment and perform regular evaluations to stay ahead of new threats and adjust to changes within your entity.
As highlighted by industry experts, almost three-fourths (75%) of executives believe there will be significant changes in their entity’s approach to crisis management and business continuity planning. This highlights the significance of a proactive and dynamic protection strategy.
By following these steps, organizations can effectively carry out an Office 365 security risk assessment for their environment, ensuring vigilance against potential dangers and strengthening a robust defense posture.
Common Risks Associated with Office 365
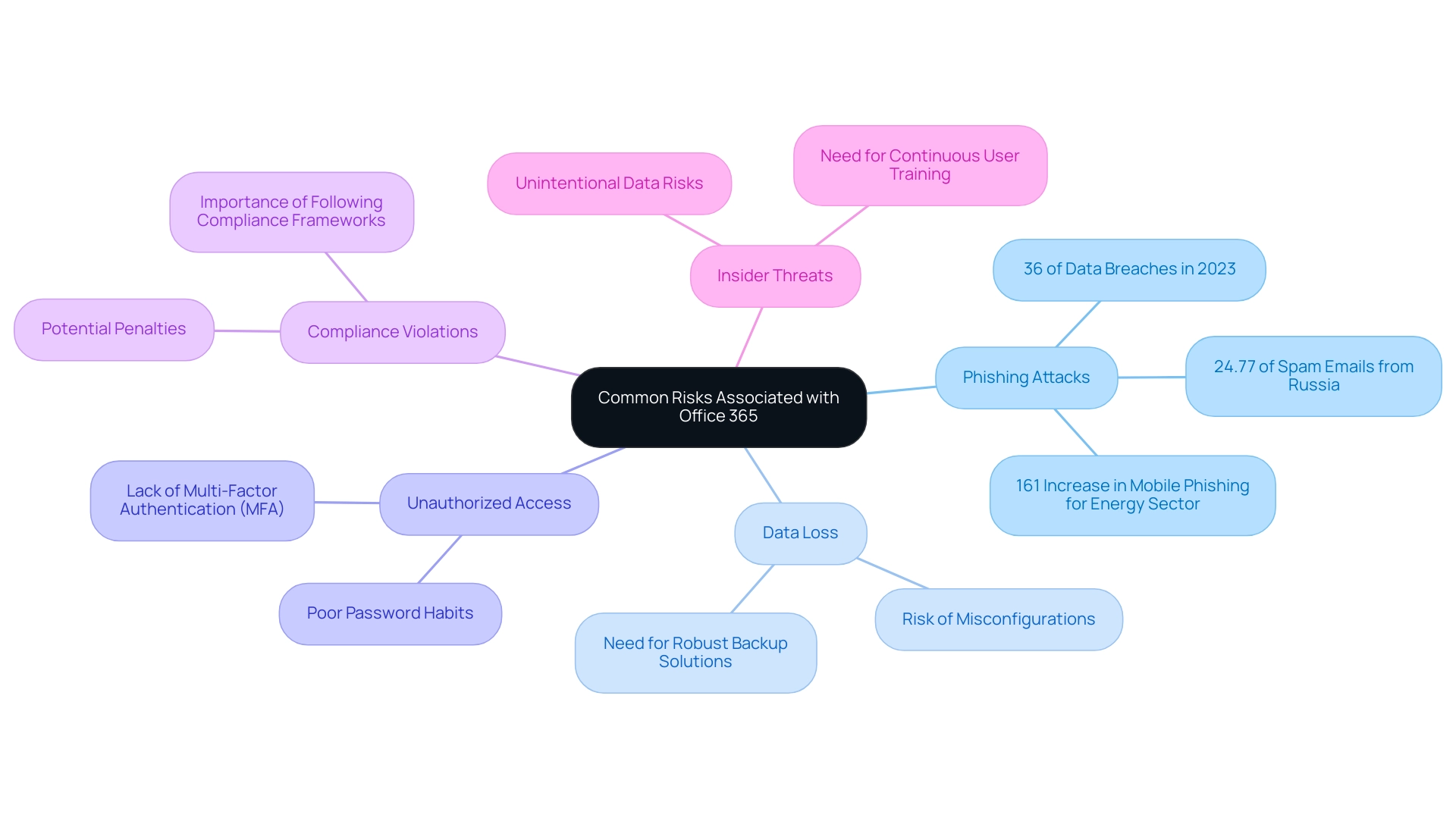
Organizations using Office 365 must navigate a variety of common threats that can weaken their protective stance, including:
-
Phishing Attacks: Cybercriminals often target Office 365 users through deceptive emails aimed at obtaining sensitive credentials. Significantly, phishing attacks accounted for 36% of all data breaches in the U.S. in 2023, emphasizing the urgent need for strengthened email protection protocols. Furthermore, as mobile phishing attacks targeting the energy sector surged by 161% between 2020 and 2021, the landscape of threats continues to evolve.
-
Data Loss: The potential for data loss due to misconfigurations or inadvertent deletions necessitates the implementation of robust backup solutions. This is especially vital as entities move to cloud settings, where data integrity may be jeopardized.
-
Unauthorized Access: Poor password habits and the lack of multi-factor authentication (MFA) greatly heighten the likelihood of unauthorized access to sensitive information. Organizations must prioritize MFA to safeguard against such vulnerabilities.
-
Compliance Violations: Non-compliance with industry regulations can result in substantial penalties and reputational harm. It is crucial for entities to stay alert in following compliance frameworks to reduce these risks.
-
Insider Threats: Employees may unintentionally or deliberately endanger data integrity, making continuous user training and monitoring vital. This involves promoting a culture of awareness to reduce threats from within.
Moreover, it is significant that 24.77% of spam emails worldwide in 2021 came from Russia, further highlighting the necessity for entities to be cautious against phishing attempts. Understanding these threats is essential for companies to efficiently customize their evaluations and apply suitable protective measures in their Office 365 security risk assessment. The data highlights the critical need for improved email protection protocols to guard against phishing-related breaches, particularly as sophisticated email attacks rose by 24% in the first half of the year.
Best Practices for Mitigating Risks in Office 365
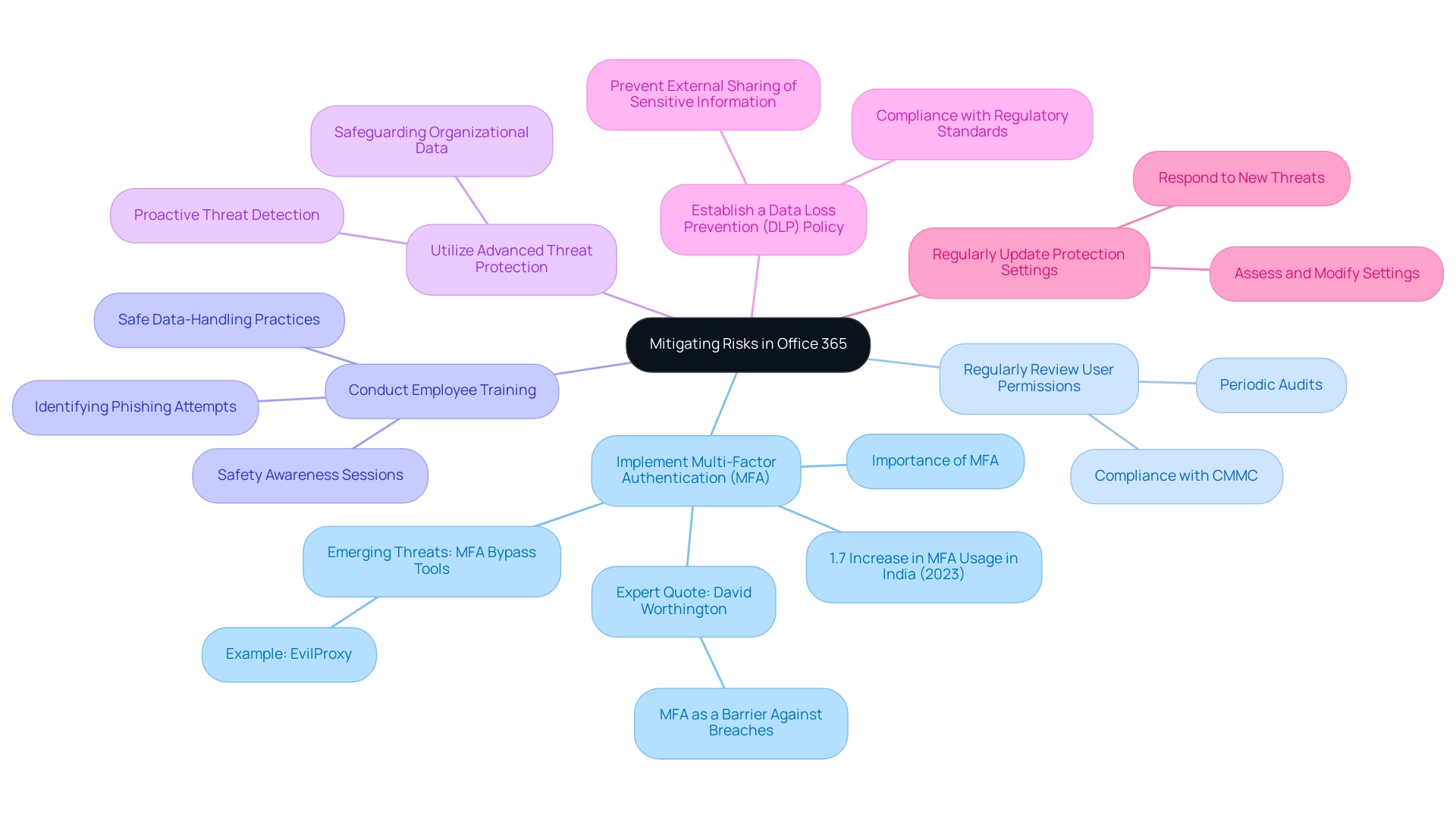
To effectively mitigate risks within Office 365, organizations should conduct an Office 365 security risk assessment and adopt the following best practices:
- Implement Multi-Factor Authentication (MFA): MFA is essential as it provides an additional layer of protection, significantly reducing the likelihood of unauthorized access. Recent statistics indicate a 1.7% increase in MFA usage in India during 2023, demonstrating its growing importance in cybersecurity.
As David Worthington, a recognized expert in the field, states,
MFA is an effective barrier against breaches, reinforcing the necessity of this measure in today’s threat landscape. This is particularly crucial in light of emerging threats such as MFA bypass tools, exemplified by tools like EvilProxy, which can exploit weaknesses in authentication processes.
- Regularly Review User Permissions: Conduct periodic audits of user access levels to ensure that employees maintain access only to the data essential for their roles.
This practice not only improves protection but also aligns with compliance requirements, especially considering the recent developments in the Cybersecurity Maturity Model Certification (CMMC) that emphasize the need for stringent access controls.
-
Conduct Employee Training: Implement regular training sessions focused on safety awareness. These sessions should highlight identifying phishing attempts and safe data-handling practices, vital in minimizing human error—a frequent weakness in breaches.
-
Utilize Advanced Threat Protection: Leverage Office 365’s built-in protective features, such as Advanced Threat Protection (ATP), to proactively detect and respond to potential threats. This tool plays a critical role in safeguarding organizational data against sophisticated attacks.
-
Establish a Data Loss Prevention (DLP) Policy: Develop and enforce DLP policies to prevent sensitive information from being shared externally.
This is vital for ensuring compliance with regulatory standards and protecting critical data.
- Regularly Update Protection Settings: Keeping protection settings up to date is imperative. Organizations must regularly assess and modify these settings to tackle new threats and respond to changes within the organization.
By applying these best practices, organizations can greatly reduce their vulnerability and improve the protective stance of their Office 365 environments through an Office 365 security risk assessment. The rise of MFA bypass tools emphasizes the need for continuous monitoring and employee security training to strengthen defenses, and the evolving regulatory landscape, as highlighted by the CMMC, underscores the importance of compliance in today's security framework.
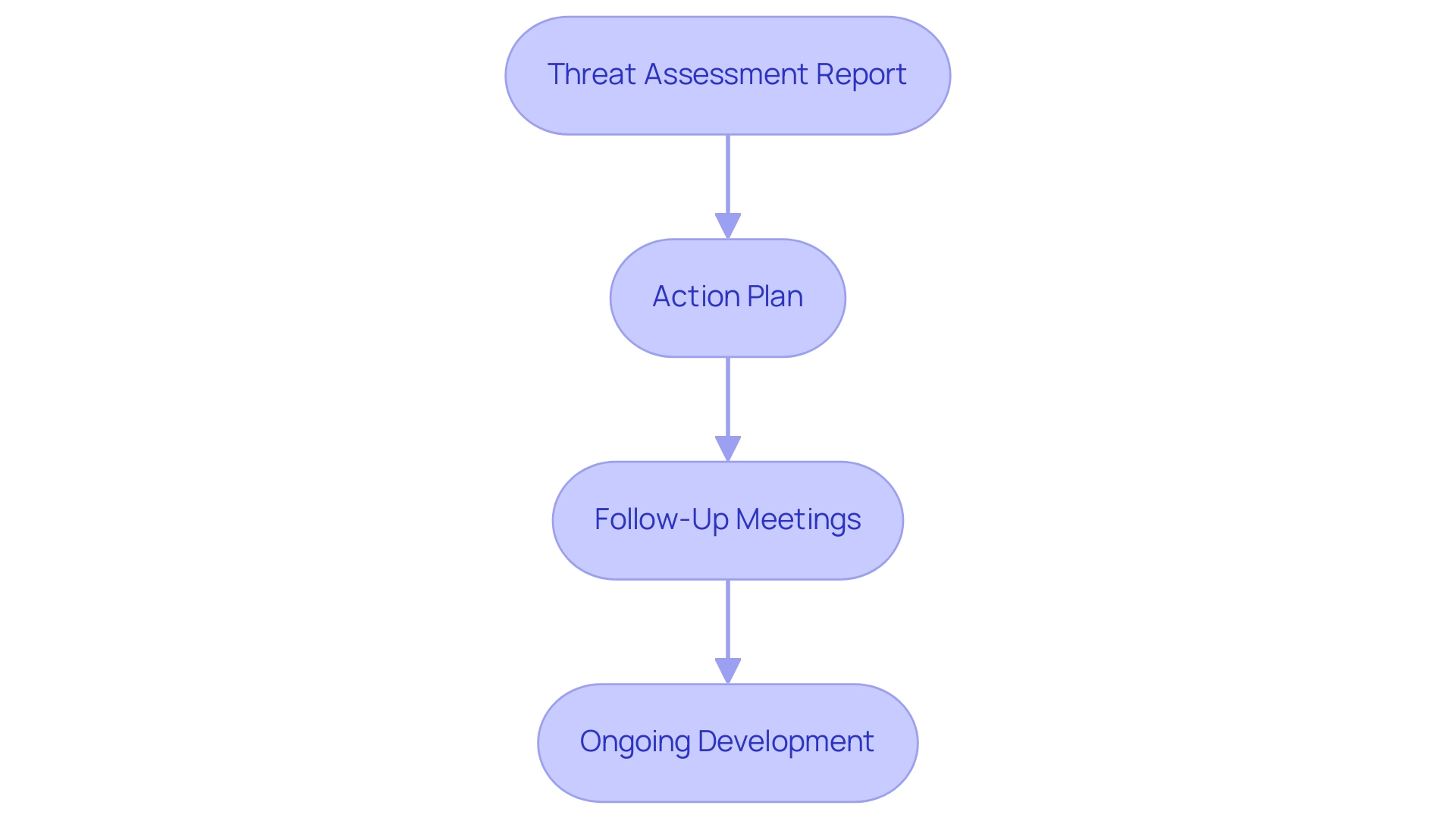
Documenting and Reporting the Risk Assessment
Upon finishing the evaluation, it is essential to carefully record the results and efficiently convey them to all pertinent stakeholders. This process should encompass several key components:
- Threat Assessment Report: Develop a comprehensive report that details identified threats, assesses their potential impacts, and outlines recommended mitigation strategies. An executive summary should be included to provide higher management with an overview of critical findings.
- Action Plan: Formulate a detailed action plan that specifies the steps necessary to address each identified risk, complete with timelines and designated responsibilities.
- Follow-Up Meetings: Schedule follow-up meetings with stakeholders to review evaluation findings and discuss the implementation of the action plan, ensuring alignment and accountability. Engaging the appropriate stakeholders in this process is vital, as it promotes cooperation and guarantees that all viewpoints are taken into account.
- Ongoing Development: Cultivate a culture of safety by promoting input on the evaluation process and its results. This feedback is crucial for improving future evaluations and strengthening the overall stance of the entity. Routine threat evaluations, such as an office 365 security risk assessment, guarantee that the organization stays ready for new challenges, emphasizing the importance of continuous reviews.
By carefully recording and reporting on evaluations, organizations not only adhere to best practices but also foster a culture of awareness and responsibility. Such proactive measures ensure that security remains a top priority at all organizational levels, which is vital in the face of emerging threats. As noted by Damodar Vishnu Lele,
We can only reduce the probability or likelihood to an acceptable level
—a reminder that thorough risk evaluation documentation is key to managing risks effectively.
This aligns closely with the oil and energy sector's emphasis on environmental, health, and safety priorities, highlighting the critical nature of these assessments.
Conclusion
Conducting comprehensive risk assessments for Office 365 security is not merely a best practice but a fundamental necessity in today’s digital landscape. As highlighted throughout this article, organizations face a myriad of threats, particularly from phishing attacks and unauthorized access, which have seen alarming increases in frequency. By systematically identifying vulnerabilities, evaluating potential impacts, and implementing robust mitigation strategies, organizations can significantly bolster their defenses against cyber threats.
The structured approach to conducting risk assessments—encompassing:
- Asset identification
- Threat evaluation
- Continuous monitoring
ensures that organizations remain vigilant and responsive to emerging risks. Moreover, adherence to best practices such as implementing multi-factor authentication and conducting regular employee training can further enhance security measures and compliance with regulatory standards like GDPR and HIPAA.
Ultimately, the commitment to regular risk assessments and proactive security strategies not only protects sensitive data but also fosters a culture of security awareness within organizations. As the threat landscape continues to evolve, prioritizing these assessments is essential for safeguarding digital assets and ensuring operational resilience. By taking decisive action today, organizations can lay a strong foundation for a secure future in an increasingly perilous cybersecurity environment.




