Introduction
In an increasingly digital world, the security of organizational data has never been more critical. As businesses continue to adopt cloud solutions like Office365, the need for comprehensive security measures becomes paramount.
- Vulnerability assessments and penetration testing stand at the forefront of these strategies, playing essential roles in identifying and mitigating potential threats.
This article delves into the intricacies of these processes, highlighting:
- Best practices
- The importance of continuous monitoring
- The tools that can enhance security frameworks
By understanding and implementing these strategies, organizations can not only safeguard their assets but also navigate the complex landscape of compliance and regulatory requirements that govern data protection.
Understanding Vulnerability Assessments and Penetration Testing
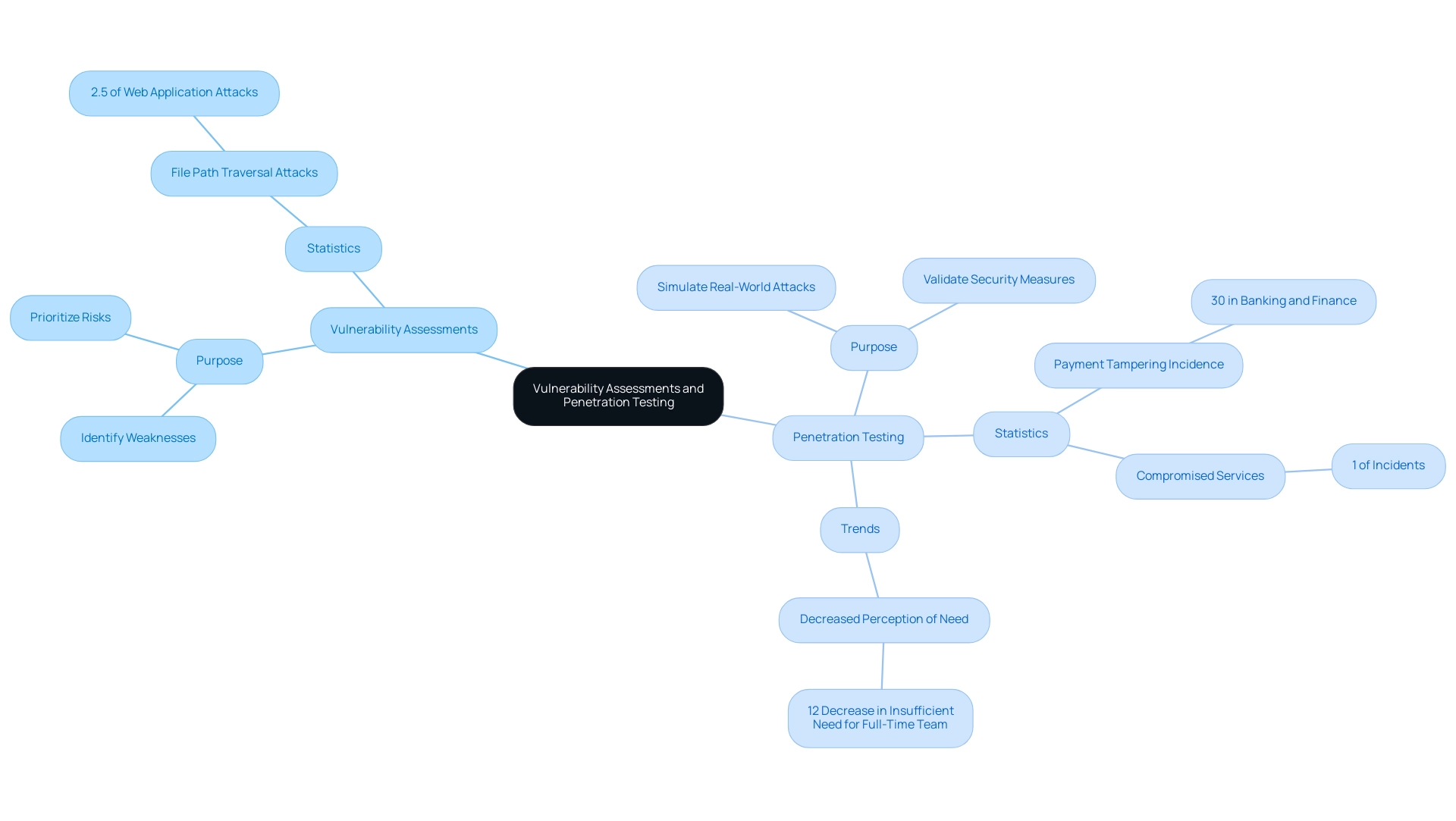
Vulnerability evaluations and penetration testing, known collectively as office365 vulnerability assessment and penetration testing, are essential elements of a strong security strategy for Office 365, each fulfilling different yet supportive functions. Assessments concentrate on recognizing, measuring, and prioritizing weaknesses within a system, offering a thorough overview of possible flaws. For example, file path traversal attacks constitute 2.5% of web application attacks, emphasizing particular weaknesses that penetration testing can tackle.
In contrast, penetration testing simulates real-world attacks, actively exploiting these vulnerabilities to evaluate the actual risk they present to the entity. This dual approach not only identifies potential points of failure but also validates the effectiveness of existing security measures. Notably, recent findings indicate a 12% decrease in organizations perceiving insufficient need for a full-time penetration testing team, reflecting a growing recognition of its importance in today’s cybersecurity landscape.
Furthermore, case studies reveal a 30% incidence rate of payment tampering in banking and finance, underscoring the real-world implications of these assessments. Furthermore, a statistic indicating that compromised services represent 1% of incidents highlights the dangers linked to inadequate protective measures. By understanding the nuances between these processes, entities can tailor their security strategies more effectively by incorporating an office365 vulnerability assessment and penetration testing, ensuring a proactive stance against evolving threats.
Best Practices for Office365 Vulnerability Assessment and Penetration Testing
-
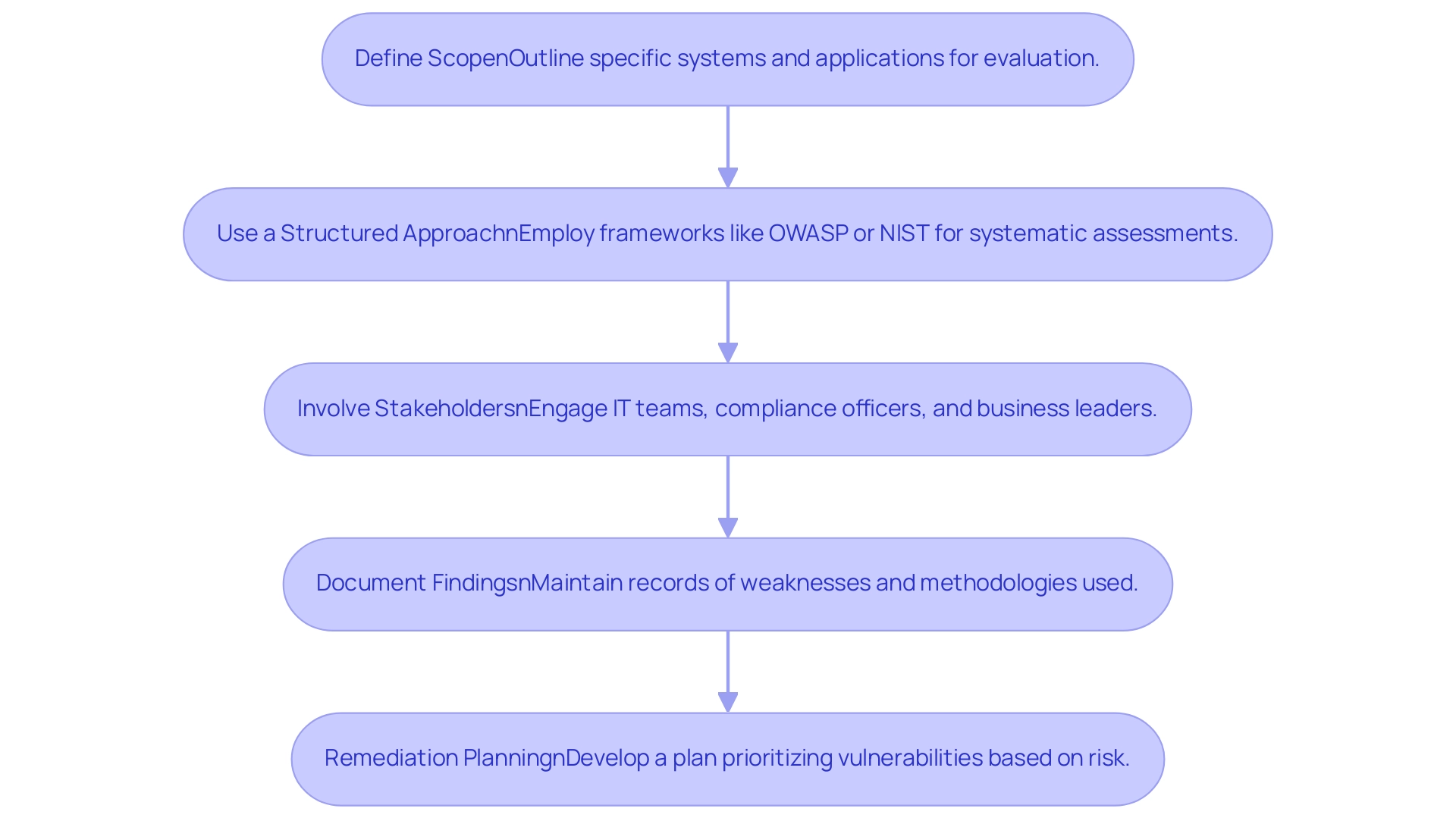
Define Scope: It is essential to begin by clearly outlining the specific systems and applications within Microsoft 365 that will be subjected to evaluation. This initial step guarantees that the office365 vulnerability assessment and penetration testing is both thorough and focused on the most essential elements of the entity's digital infrastructure. Significantly, merely 4% of organizations that do not utilize Office 365 reported data loss incidents, emphasizing the necessity of a comprehensive review process.
-
Use a Structured Approach: Employing a recognized framework such as the OWASP Testing Guide or NIST SP 800-115 for office365 vulnerability assessment and penetration testing provides a systematic methodology for evaluations. These frameworks enable comprehensive assessments of weaknesses and align with established compliance requirements, ensuring a robust security posture.
-
Involve Stakeholders: Engaging relevant stakeholders, including IT teams, compliance officers, and business leaders, is crucial for aligning the testing process with organizational objectives. This collaborative method guarantees that the office365 vulnerability assessment and penetration testing not only identifies weaknesses but also considers business impacts and compliance obligations.
-
Document Findings: Maintaining detailed records of identified weaknesses and the methodologies employed during testing is vital for future reference and remediation efforts. Documentation serves as a key resource for ongoing risk management and facilitates continuous improvement in security practices, particularly through office365 vulnerability assessment and penetration testing.
-
Remediation Planning: Following the office365 vulnerability assessment and penetration testing to identify weaknesses, it is imperative to develop a comprehensive remediation plan. This plan should prioritize vulnerabilities based on risk assessment results, ensuring that the most critical issues are addressed promptly. Consistently refreshing protection configurations can assist in reducing risks linked to recently identified threats, strengthening the entity's defense structure. As detailed in the case study titled "Best Practices for Microsoft 365 Security," implementing practices such as user education, secure collaboration, and enforcing Multi-Factor Authentication (MFA) can significantly improve the overall protection stance. As Damodar Vishnu Lele aptly states,
We can only reduce the probability or likelihood to an acceptable level — a reminder that thorough risk evaluation documentation is key to managing risks effectively. By following these organized methods and optimal techniques, including routine evaluations of user permissions and employing Advanced Threat Protection, organizations can improve their protective stance in Microsoft 365 and defend against possible weaknesses.
The Importance of Continuous Testing and Monitoring in Office365 Security
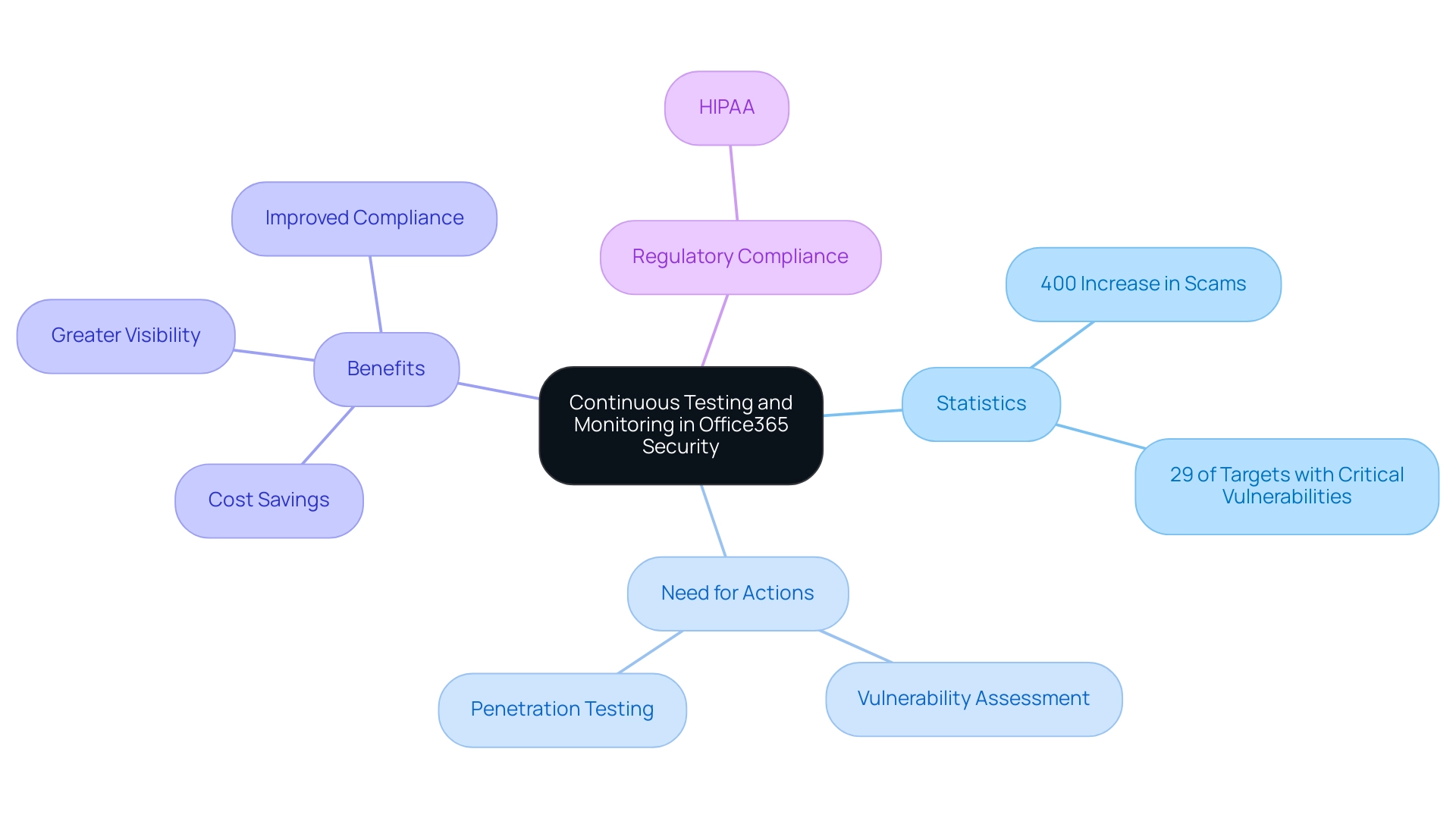
In the rapidly evolving landscape of cybersecurity, continuous testing and monitoring have become indispensable. The shift towards a proactive security posture is underscored by alarming statistics, such as the 400% increase in scams since March 2020, making the pandemic a significant catalyst for security threats. This alarming increase in cybersecurity incidents highlights the urgent need for regular office365 vulnerability assessment and penetration testing to uncover new weaknesses that may emerge due to software updates or changes in the threat landscape.
Notably, in 2020, 29% of penetration test targets possessed at least one critical vulnerability, further emphasizing the need for office365 vulnerability assessment and penetration testing.
Implementing automated monitoring tools is a strategic measure that can yield real-time alerts for unusual activities, enabling entities to respond swiftly to potential threats. This proactive strategy not only strengthens protection but also fosters a culture of alertness within the entity. The case study on Continuous Attack Surface Penetration Testing shows that although the initial investment may be higher, the long-term advantages include cost savings, greater visibility, and improved compliance, making it a crucial element of contemporary protective strategies.
As healthcare organizations increasingly rely on office365 vulnerability assessment and penetration testing to comply with regulatory standards such as HIPAA, it is clear that these methodologies are no longer optional but essential. Adopting automated monitoring tools can greatly improve threat detection abilities, ensuring that weaknesses are addressed quickly and efficiently, thus conforming to the essential compliance standards in today's protective environment.
Navigating Compliance and Regulatory Requirements in Office365 Security
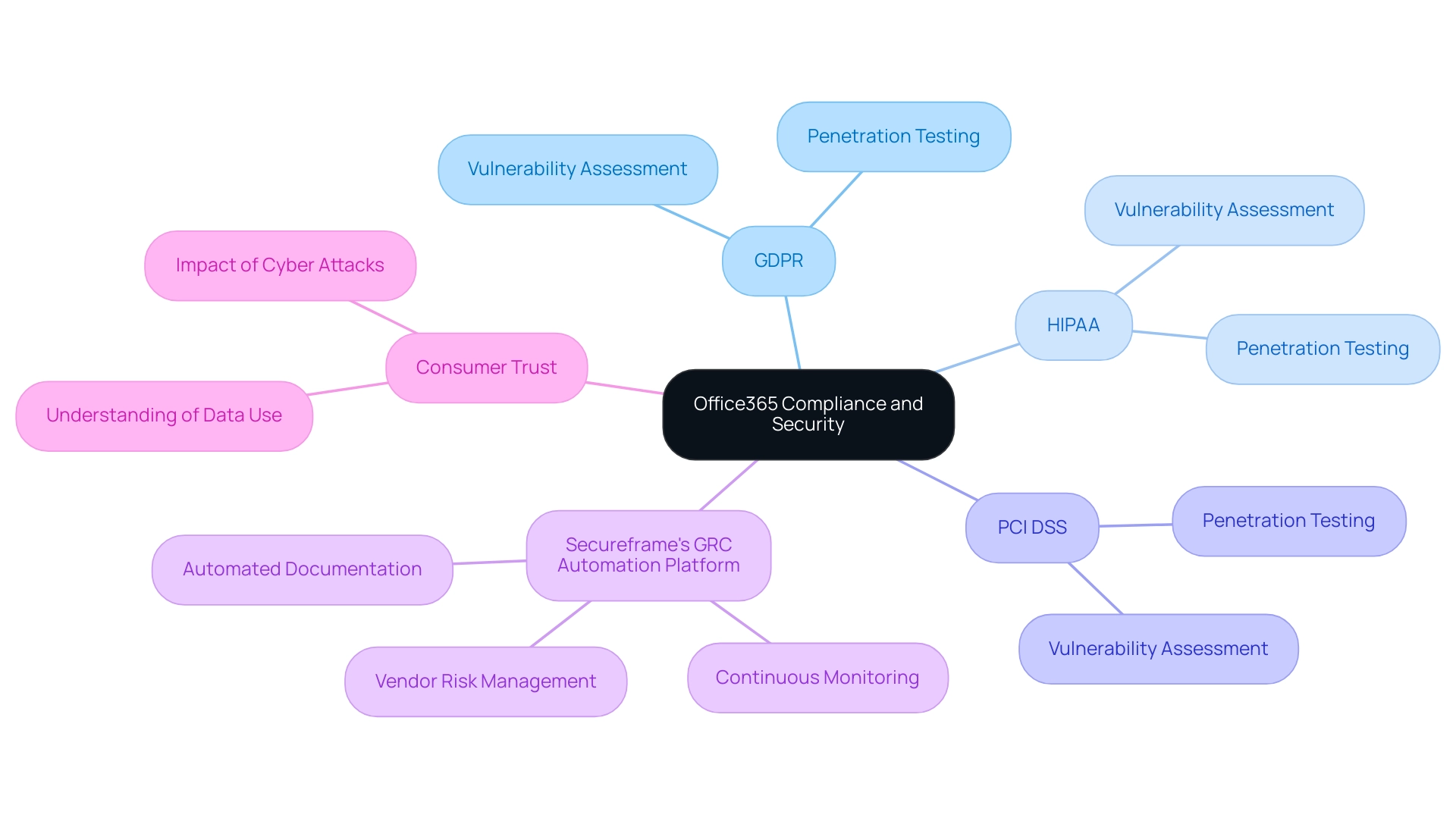
Organizations must navigate a range of compliance frameworks, including GDPR, HIPAA, and PCI DSS, which establish stringent guidelines for data handling and protection. Carrying out regular Office 365 vulnerability assessment and penetration testing is essential for detecting security gaps within systems. These Office 365 vulnerability assessment and penetration testing assessments not only reveal potential vulnerabilities but also serve as a proactive measure to demonstrate due diligence in compliance efforts.
For instance, Secureframe's GRC Automation Platform aids entities in navigating complex data privacy regulations by offering:
- Continuous monitoring
- Vendor risk management
- Automated documentation
This ensures compliance and adaptation to evolving threats. In light of the 2023 Thomson Survey Report, which noted an increase in the specialization of compliance roles—57% of professionals agree with this shift—businesses must acknowledge the need for expert guidance. Engaging with legal and compliance professionals ensures that all testing activities align with the latest regulatory requirements and industry standards.
Furthermore, as Pew Research highlights, over half (59%) of consumers claim to have little to no understanding of what businesses do with their data, emphasizing the need for transparency and trust. Given that more than 80% of consumers are likely to cease business with a company following a cyber attack, it is imperative to maintain robust cybersecurity practices to uphold both compliance and consumer trust.
Tools and Technologies for Effective Office365 Security Testing
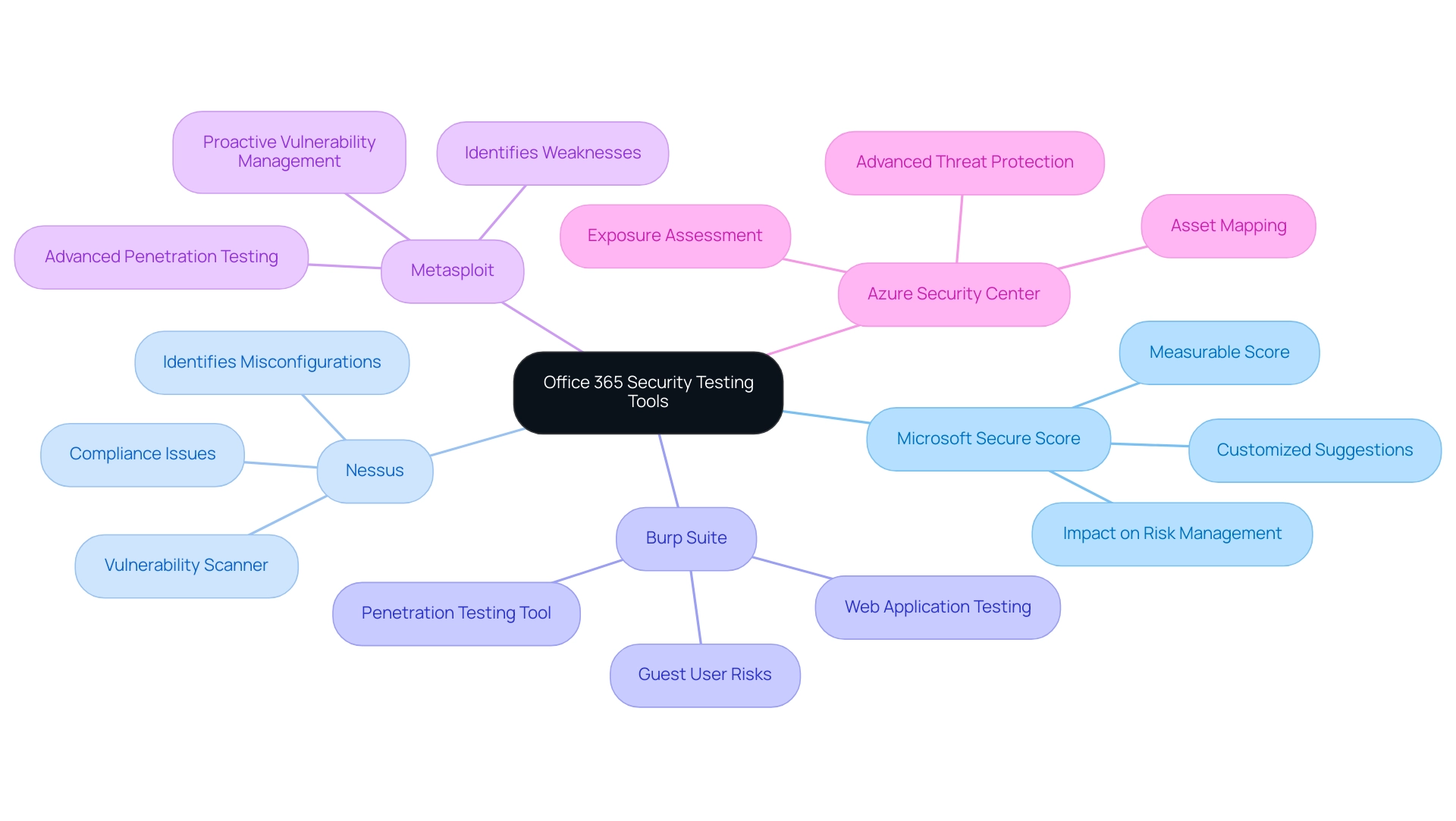
Key Tools for Vulnerability Assessment in Office 365
-
Microsoft Secure Score: This tool provides entities a measurable score derived from their protection configurations, along with customized suggestions for improving their safety stance. Recent statistics show that entities actively using Microsoft Secure Score have experienced notable enhancements in their protective measures, emphasizing its importance in efficient risk management. Furthermore, usage statistics indicate that entities utilizing Microsoft Secure Score have successfully diminished their weaknesses, highlighting its significance in an all-encompassing security plan.
-
Nessus: Renowned for its effectiveness, Nessus is a widely-used vulnerability scanner that excels in identifying vulnerabilities, misconfigurations, and compliance issues across various cloud environments. Its robust capabilities make it a staple for companies looking to maintain a secure infrastructure. As part of a comprehensive asset mapping strategy, the Office 365 vulnerability assessment and penetration testing enables organizations to understand their exposure across different technologies.
-
Burp Suite: As a favored penetration testing tool for web applications, Burp Suite is particularly useful in testing Office 365 applications. Its extensive range of features enables professionals to recognize and tackle potential weaknesses through Office 365 vulnerability assessment and penetration testing, thereby improving the protective framework of Office 365 solutions. This tool is particularly pertinent considering the risks linked to guest users, as emphasized in the case study on guest user invitation risks, where unauthorized access could result in significant breaches of safety.
-
Metasploit: This advanced penetration testing framework enables professionals to identify and exploit weaknesses within systems. Its versatility and depth render it an indispensable instrument for performing comprehensive evaluations and improving overall resilience against possible attacks. By incorporating Metasploit into their Office 365 vulnerability assessment and penetration testing, organizations can proactively tackle vulnerabilities before they are exploited.
-
Azure Security Center: Providing advanced threat protection across hybrid cloud workloads, Azure Security Center seamlessly integrates with Office 365, offering a comprehensive security solution. Its capabilities in asset mapping and exposure assessment are crucial for mitigating data breach risks, as emphasized by recent industry insights. The significance of these abilities cannot be exaggerated, particularly considering the necessity for thorough asset mapping in effective risk management.
In a time when effective vulnerability management is crucial, employing Office 365 vulnerability assessment and penetration testing tools can significantly enhance a company's protective framework. As mentioned by a safety expert, "By remaining informed and proactive, you can protect your entity from potential threats in M365 protection and avert data loss before it escalates into a major problem." Furthermore, Rapid7 InsightVM is ideal for large corporations needing comprehensive analytics and real-time insights, providing customized solutions for entities with intricate protective requirements.
By incorporating these tools and insights, organizations can better navigate the evolving landscape of Office 365 security.
Conclusion
In today's digital landscape, safeguarding organizational data through effective vulnerability assessments and penetration testing is essential. These practices not only identify and prioritize vulnerabilities but also simulate real-world attacks to evaluate the effectiveness of existing security measures. By adopting a structured approach and engaging relevant stakeholders, organizations can ensure that their security assessments are comprehensive and aligned with their business objectives.
Continuous testing and monitoring are critical in light of the increasing cybersecurity threats. As the statistics reveal, the rise in scams and vulnerabilities underscores the necessity of regular assessments to uncover new risks. Implementing automated monitoring tools enables organizations to respond swiftly to potential threats, fostering a culture of vigilance that is vital for maintaining robust security.
Navigating compliance and regulatory requirements further emphasizes the importance of these security measures. Regular assessments not only help identify security gaps but also demonstrate due diligence in meeting stringent guidelines such as GDPR and HIPAA. Engaging with legal and compliance professionals ensures that organizations remain aligned with evolving regulations, thereby reinforcing consumer trust.
Utilizing advanced tools such as Microsoft Secure Score, Nessus, and Metasploit enhances the effectiveness of vulnerability management strategies. By integrating these technologies into their security frameworks, organizations can proactively address vulnerabilities and bolster their defenses against potential attacks.
Ultimately, a commitment to continuous improvement in security practices, coupled with a proactive approach to vulnerability assessments and penetration testing, positions organizations to effectively navigate the complexities of today’s cybersecurity landscape. Prioritizing these strategies is not just an option; it is a necessity for safeguarding sensitive data and maintaining compliance in an increasingly regulated environment.




