Introduction
In an age where digital transformation is paramount, the integrity of cloud security cannot be overstated. As organizations increasingly rely on cloud infrastructures to store sensitive data and facilitate operations, the imperative for comprehensive security assessments becomes clearer.
Recent incidents, such as the staggering breach affecting the Real Estate Wealth Network, which compromised 1.5 billion records, underscore the vulnerabilities inherent in these environments.
Cloud security assessments serve as a critical tool for identifying weaknesses, evaluating risks, and ensuring compliance with regulatory standards. This article delves into the essential concepts of cloud security assessments, providing a structured guide for organizations to navigate the complexities of securing their cloud environments effectively.
By understanding the shared responsibility model and embracing best practices, organizations can not only mitigate risks but also enhance their overall cloud strategy, aligning security initiatives with their business objectives.
Understanding Cloud Security Assessments: Key Concepts and Importance
A cloud computing assessment is crucial for examining the protective measures and protocols within cloud environments, focused on safeguarding sensitive data and ensuring adherence to relevant regulations. The importance of these evaluations is intensified by concerning trends; for example, in December 2023, the Real Estate Wealth Network experienced a breach that exposed 1.5 billion records, emphasizing the urgent requirement for strong protective measures. By conducting a cloud computing assessment, entities can identify vulnerabilities, evaluate risks, and implement necessary controls to safeguard their operations effectively.
Key concepts in this field include:
- Comprehending shared responsibility models, which outline the obligations of both service providers and users.
- Essential practices such as data encryption, identity and access management, and adherence to compliance standards like GDPR and HIPAA.
Moreover, studies show that 82% of organizations regard cost management in the digital realm as a primary challenge, with ransomware incidents rising by 13% over the last five years. This highlights the significance of conducting a cloud computing assessment, which is essential not only to reduce risks but also to improve the overall strategy, aligning protective measures with business goals and strengthening operational efficiency.
As Meeta Sharma aptly puts it,
Using Sprinto, your business can remain agile and innovative without sacrificing protection.
Moreover, recent reports indicate that CloudFlare's automated systems effectively halted over 4.5 million DDoS attacks in the initial three months of 2024, a 50% rise from the prior year, further underscoring the persistent challenges related to safety in online environments. Therefore, a proactive strategy for online security evaluations is essential in today’s intricate environment, where 76% of enterprises use various service providers, making security management more challenging.
Step-by-Step Guide to Conducting a Cloud Security Assessment
-
Define the Scope of the Cloud Computing Assessment: Start by clearly identifying the specific online services and data sets that will be evaluated in the cloud computing assessment. Defining the limits of the evaluation and recognizing pertinent stakeholders are essential to ensuring a thorough review.
-
Gather Relevant Documentation: Accumulate all pertinent documentation related to online service agreements, existing safety policies, and compliance requirements. This foundational information is essential for contextualizing the cloud computing assessment evaluation process.
-
Identify Security Controls: Conduct a thorough evaluation of the existing security measures within the online environment. This assessment should encompass access controls, data encryption methods, and incident response plans to ascertain their effectiveness. Implement robust access control mechanisms, including role-based access control (RBAC) and least privilege access, to restrict unauthorized access to resources.
-
Conduct a cloud computing assessment: Identify potential risks associated with the online services being utilized. This involves assessing both the likelihood of these risks occurring and their potential impact on the organization’s operational integrity.
-
Evaluate Compliance: Review adherence to relevant regulations and industry standards. Ensuring compliance is vital for meeting legal obligations and aligning with best practices in cloud computing assessment.
-
Document Findings and Recommendations: Compile the results of your cloud computing assessment, emphasizing identified vulnerabilities and areas requiring enhancement. Develop practical suggestions to enhance protective measures throughout the organization.
-
Communicate Results: Effectively present your findings to relevant stakeholders, including technical teams and executive management. Utilize clear and concise language to facilitate understanding across diverse organizational levels. As Bhavna B. Sehgal, Senior Manager of Product Marketing for Online Protection at CrowdStrike, states, "Experience across product marketing, product management, and consulting is crucial for effective assessments of online safety."
-
Implement Changes: Collaborate with various teams to put the recommended changes into action. This could involve updating safety protocols, enhancing training programs, or investing in new protective technologies.
-
Oversee and Evaluate: Create a continuous procedure for tracking online protection measures. Frequent evaluations and modifications are essential for sustaining a strong defense strategy and adjusting to changing dangers in the digital environment. Furthermore, in the Testing Phase, it is crucial to confirm that previously recognized issues have been fixed following remediation efforts, ensuring that vulnerabilities have been effectively addressed.
Common Challenges in Cloud Security Assessments
- A major obstacle entities encounter in a cloud computing assessment is the lack of insight into their cloud environments. This obscurity complicates the cloud computing assessment of protective measures, which may lead to potential vulnerabilities. Statistics reveal that 93% of entities express concern over human error leading to accidental exposure, further emphasizing the need for robust visibility solutions. Furthermore, 52% of entities mention insecure interfaces as a significant security risk in their public computing environments (Cloudzero), which emphasizes the essential need for improved visibility. To address these issues, conducting a cloud computing assessment and adopting advanced management tools is crucial. These tools can enhance visibility, providing comprehensive insights that empower organizations to monitor their assets effectively.
Complexity of Shared Responsibility: The shared responsibility model outlines the distribution of responsibilities related to safety between the cloud provider and the customer. However, this model often generates confusion about which party is responsible for specific protective measures. The 2023 Toyota Hack exemplifies the risks associated with misconfiguration errors, where data was exposed for over eight years, underscoring the importance of clear roles and responsibilities. To mitigate this issue, entities should establish clear communication strategies and maintain detailed documentation outlining each party's roles and responsibilities. This clarity is essential in reinforcing accountability and ensuring that security measures are appropriately implemented.
-
Rapidly Evolving Threat Landscape: The ever-changing cyber threat environment poses a persistent challenge for entities. New vulnerabilities emerge regularly, making it difficult to stay informed and prepared. Organizations can combat this by implementing regular training programs and fostering a culture of threat intelligence sharing. By ensuring that their teams are equipped with the latest knowledge on potential risks, organizations can proactively address vulnerabilities before they can be exploited.
-
Resource Constraints: Limited resources, whether related to personnel or budget, can significantly impede the cloud protection evaluation process. Organizations must prioritize critical areas in their evaluations while leveraging automation tools to maximize efficiency. By concentrating on high-risk regions and employing technology to optimize processes, entities can surpass resource constraints and improve their overall defense stance.
Best Practices for Effective Cloud Security Assessments
-
Engage Stakeholders Early: Involving relevant stakeholders at the initial stages of technology assessments is crucial for fostering alignment and securing buy-in across the organization. This collaborative method not only fosters a culture of awareness but also instills a sense of accountability among all parties involved. As highlighted in the 2023 Thales Security Report, 39% of businesses reported experiencing a data breach in their online environment, underscoring the imperative for comprehensive stakeholder engagement to mitigate risks effectively. Moreover, with 72% of firms considering online protection as a future issue, the necessity for proactive involvement is more urgent than ever.
-
Employ a Structure: To improve the uniformity and comprehensiveness of online protection evaluations, organizations should embrace established structures such as NIST or ISO 27001. These structured methodologies provide clear guidelines and best practices, facilitating a comprehensive evaluation process that aligns with industry standards. Utilizing a framework ensures that all critical aspects of cloud protection are addressed systematically, reinforcing the shared responsibility between cloud providers and customers in maintaining safety.
-
Conduct Regular Assessments: A cloud computing assessment should not be regarded as a one-time event but rather as an ongoing practice. Routine cloud computing assessments are crucial for organizations to adapt to the changing threat environment and emerging challenges. According to forecasts, the worldwide software market for protection is anticipated to expand from $29.5 billion in 2020 to around $37 billion by 2026, indicating the growing acknowledgment of the necessity for ongoing vigilance. The adoption of the Zero Trust model, with 80% of enterprises considering or implementing such strategies, further emphasizes the importance of regular assessments to adapt to complex environments.
-
Invest in Training: Providing teams with the essential abilities and understanding to carry out efficient online protection evaluations is crucial. Ongoing training guarantees that personnel remain informed about the latest protection trends and technologies. This investment in human resources is essential for establishing a proactive defense strategy and improving the overall efficiency of evaluations. The impact of Zero Trust principles on the strategies of 30% of organizations emphasizes the need for continuous education to navigate the complexities of contemporary risk environments.
Post-Assessment Actions: Implementing Findings and Continuous Improvement
-
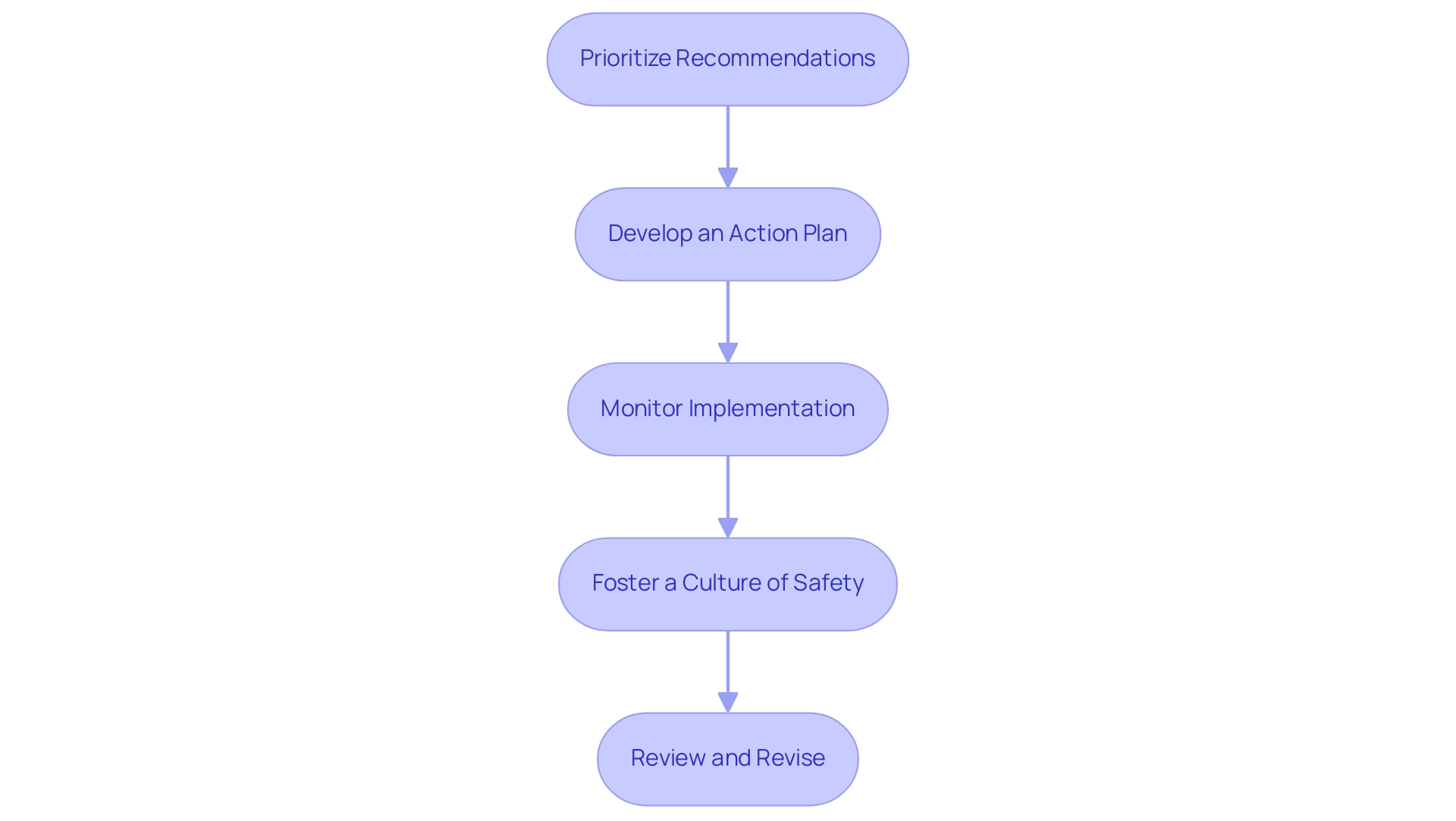
Prioritize Recommendations: Begin by thoroughly reviewing the documented findings from your cloud computing assessment. Prioritize recommendations according to risk levels and their potential impact on the organization. Addressing high-risk vulnerabilities first is crucial in minimizing the threat landscape and protecting sensitive data.
-
Develop an Action Plan: Formulate a comprehensive action plan that specifies distinct steps, timelines, and assigns responsibility to relevant parties for the implementation of the recommendations. Clear communication of this plan to all stakeholders is essential for fostering accountability and engagement.
-
Monitor Implementation: Design a robust monitoring process to track the implementation of the recommended changes. Regular check-ins and progress updates are essential to ensure that actions are executed as intended, enhancing the overall effectiveness of your protective stance.
-
Foster a Culture of Safety: Cultivate an organizational culture that prioritizes safety through ongoing discussions and awareness initiatives. By encouraging training and involvement, you can foster a proactive mindset regarding safety among all employees, thereby decreasing the risk of human mistakes, which is a contributing factor in over 25% of online threats. Significantly, 41% of professionals in risk management have indicated that their entity’s approach to staying updated with current risk management practices for online services relies informally on staff self-training, highlighting the necessity for structured education and training programs.
-
Review and Revise: After executing the changes, conduct a thorough review to evaluate their effectiveness. Make necessary adjustments based on this cloud computing assessment to ensure that continuous improvement remains a cornerstone of your organization’s protection strategy. This commitment to evolving practices is essential in a landscape where cloud breaches have surpassed on-premises incidents. Additionally, consider adopting a Zero Trust Approach, which emphasizes strict access controls and context-based trust, illustrating a proven method for enhancing security posture and achieving significant cost savings per incident.
Conclusion
Cloud security assessments are integral to safeguarding sensitive data and ensuring compliance in an increasingly digital landscape. As highlighted throughout this article, these assessments empower organizations to identify vulnerabilities, evaluate risks, and implement necessary controls to bolster their security posture. The alarming statistics surrounding recent breaches, such as the one involving the Real Estate Wealth Network, serve as a stark reminder of the potential consequences of inadequate security measures.
A structured approach to conducting cloud security assessments is essential. From defining the scope and gathering documentation to identifying security controls and evaluating compliance, each step plays a pivotal role in achieving a comprehensive understanding of an organization’s cloud security landscape. Furthermore, addressing common challenges such as:
- Lack of visibility
- Shared responsibility complexities
- Resource constraints
is crucial for effective assessments. By adopting best practices and engaging stakeholders early, organizations can foster a culture of security awareness and accountability.
Ultimately, the continuous improvement of cloud security practices is vital in adapting to an ever-evolving threat landscape. By prioritizing recommendations, developing actionable plans, and fostering a culture of security, organizations can not only mitigate risks but also align their security initiatives with broader business objectives. The commitment to regular assessments and investments in training will ensure that organizations remain resilient in the face of emerging threats, safeguarding their operations and sensitive data in the cloud.




