Introduction
In the realm of cybersecurity, understanding and adapting to the ever-evolving tactics employed by adversaries is paramount for organizations aiming to bolster their defenses. The MITRE ATT&CK Framework serves as a comprehensive knowledge base that elucidates these tactics and techniques, derived from real-world incidents. By categorizing adversarial behaviors across various environments, this framework not only aids in assessing current security postures but also provides a roadmap for enhancing security operations.
As cyber threats become increasingly sophisticated and rapid, the urgency for organizations to harness the insights offered by the MITRE ATT&CK Framework has never been more critical. This article delves into the framework's foundational principles, practical steps for alignment with security operations, training initiatives for security teams, integration into incident response plans, and methods for evaluating security effectiveness, ultimately equipping organizations to navigate the complex landscape of cybersecurity with confidence.
Understanding the MITRE ATT&CK Framework: A Foundation for Security Operations
The MITER ATT&CK structure stands as a pivotal knowledge repository detailing adversary tactics and techniques derived from real-world observations. This framework is instrumental for organizations striving to assess and enhance their protective stance, particularly when contrasted with the Cyber Kill Chain developed by Lockheed Martin, which focuses on the stages of an attack rather than the tactics used by adversaries.
The ATT&CK Model is meticulously categorized into various matrices tailored to distinct environments, including enterprise, mobile, and cloud settings. Each matrix delineates a spectrum of tactics that adversaries may employ, complemented by specific techniques that organizations can deploy to counter these threats.
Mastery of the framework necessitates an understanding of its architecture, which encompasses diverse tactics such as initial access, execution, and persistence, alongside associated techniques like phishing and malware deployment. This foundational grasp is crucial for aligning operations effectively, as it enables teams to map their controls against recognized threats, thereby identifying and addressing gaps in their defenses.
The influence of the ATT&CK model on an organization’s security stance is significant; it enables security teams to proactively foresee possible attacks and strengthen their defenses accordingly. Significantly, as cybercriminals are now exploiting new industry vulnerabilities 43% faster than the first half of 2023, the urgency for organizations to utilize the ATT&CK Framework cannot be overstated.
The organization emphasizes that the techniques selected for evaluation often reflect those utilized by advanced persistent threats (Apts) in recent incidents, ensuring that the framework remains relevant and aligned with the evolving threat landscape. For example, organizations that have adopted the framework have reported a significant increase in their ability to detect and respond to threats, illustrating its effectiveness in improving operational measures.
Step-by-Step Guide to Aligning Security Operations with MITRE ATT&CK
To align your protection operations with the ATT&CK structure, follow these steps:
-
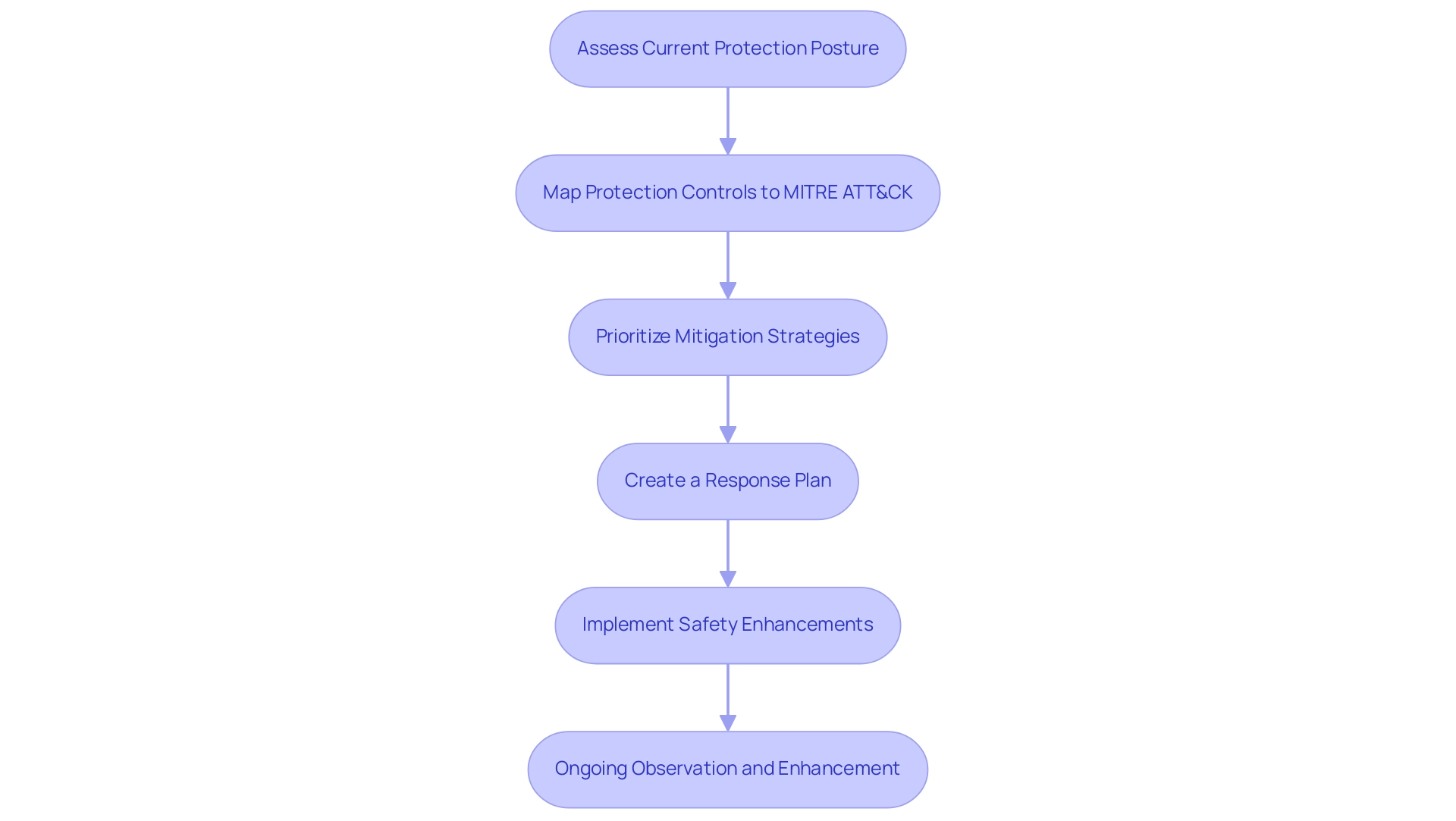
Assess Current Protection Posture: Begin by evaluating your existing measures and controls. Determine which tactics and techniques from the ATT&CK model are already included and where there are deficiencies.
-
Map Protection Controls to MITER ATT&CK: Create a mapping of your current protective measures against the tactics and techniques in the MITER ATT&CK Framework. This will help visualize strengths and weaknesses in your defenses.
-
Prioritize Mitigation Strategies: Based on the mapping, prioritize which techniques need immediate attention. Focus on those that are most relevant to your organization’s threat landscape and risk profile.
-
Create a Response Plan: For each identified gap, create a response plan that outlines the steps to implement necessary protective measures. This plan should include timelines, responsible teams, and required resources.
-
Implement Safety Enhancements: Begin implementing the prioritized protective measures. This may involve deploying new technologies, updating processes, or enhancing employee training programs.
-
Ongoing Observation and Enhancement: Create a continuous oversight process to routinely evaluate the efficiency of your operations against the ATT&CK model. Utilize this feedback to improve your strategies and adjust to changing threats.
By adhering to these steps, organizations can ensure that their operations are aligned with the most recent threat intelligence and best practices, ultimately enhancing their overall protection stance.
Training and Awareness Programs for Security Teams
Investing in training and awareness initiatives for response teams is crucial for organizations looking to effectively utilize the ATT&CK methodology. This strategic approach encompasses several key components:
-
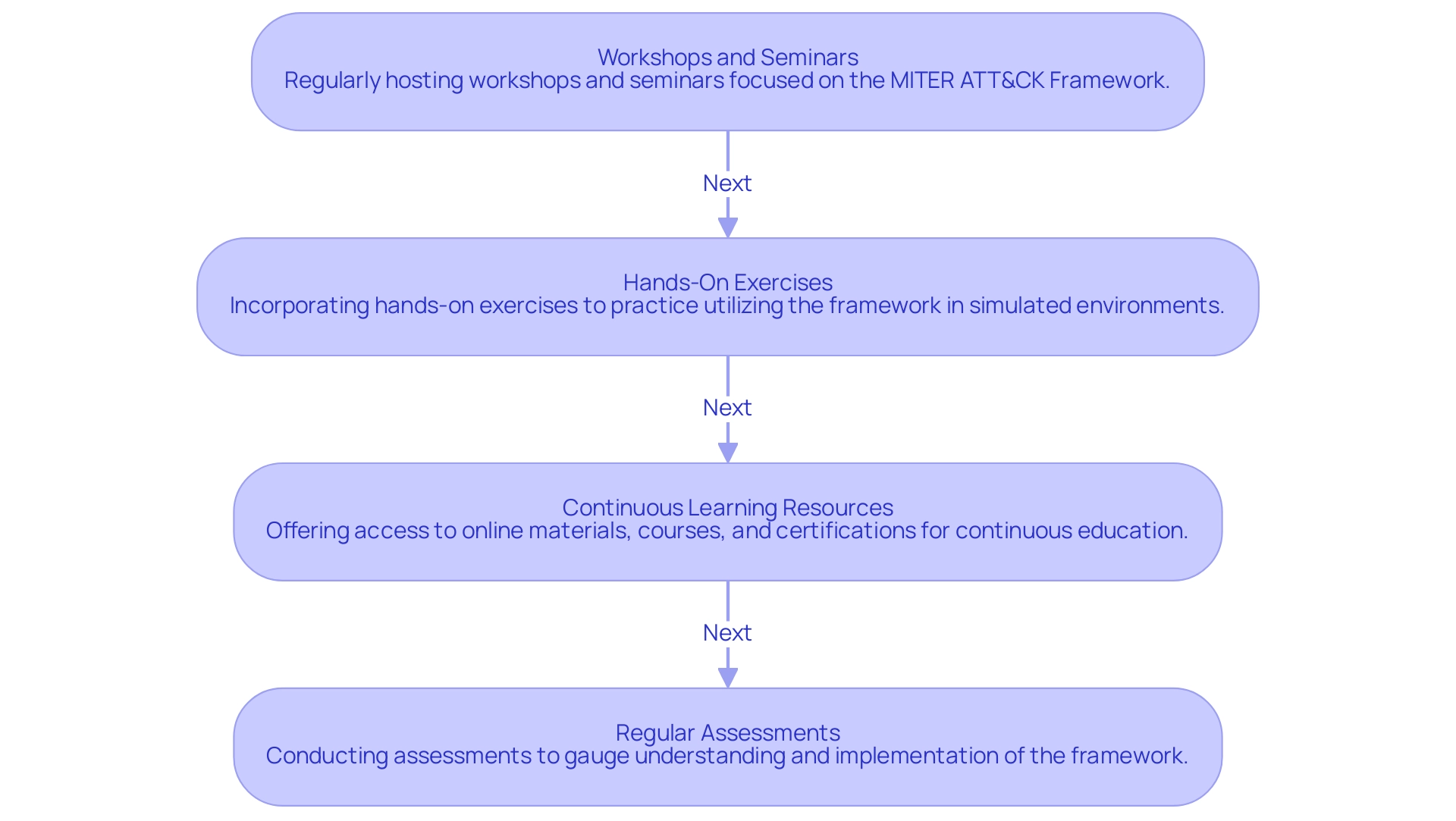
Workshops and Seminars: Regularly hosting workshops and seminars focused on the MITER ATT&CK Framework allows organizations to delve into its application within real-world contexts. Engaging experts who can share valuable insights and best practices enhances the learning experience, equipping teams with the knowledge necessary to combat evolving threats.
-
Hands-On Exercises: Incorporating hands-on exercises enables teams to practice utilizing the framework in simulated environments. This practical experience not only strengthens theoretical learning but also instills confidence in team members as they navigate potential risks.
-
Continuous Learning Resources: Offering access to a range of online materials, courses, and certifications associated with the ATT&CK model and cybersecurity best practices encourages a culture of continuous education. Encouraging team members to pursue continuous learning is vital, particularly given that nearly two-thirds of cybersecurity experts report feeling understaffed, with 20% stating it takes more than six months to find qualified cybersecurity candidates for open roles. This underscores the pressing need for well-trained professionals in the industry.
-
Regular Assessments: Conducting assessments to gauge the team's understanding of the framework and its implementation is crucial. By examining the results, organizations can pinpoint areas that need additional enhancement and customize upcoming training initiatives to tackle these deficiencies efficiently.
Promoting a culture of ongoing education not only improves the abilities of protective teams but also strengthens an organization’s overall defense stance, allowing them to skillfully identify and react to the strategies and methods outlined in the ATT&CK model. Furthermore, this proactive approach is imperative in light of recent findings indicating that IT users are often the most frequent offenders in downloading malicious files, as noted by Terranova Security. This underscores the necessity for comprehensive training across all levels of the organization. Additionally, the significant cybersecurity skills gap, where 63% of companies have unfilled cybersecurity positions, highlights the urgency for workforce development and the impact of understaffing on security operations.
Integrating MITRE ATT&CK into Incident Response Plans
To effectively incorporate the ATT&CK model into your incident response plans, consider the following steps:
-
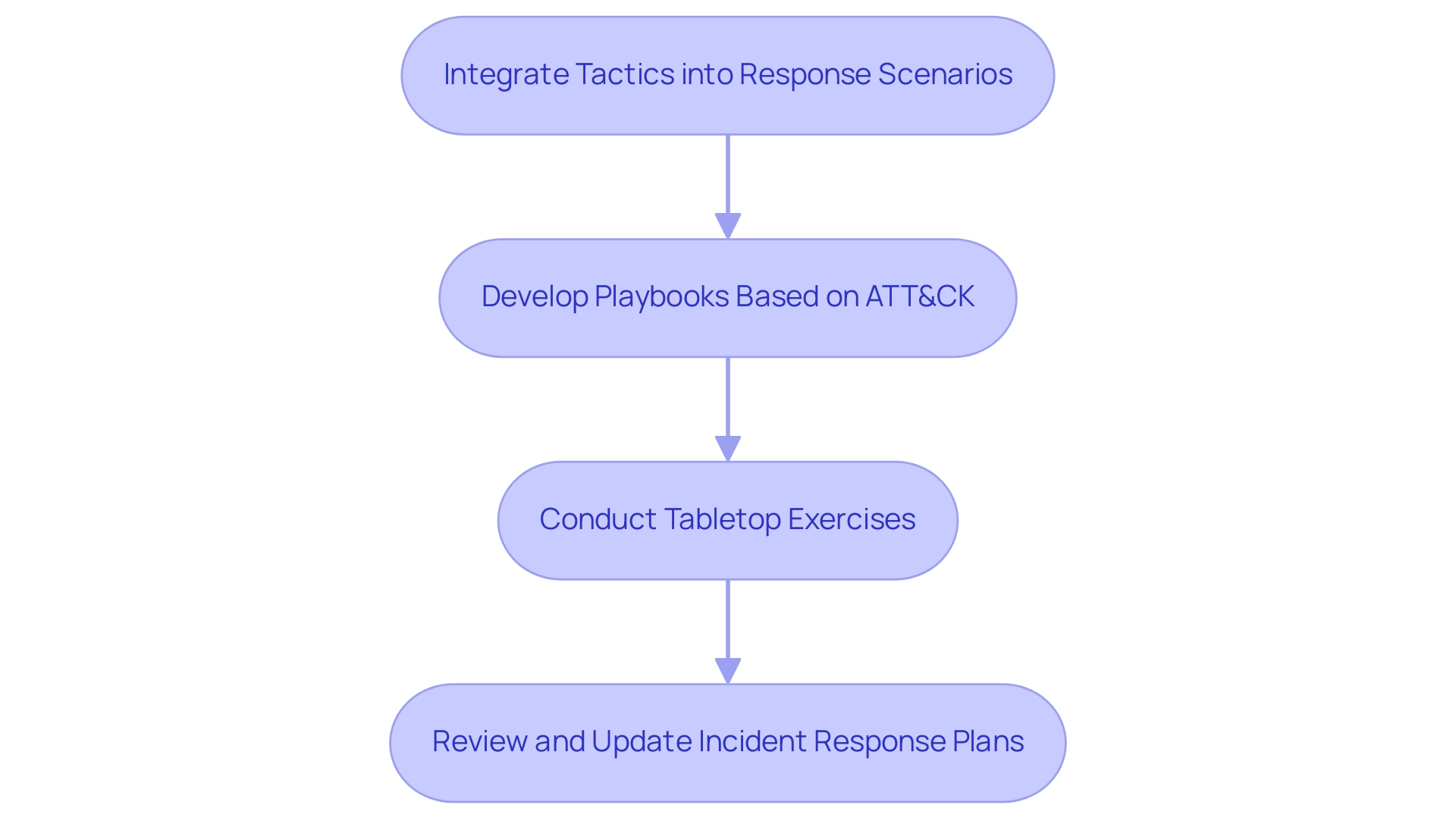
Integrate Tactics into Response Scenarios: When creating incident response scenarios, integrate the strategies and methods described in the ATT&CK model. This ensures that response teams are prepared for known threats.
-
Develop Playbooks Based on ATT&CK: Create incident response playbooks that align with the framework. These playbooks should outline specific actions to take when encountering various tactics and techniques.
-
Conduct Tabletop Exercises: Regularly perform tabletop drills that replicate incidents based on the ATT&CK model. These exercises help teams practice their response strategies and identify areas for improvement.
-
Review and Update Incident Response Plans: Periodically assess and revise incident response plans to reflect changes in the threat landscape and advancements in the ATT&CK methodology. Make certain that every team member is informed of these updates.
By incorporating the ATT&CK structure into incident response strategies, organizations can improve their readiness and capacity to react efficiently to incidents.
Evaluating and Measuring Security Operations Effectiveness
To assess and gauge the efficiency of your protective operations aligned with the ATT&CK model, follow these steps:
-
Define Key Performance Indicators (KPIs): Establish KPIs that reflect the objectives of your operational activities. These may include metrics such as incident response times, number of detected threats, and successful mitigations.
-
Regular Safety Assessments: Conduct regular evaluations of your safety posture using the MITER ATT&CK Framework as a reference. Identify areas of improvement and track progress over time.
-
Feedback Loops: Establish feedback loops that enable teams to learn from incidents and improve their strategies. Utilize knowledge from previous events to guide future enhancements in protection.
-
Reporting and Analysis: Create a reporting system that enables the examination of operations data. Regularly review these reports with stakeholders to ensure alignment with business objectives and to make informed decisions.
By implementing a robust evaluation and measurement process, organizations can ensure that their security operations remain effective and responsive to the evolving threat landscape.
Conclusion
The MITRE ATT&CK Framework serves as a crucial tool for organizations seeking to enhance their cybersecurity defenses in an increasingly complex threat landscape. By understanding the framework's architecture, organizations can effectively assess their current security posture, identify gaps, and implement targeted strategies to mitigate risks. The structured approach of mapping security controls to the framework not only highlights strengths but also prioritizes areas needing immediate attention, ensuring that security operations are aligned with the most relevant threats.
Investing in training and awareness programs for security teams is equally vital. Regular workshops, hands-on exercises, and continuous learning initiatives empower personnel to adeptly navigate the intricacies of the MITRE ATT&CK Framework. This commitment to education fosters a culture of preparedness, enabling teams to recognize and respond to adversarial tactics with increased confidence and efficiency.
Furthermore, the integration of the MITRE ATT&CK Framework into incident response plans enhances an organization's ability to address security incidents effectively. By developing tailored playbooks and conducting realistic tabletop exercises, organizations can ensure their response strategies are both practical and adaptable to the evolving threat landscape.
In conclusion, leveraging the MITRE ATT&CK Framework is not merely a best practice; it is a necessity for organizations aiming to stay ahead of sophisticated cyber threats. By systematically aligning security operations with the framework, investing in team training, and integrating it into incident response protocols, organizations can significantly bolster their defenses. The proactive adoption of these strategies will ultimately lead to a more resilient security posture, equipping organizations to confront and mitigate the ever-present risks posed by cyber adversaries.




