Introduction
The CIS Controls have evolved into a comprehensive framework designed to fortify organizations against cyber threats. From asset management to data protection, these controls provide a robust security posture. The framework's adaptability is reflected in its approach to software lifecycle management and third-party security assessments.
As technology advances, the CIS Controls emphasize the need for security measures to be integrated from the onset. By following these controls, organizations can navigate the treacherous waters of cybersecurity. The integration of the CIS Controls with other frameworks such as ISO 27001 and NIST CSF ensures comprehensive protection.
Leveraging the right tools and resources, organizations can effectively implement the CIS Controls and enhance their security posture.
History and Evolution of CIS Controls
The CIS Controls, with their inception rooted in addressing the dynamic nature of cyber threats, have evolved into a comprehensive framework designed to fortify the technological fortresses of organizations. At first, the emphasis was on the fundamentals of asset management and access restriction, and now these measures encompass detailed directives for data, network, and application safeguarding. The framework is meticulously structured into foundational categories, each building upon the other to provide a robust protection position. Starting with fundamental measures that establish the groundwork for protection, the framework advances to more intricate suggestions for safeguarding against sophisticated cyber attacks. Organizational controls, the third tier, are focused on integrating protection into the very structure of an organization, covering everything from policy development to awareness training.
The evolution of the CIS Measures over time is also evident in their approach to software lifecycle management and third-party evaluations, guaranteeing that every piece of software and every external service provider adhere to strict standards. This is vital considering recent cybersecurity incidents, like the identified network anomaly at the ICC, which emphasized the necessity for ongoing vigilance and enhancement in protective measures.
As technology progresses, the CIS guidelines have maintained stride, recognizing the crucial role of safeguarding in every IT expenditure, whether it's a new laptop or the latest software, which must be equipped with protective measures right from the beginning. The white paper's latest update echoes this sentiment, urging software manufacturers to take a 'secure-by-design' approach. This means creating products that are inherently resilient to cyber threats, incorporating protection as a primary consideration throughout the development process, and promoting radical transparency and accountability, including the proactive sharing of information on vulnerabilities.
The CIS guidelines not only serve as a guideline but also as a beacon for organizations to navigate the treacherous waters of cybersecurity. The instance of the U.S. state government department, with its efficient yet flexible IT team, showcases the implementation of the CIS Measures in a real-life situation, ensuring the protection of over 1,500 devices with a dedicated emphasis on network access management and firewalls.
Promoting a collaborative approach, the CIS Measures aim to bring together endeavors among different stakeholders, as emphasized by CISA's position as a national coordinator for infrastructure protection. The statistical data from OHSS and CISA's annual reports offer insights into the broader cybersecurity landscape, emphasizing the collective endeavor to mitigate risks and enhance resilience. This development of the CIS, from basic protective measures to a multi-faceted defense approach, encompasses the continuous dedication to protecting our digital ecosystem from the constantly changing cyber risks.
Key Components of CIS Controls
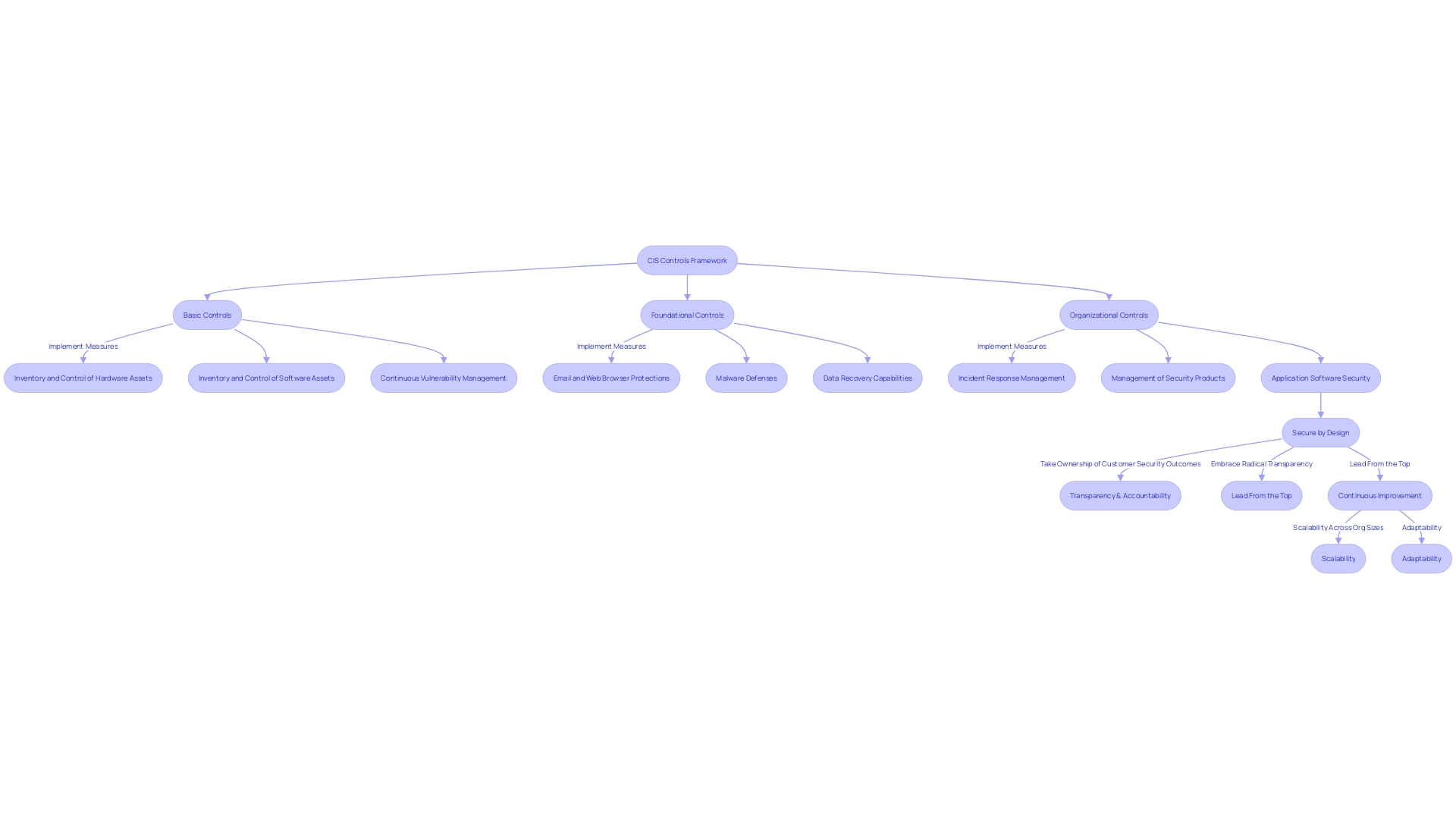
The CIS (Center for Internet Security) Controls offer a strategic framework for enhancing an organization's cybersecurity defenses, effectively becoming the foundation of a strong protective stance. The management is meticulously arranged into three main divisions: Basic, Foundational, and Organizational. The Fundamental measures handle the vital aspects such as access management, asset supervision, and vulnerability supervision, functioning as the foundation for any cybersecurity program. The Foundational measures build upon this base, providing detailed guidance for securing data, networks, and applications. Finally, Organizational controls emphasize the importance of holistic protection management practices, including the development of comprehensive policies and training programs.
Demonstrating the scalability and adaptability of the framework across different organizational sizes, a state government department with a dedicated team of 15 IT professionals effectively manages the protection of approximately 1,500 devices. The framework's relevance is further underscored by the recent update known as 'CSF 2.0,' which reflects a collaborative, two-year revision process incorporating stakeholder feedback to ensure the framework meets the evolving cybersecurity landscape.
To ensure the continuous improvement of cybersecurity measures, the framework encourages the 'secure-by-design' approach, advocating for products that inherently protect against cyber threats without placing the onus solely on the end-user. Embracing this approach, alongside a commitment to radical transparency and accountability, can significantly enhance a product's protection lifecycle and help establish robust incident response capabilities. This philosophy is echoed in the protection community, with industry experts emphasizing the necessity for manufacturers to prioritize safety in their design process, thereby contributing to a safer digital environment.
Recent advancements in cloud service offerings, like the introduction of the initial Cloud Federation Catalogue by CISPE, emphasize the growing requirement for compatible digital services that comply with rigorous data protection and cybersecurity standards, in line with the framework of CIS. As protection becomes a pivotal aspect of organizational success, the CIS Guidelines offer a structured pathway to achieve and maintain a fortified security stance, reflecting a comprehensive approach to cybersecurity that is essential in today's digital world.
How CIS Controls Work
The CIS Controls provide a strategic framework that classifies measures into three distinct groups: Basic, Foundational, and Organizational. Fundamental measures are crucial for establishing a sturdy foundation for safety, emphasizing important aspects such as access management, asset supervision, and vulnerability oversight. Fundamental measures extend beyond this foundation with comprehensive guidance on protecting data, networks, and applications. Organizational controls, meanwhile, emphasize protection management across the enterprise, including policy development and safety training, among other practices.
For instance, a state government department with a 15-person IT team successfully monitors around 1,500 devices, demonstrating how a modest-sized team can effectively manage a significant technology stack. Their approach includes continual evaluation of new technologies, which demonstrates the significance of adaptability in safeguarding practices. Furthermore, the call for responsibility and openness in product safeguarding, as emphasized in recent white papers, underscores the necessity for software producers to give priority to protective results for their customers. This secure-by-design approach ensures products are inherently more resilient against cyber threats.
Moreover, research by ASIS on access provides valuable benchmarks, indicating that a combination of technology, policies, and procedures is necessary to regulate secure access within facilities. The study of over 1,000 professionals in the field emphasizes the importance of effective access control systems as a fundamental part of a physical safety strategy. These observations correspond with the CIS emphasis on strong access management as an important measure.
Implementing the CIS measures not only assists organizations in tackling the crucial aspects of cybersecurity but also aligns with global standards. The Common Criteria for Information Technology Evaluation offers a structured process for certifying properties of products, promoting an international benchmark for features and capabilities.
Implementation Groups and Resource Allocation
Optimizing the implementation of CIS Measures is a strategic process that requires precise resource allocation and the establishment of specialized teams. These groups are crucial for ensuring that each control is effectively addressed and that protective measures are comprehensive. To illustrate, Chess.com, with its vast user base of over 150 million chess enthusiasts, leverages the implementation of CIS Controls to safeguard its digital platform. James Kelty, the Head of Infrastructure at Chess.com, emphasizes the importance of expanding and maintaining a resilient IT infrastructure to support their global community. He also highlights the use of RackConnect Global to efficiently scale their infrastructure needs with the Google Cloud Platform.
Similarly, a U.S. state government department, with a modest IT team of 15 members overseeing 1,500 devices, showcases agility in adopting new technologies to fortify their cybersecurity posture. These examples underline the significance of tailoring the implementation groups to the organization's scale and resources.
Recent data from January to July 2023 shows that only 0.1% of the ninety-five billion analyzed events were classified as alarms, with just 9.7% flagged for review. This highlights the crucial role of AI in event detection and prioritization. Furthermore, an industry report highlights a worrisome fluctuation in IT safety budget allocations across various sectors, supporting the need for a more uniform and committed investment in cybersecurity.
The most recent white paper on cybersecurity highlights the necessity of possession, clarity, and guidance in guaranteeing customer safety results. It also stresses the need for 'secure-by-design' products, which are inherently resilient against cyber threats. These principles are echoed in quotes from leading authorities, such as the National Telecommunications and Information Administration's advocacy for a comprehensive Software Bill of Materials (SBOM).
Statistics from various organizations emphasize the need for structured security management, with some lacking written security plans or designated security committees. This emphasizes the need for a systematic approach to cybersecurity, including the careful planning and implementation of CIS Measures, to safeguard against possible cyber threats efficiently.
New Features in CIS Controls v8.1
The CIS Controls, a critical framework for cybersecurity, have undergone significant updates to reflect the evolving threat landscape and best practices in the industry. The most recent update, release 8.1, strengthens organizational defenses against cyber threats by introducing streamlined controls, guaranteeing that vital protective measures are both effective and up to date. These improvements are especially important for sectors undergoing fast digital changes, like banking, where the importance of data protection and regulatory adherence is extremely high.
For instance, M&T Bank, with its rich 165-year history, has embraced a digital-first approach, necessitating stringent Clean Code standards to ensure the integrity, performance, and maintainability of its software. Similarly, state government IT departments, though smaller in scale, must continuously evaluate and integrate the newest technologies to safeguard a vast network of devices. The CIS Controls v8.1 provides a structured and comprehensive approach for such organizations to strengthen their posture.
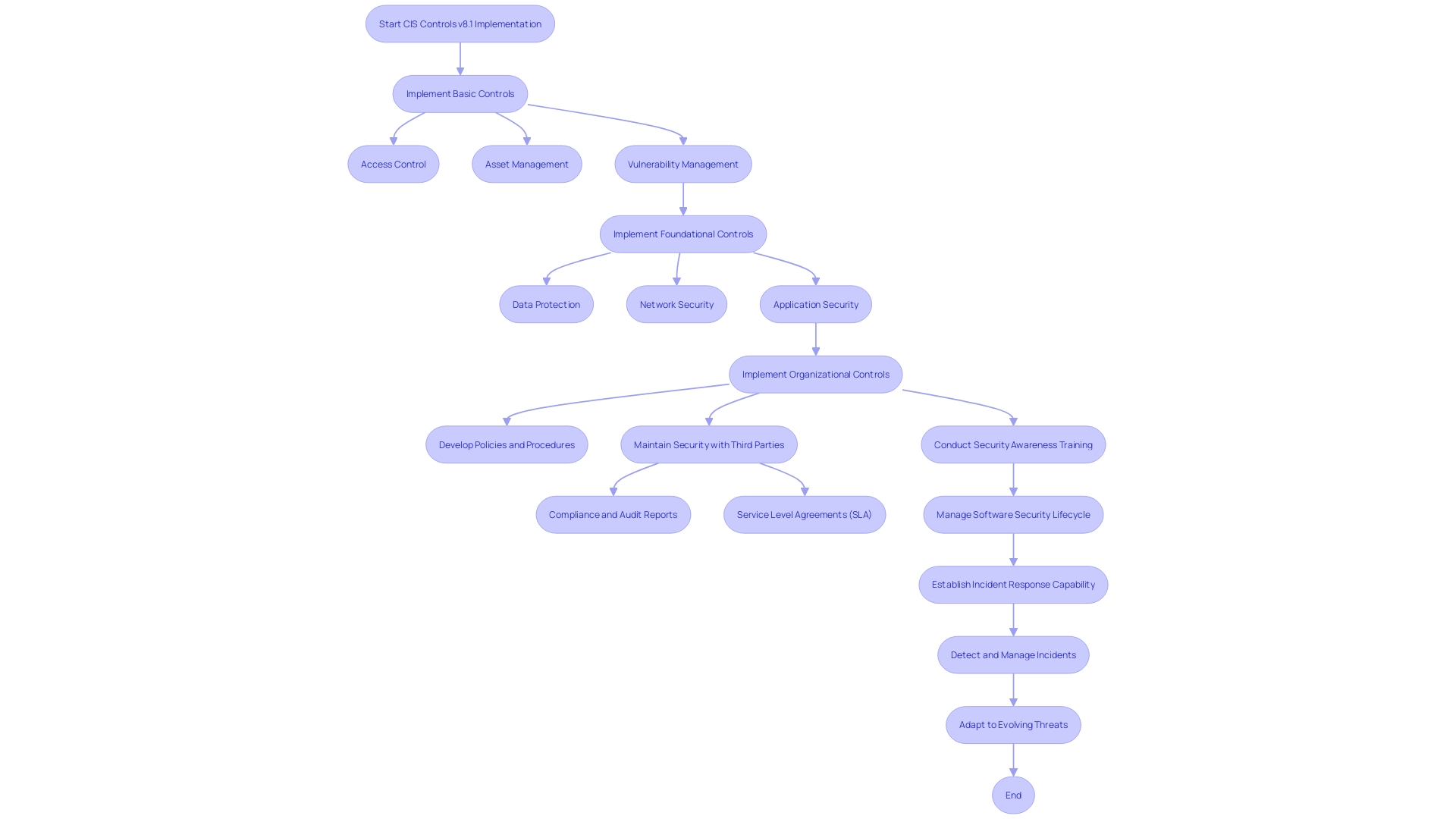
The measures are categorized into fundamental areas, emphasizing on essential protective actions like access management and vulnerability handling, and expanding into higher-level domains such as data and network safeguarding, as well as organizational procedures necessary for maintaining a strong framework. The reduction from 20 controls in version 7 to 18 in version 8 reflects a more concise and targeted strategy, allowing organizations to prioritize and implement the most critical defenses first.
This CIS update also echoes the principles highlighted in a recent white paper advocating for secure-by-design software products. It highlights the necessity for complete openness, responsibility, and organizational guidance in practices related to safeguarding, aligning with the suggestions for software producers to actively incorporate protection into their development procedures.
Real-world incidents, such as vulnerabilities identified by CISA, underscore the importance of adopting and maintaining up-to-date security measures. By following the most recent CIS guidelines, organizations can reduce vulnerability to cyber threats and adopt recommended practices such as segregating vital networks and employing secure methods for remote access. The CIS v8.1 serves as a strategic blueprint for organizations to not only respond to but also anticipate and neutralize potential cyber threats.
Governance Security Function and Alignment with NIST CSF 2.0
The seamless integration of the CIS Measures with the NIST Cybersecurity Framework (CSF) 2.0 is a strategic imperative for crafting a robust protection architecture. As landscapes evolve and threats become increasingly sophisticated, it's clear that a single framework is not sufficient. The inclusion of a new 'Govern' function in the CSF 2.0 underscores the importance of governance in cybersecurity management. This progressive inclusion aligns seamlessly with the governance protection function crucial for implementing the CIS Measures effectively.
Consider the practical application of these frameworks in a U.S. state government department, where a lean IT team of 15 handles the protection of approximately 1,500 devices. Here, the integration of the CIS Controls with the NIST CSF has proved invaluable. By utilizing a cohesive safety strategy, this department gains from a centralized dashboard, thanks to Armis, which speeds up daily operations, simplifies vulnerability prioritization, and proactively seals safety gaps.
The NIST CSF, a decade after its initial release, continues to serve as a comprehensive set of guidelines with its five core functions: Identify, Protect, Detect, Respond, and Recover. It has helped organizations of all sizes to comprehend, arrange, and enhance their posture regarding protection using a shared language. The latest iteration, CSF 2.0, enhances this foundation with its emphasis on continuous cybersecurity improvement and proactive risk management.
As asserted by industry experts, the principles of cybersecurity need to shift towards manufacturers taking greater ownership of secure outcomes and fostering a culture of radical transparency. This change in approach towards secure-by-design products is in line with the objectives of both the CIS and the NIST CSF, promoting the creation of inherently secure environments that can adapt to the ever-changing threat landscape.
Asset Classifications and Mappings to Safeguards
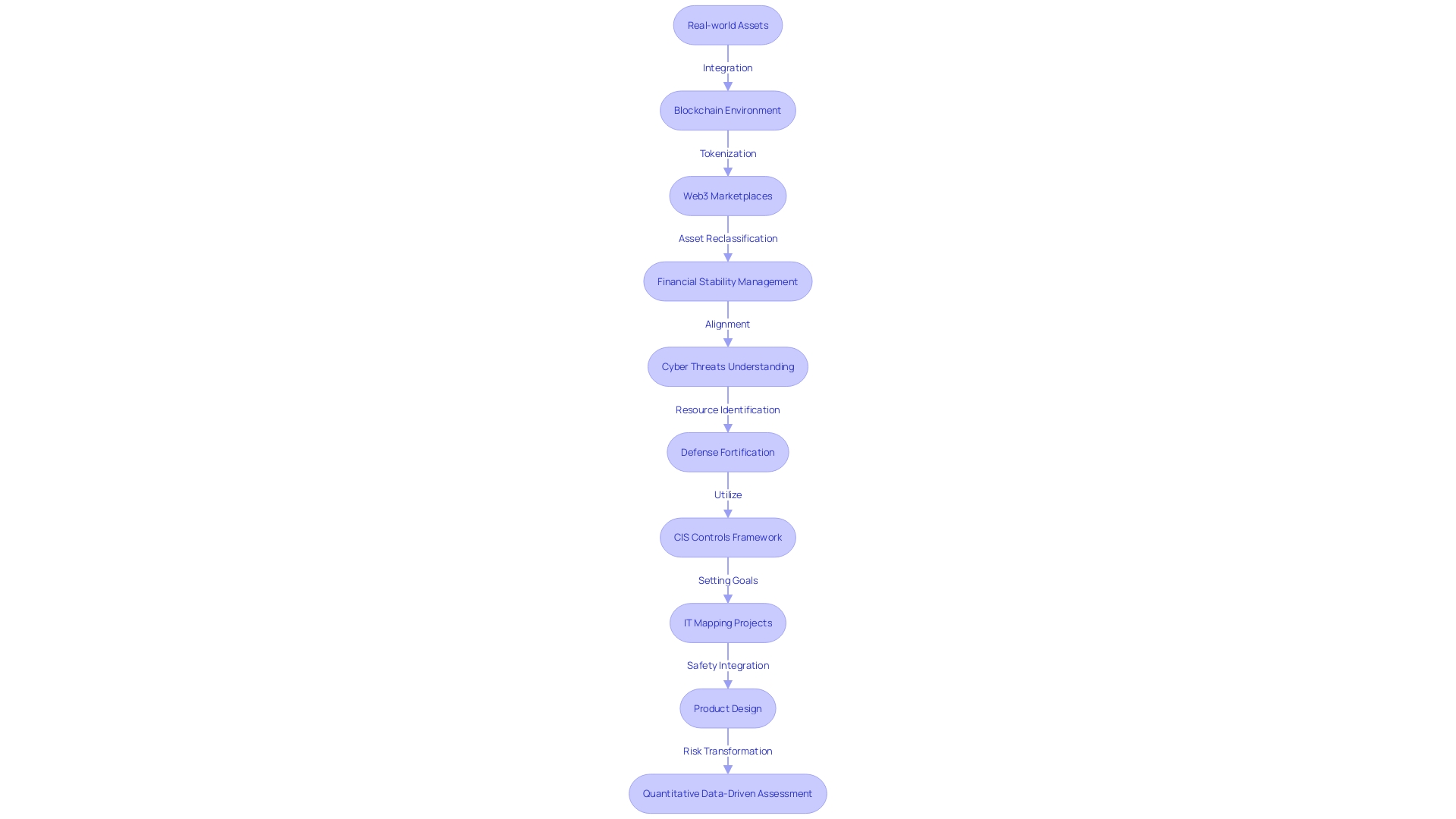
Asset classification and the effective mapping of cybersecurity controls are crucial for any organization aiming to enhance its protection. Prompted by the dynamic nature of cyber threats, a strategy that has gained traction is the integration of real-world assets (RWA) into more secure and less volatile blockchain environments. This innovative approach, illustrated by initiatives where tangible assets such as real estate are tokenized for exchange in Web3 marketplaces, offers a compelling blueprint for asset management in the digital realm.
In light of these developments, organizations must align their asset classification with an understanding of their operational landscape. This involves recognizing the potential targets and vectors for cyber threats, as well as identifying necessary resources to fortify their defenses. The CIS Controls framework becomes instrumental here, guiding entities to not only recognize but also systematically manage their digital and physical assets.
To put this into context, recent shifts in the financial sector underscore the relevance of strategic asset management. A notable example is a bank altering its business model for a sub-portfolio of private corporate bonds, transitioning from 'held to collect and sell' to 'held to collect', aiming for stability and structural reformation. Such a move emphasizes the significance of tactical asset reclassification and its impact on an organization's financial robustness.
Goal setting is the cornerstone of any IT mapping project. By establishing the objective and desired results of the mapping, organizations can extract actionable insights and prioritize protective measures effectively. Whether it's evaluating incident response times, mission impact, or the bottom line, the goal is to present data in a comprehensible manner that facilitates informed decision-making.
The importance of integrating safety into the structure of product design is emphasized by industry professionals who support a 'design-with-safety' approach. This principle is not limited to traditional software but extends to AI systems and models, reinforcing the notion that security must be an organizational priority across all technological domains.
In summary, an organization's ability to handle and protect its assets is enhanced by a well-planned mapping of CIS Measures. This strategic approach is underpinned by a thorough understanding of one's assets, the adoption of secure-by-design principles, and the transformation of qualitative risk assessment into quantitative data-driven practices. By doing so, organizations can effectively navigate the complexities of cybersecurity and safeguard their operations against an ever-evolving threat landscape.
Enhanced Safeguard Descriptions and Clarifications
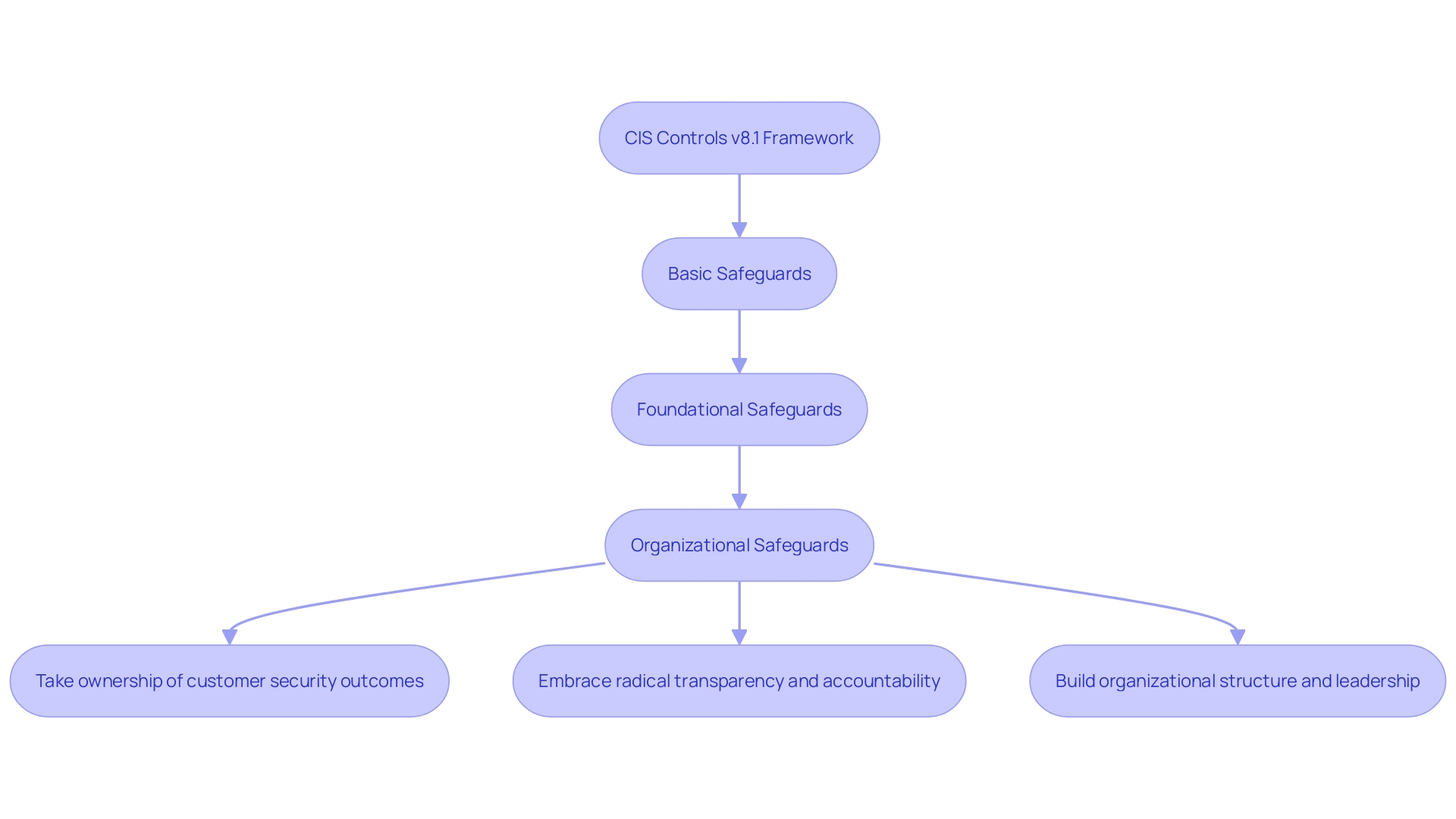
The most recent version of the CIS Controls v8.1 not only offers improved safeguard descriptions but also provides crucial clarifications, enabling a deeper understanding of the requirements of each safeguard. This transformation is essential for organizations aiming to strengthen their defensive position, as accurate execution of the measures is crucial. The CIS Framework classifies the various measures into Basic, Foundational, and Organizational groups, each increasing in detail and complexity. Fundamental measures establish essentials like access management and asset management, while Foundational measures delve deeper into data and network protection. Organizational measures extend to broader practices necessary for upholding a strong stance on protection.
Real-world applications of these measures exemplify their significance. For example, a state government department, despite its small scale, utilizes these measures to supervise the protection of 1,500 devices. Similarly, a global hospitality leader, IHG Hotels & Resorts, incorporates these principles by shifting to a secure SD-WAN solution, streamlining network management and improving safety. Furthermore, the consolidation of safety and networking by Armis using a unified dashboard exemplifies the efficacy of these controls in real-time threat prioritization and vulnerability management.
Backing this framework, the most recent updates promote a secure-by-design approach, urging software manufacturers to proactively embed safety into their products, reflecting an ethos where transparency, accountability, and leadership are paramount. This aligns with the goals of the Office of Homeland Security Statistics, which underscores the importance of comprehensive security management, as evidenced by their detailed reports on security coordination within organizations.
As organizations navigate the complexities of cybersecurity, the CIS guidelines v8.1 serves as a beacon, guiding them towards a secure, resilient future. The thorough guidance provided by these measures, combined with the insights from industry leaders and government institutions, highlights the framework's significance in today's rapidly changing threat landscape.
Best Practices for Implementing CIS Controls
The CIS (Center for Internet Security) Controls represent a pivotal set of practices designed to safeguard organizations from cyber threats. These measures are systematically organized into three separate categories. The initial group, referred to as Foundational controls, are fundamental and include essentials like access management, asset oversight, and vulnerability oversight. The second set, Implementation measures, delve deeper, offering advanced guidance on securing data, networks, and applications. Finally, Organizational measures illuminate comprehensive management of safety throughout businesses, encompassing the development of guidelines and the significance of safety education.
In practice, the effectiveness of these controls has been shown by a U.S. state government department, which, despite its lean IT team of 15 managing 1,500 devices, has maintained strong protocols for its operations. Their success can be attributed to a strategic implementation of CIS Controls, coupled with a thorough understanding of their IT landscape.
Recent industry insights underscore the necessity for adopting a 'secure-by-design' approach. A white paper promotes three fundamental principles: ownership of customer protection outcomes, radical transparency, and developing an organizational structure conducive to safeguarding. This philosophy encourages software manufacturers to develop intrinsically safe products, thereby transferring some of the protection responsibilities from end-users. It emphasizes the significance of integrating protection into the DNA of software development â a notion also relevant to AI systems and models.
Leaders in the field, according to industry stories, are acknowledging the significance of taking a proactive approach instead of a reactive one when it comes to safeguarding measures. The necessity to incorporate protection into organizational and product strategies is more pertinent than ever, indicating a fundamental change in how safety is perceived and implemented across the tech industry.
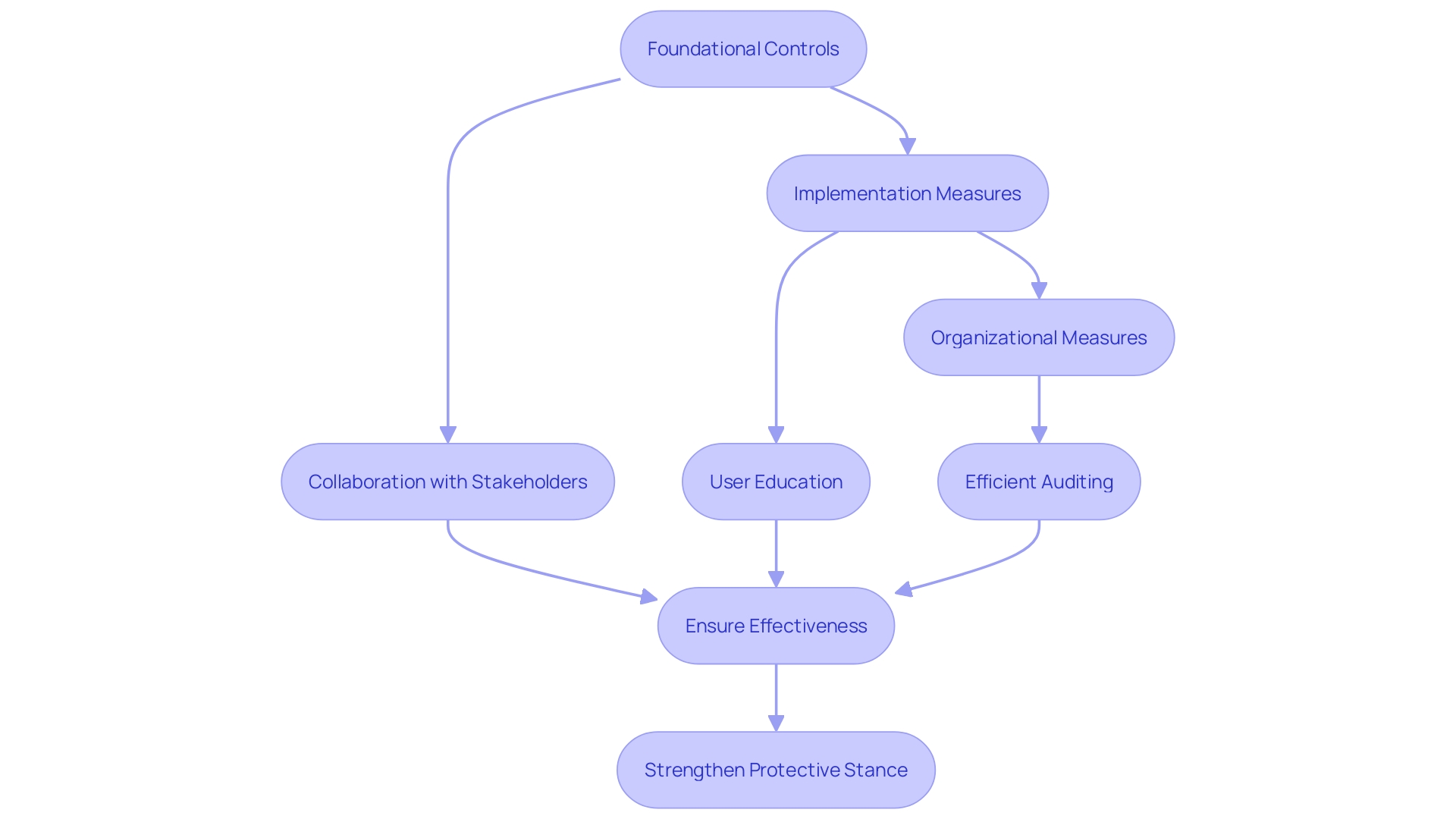
As organizations begin to implement CIS Measures, it is essential to not only concentrate on the technical elements but also to cultivate collaborations with important stakeholders, guaranteeing that systems are supported by strong policies, user education, and efficient auditing to confirm their effectiveness. The journey towards a strengthened protective stance is continuous and demands an adaptive strategy aligned with the evolving threat landscape.
Benefits of Using CIS Controls for Enhanced Security
Implementing the CIS Controls can significantly enhance an organization's posture by mitigating cyber risks and improving incident response capabilities. For example, a U.S. state government department, with a dedicated IT team overseeing 1,500 devices, could streamline its management of protection and reduce downtime for critical protection devices such as firewalls by implementing these controls. Similarly, global hospitality leader IHG Hotels & Resorts experienced significant cost savings and operational efficiencies by integrating networking and protection functions within its SD-WAN solution from Fortinet, highlighting the effectiveness of the CIS Framework in diverse environments.
The recent guide published by the CIS Controls team, 'The Cost of Cyber Defense: Implementation Group 1 (IG1),' offers insights into how organizations can develop cyber hygiene cost-effectively, emphasizing the importance of a reliable inventory of hardware, software, and data for a robust architecture. Furthermore, the document published by the team highlights the importance for software manufacturers to prioritize the design of products with safeguarding in mind, thereby guarding against cyber threats proactively.
The principles of secure-by-design products and embracing radical transparency are crucial for building trust in technology solutions. These principles also apply to the realm of artificial intelligence (AI), where the same safety considerations must be applied to AI systems and models. As noted by CISOs in a global survey, proactive defense strategies are essential, and tools like XDR (Extended Detection and Response) provide the necessary visibility for early threat detection, which is critical in bolstering organizational cyber resilience.
In general, the strategic implementation of the CIS Measures provides companies with the resources and structures needed to successfully navigate the changing environment of cyber threats, guaranteeing they can keep operating with assurance and protection.
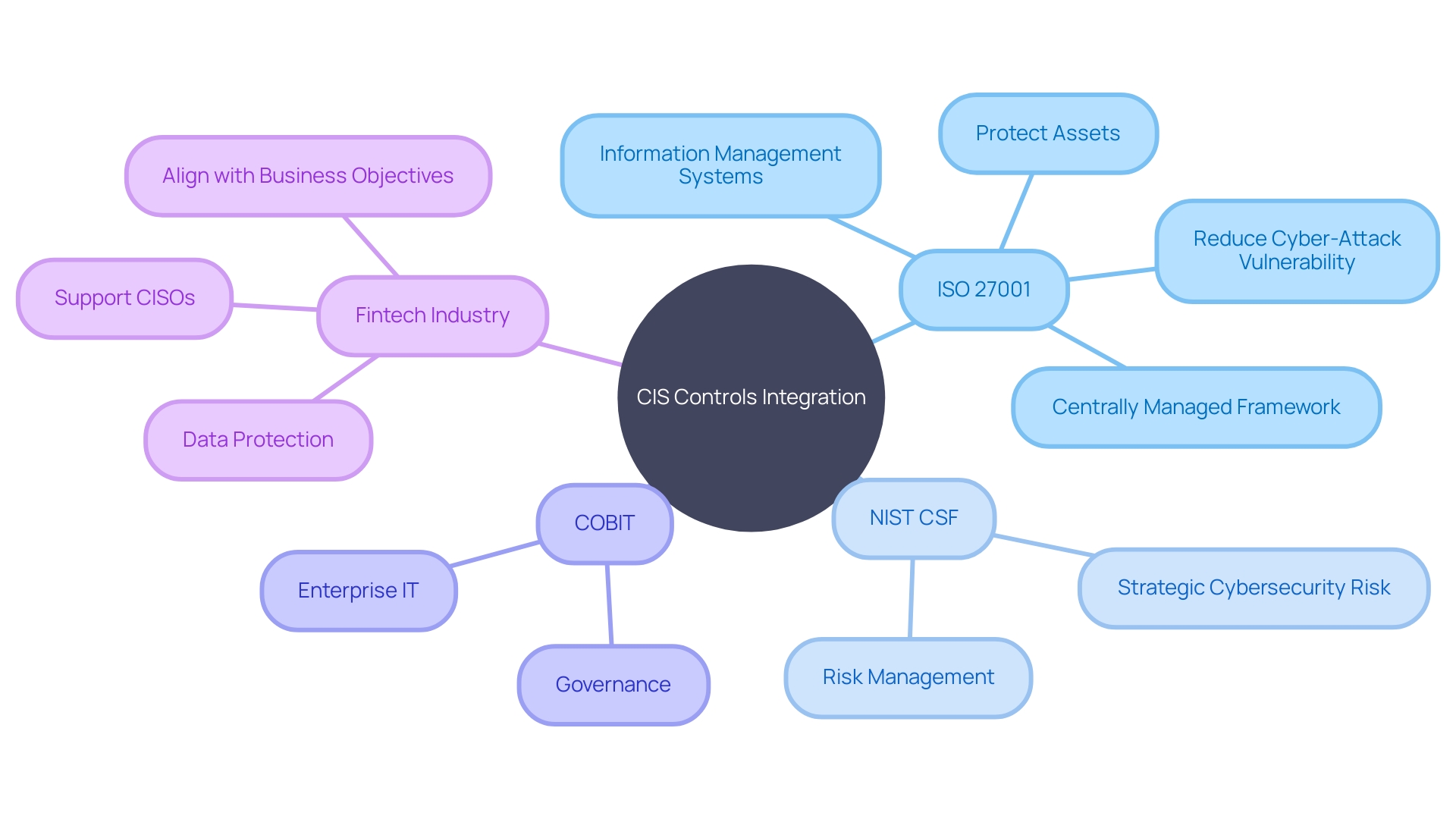
Integration with Other Security Frameworks
Incorporating the CIS Controls with globally recognized frameworks forms a robust foundation for organizations aiming to safeguard their digital environments. ISO 27001, for example, serves as a benchmark for information management systems, outlining a complete set of measures in Annex A, which organizations can customize according to a detailed risk evaluation. These controls align well with the CIS's pragmatic approach to safeguarding, allowing for a harmonized set of practices that enhance an organization's posture.
Likewise, systems such as the NIST Cybersecurity Framework (CSF) offer a strategic perspective on handling and reducing cybersecurity risk that complements the tactical advice provided by CIS measures. COBIT, with its emphasis on governance and enterprise IT, provides a framework that can be aligned with CIS measures to guarantee that security measures are not only technically efficient but also optimized in the context of business goals.
Notably, fintech industry expert Sergey Kondratenko highlights the importance of ISO standards in ensuring consistent and secure methods across industries. ISO standards in FinTech, for instance, focus on important aspects like risk management and data protection, which are essential to the CIS guidelines. As organizations implement cutting-edge technologies like AI, IoT, and big data analytics, the convergence of CIS Controls with these established frameworks ensures comprehensive protection against evolving threats.
The implementation of these integrated safety measures decreases susceptibility to cyber-attacks, protects vital resources like intellectual property and financial data, and establishes a centrally managed protection framework. This strategic alignment of defense frameworks not only strengthens defenses but also supports the expanded role of CISOs in guiding cybersecurity strategies in line with overarching business objectives.
Tools and Resources for CIS Controls Implementation
Utilizing the appropriate tools and resources is crucial for the effective implementation of CIS Measures. Organizations must develop a dependable inventory of their hardware, software, and data to build an efficient architecture, which acts as the basis for implementing CIS Measures. Effective metrics and indicators are essential for organizations to gauge the effectiveness of their security measures. A set of tailored assessment tools, such as commercial Governance, Risk Management, and Compliance (GRC) platforms, can furnish organizations with actionable insights into the status of their CIS Controls implementation. For example, using these assessment tools to address the five safeguards under control 1 (Inventory and Control of Enterprise Assets), an organization can ensure a detailed hardware asset inventory is maintained.
The journey towards robust cybersecurity is not without its challenges. One of the most significant is securing the endorsement and support of top-level management. This support is crucial for accessing and integrating data across various organizational silos and setting realistic timelines for the completion of protection projects. Support at the C-level helps in overcoming bureaucratic hurdles that may impede the gathering of necessary data, ensuring the smooth advancement of the CIS implementation process.
The evolving regulatory landscape, such as the European Unionâs Cybersecurity Certification Scheme for Cloud Services (EUCS) and Japan's Information System Security Management and Assessment Program (ISMAP), demands that Software-as-a-Service (SaaS) providers adhere to stringent safety and privacy standards. These regulations emphasize the importance of strong protective frameworks like the CIS Controls.
Organizations also have access to a comprehensive knowledge base of Software Supply Chain Security resources, including the Minimum Elements for a Software Bill of Materials (SBOM) from the National Telecommunications and Information Administration (NTIA). This repository is a testament to the significance of secure-by-design principles, as it equips software manufacturers with necessary guidance to ensure protection from the onset of product development.
Finally, embracing radical transparency and accountability in product design and development is crucial. According to the most recent revisions to cybersecurity white papers, software and AI system manufacturers are advised to integrate measures that are inherently strong against cyber threats. This approach to security design not only protects against vulnerabilities but also strengthens the overall posture of an organization’s cyber defense.
Conclusion
The CIS Controls provide a comprehensive framework for organizations to fortify themselves against cyber threats. From asset management to data protection, these controls offer a robust security posture. By integrating the CIS Controls with other frameworks such as ISO 27001 and NIST CSF, organizations can ensure comprehensive protection and align with global standards.
Leveraging the right tools and resources, organizations can effectively implement the CIS Controls and enhance their security posture. This strategic alignment equips businesses with the necessary tools to navigate the evolving landscape of cyber threats confidently.
In conclusion, the CIS Controls serve as a beacon for organizations, guiding them through the complexities of cybersecurity. By adopting these controls and leveraging the right tools, organizations can enhance their security posture, mitigate risks, and operate with confidence in today's digital world. The strategic adoption of the CIS Controls aligns with global standards and equips businesses with the necessary tools to protect their digital environments effectively.




