Introduction
In an era where cyber threats are increasingly sophisticated and pervasive, the importance of penetration testing cannot be overstated. Penetration testing, often referred to as ethical hacking, is a proactive approach to identifying and addressing vulnerabilities within an organization's systems, networks, and applications. By simulating real-world cyberattacks, penetration testing uncovers weaknesses that could be exploited by malicious actors, thereby fortifying an organization's security posture.
This article delves into the multifaceted nature of penetration testing, examining various types such as black box, white box, and grey box testing, and their specific applications. It also explores asset-based, network, web application, mobile application, API, cloud, wireless network, blockchain, and social engineering penetration testing, providing a comprehensive overview of each method's unique benefits and challenges. Additionally, the article outlines the critical phases of penetration testing, from planning and reconnaissance to scanning, exploitation, and post-exploitation reporting, emphasizing the importance of a structured and thorough approach in safeguarding digital assets.
By understanding the nuances and strategic implementation of penetration testing, organizations can better prepare for and defend against the ever-evolving landscape of cyber threats, ensuring robust protection and business continuity.
Why Penetration Testing is Important
Penetration evaluation is a crucial component of a company's defense strategy, mimicking cyberattacks to identify weaknesses in systems, networks, and applications. By proactively identifying and addressing these weaknesses, entities can significantly reduce the risk of data breaches, thereby safeguarding their information assets.
One of the key advantages of security assessments is its alignment with industry regulations and standards, ensuring that organizations meet the necessary security requirements to protect sensitive information. According to Gartner®, the implementation of a robust cybersecurity management plan is crucial for businesses of all sizes and industries. This plan should encompass identifying potential risks, assessing their impact, and devising appropriate responses.
Developing a comprehensive project plan for penetration evaluation is essential. This plan should outline the assessment scope, the specific systems and assets to be evaluated, the timeline, objectives, and expected outcomes. Choosing the appropriate evaluation methodology, whether it be Black Box, White Box, or Gray Box assessments, is also crucial to align with the scope of the project.
Supporting the security team with the necessary expertise, resources, and budget is another critical factor. Organizations must determine whether to handle the project in-house or involve outside assessment service providers.
In today's digital environment, with the ongoing increase of cyberattacks aimed at weaknesses, penetration assessment services play a crucial role in ensuring business continuity and protecting operations. This proactive method not only improves a group's defensive stance but also enables them to adopt new technologies with assurance.
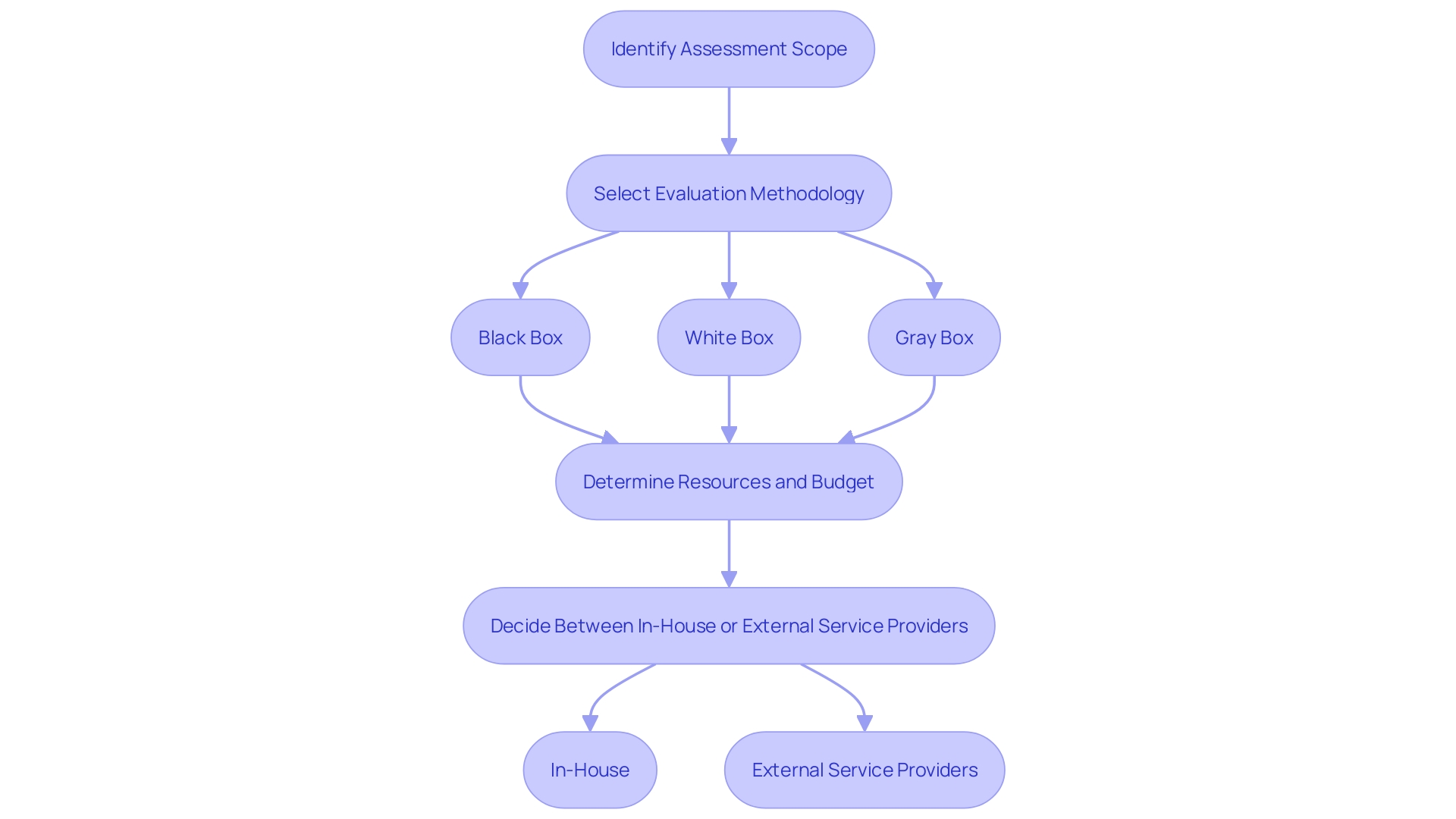
Types of Penetration Testing
Penetration evaluations can be classified into multiple kinds, each aimed at examining various elements of a company's security stance. Comprehending these types allows entities to choose the most suitable testing methods according to their particular requirements and threats.
-
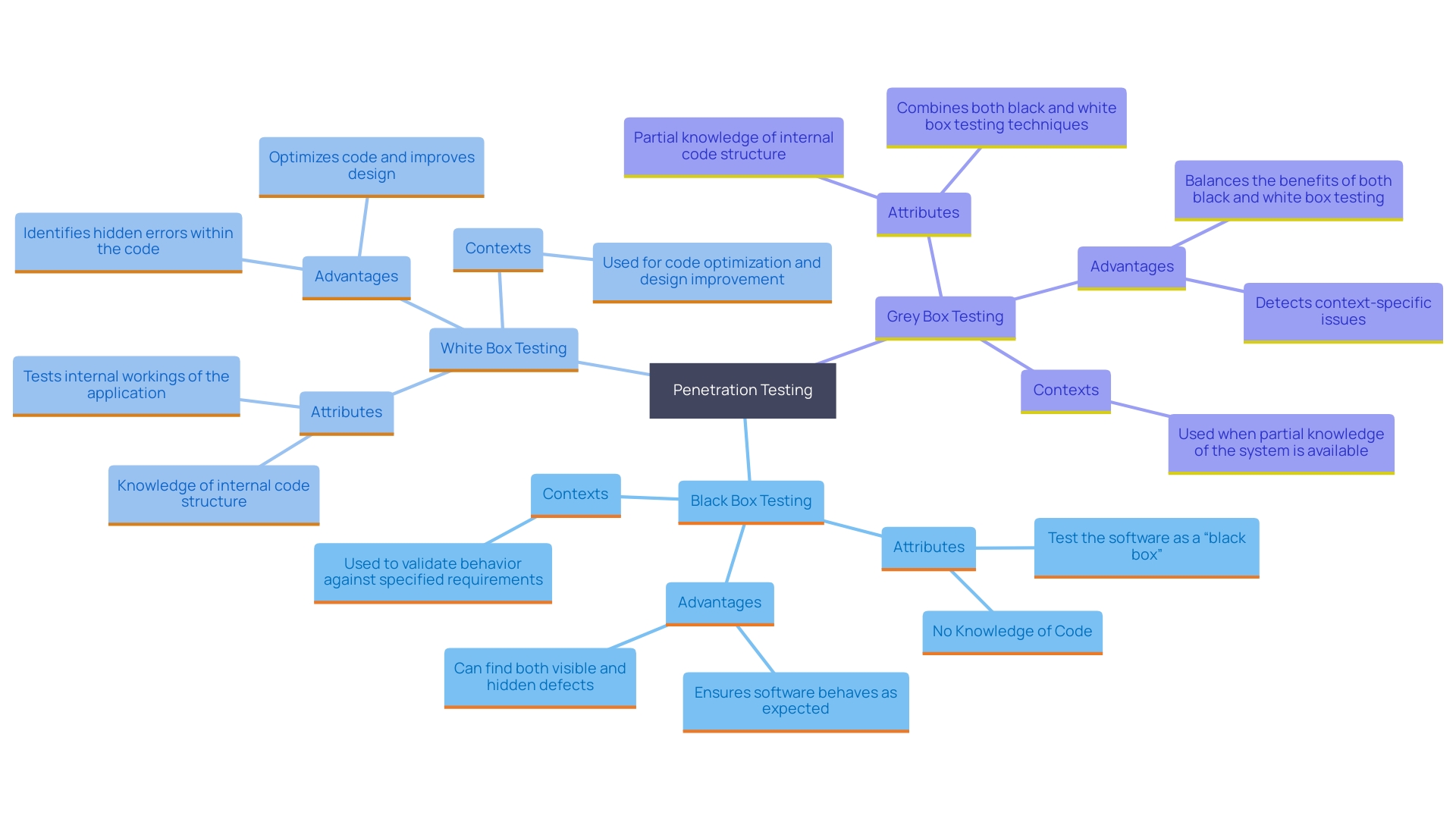
Black Box Testing: This type simulates an attack by an external hacker with no prior knowledge of the system. It's an effective way to evaluate how well an organization's perimeter defenses can withstand external threats. According to BreachLock, this method provides a realistic picture of vulnerabilities that an outsider could exploit.
-
White Box Testing: In this approach, the tester has full knowledge of the system, including access to source code, architecture documentation, and network information. This comprehensive access allows for a more thorough examination of potential security vulnerabilities. As highlighted in a study by Daniel Dalalana Bertoglio and colleagues, this method is crucial for identifying deep-rooted issues within the system's architecture.
-
Grey Box Testing: This method combines elements of both black and white box testing. The tester has partial knowledge of the system, typically credentials or documentation provided by the organization. This balance ensures a realistic yet thorough evaluation of the system's protection.
Penetration evaluation, as highlighted by a report on contemporary Pentest challenges, is about more than identifying vulnerabilities. It involves a detailed examination of business logic, financial transactions, and the flow of goods through web forms and mobile applications. This holistic approach not only identifies vulnerabilities but also ensures adherence to regulatory and business requirements, making it an indispensable tool for maintaining robust cybersecurity.
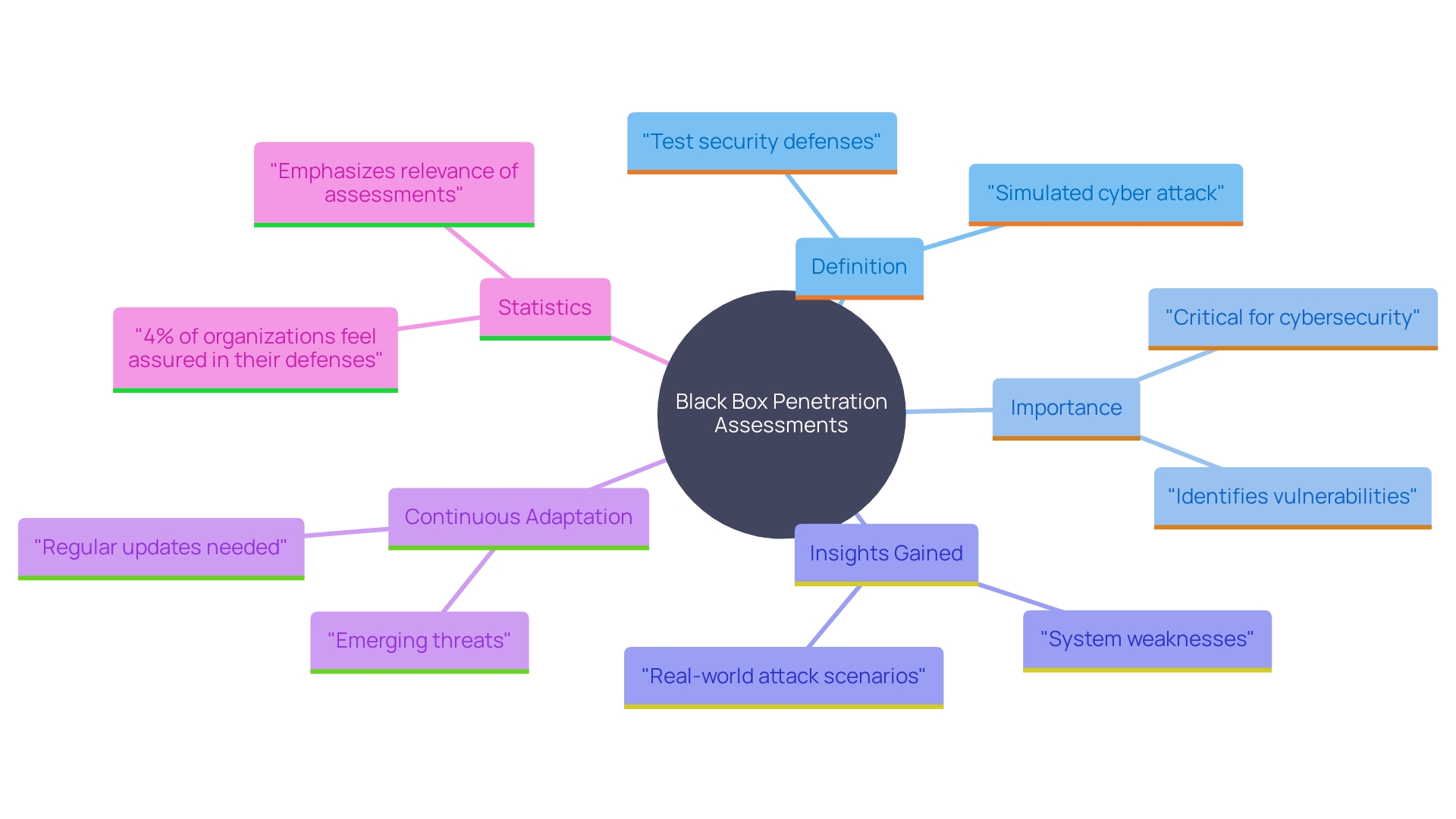
Black Box Penetration Testing
Black box penetration assessment is a method where testers evaluate a system without any prior knowledge of its internal structures. Acting as external attackers, they simulate real-world hacking attempts to identify and exploit vulnerabilities. This approach is invaluable for assessing the system's defenses from an outsider's perspective, offering critical insights into how well the system can withstand external attacks. As emphasized by BreachLock's PTaaS model, this type of assessment is created to imitate the actions of an actual hacker, offering a genuine evaluation of the system's protection. The significance of such evaluations is highlighted by the fact that only 4% of organizations feel assured in their defenses against cyberattacks. This method is essential for maintaining the integrity and confidentiality of company data, making it a crucial component in any comprehensive cybersecurity strategy. For instance, the Black Hat conferences, known for their deeply technical hands-on trainings, emphasize the latest research and vulnerability disclosures, reinforcing the need for continuous adaptation to emerging threats.
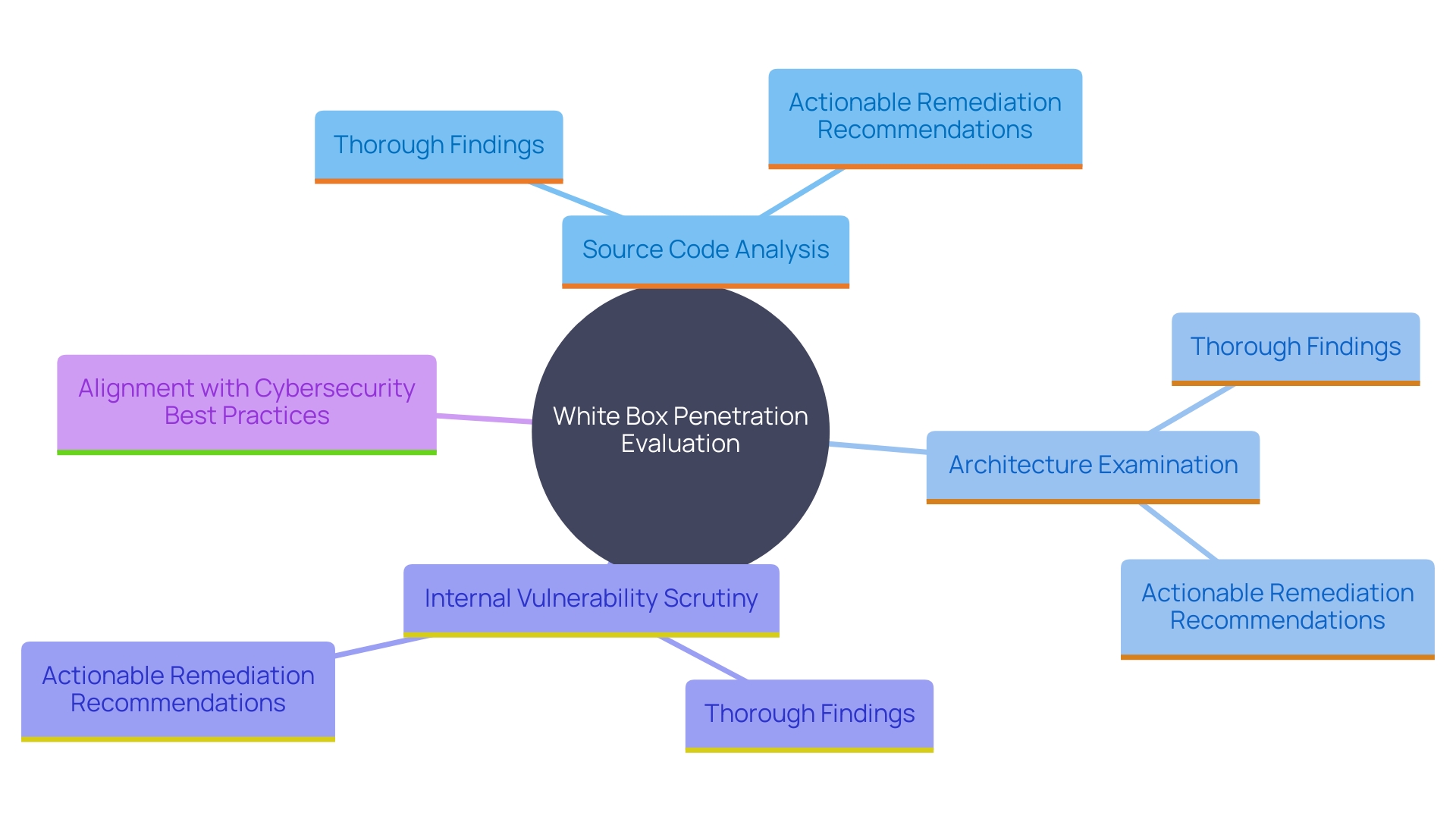
White Box Penetration Testing
White box penetration evaluation equips testers with an exhaustive understanding of the system's inner workings, including source code and architecture. This method empowers testers to scrutinize internal vulnerabilities and security flaws that might remain concealed in external assessments. Leveraging comprehensive information, testers can perform an in-depth analysis, yielding more thorough findings and actionable recommendations for remediation. As noted by Erfan, a seasoned Security Consultant, the meticulous nature of white box analysis ensures a robust evaluation of the system's defenses, aligning with the best practices advocated by cybersecurity experts.
Grey Box Penetration Testing
Grey box penetration evaluation integrates the strengths of both black box and white box approaches by providing testers with partial knowledge of the system. This approach enables testers to simulate insider threats and evaluate external vulnerabilities simultaneously. For example, M&T Bank, with its rich background in digital transformation, utilizes grey box evaluation to uphold strict safety measures while promoting innovation. This method effectively balances the comprehensive insights of white box evaluation with the realistic attack simulations of black box evaluation, thereby ensuring a robust security posture from multiple angles.
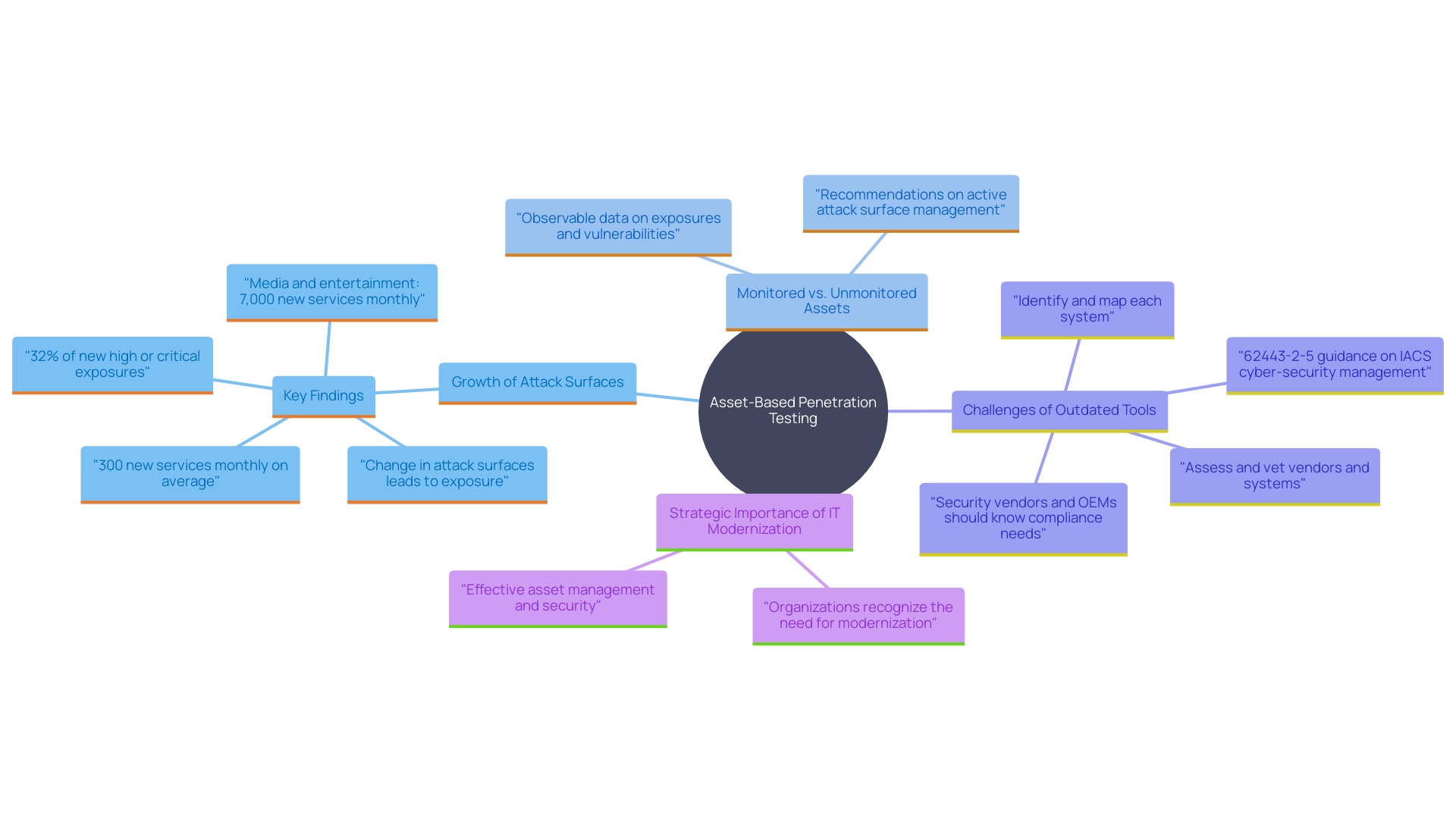
Asset-Based Penetration Testing Types
Asset-based penetration testing focuses on particular assets within a company, emphasizing their importance to ensure the most valuable components receive the necessary attention. This approach is particularly vital given the dynamic nature of modern attack surfaces. On average, an entity's attack surface expands with over 300 new services each month, contributing to 32% of new high or critical exposures. This rapid growth underscores the importance of precisely targeted assessments to mitigate risks effectively.
Real-world data further emphasizes the need for focused asset management. Research reveals that only 60% of assets are typically monitored, leaving 40% unmonitored and vulnerable. The unmanaged assets represent the fastest-growing attack surface, a significant threat that outdated tools and techniques struggle to address. For instance, almost 44% of entities still depend on manual spreadsheets to monitor assets, covering a mere 12% of their corporate network, highlighting significant visibility gaps.
'Sophos' acquisition of Secureworks exemplifies market moves towards enhancing asset-based protection. By incorporating advanced features such as identity detection and next-gen SIEM, entities can more effectively prioritize vulnerabilities and enhance their overall defense stance. This strategic alignment between technology and business needs is crucial, as evidenced by 69% of organizations recognizing IT modernization as essential for achieving business goals.
In summary, asset-focused evaluations not only tackle existing weaknesses but also correspond with wider safety and commercial strategies, guaranteeing strong defense for essential assets.
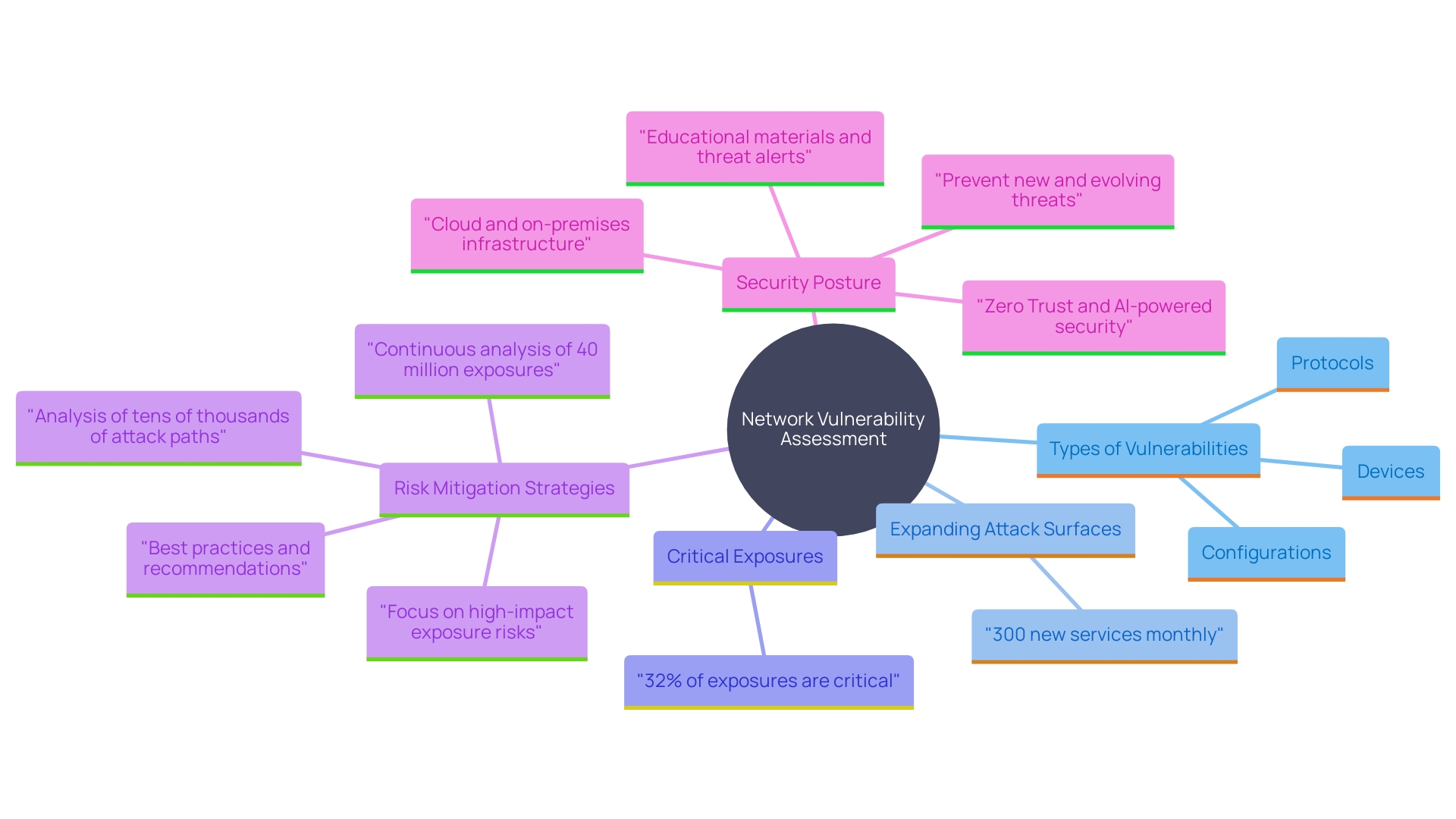
Network Penetration Testing
Network vulnerability assessment is an essential procedure that examines the safety of network infrastructures. This method identifies vulnerabilities within devices, configurations, and protocols. Recent findings highlight that a company's attack surface can expand by over 300 new services monthly, with 32% of these leading to high or critical exposures. Efficient evaluation exposes these vulnerabilities, allowing organizations to establish strong strategies to protect against possible risks. As one cybersecurity expert notes, 'Our innovative solutions help more than 50,000 customers worldwide securely connect devices and applications, reducing risk and improving operational efficiency.' By understanding and addressing these vulnerabilities, companies can enhance their defenses, ensuring a secure and resilient network infrastructure.
Web Application Penetration Testing
'Web application penetration assessment is an essential procedure for identifying and reducing weaknesses in web applications, which are often targets for cyberattacks.'. This type of testing focuses on uncovering common vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure configurations. For instance, SQL injection remains a significant threat, capable of exposing sensitive data and compromising entire databases. Tools like SQLMap can automate the detection and exploitation of SQL injection flaws across various database systems, including MySQL, PostgreSQL, and Oracle.
A comprehensive approach to web application protection involves evaluating the entire software supply chain. This includes identifying zero-day vulnerabilities—unknown flaws without an existing fix—that can be exploited by attackers. Recent data indicate that 94% of applications tested had some form of broken access control, emphasizing the need for rigorous protection assessments and continuous monitoring.
Practical instances, like assessments on sophisticated systems such as Moodle, unveil the complex challenges organizations encounter. At RWTH Aachen University, vulnerability assessments on Moodle revealed that individuals with the 'trainer' role could perform cross-site scripting attacks, highlighting the significance of comprehensive and continuous safety evaluations.
In summary, web application security evaluation is essential for preserving the integrity and safety of online platforms. By identifying and addressing vulnerabilities, organizations can protect their digital assets from cyber vandalism, data theft, and other malicious activities.
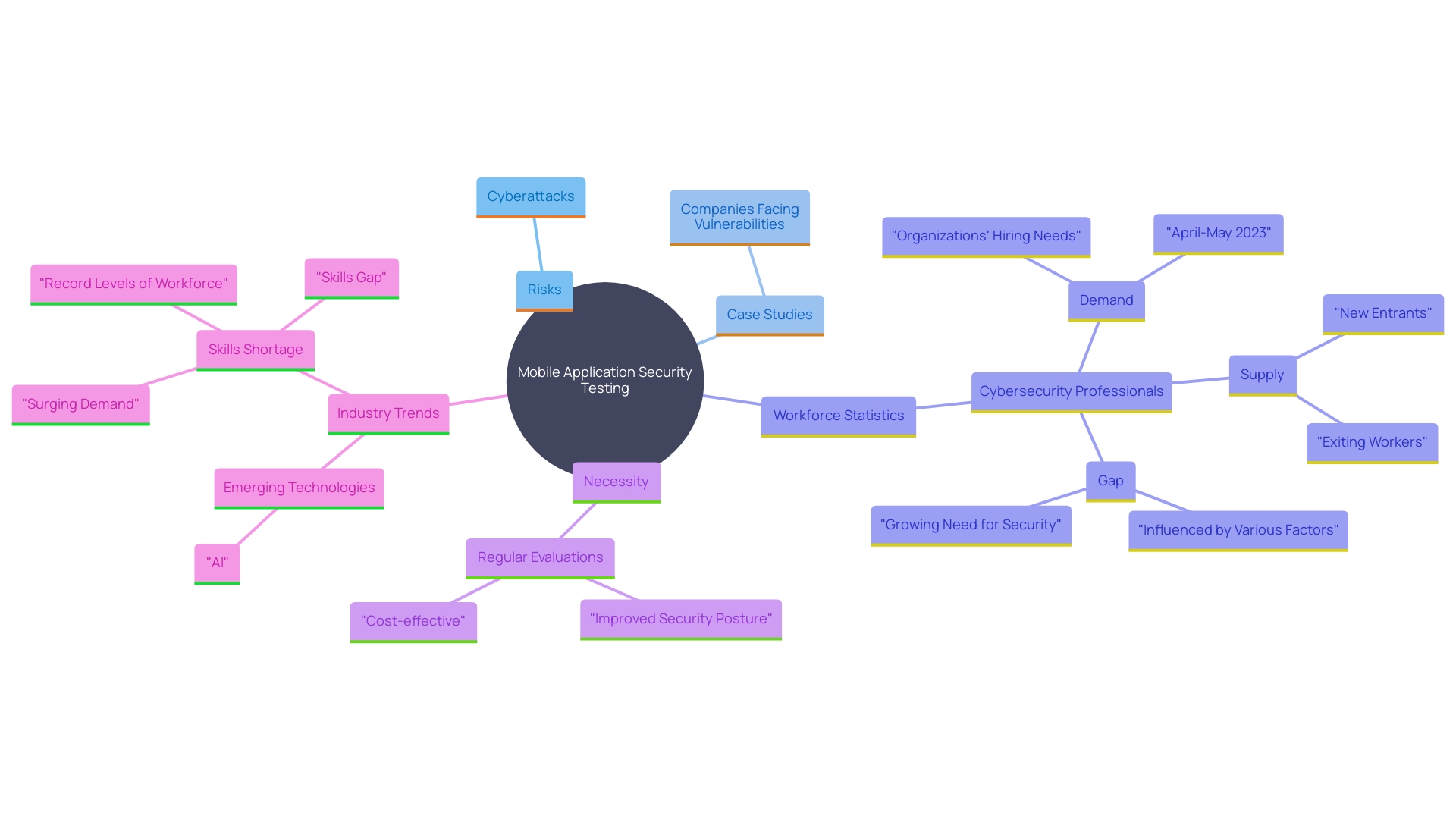
Mobile Application Penetration Testing
Mobile application security testing is essential in safeguarding mobile apps across various platforms. With nearly everyone having access to mobile technology, the risk of cyberattacks and data breaches has significantly increased. For instance, a recent incident involved a malicious application named PDF AI: Add-On, which exploited Android’s Accessibility features to access sensitive user data and prevent its removal. Such vulnerabilities emphasize the significance of thorough assessments to safeguard user data.
A case study involving a well-known retail company highlights the importance of thorough vulnerability assessments. The company’s online shopping mini program faced various cyberattack and data leakage risks. Because of the absence of protective abilities among their internal technical staff and the high expenses of protective tools, the company chose to conduct a comprehensive assessment to identify weaknesses and strengthen their protective measures.
Statistics show that only 4% of organizations feel assured about their protection strategies for connected devices. This low confidence level highlights the essential requirement for regular mobile application evaluations to guarantee strong protection. As the cybersecurity workforce expands, currently estimated at around 4.7 million individuals worldwide, the industry keeps adjusting to changing dangers, making vulnerability assessment a crucial part of overall protection strategies.
Expert insights emphasize the transformative impact of digital technologies on various sectors, including business and finance. Despite this, a significant digital divide remains, posing additional challenges for ensuring comprehensive mobile security. Consequently, keeping informed about the newest cybersecurity trends and incorporating sophisticated security assessment methods are essential for safeguarding sensitive user information and upholding the integrity of mobile applications.
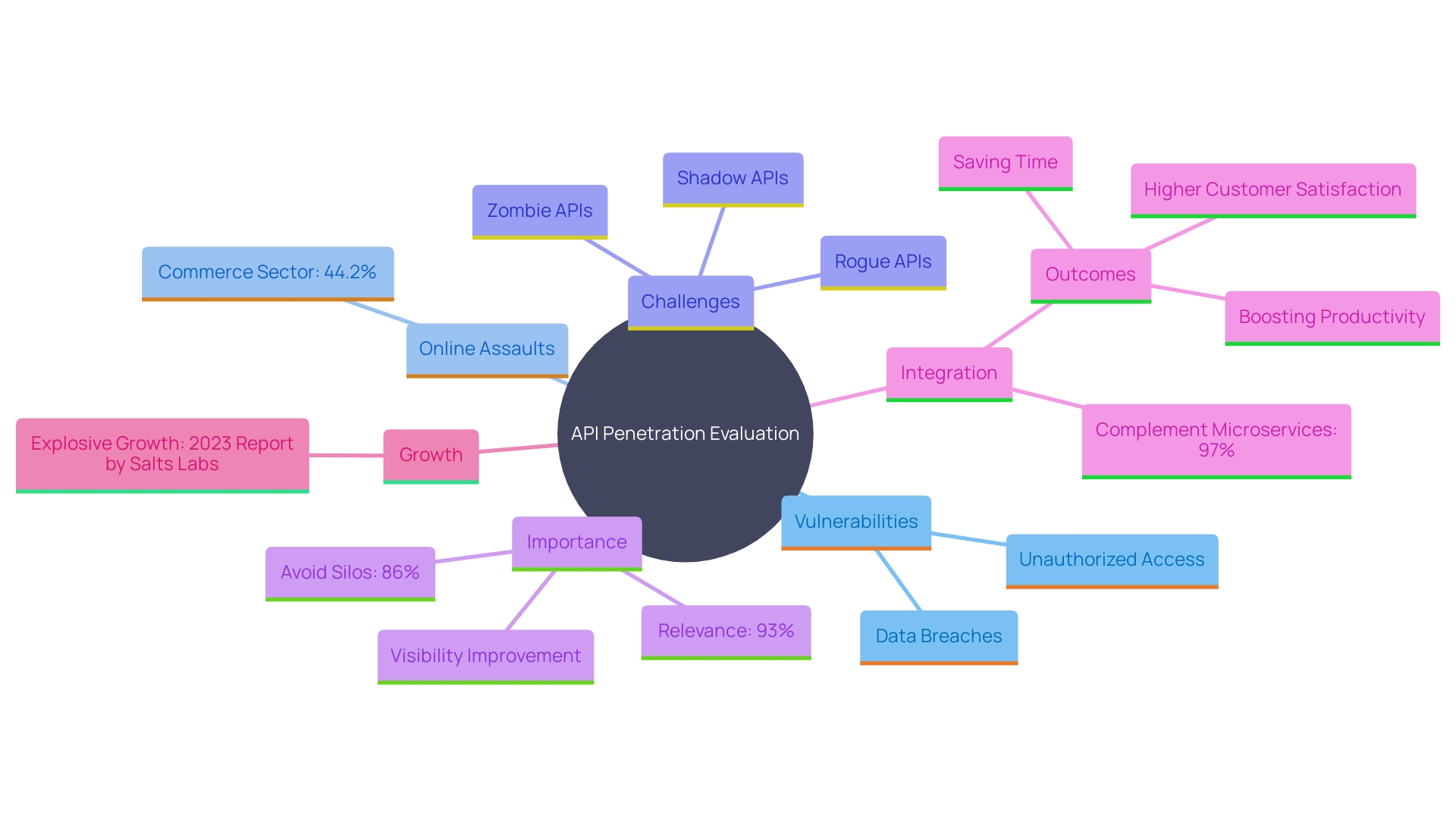
API Penetration Testing
API penetration evaluation is a crucial aspect of securing application programming interfaces, which are essential for enabling communication between different software applications. This form of testing aims to uncover vulnerabilities that could potentially lead to unauthorized access or data breaches. Considering that 44.2% of online assaults aimed at businesses in the commerce sector concentrate on APIs, highlighting the necessity of strong protective measures is crucial. Moreover, the swift implementation of APIs has created blind spots such as zombie, shadow, and rogue APIs, making thorough visibility and strict protective measures essential elements of an entity's application protection initiatives.
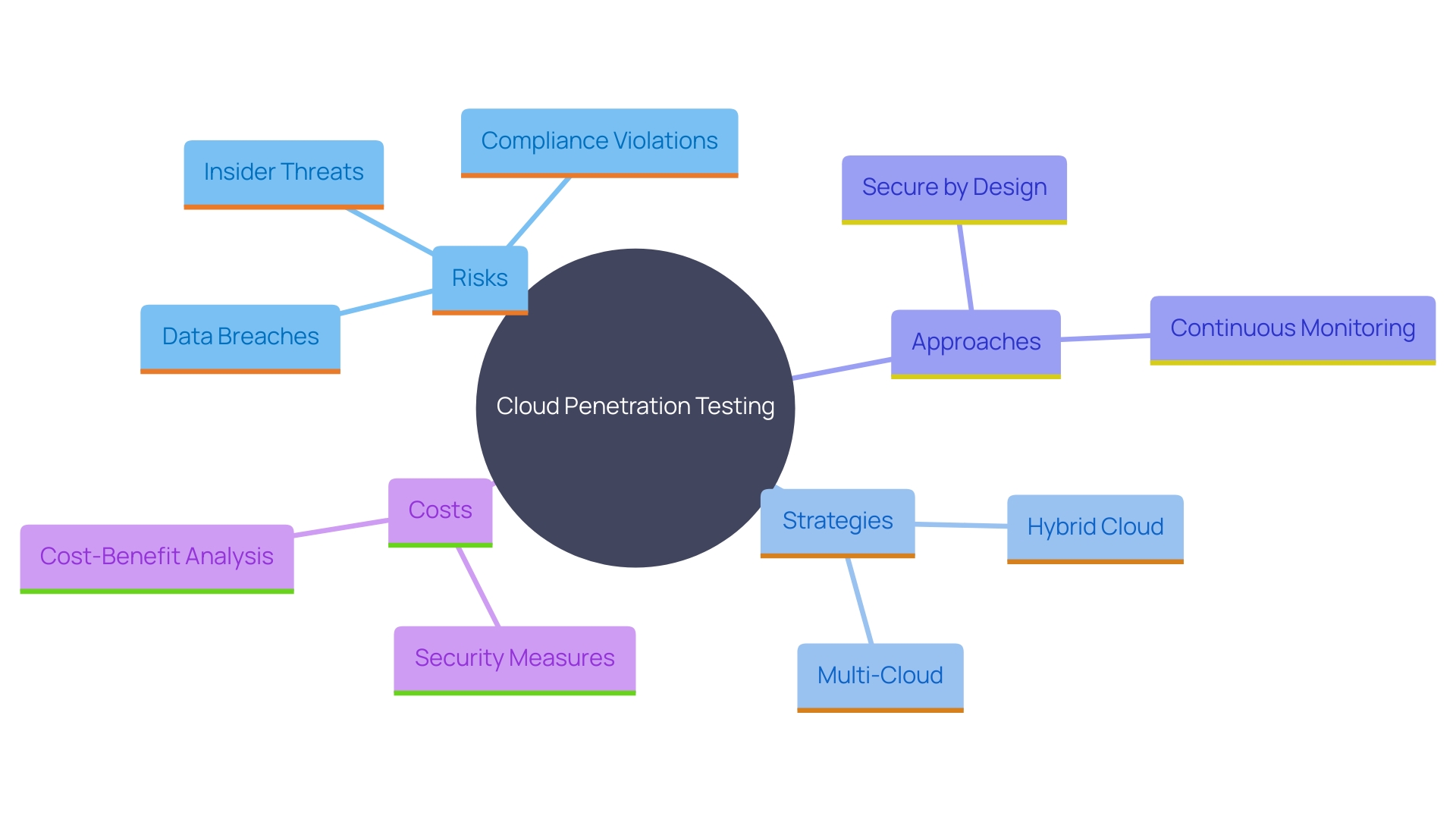
Cloud Penetration Testing
Cloud penetration testing is an essential practice for evaluating the safety of cloud environments and services. By identifying potential risks in data storage, access controls, and service configurations, entities can fortify their cloud infrastructure against evolving threats. With 78% of organizations adopting hybrid and multi-cloud strategies, the need for strict protective measures is more critical than ever. The importance of this is underscored by incidents such as a suspicious support case in an AWS account that highlighted vulnerabilities in cloud service configurations. Furthermore, specialists such as Corey Quinn highlight the interconnected relationship between protection and cost, pointing out that effective cloud design can deter harmful individuals while maximizing expenses. As cloud adoption continues to grow, albeit at a slower pace, maintaining a Secure by Design approach ensures that security is integrated into every phase of development and deployment, ultimately safeguarding against data breaches and misuse of cloud services.
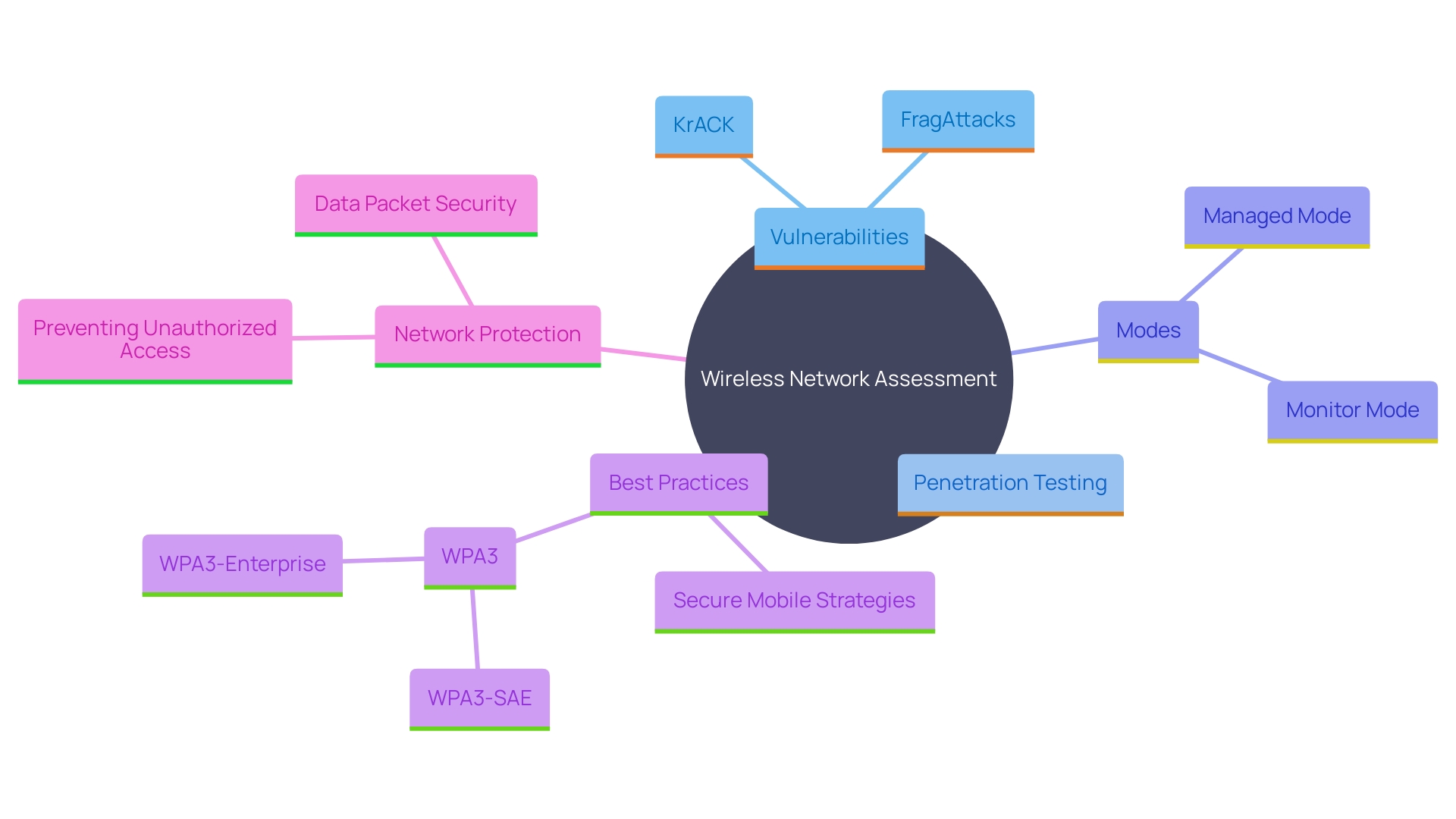
Wireless Network Penetration Testing
'Wireless network assessment is essential for protecting the integrity of an organization's wireless infrastructure.'. This evaluation process meticulously identifies vulnerabilities that could be exploited by potential attackers within proximity. By simulating real-world attack scenarios, penetration testing ensures robust encryption protocols and stringent access controls are in place, thus fortifying wireless communications against unauthorized access. According to industry specialists, comprehending the complexities of wireless modes, like Managed Mode and Monitor Mode, is crucial for improving network protection. Managed Mode, the standard for most devices, enables connection to access points for data transmission, while Monitor Mode permits passive data collection, crucial for identifying potential vulnerabilities. Carrying out thorough wireless protection evaluations not only reduces risks but also conforms to best practices for implementing secure mobile strategies.
Blockchain Penetration Testing
Blockchain security assessment is crucial in protecting the integrity and safety of blockchain technologies and applications. The growing acceptance of blockchain in different industries requires this thorough evaluation to identify and reduce vulnerabilities specific to distributed ledger technologies. For instance, the Revoke. Cash incident highlighted the critical nature of securing blockchain applications against supply chain attacks. In such cases, developers can protect their applications by 'pinning' specific versions of dependencies rather than using the latest versions, thereby avoiding compromised updates.
Expert Kaloyan Velikov emphasizes the importance of continuous learning and adapting new tools in penetration testing. His experience highlights the necessity for developers to remain vigilant and informed about the protective aspects of the technologies they use. Furthermore, the swift reaction and crisis handling emphasized by entities such as OODA offer enhanced assistance in strategy, risk, and threat management, further improving blockchain protection.
The Asia-Pacific region's swift adoption of blockchain AI technologies, driven by industrialization and supportive government policies, illustrates the dynamic growth and investment in this field. Nonetheless, as blockchain technology progresses, so do the obstacles, making vulnerability assessments a crucial practice to uphold trust and safety in this digital era.
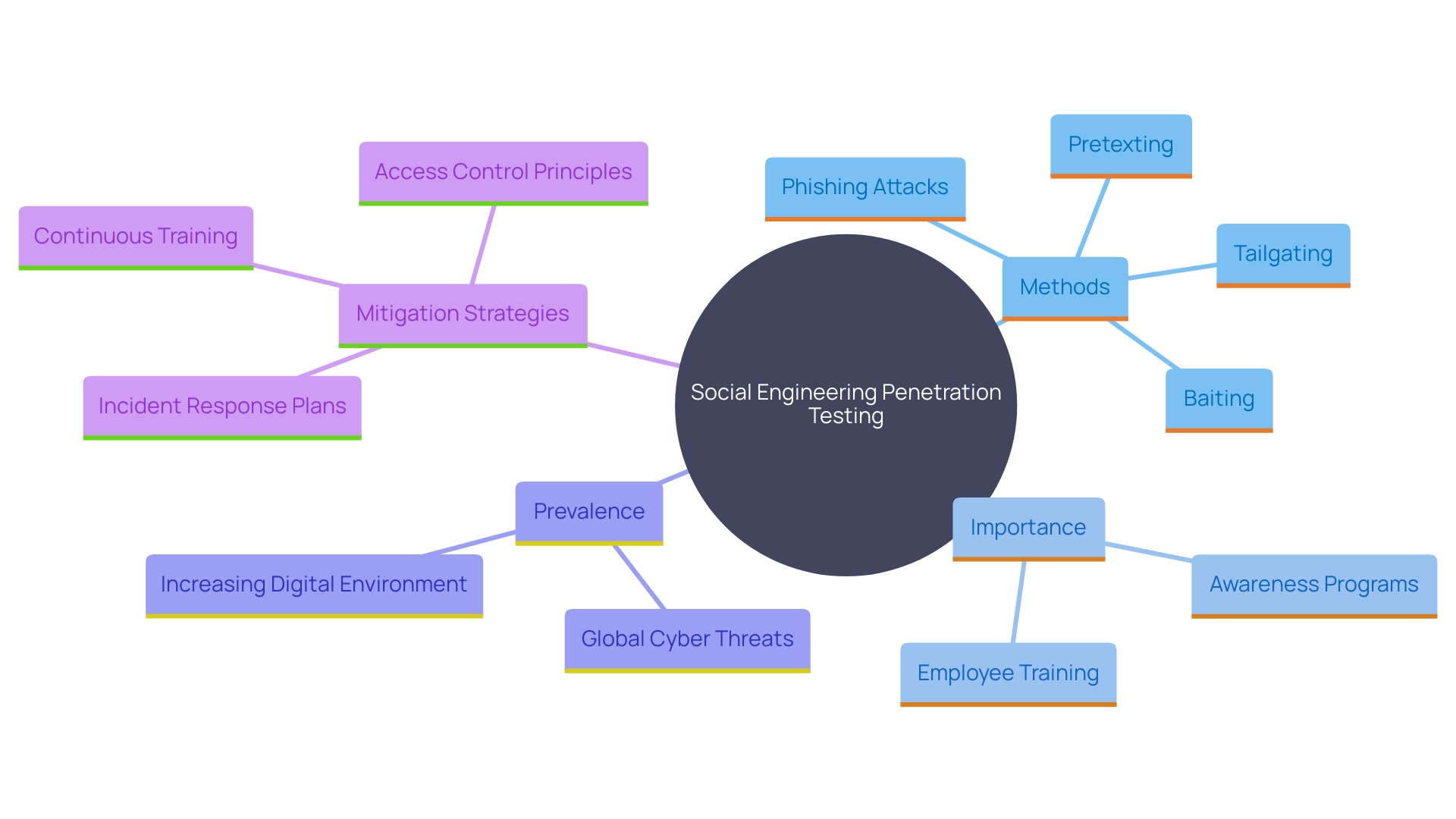
Social Engineering Penetration Testing
Social engineering penetration testing scrutinizes the human factor in security by replicating phishing attacks and other deceptive strategies. This method is essential for companies as it emphasizes employees' susceptibility to social engineering, allowing them to create effective training programs that improve awareness and resilience. Long-standing as a significant threat, social engineering attacks constitute a major portion of global cyberattacks, with businesses facing substantial numbers annually. By simulating these attacks, entities can better prepare their workforce, minimizing the risk of falling prey to such schemes. Experts emphasize that social engineering preys on human trust, often manipulating individuals into divulging sensitive information. Implementing continuous, updated training and adopting the principle of least privilege for access control are essential steps in mitigating these risks.
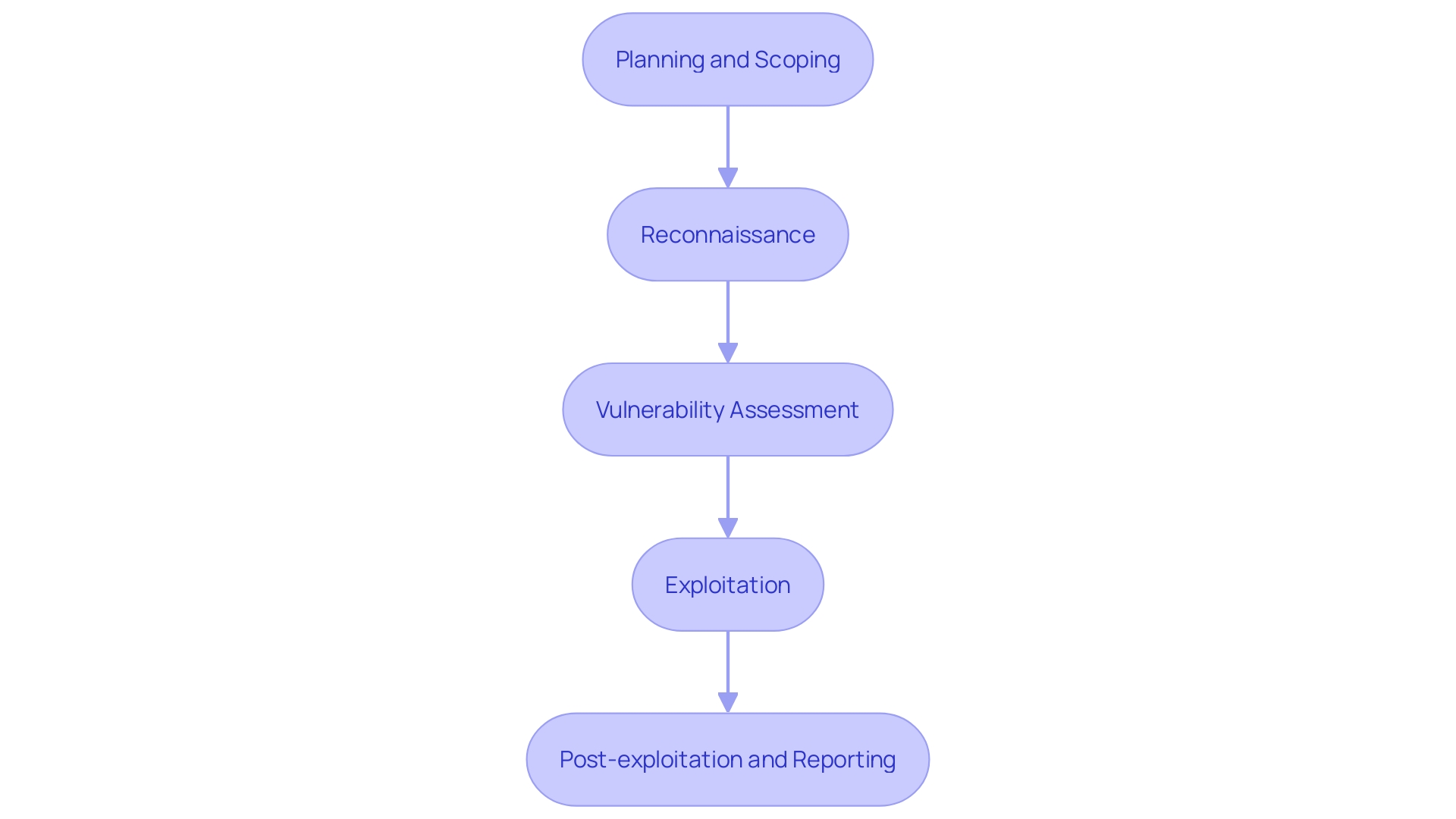
Phases of Penetration Testing
The penetration evaluation process is integral to identifying and rectifying vulnerabilities within an organization's IT infrastructure. This meticulous process is divided into several critical phases, each contributing to a thorough security evaluation.
-
Planning and Scoping: This initial phase involves creating a detailed project plan that outlines the testing's scope, including specific systems and assets targeted, timelines, objectives, and expected outcomes. Identifying key stakeholders and decision-makers, along with defining their roles and approval stages, ensures clear objectives and a structured approach.
-
Reconnaissance: Often referred to as the information-gathering phase, this step focuses on identifying and cataloging all assets, systems, and applications within the entity. This stage is crucial as it sets the groundwork for subsequent vulnerability assessments.
-
Vulnerability Assessment: In this phase, the identified assets are evaluated for potential vulnerabilities, weaknesses, and exposures. Techniques such as vulnerability scanning help in pinpointing areas that could be exploited by attackers.
-
Exploitation: Using the methodologies selected—whether Black Box, White Box, or Gray Box testing—this phase involves actively attempting to exploit the identified vulnerabilities. This simulates real-world attacks to understand the potential impact on the organization's protective stance.
-
Post-exploitation and Reporting: After exploitation, the focus shifts to analyzing the results and understanding the extent of the potential damage. Comprehensive reporting is then conducted, detailing the vulnerabilities found, the methods used to exploit them, and recommendations for mitigation.
Assisting the protection team with the appropriate expertise, resources, and budget is crucial throughout the process. Determining if the project will be managed in-house or by an outside security evaluation service provider can greatly influence the efficiency of the assessment.
By adhering to these phases diligently, organizations can proactively identify and mitigate threats, ensuring robust protection of their digital assets and continuity of operations.
Planning and Reconnaissance
'The planning and reconnaissance phase is pivotal in penetration assessment, as it involves meticulously defining the scope and gathering critical information about the target.'. This step involves identifying key assets, understanding the network structure, and evaluating existing protective measures, which collectively inform the subsequent testing activities. For instance, companies like United Airlines, with its extensive network of operational technology devices across seven hubs, faced significant challenges in identifying all devices within their OT network. 'Chris Peters, their principal architect for OT cybersecurity, emphasizes the significance of this phase in maintaining robust protection.'. Similarly, an audio-visual company with a global presence contended with the risks posed by numerous devices connected to their network, emphasizing the necessity of thorough reconnaissance to locate and mitigate potential threats. These examples underscore the importance of detailed planning and reconnaissance in safeguarding complex and expansive digital environments.
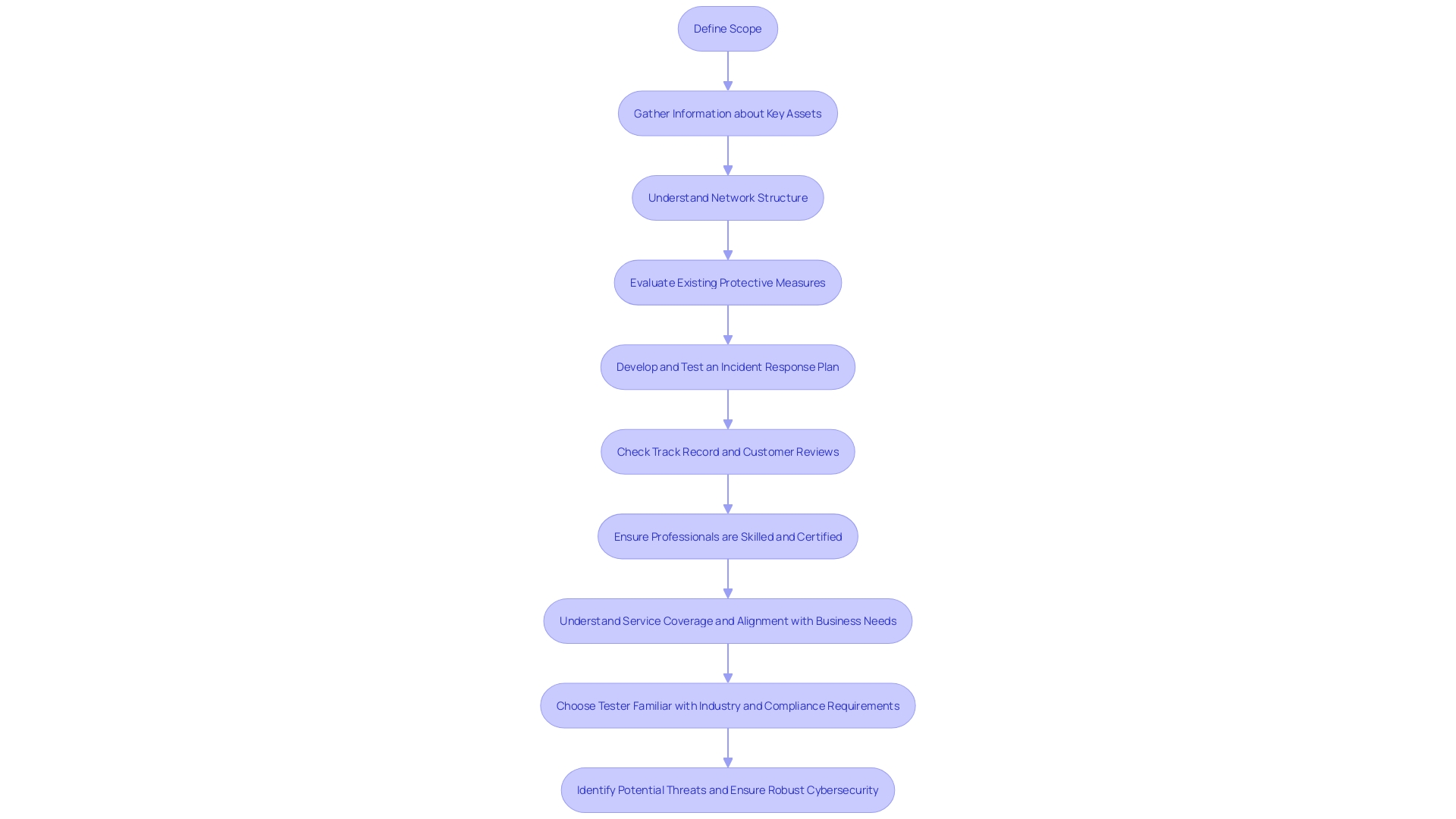
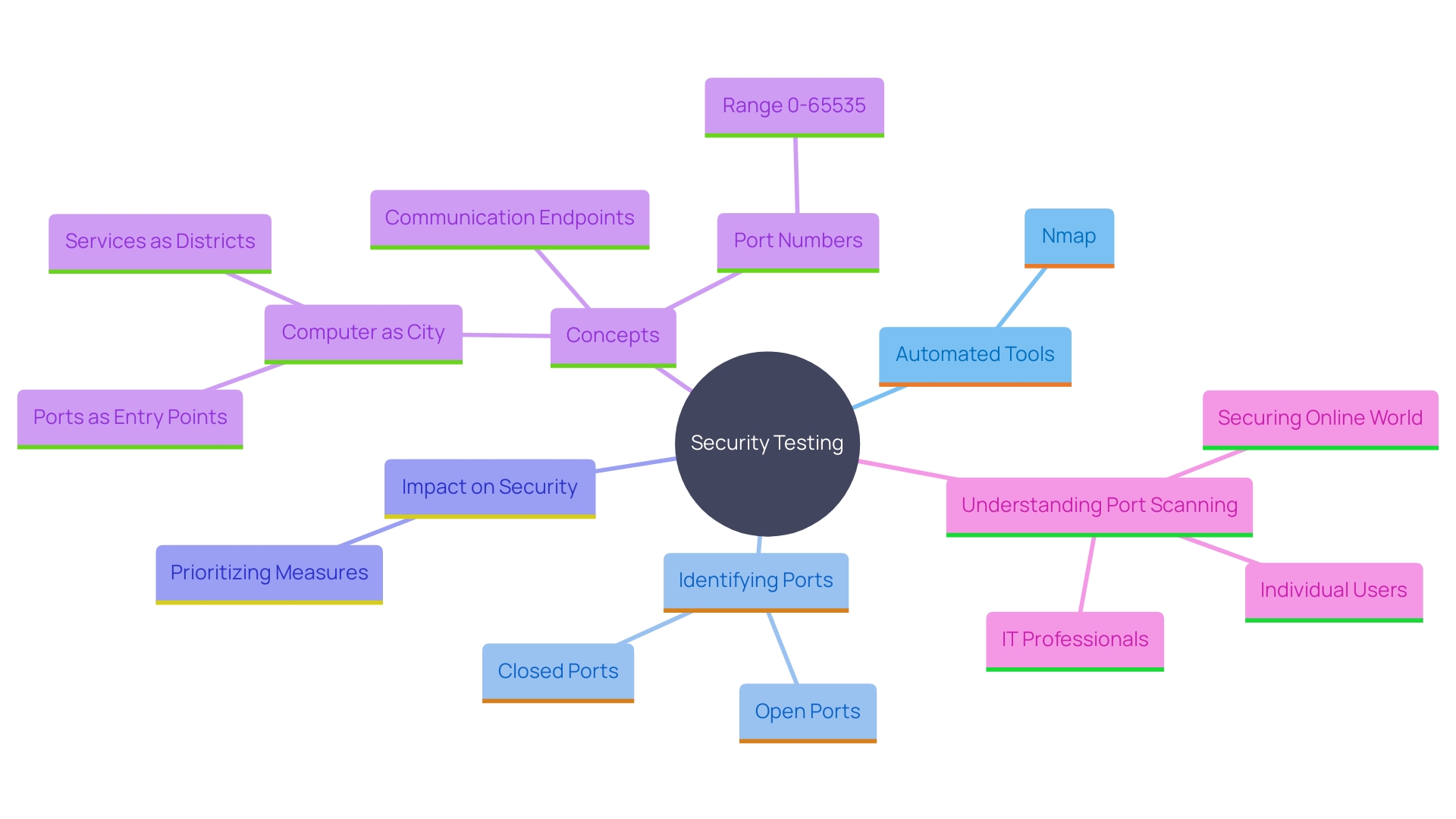
Scanning and Enumeration
During the scanning and enumeration phase, security testers utilize advanced automated tools to identify open ports, services, and potential vulnerabilities within the target systems. This critical step, often performed using tools like Nmap, provides a comprehensive overview of the attack surface, highlighting which applications are listening for TCP connections or UDP packets and which ports are available yet unresponsive.
Understanding the distribution of open and closed ports is paramount as it allows testers to prioritize areas for deeper analysis. For instance, analyzing patterns in port states helps in identifying potential entry points that are more susceptible to attacks. As Benny Czarny, OPSWAT CEO, emphasizes, the complexity of modern web applications demands more than just basic tools for securing highly sensitive data across sectors like healthcare, finance, and government. This phase is foundational for ensuring that subsequent security measures are effectively targeted, thereby enhancing the overall resilience of the systems against sophisticated threats.
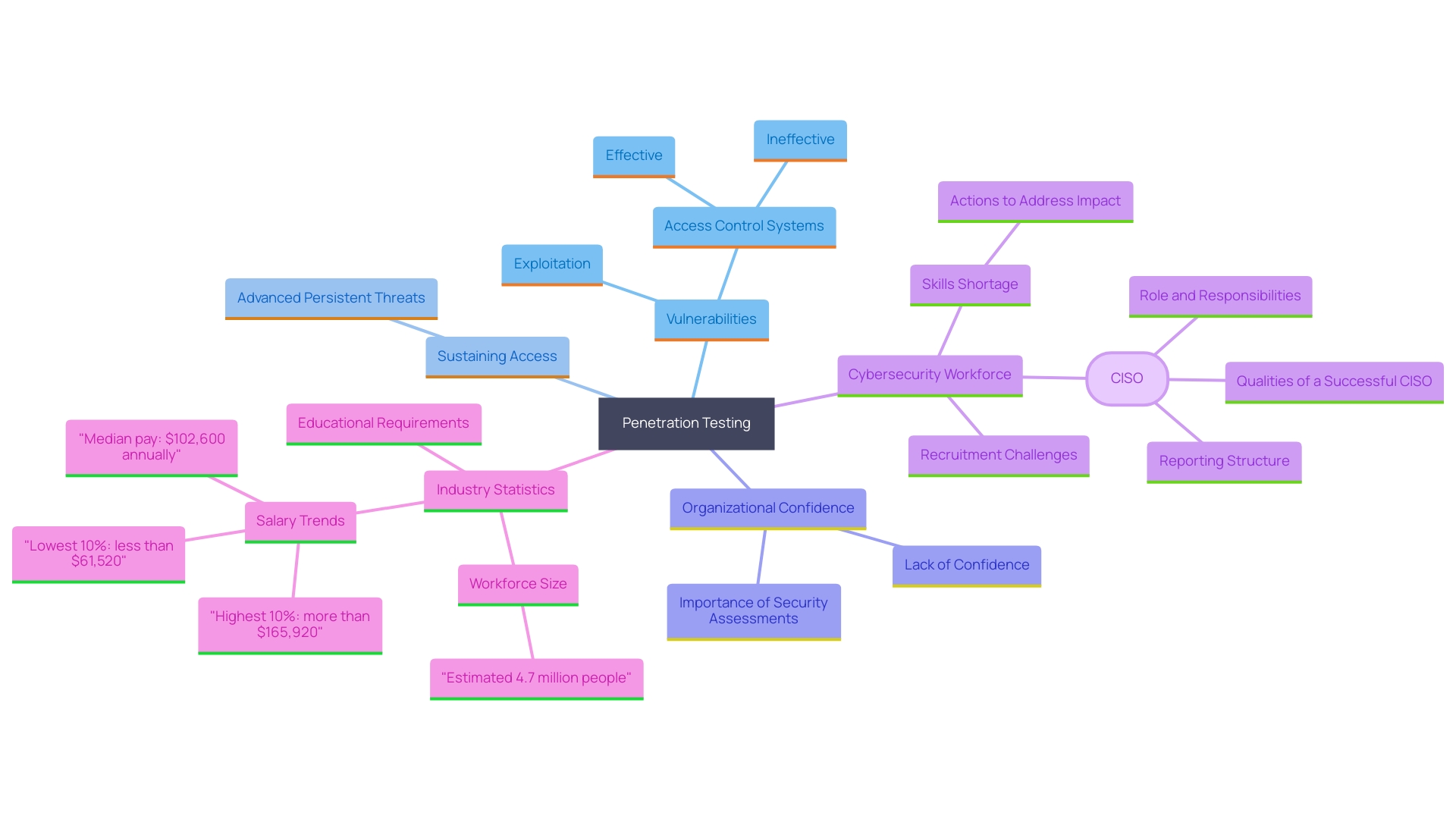
Gaining Access and Maintaining Access
During this phase, penetration testers actively exploit discovered vulnerabilities to gain unauthorized access to the system. Once successful, they probe for methods to sustain this access, emulating the techniques of advanced persistent threats (Apts). 'This approach not only tests the system's resilience but also assesses the entity's capability to detect and respond to such breaches.'. According to ASIS International's research, effective access control systems combining technology with robust policies are pivotal in mitigating these risks. Moreover, only 4% of organizations feel confident in their cybersecurity measures, underscoring the critical need for comprehensive security assessments.
Conclusion
The significance of penetration testing in fortifying organizational security cannot be overstated. It serves as a proactive measure to identify vulnerabilities within systems, networks, and applications, ultimately reducing the risk of data breaches. By simulating real-world cyberattacks, organizations can gain insights into their security posture and address weaknesses before malicious actors can exploit them.
This proactive approach not only enhances compliance with industry regulations but also aligns with broader business strategies, ensuring that sensitive data remains protected.
Different types of penetration testing, including black box, white box, and grey box methods, cater to various organizational needs. Each type offers unique advantages, from assessing perimeter defenses to examining internal vulnerabilities. Furthermore, specialized testing methods addressing specific assets, network configurations, web applications, and mobile platforms ensure that organizations can tailor their security assessments to their most critical areas of concern.
As the landscape of cyber threats continues to evolve, the importance of a structured approach, encompassing planning, reconnaissance, and thorough analysis, becomes increasingly apparent.
In conclusion, the multifaceted nature of penetration testing underscores its essential role in maintaining robust cybersecurity practices. Organizations that prioritize regular and comprehensive penetration testing not only safeguard their digital assets but also cultivate a culture of security awareness. By investing in this vital practice, businesses can confidently navigate the complexities of the digital age, ensuring resilience against emerging threats and fostering trust among stakeholders.




