Introduction
Amazon EC2, or Elastic Compute Cloud, is a cornerstone service from Amazon Web Services that offers configurable compute resources in the cloud. It is designed to make web-scale cloud computing easier for developers by providing secure, resizable compute capacity. With EC2, you can launch as many or as few virtual servers as needed, manage storage, and configure security and networking.
In this article, we will explore the key components of Amazon EC2, learn how to get started with EC2, discover the process of launching an EC2 instance, understand how to securely connect to an EC2 instance, explore different EC2 instance types and configurations, delve into the security and networking capabilities of EC2, grasp the pricing models for EC2, explore various use cases for EC2, learn how to manage and monitor EC2 instances effectively, and adopt best practices for using Amazon EC2.
By the end of this article, you will have a comprehensive understanding of Amazon EC2 and how it can empower your organization in the cloud. So let's dive in and explore the transformative potential of EC2 in the world of cloud computing.
What is Amazon EC2?
Amazon EC2, or Elastic Compute Cloud, is a cornerstone service from Amazon Web Services that offers configurable compute resources in the cloud. It is designed to make web-scale cloud computing easier for developers by providing secure, resizable compute capacity. With EC2, you can launch as many or as few virtual servers as needed, manage storage, and configure security and networking.
It enables businesses to run applications on a virtual server known as an EC2 instance, which is akin to a traditional server, but with the benefits of scalability and cost-effectiveness.
EC2's ability to scale resources up or down based on demand is crucial for companies like Talent.com, which centralizes over 30 million job listings from various sources into a single platform for job seekers. The use of EC2 allows Talent.com to optimize their job matching algorithm's performance, which is critical to their mission of providing relevant job recommendations to users.
Amazon's commitment to providing comprehensive services and robust documentation is highlighted by AWS's extensive offerings, which include not only EC2 but also networking through VPC, container services like ECS, and security services via IAM. This ecosystem supports a variety of workloads and is chosen by companies for its market leadership and the value that experience with AWS brings in the job market.
Recent trends in the cloud industry showcase the competition among leading providers like AWS, Google Cloud, and Azure. Compute instances, such as those provided by EC2, are among the most utilized services, demonstrating their status as foundational elements for numerous applications. As per Vantage's insights, the market share dynamics are shifting, with Azure gaining ground on AWS.
Overall, AWS EC2 exemplifies the transformative potential of cloud computing, offering scalable solutions that support businesses in various stages of growth and technological advancement.
Key Components of Amazon EC2
Amazon EC2, a cornerstone of AWS's cloud computing platform, is designed to make web-scale cloud computing more accessible for developers. At its core, the service provides resizable compute capacity in the cloud, aimed at making web-scale computing easier for developers.
- Instances: Think of instances as the backbone of EC2. They're essentially virtual servers that can be sized according to the workload requirements, from small tasks to large enterprise applications.
- Amazon Machine Images (AMIs): AMIs serve as the blueprints for launching your instances. They come pre-packaged with an OS, and potentially additional software, making setup swift and standardized.
- Regions and Availability Zones: AWS's global presence is segmented into regions, each containing multiple isolated locations known as Availability Zones. This design ensures resilience, high availability, and helps reduce latency by locating resources closer to end users.
- Security Groups: Acting as virtual firewalls, security groups define the rules that allow traffic to and from your EC2 instances. This is critical for maintaining the security and integrity of your applications.
- Elastic Block Store (EBS): EBS provides persistent storage volumes that attach to instances, allowing you to store data beyond the lifecycle of a single EC2 instance.
- Elastic IP Addresses: With Elastic IP addresses, you can assign static IP addresses to your instances, which is vital for hosting reliable, accessible web services.
- Key Pairs: For secure SSH access to your instances, key pairs are essential. They help ensure that only authorized users can manage the servers.
- Elastic Load Balancer (ELB): ELB plays a crucial role in application scalability and fault tolerance by distributing incoming application traffic across multiple instances.
Understanding these components is essential for deploying robust, scalable, and secure applications on the cloud. Companies like Talent.com leverage these features to manage vast data sets and ensure their platforms are both reliable and capable of scaling to meet user demand. AWS's commitment to providing a wide array of services, from computing power to data warehousing, alongside its robust documentation, makes it an excellent choice for businesses seeking to innovate and grow in the cloud.
Getting Started with Amazon EC2
Embarking on the journey with Amazon EC2 is a step towards harnessing the power of cloud computing. Before diving into the practical aspects of EC2, it's important to recognize its position as a market leader in cloud services. AWS's extensive service offerings, including networking, container services, and security, provide a robust infrastructure to build a production-like environment, which is why it's vital to understand the initial setup and configuration process.
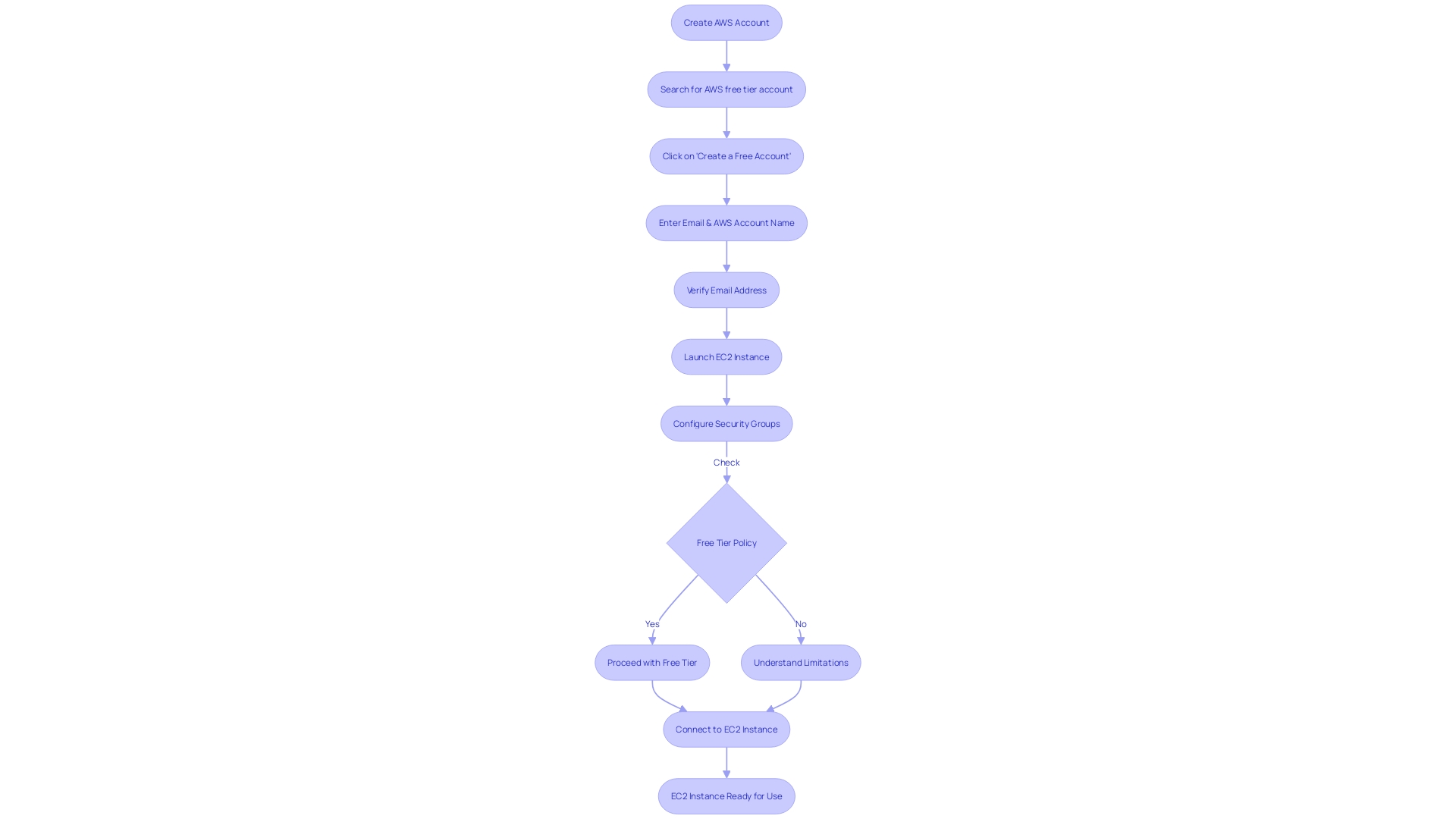
The first step in utilizing Amazon EC2 is to create an AWS account. This is a straightforward process, and AWS's comprehensive documentation offers easy-to-follow guidelines that assist both beginners and experienced users. Once your account is set up, you're ready to launch your first EC2 instance.
AWS Management Console streamlines this process, allowing you to select and deploy an instance that matches your specific needs, such as the Ubuntu EC2 instance.
Security is paramount when operating in the cloud, and AWS offers a secure infrastructure that lets you focus on business development without compromising data privacy. Security groups are a fundamental component of this, acting as virtual firewalls to control the traffic to and from your EC2 instances. Configuring security groups correctly is crucial to protect your applications from unwanted access.
Connecting to your EC2 instance, whether through SSH for Linux-based instances or Remote Desktop for Windows, is the final step to get your environment up and running. It's essential to understand the connection process, which AWS simplifies with its detailed guidance and resources. Remember, the free tier policy is beneficial for new users, but it's important to be aware of its limitations to avoid unexpected charges.
As you embark on this practical journey with AWS EC2, it's a valuable opportunity to build skills that are highly regarded in the job market. The knowledge acquired through setting up and managing your EC2 environment lays a foundation for further exploration into the ever-evolving cloud and cybersecurity landscapes.
Launching an EC2 Instance
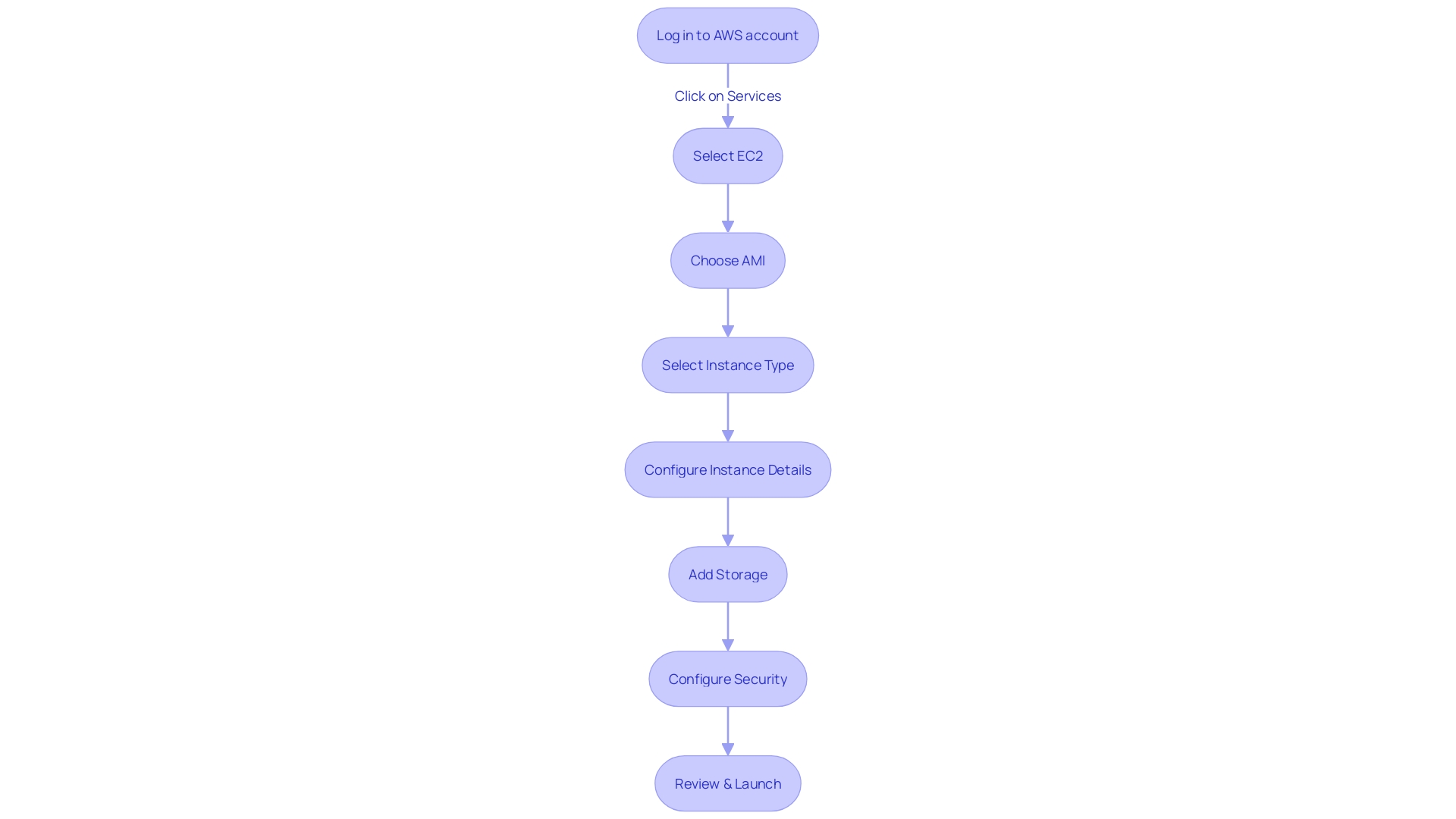
To efficiently launch an EC2 instance, it's imperative to navigate through the various options and configurations AWS provides. This includes making informed decisions such as selecting the appropriate Amazon Machine Image (AMI) that fits your specific needs. With an array of instance types at your disposal, it's crucial to choose one that aligns with the performance requirements of your workloads.
Configuring your instance details is another critical step, involving network settings, storage options, and monitoring configurations. As per AWS's robust security infrastructure, which is a top priority for data-driven companies, you'll also learn how to add persistent storage using Elastic Block Store (EBS) volumes to your instances.
Furthermore, securing your EC2 instances is non-negotiable. AWS offers a multi-layered security approach that allows companies to focus on growth without compromising confidentiality. You'll discover best practices for managing security groups, key pairs, and IAM roles to ensure the highest level of security.
Lastly, the process culminates with a review of your instance's configuration before you proceed to launch. This step-by-step guide is not only aimed at beginners but also serves as a comprehensive reference for experienced users. With AWS's announcement of an independent European cloud, organizations facing stringent regulations now have additional options to fulfill their digital sovereignty requirements, ensuring that your infrastructure is current with global digital trends.
For those new to AWS, a free tier account is available, offering limited usage for the first year. It's crucial to understand the free tier policy thoroughly before launching your instance to avoid unintended charges. By following this guide, you'll have the necessary knowledge to initiate your EC2 instance confidently and efficiently.
Connecting to an EC2 Instance
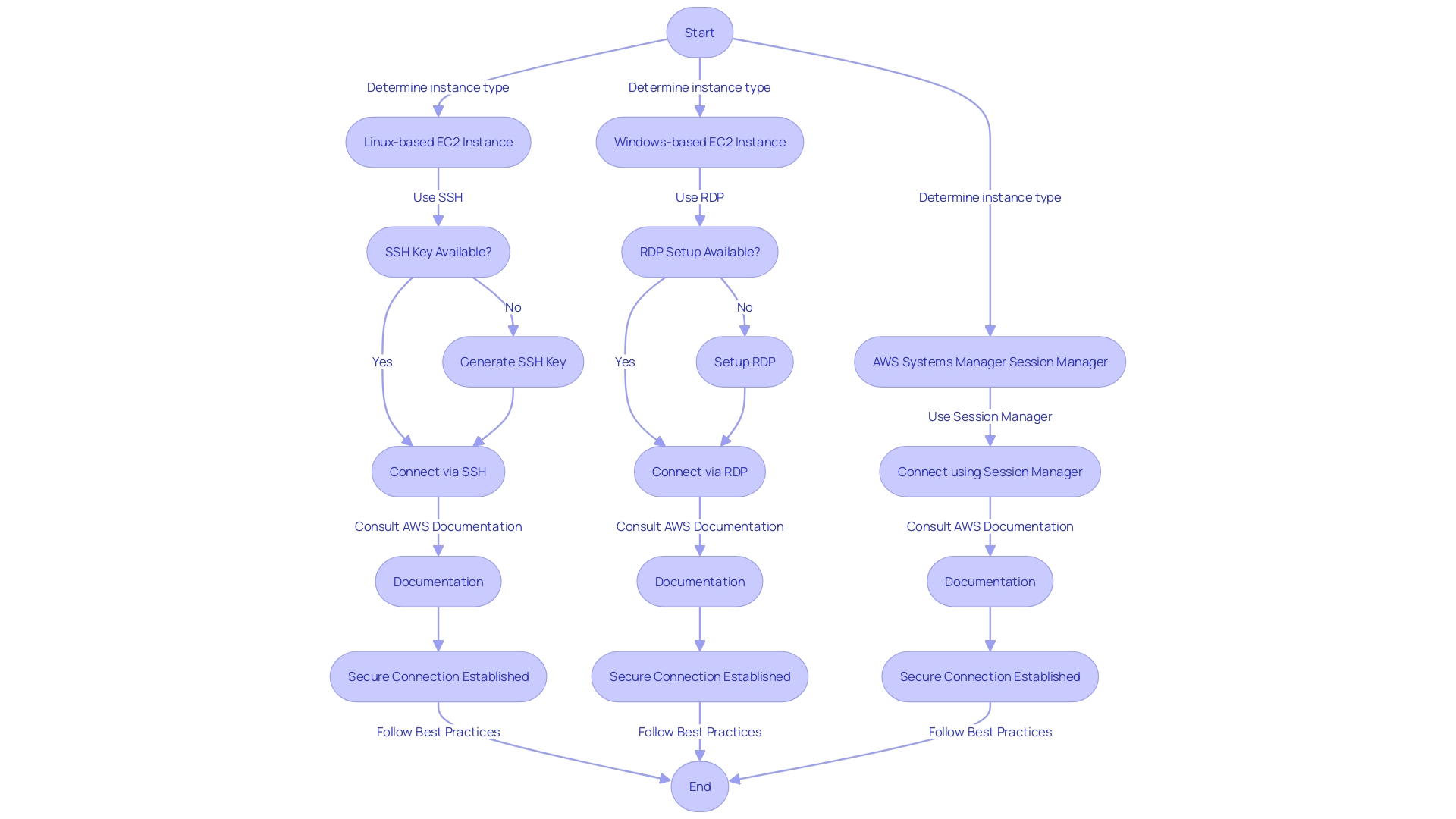
Amazon EC2 instances, essentially virtual servers in the cloud, offer a range of CPU, memory, storage, and networking options to fit any workload. To harness the full power of EC2, it's critical to know how to securely connect to your instances. Let's dive into the different methods available for establishing a connection:
-
SSH (Secure Shell): For Linux-based EC2 instances, SSH is the go-to method for secure remote access. Ensure you have your instance set up, along with the private key file (.pem or .ppk) that's associated with your instance.
-
Remote Desktop Protocol (RDP): Windows-based EC2 instances can be accessed using RDP. This gives you a graphical interface to manage your instance as if you were sitting right in front of it.
-
AWS Systems Manager Session Manager: This is a highly secure way to connect to your EC2 instances that eliminates the need for SSH keys or RDP setup. Session Manager facilitates seamless and secure access, making it a breeze to maintain your instances.
Remember to take advantage of resources such as AWS documentation and support when transitioning to these methods or when enforcing policies like the mandatory use of Instance Metadata Service Version 2 (IMDSv2).
Connecting to your EC2 instance is a foundational skill for any developer or system administrator working with AWS. By following best practices and using the AWS Command Line Interface (CLI), you can manage your virtual machines efficiently, scaling them as needed to ensure optimal performance and cost-effectiveness.
EC2 Instance Types and Configurations
Amazon EC2 (Elastic Compute Cloud) is a pivotal offering from AWS, providing scalable computing resources in the cloud to cater to various workload requirements. The service's versatility is evident in its array of instance types, each optimized for particular performance needs.
-
General Purpose Instances: A balanced mix of compute, memory, and networking resources makes these instances versatile. They are the go-to choice for diverse applications, ranging from web servers to development environments.
-
Compute-Optimized Instances: For workloads that demand high-performance computing, these instances stand out. They are engineered to run batch processing workloads, media transcoding, and high-traffic web applications efficiently.
-
Memory-Optimized Instances: When applications such as in-memory databases and real-time analytics require extensive memory capacity, these instances deliver optimized performance.
-
Storage-Optimized Instances: These instances excel in providing high disk throughput and low latency, ideal for data warehousing and distributed file systems that manage large data sets.
The selection of the right instance type is crucial for achieving the desired efficiency and cost-effectiveness. As quoted by industry experts, "Computer is like a brain... in a cloud world, computing is an important service." The choice between creating an in-house solution or leveraging cloud services like EC2 often depends on the specific business goals and technical requirements.
With the cloud's ability to run modern, scalable workloads on the latest hardware, organizations can enjoy pay-as-you-go pricing and focus on their core business rather than infrastructure management.
The current landscape shows a competitive market among cloud providers, with AWS EC2's market spend showing a downward trend in contrast to Azure's growth. Yet, EC2 remains a strong contender, essential for anyone's AWS journey and capable of supporting everything from simple applications to complex enterprise systems. Understanding each instance type's capabilities and aligning them with your workload needs is key to harnessing the full potential of Amazon EC2.
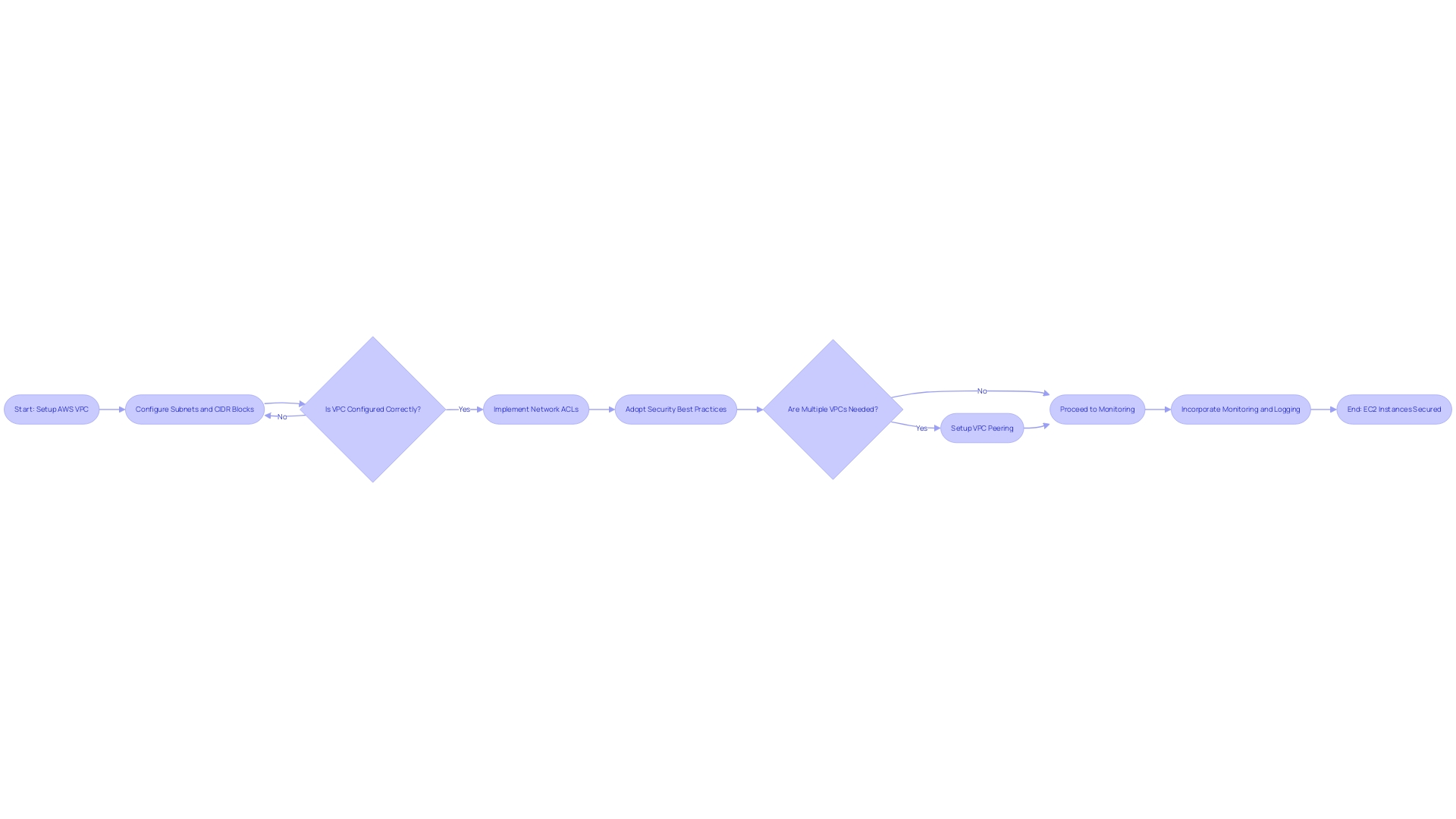
Security and Networking in EC2
Amazon EC2 provides the backbone for a myriad of applications across the globe, and its security and networking capabilities are foundational to the resilience and reliability of services deployed on it. A robust strategy for EC2 involves setting up a Virtual Private Cloud (VPC) that offers a logically isolated environment, ensuring that instances are shielded within your controlled network space. This isolation is further enhanced by configuring subnets and CIDR blocks which play a critical role in structuring the network for efficient traffic management.
Network Access Control Lists (ACLs) are pivotal in safeguarding your subnets, enabling fine-grained control over inbound and outbound traffic, thereby thwarting unauthorized access attempts. It is essential to adopt security best practices such as secure access controls, diligent monitoring, and stringent encryption protocols to fortify your EC2 instances against potential threats. These practices are not just about averting risks but about fostering an ecosystem where privacy, integrity, and resilience are prioritized.
Connecting multiple VPCs through VPC peering can be leveraged for scenarios where cross-account or cross-region communications are necessary, without compromising on the security stance. Take the case of an e-commerce portal with a customer base in Africa, aiming for low-latency access and rapid retrieval of relational user data. The architects must design a solution that is not only fault-tolerant and highly available but also aligns with budget constraints while upholding stringent security measures for both data at rest and in transit.
Incorporating comprehensive monitoring and logging mechanisms further solidifies the security framework, enabling swift response to any anomalies.
Recent initiatives by AWS, such as the Open Cybersecurity Schema Framework (OCSF), underscore the commitment to elevate open source security standards. AWS's active contribution to security-related technologies and sharing of best practices, including responses to vulnerabilities like the Apache Log4j (Log4Shell), provides valuable insights into maintaining a secure application ecosystem.
In today's digital landscape, where the threat of breaches is ever-present, it is vital to recognize that security is not just a technical measure but a core aspect of organizational culture. As one senior software engineer with over a decade of experience articulates, implementing security features is an act of stewardship towards building a more secure digital future for everyone involved.
For organizations operating in the cloud, the management of static, long-lived credentials remains a pressing issue, as they are a predominant cause of security breaches. A shift towards centralized identity management and the adoption of short-lived credentials can significantly mitigate this risk, as evidenced by analysis across AWS, Azure, and Google Cloud platforms.
Ultimately, ensuring the integrity and availability of your EC2 instances is not a one-off task but a continuous endeavor, requiring vigilance, adaptation, and a proactive approach to security and networking configurations.
Pricing Models for Amazon EC2
Grasping Amazon EC2's pricing models is crucial for cost optimization and making savvy decisions. Let's delve into these models:
-
On-Demand Instances: This model offers a pay-as-you-go approach, charging for compute capacity by the hour without requiring long-term commitments. It's ideal for projects with variable workloads that cannot be interrupted.
-
Reserved Instances: They offer a notable cost reduction, suitable for applications with consistent usage patterns. By committing to EC2 capacity for a 1 or 3-year term, businesses can save up to 75% over On-Demand rates.
-
Spot Instances: These instances allow you to bid for unused EC2 capacity at potentially lower rates, providing cost savings of up to 90% compared to On-Demand prices. However, they can be interrupted with two minutes of notification, making them suitable for flexible workloads.
-
Dedicated Hosts: With Dedicated Hosts, you get physical servers fully dedicated to your use, which can help meet compliance requirements and provide more control over instance placement.
To manage EC2 costs effectively, employing strategies like rightsizing instances, auto-scaling, and taking advantage of Spot Instances can be impactful. According to a DigitalOcean survey, 89% of respondents reported increases in cloud spending, underscoring the importance of cost management.
Furthermore, the Well-Architected Framework's Cost Optimization pillar highlights that cost optimization is an ongoing process throughout a workload’s lifecycle. By integrating financial and technological expertise, businesses can refine cost management strategies, ensuring technology investments align with business outcomes and maximize ROI.
Use Cases for Amazon EC2
Amazon EC2 (Elastic Compute Cloud) is renowned for its flexibility, catering to a myriad of use cases across different industries. One notable scenario is web application hosting. With EC2's ability to scale according to demand, businesses can ensure high availability for their web applications.
This robust infrastructure is particularly advantageous for e-commerce platforms that require the agility to handle varying traffic loads without compromising on performance, a factor that is closely tied to customer retention.
For data-intensive tasks, EC2 stands out in big data processing. Companies like Talent.com, which aggregates millions of job listings globally, rely on the efficient analysis of large datasets to drive their matching algorithms—an essential component of their service delivery. In such contexts, EC2's computing power can be harnessed to process vast amounts of data swiftly, making it an indispensable tool for businesses whose core operations depend on data analytics.
High-performance computing (HPC) is another domain where EC2's capabilities are leveraged. From scientific simulations to financial modeling, EC2 provides the computational might required for complex calculations, enabling researchers and financial analysts to achieve breakthroughs in their respective fields.
Moreover, in the realm of DevOps and Continuous Integration/Continuous Deployment (CI/CD), EC2 facilitates the creation of efficient pipelines and automation of testing. Infrastructure as code (IAC) is also supported, streamlining the management and deployment of IT resources, thereby enhancing productivity and innovation within technology teams.
By understanding these diverse applications of Amazon EC2, companies can envision how this service can be integrated into their own technological framework to drive growth and maintain a competitive edge in their industry.
Managing and Monitoring EC2 Instances
Efficiently managing and monitoring Amazon EC2 instances is paramount to maintain their performance, reliability, and cost-effectiveness. Amazon EC2 Auto Scaling ensures that the number of EC2 instances you're using adjusts automatically based on the actual demand, keeping the balance between performance and cost. Amazon CloudWatch offers robust monitoring tools that allow you to set custom metrics, alarms, and create intuitive dashboards for real-time visibility into your operations.
AWS Systems Manager is an invaluable suite of tools for streamlined management. It enables features such as Session Manager for secure instance access, Parameter Store for managing configuration data, and automation for routine tasks. AWS Trusted Advisor acts as your guide to optimize for cost, improve performance, and enhance security and fault tolerance.
For those looking to extract deeper insights from their EC2 instances, Grafana, an open-source analytics and monitoring platform, can be configured on Amazon EC2. It offers powerful visualization capabilities, which, combined with EC2's scalability, provide a stable environment for monitoring. Setting up Grafana involves configuring the inbound rules of your EC2 instance to allow access to port 3000, as Grafana operates on this port.
Recent advancements have also seen the introduction of Amazon EC2 Capacity Blocks, which allow for the reservation of instances for a defined time block, providing cost certainty and resource optimization. This is particularly beneficial for tasks requiring access to high-demand GPUs, such as running large language models or AI-related jobs.
To start, one must establish an IAM role and enable an agent on the instance that communicates with Systems Manager. Following best practices, run the AWS-UpdateSSMAgent document to upgrade the Systems Manager Agent, and then use Systems Manager to execute commands on your instance.
As we delve into EC2 management, it's clear that Amazon EC2 serves as a formidable resource in AWS cloud computing, providing the flexibility to scale computing resources as needed. Embracing these tools and techniques will greatly enhance your ability to manage and monitor your virtual servers effectively.
Best Practices for Using Amazon EC2
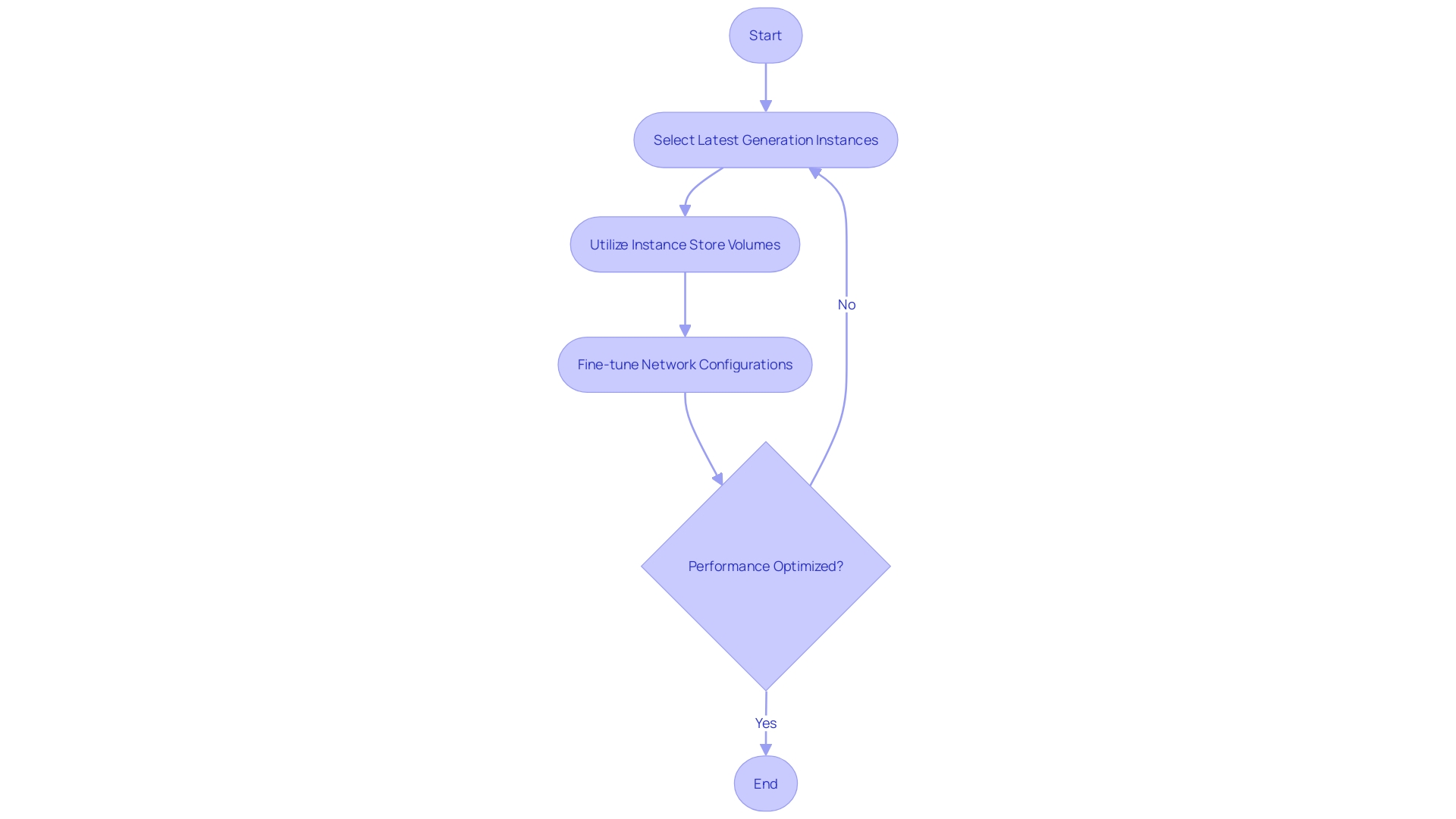
To harness the full potential of Amazon EC2, it is imperative to adopt certain best practices that ensure optimal performance, high availability, robust security, and effective disaster recovery. Optimizing Instance Performance is critical; this involves selecting the latest generation instances, utilizing instance store volumes, and fine-tuning network configurations to enhance the performance of your EC2 instances. For example, companies like GoDaddy have streamlined their operations by optimizing batch processing jobs, following a structured methodology for improvement.
In terms of Implementing High Availability, leveraging multiple availability zones and incorporating load balancing are fundamental practices. Automated failover systems play a crucial role in maintaining uninterrupted service, similar to how Talent.com relies on AWS's extensive services to ensure their platform remains highly available and reliable for millions of job seekers.
Backup and Disaster Recovery strategies are essential to safeguard EC2 instances. Employing EBS snapshots and cross-region replication provides a safety net against data loss. For instance, AWS's comprehensive documentation supports users in implementing resilient backup and recovery mechanisms.
Lastly, Security and Compliance necessitate a vigilant approach, including encryption, access controls, and consistent security audits to protect EC2 environments. As AWS continues to lead the market, reflected in its rising stock valuation and widespread adoption, maintaining stringent security standards remains crucial for businesses operating in the cloud.
Conclusion
In conclusion, Amazon EC2 is a versatile and powerful service that simplifies web-scale cloud computing for developers. With key components like instances, AMIs, regions, security groups, EBS, and ELB, EC2 provides a robust infrastructure for scalable and secure applications.
Getting started with EC2 is easy with AWS's comprehensive documentation and user-friendly interface. By creating an account, launching instances, and securely connecting to them, users can quickly harness the power of EC2.
Launching an EC2 instance involves careful configuration and selection of the appropriate AMI and instance type. AWS's guide ensures optimal performance and scalability.
Securely connecting to EC2 instances is essential, and methods like SSH, RDP, and Session Manager provide secure remote access. AWS's resources simplify the process and facilitate efficient management.
EC2 offers a wide range of instance types tailored to different workload requirements. From general-purpose to compute-optimized, memory-optimized, and storage-optimized instances, users can choose the most suitable option.
Security and networking capabilities in EC2 are foundational to reliability and resilience. Configuring VPCs, subnets, and implementing security measures ensure a secure environment.
Understanding EC2's pricing models is crucial for cost optimization. On-Demand Instances, Reserved Instances, Spot Instances, and Dedicated Hosts offer flexibility and cost savings.
EC2's use cases span various industries, including web application hosting, big data processing, high-performance computing, and DevOps. Its scalability and agility make it a valuable tool for driving growth.
Efficient management and monitoring of EC2 instances are vital for performance and cost-effectiveness. AWS tools like Auto Scaling, CloudWatch, and Systems Manager provide comprehensive capabilities.
By adopting best practices, businesses can optimize performance, ensure high availability, implement robust security measures, and establish effective disaster recovery strategies with EC2.
In summary, Amazon EC2 empowers organizations by providing a scalable and secure infrastructure. Its ease of use, extensive documentation, and reputable market leadership make it a valuable resource for businesses in cloud computing. By leveraging EC2's capabilities, organizations can innovate, grow, and succeed in the digital landscape.




