Introduction
CloudFormation: Simplifying Infrastructure Management and Deployment
As organizations increasingly rely on cloud computing, the need for efficient and reliable infrastructure management and deployment becomes paramount. Enter AWS CloudFormation, a powerful service that enables users to automate the deployment of complex environments, ensuring consistency and scalability. In this article, we will explore the benefits of using CloudFormation, learn how to set up your environment, dive into writing CloudFormation templates, understand the template structure, and discover best practices for template development.
We will also discuss common use cases and examples, troubleshooting and debugging techniques, and the management of multiple stacks. With CloudFormation, businesses can streamline their infrastructure management processes, enhance reliability, and achieve their organizational goals in the dynamic cloud computing landscape.
Benefits of Using CloudFormation
CloudFormation's capabilities extend well beyond simple infrastructure management, offering a structured way to automate the deployment of complex environments. For instance, Dunelm Group plc leverages CloudFormation to manage their expansive digital platform, which is critical to their revenue, signifying the tool's capacity to handle high-traffic systems. Similarly, Chime Financial employs CloudFormation to ensure the integrity and security of their financial services, underscoring the service's utility in maintaining robust, compliant, and secure infrastructures even in heavily regulated industries.
By utilizing CloudFormation templates, organizations can articulate their infrastructure requirements, including servers, databases, and network configurations, all within a virtual architecture. This not only facilitates consistent deployments but also allows for the intricate orchestration of resources that align with specific compliance mandates. As such, AWS Amplify and AWS Application Composer have emerged as valuable tools for managing cloud applications, with CloudFormation being pivotal in infrastructure as code (IAC) practices.
IAC affords benefits like version control and code reuse, while empowering teams to manage infrastructure changes with the same rigor as software modifications.
Furthermore, the nature of evolving services like AWS Amplify and Application Composer necessitates staying abreast with the latest updates to capitalize on new features that refine the management of cloud applications. These continuous enhancements ensure that CloudFormation remains a critical tool for the automated, declarative provisioning of AWS resources, integral for companies like Dunelm and Chime that demand reliability and scalability from their technological frameworks.
Setting Up Your Environment
Embarking on the journey of utilizing AWS CloudFormation requires a foundational understanding and setup of your environment. This involves not just installing tools like the AWS CLI but also grasping the essentials of CloudFormation templates and the initialization process. By exploring a real-world example, such as setting up an Elastic Container Service (ECS) cluster across various subnets, we can appreciate the balance CloudFormation strikes between accessibility, security, and performance.
Diving into the specifics, you'll need to create an IAM role for your resources, which can be accomplished by initializing a CloudFormation template and declaring the IAM role within. This step is crucial for access management and ensuring secure interactions with CloudFormation services. A template example, when deployed, visibly results in the creation of an IAM role, illustrating the tangible outcomes of your setup efforts.
Moreover, understanding the initialization process is integral to managing AWS resources effectively. CloudFormation templates serve as the blueprint for your infrastructure, enabling you to automate and streamline the deployment process. This methodology is not only a time-saver but also reduces the risk of manual errors, providing a repeatable and reliable means to provision your AWS environment.
The importance of CloudFormation in the cloud computing landscape cannot be overstated. As emphasized by industry experts, the service is a cornerstone for Infrastructure as Code (IAC), offering notable benefits such as version control, code reuse, and treating infrastructure modifications with the same rigor as software changes. Additionally, the automation capabilities of CloudFormation allow for seamless provisioning of resources, a testament to the efficiency gains it provides.
Statistics from various industry solutions highlight the intricate nature of CloudFormation at work. For instance, the architecture for data extraction and storage showcases the interaction between different components and AWS services, which together form a robust solution built upon CloudFormation's capabilities.
To ensure that you're well-prepared to navigate CloudFormation's environment, it's paramount to have the necessary permissions, which are secured through the creation of access keys via the AWS CLI—a step that's as critical as it is straightforward. This setup paves the way for a smooth and secure management of your cloud infrastructure, enabling you to leverage the full spectrum of CloudFormation's offerings.
As we move forward, it becomes increasingly clear that CloudFormation is not just a tool but a strategic enabler for organizations like Vodafone, which has partnered with Microsoft to scale its IoT business and enhance customer experiences using cloud solutions. Such partnerships underscore the transformative potential of Cloud Formation in driving business innovation and success in the dynamic cloud computing arena.
Writing Your First CloudFormation Template
Embarking on the journey of writing your inaugural CloudFormation template, it's essential to grasp the template's anatomy, which serves as the blueprint for your AWS infrastructure. A CloudFormation template is structured into several key sections including parameters, resources, and outputs, each with a distinct function.
Starting with parameters, these act as the customizable elements of your template, allowing you to input values that can be referenced throughout the template, facilitating flexibility and reusability. The resources section is the core of your template, where you define the AWS services and components that you wish to provision. It's where you articulate what you need, akin to listing ingredients for a recipe.
For example, if you're setting up an S3 bucket, its declaration would resemble AWS::S3::Bucket, allowing CloudFormation to provision it as specified.
Outputs are another crucial section, providing a way to output values that can be used elsewhere in your AWS environment or in other CloudFormation stacks. This could be an endpoint URL, an ARN, or any other significant piece of information resultant from the creation of your resources.
The power of CloudFormation lies in its ability to turn complex infrastructure configurations into a simple, readable code format, which can be version-controlled, shared, and reused. This aligns with the principles of Infrastructure as Code (IAC), which emphasizes the management of infrastructure through machine-readable definition files, rather than physical hardware configuration or interactive configuration tools.
Furthermore, the automation capabilities CloudFormation provides enable swift and consistent deployments. It streamlines the process of infrastructure provisioning, removing manual intervention and reducing the scope for human error.
As you construct your CloudFormation template, think about the infrastructure you're aiming to deploy and how the template's sections come together to define it. By the conclusion of this process, you'll have laid a strong foundation for developing robust, scalable CloudFormation templates, paving the way for more efficient and automated infrastructure management.
Understanding Template Structure
AWS CloudFormation templates are the blueprint for your AWS infrastructure, akin to a recipe in cloud computing that details every ingredient needed for your application's environment. At the heart of CloudFormation's power is the ability to define all the AWS resources you require within a single, version-controlled document, which can be deployed and updated consistently.
The template is composed of several key sections—each plays a vital role in the orchestration of AWS services. For instance, 'Mappings' provide a way to manage environment-specific variables, 'Conditions' can dictate when specific resources are created, and 'Metadata' offers details about the template itself or the resources within it.
Creating a simple template, such as one for a new S3 storage bucket named 'easyonebucket,' illustrates the straightforward nature of CloudFormation. You specify the resource type, in this case, 'AWS::S3::Bucket,' and CloudFormation handles the provisioning. This encapsulates the template's essence: describe what you need, and let the automation do the heavy lifting.
By leveraging the Infrastructure as Code (IAC) methodology, CloudFormation enables not just version control and code reuse, but also the automation of infrastructure provisioning. These attributes are particularly beneficial for organizations striving for efficient and secure cloud infrastructure deployment. A practical example of this can be seen in the ECS cluster template, which sets up an orchestrated environment balancing accessibility, security, and performance, demonstrating the sophistication and control CloudFormation offers.
Furthermore, CloudFormation's capacity to manage infrastructure as code and automate the process is exemplified by organizing resources into logical stacks. Consider the Flat File Handler stack, which centralizes the deployment of all resources necessary for handling flat files received via SFTP, showcasing how CloudFormation simplifies complex workflows into manageable sections. This results in a system where infrastructure modifications are treated with the same rigor and traceability as software updates, enhancing overall operational efficiency.
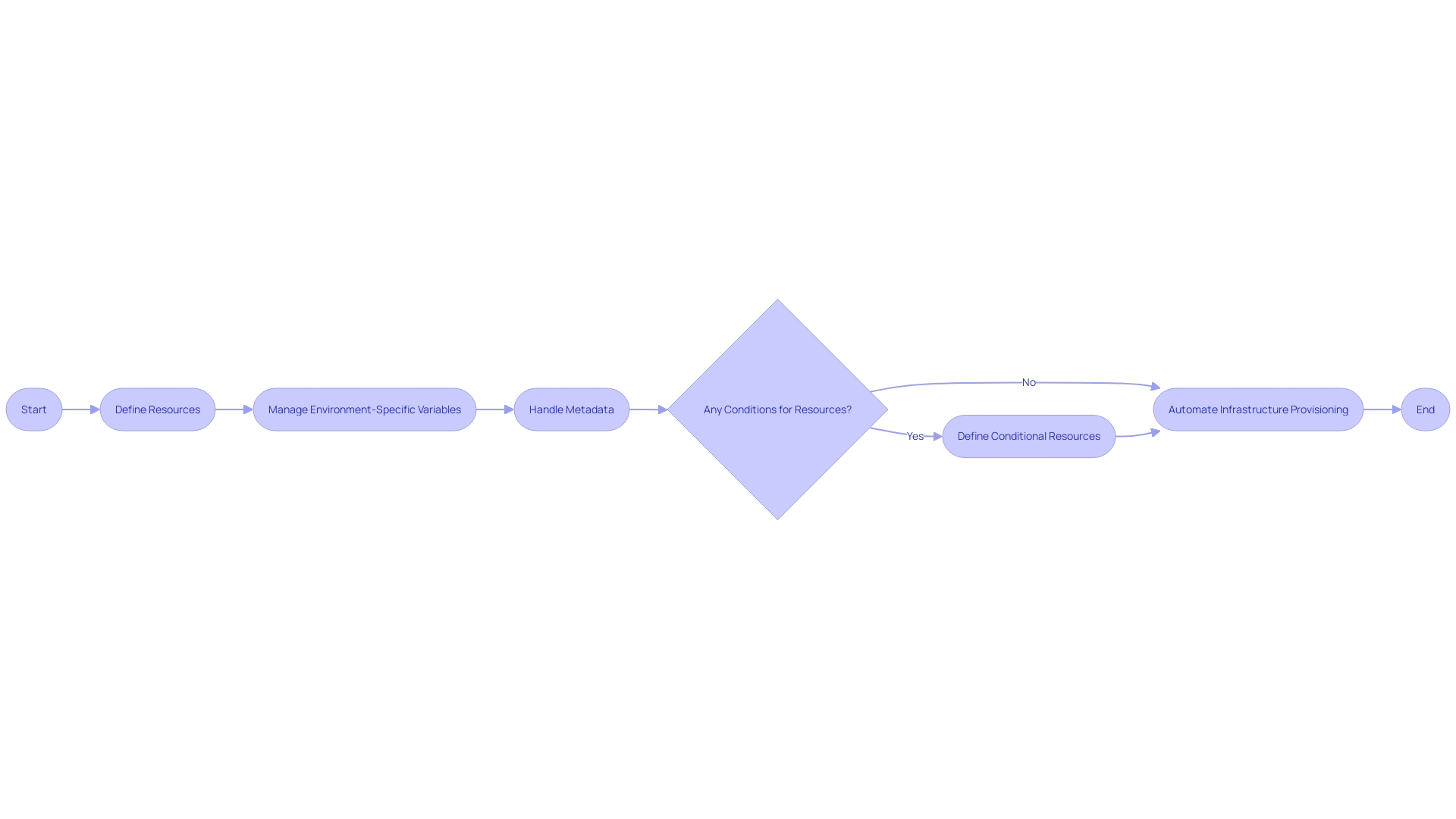
Parameters, Resources, and Outputs
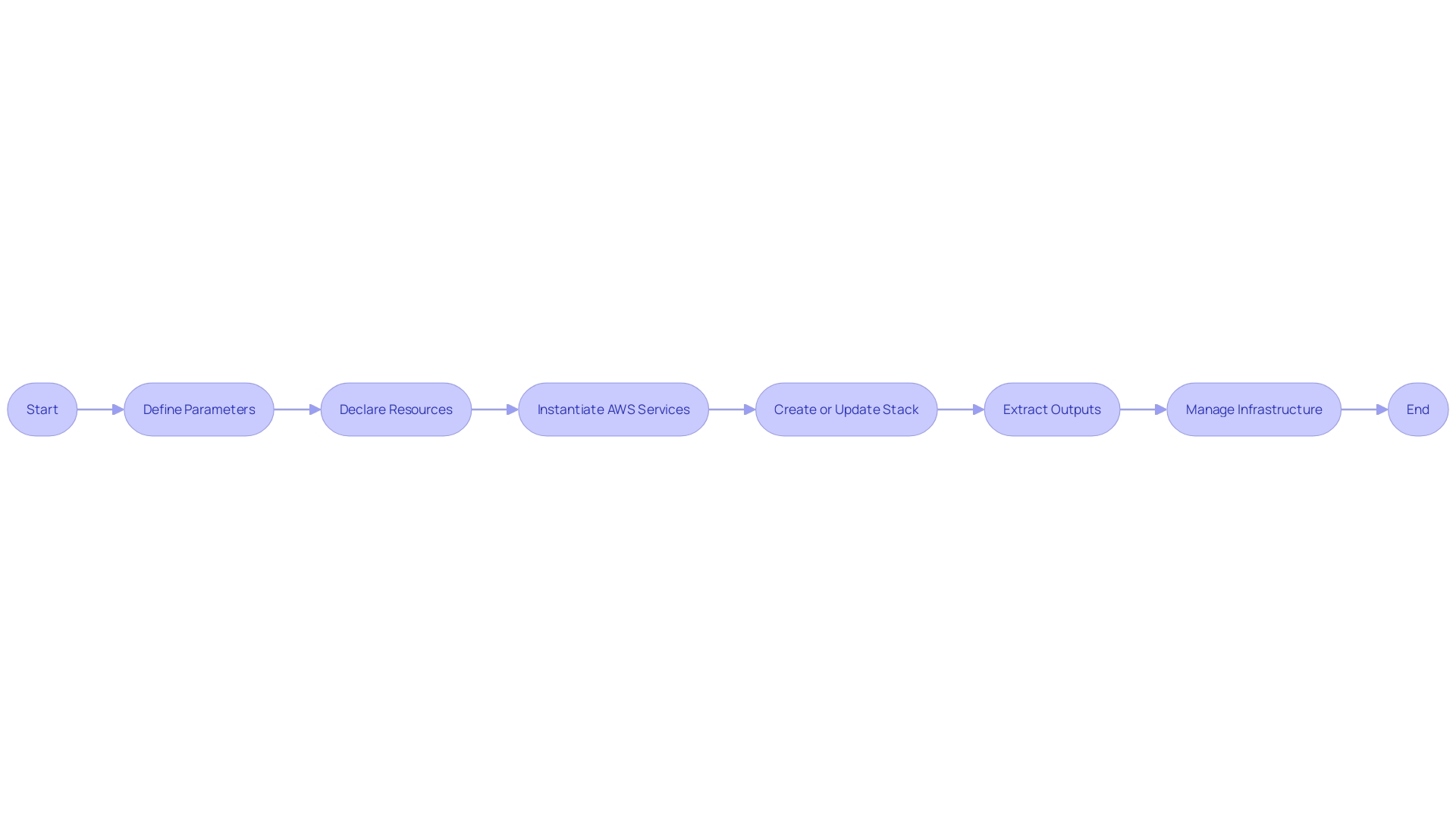
Understanding the structure and capabilities of CloudFormation templates is critical for efficient infrastructure management. Parameters within a template offer the flexibility to customize deployments, allowing users to input specific values during stack creation or update operations. This customizability ensures that a single template can be repurposed across different environments or scenarios by simply altering the parameters instead of the core template structure.
Resources are the backbone of a CloudFormation template, representing the AWS services that will be deployed. For instance, when constructing a storage solution, specifying an AWS::S3::Bucket resource within your template automatically handles the creation of a new S3 bucket, named per your configuration. The resource declaration includes the type and properties of the service, such as an IAM role necessary for a bot's operation, which can be defined within the template and instantiated upon deployment.
Outputs are equally essential, serving as a mechanism to retrieve valuable information post-deployment, such as endpoints, Arms, or other crucial data generated during the creation of resources. They enable the extraction of key results from the stack, which can be used in other stacks or returned to the user for reference.
By leveraging sample configurations, as suggested by the AWS Cloud Control provider feedback, users can efficiently initiate projects with pre-filled attribute values, reducing setup complexity and potential errors. These configurations act as starting points, offering structured examples that can be customized to fit unique requirements.
Furthermore, the open-source community's contributions to tools like 'cfnupd' enhance users' ability to maintain and update their CloudFormation stacks, exemplifying the power of shared knowledge and resources in the field of infrastructure as code (IAC).
Testing and Validating Your Template
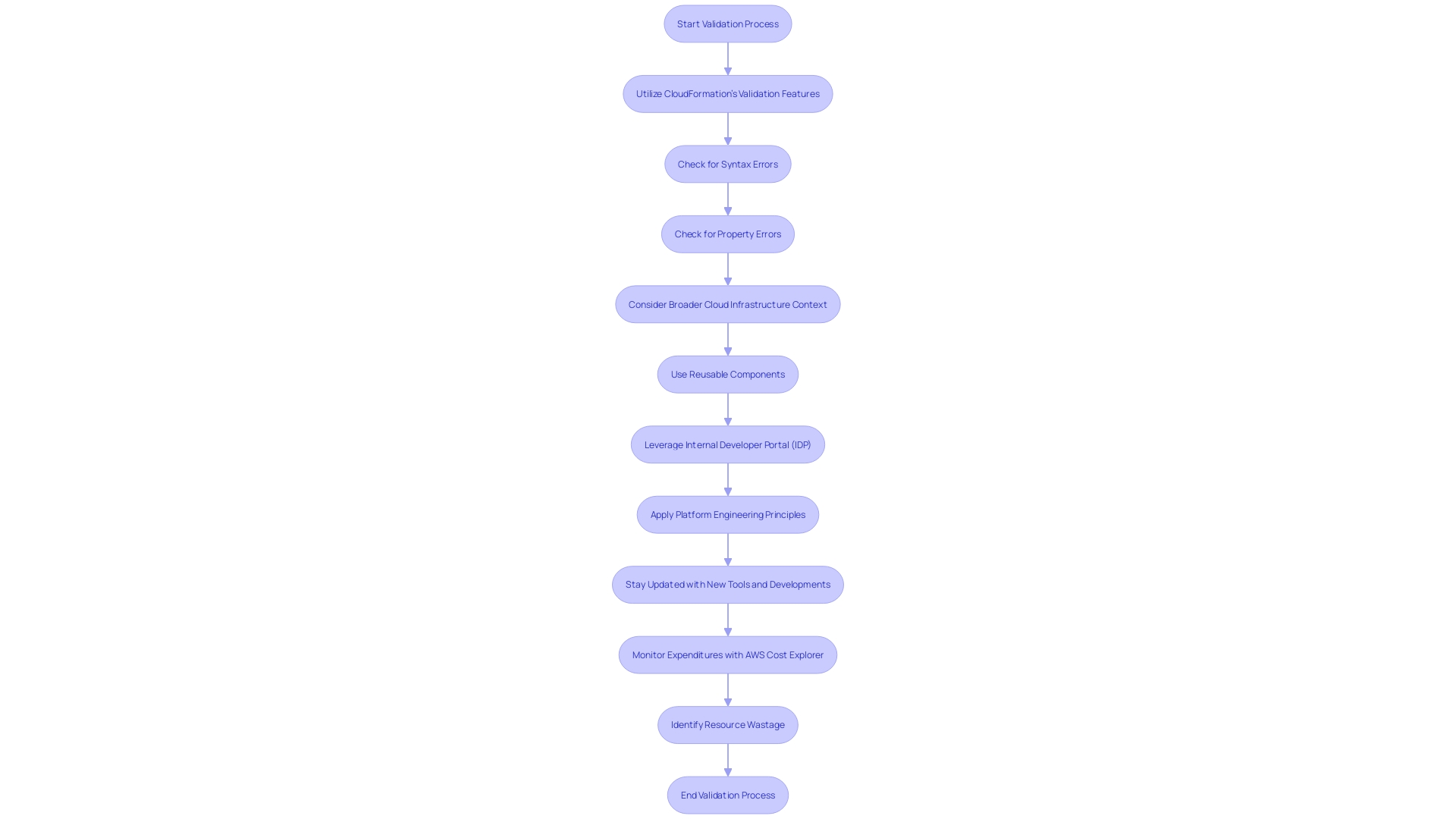
Ensuring the fidelity of your CloudFormation templates is a critical step before deployment. The process begins by utilizing CloudFormation's validation features to check for syntax and property errors in your templates. It is akin to following a detailed recipe for cloud resource creation, where the template details the resources like storage buckets or IAM roles, and CloudFormation brings them to life.
For instance, when setting up an IAM role through a CloudFormation template, you can witness the role coming to existence upon deployment.
As part of this validation, it's also essential to consider the broader context of your cloud infrastructure. DevOps and platform engineering teams often employ reusable components to streamline deployments. This approach not only reduces complexity but also enhances speed and safety through standardized builder tooling.
By leveraging internal developer portals, you can kickstart projects effectively, tapping into the shared knowledge and tooling within your organization.
To shed light on the practical application of these principles, consider the case where you create a CloudFormation template to instantiate an IAM role for a specific function. Once you've downloaded and deployed the example template, the IAM role materializes, demonstrating the template's efficacy. This modular approach echoes the sentiments of industry leaders who advocate for repeatable processes to be encapsulated as modules, enhancing efficiency and reducing the risk of errors that could lead to outages or security vulnerabilities.
Moreover, it's crucial to keep abreast of new developments and tools that can aid in identifying resource wastage. For instance, Terraform's Test Framework can now pinpoint unused provisioned resources, allowing for automated resource reclamation. Similarly, AWS Cost Explorer serves as a valuable tool for monitoring expenditures and resource usage, ensuring that your cloud operations remain cost-effective and aligned with your organizational goals.
In conclusion, testing and validating your CloudFormation template is not just a technical necessity but a strategic exercise that encompasses best practices, governance, and continuous learning. By doing so, you're not only ensuring the reliability of your deployment but also aligning it with the latest trends and tools that promote efficient and secure cloud management.
Using CloudFormation Linter (cfn-lint)
Linters are indispensable in software development, serving as automated tools that meticulously scan source code for potential errors, bugs, stylistic inconsistencies, and non-adherence to coding standards. The CloudFormation Linter, commonly referred to as cfn-lint, is a prime example of such a tool, tailored for AWS CloudFormation templates. With cfn-lint, developers can ensure their infrastructure as code (IAC) is not only error-free but also compliant and secure by design.
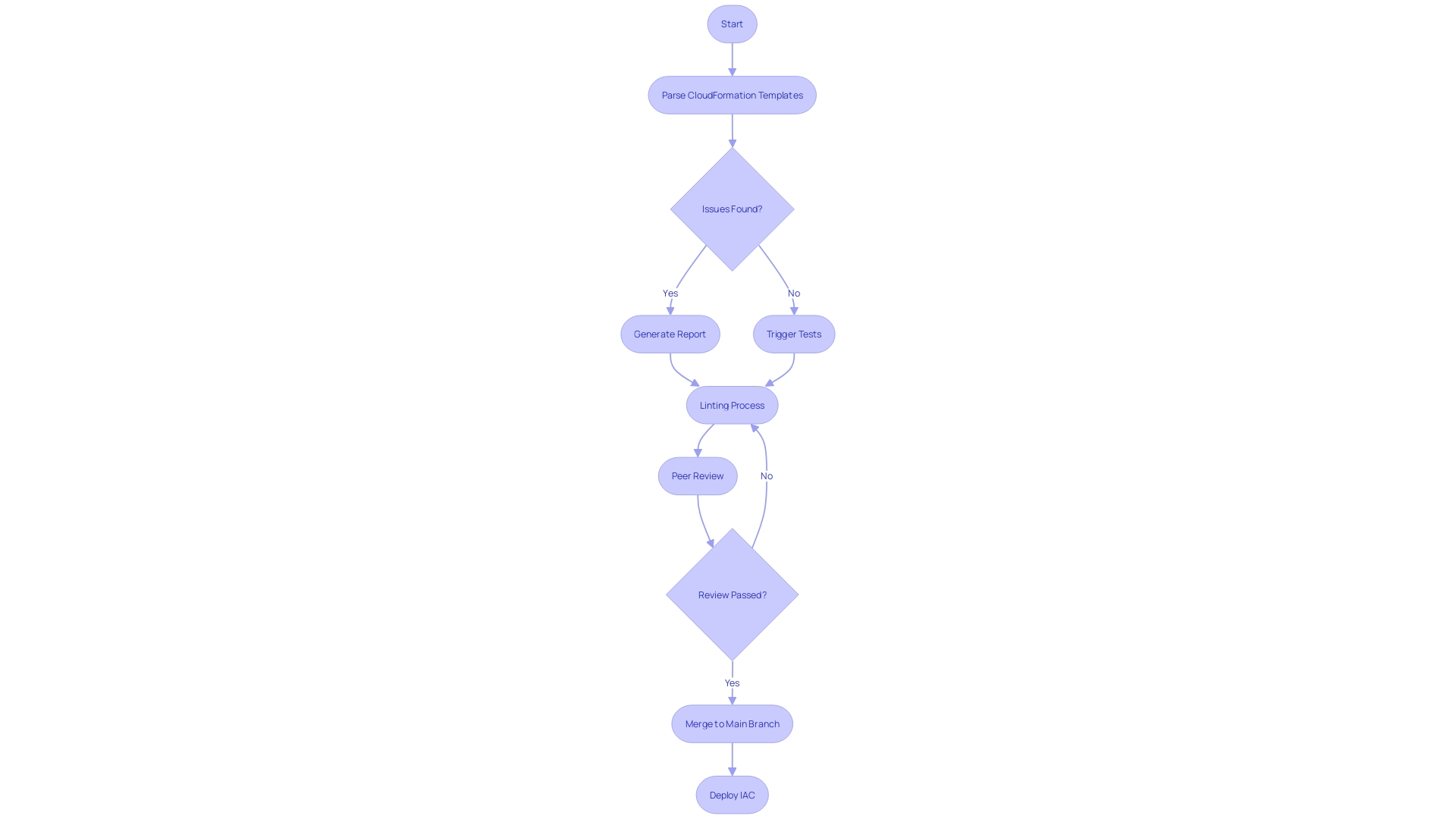
As we delve into the capabilities of cfn-lint, we find it parses CloudFormation templates, identifying patterns indicative of common issues. The tool provides detailed reports, pinpointing problems and their locations, streamlining the debugging process. By integrating cfn-lint into the development workflow, specifically within a CI/CD pipeline, a developer's push to a feature branch can automatically trigger tests and linting.
This process is neatly showcased in a system where a pull request, depending on the target branch, initiates a CodeBuild project running these validations. Upon successful linting, the CodeChecker grants approval, needing just one more peer review before merging to the main branch. This not only elevates the quality and maintainability of the templates but also aligns with the DevOps paradigm of continuous integration and delivery, contributing to the impressive feat of deploying compliant and secure infrastructure at scale.
Embracing open source tools like cfn-lint fosters a collaborative environment where developers can engage with maintainers, providing feedback and contributing to the evolution of the tool. This engagement is a testament to the vibrant open source community, where contributions from individuals like Konstantinos Keramaris and teams across companies like Tenable and AWS shape the future of software development and deployment.
Deploying Your Stack
Deploying your CloudFormation stack is a critical step in managing your AWS infrastructure. The deployment process involves various options that allow you to create and update stacks as well as manage resources efficiently. To initiate the deployment, you typically start by defining an IAM role within your CloudFormation template, which serves as a foundation for further resource initialization.
For example, initializing a bot's IAM role involves adding it as a resource in your CloudFormation template. By downloading and deploying a provided example template, you can effortlessly create the necessary IAM roles.
In the context of AWS CloudFormation, understanding the service's capability to define and provision infrastructure through code is pivotal. CloudFormation templates act as blueprints for your AWS resources, enabling you to deploy complex environments predictably and repeatedly. As new features continuously enhance services like AWS Amplify and AWS Application Composer, keeping abreast of these developments ensures you select the tools that best meet your compliance and operational requirements.
When dealing with deployments, it's also essential to consider rollback strategies and failure management. CloudFormation supports these scenarios, ensuring that your business operations are minimally disrupted during migrations. This support is crucial in maintaining the 143 compliance certifications that Amazon boasts, all while deploying up to 150 million times per year.
As you navigate through the deployment process, it is also beneficial to understand the broader context, such as the reasons for migrating to the cloud. Factors like the need to handle increased demand, the agility to scale at your own pace, and the flexibility offered by services like AWS Glue for data integration and SageMaker for machine learning model deployment come into play. These considerations guide you in creating a comprehensive cloud migration strategy that encompasses technical, operational, financial, and security aspects.
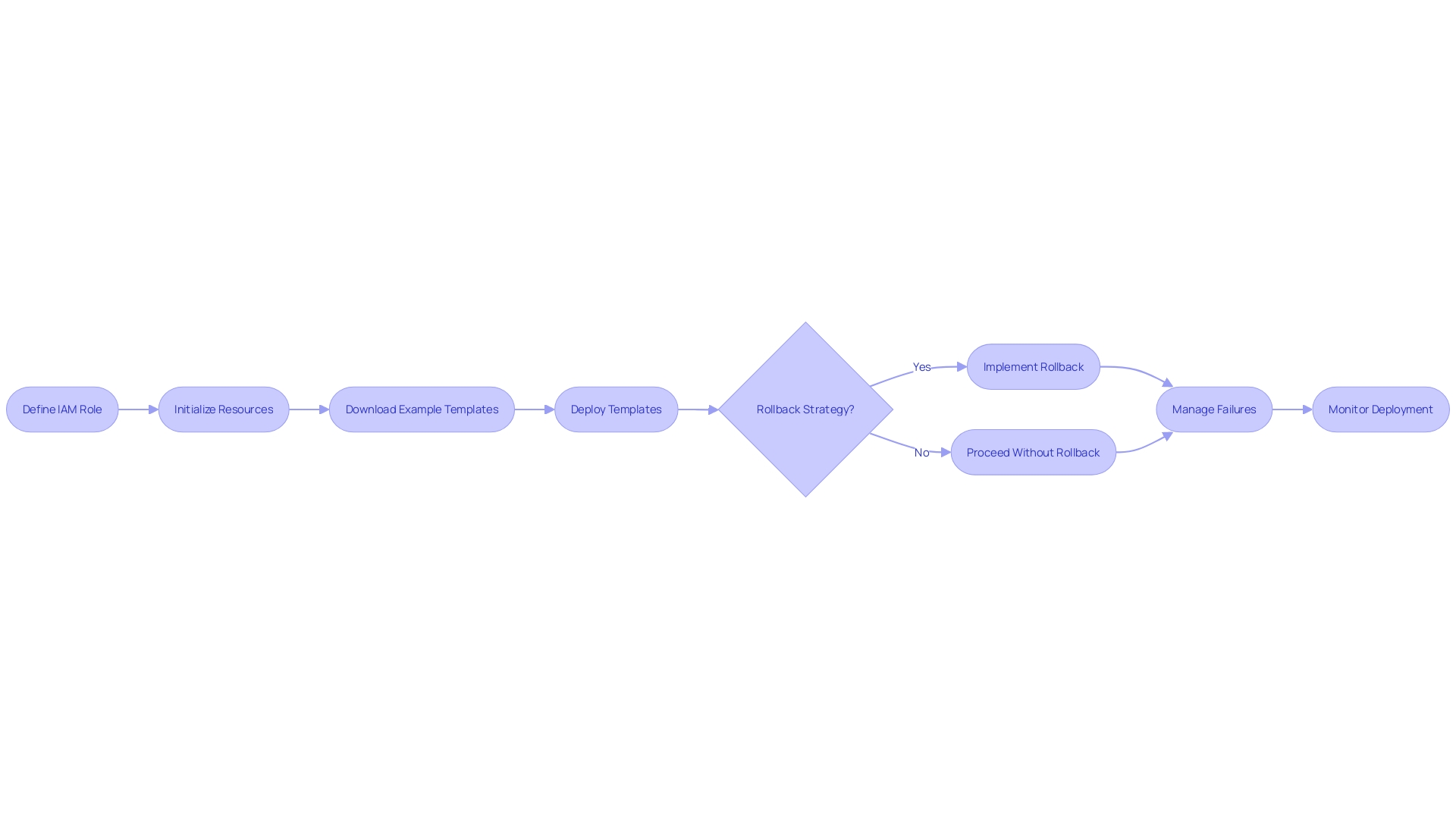
Creating Deployment Scripts
Automation in cloud infrastructure is a game-changer for deploying complex systems with efficiency and precision. AWS CloudFormation is an exceptional tool that allows the definition and provisioning of infrastructure resources in your AWS account. By scripting deployments, you encapsulate the complexity of your infrastructure in code, enabling repeatable and reliable execution of tasks.
Utilizing AWS CloudFormation, you can craft templates that describe the AWS resources required for your applications, ensuring that infrastructure deployment becomes a predictable and automated process. One fundamental step involves establishing an IAM role, which is crucial for resource access during operations. The initialization of a CloudFormation template allows you to define such a role as a resource within the template itself.
For instance, you can start by creating a CloudFormation template for initializing an IAM role to grant the necessary permissions for a bot designed to book hotels. Upon deployment of the example template, an IAM role materializes, ready for use. This modular approach to template design means you can merge incremental changes progressively, refining your infrastructure with each iteration.
Moreover, the integration of AWS CloudFormation with developer tools such as CodeCommit allows you to manage your application's infrastructure alongside its code. For example, to set up a deployment pipeline, you simply download a pipeline.yml template from a CodeCommit repository and create a new stack in the CloudFormation console using this template.
The CloudFront Hosting Toolkit is another powerful feature that simplifies the deployment of web applications by automating the creation of the necessary infrastructure. It enables the hosting of static front ends, incorporating security and caching best practices, while giving developers the flexibility to customize the content delivery network to enrich the user experience with custom logic.
To underscore the significance, CloudFormation is acknowledged by experts as a quintessential element of Infrastructure as Code (IAC), offering automation, version control, and code reuse. This transforms the way we handle infrastructure, treating it much like software—continuously improving and adapting to new requirements.
As AWS continues to innovate and expand its offerings, businesses and individuals leverage its services more extensively, making AWS outages impactful on a large scale. Open source contributions significantly enrich the cloud ecosystem, and engaging with these projects can provide valuable insights and opportunities for feedback or contribution.
In conclusion, by embracing AWS CloudFormation and associated toolkits, organizations can achieve an optimal balance between managed service convenience and the ability to customize their application infrastructure, thus streamlining their deployment processes and enhancing their cloud strategies.
Managing Multiple Stacks
As enterprises expand their cloud footprint, the complexity of managing multiple CloudFormation stacks can become a significant challenge. Mastering the orchestration of these stacks is crucial for maintaining an efficient and organized infrastructure. Focusing on how to effectively structure your stacks, address inter-stack dependencies, and streamline stack operations is paramount.
Structuring CloudFormation stacks thoughtfully can mirror the organizational blueprint of your company, aligning technical resources with business units, much like the template.yml that delineates an organizational structure.
Moreover, the management of these stacks can be further optimized by leveraging AWS services such as AWS Amplify and AWS Application Composer, which can assist in crafting and administering cloud applications tailored to specific operational needs. These tools are constantly evolving, with new features that can be critical in managing complex cloud environments.
The significance of a well-architected environment becomes evident when considering companies that have transitioned from a single AWS account to multiple accounts for specialized functions. This evolution necessitates a robust framework for governing security policies and streamlining logging.
In the realm of platform engineering, where teams construct toolchains and services to support workloads, governance plays a crucial role. At Amazon, the effectiveness of platform engineering is demonstrated by their ability to maintain numerous compliance certifications and achieve frequent deployments.
To manage your cloud infrastructure effectively, understanding the importance of modules in scaling processes is essential. These modules, which encapsulate repeatable processes, can be sourced from a registry and integrated into your codebase. However, due diligence is required as errors within a module can propagate across the ecosystem, emphasizing the need for a meticulous testing framework.
Lastly, the choice of backend in Terraform is a vital decision in infrastructure management. Backends not only determine the state storage location but also the methodology for state locking, which is critical for avoiding conflicts in large-scale infrastructures. Selecting the appropriate backend type, whether local or remote, can significantly impact the predictability and efficiency of infrastructure operations.
Best Practices for Template Development
To enhance the efficacy of your CloudFormation templates, embracing best practices is paramount. These practices not only fortify the templates' reliability and scalability but also simplify their management. Modularization, for instance, compartmentalizes your infrastructure into manageable, reusable pieces, promoting ease of updates and reducing the risk of errors in large ecosystems.
AWS's own adoption of platform engineering, which includes building reusable components, exemplifies this efficiency, as seen in their 150 million deployments per year.
Versioning is another pillar of robust CloudFormation templates, allowing you to maintain a history of changes and revert to previous states if necessary. This approach mirrors the advantages outlined by experts who recommend preserving previous state versions in infrastructure as code (IaC) applications.
Parameterization confers flexibility, letting you customize deployments without altering the underlying code, thereby streamlining the process of managing different environments or requirements. As advocated by platform engineering practices, parameterization can reduce complexity and accelerate project startups, enhancing the deployment process.
Lastly, comprehensive error handling ensures resilience and stability. By anticipating and coding for potential failures, your templates become more dependable. For example, clear error messages can guide quick resolution, akin to the streamlined troubleshooting in a well-architected flat file handling system.
By integrating these best practices into your CloudFormation workflow, the benefits become clear: templates transform into resilient, adaptable, and efficient blueprints that support your infrastructure's evolution amidst the dynamic cloud computing landscape.
Common Use Cases and Examples
Amazon Web Services (AWS) CloudFormation is an essential service that facilitates infrastructure as code (IAC), enabling the creation, management, and deployment of a wide array of AWS resources through the use of templates. These templates act as blueprints for entire environments, detailing the necessary resources and configurations. This method offers several advantages, particularly for intricate deployments such as microservices architectures or complex applications.
For instance, Dunelm, the UK's top homewares retailer, leveraged AWS CloudFormation to transition their e-commerce platform to a serverless microservices architecture. This shift aimed to enhance their business agility and reduce the total cost of ownership. Despite the benefits, challenges arose, particularly with their monolithic frontend, which necessitated comprehensive testing and deployment for any alterations, thus amplifying risk and complexity.
Similarly, Vertex Pharmaceuticals tapped into the power of AWS CloudFormation to bolster their drug discovery efforts. By employing machine learning for image segmentation, they could analyze vast datasets more swiftly and precisely. This underscores the versatility of AWS CloudFormation in facilitating complex analytical tasks requiring robust computational infrastructure.
In the realm of nonprofit organizations, CloudFormation has proven invaluable as well. For example, an organization dedicated to combating child sexual abuse employs machine learning tools to sift through millions of digital files rapidly. The efficiency gains from such technological capabilities are substantial, with artificial intelligence greatly expediting the detection process.
AWS CloudFormation and tools like AWS Amplify and AWS Application Composer constantly evolve, gaining new features that cater to diverse needs. As these tools expand, staying abreast of the latest developments is crucial to ensure that the most suitable service is selected to meet specific requirements and regulatory compliance for production environments.
When comparing AWS CloudFormation with other IaC tools like Terraform, it becomes clear that each has its strengths. Terraform is applauded for its flexibility and support across multiple cloud providers, offering a consistent syntax and deployment approach, which is advantageous for organizations leveraging multi-cloud strategies.
In summary, CloudFormation provides a predictable and repeatable way to orchestrate and manage AWS infrastructure, proving to be an indispensable asset in various scenarios—from retail and pharmaceuticals to nonprofit initiatives—highlighting the importance of strategic infrastructure management in achieving organizational goals.
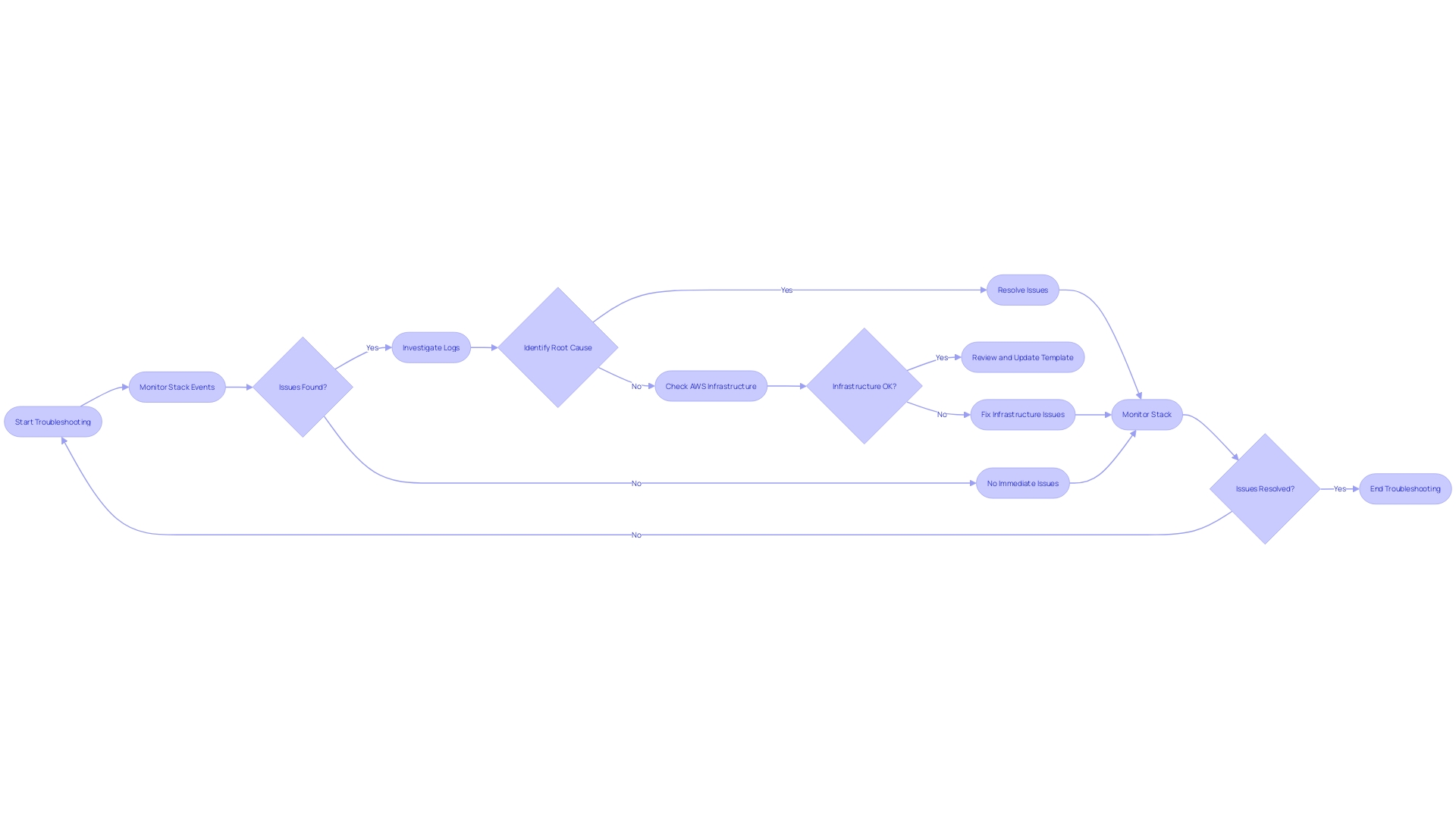
Troubleshooting and Debugging
Troubleshooting and debugging CloudFormation stacks can be a nuanced process, with potential pitfalls even for the most seasoned AWS users. One common challenge is misconfigured security group rules, leading to denied access to resources such as EC2 instances. This denial often traces back to the default "deny all" principle in AWS, requiring explicit permission through security group rules for any traffic.
To navigate these challenges, paying close attention to stack events is crucial. Events provide a chronological record, helping to pinpoint the exact moment and cause of failures. By analyzing these events, you can track down the root cause of many common issues.
Additionally, diving into CloudFormation logs can reveal insights into stack operations, offering a detailed view of the actions performed and the outcomes. These logs are instrumental when dissecting the behavior of your CloudFormation templates during execution.
AWS CloudTrail also plays a key role in troubleshooting. It logs every action taken on your AWS account, giving you a thorough audit trail of changes and access to resources. By examining CloudTrail logs, you can uncover the sequence of events that led to an issue, making it easier to diagnose and rectify.
Moreover, serverless computing models like AWS Lambda may introduce new complexities in troubleshooting. Despite the convenience of not managing servers, understanding the nuances of serverless architecture is essential for identifying and resolving issues specific to such environments.
When dealing with service outages or disruptions, remember that AWS's global infrastructure is designed to provide high availability and resilience. Despite this, some degree of failure is always possible, as even with a 99.99% availability rate, a fraction of servers may experience issues at any given moment. Therefore, designing for failure by expecting the unexpected is a mindset ingrained in the architecture of resilient services like Amazon ECS.
In summary, a combination of vigilant monitoring of stack events, thorough investigation of CloudFormation and CloudTrail logs, and a deep understanding of AWS infrastructure's availability and resilience are the cornerstones of effective CloudFormation troubleshooting.
Conclusion
CloudFormation is a powerful service offered by AWS for infrastructure management and deployment in the cloud computing landscape. It provides automation of complex environment deployments, ensuring consistency and scalability. By utilizing CloudFormation templates, organizations can articulate their infrastructure requirements and orchestrate resources effectively.
Setting up the environment for CloudFormation involves understanding templates, initializing IAM roles, and leveraging infrastructure automation. CloudFormation templates serve as blueprints for infrastructure, enabling reliable and error-free deployments.
Testing and validating CloudFormation templates are crucial for ensuring reliable deployments. CloudFormation's validation features help identify errors, while considering the broader context of cloud infrastructure ensures compliance and operational requirements are met.
The CloudFormation Linter, or cfn-lint, is an indispensable tool for ensuring error-free and compliant templates. By integrating cfn-lint into the development workflow, developers can automate tests and linting, promoting quality and maintainability.
Deploying CloudFormation stacks involves defining IAM roles, understanding template capabilities, and considering rollback strategies. CloudFormation supports various deployment options and ensures minimal disruption during migrations.
Managing multiple stacks requires effective orchestration and streamlining stack operations. Tools like AWS Amplify and AWS Application Composer assist in crafting and administering cloud applications tailored to specific needs.
Best practices for template development enhance the reliability, scalability, and manageability of CloudFormation templates. Modularization, versioning, parameterization, and error handling are key pillars of robust templates.
CloudFormation finds application in various use cases, from retail and pharmaceutical industries to nonprofit initiatives. Staying informed about the latest developments in CloudFormation ensures selecting the most suitable services for specific requirements.
Troubleshooting and debugging CloudFormation stacks require attention to stack events, analysis of logs, and utilization of AWS CloudTrail. Understanding AWS infrastructure's availability and resilience is crucial for effective troubleshooting.
In conclusion, CloudFormation simplifies infrastructure management and deployment in the cloud computing arena. By following best practices, leveraging automation, and staying informed about new developments, organizations can achieve efficient and reliable infrastructure management.




