Introduction
As organizations increasingly adopt cloud technologies, ensuring a secure transition becomes paramount. This article delves into the critical pre-migration security considerations that enterprises must address to safeguard their digital assets. It explores the importance of conducting comprehensive risk assessments, mapping out dependencies, and choosing an appropriate migration strategy aligned with security protocols.
The article further outlines best practices for maintaining security during the migration process, emphasizing robust Identity and Access Management (IAM), data encryption, and network security measures. Additionally, it highlights the necessity of continuous security monitoring, post-migration validation, and adherence to sector-specific regulations to maintain compliance and mitigate risks. By following these guidelines, organizations can achieve a secure and seamless migration to the cloud, ensuring the integrity and confidentiality of their data.
Pre-Migration Security Considerations
Prior to starting a data migration, organizations must carefully assess their protection stance. This involves conducting a comprehensive risk assessment to identify potential vulnerabilities within cloud environments. Essential elements encompass grasping data sensitivity, compliance obligations, and existing protective measures. The GDPR, for example, mandates strict protocols like data residency and minimization to safeguard privacy. Furthermore, businesses ought to create a transition plan that includes protection from the beginning. As pointed out by Rob Joyce, NSA’s Director of Cybersecurity, proper implementation of online services is essential to avoid becoming an appealing target for adversaries. By following optimal methods and utilizing safe online identity and access management, entities can guarantee a strong protective framework throughout the transfer process.
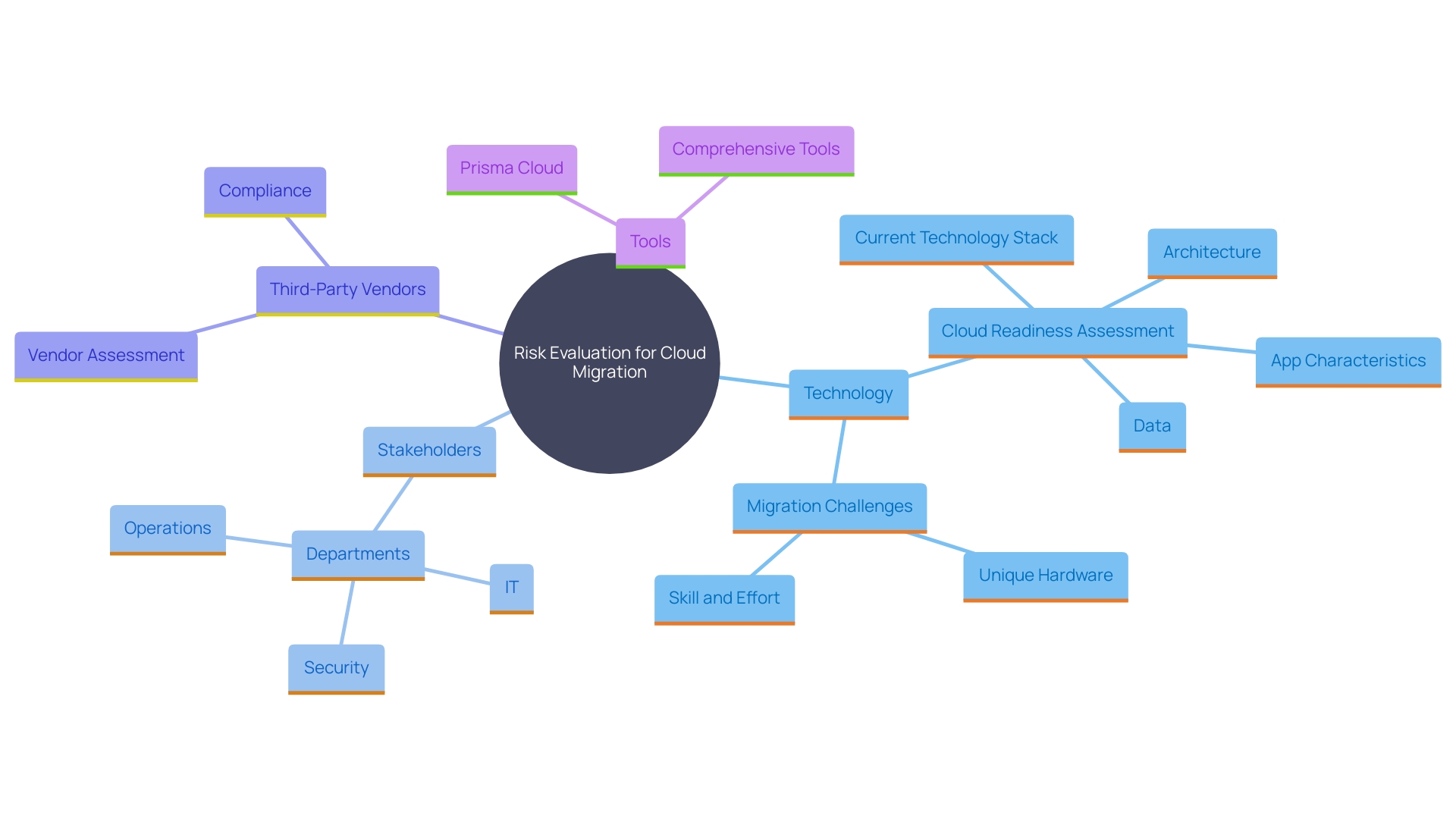
Conduct a Comprehensive Risk Assessment
Carrying out a thorough risk evaluation is essential for guaranteeing the safety of cloud migration. This involves not only identifying potential threats and vulnerabilities but also evaluating the likelihood of these risks affecting the entity. Engaging stakeholders from various departments provides a holistic view of potential concerns. It's important to also consider third-party vendors and their protective measures. According to Forrester Consulting, organizations leveraging comprehensive risk assessments, like those using Prisma Cloud, have found them invaluable for managing complex cloud environments. As one senior protection architect noted, “There was no way we could manage 100 accounts without a tool like Prisma Cloud.” This highlights the necessity of having a unified platform to handle diverse protection needs. Additionally, the AI Risk Repository's approach to categorizing risks based on causes and domains emphasizes the complexity and variety of potential security threats. Gartner research further supports that by 2025, 85% of companies will adopt a cloud-first strategy, underscoring the importance of meticulous risk assessment in facilitating secure cloud transition.
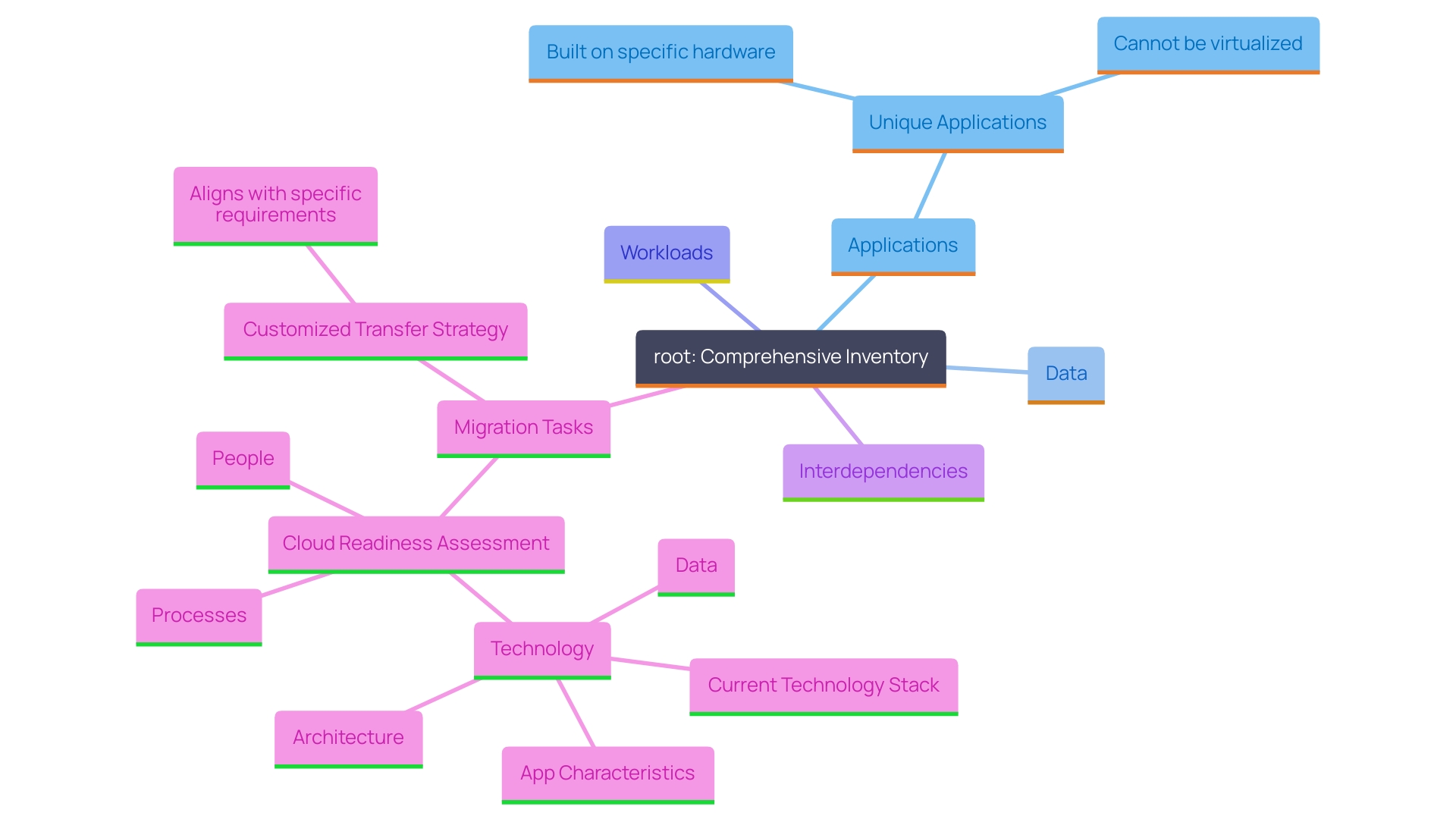
Inventory and Dependency Mapping
Carrying out a comprehensive inventory of all applications, data, and workloads planned for transfer is a fundamental step. This comprehensive assessment should also map out the dependencies to understand the interconnections between various services. Visualizing these relationships allows entities to prioritize migration tasks effectively and mitigate any security implications arising from these dependencies. For instance, applications built on unique hardware not represented in remote servers or those that can't be virtualized, such as certain IoT applications and cryptocurrency cold wallets, require special attention. By evaluating the current technology stack, application characteristics, architecture, and data, entities can ensure a seamless transition to the cloud. Every IT asset has unique cost, performance, and complexity traits, making it crucial to customize the transfer strategy to the specific requirements of the entity. This approach not only facilitates digital transformation but also accelerates growth and enhances business agility.
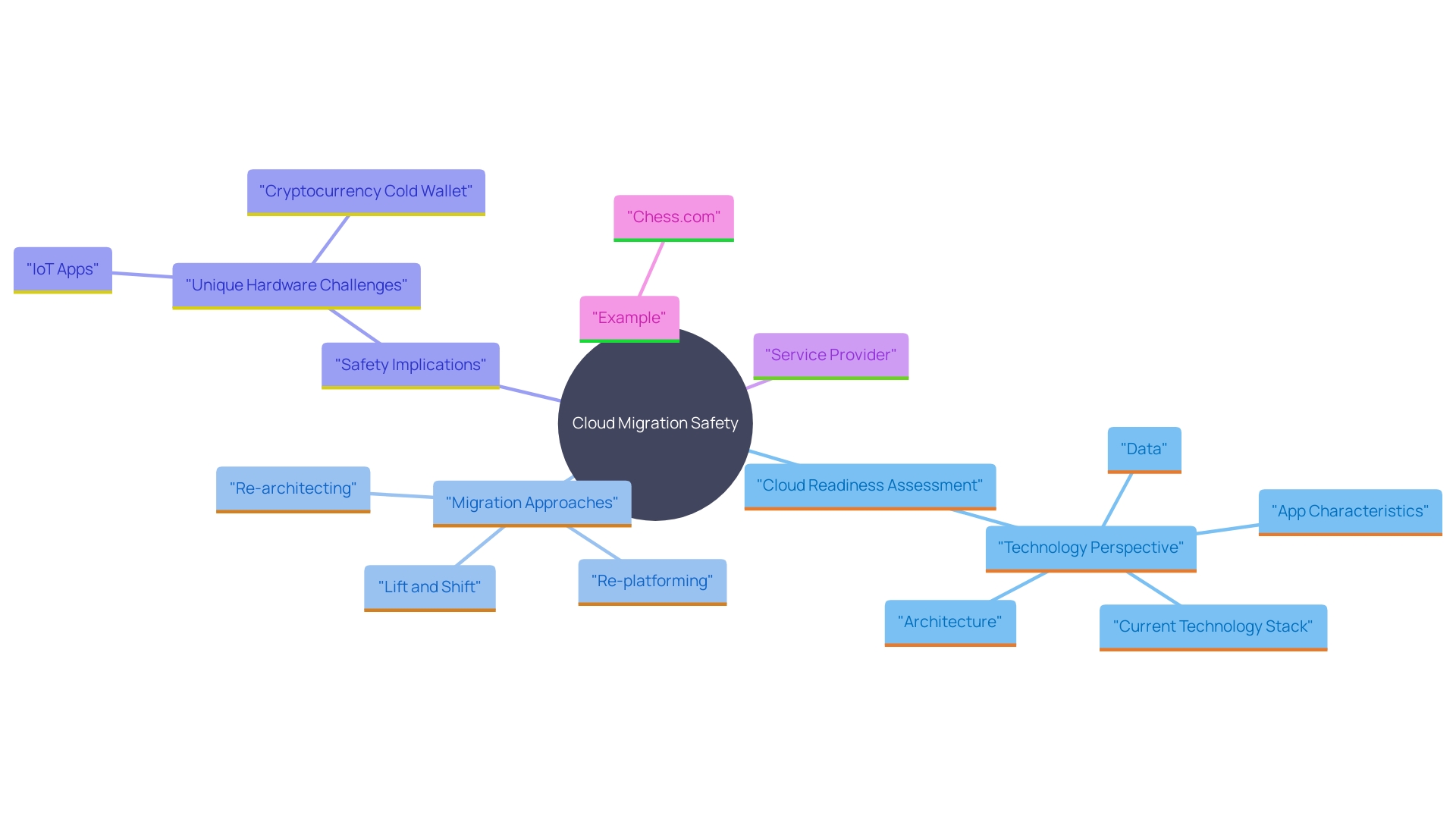
Choosing a Secure Migration Strategy
Selecting the suitable migration approach—whether it be 'lift and shift,' re-platforming, or re-architecting—can greatly influence an organization's defense stance. Each approach has distinct safety implications that must be carefully evaluated. For example, 'lift and shift' may provide a faster transition but might not enhance the protective features inherent to the cloud. 'Re-platforming and re-architecting, on the other hand, could provide improved protection configurations but require more time and resources.'.
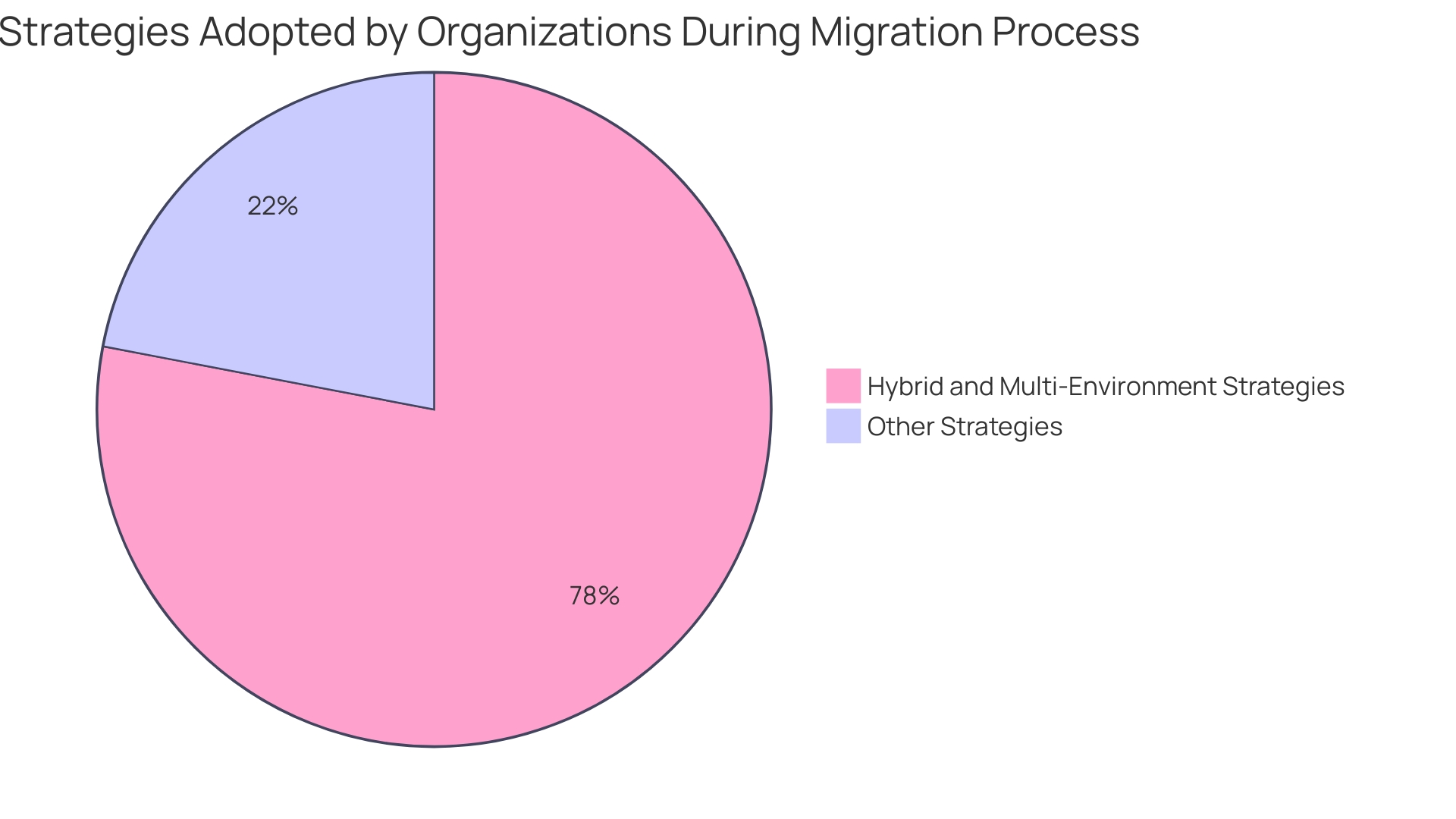
Organizations should start with a comprehensive Cloud Readiness Assessment to review their current technology stack, application characteristics, architecture, and data. This assessment will help identify specific needs and potential gaps in protection that must be addressed during migration. As per a study of 927 cybersecurity experts, 78% of entities are currently choosing hybrid and multi-cloud approaches, highlighting the essential need to balance protection with operational needs.
Moreover, choosing a service provider with a demonstrated history in protection is essential. Providers should offer strong protection measures and a range of services that align with the organization's goals. As emphasized by Corey Quinn in a discussion, the connection between protection and expense is closely intertwined in online infrastructures, where effective design can lessen risks and lower expenses.
Real-world examples underscore the importance of a well-rounded approach. Chess.com, with its extensive user community and intricate framework, has effectively combined public internet and on-site solutions to guarantee both scalability and protection. Their experience illustrates the importance of careful planning and the appropriate technology selections in accomplishing a secure transfer to the online environment.
In conclusion, aligning the transition approach with the organization’s protection policies and selecting the appropriate cloud service provider are key steps in ensuring a safe and successful shift to the cloud.
Security Best Practices During Migration
During the migration process, applying best practices for protection is essential to safeguarding organizational assets. This requires a robust approach to Identity and Access Management (IAM), ensuring data security through encryption, and establishing comprehensive network security measures. Based on a study of 927 cybersecurity experts, most entities (78%) are choosing hybrid and multi-environment strategies, emphasizing the significance of secure practices in these settings. 'Anthony James, VP of Product Marketing at Infoblox, stresses the importance of secure remote identity and access management practices, urging companies to comprehend their service provider’s documentation and best practices.'.
Additionally, continuous monitoring is essential to detect and respond to any anomalies swiftly. OODA's group of global specialists offers sophisticated intelligence and analysis to aid in risk and threat management, highlighting the importance of proactive actions in online protection. The collaborative accountability framework in online services requires that entities not only depend on their suppliers but also maintain their share of protective duties, as mentioned in the guidance widely relevant to different industries. By adhering to these optimal approaches, organizations can guarantee a safe and robust transition to the online environment.
Identity and Access Management (IAM)
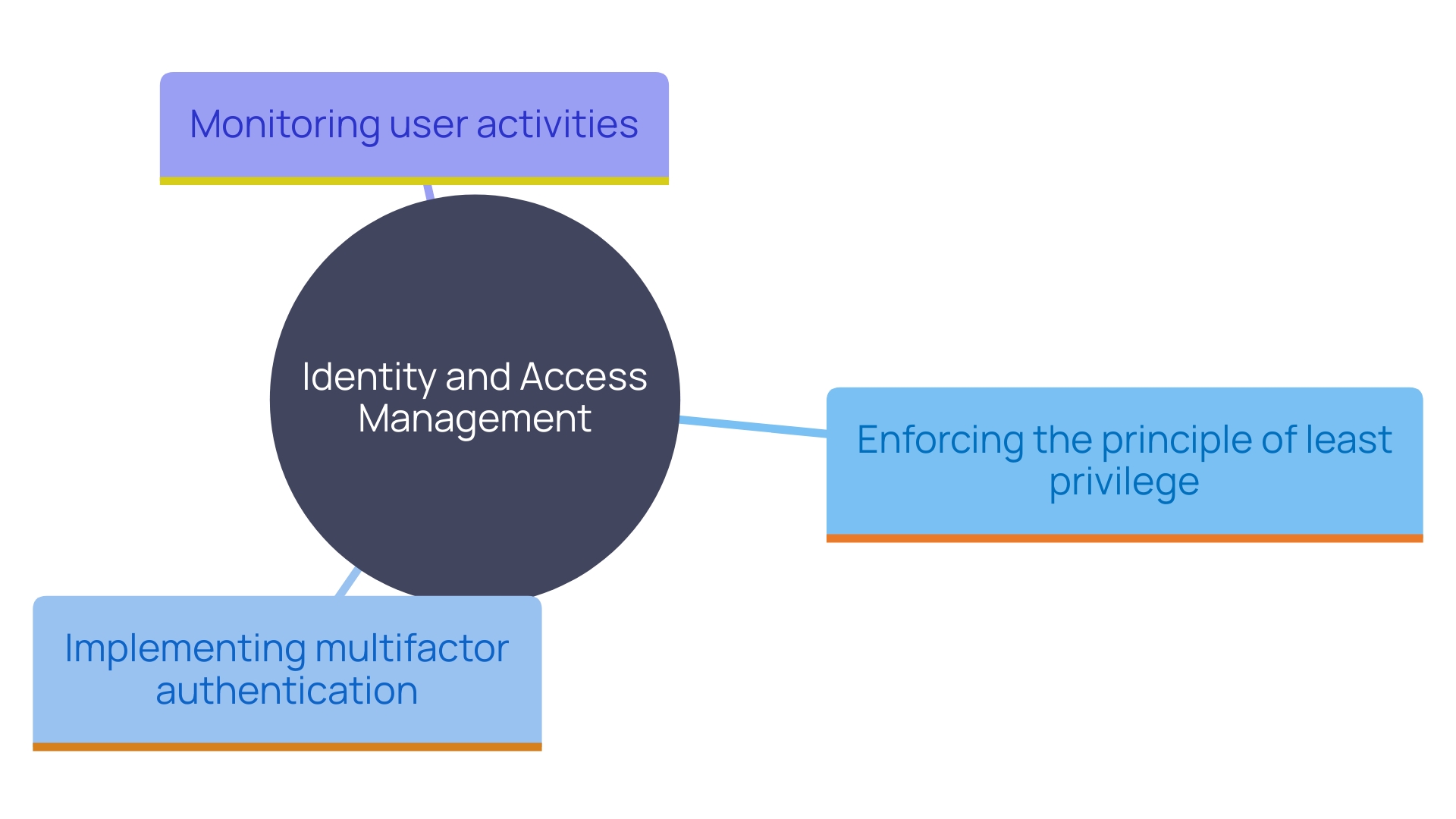
'Identity and Access Management (IAM) solutions are essential for managing access to online resources, ensuring that protection and compliance are maintained during migration.'. Enforcing the principle of least privilege is essential; this means granting users only the permissions necessary for their specific roles. Such a strategy minimizes the risk of unauthorized access and potential breaches. Furthermore, implementing multifactor authentication (MFA) adds an extra layer of protection, significantly reducing vulnerabilities associated with traditional password-only systems. Protection specialists, like Jack Poller, stress the significance of a strong IAM approach in preserving the integrity and safety of digital infrastructures. Efficient IAM solutions not only defend against unauthorized access but also assist in observing and controlling user activities, offering a thorough approach to online safety.
Data Security
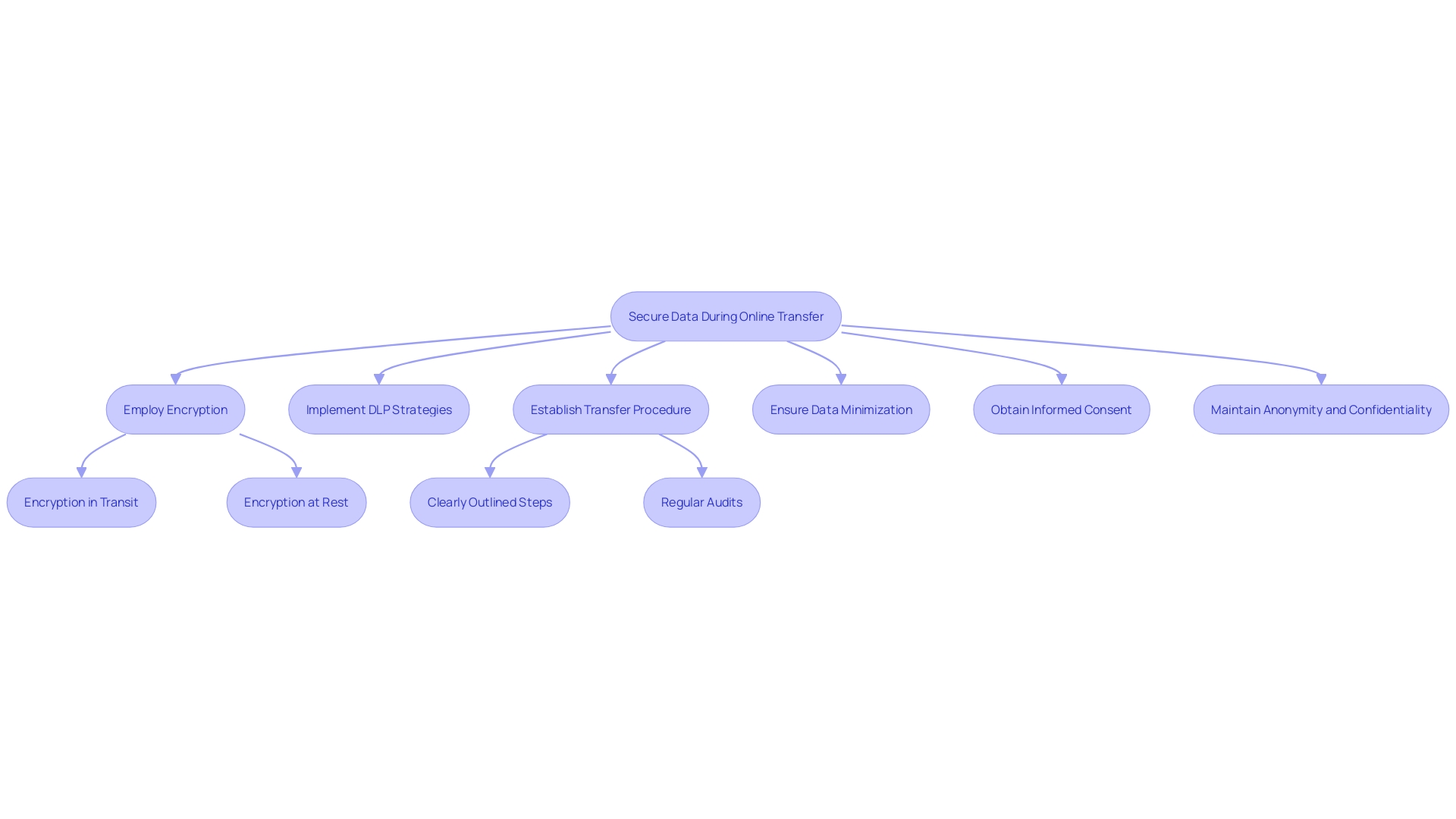
Guaranteeing information protection during online transfer is essential. Encryption should be employed both in transit and at rest to protect sensitive information from unauthorized access. This dual approach ensures that data remains secure as it moves between locations and while stored in the cloud. Additionally, implementing Data Loss Prevention (DLP) strategies is crucial for monitoring and preventing potential data breaches. 'According to a survey of over 700 data leaders, maintaining consistent data protection is challenging due to siloed protection controls and the rise of generative AI technologies.'. This emphasizes the significance of strong security protocols during data transfer. As one expert pointed out, 'Data is essential in business… and it is where it often falters,' highlighting the necessity for a clearly outlined transfer procedure to prevent typical mistakes and guarantee dependability. By incorporating these best practices, organizations can safeguard their data during the transfer process and beyond.
Network Security
Establishing secure network configurations is paramount during cloud migration. Organizations should utilize advanced protective measures such as firewalls, VPNs, and intrusion detection systems to safeguard data in transit. Based on an extensive study of 927 cybersecurity experts, most organizations (78%) are choosing hybrid and multi-cloud strategies, which requires strong protection frameworks. Network segmentation is a crucial tactic that can further improve protection by limiting access to sensitive areas, ensuring that unauthorized users are kept at bay.
Bob Hansmann, a seasoned expert in cyberthreat prevention, highlights the growing complexity of networks and the crucial need for dynamic IP address management (IPAM). This makes it imperative to adopt flexible, cloud-delivered protection solutions that can adapt to the evolving network landscape. As Jeetu Patel, Executive Vice President at Cisco, asserts, “The power of Cisco Hypershield is that it can put security anywhere you need it – in software, in a server, or in the future even in a network switch.”
This multi-layered security approach is crucial as organizations embrace decentralized, hybrid work environments, requiring scalable and agile solutions to protect their expanding digital footprint. The swift embrace of cloud-native protection frameworks, such as Cisco Hypershield, exemplifies the industry's transition towards more independent and cost-effective enforcement mechanisms.
Continuous Security Monitoring
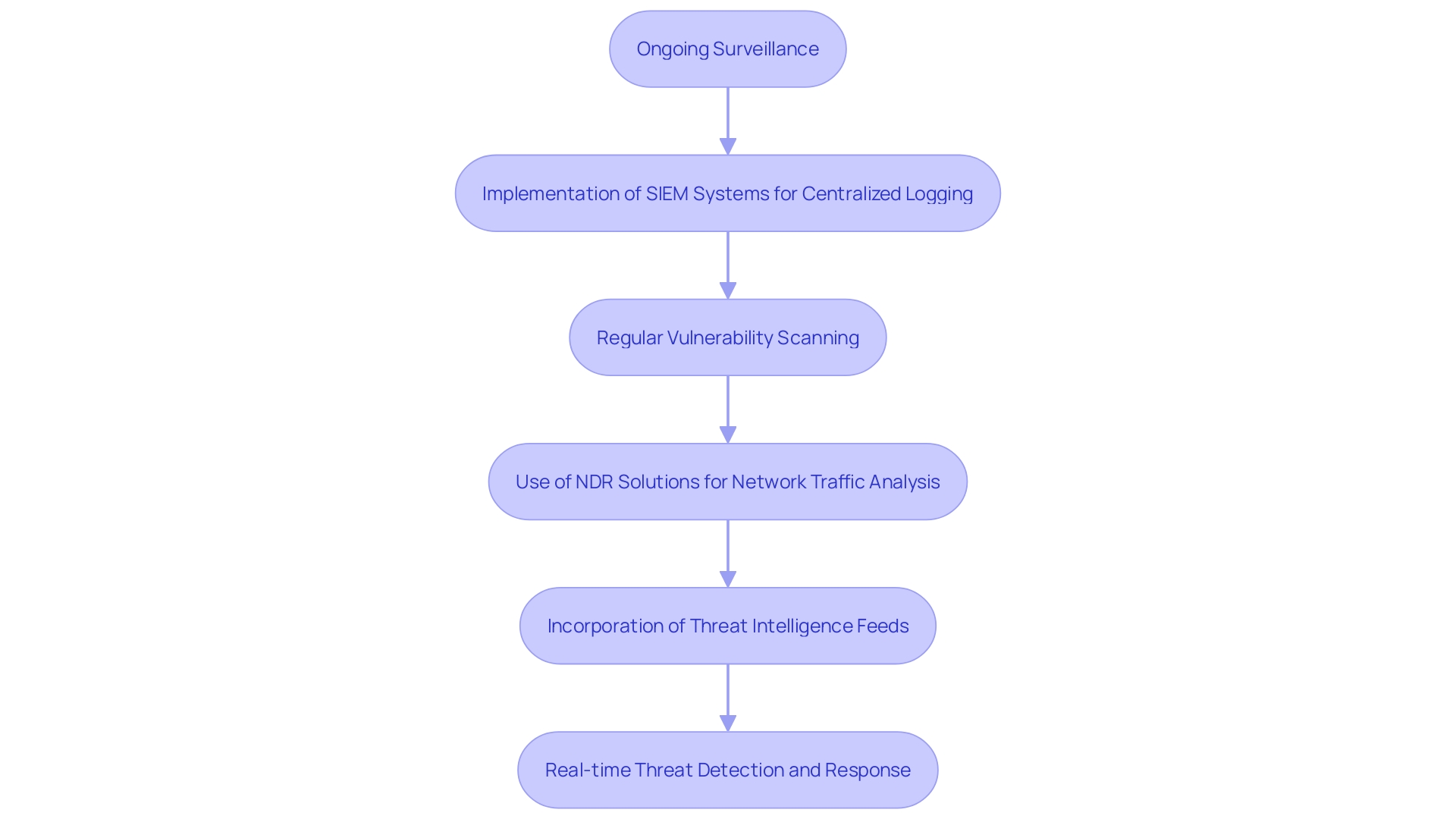
Ongoing surveillance is essential for real-time threat identification and alleviation. Implementing Security Information and Event Management (SIEM) systems enables centralized logging and analysis, making it easier to track and respond to potential threats efficiently. Regular vulnerability scanning and proactive threat detection are essential components of this strategy. Network Detection and Response (NDR) solutions can enhance this approach by analyzing network traffic patterns to detect anomalies indicative of threats. By leveraging contextual information about network activity and prioritizing alerts based on their severity, entities can better assess and respond to potential threats. Utilizing threat intelligence feeds can further enhance risk assessment, providing deeper insights into emerging threats and their potential impact.
Post-Migration Validation and Compliance
Following migration, entities must confirm the effective execution of protective measures, ensuring adherence to sector-specific regulations and performing comprehensive audits to pinpoint areas requiring enhancement. The banking industry, for instance, faces stringent regulatory requirements to protect sensitive data and transactions. M&T Bank's method emphasizes the significance of setting strong criteria to ensure software quality and adherence, thereby preventing the dangers of breaches and financial losses. The rise in compliance and privacy regulations, as seen with the GDPR, necessitates organizations to adhere to protocols such as data residency, minimization, and storage limitation. Furthermore, utilizing Infrastructure-as-Code can improve cloud resource protection, making it vital to promote safe practices among vendors and partners.
Ensure Compliance with Sector-Specific Regulations
Organizations must ensure continuous compliance monitoring with relevant regulations and standards after migration. This involves conducting regular assessments and updating protection practices to keep pace with evolving compliance requirements. As regulatory landscapes rapidly change, the nuances of each new legislation present fresh challenges, making it crucial to stay vigilant. For instance, TBC Bank, Georgia's leading financial institution, has significantly improved its digital product time-to-market by adhering to stringent regulatory requirements. Similarly, M&T Bank in the U.S. has adopted comprehensive Clean Code standards to maintain software quality and compliance, safeguarding against security breaches and financial losses. The GDPR protocols, including data residency, minimization, and storage limitations, further exemplify the rigorous standards entities must meet to protect sensitive data. As highlighted by James Tarala from the SANS Institute, understanding new risk assessment requirements from regulatory bodies like the SEC and NYDFS is vital. These efforts ensure that organizations not only meet compliance standards but also enhance their cybersecurity posture, mitigating risks associated with digital transformations.
Continuous Monitoring and Optimization
Continuous observation and enhancement are crucial for upholding strong cloud protection. Organizations must regularly review and update protection configurations to address emerging threats and vulnerabilities. For instance, a notable incident involved a suspicious support case within an AWS account, which triggered an alert due to an unauthorized request to increase Simple Email Service (SES) sending limits. This example highlights the critical need for continuous vigilance, as SES can be exploited for phishing and spam campaigns.
'Adopting a 'Secure by Design' approach further improves protection by integrating it into the development lifecycle from the outset. This method balances agility, cost optimization, and protection goals, ensuring the cloud environment remains safe and efficient over time. Based on a poll of 927 cybersecurity experts, 78% of organizations are currently choosing hybrid and multi-cloud approaches, emphasizing the significance of stringent protective measures across various infrastructures.
In the evolving landscape, implementing effective monitoring relies heavily on the expertise of service managers who understand system architecture and dependencies. As Paul Vixie, Ph.D., Deputy CISO at AWS, emphasizes, embracing security as a core business requirement is key to mitigating vulnerabilities and achieving technological objectives. Ensuring that cloud environments are both secure and efficient requires a proactive stance and continuous improvement.
Conclusion
The transition to cloud technologies mandates a strong emphasis on security to protect digital assets and maintain compliance. A comprehensive risk assessment is vital for identifying vulnerabilities and understanding data sensitivity, which informs the overall migration strategy while involving stakeholders across the organization.
Mapping application dependencies and inventorying workloads are essential steps that help prioritize migration tasks effectively. Each application's unique characteristics must be taken into account to tailor the migration approach, thereby enhancing business agility. The choice of migration strategy—whether 'lift and shift,' re-platforming, or re-architecting—has significant implications for security configurations.
During migration, implementing robust security best practices is crucial. This includes effective Identity and Access Management (IAM), data encryption, and comprehensive network security measures. Continuous monitoring is essential for real-time threat detection and response, highlighting the shared responsibility between organizations and cloud service providers.
After migration, validating security measures and ensuring compliance with sector-specific regulations is imperative. Ongoing monitoring and optimization allow organizations to adapt to emerging threats and regulatory changes. Adopting a 'Secure by Design' approach integrates security into the development lifecycle, balancing agility with robust practices.
Ultimately, a cohesive strategy that includes pre-migration assessments, diligent monitoring, and continuous optimization is key to achieving a secure cloud migration, safeguarding the integrity and confidentiality of organizational data.




