Introduction
In an era where digital communication forms the backbone of business operations, the significance of robust email security cannot be overstated. This article delves into the essential features that constitute effective email security solutions, offering a comprehensive analysis of advanced threat protection, spam filtering, and data loss prevention capabilities. It also provides an overview of leading email security solutions, comparing their strengths and unique features to guide organizations in making informed decisions.
Additionally, the article explores the advanced functionalities and capabilities that modern solutions leverage to counter sophisticated threats such as Business Email Compromise (BEC). Finally, it addresses crucial pricing and scalability considerations, ensuring that businesses of all sizes can find the right balance between cost and security to protect their digital communications effectively.
Key Features of Effective Email Security Solutions
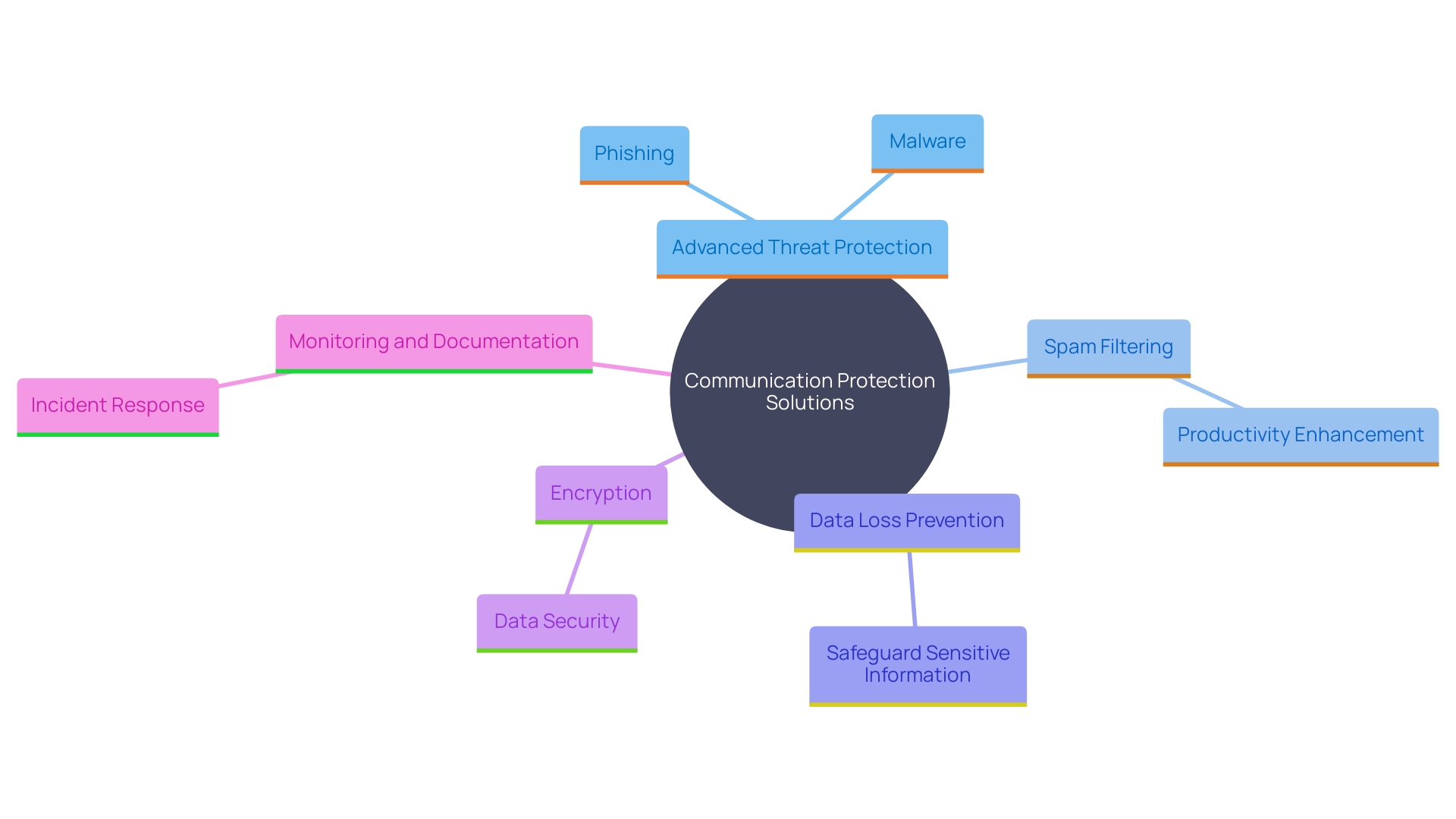
All-encompassing communication protection solutions must include various levels of defense to tackle the intricacy of contemporary dangers. Advanced threat protection, for instance, is critical for identifying and neutralizing phishing attacks and malware before they can infiltrate an inbox. This is especially crucial as recent studies show that over 3.6% of messages, amounting to more than 585 million, were marked as harmful.
Effective spam filtering is another vital element, intended to decrease the amount of unwanted messages that can congest inboxes and deplete resources. As Tony Pepper, CEO of Egress, points out, graymail detection can significantly enhance productivity by freeing up time for IT and cybersecurity teams.
Data loss prevention (DLP) capabilities are indispensable for ensuring that sensitive information is not accidentally leaked. Encryption options offer an extra layer of protection, safeguarding data as it moves across different networks.
Instantaneous observation and documentation features are crucial by providing understanding of communication-related incidents. This enables organizations to react promptly to potential breaches. For instance, a Canadian branch of an international law firm opted to handle its cybersecurity at the regional level, emphasizing the significance of customized protective measures to safeguard client information and adhere to privacy regulations.
By incorporating these attributes, messaging protection systems not only defend against present dangers but also provide a flexible structure for continuous oversight and adjustment, thus improving the general view of data privacy measures.
Overview of Top Email Security Solutions
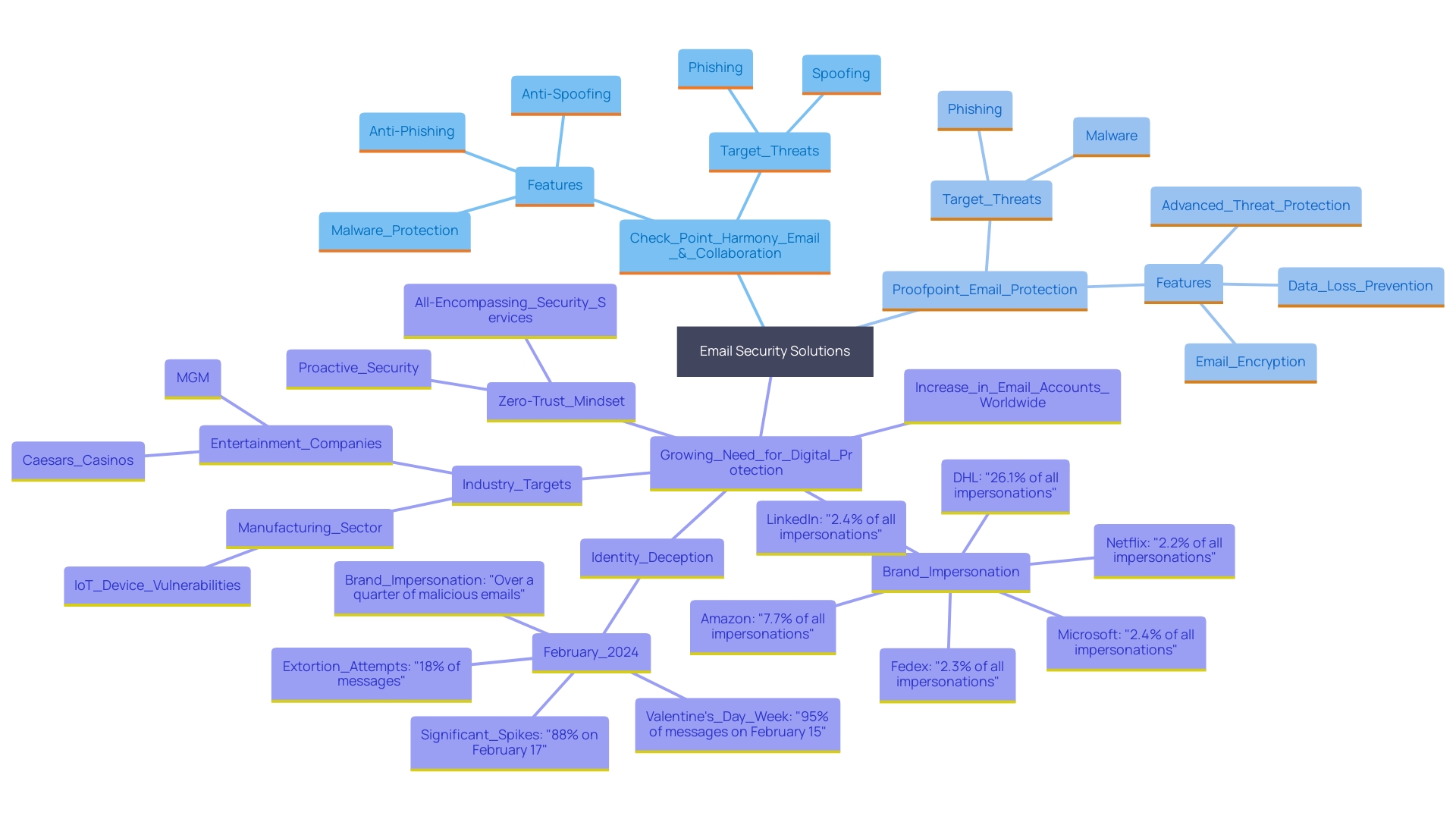
In the realm of email security, a variety of options are available, each bringing unique features to address the multifaceted needs of businesses. Prominent offerings consist of Check Point Harmony Email & Collaboration, Proofpoint Email Protection, Mimecast Email Security, Microsoft Defender for Office 365, and Barracuda Email Security Gateway. 'These tools are pivotal in fortifying defenses against increasingly sophisticated dangers, such as those from Muddy Water, which now utilize custom backdoors like BugSleep and simpler lures targeting diverse sectors.'.
Each option offers distinct approaches to threat detection, user experience, and integration capabilities. For instance, Barracuda Email Security Gateway is celebrated for its adaptability and comprehensive support, making it a preferred choice for many organizations. Hornetsecurity's research underscores the importance of these solutions, revealing that brands like LinkedIn, Microsoft, and Netflix frequently face spoofing attempts, with DHL, Amazon, and FedEx also being major targets. This emphasizes the essential requirement for strong electronic communication protection to guard against wide-ranging phishing and malware assaults.
The Radicati Group's study further emphasizes the prevalence of electronic mail, with nearly 3.8 billion accounts worldwide as of early 2019, projected to reach 4.2 billion by 2022. This growth highlights the increasing demand for sophisticated digital protection measures to safeguard online communications. Organizations must thoroughly assess their protection needs and infrastructure to choose the most appropriate option, ensuring they can efficiently identify, react to, and recuperate from email-related risks.
Comparing Email Security Solutions
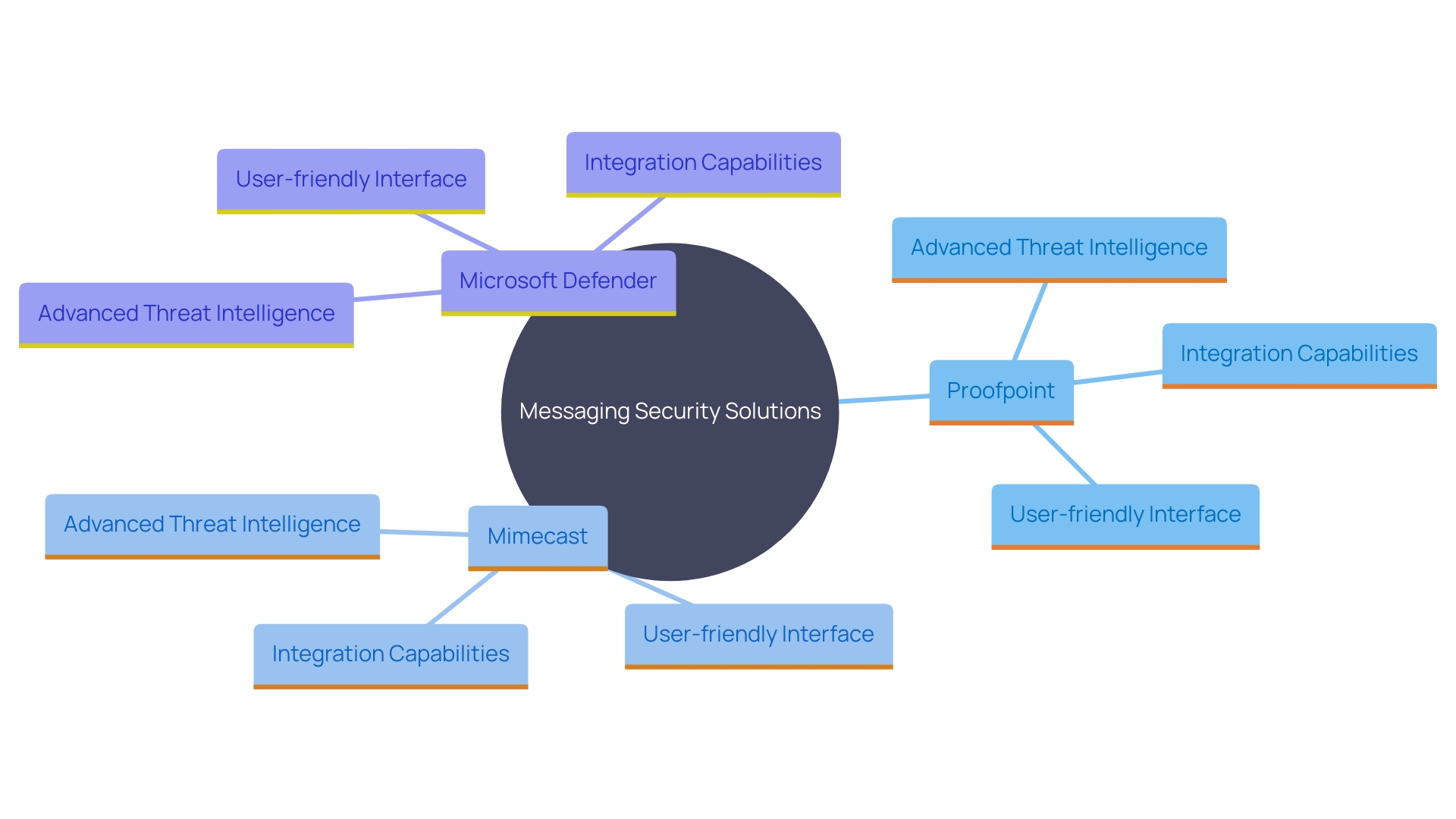
When assessing messaging security options, it is essential to analyze their efficacy in addressing advanced risks, the simplicity of implementation, and the thoroughness of their functionalities. Solutions like Proofpoint are celebrated for their advanced threat intelligence capabilities, leveraging behavioral-based approaches to safeguard against email risks and data loss. Mimecast, in contrast, distinguishes itself with its user-friendly interfaces and comprehensive archiving options, making it a favored selection for businesses prioritizing ease of use and data management. Microsoft Defender seamlessly integrates with other Microsoft services, providing an enhanced user experience for organizations already within the Microsoft ecosystem.
Grasping the particular strengths and weaknesses of each option enables organizations to make informed choices tailored to their unique security needs. For example, AI and machine learning-enabled solutions effectively combat advanced communication risks like spear-phishing and business correspondence compromise. This is becoming more significant as malicious individuals exploit new technologies to create more convincing and targeted attacks. Utilizing AI in message protection guarantees that companies stay strong against the changing risk environment, ultimately safeguarding their communications and data integrity.
Advanced Features and Capabilities
Sophisticated functions are essential in improving electronic communication protection, especially amid the rise of Business Email Compromise (BEC) risks. Solutions like Barracuda Email Security Gateway offer robust impersonation protection, significantly mitigating the risk of BEC. BEC, where attackers gain access to a business email account and spoof the owner’s identity to defraud the company or its partners, has become a prevalent and costly risk. The nature of BEC attacks, which often involve spoofing, phishing, and malware, requires advanced protective measures.
Check Point Harmony illustrates this by merging with current protection frameworks to establish a thorough defense against cyber risks. The integration approach enhances the ability to detect, investigate, and respond to dangers efficiently, reducing the risk of breaches and minimizing the impact of security incidents.
The use of machine learning and artificial intelligence across these platforms further elevates their capabilities. These technologies improve detection rates and automate reactions to possible dangers, making it easier for organizations to maintain a proactive stance. As Tony Pepper, CEO of Egress, highlights, advanced graymail detection can significantly boost productivity and free up valuable time for IT and cybersecurity teams.
It is essential for organizations to prioritize options that utilize these advanced capabilities to stay ahead of developing cyber risks. 'With the ongoing development of risks, technologies such as those from Barracuda and Check Point are essential in protecting communication and ensuring strong defense strategies.'.
Pricing and Scalability Considerations
The pricing structures for email protection services can differ significantly, ranging from subscription-based fees to tiered plans determined by feature sets. Organizations must weigh both initial costs and long-term scalability. For small businesses, some solutions offer competitive pricing but may lack the scalability needed for larger enterprises. Conversely, advanced features at elevated price levels can greatly improve protection and functionality. Dr. Olga Livingston, Senior Economist, and Bob Lord, Senior Technical Advisor at CISA, emphasize that essential security features should be part of the basic service offering, without hidden surcharges. This makes it crucial to balance cost against the value provided, particularly as 65% of successful intrusions in 2023 began with exploits like phishing or stolen credentials. In today's rapidly evolving threat landscape, a robust incident response plan is indispensable. Businesses must ensure they are prepared to detect, respond to, and recover from email-based attacks efficiently.
Conclusion
In summary, the importance of robust email security in today’s digital landscape cannot be overstated. Comprehensive solutions that incorporate advanced threat protection, spam filtering, and data loss prevention are essential for safeguarding organizations against increasingly sophisticated threats. With a staggering percentage of emails flagged as malicious, the need for effective defenses has never been more critical.
The evaluation of leading email security solutions reveals a diverse range of features tailored to meet the unique needs of businesses. From Check Point Harmony to Microsoft Defender, each solution offers distinct advantages in threat detection and user experience. Understanding these differences allows organizations to make informed decisions that align with their specific security requirements.
Moreover, advanced features such as machine learning and artificial intelligence play a pivotal role in enhancing email security capabilities. These technologies not only improve detection rates but also streamline responses to potential threats, ensuring that organizations remain resilient in the face of evolving cyber threats.
Finally, pricing and scalability considerations are crucial for organizations of all sizes. Balancing cost with the value of security features is essential, particularly as the landscape of threats continues to grow. A proactive approach, underpinned by a robust incident response plan, is vital to effectively counter email-based attacks and protect sensitive communications.




