Introduction
In an increasingly interconnected world, where cyber threats loom larger than ever, organizations must prioritize their cybersecurity measures to safeguard sensitive data and maintain compliance with industry standards.
Penetration testing, often referred to as ethical hacking, emerges as a critical strategy in this endeavor, enabling businesses to proactively identify vulnerabilities before malicious actors can exploit them.
This comprehensive approach not only evaluates the effectiveness of existing security controls but also delivers actionable insights for remediation, thereby fortifying an organization's defenses against an evolving threat landscape.
As the frequency of cyber incidents escalates, understanding the nuances of penetration testing becomes essential for organizations striving to enhance their security posture and navigate the complexities of modern cybersecurity challenges.
Understanding Penetration Testing: A Comprehensive Overview
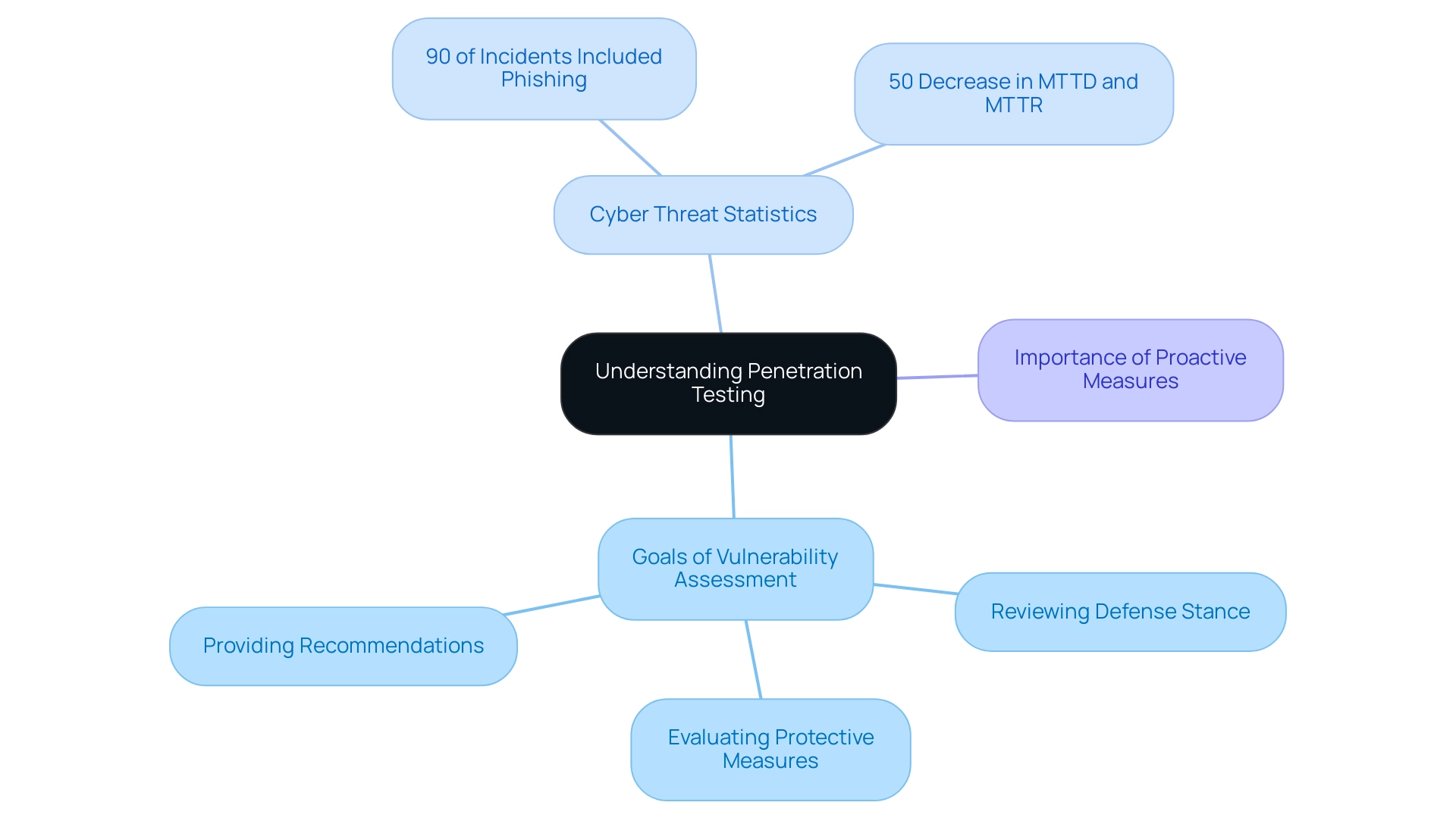
Penetration testing companies in Dubai perform penetration assessments, commonly referred to as ethical hacking, which involve simulating cyber attacks on a company's systems to reveal weaknesses before they can be exploited by harmful individuals. This proactive methodology is essential for protecting sensitive data and ensuring adherence to industry compliance standards. The main goals of vulnerability assessment include:
- Reviewing the defense stance of IT systems
- Evaluating the efficiency of current protective measures
- Providing practical recommendations for improvement
As companies encounter a growing occurrence of cyber threats—shown by the increase of phishing attacks, which, according to estimates, included a phishing component in 90% of incidents and breaches in 2019—grasping the basics of security assessments becomes crucial. Moreover, entities investing in Managed Detection and Response (MDR) services have experienced an impressive 50% decrease in both Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), highlighting the efficacy of proactive protective measures alongside vulnerability assessments. Furthermore, despite the acknowledgment of Zero Trust as a vital priority for protection, only 21% of IT professionals expressed confidence in their entity's understanding of the framework, highlighting the challenges entities face in navigating cybersecurity frameworks.
By recognizing the critical role that penetration testing companies in Dubai play, businesses can enhance their cybersecurity frameworks and significantly bolster their defenses against evolving threats.
Diverse Penetration Testing Services Offered by Dubai Companies
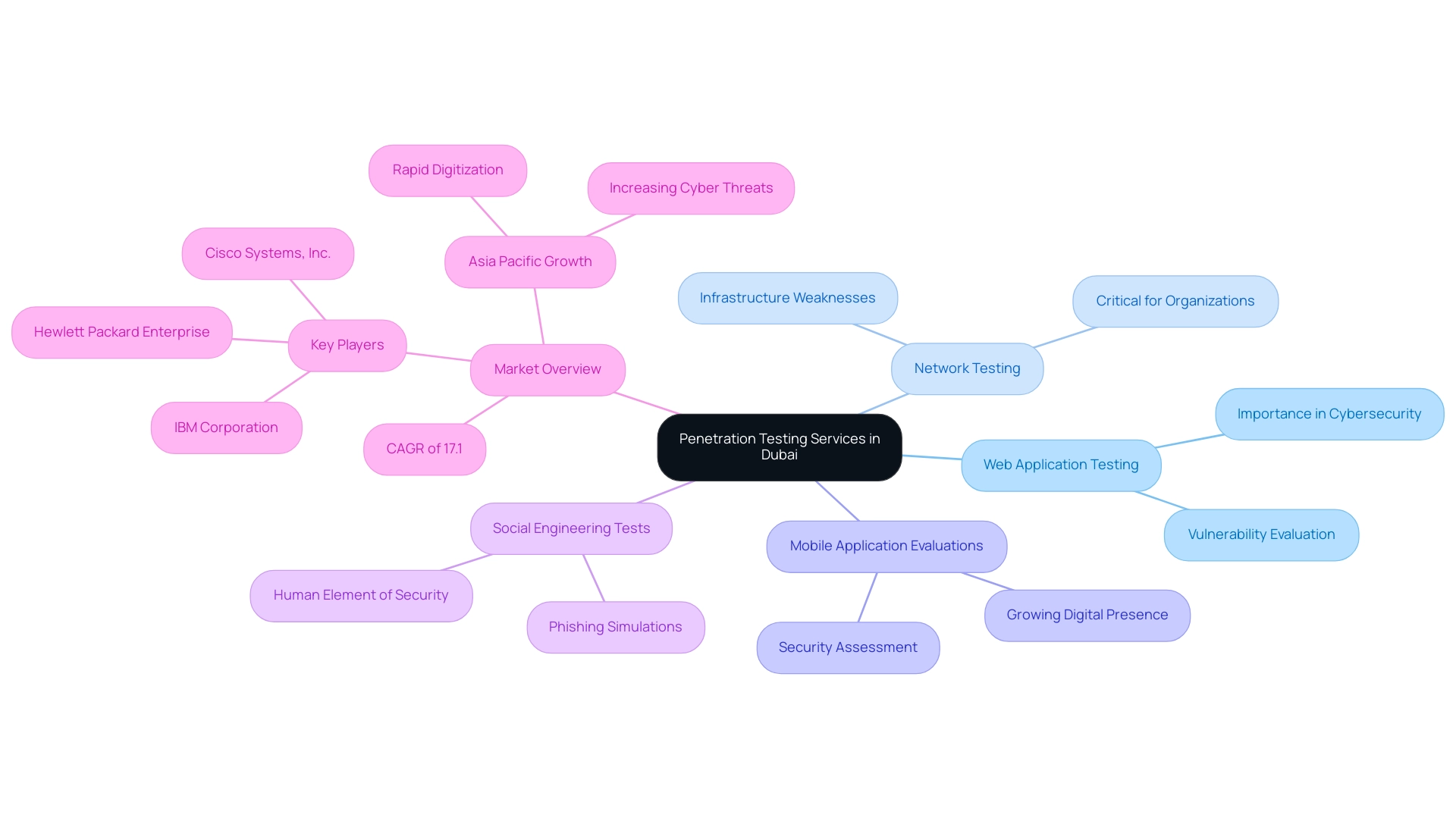
In Dubai, penetration testing companies in Dubai offer an extensive range of services designed to meet the varied protective requirements of businesses. Among the prominent offerings from penetration testing companies in Dubai are:
- Web application penetration testing, which meticulously evaluates online platforms for vulnerabilities.
- Network penetration testing, aimed at uncovering weaknesses within an organization's network infrastructure.
- Mobile application evaluations, which are becoming increasingly essential as companies grow their digital presence.
Some firms also specialize in social engineering tests, designed to scrutinize the human element of protection by simulating phishing attacks and other manipulation tactics. This diverse strategy for vulnerability assessment is crucial for entities looking to strengthen their defense stance in a changing digital environment, which can be effectively supported by penetration testing companies in Dubai. The market for these services is expected to grow at a compound annual growth rate (CAGR) of 17.1%, reflecting the increasing demand for robust cybersecurity measures.
Notably, leading players in the Penetration Testing Market include:
- IBM Corporation
- Hewlett Packard Enterprise Development LP
- Cisco Systems, Inc.
This underscores the competitive landscape. Furthermore, the Asia Pacific region is projected to experience significant growth due to rapid digitization and increasing cyber threats, which presents both challenges and opportunities for penetration testing companies in Dubai as they navigate the complexities of cybersecurity.
Choosing the Right Penetration Testing Company: Key Considerations
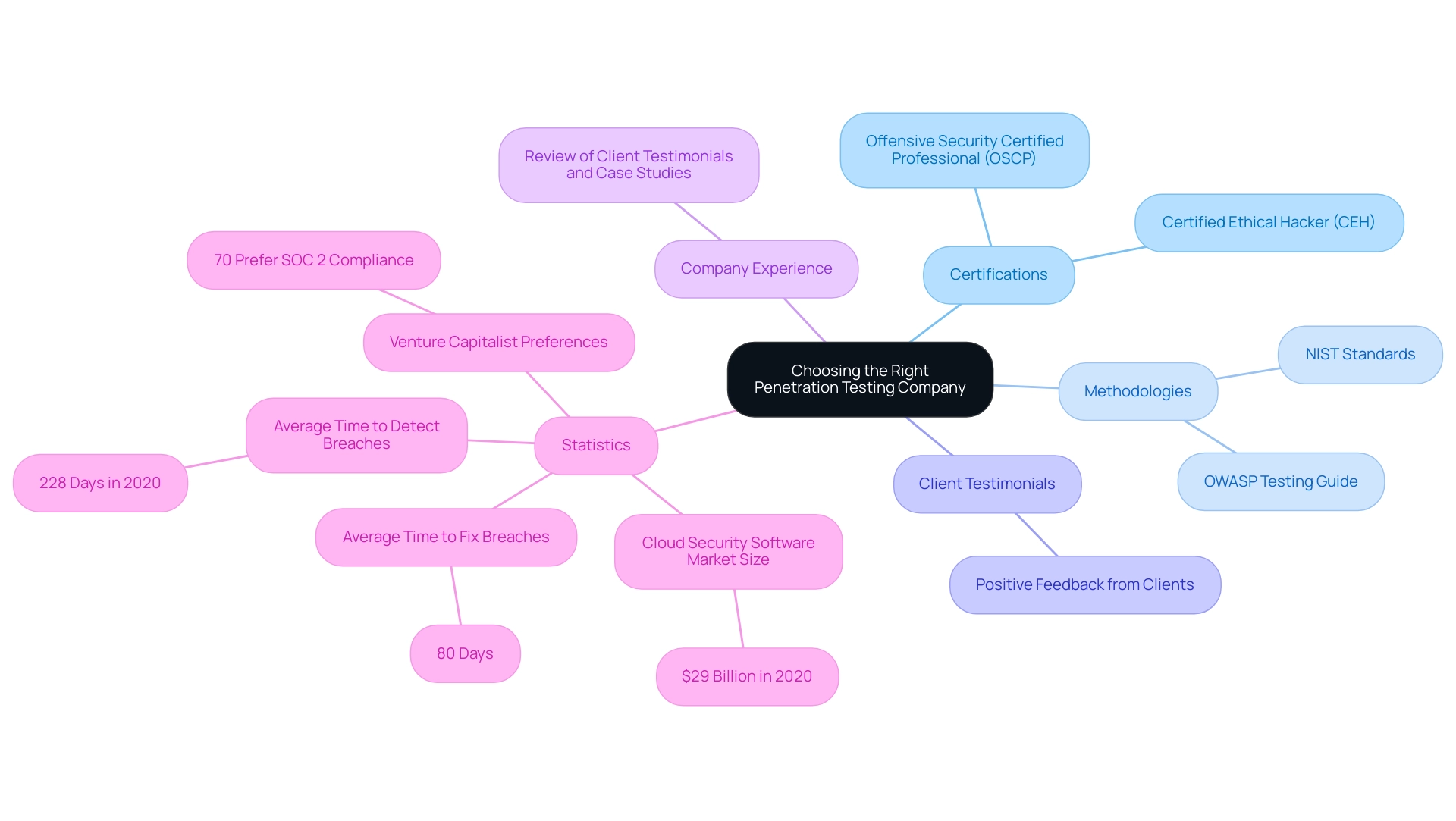
When choosing penetration testing companies in Dubai, entities must thoroughly assess various essential factors to guarantee they collaborate with a provider that fulfills their particular security needs. Foremost among these factors is the presence of recognized certifications, such as the Certified Ethical Hacker (CEH) and the Offensive Security Certified Professional (OSCP). These credentials not only signify a practitioner's proficiency but also reflect a commitment to adhering to established industry standards.
STS Consulting Group's team is well-versed in various testing methodologies, including OWASP Testing Guide and NIST standards, and employs advanced tools like Burp Suite and Nessus during assessments to ensure thorough evaluations. Furthermore, assessing a company's experience is vital; organizations should review client testimonials and case studies to gain insights into their past performance and reliability. As one client noted,
'I was really impressed with the way STS Consulting Group handled everything.
From the first conversation to everything in between, they were very helpful and knowledgeable.'
This sentiment echoes the importance of thorough evaluations. Another testimonial states,
'STS Consulting Group was the missing piece to my puzzle.
From start to finish, they solved every problem and helped us achieve our goals in the most professional way possible.'
Such feedback highlights the effectiveness and professionalism of the team. A thorough examination of a company’s history can reveal its ability to adapt to evolving threats, especially in a landscape where the average time to detect web application breaches spanned 228 days in 2020, underscoring the necessity for swift remediation strategies.
This is further emphasized by the case study which indicates that the average time to fix a breach was 80 days, highlighting the critical need for prompt response measures. Additionally, understanding the methodologies employed and tools utilized during evaluation is crucial for gauging the thoroughness of the assessments. The rising investment in cybersecurity solutions is clear, with the cloud protection software market size reaching $29 billion in 2020, reflecting the increasing significance of strong protective measures.
Moreover, as noted by John Doe,
'70% of venture capitalists prefer investing in companies with SOC 2 compliance,'
underscoring the significance of compliance and certifications in the industry. This thorough strategy guarantees that entities choose penetration testing companies in Dubai as partners that not only align with their security goals but also possess the necessary expertise to protect their digital assets from increasingly significant threats.
The Benefits of Penetration Testing for Businesses in Dubai
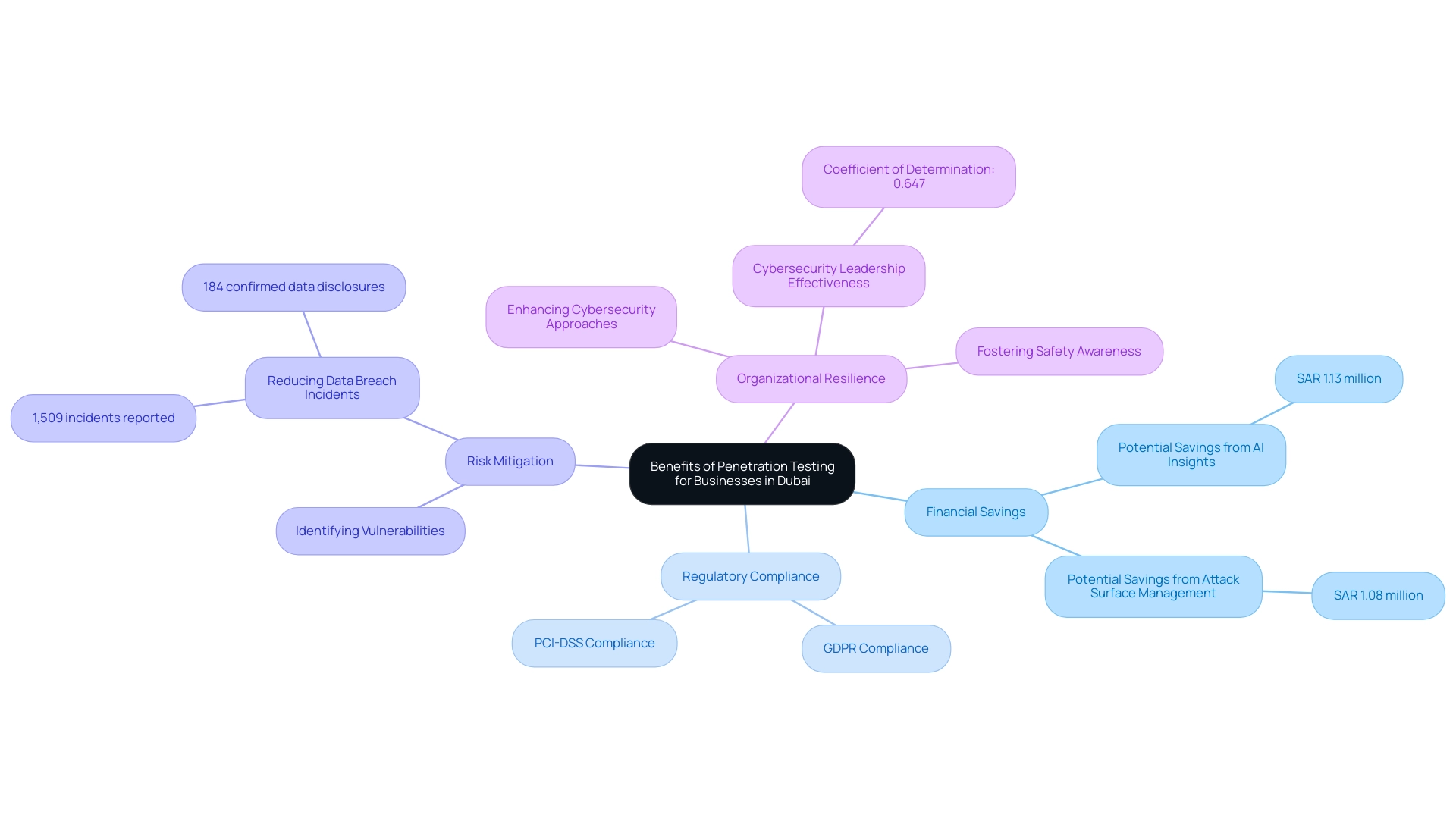
Penetration testing companies in Dubai serve as a vital tool for businesses, significantly enhancing cybersecurity measures while ensuring compliance with essential regulatory frameworks. By proactively identifying vulnerabilities before they can be exploited, entities can substantially mitigate the risk of data breaches, which have been a pressing concern. For instance, Kaspersky reported over 1,509 incidents within financial organizations, with 184 confirmed data disclosures in recent years.
This clearly illustrates the financial ramifications of inadequate security measures. Additionally, the case study titled "Reducing the Cost of a Data Breach" emphasizes how AI-driven insights and attack surface management tools can result in possible savings of SAR 1.13 million and SAR 1.08 million respectively, illustrating the concrete advantages of security assessments in diminishing the financial repercussions of data breaches. Furthermore, security assessments play a crucial role in meeting compliance standards such as GDPR and PCI-DSS, which require that businesses demonstrate due diligence in protecting sensitive information.
The findings obtained from vulnerability assessments allow companies to strategically prioritize protective investments, enhance their cybersecurity approaches, and foster a culture of awareness regarding safety among staff. Moreover, as Ratten discusses, the influence of cybercrime on innovation in technology firms underscores the importance of robust cybersecurity measures for business growth. The coefficient of determination statistic of 0.647 for Cybersecurity Leadership further reinforces the effectiveness of these strategies, making vulnerability assessments an essential component of a comprehensive protective framework that not only defends against current threats but also strengthens the organization’s resilience against future challenges.
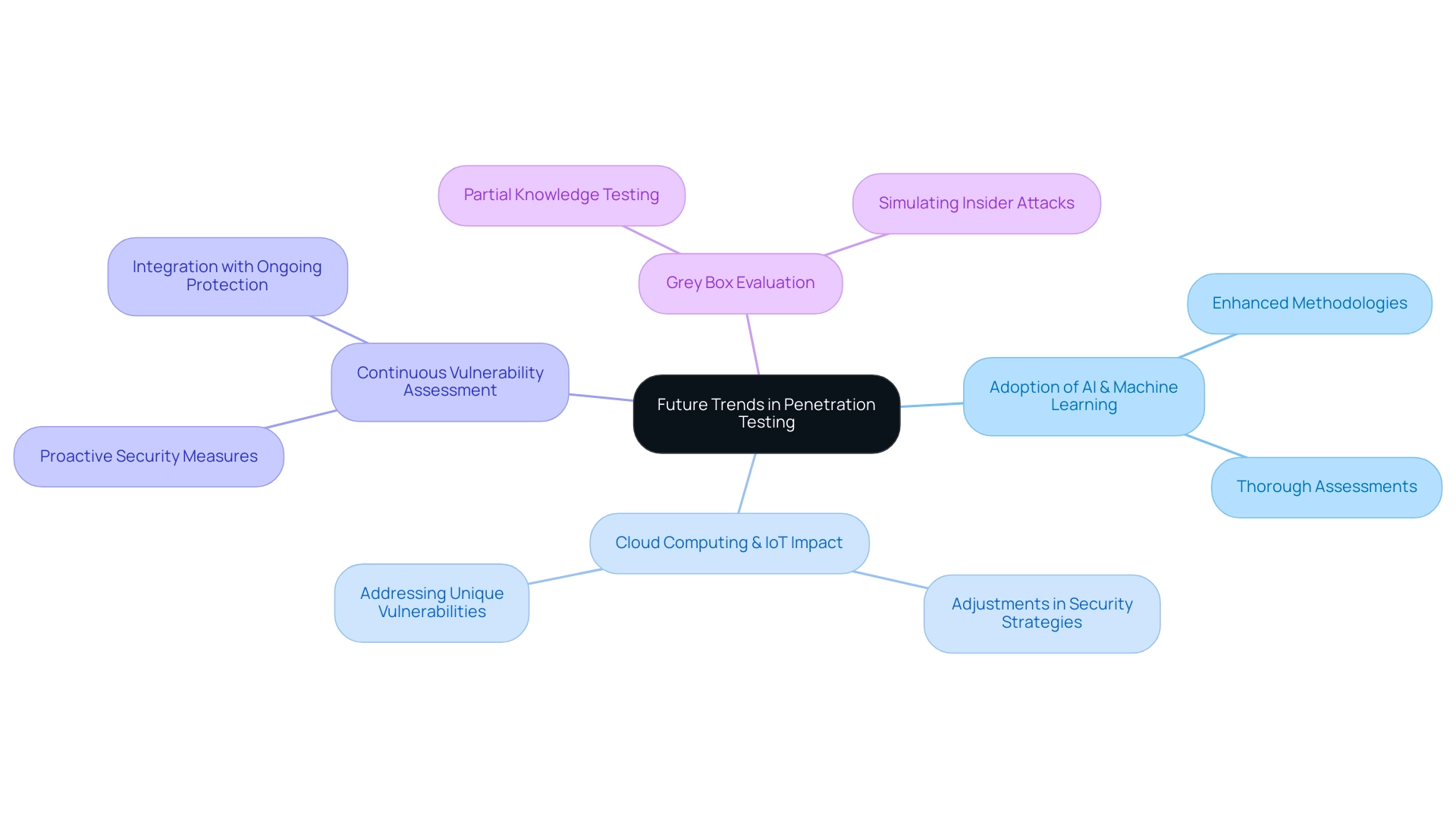
Future Trends in Penetration Testing: What to Expect
The future of security evaluation is on the verge of substantial change, largely shaped by swift technological progress and a shifting threat environment. One of the most notable emerging trends is the adoption of artificial intelligence and machine learning to enhance evaluation methodologies, which allows for more thorough assessments of security postures. Organizations are increasingly investing in security assessments, with an average expenditure of $349, underscoring its significance in the context of cybersecurity investments.
As enterprises adopt cloud computing and IoT devices, security evaluation strategies will require adjustments to effectively tackle the distinct weaknesses these technologies present. Furthermore, the increase of continuous vulnerability assessment practices indicates a transition towards incorporating intrusion evaluation within ongoing protective measures, instead of regarding it as a one-time, separate occurrence. This proactive approach is crucial for organizations looking to maintain robust cybersecurity defenses in an increasingly complex environment.
A security assessment exercise aims to identify weaknesses or vulnerabilities in a system that an attacker could exploit and provide guidance on how to address or reduce those vulnerabilities before an attack happens. Additionally, grey box evaluation, which involves security assessments where the tester possesses partial knowledge of the target system, illustrates the evolving methodologies in this field. As these trends continue to evolve, organizations must stay agile and well-informed to fully harness the potential of penetration testing in their cybersecurity strategies.
Conclusion
In an era where cyber threats are omnipresent, the importance of penetration testing cannot be overstated. This proactive approach allows organizations to simulate potential attacks, identify vulnerabilities, and fortify their defenses before malicious actors strike. By understanding the nuances of penetration testing, businesses can not only protect sensitive data but also ensure compliance with essential regulatory frameworks, significantly reducing the risk and financial impact of data breaches.
The diverse services offered by penetration testing firms in Dubai highlight the tailored approaches necessary to address varying security needs. From web and network application assessments to social engineering tests, these services are crucial for organizations striving to maintain a robust cybersecurity posture. As the demand for such services continues to grow, selecting the right penetration testing partner becomes paramount. Organizations must evaluate:
- Certifications
- Methodologies
- Past performance
to ensure they align with their specific security objectives.
Looking ahead, the future of penetration testing is poised for transformation, driven by advancements in technology and emerging threats. The integration of artificial intelligence and continuous security testing practices will redefine how organizations conduct assessments, making it essential for them to adapt to the evolving landscape. By prioritizing penetration testing as a fundamental element of their cybersecurity strategy, businesses can not only safeguard their digital assets but also foster a culture of security awareness that is vital for long-term resilience.




