Introduction
In today's interconnected digital landscape, email remains a cornerstone of communication for both individuals and organizations. However, with its widespread use comes a significant risk: email viruses. These malicious entities not only threaten individual users but can also cause extensive damage to businesses, leading to data breaches, financial loss, and reputational harm.
This article delves into the mechanics of how email viruses operate, the various forms they can take, and the potential risks they pose. Additionally, it offers crucial insights into protective measures and best practices to safeguard against these pervasive threats. Understanding the intricacies of email security is paramount to maintaining the integrity and confidentiality of sensitive information in an era where cyber threats are ever-evolving.
Can You Get a Virus from Opening an Email?
It is indeed possible to contract a virus from opening a message, but the mechanics are more complex than one might think. Typically, merely opening a message does not activate a virus. However, cybercriminals often embed malicious links or attachments within the email. When these links are clicked or attachments are downloaded, they can execute harmful software. Attackers employ advanced strategies to entice individuals into interacting with these elements, heightening the chance of infection. For instance, in one notable case, attackers exploited Amazon’s Simple Email Service (SES) to send out phishing and spam campaigns from a seemingly trusted sender, catching many individuals off guard.
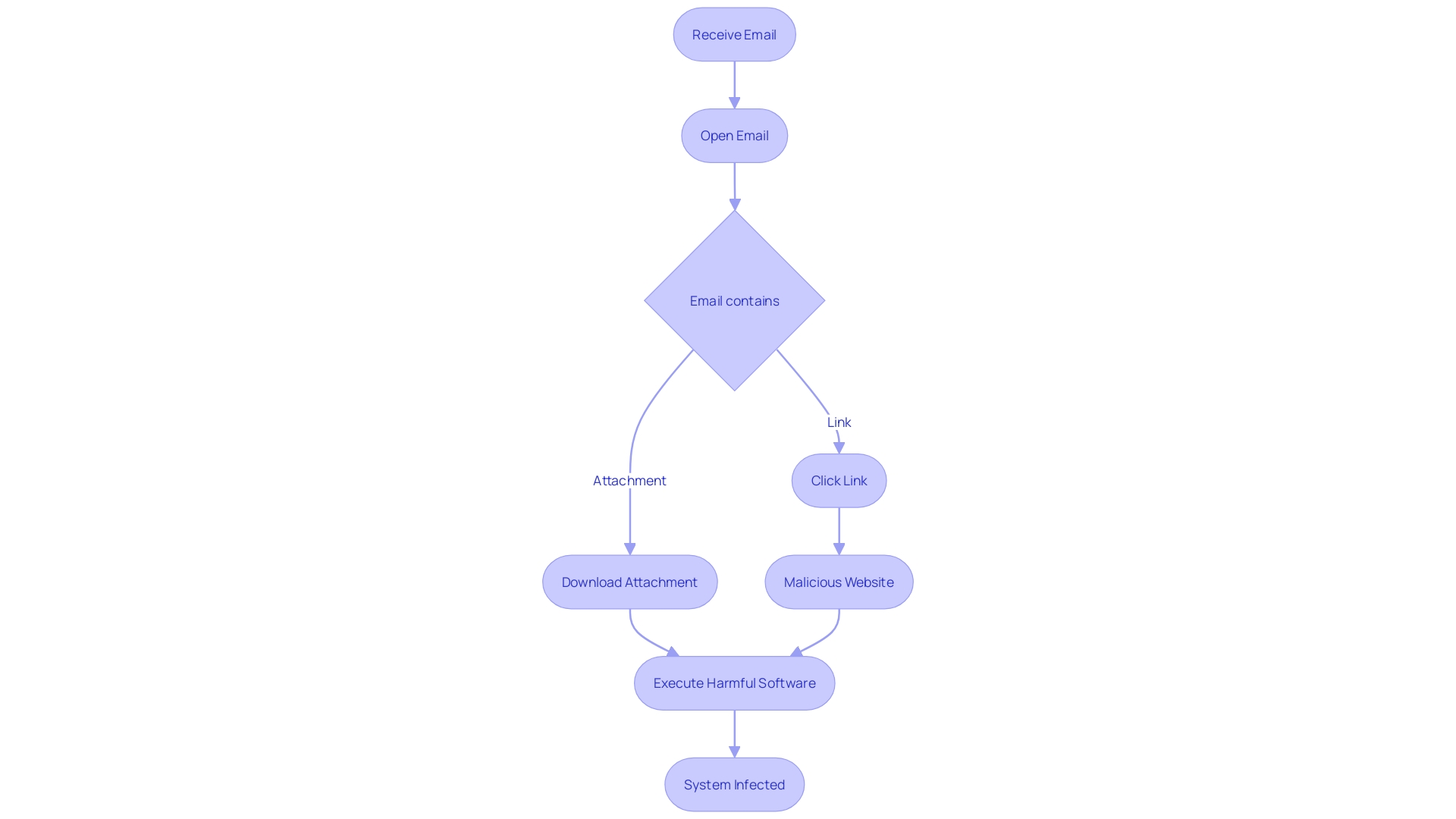
How Email Viruses Work
Email viruses often employ sophisticated social engineering tactics to deceive individuals into executing malicious code. When an individual clicks on an infected link or opens a compromised attachment, the virus can exploit system vulnerabilities to install malware. This malware can then propagate by sending infected messages to contacts within the user's address book, thereby perpetuating the spread of the virus. 'As noted in recent instances, attackers have succeeded in breaching systems by generating fake support cases to enhance service limits, which are then utilized to spread phishing and spam campaigns.'. This underscores the critical need for comprehensive email security measures to mitigate the risks posed by such deceptive techniques. According to cybersecurity experts, 'social engineering is an art of deception, aiming to exploit the weakest link in the cyber defense system: the human element.' This emphasizes the significance of informing individuals about the potential hazards and how to identify questionable behaviors.
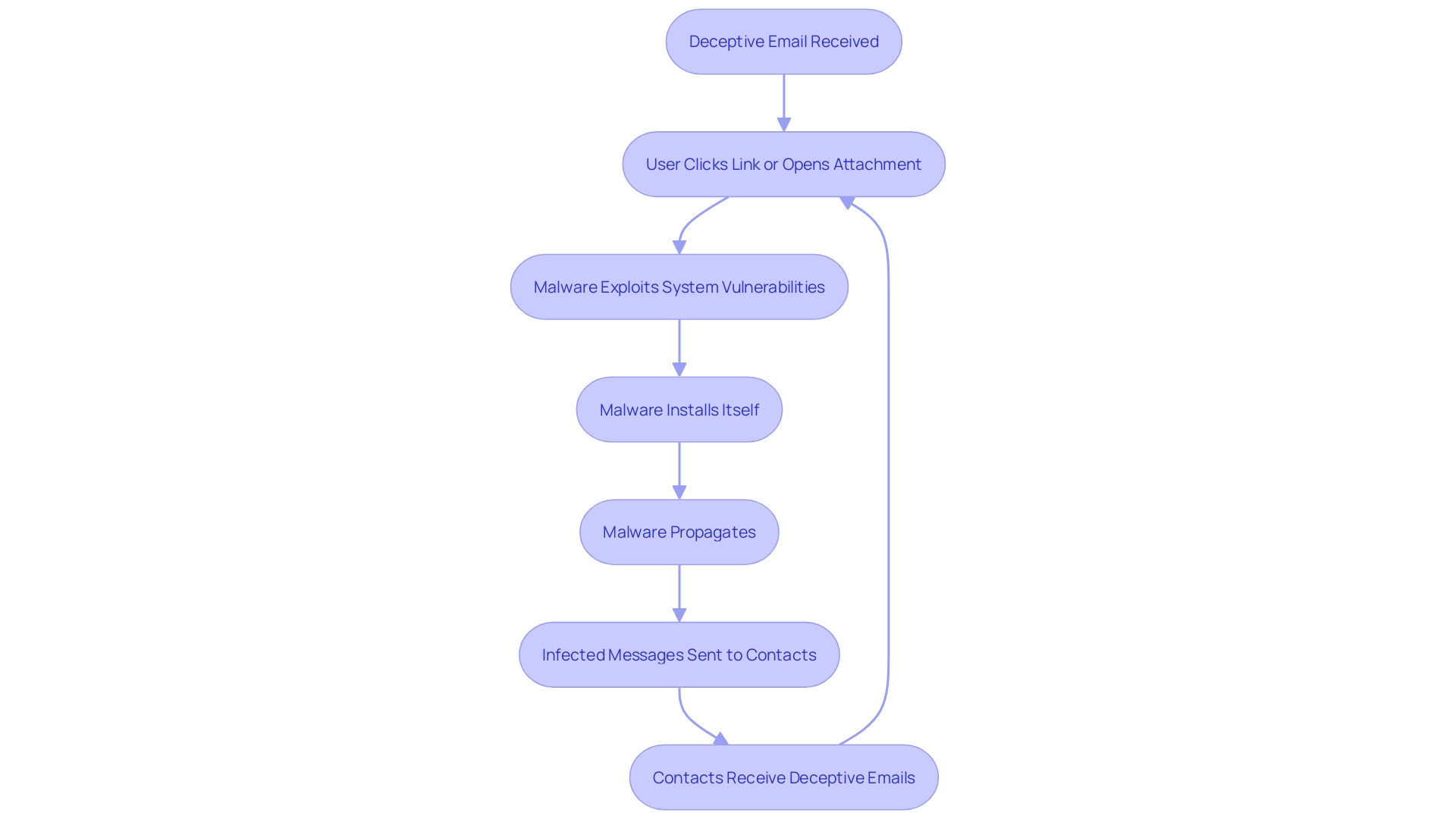
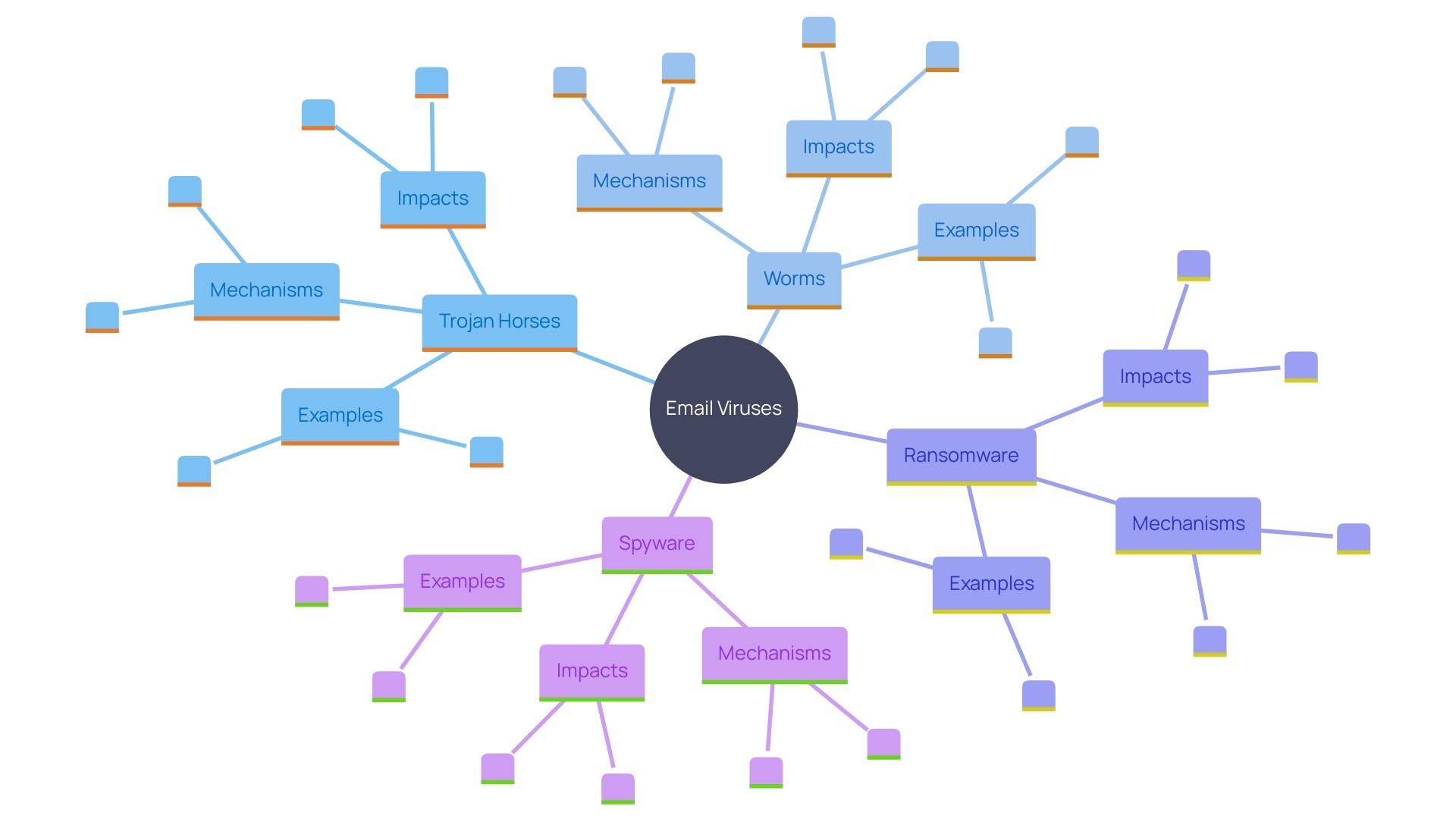
Types of Email Viruses
Email viruses come in various forms, each with unique mechanisms and impacts:
- Trojan Horses: These malicious programs masquerade as legitimate software or files, often tricking users into executing them. Once activated, they can infiltrate systems, providing unauthorized access to attackers. '- Worms: Unlike other malware, worms replicate themselves and spread across networks without any human intervention, potentially causing widespread disruptions.'.
- Ransomware: This type of malware encrypts an individual's files and demands a ransom for their release. The financial and operational effects of ransomware can be devastating, making it a significant danger.
- Spyware: Operating stealthily, spyware collects sensitive information, such as passwords and personal data, without the user's knowledge or consent.
Understanding these threats is crucial for recognizing and mitigating potential risks. For example, a recent incident involved a suspicious support case in an AWS account, where attackers attempted to exploit Amazon's Simple Email Service (SES) to send out phishing campaigns. This emphasizes the significance of strong communication protection strategies to defend against such advanced assaults.
As highlighted by industry specialists, "Email protection includes the methods and technologies utilized to safeguard email accounts and communications from unauthorized access, loss, or compromise." Given the high volume of sensitive information exchanged via email, strong protective measures are crucial to avert data breaches, financial losses, and reputational harm.
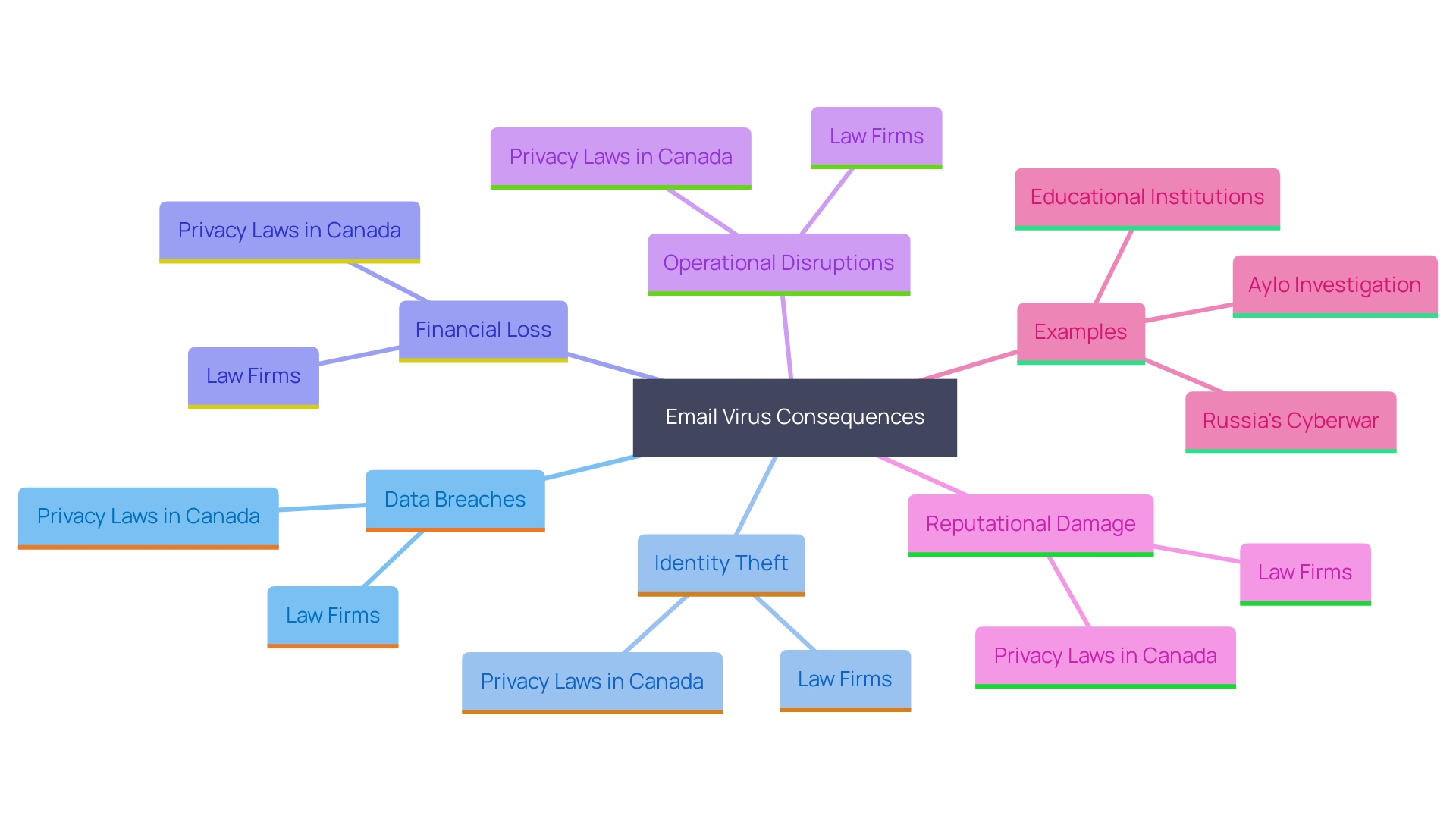
Risks of Email Viruses
Email viruses pose a substantial threat, leading to severe consequences such as data breaches, identity theft, and financial loss. A successful cyberattack can compromise not only the victim's data but also that of their contacts, causing widespread repercussions. For organizations, this can result in operational disruptions and significant reputational damage. For instance, law firms, which handle highly sensitive client information, risk losing client trust and facing legal ramifications if their cybersecurity is breached. In Canada, where privacy laws require the public disclosure of breaches, the stakes are even higher. Recent research highlights that nearly a quarter of UK SMEs experienced breaches, impacting operations and eroding confidence in their ability to manage risk. Such incidents highlight the critical need for strong communication security measures to protect organizational integrity and client confidentiality.
How to Protect Yourself from Email Viruses
To protect against messaging viruses, it is essential to implement several strategic practices. First, enable robust spam filters to block suspicious messages, which can significantly reduce the risk of Business Email Compromise (BEC) attacks. Second, avoid opening attachments or clicking links from unknown senders. This strategy is particularly crucial given the sophisticated nature of phishing attacks that exploit human psychology to harvest credentials or install malware.
Consistently refreshing operating systems and antivirus programs is another essential action to counter the latest dangers. For example, tools like YARA, designed to identify and categorize malware, can be highly effective when kept up-to-date. Furthermore, training all staff on identifying phishing attempts and harmful messages can strengthen internal protections. A case in point is a phishing campaign conducted by Baker Tilly for a healthcare services organization, where enhanced training reduced the number of employees who clicked on phishing links.
In today's swiftly changing cybersecurity environment, implementing these extensive measures can assist organizations in staying ahead of possible risks and safeguarding their technological resources.
Safe Email Practices
Adopting strong electronic communication protection methods is crucial in reducing dangers linked to cyber threats. Regularly updating passwords and enabling multi-factor authentication (MFA) are fundamental steps. MFA combines something you have, such as an authentication app, with something you are, like fingerprint recognition, to enhance security. Caution is imperative when sharing personal information to prevent unauthorized access.
Consistently examining and tidying the inbox can assist in spotting and removing questionable messages before they turn into an issue. This proactive approach is crucial as electronic communication remains a significant vector for cyber-attacks. According to a study by AppRiver, email accounts for 35% of all data loss incidents among enterprises, highlighting the importance of maintaining a secure email environment.
Fostering a culture of security awareness within organizations is essential. This involves educating employees about the latest phishing tactics and ensuring they can recognize potential risks. As Mike Britton from Abnormal Security points out, understanding and applying optimal cybersecurity practices in a swiftly changing risk environment is essential. By adopting these measures, individuals and organizations can better protect themselves from email-related threats.
Conclusion
Email viruses present a significant threat in today's digital communication landscape, impacting both individuals and organizations. The intricate mechanics of these malicious entities reveal that simply opening an email does not trigger a virus; rather, it is the interaction with embedded links or attachments that can lead to infection. Cybercriminals employ sophisticated social engineering tactics to manipulate users into unwittingly executing harmful software, illustrating the critical importance of heightened awareness and education regarding email security.
The various forms of email viruses, including Trojan horses, worms, ransomware, and spyware, each have unique mechanisms and potential impacts. Understanding these distinctions is essential for recognizing and mitigating risks. The consequences of a successful email virus attack can be severe, leading to data breaches, financial loss, and reputational damage, particularly for organizations handling sensitive information.
The risks are compounded by stringent privacy laws in certain regions, emphasizing the need for robust email security measures.
Protective strategies against email viruses include implementing strong spam filters, avoiding interactions with unknown senders, and regularly updating security software. Additionally, fostering a culture of security awareness through employee education is paramount. By adopting comprehensive measures and safe email practices, individuals and organizations can significantly enhance their defenses against the evolving landscape of cyber threats.
The proactive implementation of these strategies is vital to maintaining the integrity and confidentiality of sensitive information in an increasingly interconnected world.




