Introduction
In today's digital age, organizations face an ever-increasing threat of cyberattacks. To effectively safeguard their assets, it is crucial for organizations to have a robust incident response plan (IRP) in place. An IRP provides a systematic and structured approach to addressing cybersecurity threats, ensuring that teams are prepared to respond effectively.
This article explores the key components of an IRP, the importance of testing and reviewing the plan, and the benefits of outsourcing incident response. By following best practices and continuously improving their incident response strategies, organizations can enhance their resilience against cyber threats and minimize the impact on their operations. So, let's delve into the world of incident response and discover how organizations can fortify their cybersecurity defenses.
Why an Incident Response Plan is Crucial
The development of a strong incident management strategy (IMS) is a crucial and strategic undertaking for protecting organizational assets in the digital era. An IRP encompasses comprehensive procedures which are meticulously documented to guide teams through each phase of responding to cybersecurity threats. The strategy must encompass distinct duties, efficient communication approaches, and standardized reaction measures. It is crucial to clarify the terminology within the strategy, such as differentiating between an 'event,' which is a change in system settings or status, and an 'alert' or 'incident,' which may indicate a more serious breach or security issue.
Testing the IRP is a step that should not be overlooked. Consistently testing the strategy with simulated events can reveal vulnerabilities and guarantee that crucial procedures such as escalation, triage, and establishing alternative communication channels are successful when they are most necessary. Metrics such as the Mean Time to Respond (MTTR) are crucial, as they reflect the effectiveness of your response team in identifying and resolving issues. Moreover, the seriousness of a cybersecurity occurrence cannot be underestimated, as legal obligations demand organizations to reveal breaches within specific timeframes, such as within 72 hours in the UK.
In the broader context of organizational resilience, an Incident Response Plan is complemented by a Disaster Recovery Plan (DRP), which is integral to business continuity. A comprehensive DRP safeguards against data loss through regular backups, maintains communication with all stakeholders during a crisis, and identifies the allocation of resources to facilitate swift recovery. The partnership between an IRP and a DRP guarantees that a business can address, bounce back from, and endure cybersecurity occurrences with minimal operational disturbance.
Key Components of an Incident Response Plan
A successful strategy for modern cybersecurity defense relies on a well-organized and methodical approach to address possible disruptions. The basis of a strong strategy for handling unexpected events is created by multiple crucial elements, each essential to the functionality and effectiveness of the approach.
To begin with, the plan for addressing the situation must include thorough descriptions of sub-processes, such as escalation, triage, and activation of alternative communication channels. Regular testing of these processes is imperative to ensure they function optimally during an actual cyber incident. By simulating scenarios and assessing the reaction, entities can identify and rectify any deficiencies in their procedures.
Moreover, the plan should be customized to reflect the unique needs of the organization, considering the potential impact on business operations and stakeholder interests. Collaboration across various business units, including public relations, legal, and communications, is essential for a coordinated response to cyber threats.
A recent report emphasizes the definition of a 'reportable cyber event' as one that significantly impacts the confidentiality, integrity, or availability of critical systems, disrupts business operations, or compromises sensitive personal information. This emphasizes the significance of having a comprehensive strategy that encompasses a wide range of occurrences.
Essential stages of a successful handling of an unexpected event comprise recognition and recording, evaluation of impact and seriousness, examination and interpretation, reduction and solution, and concluding with comprehensive record-keeping and communication to interested parties. These steps constitute the management workflow, ensuring that issues are handled efficiently from detection to resolution.
The importance of a well-communicated approach to handling unexpected events is further highlighted by the Cybersecurity and Infrastructure Security Agency (CISA), which spearheads initiatives to minimize risk to the nation's cyber and physical infrastructure. CISA's mission underscores the importance of collaboration and sharing resources to build resilience against cyber threats.
To summarize, a preparedness and adaptability reflection of an entity can be seen in their set of procedures when facing cyber threats. Customizing this strategy to the particular requirements and intricacies of the company, while adhering to industry standards, is essential for sustaining operational stability and security.
Preparation
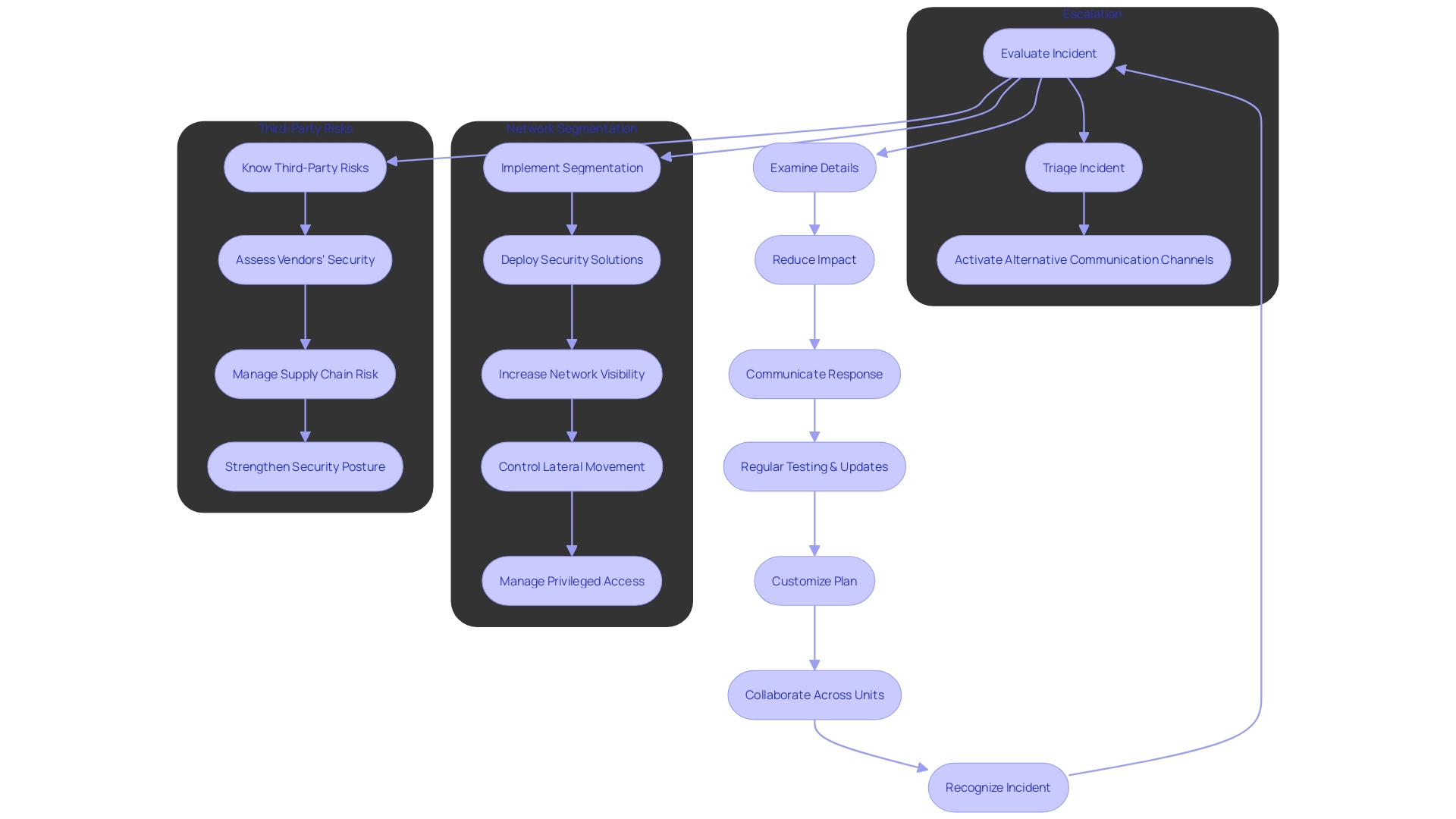
The foundation of strong cybersecurity protection is a carefully designed action strategy, which depends on a thorough comprehension of your company's distinctive security position. It's crucial to acknowledge that a reaction strategy extends beyond a simple protocol; it's a dynamic design customized to meet the specific requirements of your company, intended to develop with each simulated examination. By diligently testing and refining key processes—ranking them by criticality and necessary effort—you can expose and bridge gaps in your escalation, triage, and communication strategies.
A comprehensive strategy for managing unexpected occurrences must incorporate clear definitions to avoid confusion, particularly when distinguishing between an event, alert, and situation. Furthermore, it should outline the legal obligations that follow a breach, ensuring your organization maintains transparency and meets mandatory disclosure timelines, like the 72-hour window mandated in the UK.
Statistics underscore the importance of preparedness; out of ninety-five billion security events analyzed in the first half of 2023, 0.1% were flagged as potential threats, with a subset requiring immediate action. This information, supported by real-life examples and specialist perspectives, demonstrates the importance of having a crisis management strategy that is both thorough and consistently evaluated and revised in light of developing risks.
Remember, the goal is not just to respond but to do so effectively, minimizing the impact on your business operations and maintaining trust with stakeholders. As such, your response plan should be a living document, rigorously examined and continuously refined to ensure readiness for any cybersecurity threat.
Detection and Analysis
The first measures in addressing cybersecurity events are vital for the integrity of IT systems and the business's resilience. Implementing sophisticated monitoring solutions that vigilantly watch over network activities is imperative. These systems must be fine-tuned to recognize anomalies that may indicate a breach or unauthorized access. When a situation arises, it is crucial to not only control it but also to conduct a comprehensive analysis to understand its extent, consequences, and root cause. For instance, there was a case involving an AWS account where a dubious support case was the red flag that led to the discovery of a broader malicious activity spanning over a month. The event developed in three clear stages, with each stage classified using the MITER ATT&CK framework. It began with the creation of a support case by an unrecognized IAM user and escalated into a complex situation requiring immediate response and investigation.
Recent analysis of ninety-five billion events across various security tools has shed light on the prevalence of potential security threats. Alarmingly, 985,000 of these events were marked as 'alarms', signaling possible malicious intent. Out of these, only a fraction underwent review by security teams, and an even smaller subset was deemed high-risk, necessitating urgent action by cybersecurity professionals. These findings underscore the importance of vigilant monitoring and rapid analysis to prevent cyber threats from escalating.
Moreover, AI's role in detection and analysis phases has become increasingly significant. By examining patterns and identifying deviations from normal behavior, AI systems offer a powerful means to pinpoint potential threats. Research by Columbia University and Barracuda Networks has demonstrated AI's efficacy, particularly in recognizing and thwarting email-based blackmail scams.
In the grand scheme of incident management, an Incident Response Plan (IRP) and an Incident Response Team (IRT) are essential components. The IRP provides a roadmap for detecting, responding to, and mitigating the effects of cyber-attacks, while the IRT is tasked with executing these plans effectively. The overarching goal of these concerted efforts is to resume normal operations as swiftly as possible, thereby preserving the enterprise's reputation and maintaining the trust of stakeholders.
The dynamic nature of cyber threats today demands that organizations remain proactive and prepared. By implementing effective strategies and utilizing appropriate tools, businesses can protect themselves from the potentially harmful effects of cybersecurity events and strengthen their operational stability.
Containment, Eradication, and Recovery
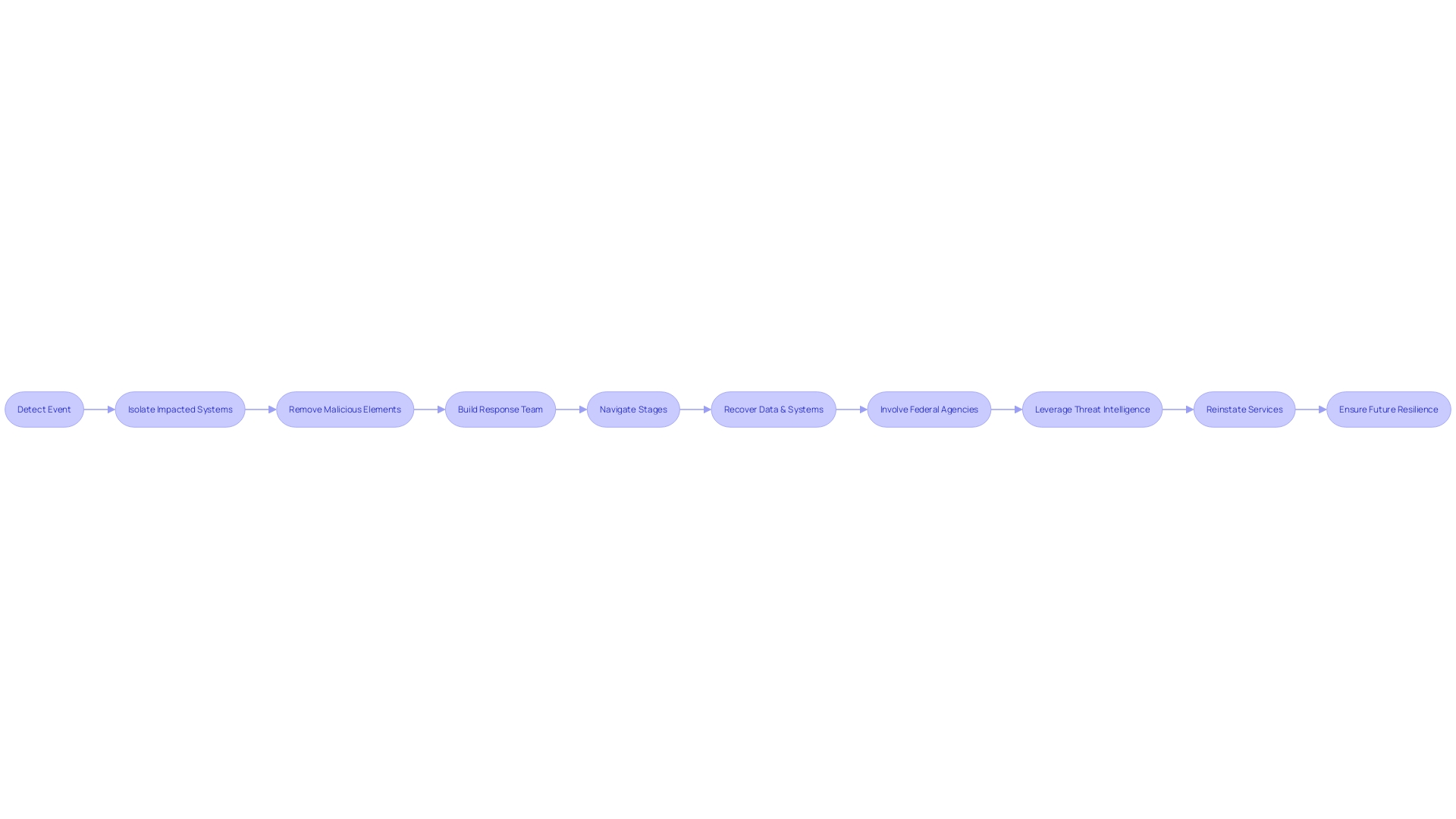
Addressing a security event efficiently necessitates a structured approach that surpasses mere technical remedies. Once a cybersecurity event is detected, a swift and coordinated action is crucial to limit damage and resume normal operations promptly. This necessitates a series of well-defined steps that start with isolating impacted systems to prevent the spread of the threat, followed by the thorough removal of any malicious elements from the environment.
Building the appropriate group is the foundation of a fruitful reaction to an event. This team should bring together key personnel, including those who reported the issue, those with the authority to make critical decisions ('Keymasters'), and those with the technical expertise to address the problem ('Fixers'). These individuals work together to navigate the stages of addressing an unexpected situation, from initial confusion to achieving clarity on the matter, and ultimately to resolving the crisis.
Reducing the consequences of an event also includes recovering data and system functionality from secure backups. Companies like Fortinet, who experienced unauthorized access to a small subset of their files, underscore the importance of swift action in mitigating potential damage and maintaining transparency with the affected stakeholders. They also emphasize the resilience of operations that continue unaffected by such incidents, which is a testament to robust incident reaction planning.
Moreover, the role of federal agencies like CISA in guiding national efforts to manage and reduce risks to cyber and physical infrastructure cannot be overstated. Their initiatives help connect stakeholders across industry and government, facilitating the sharing of resources and tools that enhance the collective security posture.
In the context of a changing threat environment, with dangers like burnout among security operation center (SOC) personnel and the increase of advanced supply chain attacks, leaders need to have a deep understanding of current threats and be proactive in their strategies. By leveraging detailed insights, such as those offered by Unit 42's report on threat landscapes and MITER ATT&CK techniques, organizations can make informed tactical decisions to fortify their defenses against cyber threats.
In the end, the objective of addressing unexpected events is to promptly reinstate services for customers, uphold the integrity of operations, and guarantee the resilience of systems against future occurrences. It is a comprehensive process that encompasses detection, analysis, and recovery efforts, fortified by the collaboration of a multi-disciplinary team and informed by the latest in cybersecurity intelligence.
Post-Incident Activities
Once the immediate danger of a cyber event is neutralized and operations have resumed, it is crucial to engage in post-episode activities to refine and strengthen future response strategies. A detailed post-incident analysis is imperative, involving meticulous documentation of the occurrence, analysis of the root causes, and identification of the exploited vulnerabilities. Gaining knowledge from occurrences, such as the brief but significant outage encountered by Graphite, highlights the significance of a transparent and accountable review process. As articulated by Greg Foster, CTO of Graphite, sharing a complete report with the community and customers not only upholds transparency but also contributes to the collective knowledge pool.
The insights gained from such post-incident reviews can be instrumental in shoring up defenses and preventing recurrences. For instance, a suspicious support case at AWS that was not initiated by the client but triggered an alert due to an abnormal request highlights the importance of having robust monitoring and alert systems. This occurrence, outlined in sequential arrangement using the MITER ATT&CK framework, emphasizes the need for explicit and accurate terms within an Incident Response Plan (IRP), such as differentiating between an event, an alert, and a situation.
Furthermore, the partnership between major players in the industry such as Microsoft and PwC to provide prompt and comprehensive reactions to cyber occurrences illustrates the changing environment of event control. It is advisable that knowledge gained from occurrences be utilized to improve security solutions and strengthen the security position of all parties involved.
In the words of Kymberlee Price, a seasoned professional in the security realm, the essence of security at an organizational level is synonymous with quality. Reliable and secure code is fundamental to an organization's cybersecurity framework. This sentiment is echoed by Wolfgang Goerlich, who emphasizes the proactive reassessment of teams and processes as vital to staying ahead of potential threats.
Regularly testing the process of addressing unexpected events is also crucial, as stated by experts who recommend breaking down the IRP into key processes and testing them for effectiveness. The reaction range, from identification through restoration to post-event examination, has developed from an improvised method to a structured approach, with the creation of Computer Emergency Response Teams (CERTs) signifying a notable milestone in its history.
By embracing a systematic approach to post-incident activities, entities can greatly enhance their resilience and preparedness for future cyber threats, aligning with the proactive cybersecurity philosophy that aims to anticipate and preempt potential attacks.
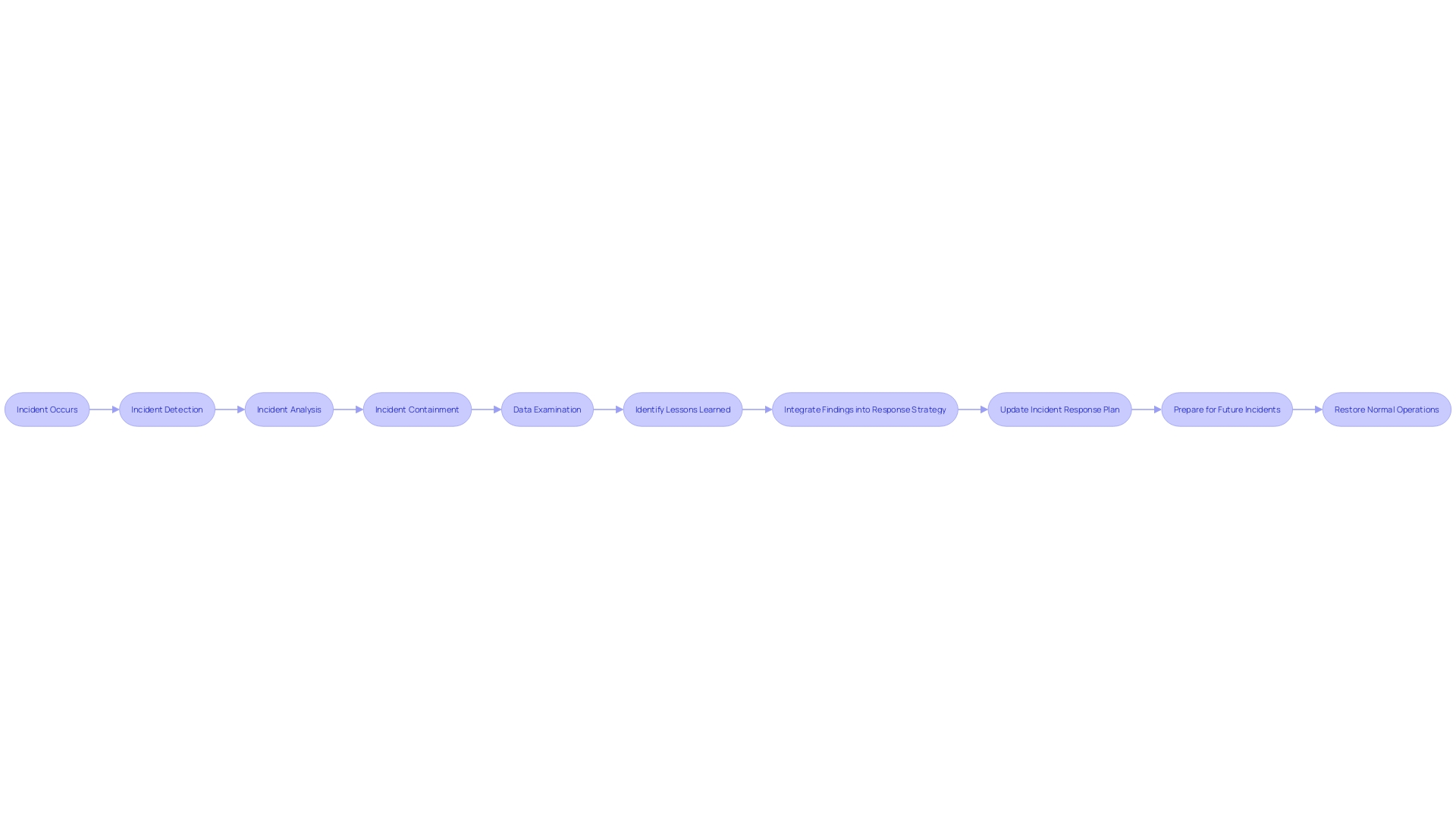
Steps to Build an Effective Incident Response Plan
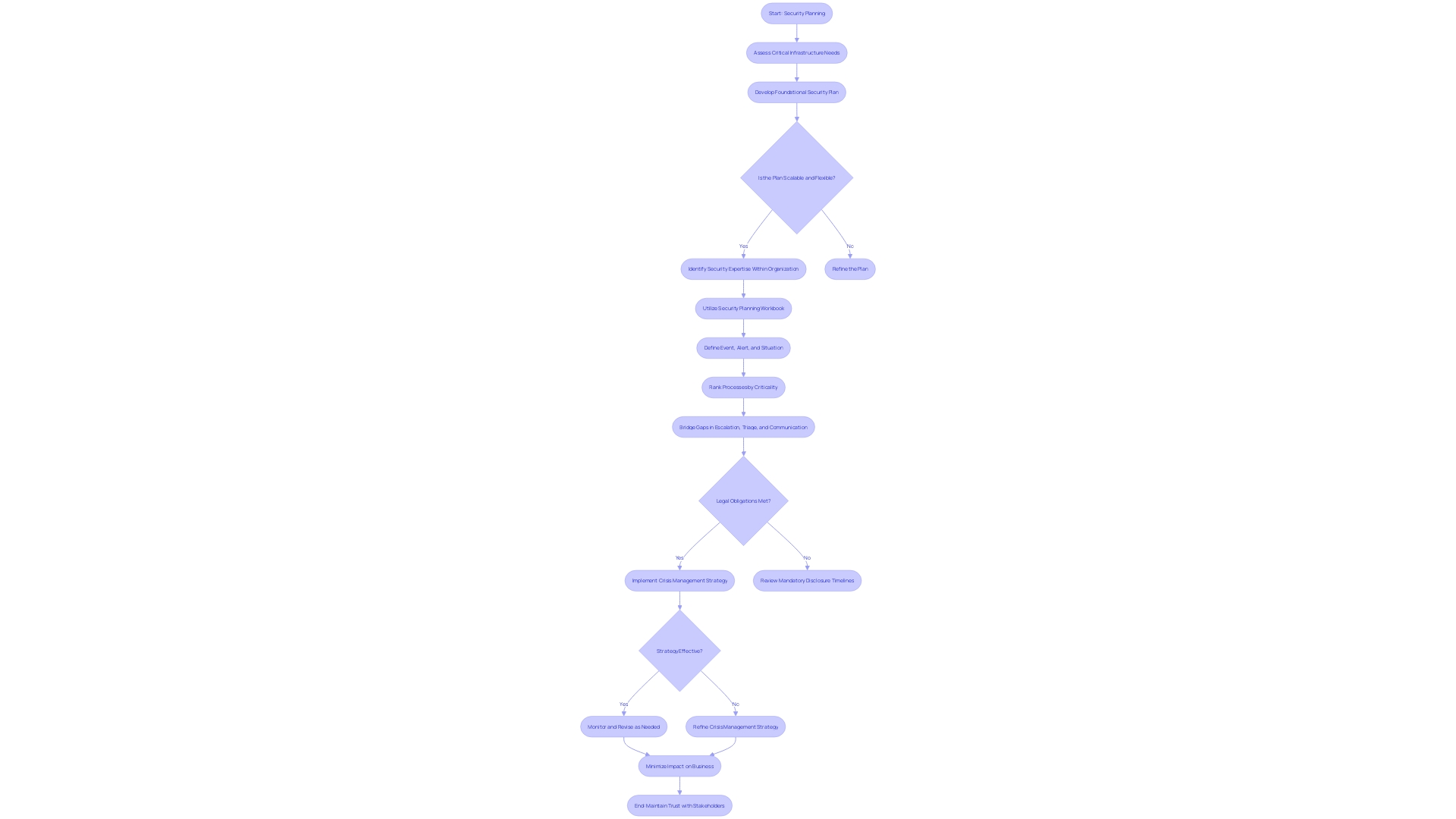
Developing a strong strategy to address and reduce the consequences of security events is vital for every company. The strategy needs to be thorough, outlining particular steps for every stage of addressing the situation, from recognition to resolution. It should clearly define roles and responsibilities, ensuring that each team member knows their tasks. Communication is key; a communication plan must be established to facilitate swift information flow among team members and stakeholders. It's critical to use unambiguous language and to clarify commonly confused terms, such as 'event,' 'alert,' and 'incident,' to prevent miscommunication.
A crucial element of responding to an event is the recognition of not only the primary reason, but also the factors that may worsen the situation. For example, configuration drift, where a web server's settings deviate from the standard due to unauthorized changes, can significantly complicate incident management. Therefore, the strategy should include methods to detect and address these contributing factors.
The strategies for dealing with incidents are dynamic records that need to adapt to the company and the changing nature of the dangers it encounters. This implies that they should be regularly evaluated and revised to include new insights from recent events and modifications in the IT environment of the entity. By implementing a methodical approach to evaluate and revise the course of action, it ensures that it continues to be efficient and applicable.
In summary, a response plan is a vital part of a cybersecurity strategy. It must be well-documented, clear, and comprehensive, incorporating roles, responsibilities, communication protocols, and strategies for identifying and managing contributing factors to events. By adhering to a structured and systematic approach, entities can minimize downtime, mitigate risks, and enhance their resilience against cyber threats.
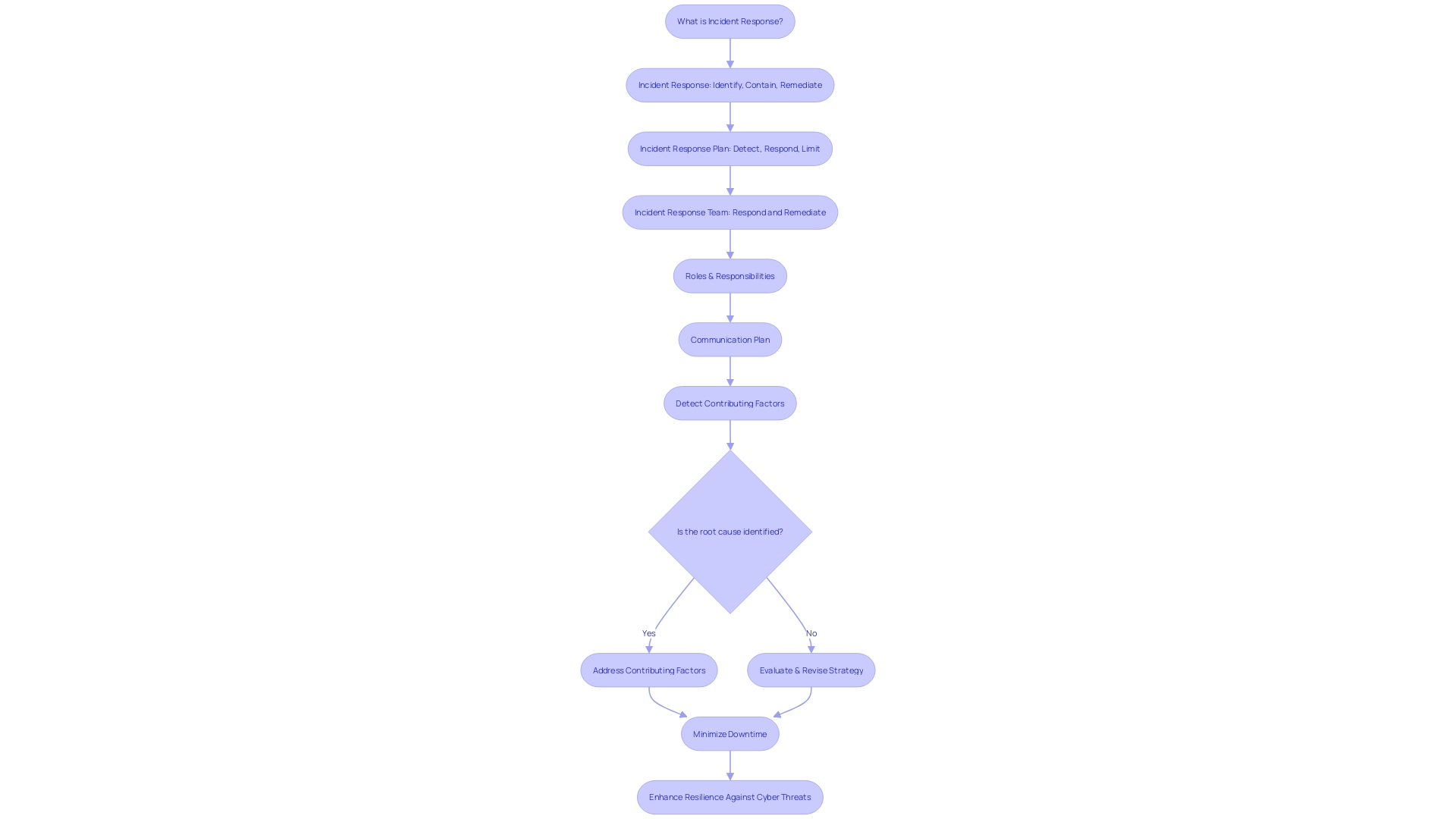
Identifying and Documenting Data Assets
To begin a thorough incident response plan, the first stage involves carefully cataloging every critical data repository vital to the heartbeat of the entity. This encompasses a broad spectrum of data, from the intricacies of customer data, proprietary intellectual creations, to the bedrock of financial documentation, and more. Each datum is a cog in the vast machinery of business continuity.
A deep dive into the company's public disclosures, such as annual reports, can shed light on the central systems that are the lifeblood of the enterprise. For instance, a government entity may hinge on systems managing public records or financial transactions. A nuanced understanding of these systems, their functionality, and the technological frameworks they employ is essential.
Moreover, the identification process should consider both internal and external data sources, whether neatly structured or amorphously unstructured, residing anywhere from spreadsheets to cloud services. In the digital era, companies are skilled at accumulating data, resulting in an overwhelming abundance of information across all technological frontiers.
The value of data surpasses its mere presence; it's shaped by its relevance and applicability to the strategic objectives of the entity. Therefore, identifying use cases that align with the goals of the entity is crucial. Data governance and strategy are mere vessels—value is realized only when they facilitate the achievement of overarching strategic aims.
Furthermore, as the Internet of Things (IoT) continues to intertwine everyday objects with the digital realm, the importance of recognizing data as a tangible, invaluable asset becomes apparent. Despite its absence on balance sheets, data's worth is undeniable, with the market actively trading data commodities and leveraging it to fuel artificial intelligence and analytics.
The integrity of data is the linchpin of its accuracy and reliability, ensuring that information remains unaltered and in its original state. This integrity is critical for maintaining data as a valuable asset, as its worth can diminish with any decline in accuracy. To uphold the data's value, companies are innovating ways to keep it current and applicable, tailoring data quality dimensions to their unique business needs and goals.
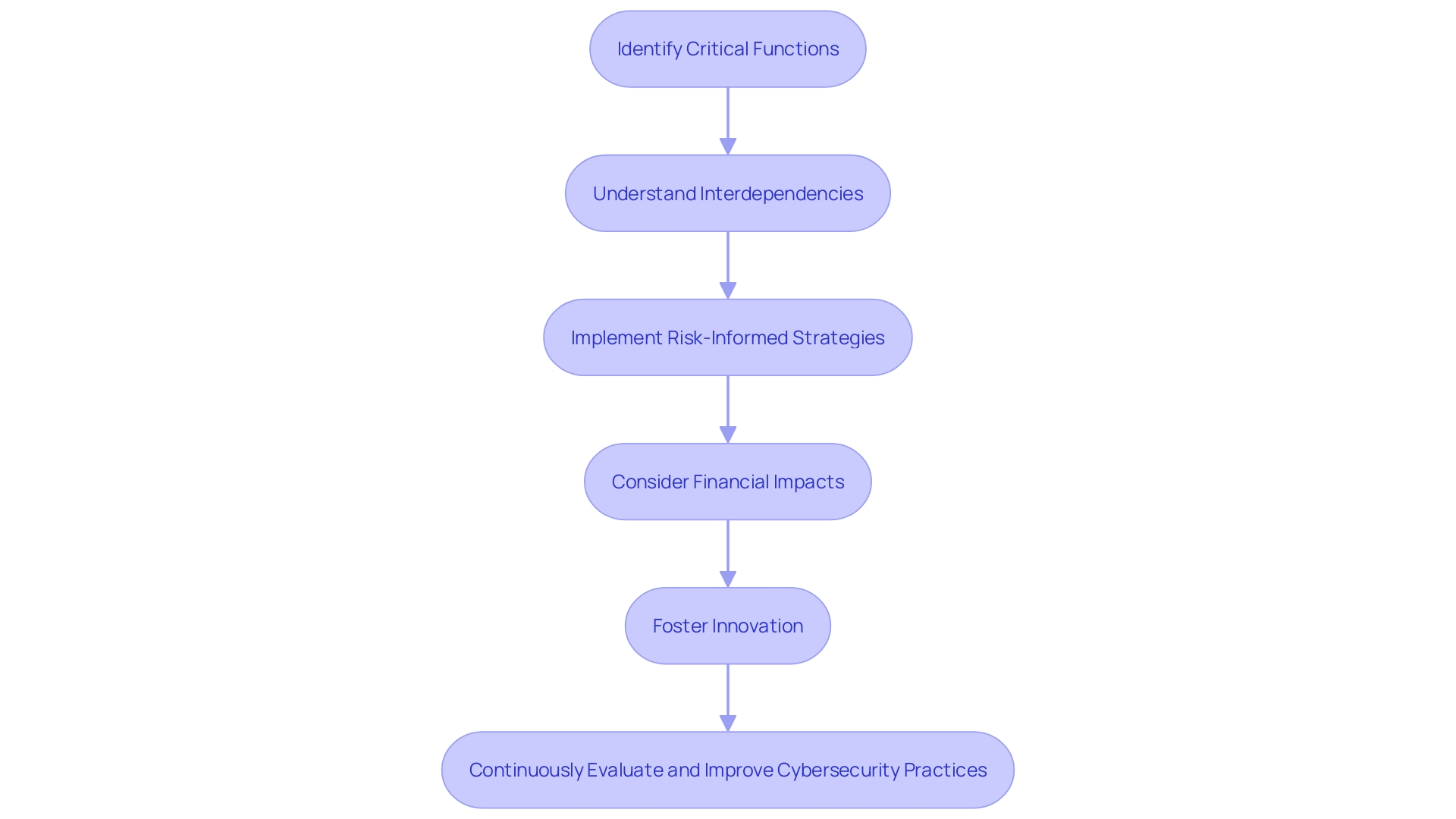
Assessing Potential Crises
Assessing cyber threats and preparing for potential crises is a critical task for organizations across various sectors. With cyber-attacks becoming increasingly sophisticated and pervasive, it's crucial to develop a response plan that is both comprehensive and adaptive. Consider, for instance, recent cyber events at MGM Resorts International and Clorox, which resulted in significant operational disruptions. These incidents underscore the importance of robust cybersecurity strategies that can withstand a range of threats, from ransomware to insider attacks.
Organizations must identify the critical functions within their ecosystems and understand the interdependencies that exist. This level of analysis is vital, as seen in the healthcare sector, where entities like Change Healthcare play a pivotal role due to their central position in processing medical claims. The interlinked structure of such entities makes them prime targets for cybercriminals, as their compromise can lead to cascading effects across the entire sector.
To counteract this, it is advised that entities develop and implement a risk-informed cybersecurity strategy, one which includes clear objectives, roles, and necessary resources. This approach has been advised to entities such as the Environmental Protection Agency (EPA) and the Department of Energy, with the aim of enhancing their cybersecurity frameworks.
Moreover, it's important to consider the very real financial impact of cyber incidents. The Ponemon Institute's report, sponsored by IBM Security, reveals that the average cost of a data breach hit a record high in 2023. This financial strain is a testament to the urgency with which entities must treat their cybersecurity measures.
Innovation in cybersecurity, often referred to as 'category creation,' is crucial. As the threat landscape evolves, so too must the solutions that protect against these threats. It's about addressing new risks and changing the way security is managed across all surfaces, as highlighted by advancements in endpoint detection and reaction systems.
By taking proactive steps to understand and mitigate risks, organizations can safeguard their operations from the potentially devastating consequences of cyber-attacks. This involves a continuous cycle of evaluating, implementing, and improving cybersecurity practices to keep pace with an ever-changing threat environment.
Establishing Employee Roles and Responsibilities
A thoroughly-documented plan for addressing unexpected events is a fundamental component of cybersecurity strategy. It outlines the systematic procedures for each phase of addressing an event and provides clear guidelines for roles and responsibilities, communication protocols, and actions. Defining distinct roles within the response team is crucial, ensuring each member understands their duties and the expectations placed upon them.
A responsibility matrix, clarifying who manages software and its configurations, becomes an essential tool. It answers critical questions such as the standard configuration settings and the communication pathway if these settings are altered. Particularly during major infrastructural changes—like migrating to a cloud environment—such clarity is indispensable. This matrix helps mitigate risks like configuration drift, where web server settings diverge from the norm due to unauthorized modifications.
The management workflow is designed to be a repeatable series of steps, aiming to handle issues efficiently from their initial report to resolution. This systematic approach is designed to minimize downtime and swiftly restore operations, crucial in a world where technology is deeply integrated into business processes. By addressing contributing factors and reinforcing preventive measures, entities can strengthen their resilience against disruptions.
Moreover, fostering a strong cybersecurity culture is integral to a robust security program. It involves instilling knowledge, beliefs, and behaviors that prioritize cybersecurity in everyday work conduct. This cultural foundation supports the incident response plan, ensuring team members are well-prepared and proactive in their designated roles.
Outlining Security Policies
To protect sensitive information within a company, it is crucial to establish strong security protocols involving data encryption, password management, and employee access controls. Take inspiration from the Arab National Bank's (anb) digital transformation, which necessitated the fortification of their cybersecurity measures to support their goal of providing 'financial services for everyone, everywhere, any time.' This was echoed by anb's Chief Security Officer, Ala Asali, who underscored the importance of modernizing their approach to meet the needs of a broader clientele while mitigating technological and industry-specific challenges.
Likewise, the hospitality industry, as exemplified by IHG Hotels & Resorts, acknowledges the significance of secure and reliable WI-Fi, not just for guest satisfaction but also for the seamless operation of cloud-based systems integral to their services. IHG's transition to a managed SD-WAN solution is anticipated to merge networking and security functionalities, thereby enhancing efficiency and yielding cost savings.
In the context of hybrid work environments, the importance of comprehensive security policies becomes even more pronounced. Employees connect from various locations, utilizing numerous applications that potentially expose sensitive data. This new reality necessitates a reevaluation of traditional security perimeters, emphasizing the adoption of multi-factor authentication (MFA) and other advanced security measures as standard practice.
The recent white paper update emphasizes the necessity for software manufacturers to take responsibility for customer security outcomes, advocate for radical transparency, and establish organizational structures that prioritize security. This directive is applicable not only to conventional software but also to AI systems and models. It underscores the need for 'secure-by-design' products that proactively protect against cyber threats.
To demonstrate the vital function of security leadership within companies, contemplate the perspectives of a CISO from a Global Financial Services Company, who emphasizes the worth of interactive exercises that aid non-technical leaders in comprehending the consequences of security breaches. This approach is supported by research from ASIS, which delves into access control best practices, informed by contributions from over 1,000 security professionals.
In an ever-evolving security landscape, it is crucial for organizations to continuously adapt and reinforce their security policies, ensuring that they are comprehensive, enforceable, and aligned with the latest industry standards and best practices.
Training the Incident Response Team
Continuous education and training are crucial to the proficiency of any response (IR) team. With cyber threats evolving rapidly, the team must stay abreast of the latest security trends through dynamic learning methods such as simulated cyber attack exercises and tabletop discussions. These training scenarios not only sharpen technical skills but also reinforce operational and managerial aspects crucial for mitigating events effectively. Engaging in exercises that mimic real-world cyber crises ensures the team can adeptly navigate the complexities of actual breaches, focusing on swift containment, eradication, and recovery to minimize organizational disruption.
Recent statistics underscore the necessity of rigorous training. For instance, during the first half of 2023, AI-based detection systems analyzed ninety-five billion events, identifying 985,000 as potential security alarms. This volume of data highlights the intricate nature of event detection and the need for teams to adeptly discern genuine threats from false positives. Furthermore, a study on embedded phishing training revealed that the periodic reminder of threats, rather than the content itself, significantly improves secure behavior. Such insights are invaluable for developing training programs that effectively prepare responders for real-time threat mitigation.
'Incident management exercises must also include clear communication strategies, both internally and externally'. The intricacy of cyber event reporting necessitates that teams comprehend how to navigate between occurrences, alerts, and situations, employing these terms accurately within their plans of action. Moreover, the capacity to effectively communicate in times of emergency is frequently the weakest aspect in organizational reaction, underscoring the significance of incorporating strong communication protocols into training curricula.
The integration of security into team training is no longer optional but a necessity. The National Cybersecurity Education Colloquium has recognized the challenge of effectively weaving security into educational frameworks, reinforcing the importance of treating security as a core knowledge area rather than an elective. By undergoing thorough and strategic training, teams can be provided with the tools and knowledge required to address the cyber threats of today and tomorrow.
Common Pitfalls to Avoid in Incident Response Planning
Creating an incident response strategy calls for a holistic approach that incorporates your organization's distinctive objectives and capabilities. A comprehensive strategy not only outlines the roles and responsibilities, communication strategies, and standardized protocols but also defines terms such as 'event,' 'alert,' and 'incident' with precision to avoid any confusion. For instance, an 'event' could be specified as any observable change in system settings, status, or communications.
Regular testing of your strategy is crucial. A thoroughly documented response procedure may involve sub-processes such as escalation, triage, and activation of alternate communication channels. However, the true effectiveness of the strategy is only realized when it's tested against real-world scenarios. By breaking down the plan into its core processes, ranking them by criticality and effort required for testing, you can ensure that each component functions as expected when a real event happens.
A reportable cyber event, as defined in recent publications, includes significant loss of confidentiality, integrity, or availability of critical systems, disruption of business operations, unauthorized disclosure of personal information, and potential disruption to other critical infrastructure. Comprehending the extent and consequences of such occurrences is crucial for efficient planning.
Besides handling incidents, a thorough strategy for recovering from disasters is essential. It should encompass data backup and restoration protocols, with regular checks to ensure data integrity, and an audit of IT systems and assets. A failure to prepare for disaster recovery equates to planning for failure when a crisis strikes.
By taking into account the impacts on stakeholders, protecting vital assets, and upholding internal procedures and systems, you can create a tailor-made plan for addressing unexpected events that is in line with your business structure and fosters organizational expansion. Adopting a design approach that prioritizes the needs of humans in this planning phase can enable your company to effectively respond to occurrences, thus reducing downtime and maintaining business continuity.
Benefits of Outsourcing Incident Response
Outsourcing addressing unexpected events offers organizations a strategic advantage in today's complex cybersecurity landscape. By enlisting the services of specialized cybersecurity firms, companies not only gain immediate access to a wealth of expertise and cutting-edge tools but also benefit from the around-the-clock vigilance that these partners provide. Such collaboration is a force multiplier, allowing companies to reinforce their internal resources with the robust capabilities of their partners.
This strategic partnership is exemplified in the case of multi-utility providers, who are tasked with safeguarding essential services and sensitive customer data. By integrating external cybersecurity experts into their operations, these providers fortify their security posture, transforming these experts into an operational extension of their team. Similarly, comprehensive IT solution firms, through collaboration and deep integration, become pivotal in driving the success of their clients, offering a suite of services that range from managed services to consulting, all aimed at propelling businesses forward.
A crucial element of addressing unexpected events, as emphasized in different reports, entails a comprehensive strategy that encompasses technical, operational, and managerial measures. From detecting to analyzing, containing, eradicating, recovering, and conducting post-incident analysis, the goal remains to minimize the impact, restore normal operations promptly, and preempt future breaches. The development of answering to an occurrence from a responsive impromptu process to an organized methodology highlights the need for a planned approach that includes contracting out as a viable component.
Statistics further emphasize the significance of a strong strategy for handling unexpected events. Organizations, such as those surveyed by the SANS Institute, show a commitment to improving cybersecurity operations, with data-driven insights revealing emerging trends and the critical need for operational threat hunting, SOAR, and staff hiring and retention strategies. This strategic insight highlights the vital role played by outsourced partnerships in strengthening a company's readiness for unforeseen events and overall security structure.
In summary, as businesses acknowledge the seriousness of cybersecurity risks, the inclusion of outsourced emergency management abilities is becoming a vital element of a comprehensive security plan. This collaboration guarantees that entities can endure and skillfully react to the complex and constantly changing cyber hazards that they encounter.
Best Practices for Incident Response
To ensure a successful handling of incidents, organizations are recommended to develop a strong Incident Management Strategy (IMS) that delineates the processes for identifying, reacting to, and mitigating the impacts of cyberattacks. Key components of an IRP include clear guidelines on roles and responsibilities, communication plans, and standardized protocols for addressing. Teams dedicated to handling unexpected events should be composed of capable individuals who can effectively address and reduce the impact of such occurrences, like a Reporter, Keymaster, and Fixer, as these positions are vital in times of crisis.
Testing the process of handling unexpected events periodically is essential. This can be achieved by breaking down the IRP into sub-processes, evaluating their criticality, and conducting drills to identify and address any gaps. As observed by an experienced response professional, being ready with a 'jump bag'âa compilation of necessary tools and softwareâis crucial for immediate and efficient response to cyber incidents.
Moreover, comprehending the difference between events, alerts, and occurrences is crucial to prevent confusion in communication. A misconfiguration or unauthorized code changes often serve as contributing factors that worsen situations, emphasizing the need for continuous monitoring and maintenance.
Recent recommendations from the Department of Homeland Security highlight the significance of aligning cyber event reporting to facilitate trend analysis and enhance national cybersecurity. This approach aids in identifying malicious activities and supports organizations in preventing and recovering from attacks. Finally, it is important to be mindful of the effects of cyber occurrences, which can vary from harm to reputation to penalties imposed by regulations, and make necessary preparations to minimize such risks.
Testing and Reviewing the Incident Response Plan
To protect the integrity of IT systems and ensure uninterrupted business operations, regular validation of the plan for handling unexpected events is crucial. This requires not only regular exercises and scenario simulations but also a thorough analytical method to uncover root causes and contributing factors to potential occurrences. For instance, a thorough review might reveal a configuration drift in a web server, a seemingly minor issue that could lead to significant vulnerabilities if left unchecked.
A successful event management workflow is crucial to dealing with such occurrences, covering a comprehensive strategy for event identification, classification, response, and resolution. This robust system ensures that organizations can swiftly recover from disruptions, thereby minimizing downtime and mitigating risks. In practice, this means asking probing questions to get to the heart of the matter: What triggered the issue? Why did certain controls fail to prevent it? Through such iterative inquiry, teams can pinpoint root causes and secondary factors, such as unauthorized code changes or external service issues, that may exacerbate the situation.
Recent occurrences have emphasized the crucial importance of cyber event reporting. A significant event can lead to significant data breaches or operational disruptions, with far-reaching impacts on public health, safety, and economic stability. Acknowledging this, authorities have proposed federal cyber reporting requirements designed to streamline the collection of essential information while reducing duplicative efforts across various sectors.
Ultimately, the goal is to enhance the resilience of enterprises in today's technology-driven world. By utilizing organized procedures and the combined knowledge of a team, organizations are more prepared to manage emergencies with efficiency and effectiveness, as emphasized by industry experts. Continuous improvement and adaptation of incident management plans using insights from real-world scenarios and regulatory frameworks are vital to maintain a state of readiness for any potential cyber threats.
Conducting Tabletop Exercises and Training
Tabletop exercises, also referred to as TTX or TTE, offer a distinctive chance for teams to discuss their roles and suitable actions during hypothetical emergencies. These sessions are intended to be casual and cooperative, enabling team members to go through different scenarios and explore alternatives without the stress of a real crisis. The focus of these exercises is on cyber security and disaster recovery, critical areas where preparedness is paramount.
During a tabletop exercise, participants address significant questions such as the immediate actions required in response to a breach, the process for filing cyber insurance claims, and methods for assessing the extent of the breach. Additionally, they contemplate the necessity of notifying data owners and consider the long-term consequences for the business.
The objective of these exercises goes beyond the immediate goals of the participants. While team members may aim to restore databases swiftly, the main objective is to thoroughly evaluate the company's disaster recovery plan and the team's collective problem-solving abilities. As recommended by the National Association of Regulatory Utility Commissioners, objectives should be SMART—specific, measurable, achievable, relevant, and time-bound—to ensure clarity and effectiveness.
In contrast to more intense functional exercises or full-scale simulations involving emergency personnel, tabletop exercises are characterized by their non-threatening, brainstorming environment. They serve to stress-test protocols and encourage a proactive stance towards emergency preparedness, ultimately enhancing a firm's resilience to unforeseen disasters.
Continuous Improvement and Lessons Learned
The ever-changing field of cybersecurity requires organizations to take a proactive approach towards addressing security events. After a cyber event, it is crucial to conduct thorough post-event evaluations. These reviews serve to extract vital insights, which then feed back into refining emergency plans. Gaining insights from occurrences, such as those encountered by CloudFlare and MITRE, showcases the importance of exchanging knowledge within the sector. CloudFlare's prompt detection and handling of a threat on their Atlassian server, along with the implementation of Zero Trust principles, demonstrated effective containment of the situation. Meanwhile, MITRE's approach to an intrusion into their network, involving independent analysis and prioritizing knowledge dissemination, underscores the importance of collaboration and transparency in enhancing cybersecurity measures.
Significant is the development of tools for handling unexpected events, which have become more advanced and extensive over time. The concept of a 'jump bag'—a collection of essential tools for immediate response—is now more crucial than ever, highlighting the need for readiness and swift action. Therefore, entities must not solely concentrate on the technological elements but also on developing a culture of handling unexpected events that embraces constant enhancement and acquiring knowledge from every unexpected event, significant or insignificant.
Statistics highlight the importance of a well-organized approach to incident handling, including the efficient utilization of AIOps for incident management. This allows companies to utilize automation, promoting a more resilient and responsive IT infrastructure. By implementing proven methods and leveraging case studies, organizations can not only enhance their immediate response capabilities but also contribute to a more secure ecosystem. Thus, a commitment to ongoing learning, combined with strategic application of technological advancements, is the cornerstone of a robust cybersecurity posture.
Conclusion
In today's digital age, organizations must prioritize the development of a robust incident response plan (IRP) to effectively safeguard their assets. An IRP provides a systematic and structured approach to addressing cybersecurity threats, ensuring teams are prepared to respond effectively.
Key components of an effective IRP include clear responsibilities, effective communication strategies, and standardized response actions. Regular testing of the plan is crucial to uncover weaknesses and ensure essential processes are effective. Collaboration across business units is vital for a coordinated response to cyber threats.
Customizing the IRP to reflect the organization's unique needs is essential, considering the potential impact on business operations and stakeholder interests. The plan should encompass a broad spectrum of incidents, addressing those that significantly affect critical systems, disrupt operations, or compromise sensitive information.
The incident response process involves steps such as identification and logging, impact assessment, investigation and analysis, mitigation and resolution, and thorough documentation and communication. Preparation is key, with organizations needing a deep understanding of their security posture. Clear definitions and compliance with legal obligations ensure transparency.
Swiftly isolating impacted systems, assembling the right team, and restoring data and system functionality from secure backups are crucial for effective incident response. Collaboration with federal agencies and leveraging insights enhance an organization's capabilities.
Post-incident activities, including analysis and knowledge sharing, contribute to refining response strategies. Continuous improvement and proactive reassessment of teams and processes are vital to stay ahead of threats.
Crafting a robust IRP requires comprehensive documentation and customization. Continuous education and training are pivotal for the proficiency of the incident response team. Outsourcing incident response offers access to specialized expertise and around-the-clock vigilance.
In conclusion, an incident response plan is a critical component of an organization's cybersecurity strategy. By following best practices, continuously improving response strategies, and leveraging partnerships, organizations can enhance their resilience against cyber threats and minimize operational impact.




